An Intelligent Bio-Inspired Autonomous Surveillance System Using Underwater Sensor Networks
Abstract
:1. Introduction
- To propose an intelligent bio-inspired Tunicate Swarm Algorithm (TSA) based autonomous surveillance system using underwater sensor networks as an efficient method for data communication.
- TSA is utilized to identify the optimal number of cluster heads based on the novel fitness function to enhance the network’s lifetime.
- The fitness function takes into account critical parameters such as inter-cluster distance, residual energy of nodes, and node density, aiding in the identification of the most suitable cluster head.
- To show the effectiveness of the proposed approach, the simulation results are compared with state-of-the-art techniques.
2. Related Works
3. System Model
- The network consists of two types of nodes: underwater sensor (UWS) nodes, which are stationary and categorized into cluster heads and cluster member’s nodes due to the clustering approach, and a Sink Node located at the periphery of the surveillance area.
- The heterogeneous network is considered in the form of heterogeneous nodes’ energy.
- A single Sink Node is present within the network, and there are sufficient energy is available.
- The position of the Sink Node is assumed to be known and fixed throughout the surveillance period.
- Underwater sensor nodes possess limited energy and do not have their own energy supply.
- Regular underwater nodes share identical baseline energy levels and unique identification numbers.
- Node positions will be determined using a localization method.
- The communication range between UWS nodes is assumed to be fixed, and nodes can only communicate with each other if they are within this range.
- The network topology is assumed to be relatively static during the surveillance period, with minimal node mobility or changes in connectivity.
- Interference from external sources or neighboring networks is assumed to be negligible, allowing for efficient communication within the network.
4. Proposed Methodology
