Machine Learning-Based Anomaly Detection in NFV: A Comprehensive Survey
Abstract
:1. Introduction
2. Taxonomy of Network-Based Anomaly Detection in NFV
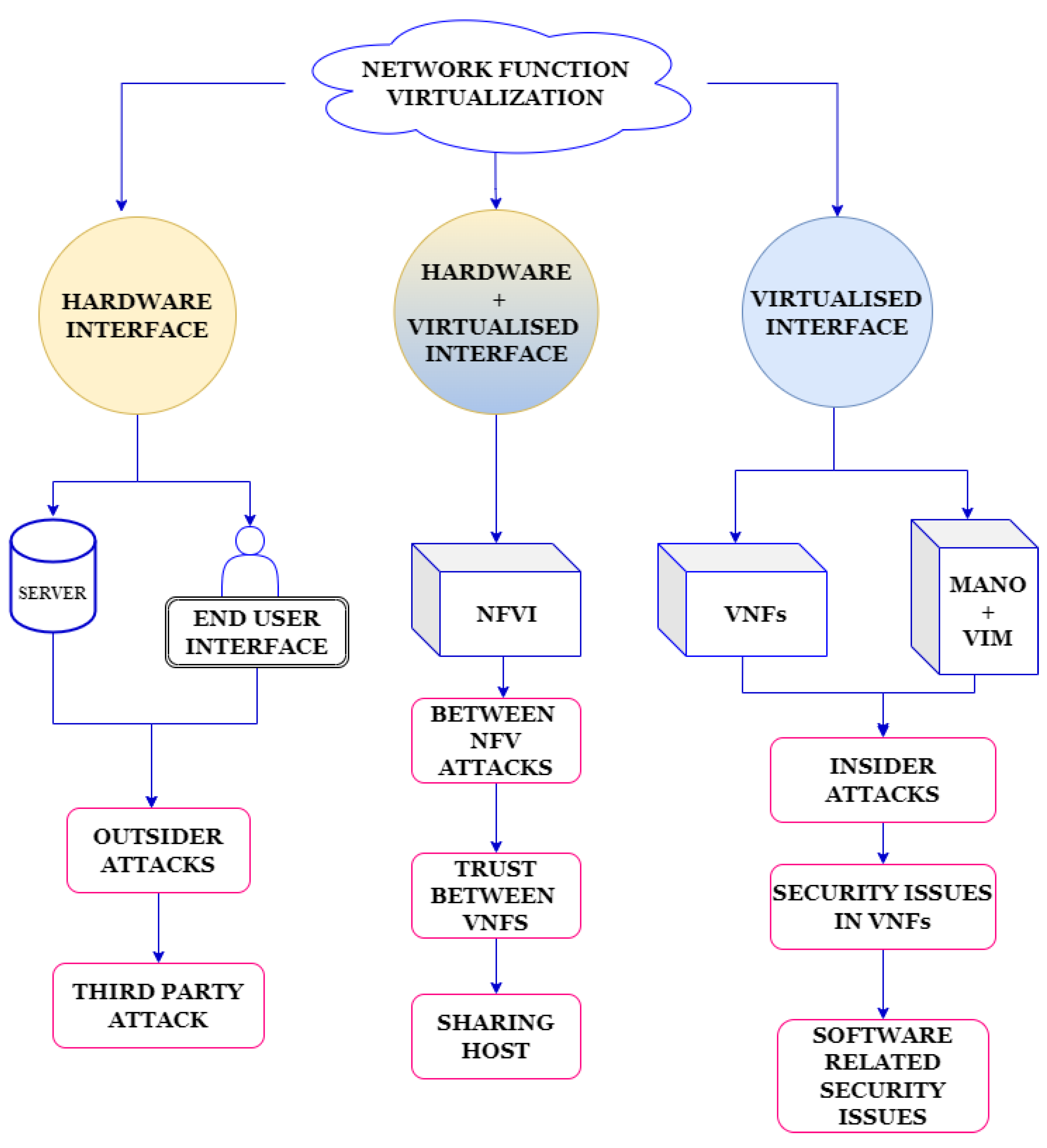
2.1. NFV Security Issues
2.2. Network-Based Anomaly Technique
2.2.1. Approaches for Anomaly Detection
2.2.2. Classification of Anomaly Detection
- a.
- Supervised Model
- b.
- Semi-supervised Model
- c.
- Unsupervised Model
2.2.3. Causes of Network Anomaly Detection
- a.
- Network Component Failure
- b.
- Non-Control Network Traffic
- c.
- Improper Monitoring
- d.
- Improper Security Perimeters
- e.
- Flash Crowd

2.2.4. Use Cases of Anomaly Detection
2.2.5. Challenges of Anomaly Detection
- (a)
- Runtime Anomaly Detection
- (b)
- Reducing False Alarm
- (c)
- Dimensionality Reduction
- (d)
- Adaptability to Unknown Attacks
- (e)
- Infrastructure Attacks
3. Review and Comparative Analysis of State-of-the-Art Anomaly Detection in NFV
3.1. State-of-the-Art Anomaly Detection in NFV
3.1.1. Anomaly Detection Using SMNRT
3.1.2. Matrix Differential Decomposition
3.1.3. Machine Learning-Base Early Anomaly Detection
3.1.4. Tree-Based Anomaly Detection
3.1.5. SLA-Aware Anomaly Detection
3.1.6. Markov Chain and K-Means Method
3.1.7. Distance-Based Anomaly Detection in NFV
3.1.8. Intelligent Orchestration of NFV for Anomaly
3.1.9. IFTM-Based Anomaly Detection in NFV
3.1.10. LSTM-Based Anomaly Detection in NFV
3.1.11. Unsupervised Neural Network SOM
3.2. Comparative Analysis of State-of-the-Art Anomaly Detection in NFV
- Supervised methods identify anomalies in the NFV network more quickly and accurately as compared to unsupervised methods.
