Optical Systems Identification through Rayleigh Backscattering
Abstract
1. Introduction
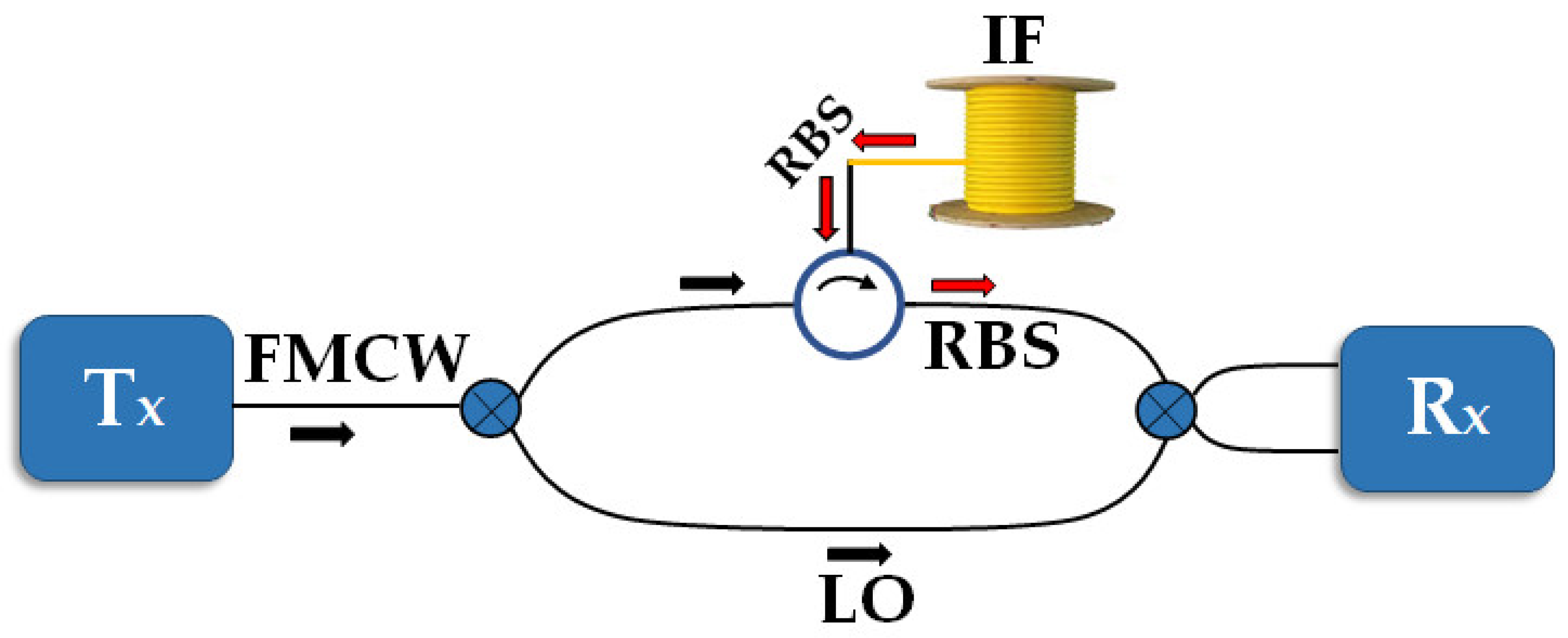
2. Reading the Network’s Constituent Devices’ Signatures
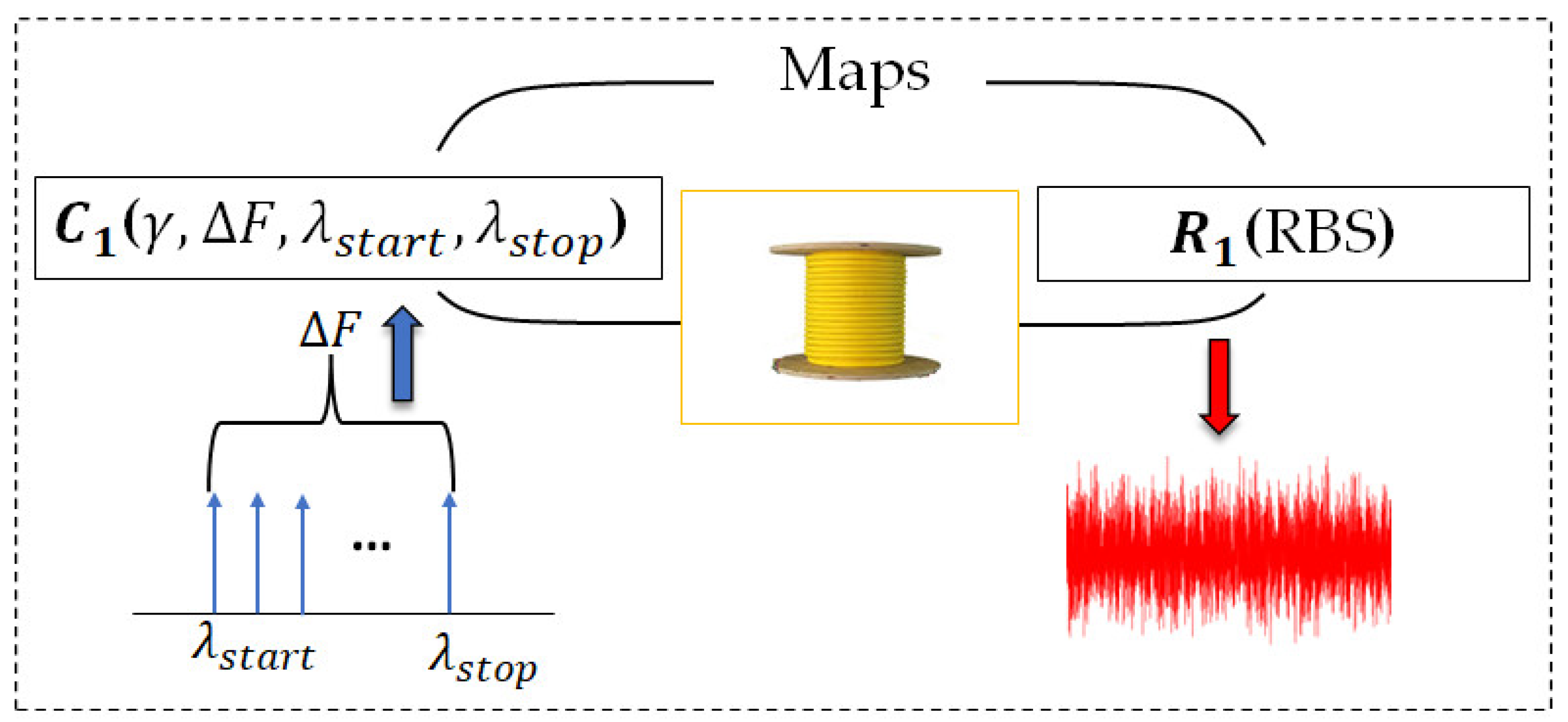
2.1. Signature Extraction
2.2. Binary Signature
3. Signature Evaluation
- (A)
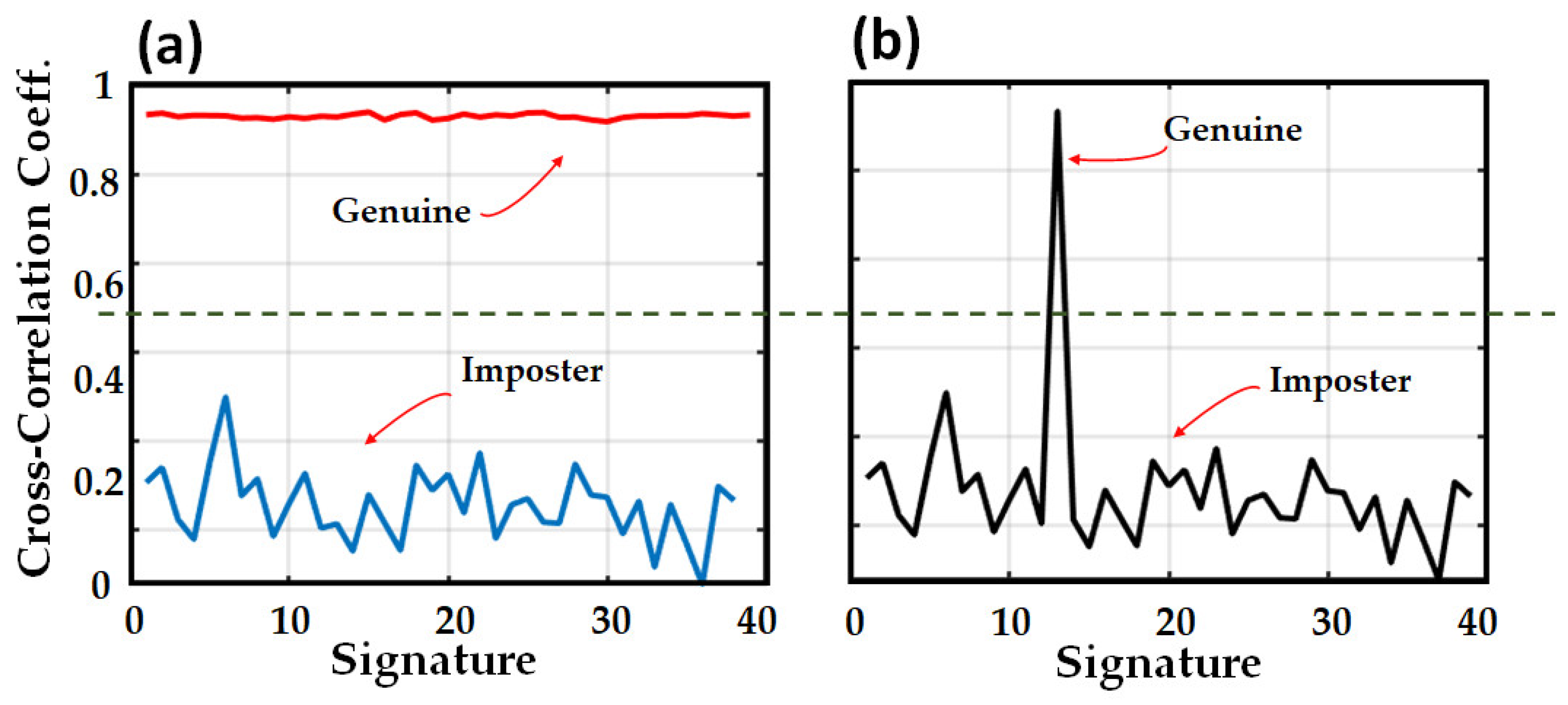
- Cross-Correlation Coefficient (XCOR-C):
- shows how distinguishable the generated signatures from a single fiber (OPUF) are with different challenges;
- shows that noisy signature is distinguishable from an imposter version which is generated with the same OPUF but with the wrong challenge;
- assists in finding the best challenges to generate more reliable signatures.