4.1. Duration of Network Installation
4.1.1. The Ability of a Node to Create Energy
4.1.2. Node Energy
4.1.3. The Percentage of the Distance between Each Node and the Sink
4.1.4. The Distance between Neighboring CHs
4.1.5. Node Density
4.2. Tunicate Swarm Based Optimized Cluster Head Selection Phase
4.2.1. Evade Clashes Amid Exploration Entities (SAs) Vector
4.2.2. Proceed in the Direction of the Optimal Neighboring Search Agent
4.2.3. Approach towards the Optimal Search Agent
4.2.4. Swarm Dynamics Behavior
| Algorithm 1: Tunicate Swarm-Based Optimized Cluster Head Selection Algorithm |
| Input: Initial quantity of individuals SNs in the population of |
| Output: Optimal selction of CHs base on fitness of SA () |
| //Initiate the Tunicate Swarm Algorithm process |
| 1. Set the initial values of parameters and |
| 2. Set |
| 3. While Do |
| 4. For each Do |
| 5. ← Assess the fitness of every search agent by employing Equation (16) |
| 6. Calculate , and using Equations (18)–(20) respectivelly |
| 7. if then |
| 8. The new location is calculated using Equation (21) |
| 9. else |
| 10. The new location is calculated using Equation (22) |
| 11. end if |
| 12. end for |
| 13. The current location of SNs are updated using Equation (23) |
| 14. Update the values of |
| 15. |
| 16. end while |
| 17. return as the CH |
| End TSA procedure |
4.3. The Data Transfer Phase
| Algorithm 2: Complete Working Process of the Proposed Method | |||||
| , , | |||||
| , , and throughput | |||||
| 1. | Sensors are placed in the underwater area i.e., in the form of heterogeneous networks | ||||
| 2. | , and | ||||
| 3. | do | ||||
| 4. | |||||
| 5. | do | ||||
| 6. | then | ||||
| 7. | Execute the election procedure of cluster heads as defined in Algorithm 1 | ||||
| 8. | + 1 | ||||
| 9. | Enforce a steady phase for transmission and collection of the sensed data from the underwater area | ||||
| 10. | else | ||||
| 11. | Update the energy dissipation of the node based on the utilization as defined by the energy model | ||||
| 12. | if then | ||||
| 13. | + 1 | ||||