- Supervised methods are either implemented in NFV orchestration and management block or VNFs services function block; this technique reduces the cost and resource utilization.
- Unsupervised methods are complex compared to supervised methods but detect novel anomalies in the NFV network.
- Unsupervised methods provide a runtime anomaly detection mechanism and are implemented as separate modules or service functions.
- Unsupervised methods have more false alarm rates than supervised methods [83].
- Unsupervised methods provide a more generalized solution for anomaly detection than supervised methods.
- Supervised methods also provide a mitigation process using root cause analysis and reduce costs by integrating with the NFV infrastructure.
- Unsupervised methods provide a zero-touch network [80] monitoring environment and automatic anomaly detection approach in the NFV, whereas supervised methods need human interaction to handle anomalies.
- Unsupervised methods also work in heterogeneous data environments in runtime scenarios [79].
| Proposed Methods | Year of Publication Strengths | Anomaly Detection Approach | ML-Based Algorithm | Strengths | Limitations | Accuracy | Future Work |
|---|---|---|---|---|---|---|---|
| SMNRT [66] | 2022 | supervised | HYBRID MODEL | Suitable for time-sensitive applications, high detection accuracy. Hybrid techniques detect anomalies in a complex and dynamic network. | Relies on labeled data for supervised learning. System’s performance may be affected by the quality. The system may require significant computational resources and expertise in machine learning. | 98% | More ML algorithms and neural network models. Address the issue of false positives. Improve real-time performance. Evaluate the proposed system in a real-world setting. |
| MDD [72] | 2019 | unsupervised | PCA | Multiple anomaly detection, handle localization, reduces computation and deployment difficulties. | Dynamic anomaly detection is not possible. | 97.24% | Develop an online-based anomaly detection system. |
| MLBEAD [73] | 2020 | supervised | Ran.F | Early detection of anomalies, anomaly handling mechanism, online detection. | A limited no. of anomalies are identifiable and need generalization, multiple algorithms are used. | 93% | Develop a more generalized mechanism for anomaly detection and also implement it in the Docker platform. |
| TBAD [74] | 2019 | unsupervised | Dec.T | Efficient anomaly detection, strong defense mechanism, timely detection of anomaly. | A small-level, real-time implementation required. | 90% | Develop a real-time online anomaly detection mechanism and use the same method with deep learning techniques. |
| SAAD [75] | 2020 | supervised | G.Bo.M | Strong identification for anomalies, good for web hosting scenarios. | Work only for web hosting, required generalization. | 95% | Extend the proposed method for large VNF scenarios. |
| MCKM [76] | 2018 | unsupervised | MC | Easily and more accurately identifies the anomaly in NFV, good defense mechanism, suitable for a large network, scalable. | Computational and resource utilization overhead. | 85% | Develop the same model using a deep-learning algorithm. |
| DBCAD [77] | 2018 | Unsupervised | DBCA | Strong defense mechanism against anomalies. Runtime legitimate behavior model for anomaly detection, low latency rate. | Detection of particular types of anomalies, more resource utilization. Human interaction required for mitigation. | 98.9% | Develop a more generalized model that covers all types of anomalies and automatically handles all processes from detection to mitigation. |
| IOCNF [78] | 2022 | Supervised | Fuzzy Logic | Minimize resource usage. Automatically mitigate anomalies in NFV. Work together with network orchestration and management module. | Work only limited datasets. Fewer features are considered for anomaly detection. | 90% | The method should be generalized. Consider large data traffic features. |
| IFTM [79] | 2018 | Unsupervised | LSTM | Reduces false alarm rate. Use the expert system to identify anomalies. | Depend upon administrative control. The method covers some specific data traffic. | 98% | Design should extend to the automatic detection of anomalies in NFV. The method should be generalized. |
| SYRROCA [80] | 2020 | Unsupervised | LSTM | Detect anomalies in a heterogeneous environment. Identifies anomaly dynamically and automatically. Provides zero-touch network orchestration in NFV. | Work only at the virtual layer. Use large metrics for anomaly detection. | 98% | Design should extend to physical and cross layers. Design for other types of data streams, such as VoIP, 4G, 5G, etc. |
| SOM [81] | 2021 | Unsupervised | Clustering | more accurate and efficient results. Joint analysis of system-level and application-level metrics. Effective in identifying similar input patterns. | Number of hyper-parameters that have to be decided. Non-negligible processing time. Not suitable for excessively large networks. | 99% | Hyperparameters to improve its accuracy and reduce false positives. Exploration of other unsupervised machine learning techniques, such as clustering. |
3.3. Quantitative Comparison of State-of-the-Art Anomaly Detection in NFV Network
| Proposed | Accuracy | Precision | Recall | F1-Score |
|---|---|---|---|---|
| SMNRT [66] | 0.98 | 0.83 | 0.98 | 0.90 |
| MDD [72] | 0.9724 | 0.89 | 0.91 | 0.90 |
| MLBEAD [73] | 0.93 | 0.92 | 0.89 | 0.91 |
| TBAD [74] | 0.90 | 0.92 | 0.91 | 0.92 |
| SAAD [75] | 0.95 | 0.94 | 0.89 | 0.91 |
| MCKM [76] | 0.85 | 0.95 | 0.95 | 0.95 |
| DBCAD [77] | 0.989 | NSp | NSp | NSp |
| IOCNF [78] | 0.90 | 0.91 | 0.92 | 0.91 |
| IFTM [79] | 0.98 | NSp | NSp | NSp |
| SYRROCA [80] | 0.98 | 0.94 | 0.93 | 0.94 |
| SOM [81] | 0.9959 | 0.9803 | 0.9992 | 0.9896 |
4. Open Research Issues and Challenges
4.1. Hybrid Approaches
4.2. Incremental Learning
4.3. Transfer Learning
4.4. Ensemble Methods
4.5. Explainable AI
4.6. Design Framework
5. Conclusions and Future Work
- The unsupervised algorithm works efficiently on cluster data, while the supervised algorithm first trains the system and then implements the output results.
