Governance of a Blockchain-Enabled IoT Ecosystem: A Variable Geometry Approach
Abstract
:1. Introduction
1.1. IoT Applications
1.2. Blockchain and IoT Inclusion
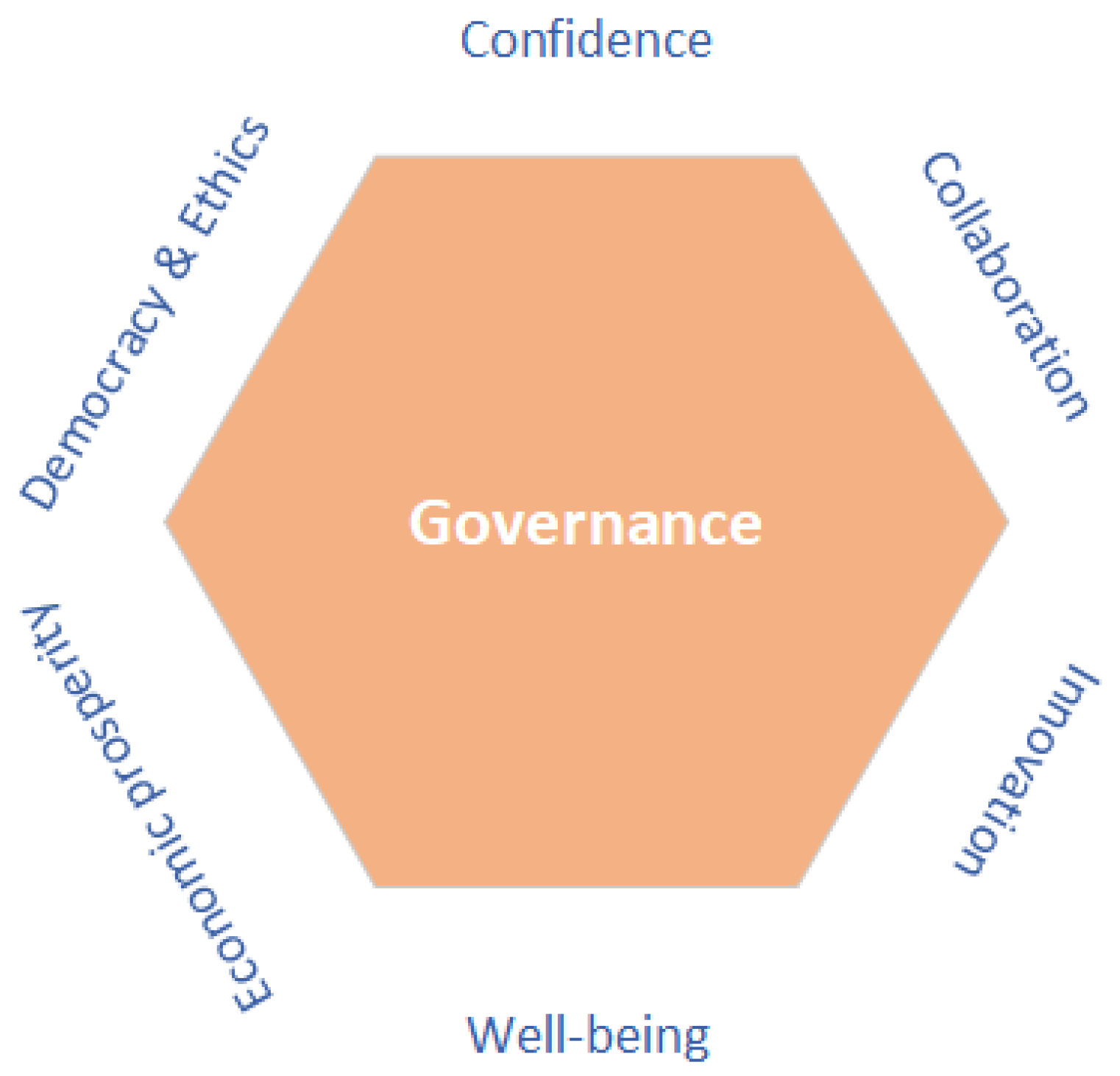
1.3. Governance
2. IoT Architectures and Reference Model
2.1. Perception Layer
Roles and Objectives
2.2. Network Layer
Roles and Objectives
2.3. Blockchain Layer
Roles and Objectives
2.4. Middleware Layer
Roles and Objectives
2.5. Application Layer
Roles and Objectives
2.6. Business Layer
Roles and Objectives
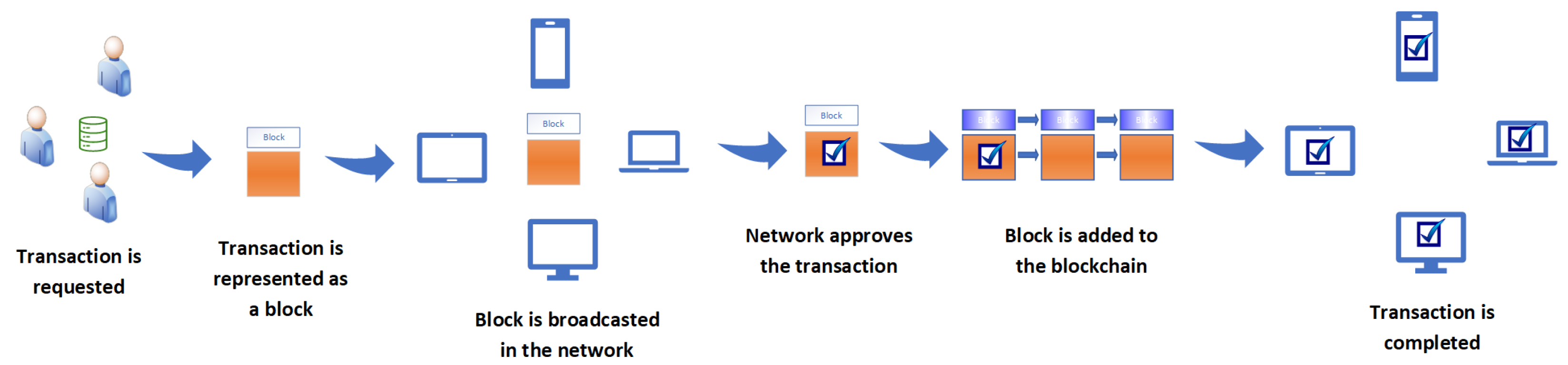
3. Blockchain
- Public key cryptography can be used to communicate with the blockchain. Users are identified by their public keys, and their private keys can be used to digitally sign transactions.