| 14. | if then | ||||
| 15. | all available SNs are dead | ||||
| 16. | break | ||||
| 17. | Else | ||||
| 18. | |||||
| 19. | end if | ||||
| 20. | end for | ||||
| 21. | end for | ||||
| 22. | return j | ||||
5. Simulation Results
5.1. Utilizing Energy That Is Present
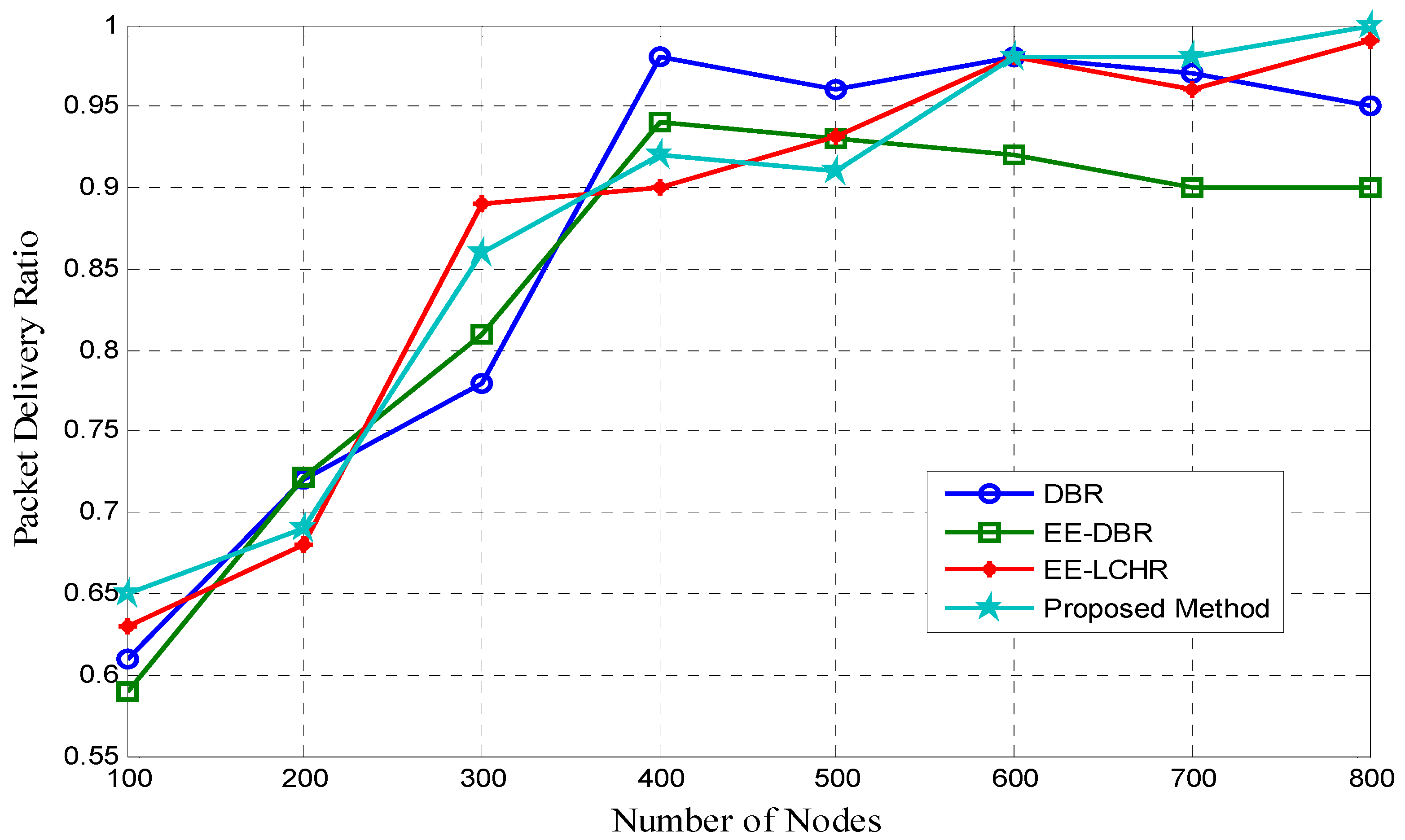
5.2. The Proportion of Successfully Delivered Packages
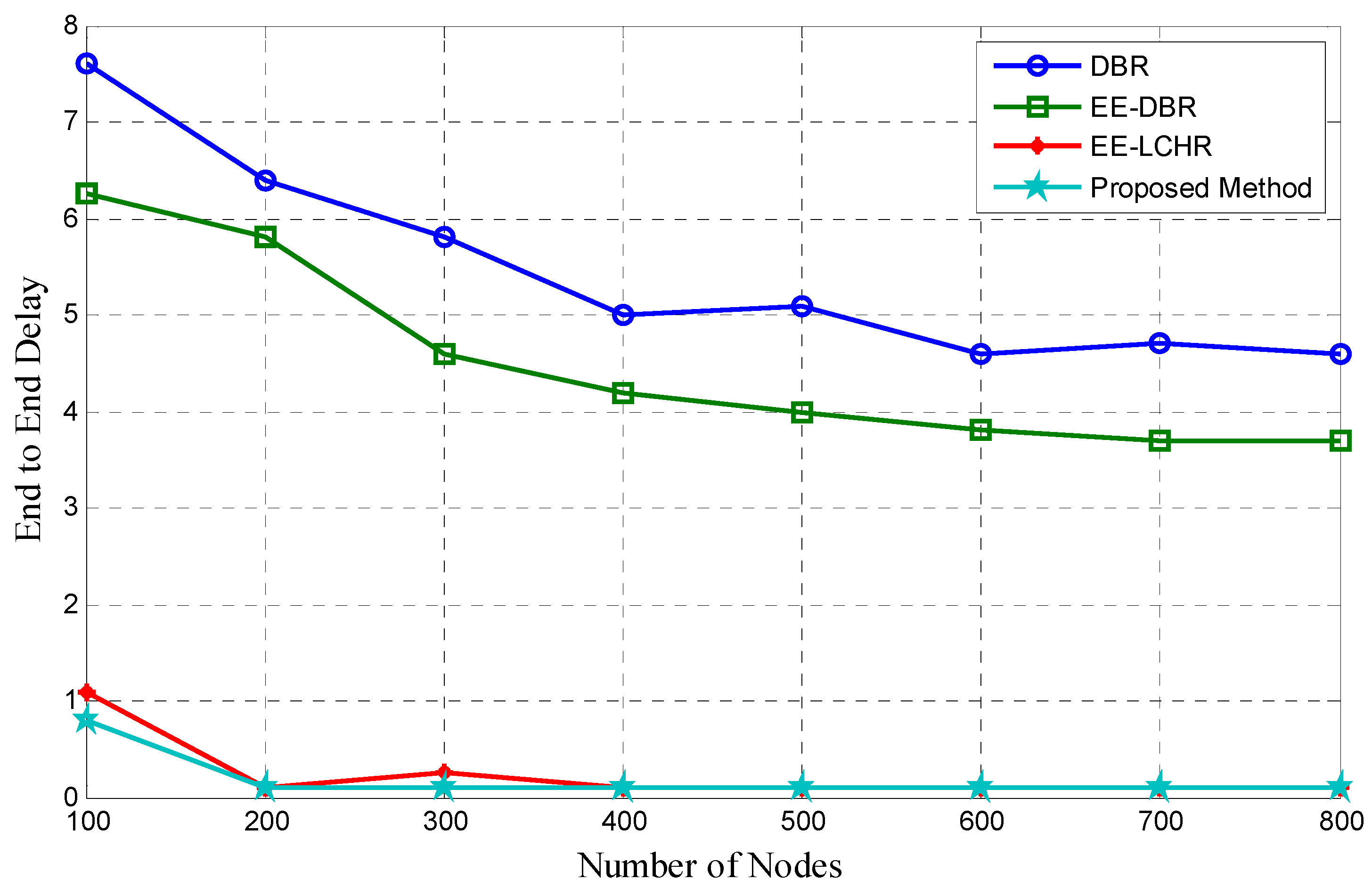
5.3. Beginning to End Delay
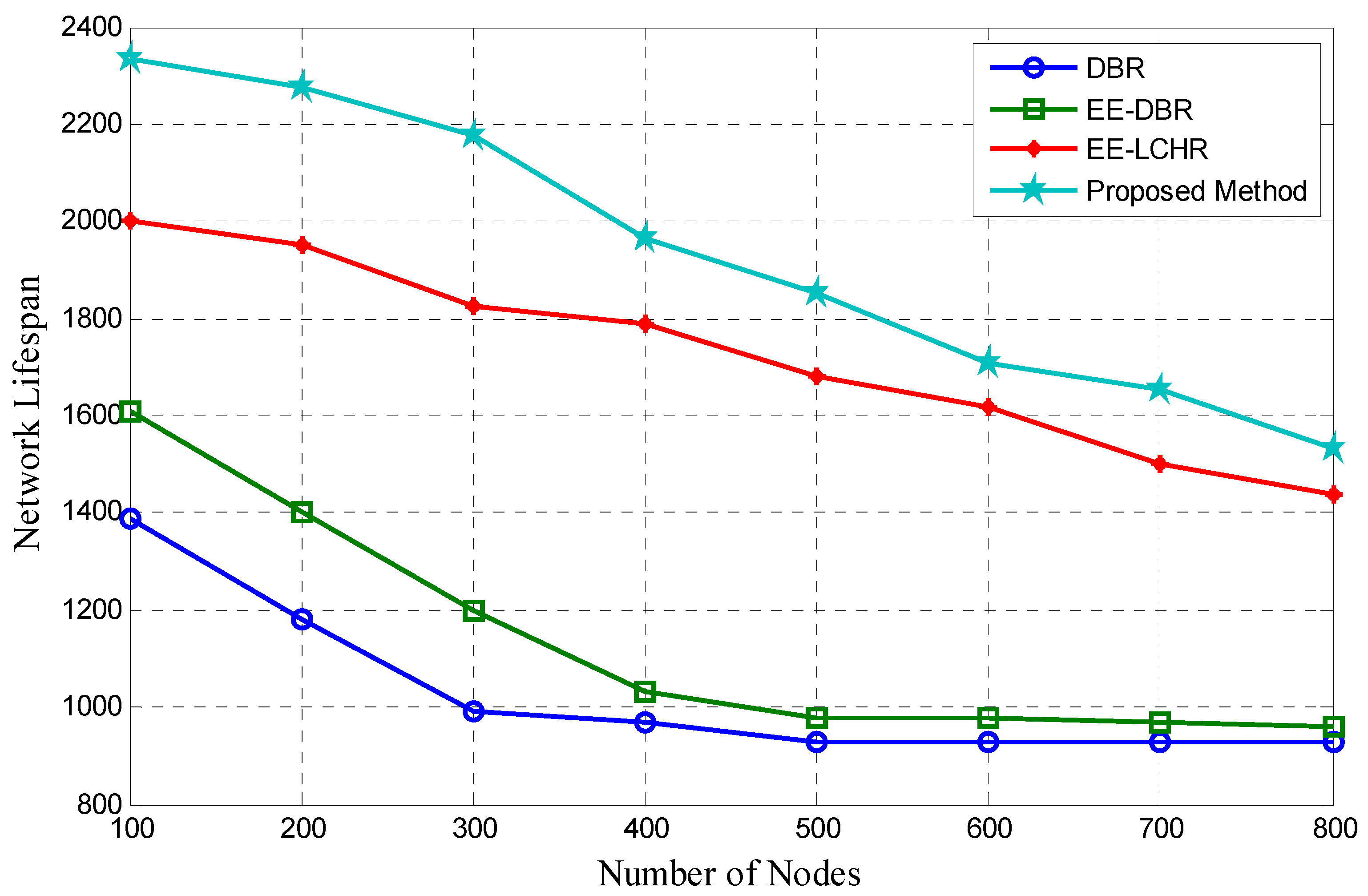
5.4. Duration of the Network’s Existence
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Iyer, S.; Rao, D.V. Genetic algorithm based optimization technique for underwater sensor network positioning and deployment. In Proceedings of the IEEE Underwater Technology (UT 5), Chennai, India, 23–25 February 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Felemban, E. Advanced Border Intrusion Detection and Surveillance Using Wireless Sensor Network Technology. Int. J. Commun. Netw. Syst. Sci. 2013, 6, 251–259. [Google Scholar] [CrossRef]
- Tuna, G.; Gungor, V.C. A survey on deployment techniques, localization algorithms, and research challenges for underwater acoustic sensor networks. Int. J. Commun. Syst. 2017, 30, e3350. [Google Scholar] [CrossRef]
- Cui, J.-H.; Kong, J.; Gerla, M.; Zhou, S. The challenges of building scalable mobile underwater wireless sensor networks for aquatic applications. IEEE Netw. 2006, 20, 12–18. [Google Scholar] [CrossRef]
- Freitag, L.; Grund, M.; Singh, S.; Partan, J.; Koski, P.; Ball, K. The WHOI micro-modem: An acoustic communications and Navigation system for multiple platforms. In Proceedings of the OCEANS 2005 MTS/IEEE, Washington, DC, USA, 17–23 September 2005; Volume 2, pp. 1086–1092. [Google Scholar] [CrossRef]
- Pompili, D.; Akyildiz, I.F. Overview of networking protocols for underwater wireless communications. IEEE Commun. Mag. 2009, 47, 97–102. [Google Scholar] [CrossRef]
- Pompili, D.; Melodia, T.; Akyildiz, I.F. A CDMA-based Medium Access Control for Under Water Acoustic Sensor Networks. IEEE Trans. Wirel. Commun. 2009, 8, 1899–1909. [Google Scholar] [CrossRef]
