Broadcast Propagation Time in SpaceFibre Networks with Various Types of Spatial Redundancy
Abstract
:1. Introduction
2. Broadcast Message Propagation Rules for SpaceFibre Networks
3. Evaluation of Broadcast Propagation Time in SpaceFibre Networks
- −
- sizes of elastic buffers,
- −
- width of the broadcast transmission channels inside the devices (between separate units),
- −
- periods of clocks,
- −
- number of cycles spent on performing various actions,
- −
- service buffers and registers (which may be required to eliminate long communication lines between individual units) and other specific components determined by the implementation technology and the technology libraries used.
- N is the number of devices on the broadcast transmission route, including the source node and the destination node;
- λport_outj is the delay in the broadcast passing through the output port of device j;
- λport_inj is the delay in the broadcast passing through the input port of device j;
- λnj is the broadcast processing time in device j;
- λphyj is a channel connecting device j with device j + 1.
4. Estimation of Broadcast Propagation Time Change
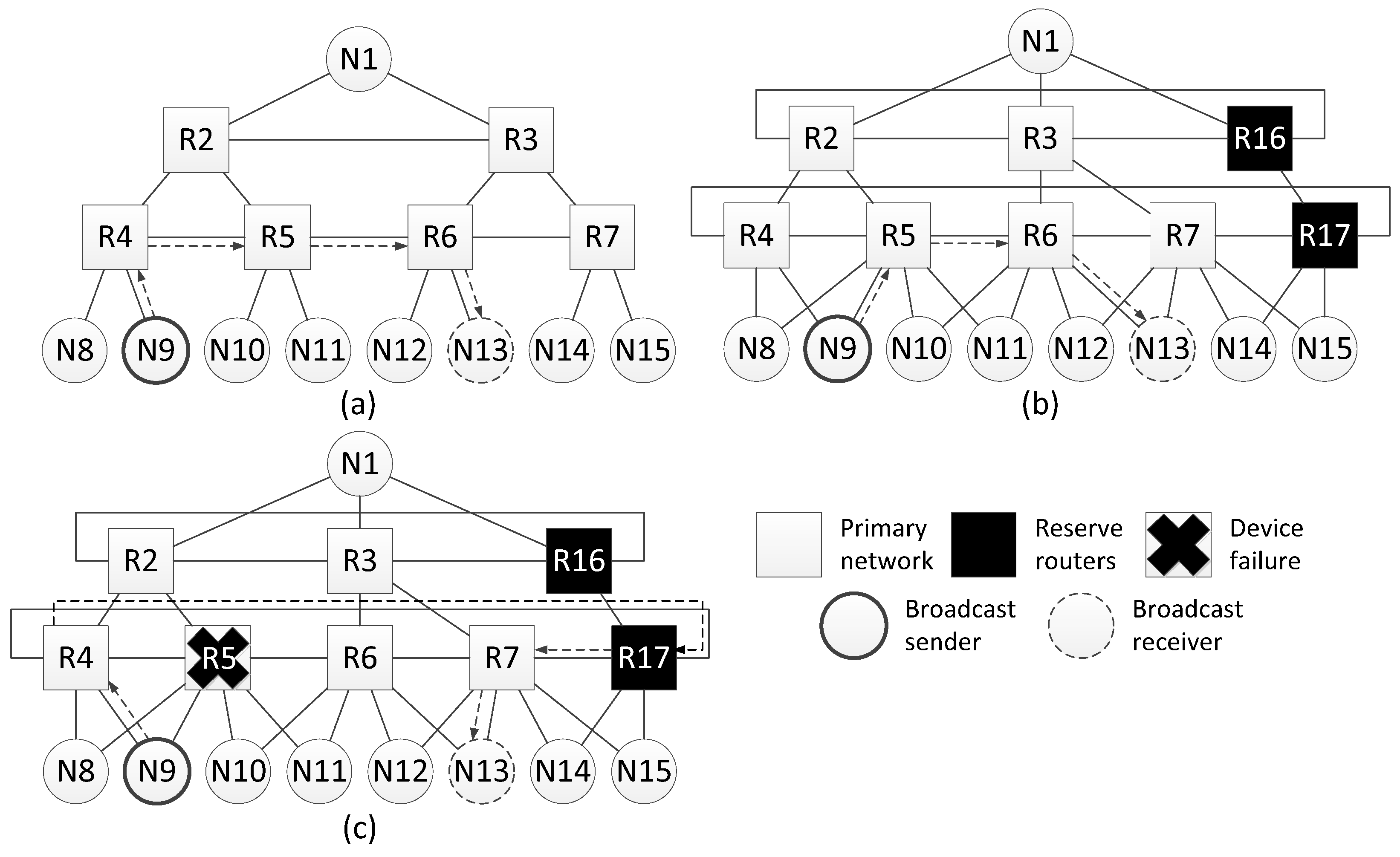
4.1. Considered Methods of Spatial Redundancy