- (B)
- Euclidean Distance (ED):
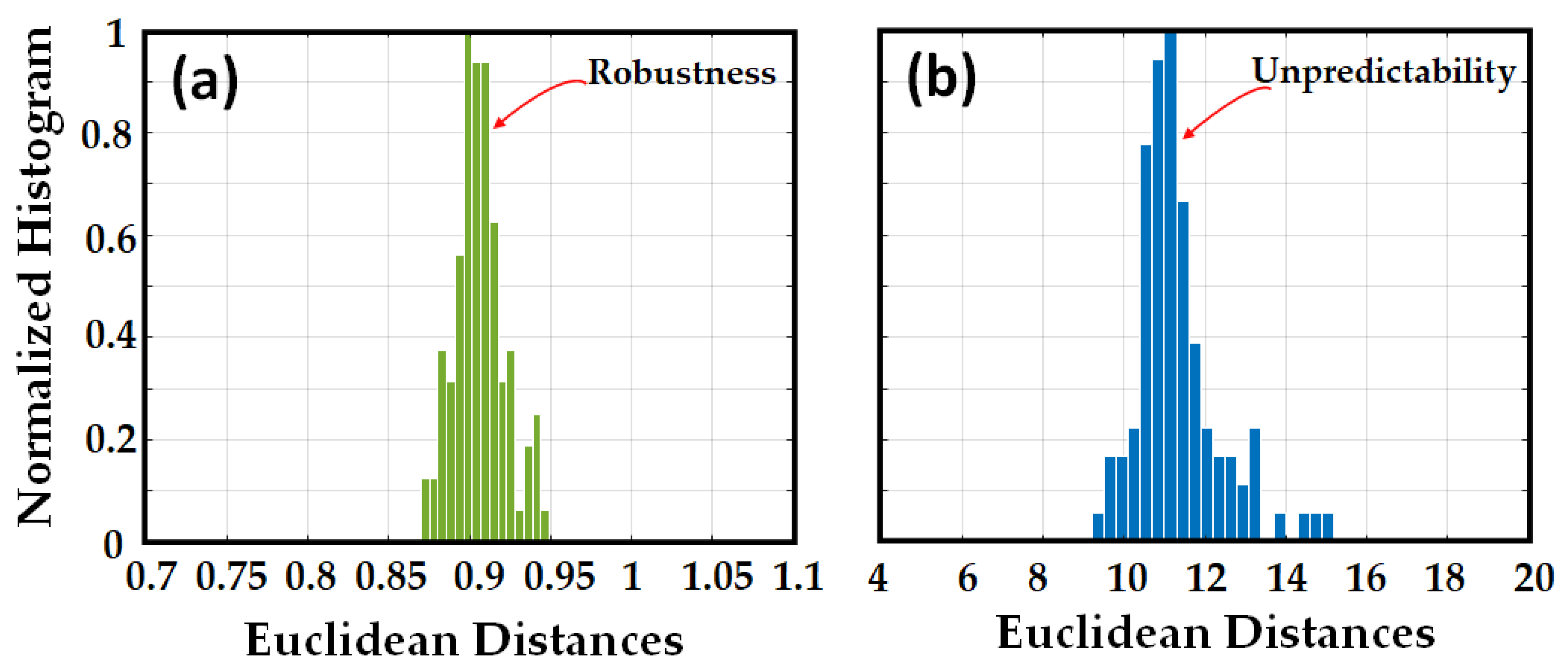
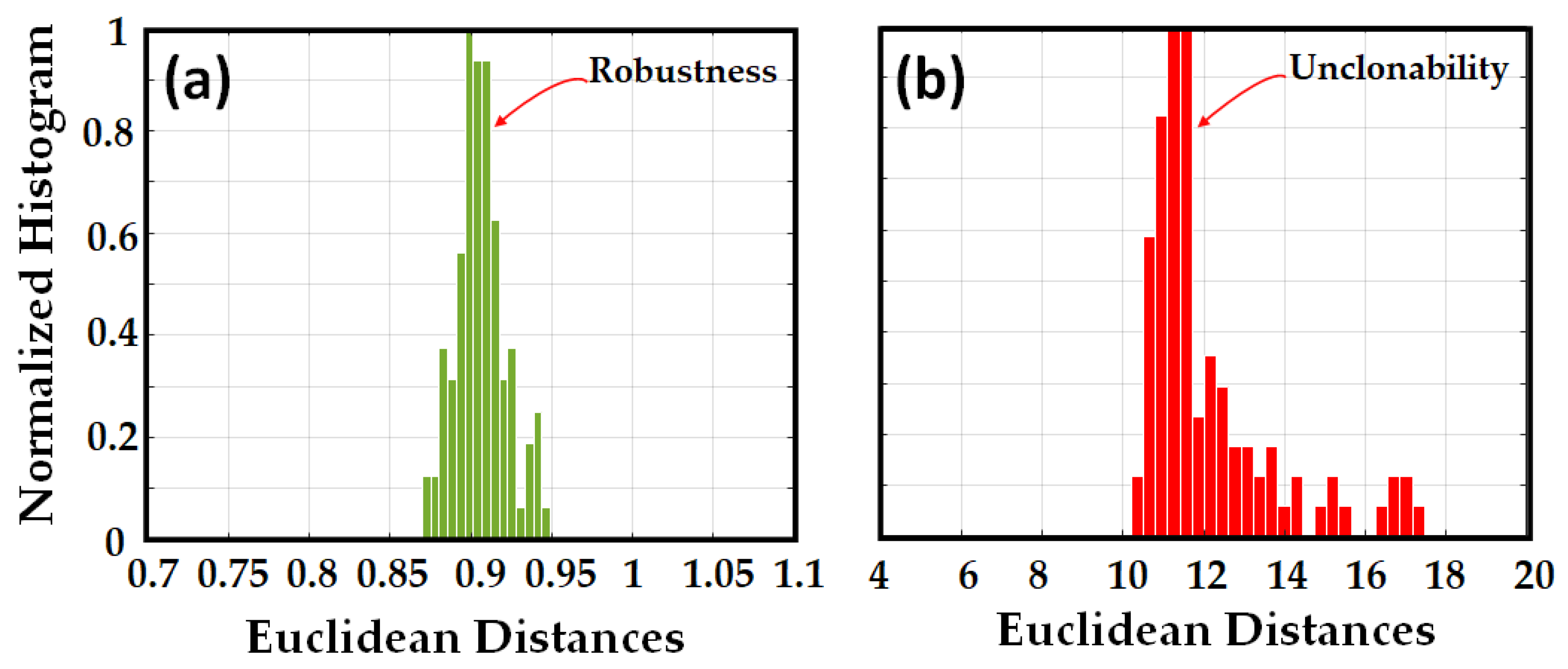
- The ED between the RBS obtained through several measurements of the same OPUF and the same challenge translates into reproducibility;
- ED between the RBS obtained through several measurements of the same OPUF but different challenges indicates unpredictability;
- ED between the RBS obtained through several measurements of various OPUFs but with the same challenges indicates unclonability.