- Heidemann, J.; Ye, W.; Wills, J.; Syed, A.; Li, Y. Research challenges and applications for underwater sensor networking. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006, Las Vegas, NV, USA, 3–6 April 2006; Volume 1, pp. 228–235. [Google Scholar] [CrossRef]
- Partan, J.; Kurose, J.; Levine, B.N. A survey of practical issues in underwater networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 23–33. [Google Scholar] [CrossRef]
- Singh, S. An energy aware clustering and data gathering technique based on nature inspired optimization in WSNs. Peer-Peer Netw. Appl. 2020, 13, 1357–1374. [Google Scholar] [CrossRef]
- Ramteke, R.; Singh, S.; Malik, A. Optimized routing technique for IoT enabled software-defined heterogeneous WSNs using genetic mutation based PSO. Comput. Stand. Interfaces 2021, 79, 103548. [Google Scholar] [CrossRef]
- Singh, S.; Nandan, A.S.; Malik, A.; Kumar, R.; Awasthi, L.K.; Kumar, N. A GA-Based Sustainable and Secure Green Data Communication Method Using IoT-Enabled WSN in Healthcare. IEEE Internet Things J. 2022, 9, 7481–7490. [Google Scholar] [CrossRef]
- Nandan, A.S.; Singh, S.; Kumar, R.; Kumar, N. An Optimized Genetic Algorithm for Cluster Head Election Based on Movable Sinks and Adjustable Sensing Ranges in IoT-Based HWSNs. IEEE Internet Things J. 2022, 9, 5027–5039. [Google Scholar] [CrossRef]
- Singh, S.; Malik, A.; Kumar, R.; Singh, P.K. A proficient data gathering technique for unmanned aerial vehicle-enabled heterogeneous wireless sensor networks. Int. J. Commun. Syst. 2021, 34, e4956. [Google Scholar] [CrossRef]
- Kaur, S.; Awasthi, L.K.; Sangal, A.; Dhiman, G. Tunicate Swarm Algorithm: A new bio-inspired based metaheuristic paradigm for global optimization. Eng. Appl. Artif. Intell. 2020, 90, 103541. [Google Scholar] [CrossRef]
- Nicolaou, N.; See, A.; Xie, P.; Cui, J.-H.; Maggiorini, D. Improving the Robustness of Location-Based Routing for Underwater Sensor Networks. In Proceedings of the Oceans 2007-Europe, Aberdeen, UK, 18–21 June 2007; pp. 1–6. [Google Scholar] [CrossRef]
