Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives
Abstract
:1. Introduction
1.1. System of IOMV
- Data Collection Layer: In the IOMV system, this layer is also known as the Physical Layer. And its key function is to collect data from various onboard medical devices related to patient health within MVs, in addition to other sensor/functional-related information from the IOV side. These medical devices enable D2D (Device-To-Device) communications and share their information with the Onboard Gateway/IVN, a layer called V2D (Vehicle To Device). D2D and V2D communications take place using Bluetooth, Zigbee, WiFi, LAN, etc., protocols. Next, Onboard-Gateway-to-Onboard-Unit (OBU) communication takes place using IVN protocols like CAN, LIN, Ethernet, etc.
- Communication or Network Layer: In this layer, when the MV is moving or located remotely on its travel path, it may be required to form multiple and different networks external to the MV to share the intra-MV data collected by the OBU by using V2X communications, such as V2P (Vehicle To Person), V2I (Vehicle To Infrastructure), V2N (Vehicle To Network), V2V (Vehicle To Vehicle), V2R (Vehicle To Road-Side Units), etc. This layer may use the Internet, mobile networks, radio signals, etc.
- Middleware or Data Management Layer: The data collected from the Communication or Network Layer are further shared with the Middleware or Data Management Layer. In this layer, the collected data are stored and aggregated as cloud data or big data for further analysis and computational analysis in the IOT Computing Layer. Preprocessing and knowledge extraction may be performed using analysis and computational techniques like artificial intelligence and machine learning (AIML). Or, as may be required, the raw information from the Network Layer may be directly shared with the Application or Business Layer, i.e., with the hospital for its analysis. Also, this layer may use the Internet, mobile networks, or radio signals for communication.
- Application or Business Layer: This is the top or final layer as per the hierarchical order of the IOMV architecture. This layer is the Application or Business Layer, i.e., the hospital setting. The preprocessed data received from the Middleware or Data Management Layer, or the raw data received directly from the Communication or Network Layer as per requirements, will be received by the Hospital Servers. Medical staff like doctors and nurses can analyse these data for their further clinical processing to provide connected healthcare to the patient onboard the remotely moving MV. Further, with the uptake of Electronic Medical Records (EMRs), the exponential adoption of IOT devices in connected healthcare services has increased cyberthreats in the healthcare sector [25,26]. Within healthcare, there has been an explosion in the real-time usage of wired and wireless devices in the care of almost every patient—the IOMT, such as computers, medical pumps, ventilators, anaesthetic machines, operating tables, operating robots, infusion pumps, pacing devices, organ support, syringe pumps, implantable medical devices, a plethora of monitoring modalities, etc. All of these devices, once connected to a hospital network with the IOMV system, as shown in Figure 1, allow the collection of a huge amount of data that can aid decision making, monitor and alert staff to unsafe situations, and expedite patient care. But this interconnectivity presents an opportunity for hackers to attack the systems directly to cause erroneous monitoring, alter the settings of any device, and even access the EMR via the IOMV system using V2X communication, which poses a danger to patient safety.
1.2. Cybersecurity Risk in IOMV System
1.3. Related Applicable Standards and Frameworks
- We evaluated global trends relevant to this research field in terms of top publications, publication patterns, types of journals, top authors in this field, top contributing nations and affiliated institutions, top sponsoring agencies, top keyword searches based on the Boolean technique, gaps, future outlooks, etc., based on a survey analysis of 1582 and 1889 published documents between 2016 and 2023 from the Scopus and WOS databases, respectively.
- We analysed the top journals and highly cited papers based on the databases WOS and Scopus relevant to this research area and present insights highlighting their methodologies, alongside contrasting each paper’s merits, challenges, and limitations.
- We conducted a statistical study to analyse the effectiveness of the top-ten countries, and the results are discussed.
- We define and present the system model and architecture of the IOMV system and types of communications and present the relevant applicable standards, protocols, and governing frameworks.
- We describe a variety of factors that are responsible for causing a cybersecurity risk in the IOT-application-based IOMV. We discuss how to perform a risk assessment and parameterisation to strengthen the cybersecurity of the IOMV system and describe solutions helpful in addressing cybersecurity risks, like using AIML, artificial general intelligence (AGI), etc.
- We classify and consolidate different types of sophisticated potential cyber-attacks in tabulated form; these attacks can occur at various layers of the IOMV, right from the source, i.e., onboard IOT-connected medical devices, up to the target recipient devices at hospitals and their interconnecting communication channels and networks. And we explain the cause and impact of various significant cyber-attacks.
- In the last section, we provide the limitations of this work, major constraints, and significant potential challenges that need to be addressed and discuss the outlook for future work related to implementing robust cybersecurity measures in these IOT-application-based vehicles.
2. Primary Data
3. Research Methodology
3.1. Important Keywords
3.2. Preliminary Analysis
4. Literature Review Analysis
5. Assessment of Cybersecurity in the IOMV System
5.1. Types and Characteristics of Cyber-Attacks
5.2. Artificial Intelligence and Machine Learning for Strengthening Cybersecurity in IOMV System
5.3. Assessment of Cybersecurity Risk in IOMV System
5.4. Parameterisation of Cybersecurity
6. Results
- We perceive that this is a niche yet unexplored research area and that it appears to be an upcoming and widely trending topic, as the concept of the IOMV is basically derived from integrating IOT-based applications, i.e., the IOV and IOMT.
- Most of the research gaps corresponding to this topic of the IOMV are still unexplored, and there is a great need to implement robust cybersecurity measures due to increasingly sophisticated cyber-attacks; many challenges and factors influencing security vulnerabilities, like integrity, interoperability, etc., and many issues like few defined standards, regulations, guidelines, frameworks, protocols, etc., are significant gaps and issues that need to be explored and addressed, and hence, it is becoming an upcoming and widely trending topic.
- Also, as part of the study and analysis, we have presented various types of potential cyber-attacks that can take place at different layers of the IOMV system.
- We have discussed and provided the application of AIML and AGI techniques as solutions for developing countermeasures to strengthen cybersecurity in IOMV systems.
- We have presented the IOMV system model and architecture and the types of communications that can take place at different layers of the IOT structure.
- We have presented details of relevant standards, protocols, frameworks, and guidelines applicable to the IOMV.
- Factors affecting the cybersecurity risk in the IOMV system have been discussed, along with various challenges and constraints affecting the cybersecurity risk in the IOMV.
- We have presented methods for assessing the cybersecurity risk and parameterisation details for assessing the strength of cybersecurity, which can help to develop countermeasures for cybersecurity.
- And we have discussed the future scope to focus on, which can be helpful for researchers to develop robust cybersecurity in IOMV systems.
7. Limitations
8. Challenges and Constraints
8.1. Unexplored and Niche Area
8.2. Not Immune to Variety of Security Anomalies
8.3. Complicated Requirements of IOMV System
- Seamless Integration—with existing technology and infrastructure.
- Scalability—without any significant decline in IOMV system performance, scalable and flexible architectures are needed to maintain uniformity in handling the future demand of rapidly increasingly connected devices, as scalability affects network capacity and device and data management, e.g., healthcare devices and their increased data and communication volume.
- Interoperability—connecting many diverse devices.
- Usability and Cost—tradeoff and balance between the cost of deployment and benefits.