- (C)
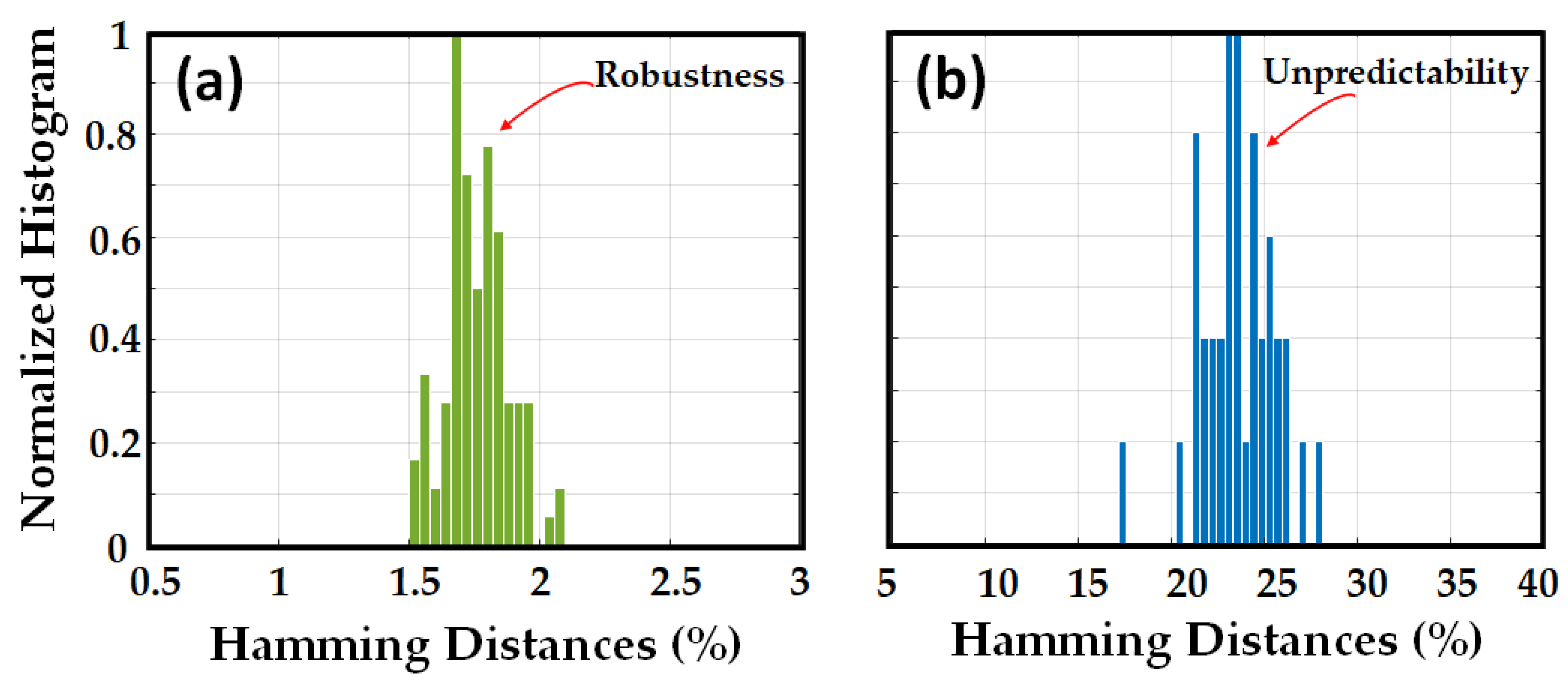
- Hamming Distance (HD):
- HD between the binary sequence achieved through several measurements of the same OPUF and the same challenge indicates reproducibility;
- HD between the binary sequence achieved through several measurements of the same OPUF but different challenges indicates unpredictability;
- HD between the binary sequence achieved through several measurements of various OPUFs but with the same challenges indicates unclonability;
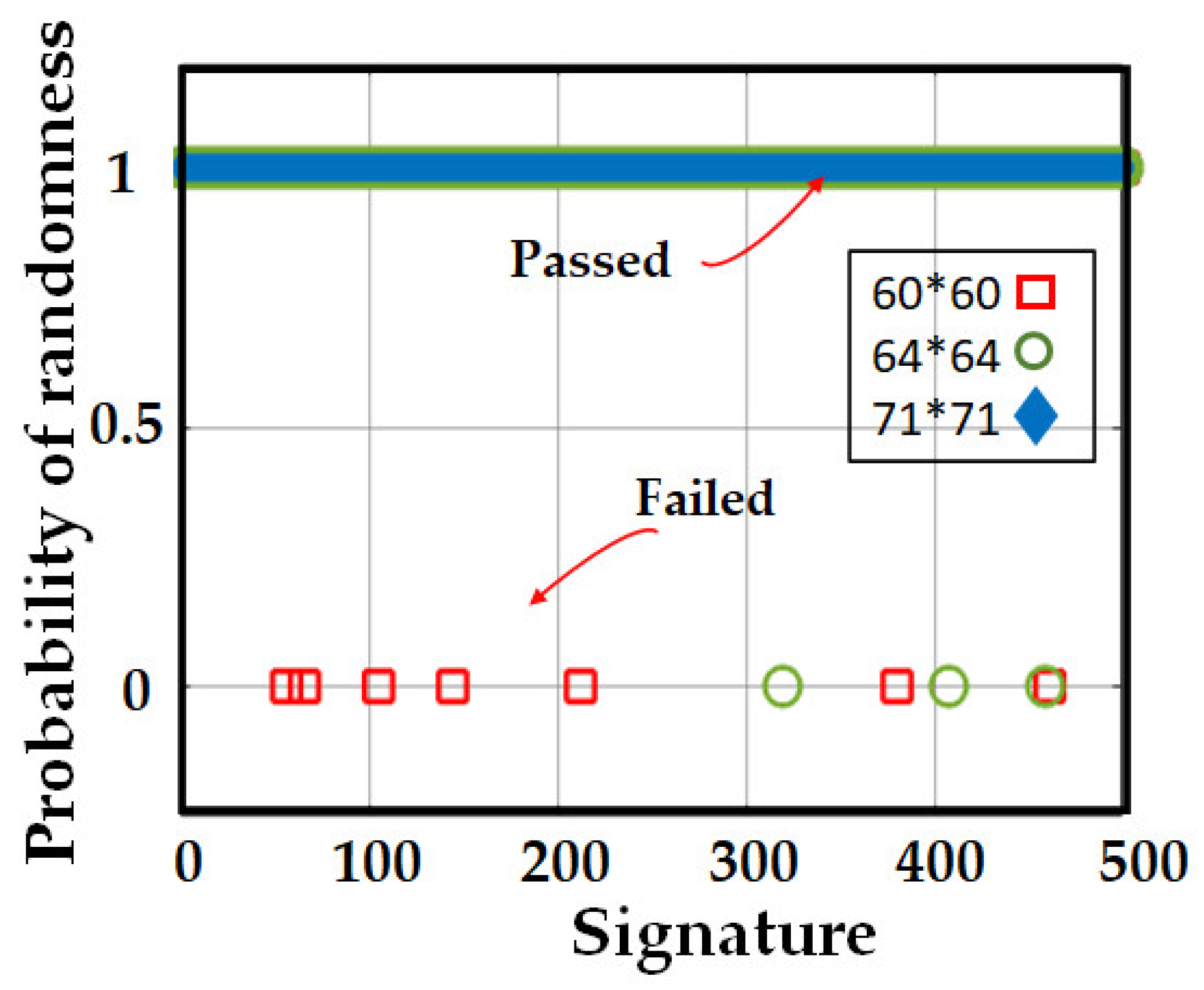
- (D) Statistical Test Suite (STS)
4. Security Validation
4.1. Signature Evaluation through the ED and HD Metrics
4.2. Signature Evaluation XCOR-C
4.3. Cyber Security
5. Discussion
- the transmitter reads the Channel Signature and Receiver Signature to be sure that the information will pass to the specific channel and reach the specific receiver;
- the receiver reads the Transmitter Signature and Channel Signature so that the receiver knows the sender and the physical path;
- the transmitter reads the receiver, and the receiver acquires the Transmitter Signature so that both know with whom they are talking. Both may even check for Channel Signatures to check the path.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Andy, H. Fiber Optic Cable Market-Growth, Trends, COVID-19 Impact, and Forecast (2021–2026); Mordor Intelligence: Dublin, Ireland, 2021. [Google Scholar]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Zhou, X.; McKay, M.R. Secure transmission with artificial noise over fading channels: Achievable rate and optimal power allocation. IEEE Trans. Veh. Technol. 2010, 59, 3831–3842. [Google Scholar] [CrossRef]
- He, J.; Giddings, R.; Jin, W.; Tang, J. DSP-Based Physical Layer Security for Coherent Optical Communication Systems. IEEE Photonics J. 2022, 14, 7250611. [Google Scholar] [CrossRef]
- Lei, C.; Lin, R.; Li, Y.; Wang, B.; Zhang, M.; Zhao, Y.; Zhang, J. Integration of Self-Adaptive Physical-Layer Key Distribution and Encryption in Optical Coherent Communication. J. Light. Technol. 2023, 1–8. [Google Scholar] [CrossRef]
- Gidney, C.; Ekerå, M. How to factor 2048 bit RSA integers in 8 hours using 20 million noisy qubits. Quantum 2021, 5, 433. [Google Scholar] [CrossRef]
- Gong, Y.; Wonfor, A.; Hunt, J.H.; Penty, R. Physical layer security monitoring of optical communication using a quantum pilot tone signal. In Proceedings of the CLEO: QELS_Fundamental Science, San Jose, CA, USA, 15–20 May 2022; Optica Publishing Group: Washington, DC, USA, 2022; pp. 1–2. [Google Scholar]
- Bennett, C.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984; IEEE Press: Piscataway, NJ, USA, 1984; pp. 175–179. [Google Scholar]
- Cavaliere, F.; Prati, E.; Poti, L.; Muhammad, I.; Catuogno, T. Secure quantum communication technologies and systems: From labs to markets. Quantum Rep. 2020, 2, 80–106. [Google Scholar] [CrossRef]