- Yan, H.; Shi, Z.J.; Cui, J.-H. DBR: Depth-based routing for underwater sensor networks. In Proceedings of the International Conference on Research in Networking, 2008, Singapore, 5–9 May 2008; Volume 4982, pp. 72–86. [Google Scholar] [CrossRef]
- Guangzhong, L.; Zhibin, L. Depth-based multi-hop routing protocol for underwater sensor network. In Proceedings of the 2010 The 2nd International Conference on Industrial Mechatronics and Automation, 2010, Wuhan, China, 30–31 May 2010; Volume 2, pp. 268–270. [Google Scholar] [CrossRef]
- Hu, T.; Fei, Y. QELAR: A Machine-Learning-Based Adaptive Routing Protocol for Energy-Efficient and Lifetime-Extended Underwater Sensor Networks. IEEE Trans. Mob. Comput. 2010, 9, 796–809. [Google Scholar] [CrossRef]
- Datta, A.; Dasgupta, M. Underwater Wireless Sensor Networks: A Comprehensive Survey of Routing Protocols. In Proceedings of the 2018 Conference on Information and Communication Technology (CICT), IIITDM, Jabalpur, India, 26–28 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Huang, C.-J.; Wang, Y.-W.; Liao, H.-H.; Lin, C.-F.; Hu, K.-W.; Chang, T.-Y. A power-efficient routing protocol for underwater wireless sensor networks. Appl. Soft Comput. 2011, 11, 2348–2355. [Google Scholar] [CrossRef]
- Gopi, S.; Kannan, G.; Desai, U.B.; Merchant, S.N. Energy Optimized Path Unaware Layered Routing Protocol for Underwater Sensor Networks. In Proceedings of the IEEE GLOBECOM 2008-2008 IEEE Global Telecommunications Conference, New Orleans, LA, USA, 30 November–4 December 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–6. [Google Scholar] [CrossRef]
- Gopi, S.; Govindan, K.; Chander, D.; Desai, U.B.; Merchant, S.N. E-PULRP: Energy Optimized Path Unaware Layered Routing Protocol for Underwater Sensor Networks. IEEE Trans. Wirel. Commun. 2010, 9, 3391–3401. [Google Scholar] [CrossRef]
- Wahid, A.; Kim, D. An Energy Efficient Localization-Free Routing Protocol for Underwater Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2012, 8, 307246. [Google Scholar] [CrossRef]