- In a peer-to-peer network, a peer generates digitally signed transactions that contain the transfer of funds.
- The signed transactions are broadcast over the peer-to-peer network.
- Neighboring peers validate the transactions and spread the transactions across the entire network.
- Miners form blocks of the validated transactions.
- Blocks are broadcast over the network.
- The nodes verify and validate the blocks, and validated blocks are added to the ledger.
- Eventually, transactions are executed.
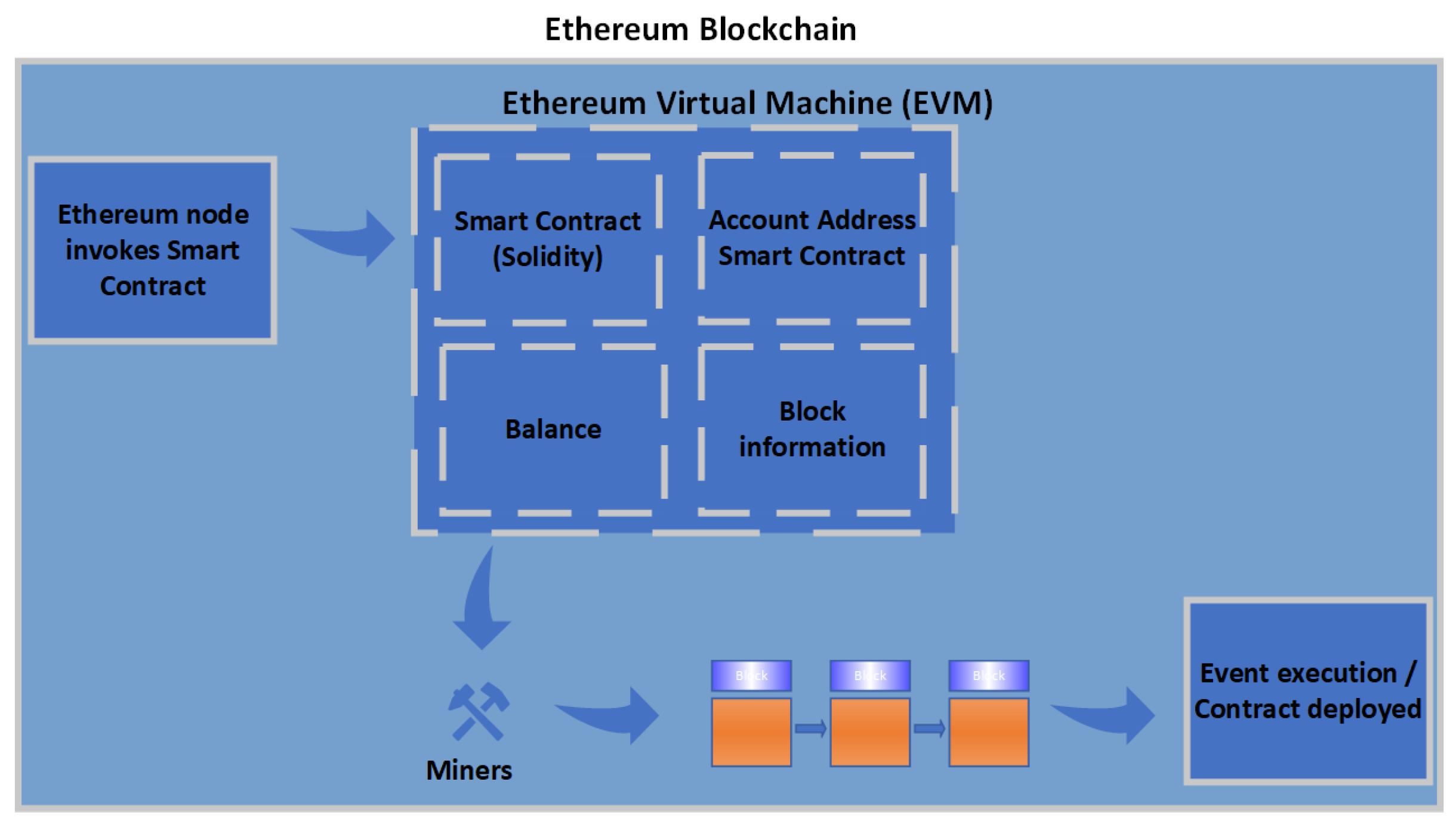
3.1. The Mechanics of Smart Contracts
3.2. Role of Blockchain in Governance
4. Related Works
4.1. IoT Governance
4.2. Role of Blockchain as Governance Mechanism
4.3. Governance for Blockchain
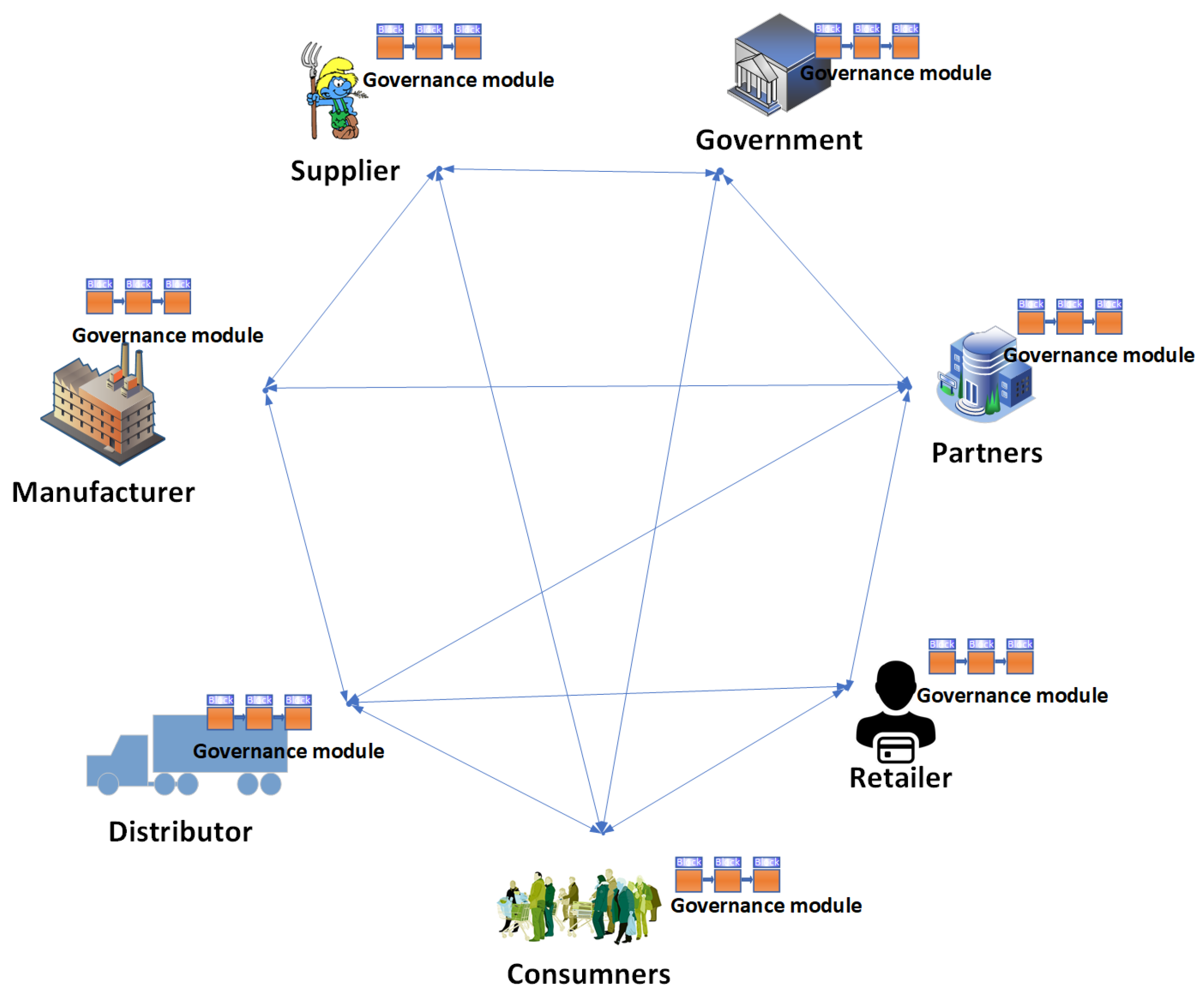
5. Blockchain-IoT Governance
5.1. Variable Geometry Approach
- The top-down approach, a centralized approach where a single entity manages all the other entities.