- Reliability—performance of the system can suffer even if one IOT device is unresponsive or compromised due to network blockages, DOS attacks, and malfunctions in communications.
- Power Management—device-level energy issues, as IOT devices are developed to be smaller, use low power, and operate using batteries.
- Data Management—collection, storage, and processing of data.
- Lack of Standardisation—absence of common agreed-upon specifications, which leads to inefficient interconnection, communication, and exchange of data between devices.
- Lack of Protocols—in the automotive and healthcare industries, systems manufactured by various manufacturers follow their own standard rules and protocols.
- Lack of Skill Set—conventional vehicle manufacturers/operators and medical personnel are not trained for cybersecurity adversaries, and usually, IT systems are supported by the IT teams.
- Device and Network Infrastructure—continuously building, maintaining, and supporting connections of large numbers of advanced IOT devices used in IOV and IOMT applications require regularly updating existing devices.
- Poor Connectivity—IOT sensors are required to monitor process data and supply information.
8.4. Complex Nature of Cybersecurity of IOMV System
- Lack of encryption—where hackers can easily manipulate the software.
- Inadequate testing and updating—automotive and medical manufacturers not placing much emphasis on system testing and updating, showing eagerness to manufacture and deliver their devices into markets.
- Brute-force password and weak credential details—make the IOT devices used in the IOV and IOMT vulnerable to cyber-attacks.
- Software Vulnerabilities—can happen from errors and mistakes like bugs and weaknesses in the software code by using unsupported or outdated software that can be exploited by attackers to carry out malicious attacks.
9. Future Outlook
10. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Leen, G.; Heffernan, D. Expanding automotive electronic systems. Computer 2002, 35, 88–93. [Google Scholar] [CrossRef]
- Rajasekhar, M.V.; Jaswal, A.K. Autonomous vehicles: The future of automobiles. In Proceedings of the 2015 IEEE International Transportation Electrification Conference (ITEC), Chennai, India, 27–29 August 2015; pp. 1–6. [Google Scholar]
- Hakak, S.; Gadekallu, T.R.; Maddikunta, P.K.R.; Ramu, S.P.; M, P.; De Alwis, C.; Liyanage, M. Autonomous vehicles in 5G and beyond: A survey. Veh. Commun. 2023, 39, 100551. [Google Scholar] [CrossRef]
- Bagloee, S.A.; Tavana, M.; Asadi, M.; Oliver, T. Autonomous vehicles: Challenges, opportunities, and future implications for transportation policies. J. Mod. Transp. 2016, 24, 284–303. [Google Scholar] [CrossRef]
- John, A.A.; Thakur, P.; Singh, G. Potential, concepts, and key advances for a ubiquitous adaptive indigenous microengineering and nanoengineering in 6G network. Int. J. Commun. Syst. 2022, 2022, e5410. [Google Scholar] [CrossRef]
- Hu, Z.; Tang, H. Design and Implementation of Intelligent Vehicle Control System Based on Internet of Things and Intelligent Transportation. Sci. Program. 2022, 2022, 6201367. [Google Scholar] [CrossRef]
- Jadaan, K.; Zeater, S.; Abukhalil, Y. Connected Vehicles: An Innovative Transport Technology. Procedia Eng. 2017, 187, 641–648. [Google Scholar] [CrossRef]
- Yang, D.; Jiang, K.; Zhao, D.; Yu, C.; Cao, Z.; Xie, S.; Xiao, Z.; Jiao, X.; Wang, S.; Zhang, K. Intelligent and connected vehicles: Current status and future perspectives. Sci. China Technol. Sci. 2018, 61, 1446–1471. [Google Scholar] [CrossRef]
- Uhlemann, E. Introducing Connected Vehicles [Connected Vehicles]. IEEE Veh. Technol. Mag. 2015, 10, 23–31. [Google Scholar] [CrossRef]
- Coppola, R.; Morisio, M. Connected car: Technologies, issues, future trends. ACM Comput. Surv. (CSUR) 2016, 49, 1–36. [Google Scholar] [CrossRef]
- Holler, J.; Tsiatsis, V.; Mulligan, C.; Karnouskos, S.; Avesand, S.; Boyle, D. Internet of Things; Academic Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Yang, F.; Wang, S.; Li, J.; Liu, Z.; Sun, Q. An overview of Internet of Vehicles. China Commun. 2014, 11, 1–15. [Google Scholar] [CrossRef]
- Ji, B.; Zhang, X.; Mumtaz, S.; Han, C.; Li, C.; Wen, H.; Wang, D. Survey on the Internet of Vehicles: Network Architectures and Applications. IEEE Commun. Stand. Mag. 2020, 4, 34–41. [Google Scholar] [CrossRef]
- Raul, N.M.; Wagdarikar, N.M.; Bhukya, C.R. Development of hardware-in-loop automated test bench for liquid-assisted after-treatment controls system’s regression tests. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–6. [Google Scholar]
- Zhang, G.; Navimipour, N.J. A comprehensive and systematic review of the IoT-based medical management systems: Applications, techniques, trends and open issues. Sustain. Cities Soc. 2022, 82, 103914. [Google Scholar] [CrossRef]
- Lu, D.; Liu, T. The application of IOT in medical system. In Proceedings of the 2011 IEEE International Symposium on IT in Medicine and Education, Cuangzhou, China, 9–11 December 2011; Volume 1, pp. 272–275. [Google Scholar]
- Dimitrov, D.V. Medical Internet of Things and Big Data in Healthcare. Healthc. Inform. Res. 2016, 22, 156–163. [Google Scholar] [CrossRef] [PubMed]
- Javdani, H.; Kashanian, H. Internet of things in medical applications with a service-oriented and security approach: A survey. Health Technol. 2017, 8, 39–50. [Google Scholar] [CrossRef]
- Mishra, P.; Thakur, P.; Singh, G. Enabling technologies for IoT based smart city. In Proceedings of the 2021 Sixth International Conference on Image Information Processing (ICIIP), Shimla, India, 26–28 November 2021; Volume 6, pp. 99–104. [Google Scholar]
- Kashani, M.H.; Madanipour, M.; Nikravan, M.; Asghari, P.; Mahdipour, E. A systematic review of IoT in healthcare: Applications, techniques, and trends. J. Netw. Comput. Appl. 2021, 192, 103164. [Google Scholar] [CrossRef]
- IEC 60601-1: 2005; Medical Electrical Equipment-Part 1: General Requirements for Basic Safety and Essential Performance. International Electrotechnical Commission: Geneva, Switzerland, 2005.