- Wahid, A.; Lee, S.; Jeong, H.-J.; Kim, D. EEDBR: Energy-Efficient Depth-Based Routing Protocol for Underwater Wireless Sensor Networks. Adv. Comput. Sci. Inf. Technol. 2011, 195, 223–234. [Google Scholar] [CrossRef]
- Ayaz, M.; Abdullah, A. Hop-by-Hop Dynamic Addressing Based (H2-DAB) Routing Protocol for Underwater Wireless Sensor Networks. In Proceedings of the 2009 International Conference on Information and Multimedia Technology, Jeju Island, Korea, 16–18 December 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 436–441. [Google Scholar] [CrossRef]
- Ayaz, M.; Abdullah, A.; Faye, I.; Batira, Y. An efficient Dynamic Addressing based routing protocol for Underwater Wireless Sensor Networks. Comput. Commun. 2012, 35, 475–486. [Google Scholar] [CrossRef]
- Noh, Y.; Lee, U.; Wang, P.; Choi, B.S.C.; Gerla, M. VAPR: Void-Aware Pressure Routing for Underwater Sensor Networks. IEEE Trans. Mob. Comput. 2013, 12, 895–908. [Google Scholar] [CrossRef]
- Jafri, M.; Ahmed, S.; Javaid, N.; Ahmad, Z.; Qureshi, R. AMCTD: Adaptive Mobility of Courier Nodes in Threshold-Optimized DBR Protocol for Underwater Wireless Sensor Networks. In Proceedings of the 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications, Compiegne, France, 28–30 October 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 93–99. [Google Scholar] [CrossRef]
- Coutinho, R.W.L.; Boukerche, A.; Vieira, L.F.M.; Loureiro, A.A.F. GEDAR: Geographic and opportunistic routing protocol with Depth Adjustment for mobile underwater sensor networks. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 251–256. [Google Scholar] [CrossRef]
- Coutinho, R.W.L.; Boukerche, A.; Vieira, L.F.M.; Loureiro, A.A.F. Geographic and Opportunistic Routing for Underwater Sensor Networks. IEEE Trans. Comput. 2016, 65, 548–561. [Google Scholar] [CrossRef]
- Chao, C.-M.; Jiang, C.-H.; Li, W.-C. DRP: An energy-efficient routing protocol for underwater sensor networks. Int. J. Commun. Syst. 2017, 30, e3303. [Google Scholar] [CrossRef]