- The bottom-up approach, where multiple entities are involved in the decision-making process. Top-down and bottom-up approaches are unsuitable for complex scenarios [8].
- The variable geometry approach, a multi-level approach that is a combination of multiple mechanisms. It is a broader approach and is thus appropriate for complex [8] and heterogeneous scenarios. Complex scenarios include multiple stakeholders, varying interests, and diverse application domains where certain partners may adhere to the overall obligations while other partners may adhere to selective obligations. This mechanism is less restrictive and can potentially enhance cooperation among regional and international partners. It provides flexibility during the negotiation process [110]. We propose a variable geometry approach to implement the governance requirements.
- Common agreements are applied as pre-conditions to each partner to achieve the fundamental interests of each partner and the collective aim of the consortium. For instance, all the partners agree on privacy and security requirements.
- Private agreements are agreed upon among partners while forming channels to provide certain services. Multiple stand-alone agreements can be signed, where every contracting party is free to join any agreement they want. For instance, certain partners can agree among themselves on a specific cost model for a service.
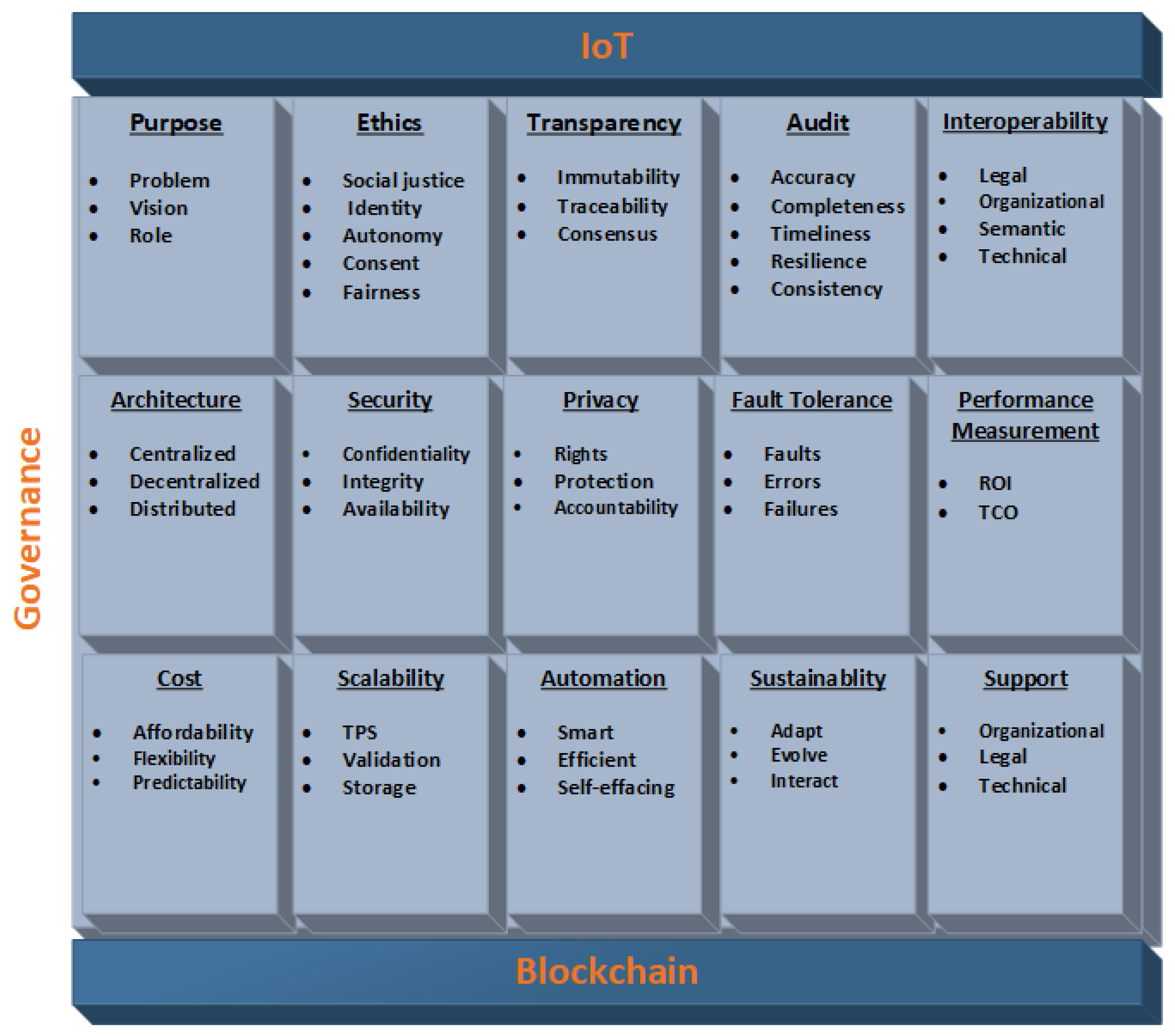
5.2. Proposed Governance Framework
5.2.1. Purpose
5.2.2. Ethics
5.2.3. Transparency
5.2.4. Audit
- Accuracy: Assesses the controls.