- Anomaly detection methods that work on the principle of unsupervised algorithms give less accurate results than supervised algorithms.
- Anomaly detection methods that use supervised algorithms could be generalized, which is not easier in unsupervised algorithms.
- Supervised algorithms are accurate and faster to implement than unsupervised algorithms.
- A separate module design is a better solution for anomaly detection in NFV networks.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| SMNRT | Simple Median Near Real-Time |
| MDD | Matrix Differential Decomposition |
| MLBEAD | Machine Learning-Based Early Anomaly Detection |
| TBAD | Tree-Based Anomaly Detection |
| SAAD | SLA-Aware Anomaly Detection |
| MCKM | Markov Chain and K-means Method |
| DBCAD | Distance-based Clustering Anomaly Detection |
| BBA | Black Box Approach |
| Ran.F | Random Forest |
| G.Bo.M | Gradient Boosting Machine |
| Dec.T | Decision Tree |
| MC | Markov Chain |
| DBCA | Distance-based Clustering Algorithm |
| PCA | Principle Component Analysis |
| SYRROCA | System Radiography and Root Cause Analysis |
| IFTM | Identity Function and Threshold Model |
| IOCNF | Intelligent Orchestration of Containerized Network Function |
| SOM | Self-Organizing Map |
| NSp | Not Specified |
References
- Madi, T.; Alameddine, H.A.; Pourzandi, M.; Boukhtouta, A. NFV security survey in 5G networks: A three-dimensional threat taxonomy. Comput. Netw. 2021, 197, 108288. [Google Scholar] [CrossRef]
- Firoozjaei, M.D.; Jeong, J.P.; Ko, H.; Kim, H. Security challenges with network functions virtualization. Future Gener. Comput. Syst. 2017, 67, 315–324. [Google Scholar] [CrossRef]
- Fernandes, G.; Rodrigues, J.J.; Carvalho, L.F.; Al-Muhtadi, J.F.; Proença, M.L. A comprehensive survey on network anomaly detection. Telecommun. Syst. 2019, 70, 447–489. [Google Scholar] [CrossRef]
- Sairam, R.; Bhunia, S.S.; Thangavelu, V.; Gurusamy, M. NETRA: Enhancing IoT security using NFV-based edge traffic analysis. IEEE Sens. J. 2019, 19, 4660–4671. [Google Scholar] [CrossRef] [Green Version]
- Farris, I.; Taleb, T.; Khettab, Y.; Song, J. A survey on emerging SDN and NFV security mechanisms for IoT systems. IEEE Commun. Surv. Tutorials 2018, 21, 812–837. [Google Scholar] [CrossRef]
- Babiker Mohamed, M.; Matthew Alofe, O.; Ajmal Azad, M.; Singh Lallie, H.; Fatema, K.; Sharif, T. A comprehensive survey on secure software-defined network for the Internet of Things. Trans. Emerg. Telecommun. Technol. 2022, 33, e4391. [Google Scholar] [CrossRef]
- Molina Zarca, A.; Bernal Bernabe, J.; Farris, I.; Khettab, Y.; Taleb, T.; Skarmeta, A. Enhancing IoT security through network softwarization and virtual security appliances. Int. J. Netw. Manag. 2018, 28, e2038. [Google Scholar] [CrossRef]
- Carvalho, L.F.; Abrão, T.; de Souza Mendes, L.; Proença, M.L., Jr. An ecosystem for anomaly detection and mitigation in software-defined networking. Expert Syst. Appl. 2018, 104, 121–133. [Google Scholar] [CrossRef]
- Aljuhani, A.; Alharbi, T. Virtualized network functions security attacks and vulnerabilities. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC) IEEE, Las Vegas, NV, USA, 9–11 January 2017; pp. 1–4. [Google Scholar]
- Mijumbi, R.; Serrat, J.; Gorricho, J.L.; Bouten, N.; De Turck, F.; Boutaba, R. Network function virtualization: State-of-the-art and research challenges. IEEE Commun. Surv. Tutor. 2015, 18, 236–262. [Google Scholar] [CrossRef] [Green Version]
- Liu, W. Performance Test and Improvement of Computer Network Virtualization Software in Cloud Computing Environment. Secur. Commun. Networks 2022, 2022, 6965880. [Google Scholar] [CrossRef]
- Gulenko, A.; Wallschläger, M.; Schmidt, F.; Kao, O.; Liu, F. A system architecture for real-time anomaly detection in large-scale nfv systems. Procedia Comput. Sci. 2016, 94, 491–496. [Google Scholar] [CrossRef]
- Pattaranantakul, M.; He, R.; Song, Q.; Zhang, Z.; Meddahi, A. NFV security survey: From use case driven threat analysis to state-of-the-art countermeasures. IEEE Commun. Surv. Tutorials 2018, 20, 3330–3368. [Google Scholar] [CrossRef]
- Rao, K.H.; Srinivas, G.; Damodhar, A.; Krishna, M.V. Implementation of anomaly detection technique using machine learning algorithms. Int. J. Comput. Sci. Telecommun. 2011, 2, 25–31. [Google Scholar]
- Zoure, M.; Ahmed, T.; Réveillère, L. Network services anomalies in NFV: Survey, taxonomy, and verification methods. IEEE Trans. Netw. Serv. Manag. 2022, 19, 1567–1584. [Google Scholar] [CrossRef]
- Bondan, L.; Wauters, T.; Volckaert, B.; De Turck, F.; Granville, L.Z. Anomaly detection framework for SFC integrity in NFV environments. In Proceedings of the 2017 IEEE Conference on Network Softwarization (NetSoft) IEEE, Bologna, Italy, 3–7 July 2017; pp. 1–5. [Google Scholar]