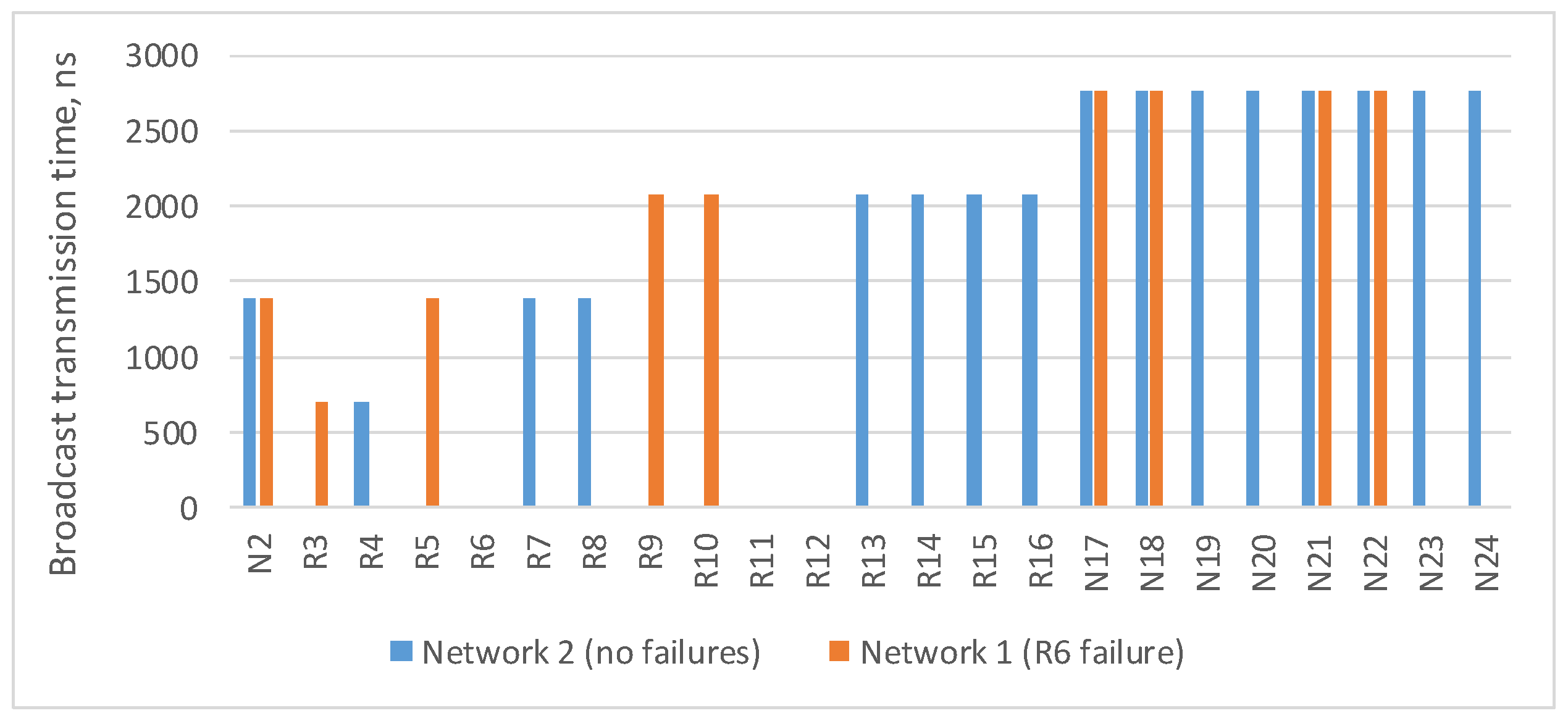
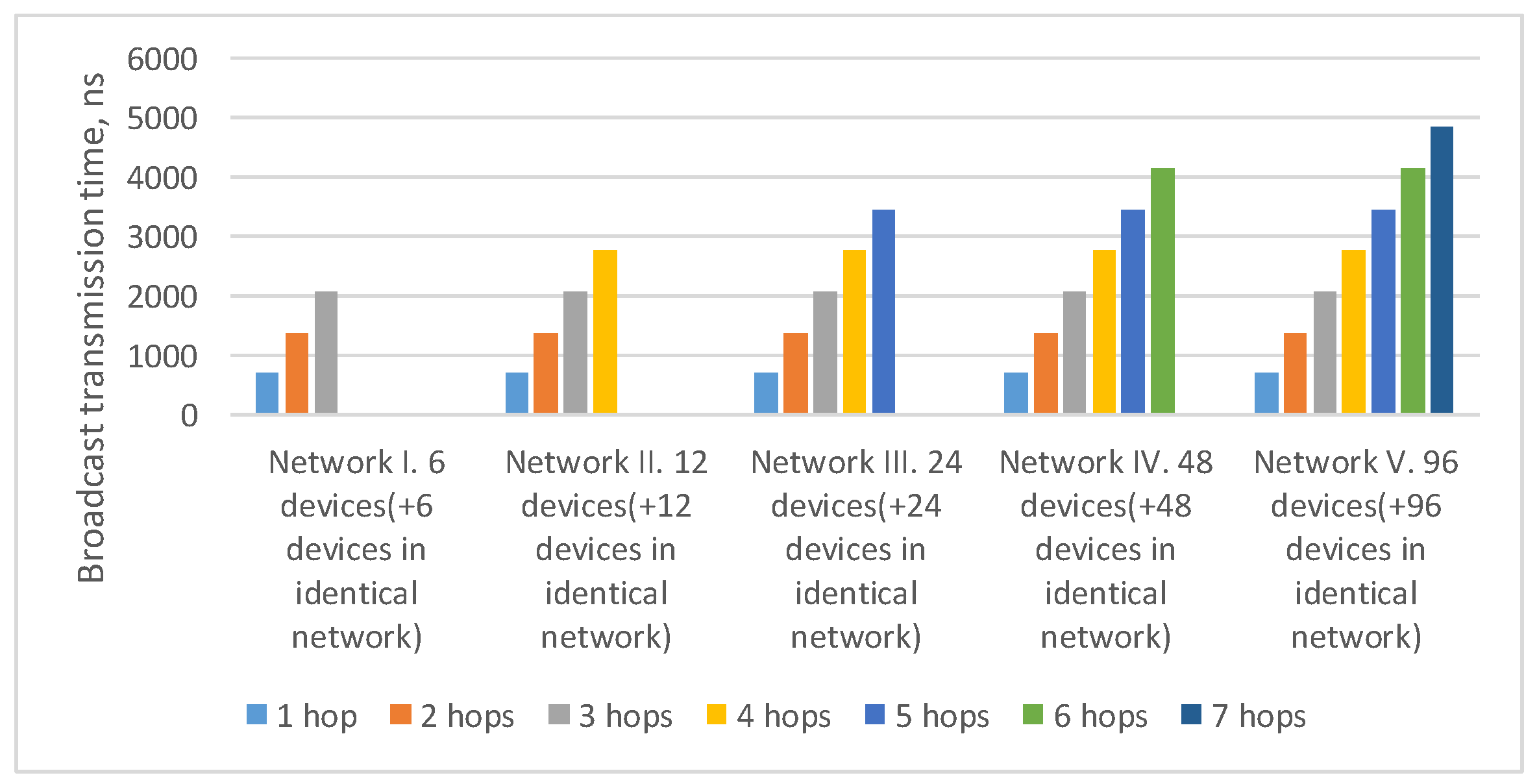
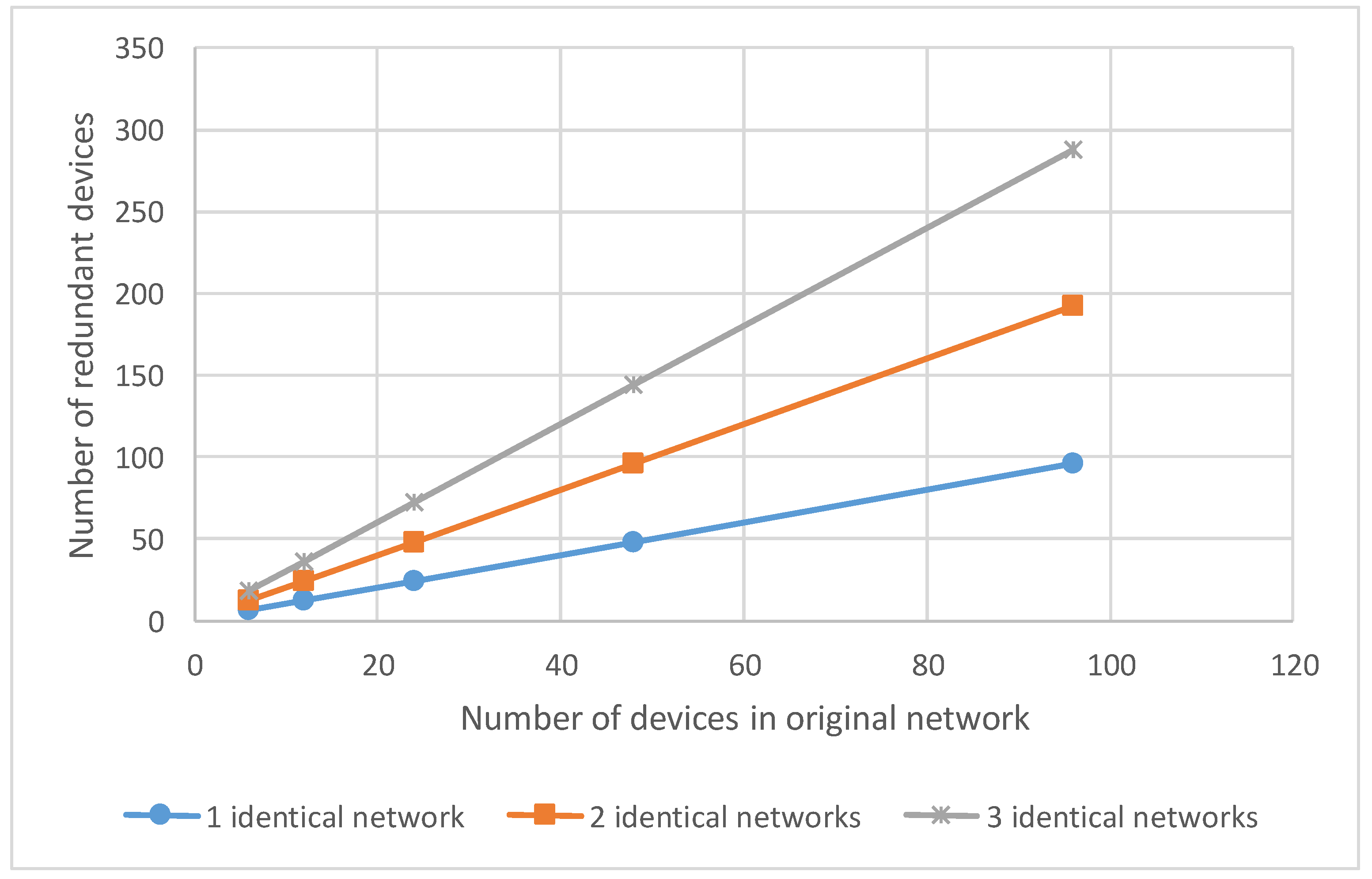
4.2. Fault Mitigation by Using Identical Networks
4.2.1. Identical Networks for Networks with Tree Topology
4.2.2. Identical Networks for Networks with 2D-Grid Topology
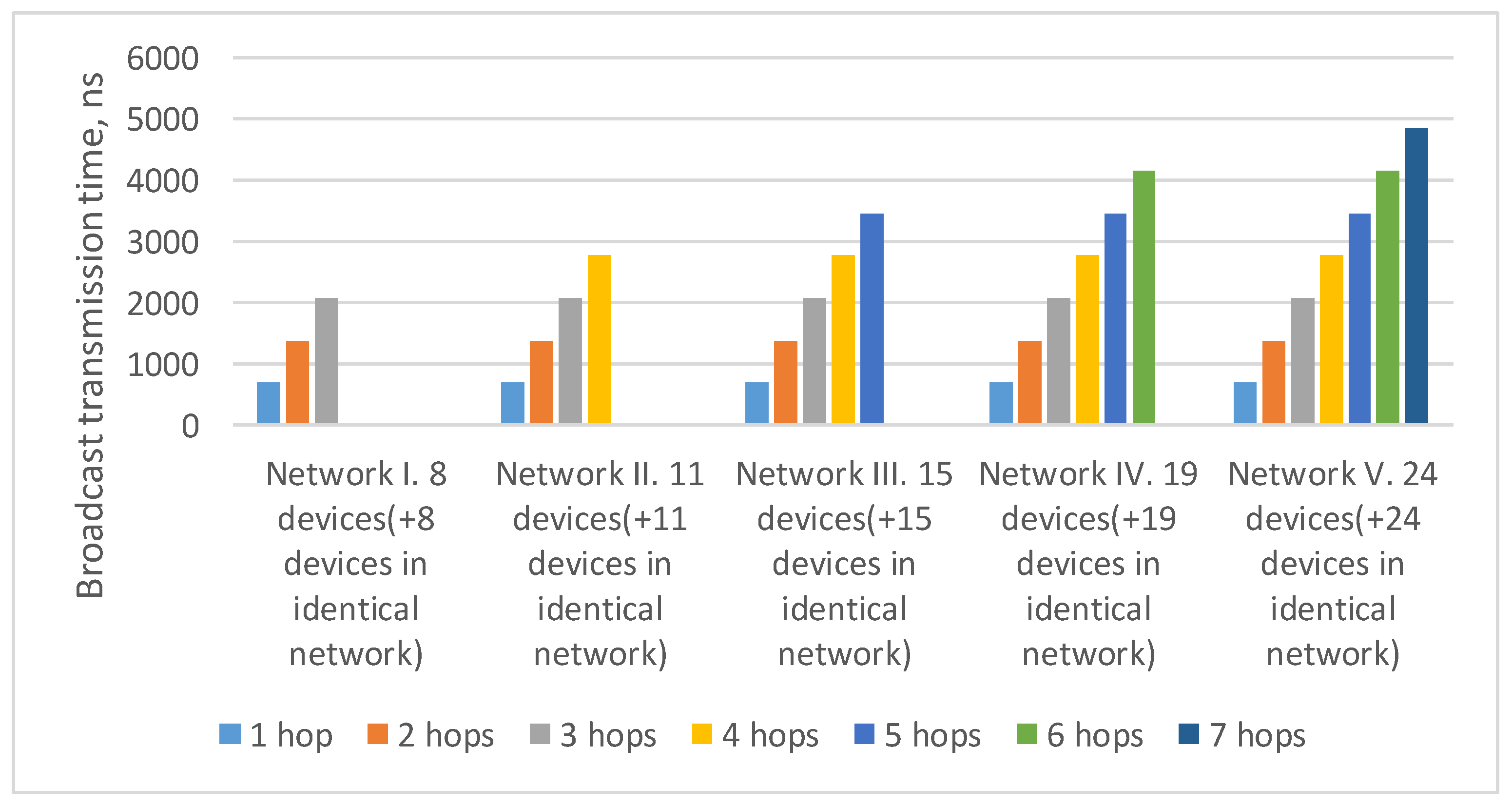
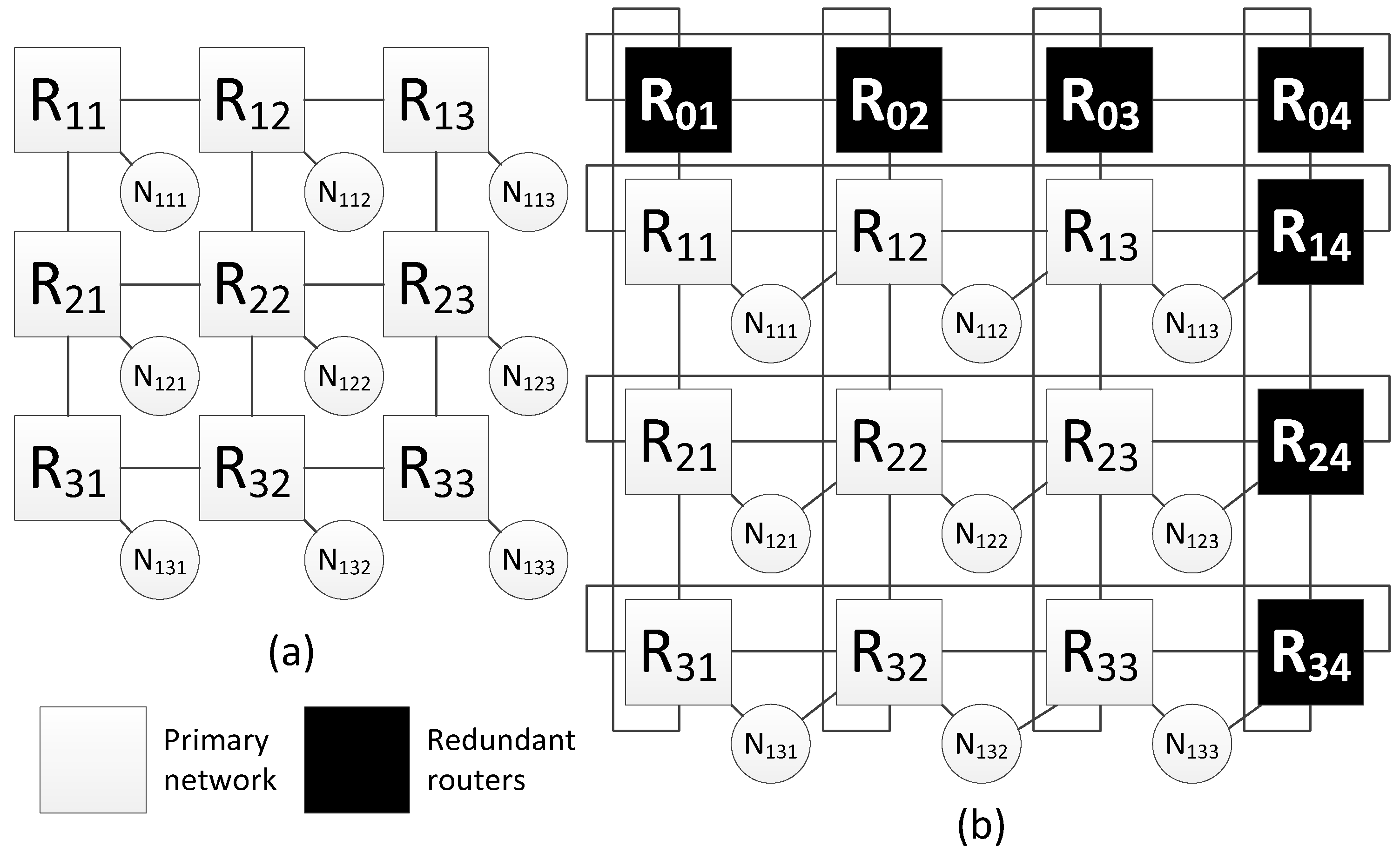
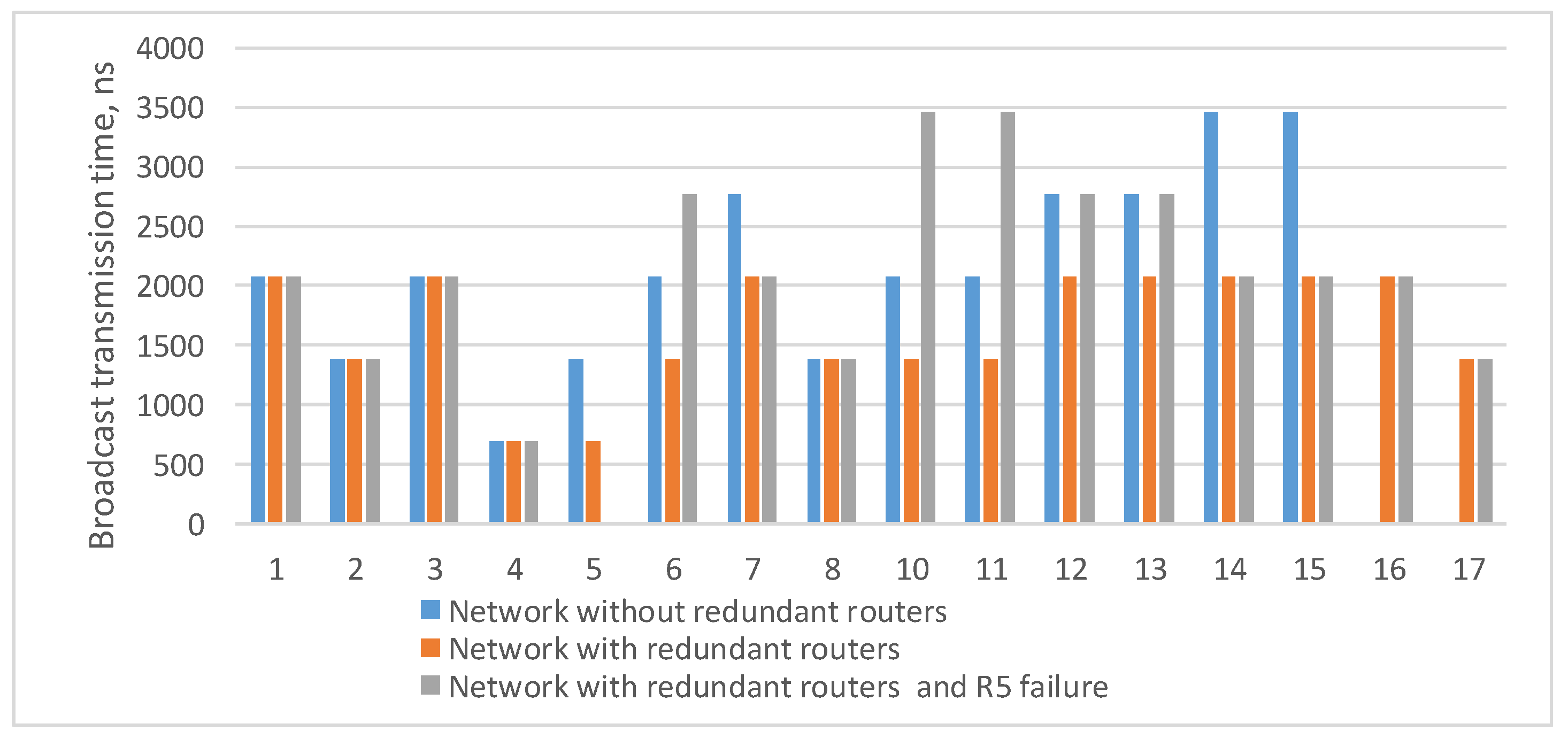
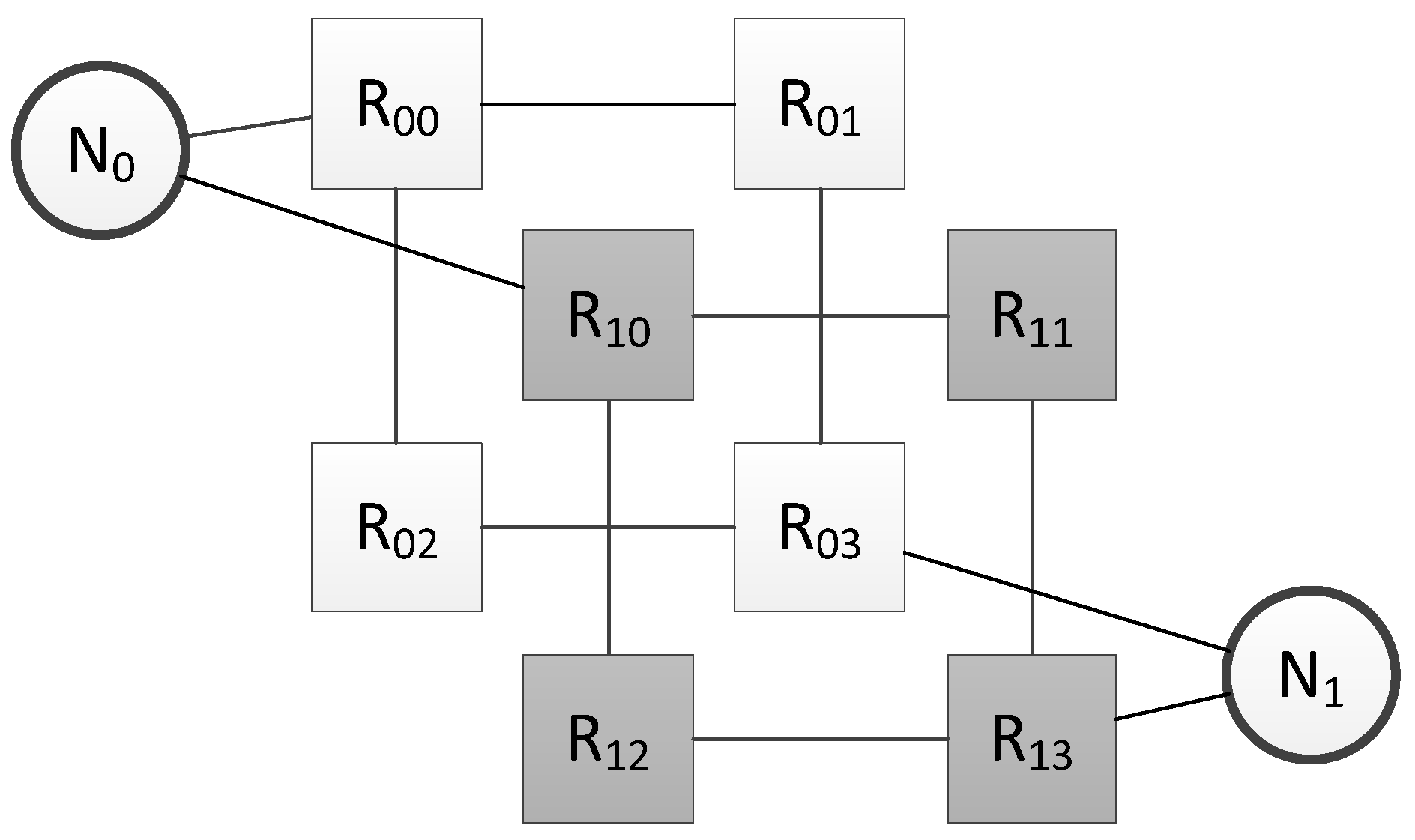
4.3. Fault Mitigation Using Redundant Routers and Cross-Links
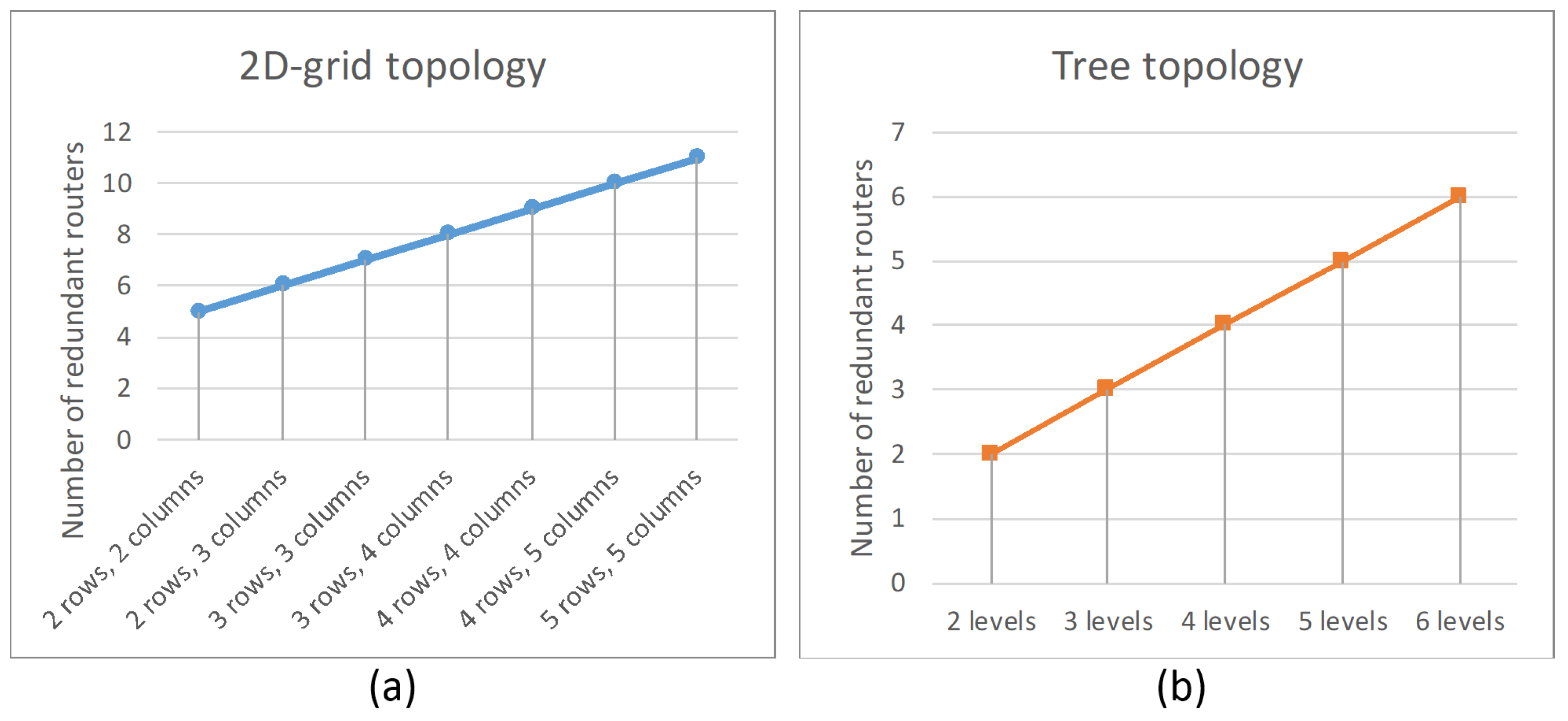
4.3.1. Redundant Routers in Networks with 2D-Grid Topology
4.3.2. Calculation of Transmission Route Length in Networks with 2D-Grid Topology
4.3.3. Redundant Routers in Networks with Tree Topology
4.3.4. Calculation of Transmission Route Length in Networks with Tree Topology
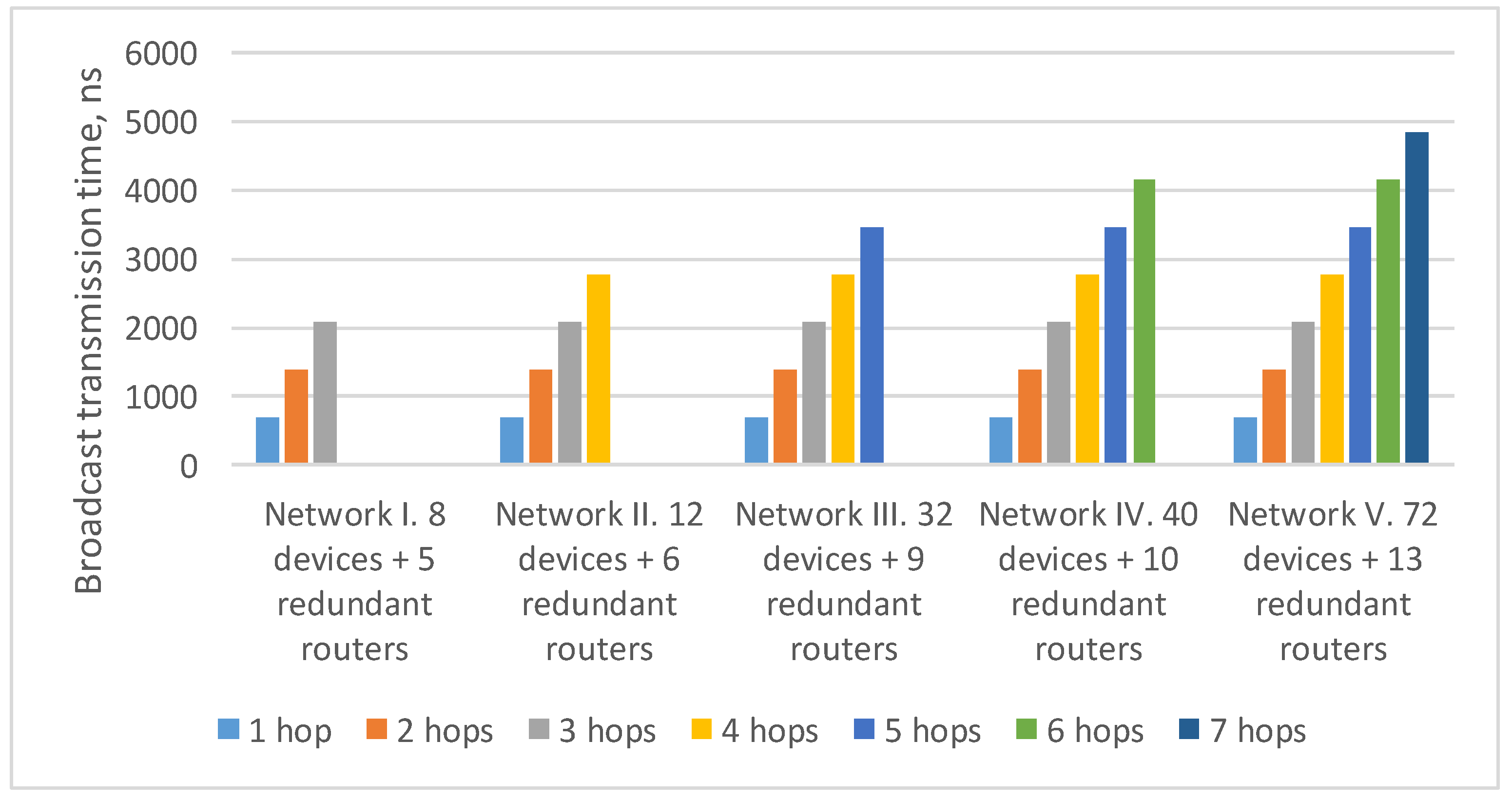
4.4. Comparative Analysis of Spatial Redundancy Methods
5. Analysis of Broadcast Message Propagation over a Network Using Petri Nets
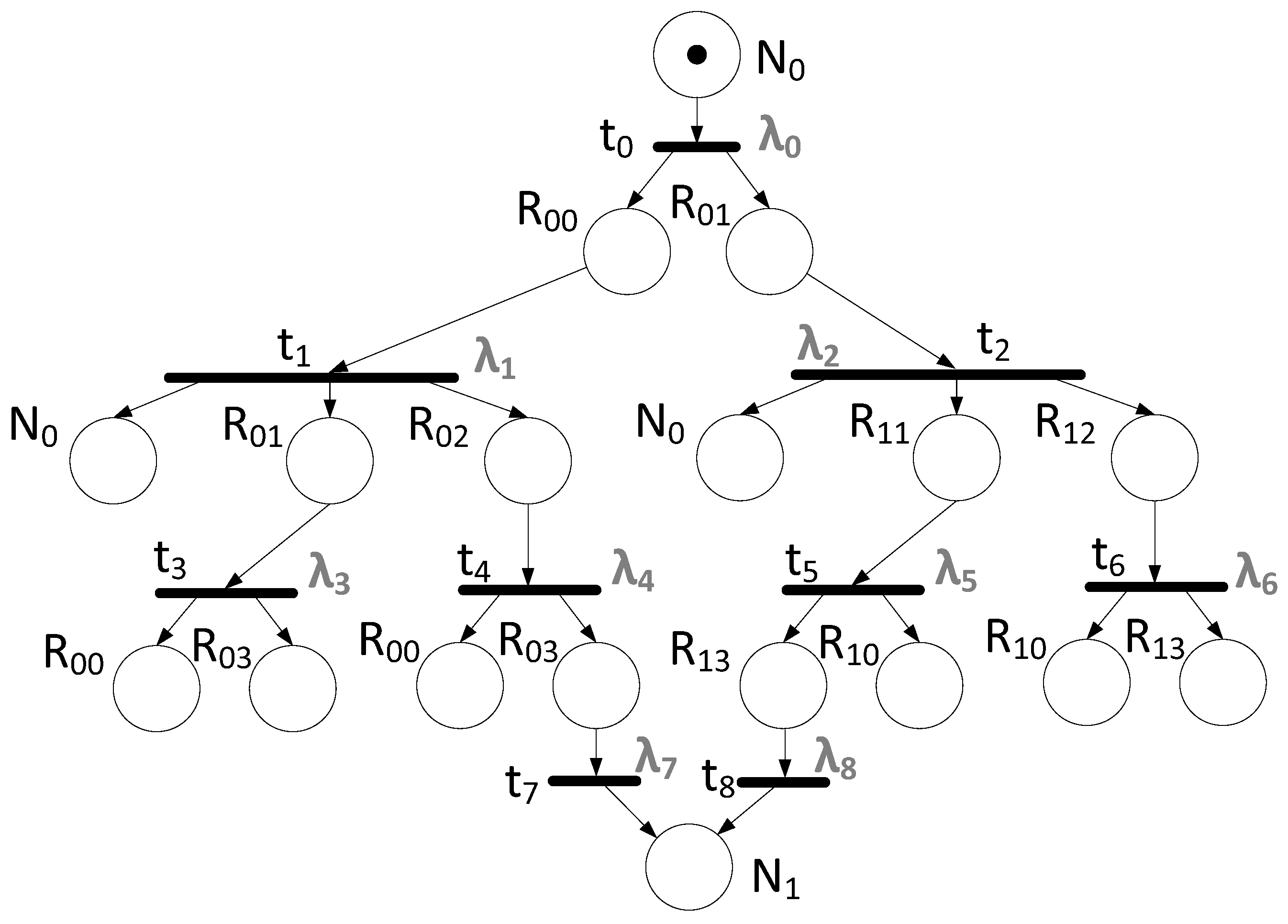
- The Initiator node and a Receiver node of the broadcast message, as well as all switches from the transmission trajectory, are represented as places of the Petri net. The names of specific network devices remain associated with place.