- Completeness: Are the controls adequate, are there gaps, and are the controls applied thoroughly.
- Timeliness: The controls are executed on time.
- Resilience: The controls are resilient to failures and there are backups if the primary controls fail.
- Consistency: The primary and secondary controls are correctly in place.
5.2.5. Interoperability
5.2.6. Architecture
5.2.7. Security
5.2.8. Privacy
5.2.9. Fault Tolerance
5.2.10. Performance Measurement
5.2.11. Cost
5.2.12. Scalability
5.2.13. Automation
5.2.14. Sustainability
5.2.15. Support
6. Proposed Governance Framework Use Cases and Evaluation
6.1. Smart Logistics Use Case
6.2. Proposed Governance Framework Evaluation
7. Conclusions
8. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Almeida, V.A.F.; Doneda, D.; Monteiro, M. Governance Challenges for the Internet of Things. IEEE Internet Comput. 2015, 19, 56–59. [Google Scholar] [CrossRef]
- Ullah, I.; Meratnia, N.; Havinga, P.J.M. Entropy as a Service: A Lightweight Random Number Generator for Decentralized IoT Applications. In Proceedings of the 2020 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Austin, TX, USA, 23–27 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Al-Ruithe, M.; Mthunzi, S.; Benkhelifa, E. Data governance for security in IoT & cloud converged environments. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Copie, A.; Fortis, T.; Munteanu, V.I.; Negru, V. From Cloud Governance to IoT Governance. In Proceedings of the 2013 27th International Conference on Advanced Information Networking and Applications Workshops, Barcelona, Spain, 25–28 March 2013; pp. 1229–1234. [Google Scholar] [CrossRef]
- Ullah, I.; Meratnia, N.; Havinga, P.J.M. iMAC: Implicit Message Authentication Code for IoT Devices. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Gerber, A.; Kansal, S. Defining Your IoT Governance Practices. 7 August 2017. Available online: https://developer.ibm.com/technologies/iot/articles/iot-governance-01/ (accessed on 3 November 2023).
- Kazmi, A.; Serrano, M.; Lenis, A. Smart Governance of Heterogeneous Internet of Things for Smart Cities. In Proceedings of the 2018 12th International Conference on Sensing Technology (ICST), Limerick, Ireland, 4–6 December 2018; pp. 58–64. [Google Scholar] [CrossRef]
- de Bossey, C. Report of the Working Group on Internet Governance. June 2005, p. 4. Available online: http://www.wgig.org/docs/WGIGREPORT.pdf (accessed on 3 November 2023).
- Weber, R. Governance of the Internet of Things—From Infancy to First Attempts of Implementation? Laws 2016, 5, 28. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the internet of things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Atzori, M. Blockchain Technology and Decentralized Governance: Is the State Still Necessary? University College of London: London, UK,, 2016. [Google Scholar] [CrossRef]
- Tasca, P.; Tessone, C. Taxonomy of Blockchain Technologies. Principles of Identification and Classification (Unpublished Manuscript). 2018. Available online: https://papers.ssrn.com/abstract=2977811 (accessed on 3 November 2023).
- Ahmad, R.W.; Salah, K.; Jayaraman, R.; Yaqoob, I.; Ellahham, S.; Omar, M. The role of blockchain technology in telehealth and telemedicine. Int. J. Med. Informatics 2021, 148, 104399, ISSN 1386-5056. [Google Scholar] [CrossRef]
- Auer, S.; Nagler, S.; Mazumdar, S.; Mukkamala, R.R. Towards blockchain-IoT based shared mobility: Car-sharing and leasing as a case study. J. Netw. Comput. Appl. 2022, 200, 103316, ISSN 1084-8045. [Google Scholar] [CrossRef]
- Ahmed, I.; Zhang, Y.; Jeon, G.; Lin, W.; Khosravi, M.R.; Qi, L. A blockchain-and artificial intelligence-enabled smart IoT framework for sustainable city. Int. J. Intell. Syst. 37 2022, 37, 6493–6507. [Google Scholar] [CrossRef]
- Omar, I.A.; Debe, M.; Jayaraman, R.; Salah, K.; Omar, M.; Arshad, J. Blockchain-based Supply Chain Traceability for COVID-19 personal protective equipment. Comput. Ind. Eng. 2022, 167, 107995, ISSN 0360-8352. [Google Scholar] [CrossRef]
- Ahmad, S.; Saxena, C. Internet of Things and Blockchain Technologies in the Insurance Sector. In Proceedings of the 2022 3rd International Conference on Computing, Analytics and Networks (ICAN), Rajpura, Punjab, India, 18–19 November 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Cole, R.; Stevenson, M.; Aitken, J. Blockchain technology: Implications for operations and supply chain management. Supply Chain Manag. 2019, 24, 469–483. [Google Scholar] [CrossRef]
- IBM (2018a) AIG, IBM, Standard Chartered Deliver First Multinational Insurance Policy Powered by Blockchain. Available online: https://www-03.ibm.com/press/us/en/pressrelease/52607.wss (accessed on 25 March 2020).
- Nayak, N.; Nguyen, D.T. Blockchain, AI and robotics: How Future Tech Will Simplify Federal Procurement. 2018. Available online: https://www.federaltimes.com/acquisition/2018/03/23/blockchain-ai-and-robotics-how-future-tech-will-simplify-federal-procurement/ (accessed on 25 March 2020).
- Lumineau, F.; Wang, W.; Schilke, O. Blockchain Governance—A New Way of Organizing Collaborations? Organ. Sci. 2021, 32, 257–525. [Google Scholar] [CrossRef]
- CBInsights (2020) Investment to Blockchain Startups Slips in 2019. Available online: https://www.cbinsights.com/research/blockchain-investment-trends-2019/ (accessed on 25 March 2020).
- van Pelt, R.; Jansen, S.; Baars, D.; Overbeek, S. Defining Blockchain Governance: A Framework for Analysis and Comparison. Inf. Syst. Manag. 2021, 38, 21–41. [Google Scholar] [CrossRef]
- Hacker, P. Corporate governance for complex cryptocurrencies? A framework for stability and decision making in blockchain-based organizations. In Regulating Blockchain: Techno-Social and Legal Challenges; Hacker, P., Lianos, I., Dimitropoulos, G., Eich, S., Eds.; Oxford University Press: Oxford, UK, 2017; pp. 40–166. [Google Scholar]
- Rennock, M.; Cohn, A.; Butcher, J. Blockchain Technology and Regulatory Investigations (Tech. Rep.). Steptoe Johnson LLP. 2018. Available online: https://www.steptoe.com/images/content/1/7/v2/171967/LIT-FebMar18-Feature-Blockchain.pdf (accessed on 3 November 2023).