- Chen, L.; Jin, W.; He, J.; Giddings, R.P.; Huang, Y.; Tang, J. A Point-to-multipoint Flexible Transceiver for Inherently Hub-and- Spoke IMDD Optical Access Networks. J. Light. Technol. 2023, 1–12. [Google Scholar] [CrossRef]
- Wang, L.; Mao, X.; Wang, A.; Wang, Y.; Gao, Z.; Li, S.; Yan, L. Scheme of coherent optical chaos communication. Opt. Lett. 2020, 45, 4762–4765. [Google Scholar] [CrossRef]
- Antonik, P.; Gulina, M.; Pauwels, J.; Rontani, D.; Haelterman, M.; Massar, S. Spying on chaos-based cryptosystems with reservoir computing. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Liang, X.; Zhang, C.; Luo, Y.; Wang, X.; Qiu, K. Secure Encryption and Key Management for OFDM-PON Based on Chaotic Hilbert Motion. J. Light. Technol. 2023, 41, 1619–1625. [Google Scholar] [CrossRef]
- Chen, W.; Mu, P. Research on methods of enhancing physical layer security of optical fiber communication system in the smart grid. J. Phys. Conf. Ser. 2022, 2237, 012002. [Google Scholar] [CrossRef]
- Jiang, N.; Zhao, A.; Liu, S.; Zhang, Y.; Peng, J.; Qiu, K. Injection-locking chaos synchronization and communication in closed-loop semiconductor lasers subject to phase-conjugate feedback. Opt. Express 2020, 28, 9477–9486. [Google Scholar] [CrossRef]
- Wohlgemuth, E.; Yoffe, Y.; Attia, I.; Imran, M.; Lakshmijayasimha, P.D.; Marotta, A.; Goki, P.N.; Shalom, H.; Fresi, F.; Antonelli, C.; et al. A Field Trial of Multi-Homodyne Coherent Detection Over Multi-Core Fiber for Encryption and Steganography. J. Light. Technol. 2023, 41, 2723–2735. [Google Scholar] [CrossRef]
- Wu, B.; Wang, Z.; Tian, Y.; Fok, M.P.; Shastri, B.J.; Kanoff, D.R.; Prucnal, P. R Optical Steganography Based on amplified spontaneous emission noise. Opt. Express 2013, 21, 2065–2071. [Google Scholar] [CrossRef]
- Rout, H.; Mishra, B.K. Pros and cons of cryptography, steganography and perturbation techniques. IOSR J. Electron. Commun. Eng. 2014, 76, 81. [Google Scholar]
- Mishra, R.; Bhanodiya, P. A review on steganography and cryptography. In Proceedings of the 2015 International Conference on Advances in Computer Engineering and Applications, Ghaziabad, India, 19–20 March 2015; pp. 119–122. [Google Scholar]
- Kamal, K.Y.; Muresan, R.; Al-Dweik, A. CMOS-Based Physically Unclonable Functions: A Review and Tutorial; Middle Technical University: Baghdad, Iraq, 2021. [Google Scholar] [CrossRef]
- Tarik, F.B.; Famili, A.; Lao, Y.; Ryckman, J.D. Scalable and CMOS compatible silicon photonic physical unclonable functions for supply chain assurance. Sci. Rep. 2022, 12, 15653. [Google Scholar] [CrossRef]
- Zhang, L.; Fong, X.; Chang, C.H.; Kong, Z.H.; Roy, K. Highly reliable memory-based physical unclonable function using spin-transfer torque MRAM. In Proceedings of the 2014 IEEE International Symposium on Circuits and Systems (ISCAS), Melbourne, VIC, Australia, 1–5 June 2014; pp. 2169–2172. [Google Scholar]