- Bondan, L. NFV Environments Security Through Anomaly Detection. Ph.D. Thesis, Universidade Federal do Rio Grande do Sul, Farroupilha, Brazil, 2019. [Google Scholar]
- Girish, L.; Rao, S.K. Anomaly detection in cloud environment using artificial intelligence techniques. Computing 2021, 105, 675–688. [Google Scholar] [CrossRef]
- Qiu, J.; Du, Q.; He, Y.; Lin, Y.; Zhu, J.; Yin, K. Performance anomaly detection models of virtual machines for network function virtualization infrastructure with machine learning. In Proceedings of the Artificial Neural Networks and Machine Learning—ICANN 2018: 27th International Conference on Artificial Neural Networks, Rhodes, Greece, 4–7 October 2018; Part II 27; pp. 479–488. [Google Scholar]
- Pang, G.; Shen, C.; Cao, L.; Hengel, A.V.D. Deep learning for anomaly detection: A review. ACM Comput. Surv. CSUR 2021, 54, 1–38. [Google Scholar] [CrossRef]
- Nassif, A.B.; Talib, M.A.; Nasir, Q.; Dakalbab, F.M. Machine learning for anomaly detection: A systematic review. IEEE Access 2021, 9, 78658–78700. [Google Scholar] [CrossRef]
- Wang, S.; Balarezo, J.F.; Kandeepan, S.; Al-Hourani, A.; Chavez, K.G.; Rubinstein, B. Machine learning in network anomaly detection: A survey. IEEE Access 2021, 9, 152379–152396. [Google Scholar] [CrossRef]
- Gebremariam, A.A.; Usman, M.; Qaraqe, M. Applications of artificial intelligence and machine learning in the area of SDN and NFV: A survey. In Proceedings of the 2019 16th International Multi-Conference on Systems, Signals & Devices (SSD) IEEE, Istanbul, Turkey, 21–24 March 2019; pp. 545–549. [Google Scholar]
- Alam, I.; Sharif, K.; Li, F.; Latif, Z.; Karim, M.M.; Biswas, S.; Nour, B.; Wang, Y. A survey of network virtualization techniques for Internet of Things using SDN and NFV. ACM Comput. Surv. CSUR 2020, 53, 1–40. [Google Scholar] [CrossRef]
- Ghaffar, Z.; Alshahrani, A.; Fayaz, M.; Alghamdi, A.M.; Gwak, J. A topical review on machine learning, software defined networking, internet of things applications: Research limitations and challenges. Electronics 2021, 10, 880. [Google Scholar]
- Lohrasbinasab, I.; Shahraki, A.; Taherkordi, A.; Delia Jurcut, A. From statistical-to machine learning-based network traffic prediction. Trans. Emerg. Telecommun. Technol. 2022, 33, e4394. [Google Scholar] [CrossRef]
- Shah, A.H.; Pasha, D.; Zadeh, E.H.; Konur, S. Automated Log Analysis and Anomaly Detection Using Machine Learning. In Fuzzy Systems and Data Mining VIII; IOS Press: Amsterdam, The Netherlands, 2022; pp. 137–147. [Google Scholar]
- Gallego-Madrid, J.; Sanchez-Iborra, R.; Ruiz, P.M.; Skarmeta, A.F. Machine learning-based zero-touch network and service management: A survey. Digit. Commun. Networks 2022, 8, 105–123. [Google Scholar] [CrossRef]
- Ahmed, M.; Shatabda, S.; Islam, A.; Robin, M.; Islam, T. Intrusion detection system in software-defined networks using machine learning and deep learning techniques—A comprehensive survey. TechRxiv Prepr. 2021. [CrossRef]
- Nunez-Agurto, D.; Fuertes, W.; Marrone, L.; Macas, M. Machine Learning-Based Traffic Classification in Software-Defined Networking: A Systematic Literature Review, Challenges, and Future Research Directions. IAENG Int. J. Comput. Sci. 2022, 49, 4. [Google Scholar]
- Di Mauro, M.; Galatro, G.; Fortino, G.; Liotta, A. Supervised feature selection techniques in network intrusion detection: A critical review. Eng. Appl. Artif. Intell. 2021, 101, 104216. [Google Scholar] [CrossRef]
- Hawilo, H.; Jammal, M.; Shami, A. Exploring microservices as the architecture of choice for network function virtualization platforms. IEEE Netw. 2019, 33, 202–210. [Google Scholar] [CrossRef]
- Kawahara, R.; Watanabe, K.; Harada, S.; Kawata, T. Application of AI to Network Operation. IEICE Commun. Soc. Glob. Newsl. 2020, 44, 11. [Google Scholar] [CrossRef] [Green Version]
- Sipple, J.; Youssef, A. A general-purpose method for applying Explainable AI for Anomaly Detection. In Proceedings of the Foundations of Intelligent Systems: 26th International Symposium, ISMIS 2022, Cosenza, Italy, 3–5 October 2022; pp. 162–174. [Google Scholar]
- Ma, Q.; Sun, C.; Cui, B.; Jin, X. A novel model for anomaly detection in network traffic based on kernel support vector machine. Comput. Secur. 2021, 104, 102215. [Google Scholar] [CrossRef]
- Tahsien, S.M.; Karimipour, H.; Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 2020, 161, 102630. [Google Scholar] [CrossRef] [Green Version]
- Prabakaran, S.; Ramar, R.; Hussain, I.; Kavin, B.P.; Alshamrani, S.S.; AlGhamdi, A.S.; Alshehri, A. Predicting attack pattern via machine learning by exploiting stateful firewall as virtual network function in an SDN network. Sensors 2022, 22, 709. [Google Scholar] [CrossRef]