- Beck, R.; Müller-Bloch, C.; King, J.L. Governance in the blockchain economy: A framework and research agenda. J. Assoc. Inf. Syst. 2018, 19, 1020–1034. [Google Scholar] [CrossRef]
- Phanse, K. Data Governance Using SAP MDM-Part 1. 2008. Available online: https://archive.sap.com/kmuuid2/60022998-5d17-2b10-dbaa-8e3ab357fa55/Data%20Governance%20using%20SAP%20Master%20Data%20Management%20-%20Part%201.pdf (accessed on 3 November 2023).
- Furness, A. Internet of Things (IoT) European Research Cluster Activity Chain. International Framework for IoT Structure and Governance. (CASAGRAS2 Deliverable 4.1—A Specification of Rules and Procedures for Governance). 27 September 2011. Available online: https://docbox.etsi.org/zArchive/TISPAN/Open/IoT/20111028IERC-IoT-STD-Poznan/CASAGRAS2%20Establishing%20an%20International%20Framework%20for%20Structure%20&%20Governance%20v2.pdf (accessed on 4 March 2022).
- Worldwide Governance Indicators. Available online: https://datacatalog.worldbank.org/dataset/worldwide-governance-indicators (accessed on 18 January 2021).
- A Conceptual Framework for Data Governance in IoT-Enabled Digital IS Ecosystems. Available online: https://www.scitepress.org/Papers/2019/79243/79243.pdf (accessed on 23 January 2021).
- Merkus, J. Data Governance Maturity Model. MSc Master’s Thesis, Open Universiteit Nederland, Valkenburgerweg, The Netherland, 2015. [Google Scholar]
- General Data Protection Regulation (GDPR). 2018. Available online: https://gdpr-info.eu/ (accessed on 3 November 2023).
- Friedman, T.; Judah, S. Data Risks in the Internet of Things Demand Extensive Information Governance. 30 June 2016. Available online: https://www.gartner.com/en/documents/3362117/data-risks-in-the-internet-of-things-demand-extensive-in (accessed on 7 March 2022).
- Weber, R.H. Internet of things—Governance quo vadis? Comput. Law Secur. Rev. 2013, 29, 341–347, ISSN 0267-3649. [Google Scholar] [CrossRef]
- Esposito De Falco, S.; Cucari, N.; Canuti, E.; Modena, S. Corporate governance and blockchain: Some preliminary results by a survey. In Proceedings of the Corporate Governance: Search for the Advanced Practices, Rome, Italy, 28 February 2019. [Google Scholar] [CrossRef]
- Rafael, Z.; Geetha, P.; Gianluca, M.; Gerhard, S. Examining Gentle Rivalry: Decision-Making in Blockchain Systems. In Proceedings of the 52nd Hawaii International Conference on System Sciences (HICSS 2019), Maui, Hawaii, 8–13 January 2019. [Google Scholar]
- Williamson, O.E. Markets and Hierarchies: Analysis and Antitrust Implications: A Study in the Economics of Internal Organization; Social Science Research Network: Rochester, NY, USA, 1975; SSRN Scholarly Paper ID 1496220. [Google Scholar]
- Powell, W.W. Neither Market Nor Hierarchy. Res. Organ. Behav. 1990, 12, 295–336. [Google Scholar]
- Fukuyama, F. What Is Governance? Governance 2013, 26, 347–368. [Google Scholar] [CrossRef]
- Ch, G.D.S.; Hervas, C.; Estevez, E.; Marrone, L. High-Level IoT Governance Model Proposal for Digitized Ecosystems. In Proceedings of the 2019 International Conference on Information Systems and Software Technologies (ICI2ST), Quito, Ecuador, 13–15 November 2019; pp. 79–84. [Google Scholar] [CrossRef]
- Kooiman, J. Social-Political Governance. Public Manag. Int. J. Res. Theory 1999, 1, 67–92. [Google Scholar] [CrossRef]
- Joint Task Force Transformation Initiative. SP 800-53 Rev. 4. April 2013. Available online: https://csrc.nist.gov/publications/detail/sp/800-53/rev-4/final (accessed on 3 November 2023).
- O’Flaherty, K. Marriott Faces $123 Million Fine For 2018 Mega-Breach. 2019. Available online: https://www.forbes.com/sites/kateoflahertyuk/2019/07/09/marriott-faces-gdpr-fine-of-123-million/ (accessed on 3 November 2023).
- Lewis, B. ISO/IEC 27000-Key international Standard for Information Security Revised. Available online: https://www.iso.org/news/ref2266.html (accessed on 3 November 2023).
- ISO/IEC 30141:2018(en) Internet of Things (loT)—Reference Architecture. Available online: https://www.iso.org/obp/ui/fr/#iso:std:iso-iec:30141:ed-1:v1:en (accessed on 3 November 2023).
- ISO/IEC 27001:2022 Information Security, Cybersecurity and Privacy Protection Information Security Management Systems Requirements. 2022. Available online: https://www.iso.org/standard/27001 (accessed on 3 November 2023).
- ISO/IEC 27018:2019. Information Technology-Security Techniques-Code of Practice for Protection of Personally Identifiable Information (PII) in Public Clouds Acting as PII Processors. Available online: https://www.iso.org/standard/76559.html (accessed on 3 November 2023).
- ISO/IEC 27017:2015. Information Technology—Security Techniques—Code of Practice for Information Security Controls Based on ISO/IEC 27002 for Cloud Services. Available online: https://www.iso.org/standard/43757.html (accessed on 3 November 2023).
- Royal Netherlands Standardization Institute. NEN Netherlands. Available online: https://www.iso.org/member/2027.html (accessed on 3 November 2023).
- Alvestrand, H.T. Internet Engineering Task Force (IETF—Mission statement— RFC3935, 2004). Available online: https://rfc-editor.org/rfc/rfc3935.txt (accessed on 3 November 2023).
- Kleinwachter, W. Final Report of the EU IOT Task Force on IOT Governance. Summary. Brussels. 14 November 2012. Available online: http://ec.europa.eu/information_society/newsroom/cf/dae/document.cfm?doc_id=1748 (accessed on 3 November 2023).