- Karthika, B.; Vijayakumar, A.R. ISO 13485: Medical Devices–Quality Management Systems, Requirements for Regulatory Purposes. In Medical Device Guidelines and Regulations Handbook; Springer International Publishing: Cham, Switzerland, 2022; pp. 19–29. [Google Scholar]
- Qian, Y. The Future of e-Health and Wireless Technologies. IEEE Wirel. Commun. 2021, 28, 2–3. [Google Scholar] [CrossRef]
- Lin, D.; Tang, Y.; Labeau, F.; Yao, Y.; Imran, M.; Vasilakos, A.V. Internet of Vehicles for E-Health Applications: A Potential Game for Optimal Network Capacity. IEEE Syst. J. 2015, 11, 1888–1896. [Google Scholar] [CrossRef]
- Cartwright, A.J. The elephant in the room: Cybersecurity in healthcare. J. Clin. Monit. Comput. 2023, 1–10. [Google Scholar] [CrossRef]
- Chakraborty, C.; Nagarajan, S.M.; Devarajan, G.G.; Ramana, T.V.; Mohanty, R. Intelligent AI-based Healthcare Cyber Security System using Multi-Source Transfer Learning Method. ACM Trans. Sens. Networks 2023. [Google Scholar] [CrossRef]
- Mohanty, J.; Mishra, S.; Patra, S.; Pati, B.; Panigrahi, C.R. IoT security, challenges, and solutions: A review. In Progress in Advanced Computing and Intelligent Engineering: Proceedings of ICACIE 2019; Springer: New York, NY, USA, 2021; Volume 2, pp. 493–504. [Google Scholar]
- Noor, M.B.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Mudhivarthi, B.R.; Thakur, P.; Singh, G. Aspects of Cyber Security in Autonomous and Connected Vehicles. Appl. Sci. 2023, 13, 3014. [Google Scholar] [CrossRef]
- Abdullah, A.; Hamad, R.; Abdulrahman, M.; Moala, H.; Elkhediri, S. CyberSecurity: A review of internet of things (IoT) security issues, challenges and techniques. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019; pp. 1–6. [Google Scholar]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Cui, J.; Liew, L.S.; Sabaliauskaite, G.; Zhou, F. A review on safety failures, security attacks, and available countermeasures for autonomous vehicles. Ad. Hoc. Netw. 2018, 90, 101823. [Google Scholar] [CrossRef]
- Rathee, G.; Saini, H.; Kerrache, C.A.; Herrera-Tapia, J. A Computational Framework for Cyber Threats in Medical IoT Systems. Electronics 2022, 11, 1705. [Google Scholar] [CrossRef]
- Yaqoob, T.; Abbas, H.; Atiquzzaman, M. Security vulnerabilities, attacks, countermeasures, and regulations of networked medical devices—A review. IEEE Commun. Surv. Tutor. 2019, 21, 3723–3768. [Google Scholar] [CrossRef]
- ISO 26262-1; 2018–Road Vehicles—Functional Safety. International Organization for Standardization (ISO): Geneva, Switzerland, 2018.
- ISO/SAE 21434; 2021: Road Vehicles: Cybersecurity Engineering. International Organization for Standardization: Geneva, Switzerland, 2021.
- Ross, R.S. NIST SP 800-30 REV. 1: Guide for Conducting Risk Assessments; National Institute of Standards Technology: Gaithersburg, MD, USA, 2012. [Google Scholar]
- IEC 31010:2009; Risk Management—Risk Assessment Techniques. International Organization for Standardization: Geneva, Switzerland, 2009.
- ISO 14971: 2019; Medical Devices: Application of Risk Management to Medical Devices. British Standards Institute: London, UK, 2019.
- Malatji, M. Management of enterprise cyber security: A review of ISO/IEC 27001: 2022. In Proceedings of the 2023 International Conference on Cyber Management and Engineering (CyMaEn), Bangkok, Thailand, 26–27 January 2023; pp. 117–122. [Google Scholar]
- Janssen, M.; Schrenker, R. Guidelines From 80001: Maintaining a Medical IT Network. Biomed. Instrum. Technol. 2011, 45, 295–299. [Google Scholar] [CrossRef]
- Dempsey, K.; Witte, G.; Rike, D. Summary of NIST SP 800-53, Revision 4: Security and Privacy Controls for Federal Information Systems and Organizations; No. NIST CSWP 2; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014; p. 13. [Google Scholar]
- Clinch, J. ITIL V3 and Information Security. Best Manag. Pract. 2009. Available online: https://trainingcreatively.com/backend/web/uploads/resources/d10dc29f496ee8151f5a223d56b59eb37b8b304b.pdf (accessed on 1 August 2023).
- Disterer, G. ISO/IEC 27000, 27001 and 27002 for information security management. J. Inf. Secur. 2013, 4. Available online: https://serwiss.bib.hs-hannover.de/files/938/ISOIEC_27000_27001_and_27002_for_Information_Security_Management.pdf (accessed on 1 August 2023). [CrossRef]
- Mantelero, A. Cloud computing, trans-border data flows and the European Directive 95/46/EC: Applicable law and task distribution. Eur. J. Law Technol. 2012, 3. Available online: https://ejlt.org/index.php/ejlt/article/view/96 (accessed on 1 August 2023).
- Kumar, P.; Lee, H.-J. Security Issues in Healthcare Applications Using Wireless Medical Sensor Networks: A Survey. Sensors 2011, 12, 55–91. [Google Scholar] [CrossRef]
- Bagga, M.; Thakral, P.; Bagga, T. A Study on IoT: Model, Communication Protocols, Security Hazards & Countermeasures. In Proceedings of the 2018 Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC), Solan, India, 20–22 December 2018; pp. 591–598. [Google Scholar]
- Argaw, S.T.; Troncoso-Pastoriza, J.R.; Lacey, D.; Florin, M.-V.; Calcavecchia, F.; Anderson, D.; Burleson, W.; Vogel, J.-M.; O’leary, C.; Eshaya-Chauvin, B.; et al. Cybersecurity of Hospitals: Discussing the challenges and working towards mitigating the risks. BMC Med. Informatics Decis. Mak. 2020, 20, 1–10. [Google Scholar] [CrossRef]
- Almogren, A.; Mohiuddin, I.; Din, I.U.; Almajed, H.; Guizani, N. Ftm-iomt: Fuzzy-based trust management for preventing sybil attacks in internet of medical things. IEEE Internet Things J. 2020, 8, 4485–4497. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B. A survey on internet of vehicles: Applications, security issues & solutions. Veh. Commun. 2019, 20, 100182. [Google Scholar] [CrossRef]
- Rathee, G.; Thakur, P.; Singh, G.; Saini, H. Aspects of secure communication during spectrum handoff in cognitive radio networks. In Proceedings of the 2016 International Conference on Signal Processing and Communication (ICSC), Noida, India, 26–28 December 2016; pp. 64–69. [Google Scholar] [CrossRef]
- Mudhivarthi, B.R.; Thakur, P. Integration of artificial intelligence in robotic vehicles: A bibliometric analysis. Paladyn J. Behav. Robot. 2022, 13, 110–120. [Google Scholar] [CrossRef]
- Wagle, S.A.; Harikrishnan, R. A Bibliometric Analysis of Plant Disease Classification with Artificial Intelligence based on Scopus and WOS. Libr. Philos. Pract. 2021, 1–27. Available online: https://www.researchgate.net/profile/Shivali-Wagle/publication/350092508_A_Bibliometric_Analysis_of_Plant_Disease_Classification_with_Artificial_Intelligence_based_on_Scopus_and_WOS/links/6062165f458515e8347d7837/A-Bibliometric-Analysis-of-Plant-Disease-Classification-with-Artificial-Intelligence-based-on-Scopus-and-WOS.pdf (accessed on 1 August 2023).