- Rührmair, U.; Devadas, S.; Koushanfar, F. Security based on physical unclonability and disorder. In Introduction to Hardware Security and Trust; Springer: Berlin/Heidelberg, Germany, 2011; pp. 65–102. [Google Scholar]
- Shakiba-Herfeh, M.; Chorti, A.; Vincent Poor, H. Physical layer security: Authentication, integrity, and confidentiality. In Physical Layer Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 129–150. [Google Scholar]
- Rothe, S.; Koukourakis, N.; Radner, H.; Lonnstrom, A.; Jorswieck, E.; Czarske, J.W. Physical layer security in multimode fiber optical networks. Sci. Rep. 2020, 10, 2740. [Google Scholar] [CrossRef]
- Horstmeyer, R.; Judkewitz, B.; Vellekoop, I.M.; Assawaworrarit, S.; Yang, C. Physical key-protected one-time pad. Sci. Rep. 2013, 3, 3543. [Google Scholar] [CrossRef]
- Silvério, T.; Dias, L.; Ramalho, J.F.; Correia, S.F.; Fu, L.; Ferreira, R.A.; André, P.S. Functional mobile-based two-factor authentication by photonic physical unclonable functions. AIP Adv. 2022, 12, 085316. [Google Scholar] [CrossRef]
- Du, Y.; Jothibasu, S.; Zhuang, Y.; Zhu, C.; Huang, J. Unclonable optical fiber identification based on Rayleigh backscattering signatures. J. Light. Technol. 2017, 35, 4634–4640. [Google Scholar] [CrossRef]
- Nikolopoulos, G.M.; Fischlin, M. Quantum key distribution with post-processing driven by physical unclonable functions. arXiv 2023, arXiv:2302.07623. [Google Scholar]
- Pavanello, F.; O’Connor, I.; Rührmair, U.; Foster, A.C.; Syvridis, D. Recent advances in photonic physical unclonable functions. In Proceedings of the 2021 IEEE European Test Symposium (ETS), Bruges, Belgium, 24–28 May 2021; pp. 1–10. [Google Scholar]
- Goki, P.N.; Civelli, S.; Parente, E.; Caldelli, R.; Mulugeta, T.T.; Sambo, N.; Secondini, M.; PotÌ, L. Optical identification using physical unclonable functions. arXiv 2023, arXiv:2305.02141. [Google Scholar]
- Potì, L.; Goki, P.N.; Mulugeta, T.T.; Sambo, N.; Caldelli, R. Optical Fingerprint: A Possible Direction to Physical Layer Security, Authentication, Identification, and Monitoring. In Proceedings of the 2022 61st FITCE International Congress Future Telecommunications: Infrastructure and Sustainability (FITCE), Rome, Italy, 29–30 September 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Ding, Z.; Yao, X.S.; Liu, T.; Du, Y.; Liu, K.; Jiang, J.; Meng, Z.; Chen, H. Compensation of laser frequency tuning nonlinearity of a long range OFDR using deskew filter. Opt. Express 2013, 21, 3826–3834. [Google Scholar] [CrossRef] [PubMed]
- Zhao, S.; Cui, J.; Suo, L.; Wu, Z.; Zhou, D.P.; Tan, J. Performance investigation of OFDR sensing system with a wide strain measurement range. J. Light. Technol. 2019, 37, 3721–3727. [Google Scholar] [CrossRef]