- van Deventer, O.; Brewster, C.; Everts, M. Governance and Business Models of Blockchain Technologies and Networks (Tech. Rep. No. 776936). TNO. 2017. Available online: https://repository.tudelft.nl/view/tno/uuid:a593f6d3-6c67-4fb1-908b-4ac7662b9b7f (accessed on 3 November 2023).
- Naden, C. Reference Framework for the Internet of Things. 2018. Available online: https://www.iso.org/news/ref2340.html (accessed on 3 November 2023).
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Zhu, L.; Gai, K.; Li, M. Blockchain Technology in Internet of Things; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Kumar, N.M.; Mallick, P.K. The Internet of Things: Insights into the building blocks, component interactions, and architecture layers. Procedia Comput. Sci. 2018, 132, 109–117, ISSN 1877-0509. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Kim, B.-S.; Khan, B. IoT Elements, Layered Architectures and Security Issues: A Comprehensive Survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [PubMed]
- Hany, A.; Gary, W. IoT Security, Privacy, Safety and Ethics. In Digital Twin Technologies and Smart Cities; Springer Nature: Cham, Switzerland, 2019; pp. 1–27. [Google Scholar] [CrossRef]
- Xu, J.J. Are blockchains immune to all malicious attacks? Financ. Innov. 2016, 2, 25. [Google Scholar] [CrossRef]
- Ullah, I.; de Roode, G.; Meratnia, N.; Havinga, P. Threat Modeling—How to Visualize Attacks on IOTA? Sensors 2021, 21, 1834. [Google Scholar] [CrossRef]
- Brady, M.A.; Ullah, I.; Havinga, P.J.M. DOSing Distributed Ledger Technology: IOTA. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021; pp. 55–61. [Google Scholar] [CrossRef]
- Nofer, M.; Gomber, P.; Hinz, O.; Schiereck, D. Blockchain. Bus Inf. Syst. Eng. 2017, 59, 183–187. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentl, A. Decentralizing privacy: Using blockchain to protect personal data. In Security and Privacy Workshops (SPW); IEEE: Piscataway, NJ, USA, 2015; pp. 180–184. [Google Scholar]
- Yaga, D.; Mell, P.; Roby, N.; Scarfone, K. Blockchain Technology Overview; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [CrossRef]
- Swanson, T. Consensus-as-a-Service: A Brief Report on the Emergence of Permissioned, Distributed Ledger Systems. 2015. Available online: http://www.ofnumbers.com/wp-content/uploads/2015/04/Permissioned-distributed-ledgers.pdf (accessed on 3 November 2023).
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. Special Section on the Plethora of Research in Internet of Things (IoT). IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Announcing the Secure Hash Standard. Federal Information Processing Standards Publication 180-2 2002. Available online: http://csrc.nist.gov/publications/fips/fips180-2/fips180-2.pdf (accessed on 3 November 2023).
- Percival, C. Tarsnap—The Scrypt Key Derivation Function and Encryption Utility. Available online: http://www.tarsnap.com/scrypt.html (accessed on 15 March 2016).
- Aumasson, J.-P.; Henzen, L.; Meier, W.; Phan, R.C.W. SHA-3 Proposal BLAKE. Available online: https://131002.net/blake/blake.pdf (accessed on 16 December 2010).
- Sukhwani, H.; Martínez, J.M.; Chang, X.; Trivedi, K.S.; Rindos, A. Performance Modeling of PBFT Consensus Process for Permissioned Blockchain Network (Hyperledger Fabric). In Proceedings of the 2017 IEEE 36th Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26–29 September 2017; pp. 253–255. [Google Scholar] [CrossRef]
- Hyperledger. Available online: https://www.hyperledger.org/ (accessed on 3 November 2023).
- Skh Saad, S.M.; Raja Mohd Radzi, R.Z. Comparative Review of the Blockchain Consensus Algorithm Between Proof of Stake (POS) and Delegated Proof of Stake (DPOS). Int. J. Innov. Comput. 2020, 10. [Google Scholar] [CrossRef]
- Chen, L.; Xu, L.; Shah, N.; Gao, Z.; Lu, Y.; Shi, W. On Security Analysis of Proof-of-Elapsed-Time (PoET). In Stabilization, Safety, and Security of Distributed Systems; Spirakis, P., Tsigas, P., Eds.; SSS 2017. Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017; Volume 10616. [Google Scholar] [CrossRef]
- Zhang, C.; Wu, C.; Wang, X. Overview of Blockchain Consensus Mechanism. In Proceedings of the 2020 2nd International Conference on Big Data Engineering (BDE 2020), Shanghai, China, 29–31 May 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 7–12. [Google Scholar] [CrossRef]
- Sun, F. UTXO vs Account/Balance Model. Available online: https://medium.com/@sunflora98/utxo-vs-account-balance-model-5e6470f4e0cf (accessed on 9 August 2018).
- Governance of and with Blockchain. a Thematic Report Prepared by the European Union Blockchain Observatory & Forum. Available online: https://www.eublockchainforum.eu/sites/default/files/reports/report_governance_v1.0_0.pdf (accessed on 3 November 2023).
- Van der Elst, C.; Lafarre, A. Blockchain and Smart Contracting for the Shareholder Community. Eur. Bus. Organ. Law Rev. 2019, 20. [Google Scholar] [CrossRef]
- Arizona Revised Statutes Title 44-Trade and Commerce § 44-7061 Signatures and Records Secured through Blockchain Technology; Smart Contracts; Ownership of Information; Definitions. 2017. Available online: https://law.justia.com/codes/arizona/2017/title-44/section-44-7061/ (accessed on 3 November 2023).
- Blockchain Enabling-Vermont Laws. 12 V.S.A. § 1913 (2017). Available online: https://legislature.vermont.gov/statutes/section/12/081/01913 (accessed on 3 November 2023).
- Satoshi, N. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 3 November 2023).
- Ethereum. Available online: https://ethereum.org/ (accessed on 3 November 2023).
- XRP: The Best Digital Asset for Global Payments. Available online: https://ripple.com/xrp/ (accessed on 3 November 2023).
- Bigchaindb. Available online: https://www.bigchaindb.com (accessed on 3 November 2023).
- Corda. Available online: https://www.corda.net (accessed on 3 November 2023).
- Quorum Whitepaper v0.1.pdf. Available online: https://github.com/jpmorganchase/quorum-docs/blob/master/Quorum%20Whitepaper%20v0.1.pdf (accessed on 3 November 2023).
- Tezos. Available online: https://www.tezos.com/ (accessed on 3 November 2023).
- Multichain. Available online: https://www.multichain.com (accessed on 3 November 2023).