- Mishra, D.; Gunasekaran, A.; Childe, S.J.; Papadopoulos, T.; Dubey, R.; Wamba, S. Vision, applications and future challenges of Internet of Things: A bibliometric study of the recent literature. Ind. Manag. Data Syst. 2016, 116, 1331–1355. [Google Scholar] [CrossRef]
- Azam, M.; Hassan, S.A.; Puan, O.C. Autonomous Vehicles in Mixed Traffic Conditions—A Bibliometric Analysis. Sustainability 2022, 14, 10743. [Google Scholar] [CrossRef]
- Parekh, D.; Poddar, N.; Rajpurkar, A.; Chahal, M.; Kumar, N.; Joshi, G.P.; Cho, W. A Review on Autonomous Vehicles: Progress, Methods and Challenges. Electronics 2022, 11, 2162. [Google Scholar] [CrossRef]
- Jalali, M.S.; Razak, S.; Gordon, W.; Perakslis, E.; Madnick, S. Health Care and Cybersecurity: Bibliometric Analysis of the Literature. J. Med. Internet Res. 2019, 21, e12644. [Google Scholar] [CrossRef]
- Nair, S.V.R.; Saha, S.K. Advancements in Cyber Security and Information Systems in Healthcare from 2004 to 2022: A Bibliometric Analysis. In Proceedings of the 2023 International Conference on Intelligent Systems, Advanced Computing and Communication (ISACC), Silchar, India, 3–4 February 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Shukla, G.; Gochhait, S. Cyber security trend analysis using Web of Science: A bibliometric analysis. Eur. J. Mol. Clin. Med. 2020, 7, 2567–2576. [Google Scholar]
- Maphathe, B.F.; Thakur, P.; Singh, G.; Iddi, H.E. Deemed the Terahertz Channel Modeling in Internet of Multimedia Design In-Body Antenna. Int. J. E-Health Med Commun. 2022, 13, 1–17. [Google Scholar] [CrossRef]
- Taherdoost, H. Blockchain-Based Internet of Medical Things. Appl. Sci. 2023, 13, 1287. [Google Scholar] [CrossRef]
- Swarnkar, R.; Harikrishnan, R.; Thakur, P.; Singh, G. Electric Vehicle Lithium-ion Battery Ageing Analysis under Dynamic Condition: A Machine Learning Approach. SAIEE Afr. Res. J. 2023, 114, 4–13. [Google Scholar] [CrossRef]
- Rejeb, A.; Rejeb, K.; Treiblmaier, H.; Appolloni, A.; Alghamdi, S.; Alhasawi, Y.; Iranmanesh, M. The Internet of Things (IoT) in healthcare: Taking stock and moving forward. Internet Things 2023, 22, 100721. [Google Scholar] [CrossRef]
- Singh, A.K.; Maurya, A.K.; Prakash, R.; Thakur, P.; Tiwari, B.B. Reconfigurable intelligent surface with 6G for industrial revolution: Potential applications and research challenges. Paladyn. J. Behav. Robot. 2023, 14, 20220114. [Google Scholar] [CrossRef]
- Sharma, P.; Patel, M.; Prasad, A. A systematic literature review on Internet of Vehicles Security. arXiv 2022, arXiv:2212.08754. [Google Scholar]
- Hsu, C.-H.; Alavi, A.H.; Dong, M. Introduction to the Special Section on Cyber Security in Internet of Vehicles. ACM Trans. Internet Technol. 2022, 22, 1–6. [Google Scholar] [CrossRef]
- Rocha, D.; Teixeira, G.; Vieira, E.; Almeida, J.; Ferreira, J. A Modular In-Vehicle C-ITS Architecture for Sensor Data Collection, Vehicular Communications and Cloud Connectivity. Sensors 2023, 23, 1724. [Google Scholar] [CrossRef]
- Thakur, P.; Singh, G. Potential Simulation Frameworks and Challenges for Internet of Vehicles Networks. In Proceedings of the 2020 International Conference on Artificial Intelligence, Big Data, Computing and Data Communication Systems (icABCD), Durban, South Africa, 6–7 August 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Mishra, P.; Thakur, P.; Singh, G. Sustainable Smart City to Society 5.0: State-of-the-Art and Research Challenges. SAIEE Afr. Res. J. 2022, 113, 152–164. [Google Scholar] [CrossRef]
- Pekaric, I.; Sauerwein, C.; Haselwanter, S.; Felderer, M. A taxonomy of attack mechanisms in the automotive domain. Comput. Stand. Interfaces 2021, 78, 103539. [Google Scholar] [CrossRef]
- Pai, R.R.; Alathur, S. Bibliometric Analysis and Methodological Review of Mobile Health Services and Applications in India. Int. J. Med. Informatics 2020, 145, 104330. [Google Scholar] [CrossRef]
- Cabanillas-Carbonell, M.; Pérez-Martínez, J.; Yáñez, J.A. 5G Technology in the Digital Transformation of Healthcare, a Systematic Review. Sustainability 2023, 15, 3178. [Google Scholar] [CrossRef]
- Gandia, R.M.; Antonialli, F.; Cavazza, B.H.; Neto, A.M.; de Lima, D.A.; Sugano, J.Y.; Nicolai, I.; Zambalde, A.L. Autonomous vehicles: Scientometric and bibliometric review. Transp. Rev. 2018, 39, 9–28. [Google Scholar] [CrossRef]
- Kamalov, F.; Pourghebleh, B.; Gheisari, M.; Liu, Y.; Moussa, S. Internet of Medical Things Privacy and Security: Challenges, Solutions, and Future Trends from a New Perspective. Sustainability 2023, 15, 3317. [Google Scholar] [CrossRef]
- Akinola, S.A.; Thakur, P.; Sharma, M.S.; Kumar, K.; Singh, G. Deep learning approach to load forecasting: A survey. In Communication, Networks and Computing: Second International Conference, CNC 2020, Gwalior, India, 29–31 December 2020; Revised Selected Papers 2; Springer: Singapore, 2021; pp. 250–262. [Google Scholar]
- Benyahya, M.; Collen, A.; Kechagia, S.; Nijdam, N.A. Automated city shuttles: Mapping the key challenges in cybersecurity, privacy and standards to future developments. Comput. Secur. 2022, 122, 102904. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.-H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]
- Pham, M.; Xiong, K. A Survey on Security Attacks and Defense Techniques for Connected and Autonomous Vehicles. Comput. Secur. 2021, 109, 102269. [Google Scholar] [CrossRef]
- Arif, M.; Wang, G.; Alam Bhuiyan, Z.; Wang, T.; Chen, J. A survey on security attacks in VANETs: Communication, applications and challenges. Veh. Commun. 2019, 19, 100179. [Google Scholar] [CrossRef]