- Gomathi, R.M.; Manickam, J.M.L.; Sivasangari, A.; Ajitha, P. Energy efficient dynamic clustering routing protocol in underwater wireless sensor networks. Int. J. Netw. Virtual Organ. 2020, 22, 415. [Google Scholar] [CrossRef]
- Alasarpanahi, H.; Ayatollahitafti, V.; Gandomi, A. Energy-efficient void avoidance geographic routing protocol for underwater sensor networks. Int. J. Commun. Syst. 2020, 33, e4218. [Google Scholar] [CrossRef]
- Sozer, E.M.; Stojanovic, M.; Proakis, J.G. Underwater acoustic networks. IEEE J. Ocean. Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Datta, A.; Dasgupta, M. Energy Efficient Layered Cluster Head Rotation Based Routing Protocol for Underwater Wireless Sensor Networks. Wirel. Pers. Commun. 2022, 125, 2497–2514. [Google Scholar] [CrossRef]

| Simulation Parameters | Values |
|---|---|
| Network area | |
| Number of nodes | |
| Transmission range | |
| data packet size | |
| Node density/Energy heterogeneity (3 forms) | 10% form-3 (2 ), 20% form-2 (1.5 ), 70% form-1 (1 ) |
| power consumption for transmission mode | |
| power consumption for receive mode | |
| Maximum Iteration | 40 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, S.; Singh, Y.V.; Yadav, P.S.; Sharma, V.; Lin, C.-C.; Jung, K.-H. An Intelligent Bio-Inspired Autonomous Surveillance System Using Underwater Sensor Networks. Sensors 2023, 23, 7839. https://doi.org/10.3390/s23187839
Khan S, Singh YV, Yadav PS, Sharma V, Lin C-C, Jung K-H. An Intelligent Bio-Inspired Autonomous Surveillance System Using Underwater Sensor Networks. Sensors. 2023; 23(18):7839. https://doi.org/10.3390/s23187839
Chicago/Turabian StyleKhan, Shadab, Yash Veer Singh, Prasant Singh Yadav, Vishnu Sharma, Chia-Chen Lin, and Ki-Hyun Jung. 2023. "An Intelligent Bio-Inspired Autonomous Surveillance System Using Underwater Sensor Networks" Sensors 23, no. 18: 7839. https://doi.org/10.3390/s23187839
APA StyleKhan, S., Singh, Y. V., Yadav, P. S., Sharma, V., Lin, C.-C., & Jung, K.-H. (2023). An Intelligent Bio-Inspired Autonomous Surveillance System Using Underwater Sensor Networks. Sensors, 23(18), 7839. https://doi.org/10.3390/s23187839