- Hashgraph. Available online: https://www.hedera.com/ (accessed on 3 November 2023).
- IOTA. Available online: https://www.iota.org/ (accessed on 3 November 2023).
- R3. Available online: https://www.r3.com/ (accessed on 3 November 2023).
- Peters, G.W.; Panayi, E. Understanding Modern Banking Ledgers through Blockchain Technologies: Future of Transaction Processing and Smart Contracts on the Internet of Money. arXiv 2015, arXiv:1511.05740. [Google Scholar] [CrossRef]
- Szabo, N. Smart Contracts. 1994. Available online: http://szabo.best.vwh.net/smart.contracts.html (accessed on 3 November 2023).
- Mell, P.; Kelsey, J.; Shook, J. Cryptocurrency Smart Contracts for Distributed Consensus of Public Randomness. In Proceedings of the Stabilization, Safety, and Security of Distributed Systems: 19th International Symposium, SSS 2017, Boston, MA, USA, 5–8 November 2017. [Google Scholar] [CrossRef]
- Alexander, B.; Groer, I. Profiles in Innovation: Blockchain: Putting Theory into Practice. 2016. Available online: https://api.semanticscholar.org/CorpusID:211082114 (accessed on 3 November 2023).
- The Ethereum Virtual Machine. Available online: https://fullstacks.org/materials/ethereumbook/14_evm.html (accessed on 3 November 2023).
- Okhuysen, G.A.; Bechky, B.A. Coordination in organizations: An integrative perspective. Acad. Management Ann. 2009, 3, 463–502. [Google Scholar] [CrossRef]
- Kim, H.; Laskowski, M. A Perspective on Blockchain Smart Contracts: Reducing Uncertainty and Complexity in Value Exchange; Poellabauer, C., Abdelzaher, T., Shen, H., Eds.; Institute of Electrical and Electronics Engineers: Lowell, MA, USA, 2017; pp. 1–6. [Google Scholar]
- Azure IoT. Available online: https://azure.microsoft.com/en-us/overview/iot/ (accessed on 3 November 2023).
- Watson IoT Platform. Available online: https://www.ibm.com/cloud/watson-iot-platform (accessed on 3 November 2023).
- Xively. Available online: https://xively.com/ (accessed on 3 November 2023).
- IoTivity. Available online: https://iotivity.org/ (accessed on 3 November 2023).
- Thingsquare. Available online: https://www.thingsquare.com/ (accessed on 3 November 2023).
- Qi, R.; Feng, C.; Liu, Z.; Mrad, N. Blockchain-Powered Internet of Things, E-Governance and E-Democracy. In E-Democracy for Smart Cities; Springer: Berlin/Heidelberg, Germany, 2017; pp. 509–520. ISBN 978-981-10-4034-4. [Google Scholar] [CrossRef]
- Directive (EU) 2017/828 of the European PARLIAMENT and of the Council of 17 May 2017 Amending Directive 2007/36/EC as Regards the Encouragement of Long-Term Shareholder Engagement [2017] OJ L132/60. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32017L0828 (accessed on 23 April 2022).
- Steemit, J.S.B. Steem Moved to Limit His Power, CoinDesk, 24 February 2020, and Inside the Crypto World’s Biggest Scandal, Wired Magazine, 19 June 2018. Available online: https://www.coindesk.com/tech/2020/02/24/justin-sun-bought-steemit-steem-moved-to-limit-his-power/ (accessed on 6 April 2022).
- Finck, M. Blockchain governance. In Blockchain Regulation and Governance in Europe; Elcograf, G.B., Ed.; Cambridge University Press: Cambridge, UK, 2019; pp. 182–209. [Google Scholar]
- Ziolkowski, R.; Parangi, G.; Miscione, G.; Schwabe, G. Examining gentle rivalry: Decisionmaking in blockchain systems. In Proceedings of the 52nd Annual Hawaii International Conference on System Science HICSS, Maui, HI, USA, 8–11 January 2019; pp. 1–10. [Google Scholar]
- Peter, L. The Variable Geometry Approach to International Economic Integration. In Proceedings of the Seventh APEF Conference, Iran, 3–5 November 2008; University of Melbourne: Melbourne, Australia, 2008. [Google Scholar]
- Cornford, A. Variable Geometry for the WTO: Concept and Precedents; UNCTAD Discussion Papers No. 171; United Nations Conference on Trade and Development: Geneva, Switzerland, 2004. [Google Scholar]
- Farrach, C.H.; Pettinato, L. The Role of Fault Tolerance for Blockchain. The Beacon Group Technology Practice. Available online: https://static1.squarespace.com/static/59b80e154c0dbfd18f2fe92d/t/5bae720ff4e1fc4c51de81c5/1538159124018/The+Role+of+Fault+Tolerance+for+Blockchain.pdf (accessed on 3 November 2023).
- van den Hoven, J. European Commission, Internet of Things. Factsheet Ethics Version 4.0. Available online: https://ec.europa.eu/digital-single-market/en/news/conclusions-internet-things-public-consultation (accessed on 3 November 2023).
- Wimmer, M.A.; Boneva, R.; di Giacomo, D. Interoperability governance: A definition and insights from case studies in Europe. In Proceedings of the 19th Annual International Conference on Digital Government Research: Governance in the Data Age (dg.o ’18), Delft, The Netherlands, 30 May–1 June 2018; Association for Computing Machinery: New York, NY, USA, 2018. Article 14. pp. 1–11. [Google Scholar] [CrossRef]
- What is Personal Data? Available online: https://ec.europa.eu/info/law/law-topic/data-protection/reform/what-personal-data_en (accessed on 3 November 2023).
- What Personal Data Is Considered Sensitive? Available online: https://ec.europa.eu/info/law/law-topic/data-protection/reform/rules-business-and-organisations/legal-grounds-processing-data/sensitive-data/what-personal-data-considered-sensitive_en (accessed on 3 November 2023).
- Directive 95/46/EC of the European Parliament and of the Council. 1995. Available online: https://eur-lex.europa.eu/eli/dir/1995/46/oj (accessed on 3 November 2023).
- Directive 2009/136/EC of the European Parliament and of the Council. 2009. Available online: https://eur-lex.europa.eu/eli/dir/2009/136/oj (accessed on 3 November 2023).
- Bernabe, J.B.; Canovas, J.L.; Hernandez-Ramos, J.L.; Moreno, R.T.; Skarmeta, A. Privacy-Preserving Solutions for Blockchain: Review and Challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Why Data Privacy Is Much More than Compliance. Build Trust to Help Grow Your Business. Available online: https://www.ibm.com\/security/digital-assets/data-privacy-matters/ (accessed on 3 November 2023).