- Tariq, S.; Lee, S.; Kim, H.K.; Woo, S.S. CAN-ADF: The controller area network attack detection framework. Comput. Secur. 2020, 94, 101857. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2020, 32. [Google Scholar] [CrossRef]
- Gao, X.; Liu, H.; Deng, W.; Tian, Y.; Zou, G.; Hou, H.; Ji, X. Iron-Based Layered Cathodes for Sodium-Ion Batteries. Batter. Supercaps 2021, 4, 1657–1679. [Google Scholar] [CrossRef]
- Ramke, J.; Evans, J.R.; Habtamu, E.; Mwangi, N.; Silva, J.C.; Swenor, B.K.; Congdon, N.; Faal, H.B.; Foster, A.; Friedman, D.S.; et al. Grand Challenges in global eye health: A global prioritisation process using Delphi method. Lancet Health Longev. 2022, 3, e31–e41. [Google Scholar] [CrossRef]
- Zhang, Y.; Porter, A.L.; Cunningham, S.; Chiavetta, D.; Newman, N. Parallel or Intersecting Lines? Intelligent Bibliometrics for Investigating the Involvement of Data Science in Policy Analysis. IEEE Trans. Eng. Manag. 2020, 68, 1259–1271. [Google Scholar] [CrossRef]
- Chen, Y.; Kang, Y.; Zhao, Y.; Wang, L.; Liu, J.; Li, Y.; Liang, Z.; He, X.; Li, X.; Tavajohi, N.; et al. A review of lithium-ion battery safety concerns: The issues, strategies, and testing standards. J. Energy Chem. 2020, 59, 83–99. [Google Scholar] [CrossRef]
- Sakhnini, J.; Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G. Security aspects of Internet of Things aided smart grids: A bibliometric survey. Internet Things 2019, 14, 100111. [Google Scholar] [CrossRef]
- Kumar, S.; Pandey, N.; Lim, W.M.; Chatterjee, A.N.; Pandey, N. What do we know about transfer pricing? Insights from bibliometric analysis. J. Bus. Res. 2021, 134, 275–287. [Google Scholar] [CrossRef]
- Guo, Y.-M.; Huang, Z.-L.; Guo, J.; Guo, X.-R.; Li, H.; Liu, M.-Y.; Ezzeddine, S.; Nkeli, M.J. A bibliometric analysis and visualization of blockchain. Futur. Gener. Comput. Syst. 2020, 116, 316–332. [Google Scholar] [CrossRef]
- Sithole, S.E.; Thakur, P.; Singh, G. Congestion Control Mechanism on Transport Layer Protocol: Th Application of Terahertz Frequency. Instrum. Mes. Metrol. 2023, 22, 53. [Google Scholar] [CrossRef]
- Kumar, A.; Thakur, P.; Pandit, S.; Singh, G. HSA-SPC: Hybrid Spectrum Access with Spectrum Prediction and Cooperation for Performance Enhancement of Multiuser Cognitive Radio Network. Comput. Networks 2021, 203, 108596. [Google Scholar] [CrossRef]
- Patil, P. Artificial intelligence in cybersecurity. Int. J. Res. Comput. Appl. Robot. 2016, 4, 1–5. [Google Scholar]
- Wirkuttis, N.; Klein, H. Artificial intelligence in cybersecurity. Cyber Intell. Secur. 2017, 1, 103–119. [Google Scholar]
- Das, R.; Sandhane, R. Artificial intelligence in cyber security. J. Phys. Conf. Ser. 2021, 1964, 042072. [Google Scholar] [CrossRef]
- Thomas, M.A. Machine Learning Applications for Cybersecurity. Cyber Def. Rev. 2023, 8, 87–102. [Google Scholar]
- de Azambuja, A.J.G.; Plesker, C.; Schützer, K.; Anderl, R.; Schleich, B.; Almeida, V.R. Artificial Intelligence-Based Cyber Security in the Context of Industry 4.0—A Survey. Electronics 2023, 12, 1920. [Google Scholar] [CrossRef]
- Potula, S.R.; Selvanambi, R.; Karuppiah, M.; Pelusi, D. Artificial Intelligence-Based Cyber Security Applications. In Artificial Intelligence and Cyber Security in Industry 4.0; Springer Nature: Singapore, 2023; pp. 343–373. [Google Scholar]
- Mijwil, M.; Aljanabi, M.; ChatGPT. Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime. Iraqi J. Comput. Sci. Math. 2023, 4, 65–70. [Google Scholar] [CrossRef]
- Ali, A.; Khan, M.A.; Farid, K.; Akbar, S.S.; Ilyas, A.; Ghazal, T.M.; Al Hamadi, H. The Effect of Artificial Intelligence on Cybersecurity. In Proceedings of the 2023 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 7–8 March 2023; pp. 1–7. [Google Scholar]
- Sagar, B.S.; Niranjan, S.; Kashyap, N.; Sachin, D.N. Providing cyber security using artificial intelligence—A survey. In Proceedings of the 2019 3rd international conference on computing methodologies and communication (ICCMC), Erode, India, 27–29 March 2019; pp. 717–720. [Google Scholar]
- Kim, K.; Alshenaifi, I.M.; Ramachandran, S.; Kim, J.; Zia, T.; Almorjan, A. Cybersecurity and Cyber Forensics for Smart Cities: A Comprehensive Literature Review and Survey. Sensors 2023, 23, 3681. [Google Scholar] [CrossRef] [PubMed]
- Alshehri, M. Blockchain-assisted cyber security in medical things using artificial intelligence. Electron. Res. Arch. 2023, 31, 708–728. [Google Scholar] [CrossRef]
- Vijayakumar, K.P.; Pradeep, K.; Balasundaram, A.; Prusty, M.R. Enhanced Cyber Attack Detection Process for Internet of Health Things (IoHT) Devices Using Deep Neural Network. Processes 2023, 11, 1072. [Google Scholar] [CrossRef]
- Abbas, S.; Sampedro, G.A.; Abisado, M.; Almadhor, A.; Yousaf, I.; Hong, S.-P. Harris-Hawk-Optimization-Based Deep Recurrent Neural Network for Securing the Internet of Medical Things. Electronics 2023, 12, 2612. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, H.; Ning, Z.; Guo, L.; Zhang, Y. Blockchain Intelligence for Internet of Vehicles: Challenges and Solutions. IEEE Commun. Surv. Tutorials 2023, 1. [Google Scholar] [CrossRef]
- Shichun, Y.; Zheng, Z.; Bin, M.; Yifan, Z.; Sida, Z.; Mingyan, L.; Yu, L.; Qiangwei, L.; Xinan, Z.; Mengyue, Z.; et al. Essential Technics of Cybersecurity for Intelligent Connected Vehicles: Comprehensive Review and Perspective. IEEE Internet Things J. 2023, 1. [Google Scholar] [CrossRef]
- Yue, W.; Guo, X.; Shen, H. Internet of connected vehicles against cyber-attacks based on resilient adaptive event trigger mechanism control. Trans. Inst. Meas. Control. 2023. [Google Scholar] [CrossRef]
- Ameen, A.H.; Mohammed, M.A.; Rashid, A.N. Dimensions of artificial intelligence techniques, blockchain, and cyber security in the Internet of medical things: Opportunities, challenges, and future directions. J. Intell. Syst. 2023, 32, 20220267. [Google Scholar] [CrossRef]