- The Initiator is marked with one token corresponding to the broadcast message. Thus, the initial marking of the Petri net is μ0 = {1, 0, 0, …, 0}.
- A transition represents the event of transmitting a broadcast message through the corresponding network device. Thus, the channels of the network are transformed into transitions and some arcs of the Petri net connecting the corresponding positions.
- The multiplicity of arcs cannot be more than 1.
- The delay for a particular Petri net transition is calculated according to Equation (12).
- The Receiver can have more than one transition in the input set I(pi).
- The Petri net is built in accordance with the algorithm for constructing a Petri net for broadcast transmission.
- The algorithm operation starts from the initiator node, marked with one token.
- Petri net is built:
- each output channel is transformed into a transition, with one arc entering it with a multiplicity of 1, and the output set of arcs is formed according to the number of channels outgoing from the network device (each can transmit a broadcast);
- each newly formed arc from the transition is associated with a place corresponding to the network device where the broadcast is transmitted.
- if the Petri net already has another place corresponding to the same network device, this place is a duplicate (the broadcast has already been delivered to this node), and the construction of this branch of the Petri net stops;
- move to the next transition, which is not processed by the algorithm;
- When there are no transitions left for processing in the Petri net, all transitions leading to the receiving node from different network devices are connected into one receiving transition.
- Building the Petri net is stopped.
6. Broadcast Transmission Parameter Evaluation Using Timed Automata
6.1. The Limitations of Previous Methods
- Inability to receive a broadcast over one of the channels (ports of the router). It occurs as a result of a physical break (rupture) in the communication line, as a result of prolonged noise in the communication line, as a result of failures and faults in the router/terminal node port. In this article, we equate not receiving a broadcast and receiving a broadcast with an incorrect format, incorrect field values, since such a distorted broadcast will be discarded on the receiving side at the Network Layer.
- Inability to transmit the broadcast to one of the channels. The reasons are similar to the previous point. Note that in the case of a break or prolonged noise in the physical channel, both reception and transmission are impossible. Failures and faults inside the port controller can potentially lead to the impossibility of either receiving or transmitting separately.
- Inability to process the broadcast in the network layer. It occurs due to failures and faults in the broadcast controller unit of the network layer or due to the failure of the entire router (for example, power-off).
- Inability to process the broadcast correctly due to the resetting of the router; as a result, information on the history of the broadcast distribution is lost (timeouts, etc.)
- Situations like the “babbling idiot”, in which, because of failures and/or faults, a broadcast with the correct structure spontaneously begins to be sent to the network. Such situations may arise, for example, due to the occurrence of failures of the “stuck-at-1” type for the flags of receiving a broadcast from individual ports, for the flag of the requirement to send a broadcast at the network layer. As a result, such an outwardly correct broadcast can be sent to all or some individual output ports.