- de Haro-Olmo, F.; Varela-Vaca, Á.; Álvarez-Bermejo, J. Blockchain from the Perspective of Privacy and Anonymisation: A Systematic Literature Review. Sensors 2020, 20, 7171. [Google Scholar] [CrossRef] [PubMed]
- Jain, S. Fault Tolerance in Distributed Systems. Distributed Systems (CSE-510). Lecture Notes. 2014. Available online: https://www.slideshare.net/sumitjain2013/fault-tolerance-in-distributed-systems (accessed on 5 May 2022).
- Storm, C. Fault Tolerance in Distributed Computing. In Specification and Analytical Evaluation of Heterogeneous Dynamic Quorum-Based Data Replication Schemes; Vieweg+Teubner Verlag: Berlin, Germany, 2012. [Google Scholar] [CrossRef]
- Podgorelec, B.; Keršič, V.; Turkanović, M. Analysis of Fault Tolerance in Permissioned Blockchain Networks. In Proceedings of the 2019 XXVII International Conference on Information, Communication and Automation Technologies (ICAT), Sarajevo, Bosnia and Herzegovina, 20–23 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Bakshi, S. Performance Measurement Metrics for IT Governance. 1 November 2016. Available online: https://www.isaca.org/resources/isaca-journal/issues/2016/volume-6/performance-measurement-metrics-for-it-governance (accessed on 3 November 2023).
- Grembergen, W.V.; Haes, S.D. Measuring and Improving IT Governance Through the Balanced Scorecard. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.469.7541&rep=rep1&type=pdf (accessed on 3 November 2023).
- Balasubramanian, S.; Bhattacharya, S.; Krishnan, V.V. Pricing Information Goods: A Strategic Analysis of the Selling and Pay-per-Use Mechanisms. Mark. Sci. 2015, 34, 218–234. [Google Scholar] [CrossRef]
- Fishburn, P.; Odlyzko, A. Competitive pricing of information goods: Subscription pricing versus pay-per-use. Econ. Theory 1999, 13, 447–470. [Google Scholar] [CrossRef]
- Hazari, S.S.; Mahmoud, Q. A Parallel Proof of Work to Improve Transaction Speed and Scalability in Blockchain Systems. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 916–921. [Google Scholar] [CrossRef]
- How Visa Protects Your Data; Fast Company: New York, NY, USA, 2018; Available online: https://www.fastcompany.com/1784751/how-visa-protects-your-data (accessed on 3 November 2018).
- Xavier, B.; Christopher, C.; Thomas, H. Blockchain-Free Cryptocurrencies. A Rational Framework for Truly Decentralised Fast Transactions. Inf. Syst. 2016, 871, 45–90. [Google Scholar]
- Paula, J. Timothy.Bishop@oecd.org Blockchain Technologies as a Digital Enabler for Sustainable Infrastructure. Available online: https://www.oecd.org/finance/Blockchain-technologies-as-a-digital-enabler-for-sustainable-infrastructure-key-findings.pdf (accessed on 3 November 2023).
- Rana, R.L.; Giungato, P.; Tarabella, A.; Tricase, C. Blockchain Applications and Sustainability Issues. Amfiteatru Econ. 2019, 21, 861. [Google Scholar] [CrossRef]
- Schinckus, C. The good, the bad and the ugly: An overview of the sustainability of blockchain technology. Energy Res. Soc. Sci. 2020, 69, 101614, ISSN 2214-6296. [Google Scholar] [CrossRef]
- Ali, S. Sustainable blockchain through proof of exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Manzano, P.G. Customer Satisfaction Measurement: Strategies, Methodologies and Factors Influencing Customer Satisfaction Measures; Universitat Oberta de Catalunya (UOC): Barcelona, Spain, 2021; Available online: http://hdl.handle.net/10609/131866 (accessed on 3 November 2023).
- Solidity by Example. Voting. Available online: https://docs.soliditylang.org/en/v0.4.11/solidity-by-example.html (accessed on 3 November 2023).





| Requirement | Off-Chain | On-Chain |
|---|---|---|
| Purpose | ✓ | ✓ |
| Ethics | ✓ | ✓ |
| Transparency | - | ✓ |
| Audit | ✓ | ✓ |
| Interoperability | ✓ | ✓ |
| Architecture | ✓ | ✓ |
| Security | ✓ | ✓ |
| Privacy | - | ✓ |
| Fault tolerance | - | ✓ |
| Performance measurement | ✓ | - |
| Cost | ✓ | ✓ |
| Scalability | - | ✓ |
| Automation | - | ✓ |
| Sustainability | - | ✓ |
| Support | ✓ | ✓ |
| Component | Specifications (Raspberry Pi 4) | Specifications (Raspberry Pi 4) |
|---|---|---|
| Model | Model B | Model B |
| Processor | Broadcom 2711, Cortex-A-72, 64-bit SoC @ 1.5 GHz | Broadcom 2711, quad-core Cortex-A72, 64-bit SoC @ 1.5 GHz |
| Internal Working Memory (RAM) | 4 GB | 8 GB |
| SD card support | Micro SD card (operating system and data storage) | Micro SD card (operating system and data storage) |
| SD card size (capacity) | 64 GB | 128 GB |
| Connectivity | (a) 2.4 GHz and 5 GHz IEEE 802.11.b/g/n/ac wireless LAN (b) Bluetooth 5.0, BLE (c) Gigabit Ethernet | (a) 2.4 GHz and 5.0 GHz IEEE 802.11b/g/n/ac wireless LAN (b) Bluetooth 5.0, BLE (c) Gigabit Ethernet |
| Operating system | Raspbian | Raspbian |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah, I.; Havinga, P.J.M. Governance of a Blockchain-Enabled IoT Ecosystem: A Variable Geometry Approach. Sensors 2023, 23, 9031. https://doi.org/10.3390/s23229031
Ullah I, Havinga PJM. Governance of a Blockchain-Enabled IoT Ecosystem: A Variable Geometry Approach. Sensors. 2023; 23(22):9031. https://doi.org/10.3390/s23229031
Chicago/Turabian StyleUllah, Ikram, and Paul J. M. Havinga. 2023. "Governance of a Blockchain-Enabled IoT Ecosystem: A Variable Geometry Approach" Sensors 23, no. 22: 9031. https://doi.org/10.3390/s23229031
APA StyleUllah, I., & Havinga, P. J. M. (2023). Governance of a Blockchain-Enabled IoT Ecosystem: A Variable Geometry Approach. Sensors, 23(22), 9031. https://doi.org/10.3390/s23229031