- Alkatheiri, M.S.; Alghamdi, A.S. Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry. Electronics 2023, 12, 1801. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Hossain, M.S. A privacy-aware framework for detecting cyber attacks on internet of medical things systems using data fusion and quantum deep learning. Inf. Fusion 2023, 99, 101889. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Goyal, S.B.; Bedi, P.; Jan, T.; Whaiduzzaman; Prasad, M. Quantum Machine Learning for Security Assessment in the Internet of Medical Things (IoMT). Futur. Internet 2023, 15, 271. [Google Scholar] [CrossRef]
- Lawu, B.L.; Filbert; Asih, K.; Suharjito; Ohliati, J. A systematic literature review of internet of things cybersecurity. In AIP Conference Proceedings; AIP Publishing: Long Island, NY, USA, 2023; Volume 2594. [Google Scholar] [CrossRef]
- Manogaran, G.; Rawal, B.S.; Saravanan, V.; Kumar, P.M.; Xin, Q.; Shakeel, P.M. Token-based Authorization and Authentication for Secure Internet of Vehicles Communication. ACM Trans. Internet Technol. 2022, 22, 1–20. [Google Scholar] [CrossRef]
- Naseem, S.; Alhudhaif, A.; Anwar, M.; Qureshi, K.N.; Jeon, G. Artificial general intelligence-based rational behavior detection using cognitive correlates for tracking online harms. Pers. Ubiquitous Comput. 2022, 27, 119–137. [Google Scholar] [CrossRef]
- Rjoub, G.; Bentahar, J.; Wahab, O.A.; Mizouni, R.; Song, A.; Cohen, R.; Otrok, H.; Mourad, A. A Survey on Explainable Artificial Intelligence for Cybersecurity. IEEE Trans. Netw. Serv. Manag. 2023, 1. [Google Scholar] [CrossRef]
- Moustafa, N.; Koroniotis, N.; Keshk, M.; Zomaya, A.Y.; Tari, Z. Explainable Intrusion Detection for Cyber Defences in the Internet of Things: Opportunities and Solutions. IEEE Commun. Surv. Tutorials 2023, 1. [Google Scholar] [CrossRef]
- Yang, S.; Tan, J.; Lei, T.; Linares-Barranco, B. Smart traffic navigation system for fault-tolerant edge computing of internet of vehicle in intelligent transportation gateway. IEEE Trans. Intell. Transp. Syst. 2023. [Google Scholar] [CrossRef]
- Singh, G.; Thakur, P. Spectrum Sharing in Cognitive Radio Networks: Towards Highly Connected Environments; John Wiley & Sons: New York, NY, USA, 2021. [Google Scholar]
- Toorani, M. On vulnerabilities of the security association in the IEEE 802.15.6 standard. In Financial Cryptography and Data Security: FC 2015 International Workshops, BITCOIN, WAHC, and Wearable, San Juan, Puerto Rico, 30 January 2015; Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2015; pp. 245–260. [Google Scholar]
- Nwakanma, C.I.; Ahakonye, L.A.C.; Njoku, J.N.; Odirichukwu, J.C.; Okolie, S.A.; Uzondu, C.; Nweke, C.C.N.; Kim, D.-S. Explainable Artificial Intelligence (XAI) for Intrusion Detection and Mitigation in Intelligent Connected Vehicles: A Review. Appl. Sci. 2023, 13, 1252. [Google Scholar] [CrossRef]
- Secinaro, S.; Brescia, V.; Calandra, D.; Biancone, P. Employing bibliometric analysis to identify suitable business models for electric cars. J. Clean. Prod. 2020, 264, 121503. [Google Scholar] [CrossRef]
- Aski, V.J.; Gupta, S.; Sarkar, B. An authentication-centric multi-layered security model for data security in iot-enabled biomedical applications. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 15–18 October 2019; pp. 957–960. [Google Scholar]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and Privacy in Smart Health: Efficient Policy-Hiding Attribute-Based Access Control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Habib, M.A.; Ahmad, M.; Jabbar, S.; Khalid, S.; Chaudhry, J.; Saleem, K.; Rodrigues, J.J.C.; Khalil, M.S. Security and privacy based access control model for internet of connected vehicles. Futur. Gener. Comput. Syst. 2019, 97, 687–696. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.E.; Kim, B.-G.; Gupta, B. Secure integration of IoT and Cloud Computing. Futur. Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Khan, I.A.; Moustafa, N.; Razzak, I.; Tanveer, M.; Pi, D.; Pan, Y.; Ali, B.S. XSRU-IoMT: Explainable simple recurrent units for threat detection in Internet of Medical Things networks. Future Gener. Comput. Syst. 2022, 127, 181–193. [Google Scholar] [CrossRef]
- Almotiri, S.H.; Khan, M.A.; Alghamdi, M.A. Mobile health (m-health) system in the context of IoT. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 39–42. [Google Scholar]
- Newaz, A.I.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. A survey on security and privacy issues in modern healthcare systems: Attacks and defenses. ACM Trans. Comput. Healthc. 2021, 2, 1–44. [Google Scholar] [CrossRef]












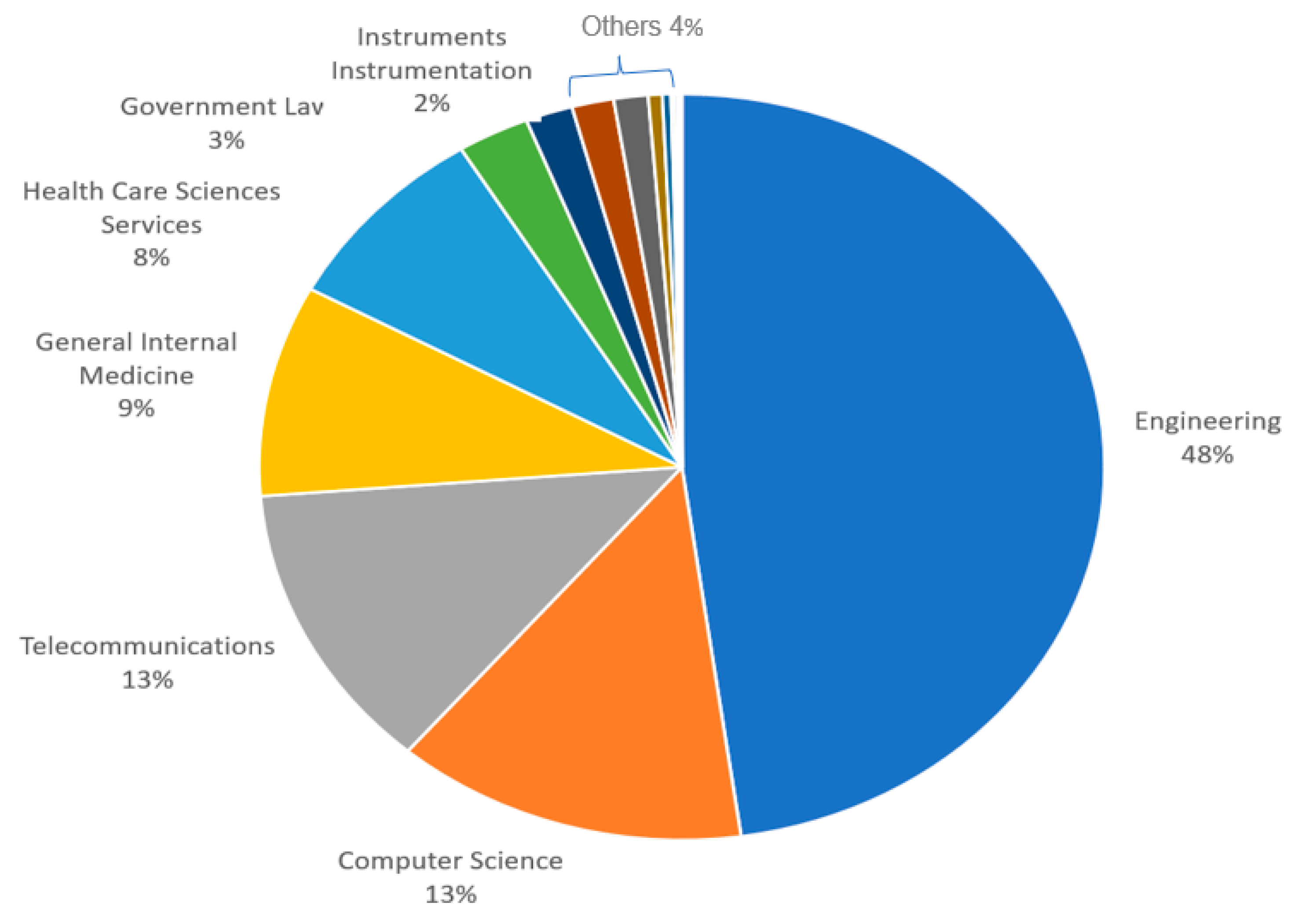







| Keywords | Number of Publications |
|---|---|
| Network Security | 424 |
| Vehicles | 340 |
| Cyber Security | 317 |
| Cybersecurity | 265 |
| Internet of Things | 255 |
| Security | 200 |
| Autonomous Vehicles | 180 |
| Vehicle-To-Vehicle Communications | 171 |
| Computer Crime | 141 |
| Intelligent Systems | 138 |
| Intrusion Detection | 124 |
| Machine Learning | 116 |
| Embedded Systems | 114 |
| Blockchain | 108 |
| Intelligent Vehicle Highway Systems | 105 |
| Citations | Area of Study | Journal | Tools |
|---|---|---|---|
| [53] | Vision, applications, and future challenges of IOT | Emerald Insight | Force Atlas Layout, Gephi and Hitscite, BibExcel |
| [54] | Interaction between AVs and human-driven vehicles, safe and efficient operation of AVs | Sustainability, MDPI | VOSviewer, Biblioshiny |
| [55] | Autonomous vehicles, challenges in sustainable urban mobility | Sustainability, MDPI | VOSviewer |