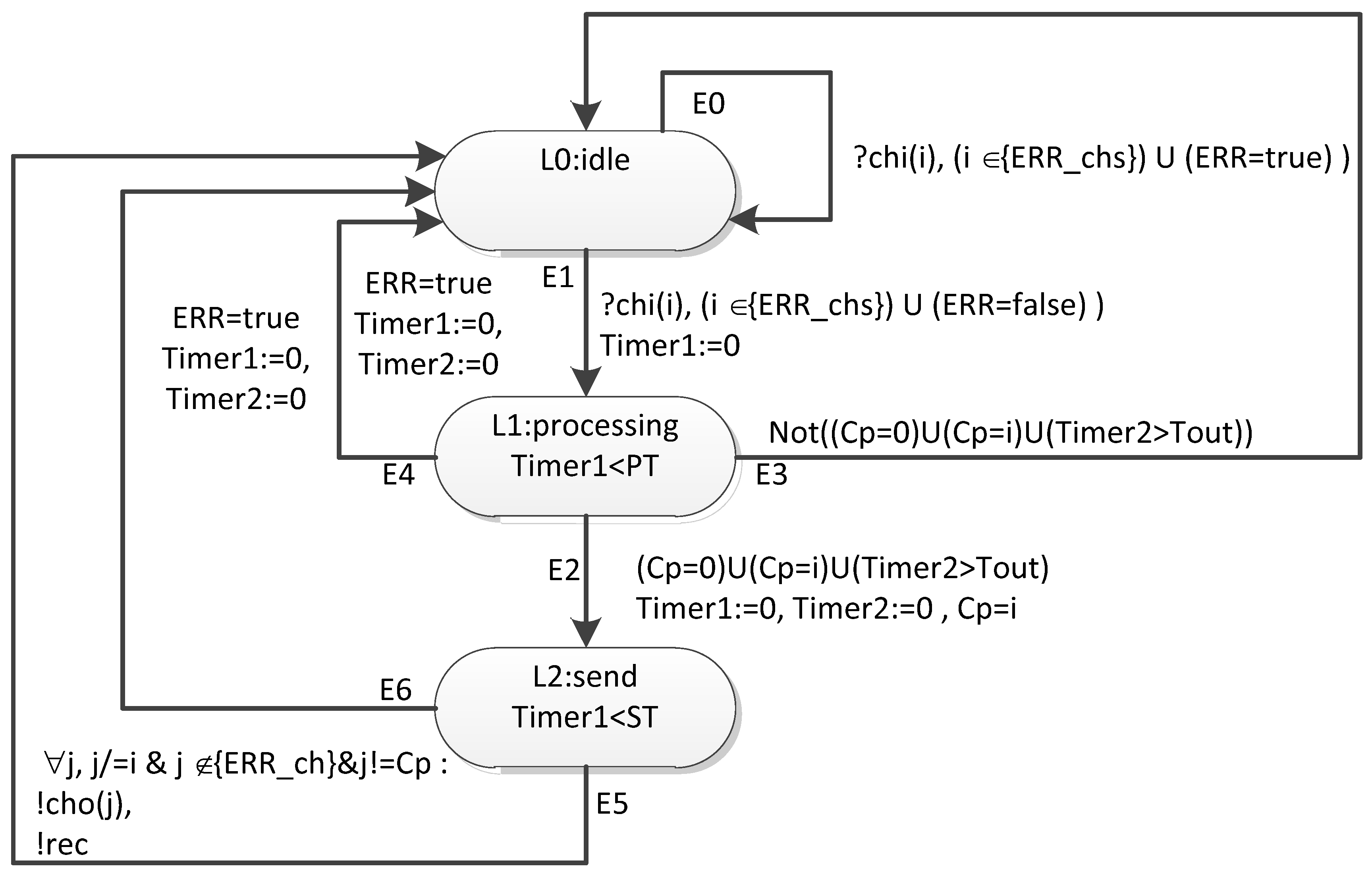
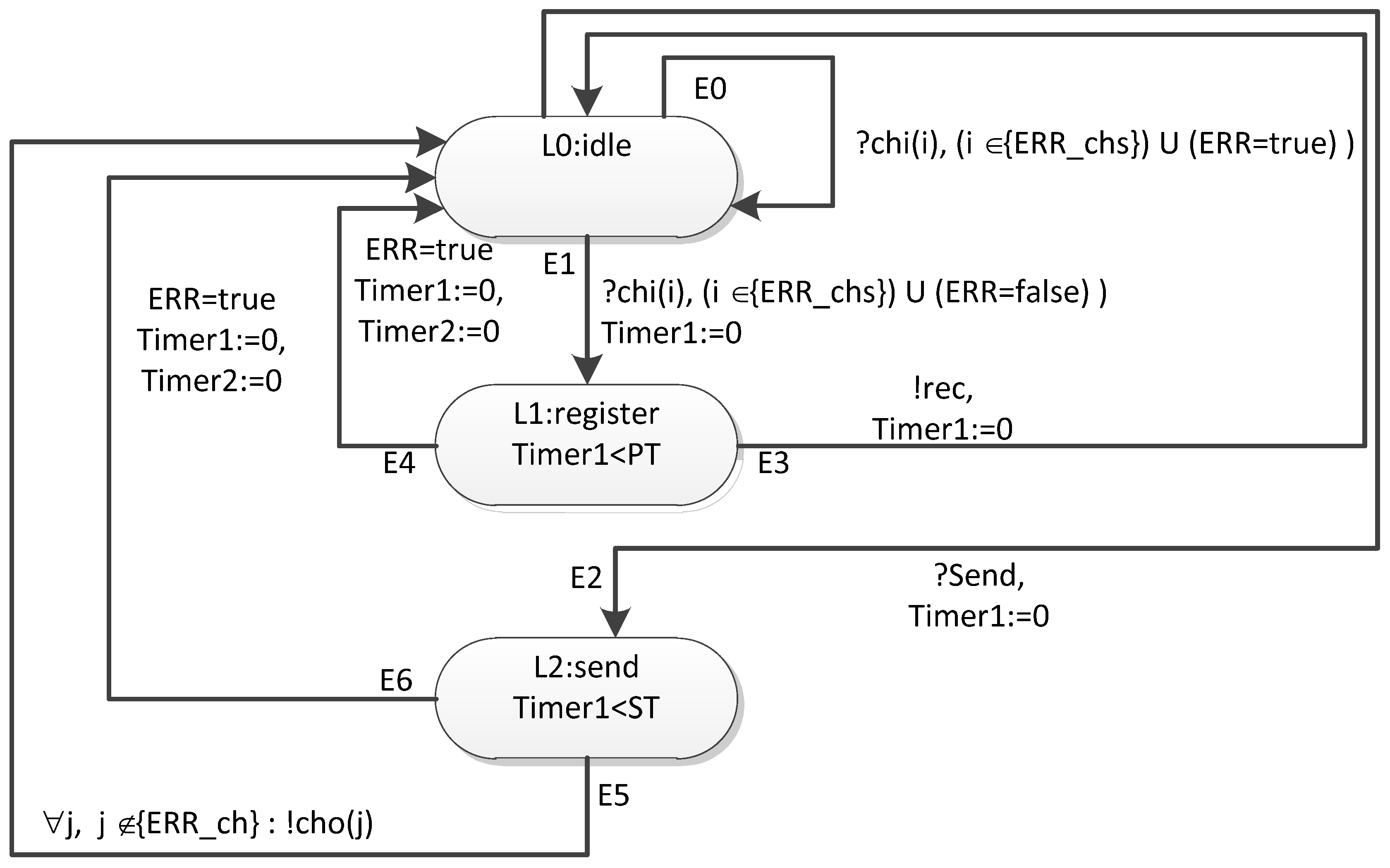
- identify the stages of the transition process;
- form connection graphs corresponding to each of the stages of the transition process;
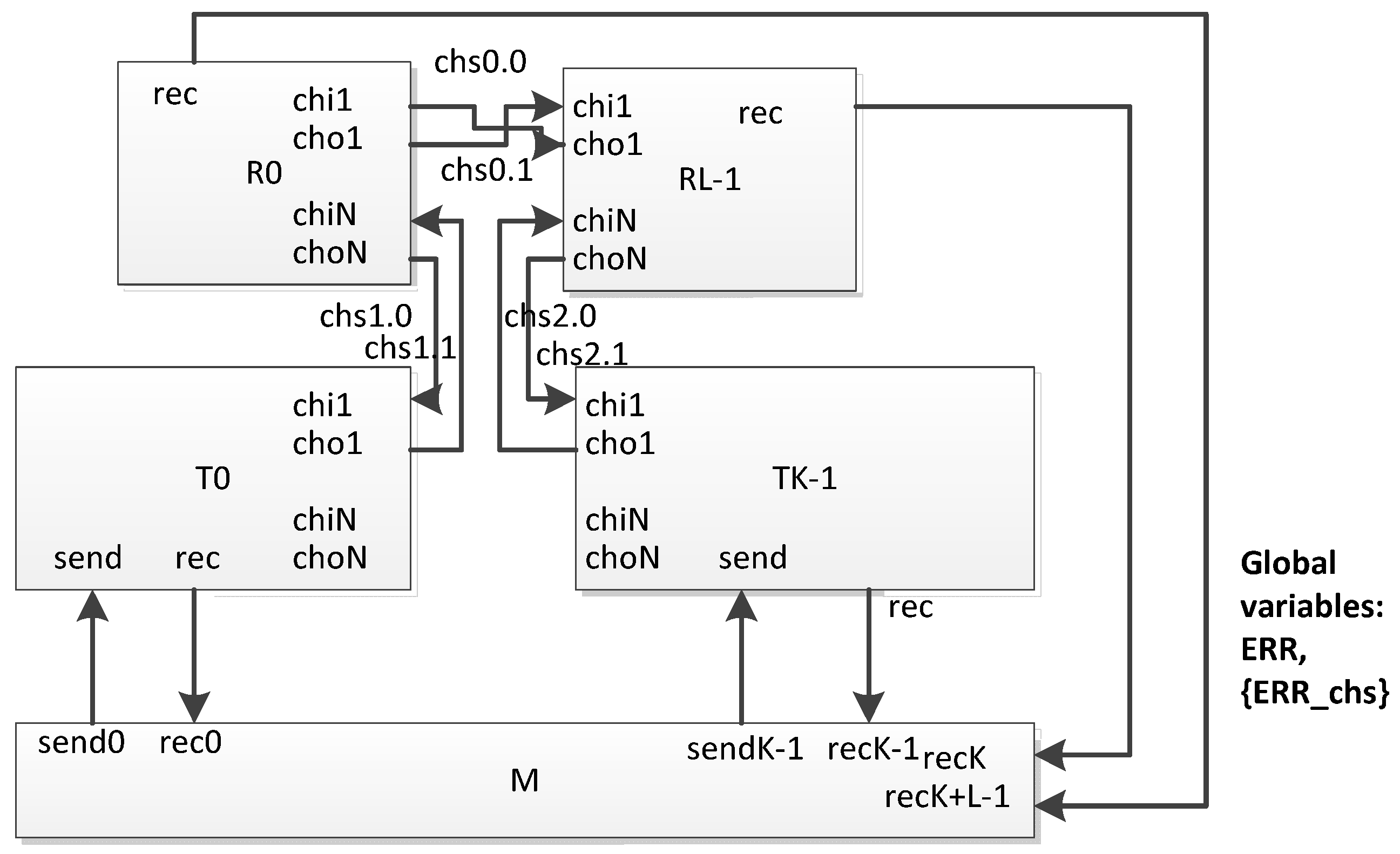
6.2. Proposed Network Model Based on Timed Automata
- routers (Rj in the figure);
- terminal nodes (Tj);
- the simulation process manager (M).
- L—the number of routers;
- K—the number of terminal nodes;
- C—the number of communication channels between routers and terminal nodes.