- Le, D.C.; Zincir-Heywood, N. A frontier: Dependable, reliable and secure machine learning for network/system management. J. Netw. Syst. Manag. 2020, 28, 827–849. [Google Scholar] [CrossRef]
- Reynaud, F.; Aguessy, F.X.; Bettan, O.; Bouet, M.; Conan, V. Attacks against network functions virtualization and software-defined networking: State-of-the-art. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft) IEEE, Seoul, Republic of Korea, 6–10 June 2016; pp. 471–476. [Google Scholar]
- Kabir, M.A.; Luo, X. Unsupervised learning for network flow based anomaly detection in the era of deep learning. In Proceedings of the 2020 IEEE Sixth International Conference on Big Data Computing Service and Applications (BigDataService) IEEE, Oxford, UK, 3–6 August 2020; pp. 165–168. [Google Scholar]
- D’Alconzo, A.; Drago, I.; Morichetta, A.; Mellia, M.; Casas, P. A survey on big data for network traffic monitoring and analysis. IEEE Trans. Netw. Serv. Manag. 2019, 16, 800–813. [Google Scholar] [CrossRef] [Green Version]
- Abdallah, E.E.; Otoom, A.F. Intrusion Detection Systems using supervised machine learning techniques: A survey. Procedia Comput. Sci. 2022, 201, 205–212. [Google Scholar] [CrossRef]
- Moustafa, N.; Hu, J.; Slay, J. A holistic review of network anomaly detection systems: A comprehensive survey. J. Netw. Comput. Appl. 2019, 128, 33–55. [Google Scholar] [CrossRef]
- Kourtis, M.A.; Xilouris, G.; Gardikis, G.; Koutras, I. Statistical-based anomaly detection for NFV services. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN) IEEE, Palo Alto, CA, USA, 7–10 November 2016; pp. 161–166. [Google Scholar]
- Bhuyan, M.H.; Bhattacharyya, D.K.; Kalita, J.K. Network anomaly detection: Methods, systems and tools. IEEE Commun. Surv. Tutor. 2013, 16, 303–336. [Google Scholar] [CrossRef]
- Makani, R.; Reddy, B. Taxonomy of machine leaning based anomaly detection and its suitability. Procedia Comput. Sci. 2018, 132, 1842–1849. [Google Scholar] [CrossRef]
- Kawasaki, J.; Mouri, G.; Suzuki, Y. Comparative analysis of network fault classification using machine learning. In Proceedings of the NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium IEEE, Budapest, Hungary, 20–24 April 2020; pp. 1–6. [Google Scholar]
- Martínez Osorio, J.S. Detection and Mitigation of DDoS/Dos Security threats in an NFV Architecture. Master’s Thesis, Universidad de Antioquia, Ciudad de Mexico, Mexico, 2022. [Google Scholar]
- Suhaimi, N.A.D.; Abas, H. A systematic literature review on supervised machine learning algorithms. Perintis Ejournal 2020, 10, 1–24. [Google Scholar]
- Vergara-Reyes, J.; Martinez-Ordonez, M.C.; Ordonez, A.; Rendon, O.M.C. IP traffic classification in NFV: A benchmarking of supervised Machine Learning algorithms. In Proceedings of the 2017 IEEE Colombian Conference on Communications and Computing (COLCOM) IEEE, Cartagena, Colombia, 16–18 August 2017; pp. 1–6. [Google Scholar]
- Akcay, S.; Atapour-Abarghouei, A.; Breckon, T.P. Ganomaly: Semi-supervised anomaly detection via adversarial training. In Proceedings of the Computer Vision–ACCV 2018: 14th Asian Conference on Computer Vision, Perth, Australia, 2–6 December 2018; Revised Selected Papers, Part III 14. pp. 622–637. [Google Scholar]
- Chiu, C.Y.; Lee, Y.J.; Chang, C.C.; Luo, W.Y.; Huang, H.C. Semi-supervised learning for false alarm reduction. In Proceedings of the Advances in Data Mining Applications and Theoretical Aspects: 10th Industrial Conference, ICDM 2010, Berlin, Germany, 12–14 July 2010; pp. 595–605. [Google Scholar]
- Johari, S.S.; Shahriar, N.; Tornatore, M.; Boutaba, R.; Saleh, A. Anomaly Detection and Localization in NFV Systems: An Unsupervised Learning Approach. In Proceedings of the NOMS 2022–2022 IEEE/IFIP Network Operations and Management Symposium, IEEE, Budapest, Hungary, 25–29 April 2022; pp. 1–9. [Google Scholar]
- Thottan, M.; Liu, G.; Ji, C. Anomaly detection approaches for communication networks. In Algorithms for Next Generation Networks; Springer: Berlin, Germany, 2010; pp. 239–261. [Google Scholar]
- Pelati, A.; Meo, M.; Dini, P. Traffic Anomaly Detection Using Deep Semi-Supervised Learning at the Mobile Edge. IEEE Trans. Veh. Technol. 2022, 71, 8919–8932. [Google Scholar] [CrossRef]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Wu, X.; Hou, K.; Leng, X.; Li, X.; Yu, Y.; Wu, B.; Chen, Y. State of the art and research challenges in the security technologies of network function virtualization. IEEE Internet Comput. 2019, 24, 25–35. [Google Scholar] [CrossRef]
- Bahri, M.; Salutari, F.; Putina, A.; Sozio, M. Automl: State of the art with a focus on anomaly detection, challenges, and research directions. Int. J. Data Sci. Anal. 2022, 14, 113–126. [Google Scholar] [CrossRef]