| [56] | Healthcare and cybersecurity—gaps and opportunities | Journal of Medical Internet Research | Abstrackr, Leximancer, Heat Maps |
| [57] | Advancements in cybersecurity and information systems in healthcare | International Conference on Intelligent Systems, Advanced Computing and Communication | VOSviewer |
| [58] | Blockchain-based Internet of Medical Things | Applied Sciences, MDPI | WordCloud |
| [60] | IOT in healthcare, smart healthcare | Internet of Things | Gephi, BibExcel |
| [61] | Performance improvement with cloud connectivity of IOT-sensed devices and real-time data | South African Institute of Electrical Engineers | WordCloud |
| [62] | Cybersecurity trend analysis | European Journal of Molecular & Clinical Medicine | VOSviewer |
| Review Doc Ref. | Discussed Points | Advantages | Disadvantages |
|---|---|---|---|
| [24] |
|
|
|
| [47] |
|
|
|
| [81] |
|
|
|
| [67] |
|
|
|
| [65] |
|
|
|
| [7] |
|
|
|
| [20] |
|
|
|
| [28] |
|
|
|
| [27] |
|
|
|
| [16] |
|
|
|
| Keyword Type | Database | Keyword Combination |
|---|---|---|
| Primary keywords | Scopus and WOS | “Internet of Vehicles” AND “Cyber Security” OR “Medical Devices” OR “Internet of Medical Things” |
| Secondary keywords | Scopus and WOS | “IOT in Vehicles” OR “IOT in Medical Things” OR “Internet of Things” AND “Security in IOT” AND “Cybersecurity in Medical Things” |
| Technique | Sign | Specimen Instance |
|---|---|---|
| Boolean | AND | All search terms must occur to be retrieved, e.g., Soft Drink AND Cold Drink |
| Boolean | OR | Any one of the search terms must occur to be retrieved, e.g., Soft Drink OR Cold Drink |
| Boolean | NOT | Excludes records that contain a given search term, e.g., Vehicle NOT Heavy. It retrieves documents with the vehicle term that do not include heavy. |
| Proximity | Search for an exact phrase and input the term in quotation marks. The use of quotation marks disables the lemmatisation of terms, e.g., “Cyber Security”. It shows documents related to the Cyber Security term only. | |
| Truncation | $ | Search for zero or more characters in between letters, e.g., hono$r = honor, honour |
| Truncation | ** | Search for zero or more characters in suffix/prefix, e.g., *form* = formation, form, transform, inform |
| Truncation | ? | Search for one character only in between letters, e.g., gre?t = great, greet |
| Regions | Max Publication Country-Wise | Countries with Highly Cited Papers | Country-Wise Highly Cited Publications |
|---|---|---|---|
| USA | 571 | China | 56 |
| China | 179 | India | 8 |
| United Kingdom | 139 | Australia | 8 |
| India | 123 | Canada | 6 |
| Italy | 111 | Turkey | 4 |
| Canada | 95 | Singapore | 2 |
| Germany | 89 | USA | 2 |
| France | 73 | Iran | 2 |
| Netherlands | 68 | Turkey | 2 |
| South Korea | 67 | Norway | 2 |
| One-Sample t-Test | |||
|---|---|---|---|
| t | df | p | |
| Max Publications Country-wise | 2.02 | 9 | 0.07 |
| Highly Cited Publications Country-wise | 1.75 | 9 | 0.12 |
| Descriptive Statistics | ||||
|---|---|---|---|---|
| Stats | Max Publications Country-Wise | Highly Cited Publications Country-Wise | Nation-States | Highly Cited Papers Nation-States |
| Valid | 10 | 10 | 10 | 10 |
| Mode | 5.00 | 1.00 | ||
| Median | 5.00 | 1.50 | ||
| Mean | 13.50 | 4.60 | ||
| Std. Deviation | 21.06 | 8.31 | ||
| Skewness | 2.89 | 3.03 | ||
| Std. Error of Skewness | 0.68 | 0.68 | ||
| Minimum | 3.00 | 1.00 | ||
| Maximum | 72.00 | 28.00 | ||
| 25th Percentile | 4.25 | 1.00 | ||
| 50th Percentile | 5.00 | 1.50 | ||
| 75th Percentile | 12.75 | 3.75 | ||
| S.No | Publication Year | Publication Title | Authors | Journal Title | Cited by |
|---|---|---|---|---|---|
| 1. | 2018 | Secure Integration of IoT and Cloud Computing | Stergiou, C., et al. | Future Generation Computer Systems | 739 |
| 2. | 2018 | Survey on Multi-Access Edge Computing for Internet of Things Realization | Porambage, P., et al. | IEEE Communications Surveys and Tutorials | 411 |
| 3. | 2020 | Deep learning for cyber security intrusion detection: Approaches, datasets, and comparative study | Ferrag, M.A., et al. | Journal of Information Security and Applications | 405 |
| 4. | 2020 | A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security | Al-Garadi, M.A., et al. | IEEE Communications Surveys and Tutorials | 383 |
| 5. | 2016 | Autonomous vehicles: challenges, opportunities, and future implications for transportation policies. | Bagloee, S.A., et al. | Journal of Modern Transportation | 356 |
| 6. | 2019 | A survey of machine learning techniques applied to software-defined networking (SDN): Research issues and challenges | Xie, J., et al. | IEEE Communications Surveys and Tutorials | 341 |
| 7. | 2020 | A Survey on the Internet of Things (IoT) Forensics: Challenges, Approaches, and Open Issues | Stoyanova, M., et al. | IEEE Communications Surveys and Tutorials | 301 |
| 8. | 2020 | Thirty Years of Machine Learning: The Road to Pareto-Optimal Wireless Networks | Wang, J., et al. | IEEE Communications Surveys and Tutorials | 296 |
| 9. | 2016 | An overview of Fog computing and its security issues | Stojmenovic, I., et al. | Concurrency and Computation: Practice and Experience | 285 |
| 10. | 2018 | The Blockchain as a Decentralized Security Framework [Future Directions] | Puthal, D., et al. | IEEE Consumer Electronics Magazine | 273 |
| 11. | 2017 | Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges | Parkinson, S., et al. | IEEE Transactions on Intelligent Transportation System | 261 |
| 12. | 2017 | Fog of Everything: Energy-Efficient Networked Computing Architectures, Research Challenges, and a Case Study | Baccarelli, E., et al. | IEEE Access | 249 |