- PT—the broadcast processing time (λn)
- ST—the broadcast transmission time (λport_out + λphy + λport_in)
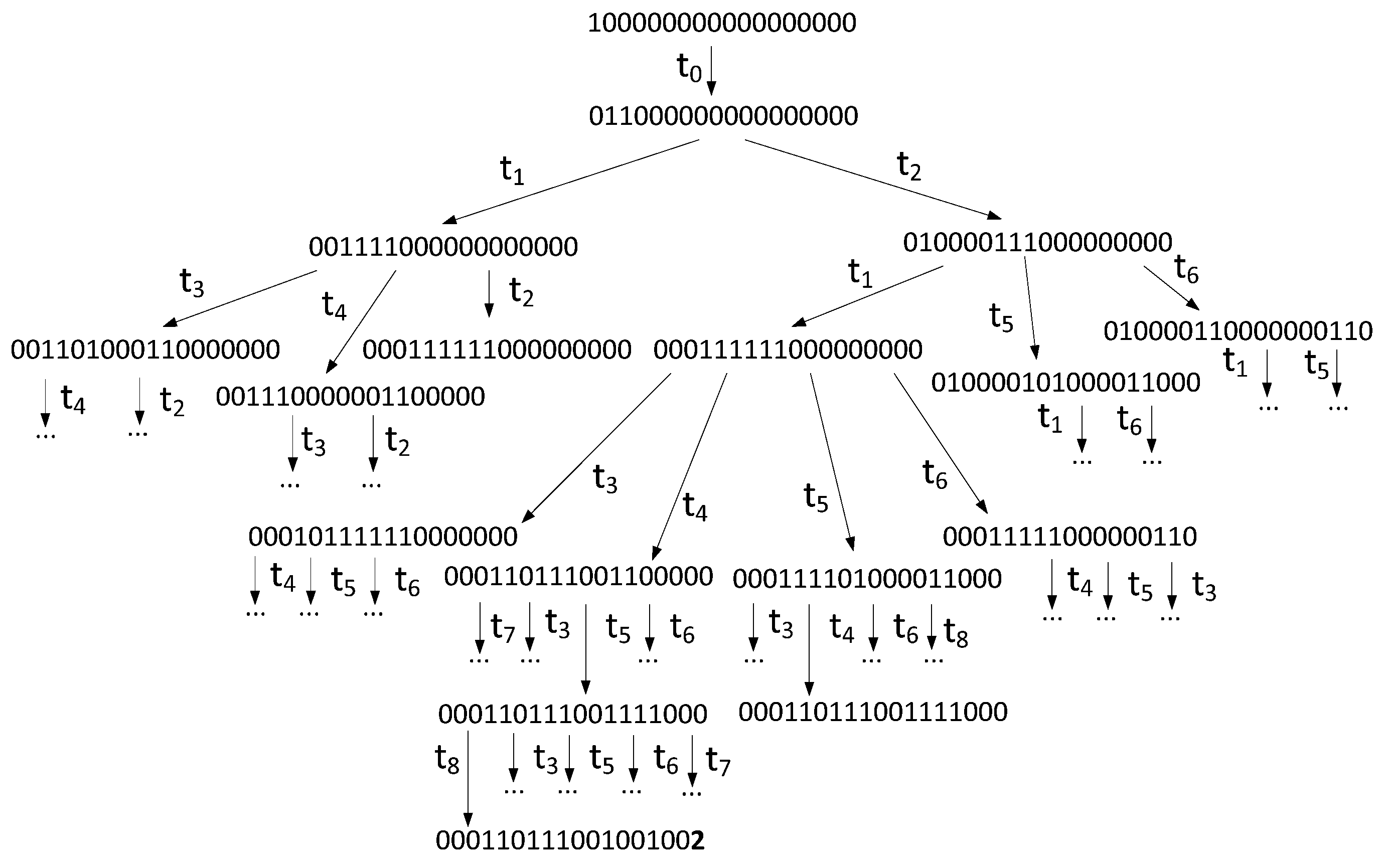
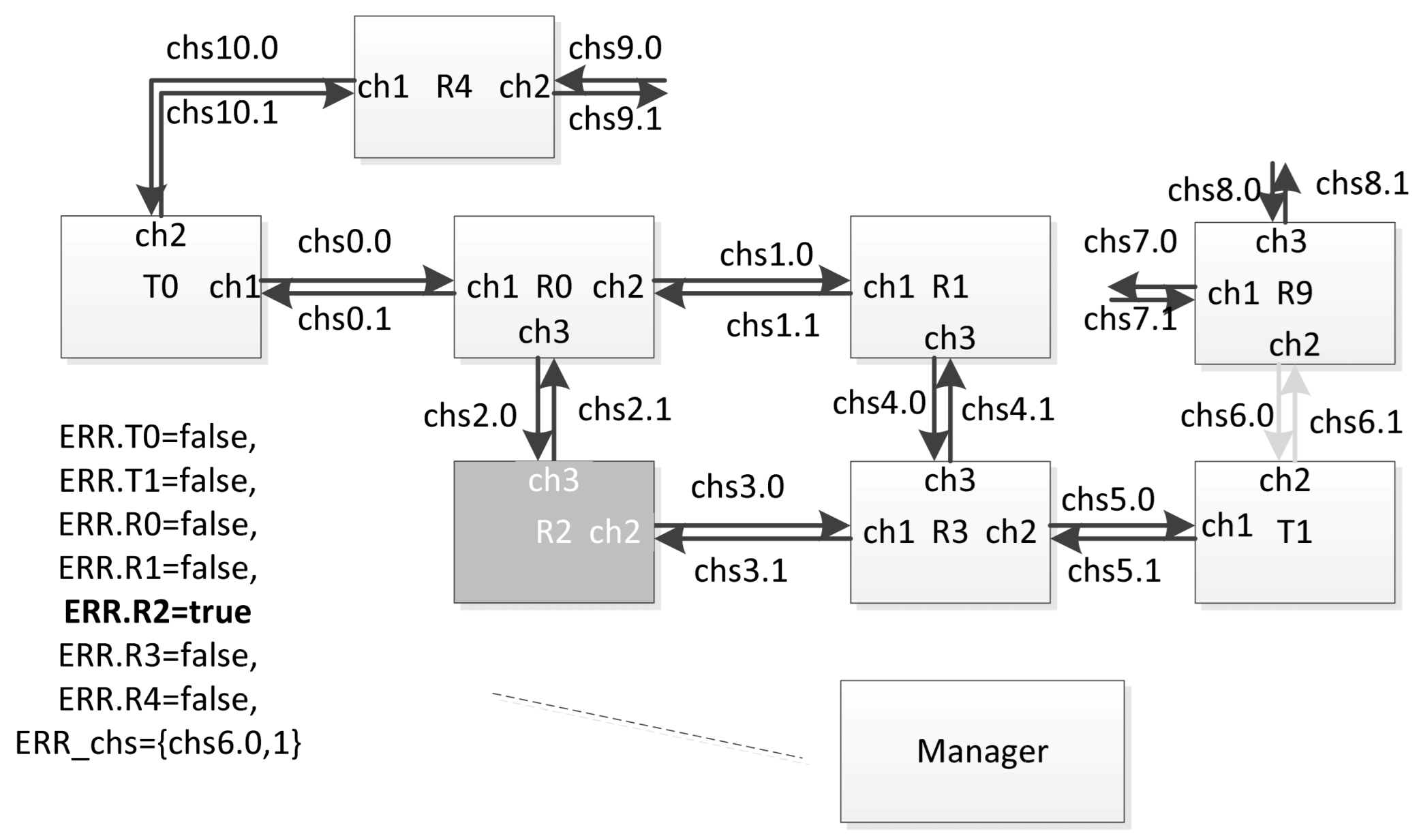
6.3. Example of Proposed Approach Use
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- ECSS-E-ST-50-11C; SpaceFibre—Very high-Speed Serial Link. ESA-ESTEC: Noordwijk, The Netherlands, 2019.