- Arzo, S.T.; Naiga, C.; Granelli, F.; Bassoli, R.; Devetsikiotis, M.; Fitzek, F.H. A theoretical discussion and survey of network automation for IoT: Challenges and opportunity. IEEE Internet Things J. 2021, 8, 12021–12045. [Google Scholar] [CrossRef]
- Kandanaarachchi, S.; Ochiai, H.; Rao, A. Honeyboost: Boosting honeypot performance with data fusion and anomaly detection. Expert Syst. Appl. 2022, 201, 117073. [Google Scholar] [CrossRef]
- Katiyar, P.; Kumarn, U.S.; Balakrishanan, S. Detection and discrimination of DDoS attacks from flash crowd using entropy variations. Int. J. Eng. Technol 2013, 5, 3514–3519. [Google Scholar]
- Lakhina, A.; Crovella, M.; Diot, C. Characterization of network-wide anomalies in traffic flows. In Proceedings of the 4th ACM SIGCOMM Conference on Internet Measurement, Taormina, Italy, 25–27 October 2004; pp. 201–206. [Google Scholar]
- Arko, A.R.; Khan, S.H.; Preety, A.; Biswas, M.H. Anomaly Detection In IoT Using Machine Learning Algorithms. Ph.D. Thesis, Brac University, Dhaka, Banglasesh, 2019. [Google Scholar]
- Sgueglia, A.; Di Sorbo, A.; Visaggio, C.A.; Canfora, G. A systematic literature review of iot time series anomaly detection solutions. Future Gener. Comput. Syst. 2022, 134, 170–186. [Google Scholar] [CrossRef]
- Adoga, H.U.; Pezaros, D.P. Network function virtualization and service function chaining frameworks: A comprehensive review of requirements, objectives, implementations, and open research challenges. Future Internet 2022, 14, 59. [Google Scholar] [CrossRef]
- Derstepanians, A.; Vannucci, M.; Cucinotta, T.; Sahebrao, A.K.; Lahiri, S.; Artale, A.; Fichera, S. Near Real-Time Anomaly Detection in NFV Infrastructures. In Proceedings of the 2022 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN) IEEE, Phoenix, AZ, USA, 14–16 November 2022; pp. 26–32. [Google Scholar]
- Pavlidis, A.; Sotiropoulos, G.; Giotis, K.; Kalogeras, D.; Maglaris, V. NFV-compliant traffic monitoring and anomaly detection based on dispersed vantage points in shared network infrastructures. In Proceedings of the 2018 4th IEEE Conference on Network Softwarization and Workshops (NetSoft) IEEE, Montreal, QC, Canada, 25–29 June 2018; pp. 197–201. [Google Scholar]
- Sood, K.; Nosouhi, M.R.; Nguyen, D.D.N.; Jiang, F.; Chowdhury, M.; Doss, R. Intrusion Detection Scheme With Dimensionality Reduction in Next Generation Networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 965–979. [Google Scholar] [CrossRef]
- Mathas, C.M.; Segou, O.E.; Xylouris, G.; Christinakis, D.; Kourtis, M.A.; Vassilakis, C.; Kourtis, A. Evaluation of Apache Spot’s machine learning capabilities in an SDN/NFV enabled environment. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–10. [Google Scholar]
- Monshizadeh, M.; Khatri, V.; Gamdou, M.; Kantola, R.; Yan, Z. Improving data generalization with variational autoencoders for network traffic anomaly detection. IEEE Access 2021, 9, 56893–56907. [Google Scholar] [CrossRef]
- Abbasi, M.; Shahraki, A.; Taherkordi, A. Deep learning for network traffic monitoring and analysis (NTMA): A survey. Comput. Commun. 2021, 170, 19–41. [Google Scholar] [CrossRef]
- Chen, J.; Chen, M.; Wei, X.; Chen, B. Matrix differential decomposition-based anomaly detection and localization in NFV networks. IEEE Access 2019, 7, 29320–29331. [Google Scholar] [CrossRef]
- Elmajed, A.; Aghasaryan, A.; Fabre, E. Machine learning approaches to early fault detection and identification in NFV architectures. In Proceedings of the 2020 6th IEEE Conference on Network Softwarization (NetSoft), IEEE, Ghent, Belgium, 29 June–3 July 2020; pp. 200–208. [Google Scholar]
- Girish, L. Anomaly Detection in NFV Using Tree-Based Unsupervised Learning Method. Int. J. Eng. Sci. Manag. Multidiscip. Publ. VTU 2019, 1, 27–31. [Google Scholar]
- Hong, J.; Park, S.; Yoo, J.H.; Hong, J.W.K. A Machine Learning based SLA-Aware VNF Anomaly Detection Method in Virtual Networks. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC) IEEE, Jeju, Republic of Korea, 21–23 October 2020; pp. 1051–1056. [Google Scholar]
- Blaise, A.; Wong, S.; Aghvami, A.H. Virtual network function service chaining anomaly detection. In Proceedings of the 2018 25th International Conference on Telecommunications (ICT) IEEE, Saint-Malo, France, 26–28 June 2018; pp. 411–415. [Google Scholar]
- Gulenko, A.; Schmidt, F.; Acker, A.; Wallschläger, M.; Kao, O.; Liu, F. Detecting anomalous behavior of black-box services modeled with distance-based online clustering. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD) IEEE, San Francisco, CA, USA, 2–7 July 2018; pp. 912–915. [Google Scholar]
- Silva, F.; Schaeffer-Filho, A. Intel-Ocnf: Intelligent Orchestration of Containerized Network Functions for Anomaly Mitigation. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4189456 (accessed on 9 March 2023).