| 13. | 2017 | A Survey on Smart Grid Cyber-Physical System Testbeds | Cintuglu, M.H., et al. | IEEE Communications Surveys and Tutorials | 247 |
| 14. | 2017 | Fog computing security: a review of current applications and security solutions | Khan, S., et al. | Journal of Cloud Computing | 240 |
| 15. | 2017 | From Cloud to Fog Computing: A Review and a Conceptual Live VM Migration Framework | Osanaiye, O., et al. | IEEE Access | 234 |
| S.No. | Publication Year | Publication Title | Authors | Journal Title | Cited By |
|---|---|---|---|---|---|
| 1. | 2017 | A Survey on Security and Privacy Issues in Internet-of-Things | Yang, Y.C., et al. | IEEE Internet of Things Journal | 572 |
| 2. | 2017 | Cyber-Physical Systems Security-A Survey | Humayed, A., et al. | IEEE Internet of Things Journal | 390 |
| 3. | 2017 | Cost Efficient Resource Management in Fog Computing Supported Medical Cyber-Physical System | Gu, L., et al. | IEEE Transactions on Emerging Topics in Computing | 240 |
| 4. | 2019 | What are the respiratory effects of e-cigarettes? | Gotts, J.E., et al. | BMJ-British Medical Journal | 236 |
| 5. | 2020 | An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture | Priya, R.M.S., et al. | Computer Communications | 172 |
| 6. | 2018 | Internet of Medical Things: A Review of Recent Contributions Dealing with Cyber-Physical Systems in Medicine | Gatouillat, A., et al. | IEEE Internet of Things Journal | 145 |
| 7. | 2017 | Industry Sponsorship and research outcome | Lundh, A., et al. | Cochrane Database of Systematic Reviews | 127 |
| 8. | 2018 | PrivacyProtector: Privacy-Protected Patient Data Collection in IoT-Based Healthcare Systems | Luo, E.T., et al. | IEEE Communications Magazine | 125 |
| 9. | 2017 | A Review of In-Body Biotelemetry Devices: Implantables, Ingestibles, and Injectables | Kiourti, A. and Nikita, K.S. | IEEE Transactions on Biomedical Transactions on Biomedical Engineering | 120 |
| 10. | 2016 | IDEAL-D: a rational framework for evaluating and regulating the use of medical devices | Sedrakyan, A., et al. | BMJ-British Medical Journal | 120 |
| 11. | 2020 | Intelligence in the Internet of Medical Things era: A systematic review of current and future trends | Al-Turjman, F., et al. | Computer Communications | 101 |
| 12. | 2016 | A Triple-Loop Inductive Power Transmission System for Biomedical Application | Lee, B., et al. | IEEE Transactions on Biomedical Circuits & Systems | 85 |
| 13. | 2016 | A survey on actuators-driven surgical robots | Le, HM., et al. | Sensors And Actuators a Physical | 84 |
| 14. | 2016 | Security Tradeoffs in Cyber Physical Systems: A Case Study Survey on Implantable Medical Devices | Altawy, H and Youssef, AM | IEEE Access | 71 |
| 15. | 2019 | Security and Privacy for the Internet of Medical Things Enabled Healthcare Systems: A Survey | Sun, YN, et al. | IEEE Access | 69 |
| IOMV Layer | Types of Potential Cyber-Attacks at Each IOMV Layer |
|---|---|
| Network and Servers | • Man in the middle • Session Hijacking • IP Spoofing • Replay • Eavesdropping • Man in the Browser • Buffer Overflow • Mobileware • Ransomware • DoS—denial of service • DDoS—Distributed Denial of Service |
| IVN | • TCP SYN flood attack • Teardrop attack • Smurf attack • Ping of death attack • Spoofing • ARP—Spoofing • DNS Tunnelling • DNS Hijacking • DNS Spoofing/Poisoning • Cross-Site Scripting Attack • URL Manipulation • Birthday Attack |
| Network devices | • Phishing |
| Physical | • Physical Tampering • Malicious code introduction through HMI devices like USBs |
| IOMV devices | • Encryption Attacks • Privilege Escalation • Brute-Force Password Attack • Credential Stuffing • Password Spraying • Dictionary Attack • Malvertising • DDoS Botnets • Cryptojacking |
| Software/firmware | • Firmware Hijacking • Botnets • Malware • Code Injection Attacks • Cross-Site Scripting (XSS) • Malvertising • SQL Injection • Malicious Node Injection • Drive-By Attacks (like legit software; fake software; fake warning messages and update prompts; links; spammy websites; drive-by download attacks) • Spyware Attacks • Zero-day exploits |
| Common attacks irrespective of IOMV layers | • Identity-Based • IOT-Based Attacks • Supply Chain Attacks • Insider Threats • Social Engineering • Illustrative cyber-attacks—(like Mirai Botnet; Verkada Hack (Network and Device); Cold in Finland (DDoS); Jeep Hack (Firmware); Stuxnet (IOT attack)) |
Severity
 | ||||||
Likelihood | Severity | Low (1) | Medium (2) | High (3) | Critical (4) | |
| Likelihood | ||||||
| Impossible (1) (Risk Unlikely to Occur) | x11 Low | x12 Medium | x13 Medium | x14 High | ||
| Possible (2) (Risk Might Occur) | x21 Low | x22 Medium | x23 High | x24 Critical | ||
| Probably (3) (Risk Will Occur) | x31 Medium | x32 High | x33 High | x34 Critical | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bhukya, C.R.; Thakur, P.; Mudhivarthi, B.R.; Singh, G. Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives. Sensors 2023, 23, 8107. https://doi.org/10.3390/s23198107
Bhukya CR, Thakur P, Mudhivarthi BR, Singh G. Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives. Sensors. 2023; 23(19):8107. https://doi.org/10.3390/s23198107
Chicago/Turabian StyleBhukya, Chidambar Rao, Prabhat Thakur, Bhavesh Raju Mudhivarthi, and Ghanshyam Singh. 2023. "Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives" Sensors 23, no. 19: 8107. https://doi.org/10.3390/s23198107
APA StyleBhukya, C. R., Thakur, P., Mudhivarthi, B. R., & Singh, G. (2023). Cybersecurity in Internet of Medical Vehicles: State-of-the-Art Analysis, Research Challenges and Future Perspectives. Sensors, 23(19), 8107. https://doi.org/10.3390/s23198107