- Alur, R.; Dill, D. A theory of timed automata. Theor. Comp. Sci. 1994, 126, 183–235. [Google Scholar] [CrossRef] [Green Version]
- Karpov, Y.G. Model Checking. In Verification of Parallel and Distributed Software Systems; BHV: Saint Petersburg, Russia, 2010; pp. 1–560. [Google Scholar]
- Abd Alrahman, Y.; Azzopardi, S.; Piterman, N. Model Checking Reconfigurable Interacting Systems. In Leveraging Applications of Formal Methods, Verification and Validation. Adaptation and Learning; Margaria, T., Steffen, B., Eds.; Springer: Cham, Switzerland, 2022; Volume 13703, pp. 59–72. [Google Scholar]
- Velder, S.E.; Lukin, M.A.; Shalyto, A.A.; Yaminov, B.R. Verification of Automata-Based Programs; Science: Saint Petersburg, Russia, 2011; pp. 1–102. [Google Scholar]
- Govind, R.; Herbreteau, F.; Srivathsan, B.; Walukiewicz, I. Abstractions for the local-time semantics of timed automata: A foundation for partial-order methods. In Proceedings of the 37th Annual ACM/IEEE Symposium on Logic in Computer Science, Haifa, Israel, 31 July–12 August 2022; pp. 1–22. [Google Scholar]
- Alur, R.; La Torre, S.; Pappas, G. Optimal Paths in Weighted Timed Automata. Theor. Comp. Sci. 2004, 318, 297–322. [Google Scholar] [CrossRef]
- André, E.; Lime, D.; Roux, O.H. Decision Problems for Parametric Timed Automata. In ICFEM: Formal Methods and Software Engineering. Lecture Notes in Computer Science; Ogata, K., Lawford, M., Liu, S., Eds.; Springer: Tokyo, Japan, 2016; Volume 10009, pp. 400–416. [Google Scholar]
- André, E.; Lime, D.; Ramparison, M. TCTL model checking lower/upper-bound parametric timed automata without invariants. In FORMATS: Formal Modeling and Analysis of Timed Systems. Lecture Notes in Computer Science; Jansen, D.N., Prabhakar, P., Eds.; Springer: Beijing, China, 2018; Volume 11022, pp. 37–52. [Google Scholar]
- Jensen, P.G.; Kiviriga, A.; Guldstrand Larsen, K.; Nyman, U.; Mijaika, A.; Høiriis Mortensen, J. Monte Carlo Tree Search for Priced Timed Automata. In Quantitative Evaluation of Systems, Proceedings of the 19th International Conference (QEST 2022), Warsaw, Poland, 13–16 September 2022; Ábrahám, E.E., Paolieri, M., Eds.; Springer: Cham, Switzerland, 2022; Volume 13479, pp. 381–398. [Google Scholar]
- Beneš, N.; Bezděk, P.; Larsen, K.G.; Srba, J. Language Emptiness of Continuous-Time Parametric Timed Automata. In Part II. Automata, Languages, and Programming, Lecture Notes in Computer Science, Proceedings of the 42nd International Colloquium, ICALP 2015, Kyoto, Japan, 6–10 July 2015; Springer: Kyoto, Japan, 2015; Volume 9135, pp. 69–81. [Google Scholar]
- André, E. What’s decidable about parametric timed automata? Int. J. Softw. Tools Technol. Transf. 2019, 21, 203–219. [Google Scholar] [CrossRef] [Green Version]
- Chakraborty, S.; Phan, L.T.H.; Thiagarajan, P.S. Event Count Automata: A State-based Model for Stream Processing Systems. In Proceedings of the 26th IEEE International Real-Time Systems Symposium, Miami, FL, USA, 5–8 December 2005; pp. 87–98. [Google Scholar]
- Boyer, M.; Roux, P. Embedding network calculus and event stream theory in a common model. In Proceedings of the 21st International Conference on Emerging Technologies and Factory Automation (ETFA), Berlin, Germany, 6–9 September 2016; pp. 1–8. [Google Scholar]
- Hammal, Y.; Monnet, Q.; Mokdad, L.; Ben-Othman, J.; Abdelli, A. Timed automata based modeling and verification of denial of service attacks in wireless sensor networks. Stud. Inform. Univ. 2014, 12, 1–46. [Google Scholar]
- Anand, M.; Dajani-Brown, S.; Vestal, S.; Lee, I. Formal Modeling and Analysis of AFDX Frame Management Design. In Proceedings of the 9th International Symposium on Object-Oriented Real-Time Distributed Computing, Gyeongju, Republic of Korea, 24–26 April 2006; pp. 393–399. [Google Scholar]
- Govind, R.; Herbreteau, F.; Srivathsan, B.; Walukiewicz, I. Revisiting local time semantics for networks of timed automata. In Proceedings of the 30th International Conference on Concurrency Theory, Amsterdam, The Netherlands, 27–30 August 2019; pp. 16:1–16:15. [Google Scholar]
- Akshay, S.; Gastin, P.; Govind, R.; Srivathsan, B. Simulations for Event-Clock Automata. In Proceedings of the 33rd International Conference on Concurrency Theory, Warsaw, Poland, 13–16 September 2022; Klin, B., Lasota, S., Anca Muscholl, A., Eds.; Schloss Dagstuhl—Leibniz-Zentrum: Dagstuhl, Germany, 2022; Volume 243, pp. 13:1–13:18. [Google Scholar]
- Zhan, Y.; Hsiao, M.S. Breaking Down High-Level Robot Path-Finding Abstractions in Natural Language Programming. In Advances in Artificial Intelligence; Baldoni, M., Bandini, S., Eds.; Springer: Cham, Switzerland, 2021; Volume 12414, pp. 59–72. [Google Scholar]
- Sherwani, N. Algorithms for VLSI Physical Design Automation, 3rd ed.; Springer: New York, NY, USA, 1998; pp. 247–290. [Google Scholar]
- Nannipieri, P.; Fanucci, L.; Siegle, F. A representative SpaceFibre network evaluation: Features, performances and future trends. Acta Astronaut. 2020, 176, 313–323. [Google Scholar] [CrossRef]
- Baillieul, J.; Antsaklis, P.J. Control and Communication Challenges in Networked Real-Time Systems. Proc. IEEE 2007, 95, 9–28. [Google Scholar] [CrossRef]
- Shooman, M.L. Reliability of Computer Systems and Networks: Fault Tolerance, Analysis, and Design; John Wiley & Sons, Inc.: New York, NY, USA, 2002; pp. 1–528. [Google Scholar]
- Alena, R.L.; Ossenfort, J.P.; Laws, K.I.; Goforth, A. Communications for Integrated Modular Avionics. In Proceedings of the IEEE Conference on Aerospace, Big Sky, MT, USA, 3–10 March 2007; pp. 1–18. [Google Scholar]
- Butz, H. The airbus approach to open integrated modular avionics (IMA): Technology, methods, processes and future road map. In Aircraft Systems Technician; Aviation Supplies & Academics Inc.: Newcastle, WA, USA, 2007; pp. 1–11. [Google Scholar]
- Aeronautical Radio Inc. Aircraft Data Network Part 7: Avionics Full-Duplex Switched Ethernet (AFDX); Network. ARINC Specification 664, Part 7; Aeronautical Radio, Inc.: Annapolis, MD, USA, 2005. [Google Scholar]
- Huang, B.; Zhou, M.; Lu, X.S.; Abusorrah, A. Scheduling of Resource Allocation Systems with Timed Petri Nets: A Survey. ACM Comp. Surv. 2023, 55, 1–27. [Google Scholar] [CrossRef]
- Komenda, J.; Zorzenon, D.; Balun, J. Modeling of safe timed Petri nets by two-level (max,+) automata. IFAC 2022, 55, 212–219. [Google Scholar] [CrossRef]
- Olenev, V. A methodology for formalized development of communication protocols based on Petri nets. Inf. Space 2022, 4, 37–45. [Google Scholar]
- Dixon, A.; Lazić, R. KReach: A Tool for Reachability in Petri Nets. In Tools and Algorithms for the Construction and Analysis of Systems, Proceedings of the 28th International Conference, Munich, Germany, 2–7 April 2022; Biere, A., Parker, D., Eds.; Springer: Cham, Switzerland, 2020; Volume 12078, pp. 405–412. [Google Scholar]
- Liu, G. Petri Nets: Theoretical Models and Analysis Methods for Concurrent Systems; Springer: Singapore, 2022; pp. 1–279. [Google Scholar]
- Glonina, A.B.; Balashov, V.V. On the Correctness of Real-Time Modular Computer Systems Modeling with Stopwatch Automata Networks. Model. Anal. Inf. Syst. 2018, 25, 174–192. [Google Scholar] [CrossRef]
- Glonina, A.B. A Tool System for Schedulability Analysis of Modular Computer Systems Configurations; Lomonosov Moscow State Universisty: Moscow, Russia, 2020; pp. 16–29. [Google Scholar]
- Glonina, A.B. General model of real-time modular computer systems operation for checking acceptability of such systems configurations. In Bulletin of the South Ural State University, Series: Mathematical Modelling, Programming and Computer Software; South Ural State University: Chelyabinsk, Russia, 2018; Volume 6, pp. 43–59. [Google Scholar]
- Tigane, S.; Guerrouf, F.; Hamani, N.; Kahloul, L.; Khalgui, M.; Ali, M.A. Dynamic Timed Automata for Reconfigurable System Modeling and Verification. Axioms 2023, 12, 230. [Google Scholar] [CrossRef]
- Bettira, R.; Kahloul, L.; Khalgui, M.; Li, Z. Reconfigurable Hierarchical Timed Automata: Modeling and Stochastic Verification. In Proceedings of the 2019 IEEE International Conference on Systems, Man, and Cybernetics, Bari, Italy, 6–9 October 2019; pp. 2364–2371. [Google Scholar]
- Bettira, R.; Kahloul, L.; Khalgui, M. A Novel Approach for Repairing Reconfigurable Hierarchical Timed Automata. In Proceedings of the 15th International Conference on Evaluation of Novel Approaches to Software Engineering, Prague, Czech Republic, 5–6 May 2020; pp. 398–406. [Google Scholar]
- Tahiri, I.; Philippot, A.; Carre-Menetrier, V.; Tajer, A. TimeBased Estimator for Control Reconfiguration of Discrete Event Systems (DES). In Proceedings of the CoDIT 2019: International Conference on Control, Decision and Information Technologies, Paris, France, 23 April 2019; pp. 1–7. [Google Scholar]
- UPPAAL. Online Documentation. Available online: https://uppaal.org/documentation (accessed on 5 June 2023).











Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Olenev, V.; Suvorova, E.; Chumakova, N. Broadcast Propagation Time in SpaceFibre Networks with Various Types of Spatial Redundancy. Sensors 2023, 23, 6161. https://doi.org/10.3390/s23136161
Olenev V, Suvorova E, Chumakova N. Broadcast Propagation Time in SpaceFibre Networks with Various Types of Spatial Redundancy. Sensors. 2023; 23(13):6161. https://doi.org/10.3390/s23136161
Chicago/Turabian StyleOlenev, Valentin, Elena Suvorova, and Nadezhda Chumakova. 2023. "Broadcast Propagation Time in SpaceFibre Networks with Various Types of Spatial Redundancy" Sensors 23, no. 13: 6161. https://doi.org/10.3390/s23136161
APA StyleOlenev, V., Suvorova, E., & Chumakova, N. (2023). Broadcast Propagation Time in SpaceFibre Networks with Various Types of Spatial Redundancy. Sensors, 23(13), 6161. https://doi.org/10.3390/s23136161