- Schmidt, F.; Gulenko, A.; Wallschläger, M.; Acker, A.; Hennig, V.; Liu, F.; Kao, O. Iftm-unsupervised anomaly detection for virtualized network function services. In Proceedings of the 2018 IEEE International Conference on Web Services (ICWS) IEEE, San Francisco, CA, USA, 2–7 July 2018; pp. 187–194. [Google Scholar]
- Diamanti, A.; Vilchez, J.M.S.; Secci, S. LSTM-based radiography for anomaly detection in softwarized infrastructures. In Proceedings of the 2020 32nd International Teletraffic Congress (ITC 32) IEEE, Osaka, Japan, 22–24 September 2020; pp. 28–36. [Google Scholar]
- Lanciano, G.; Ritacco, A.; Brau, F.; Cucinotta, T.; Vannucci, M.; Artale, A.; Barata, J.; Sposato, E. Using Self-Organizing Maps for the Behavioral Analysis of Virtualized Network Functions. In Proceedings of the Cloud Computing and Services Science: 10th International Conference, CLOSER 2020, Prague, Czech Republic, 7–9 May 2020; Revised Selected Papers 10. pp. 153–177. [Google Scholar]
- Kumar, D.; Thakur, J. Handling Security Issues in Software-defined Networks (SDNs) Using Machine Learning. In Computational Vision and Bio-Inspired Computing: Proceedings of ICCVBIC 2021; Springer: Berlin, Germany, 2022; pp. 263–277. [Google Scholar]
- Spiekermann, D.; Keller, J. Unsupervised packet-based anomaly detection in virtual networks. Comput. Netw. 2021, 192, 108017. [Google Scholar] [CrossRef]
- Bondan, L.; Wauter, T.; Volckaert, B.; De Turck, F.; Granville, L.Z. NFV Anomaly Detection: Case Study through a Security Module. IEEE Commun. Mag. 2022, 60, 18–24. [Google Scholar] [CrossRef]
- Wang, W.; Tang, L.; Wang, C.; Chen, Q. Real-Time Analysis of Multiple Root Causes for Anomalies Assisted by Digital Twin in NFV Environment. IEEE Trans. Netw. Serv. Manag. 2022, 19, 905–921. [Google Scholar] [CrossRef]
- Ghrib, Z.; Jaziri, R.; Romdhane, R. Hybrid approach for anomaly detection in time series data. In Proceedings of the 2020 International Joint Conference on Neural Networks (IJCNN) IEEE, Glasgow, UK, 19–24 July 2020; pp. 1–7. [Google Scholar]
- Patel, D.; Srinivasan, K.; Chang, C.Y.; Gupta, T.; Kataria, A. Network anomaly detection inside consumer networks—A hybrid approach. Electronics 2020, 9, 923. [Google Scholar] [CrossRef]
- Rashid, A.; Siddique, M.J.; Ahmed, S.M. Machine and deep learning based comparative analysis using hybrid approaches for intrusion detection system. In Proceedings of the 2020 3rd International Conference on Advancements in Computational Sciences (ICACS) IEEE, Lahore, Pakistan, 17–19 February 2020; pp. 1–9. [Google Scholar]
- Sadikin, F.; Kumar, S. Zigbee IoT intrusion detection system: A hybrid approach with rule-based and machine learning anomaly detection. In Proceedings of the 5th International Conference on Internet of Things, Big Data and Security (IoTBDS 2020), Prague, Czech Republic, 7–9 May 2020; pp. 57–68. [Google Scholar]
- Deshmukh, R.; Hwang, I. Incremental-learning-based unsupervised anomaly detection algorithm for terminal airspace operations. J. Aerosp. Inf. Syst. 2019, 16, 362–384. [Google Scholar] [CrossRef]
- Peng, H.; Yang, R.; Wang, Z.; Li, J.; He, L.; Philip, S.Y.; Zomaya, A.Y.; Ranjan, R. Lime: Low-cost and incremental learning for dynamic heterogeneous information networks. IEEE Trans. Comput. 2021, 71, 628–642. [Google Scholar] [CrossRef]
- Tan, C.H.; Lee, V.C.; Salehi, M. Mir_mad: An efficient and on-line approach for anomaly detection in dynamic data stream. In Proceedings of the 2020 International Conference on Data Mining Workshops (ICDMW) IEEE, Sorrento, Italy, 17–20 November 2020; pp. 424–431. [Google Scholar]
- Constantinides, C.; Shiaeles, S.; Ghita, B.; Kolokotronis, N. A novel online incremental learning intrusion prevention system. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS) IEEE, Canary Islands, Spain, 24–26 June 2019; pp. 1–6. [Google Scholar]
- Yehezkel, A.; Elyashiv, E.; Soffer, O. Network anomaly detection using transfer learning based on auto-encoders loss normalization. In Proceedings of the 14th ACM Workshop on Artificial Intelligence and Security, Virtual Event, Republic of Korea, 15 November 2021; pp. 61–71. [Google Scholar]
- Wang, W.; Chen, Q.; He, X.; Tang, L. Cooperative anomaly detection with transfer learning-based hidden Markov model in virtualized network slicing. IEEE Commun. Lett. 2019, 23, 1534–1537. [Google Scholar] [CrossRef]
- Sreelatha, G.; Babu, A.V.; Midhunchakkaravarthy, D. Improved security in cloud using sandpiper and extended equilibrium deep transfer learning based intrusion detection. Clust. Comput. 2022, 25, 3129–3144. [Google Scholar] [CrossRef]
- Pan, S.J.; Yang, Q. A Survey on Transfer Learning. IEEE Trans. Knowl. Data Eng. 2010, 22, 1345–1359. [Google Scholar] [CrossRef]