- Ito, F.; Fan, X.; Koshikiya, Y. Long-range coherent OFDR with light source phase noise compensation. J. Light. Technol. 2011, 30, 1015–1024. [Google Scholar] [CrossRef]
- Tsuji, K.; Shimizu, K.; Horiguchi, T.; Koyamada, Y. Coherent optical frequency domain reflectometry for a long single-mode optical fiber using a coherent lightwave source and an external phase modulator. IEEE Photonics Technol. Lett. 1995, 7, 804–806. [Google Scholar] [CrossRef]
- Goki, P.N.; Mulugeta, T.T.; Sambo, N.; Caldelli, R.; Potì, L. Optical Network Authentication through Rayleigh Backscattering Fingerprints of the Composing Fibers. In Proceedings of the GLOBECOM 2022-2022 IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022; pp. 2146–2150. [Google Scholar] [CrossRef]
- Akriotou, M.; Fragkos, A.; Syvridis, D. Photonic Physical Unclonable Functions: From the Concept to Fully Functional Device Operating in the Field. arXiv 2020, arXiv:2002.12618. [Google Scholar] [CrossRef]
- Goki, P.N.; Mulugeta, T.T.; Sambo, N.; Potì, L. Network Authentication, Identification, and Secure Communication through Optical Physical Unclonable Function. In Proceedings of the 2022 European Conference on Optical Communication (ECOC), Basel, Switzerland, 18–22 September 2022; pp. 1–4. [Google Scholar]
- Seve, E.; Pesic, J.; Delezoide, C.; Giorgetti, A.; Sgambelluri, A.; Sambo, N.; Bigo, S.; Pointurier, Y. Automated fiber type identification in SDN-enabled optical networks. J. Light. Technol. 2019, 37, 1724–1731. [Google Scholar] [CrossRef]
- Soumplis, P.; Christodoulopoulos, K.; Quagliotti, M.; Pagano, A.; Varvarigos, E. Network planning with actual margins. J. Light. Technol. 2017, 35, 5105–5120. [Google Scholar] [CrossRef]


| Symbol | Description | Unit |
|---|---|---|
| Sweep rate | nm/s (or Hz/s) | |
| Sweep range | nm (or Hz) | |
| (or ) | Start sweeping wavelength (or frequency) | nm (or Hz) |
| (or ) | Stop sweeping wavelength (or frequency) | nm (or Hz) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nadimi Goki, P.; Mulugeta, T.T.; Caldelli, R.; Potì, L. Optical Systems Identification through Rayleigh Backscattering. Sensors 2023, 23, 5269. https://doi.org/10.3390/s23115269
Nadimi Goki P, Mulugeta TT, Caldelli R, Potì L. Optical Systems Identification through Rayleigh Backscattering. Sensors. 2023; 23(11):5269. https://doi.org/10.3390/s23115269
Chicago/Turabian StyleNadimi Goki, Pantea, Thomas Teferi Mulugeta, Roberto Caldelli, and Luca Potì. 2023. "Optical Systems Identification through Rayleigh Backscattering" Sensors 23, no. 11: 5269. https://doi.org/10.3390/s23115269
APA StyleNadimi Goki, P., Mulugeta, T. T., Caldelli, R., & Potì, L. (2023). Optical Systems Identification through Rayleigh Backscattering. Sensors, 23(11), 5269. https://doi.org/10.3390/s23115269