- Vanerio, J.; Casas, P. Ensemble-learning approaches for network security and anomaly detection. In Proceedings of the Workshop on Big Data Analytics and Machine Learning for Data Communication Networks, Los Angeles, CA, USA, 21 August 2017; pp. 1–6. [Google Scholar]
- Chohra, A.; Shirani, P.; Karbab, E.B.; Debbabi, M. Chameleon: Optimized feature selection using particle swarm optimization and ensemble methods for network anomaly detection. Comput. Secur. 2022, 117, 102684. [Google Scholar] [CrossRef]
- Al-amri, R.; Murugesan, R.K.; Man, M.; Abdulateef, A.F.; Al-Sharafi, M.A.; Alkahtani, A.A. A review of machine learning and deep learning techniques for anomaly detection in IoT data. Appl. Sci. 2021, 11, 5320. [Google Scholar] [CrossRef]
- Tallón-Ballesteros, A.; Chen, C. Explainable AI: Using Shapley value to explain complex anomaly detection ML-based systems. Mach. Learn. Artif. Intell. 2020, 332, 152. [Google Scholar]
- Eltanbouly, S.; Bashendy, M.; AlNaimi, N.; Chkirbene, Z.; Erbad, A. Machine learning techniques for network anomaly detection: A survey. In Proceedings of the 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT) IEEE, Doha, Qatar, 2–5 February 2020; pp. 156–162. [Google Scholar]
- Sharma, S.; Nag, A.; Cordeiro, L.; Ayoub, O.; Tornatore, M.; Nekovee, M. Poster: Towards Explainable Artificial Intelligence for Network Function Virtualization. In Proceedings of the CoNEXT’20, Barcelona, Spain, 1–4 December 2020. [Google Scholar]
- Ameli, M.; Pfanschilling, V.; Amirli, A.; Maaß, W.; Kersting, K. Unsupervised Multi-sensor Anomaly Localization with Explainable AI. In Proceedings of the Artificial Intelligence Applications and Innovations: 18th IFIP WG 12.5 International Conference, AIAI 2022, Hersonissos, Crete, Greece, 17–20 June 2022; pp. 507–519. [Google Scholar]
- Dutta, B.; Krichel, A.; Odini, M.P. The challenge of zero touch and explainable ai. J. ICT Stand. 2021, 9, 147–158. [Google Scholar] [CrossRef]
- Diamanti, A.; Vílchez, J.M.S.; Secci, S. An AI-empowered framework for cross-layer softwarized infrastructure state assessment. IEEE Trans. Netw. Serv. Manag. 2022, 19, 4434–4448. [Google Scholar] [CrossRef]
- Suriano, A.; Striccoli, D.; Piro, G.; Bolla, R.; Boggia, G. Attestation of trusted and reliable service function chains in the ETSI-NFV framework. In Proceedings of the 2020 6th IEEE Conference on Network Softwarization (NetSoft) IEEE, Ghent, Belgium, 29 June–3 July 2020; pp. 479–486. [Google Scholar]
- Lindemann, B.; Maschler, B.; Sahlab, N.; Weyrich, M. A survey on anomaly detection for technical systems using LSTM networks. Comput. Ind. 2021, 131, 103498. [Google Scholar] [CrossRef]
- Vinolia, A.; Kanya, N.; Rajavarman, V. Machine Learning and Deep Learning based Intrusion Detection in Cloud Environment: A Review. In Proceedings of the 2023 5th International Conference on Smart Systems and Inventive Technology (ICSSIT) IEEE, Tirunelveli, India, 23–25 January 2023; pp. 952–960. [Google Scholar]



| Survey Paper | Year | Structured Approach | Advantages/Limitations | Critical Assessment | Coverage of Other Techniques | Technical Difficulty | Performance Comparison |
|---|---|---|---|---|---|---|---|
| Our Survey | 2023 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Pang [20] | 2021 | ✓ | ✓ | ✓ | X | X | X |
| Nassif [21] | 2021 | ✓ | ✓ | ✓ | X | X | X |
| Wang [22] | 2021 | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Gebremariam [23] | 2019 | ✓ | ✓ | ✓ | X | X | X |
| Alam [24] | 2020 | ✓ | ✓ | ✓ | X | X | X |
| Ghaffar [25] | 2021 | ✓ | ✓ | ✓ | X | X | X |
| Lohrasbinasab [26] | 2022 | ✓ | ✓ | ✓ | X | X | X |
| Shah [27] | 2022 | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Gallego-Madrid [28] | 2022 | ✓ | ✓ | ✓ | X | X | X |
| Ahmed [29] | 2021 | ✓ | ✓ | ✓ | X | X | X |
| Nunez-Agurto [30] | 2022 | ✓ | ✓ | ✓ | X | X | X |
| Di Mauro [31] | 2021 | ✓ | ✓ | ✓ | X | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zehra, S.; Faseeha, U.; Syed, H.J.; Samad, F.; Ibrahim, A.O.; Abulfaraj, A.W.; Nagmeldin, W. Machine Learning-Based Anomaly Detection in NFV: A Comprehensive Survey. Sensors 2023, 23, 5340. https://doi.org/10.3390/s23115340
Zehra S, Faseeha U, Syed HJ, Samad F, Ibrahim AO, Abulfaraj AW, Nagmeldin W. Machine Learning-Based Anomaly Detection in NFV: A Comprehensive Survey. Sensors. 2023; 23(11):5340. https://doi.org/10.3390/s23115340
Chicago/Turabian StyleZehra, Sehar, Ummay Faseeha, Hassan Jamil Syed, Fahad Samad, Ashraf Osman Ibrahim, Anas W. Abulfaraj, and Wamda Nagmeldin. 2023. "Machine Learning-Based Anomaly Detection in NFV: A Comprehensive Survey" Sensors 23, no. 11: 5340. https://doi.org/10.3390/s23115340
APA StyleZehra, S., Faseeha, U., Syed, H. J., Samad, F., Ibrahim, A. O., Abulfaraj, A. W., & Nagmeldin, W. (2023). Machine Learning-Based Anomaly Detection in NFV: A Comprehensive Survey. Sensors, 23(11), 5340. https://doi.org/10.3390/s23115340







