1. Introduction
In recent years, with the increase in the number of smart mobile devices and the popularization of cloud computing technologies, mobile cloud computing (MCC) as a novel computing paradigm has received extensive attention and significant development [
1]. A mobile user can use resource-limited mobile devices to subscribe to and access the remote cloud computing services from different types of service providers (SPs), e.g., Netflix, Apple Music, and Amazon cloud drive [
2]. The distributed locations of SPs enable subscribers to access the resources efficiently and conveniently [
3]. However, the MCC environment possesses the characteristics of openness and complexity since it is dependent on insecure wireless technology [
4]. Hence, to protect the interests of users and SPs, it is essential to provide vital security assurances, especially authentication and authorization [
5]. In addition, the quantum-safe authentication protocol for mobile devices has recently been proposed to resist quantum computer attacks [
6].
The openness of wireless communication causes the data transmitted between mobile users and SPs to be easy to maliciously intercept and modify [
7]. The attacker is likely to impersonate a legitimate mobile user or SP to steal benefits. Thus, authentication has been widely applied to assist users and SPs to identify each other [
8,
9,
10,
11,
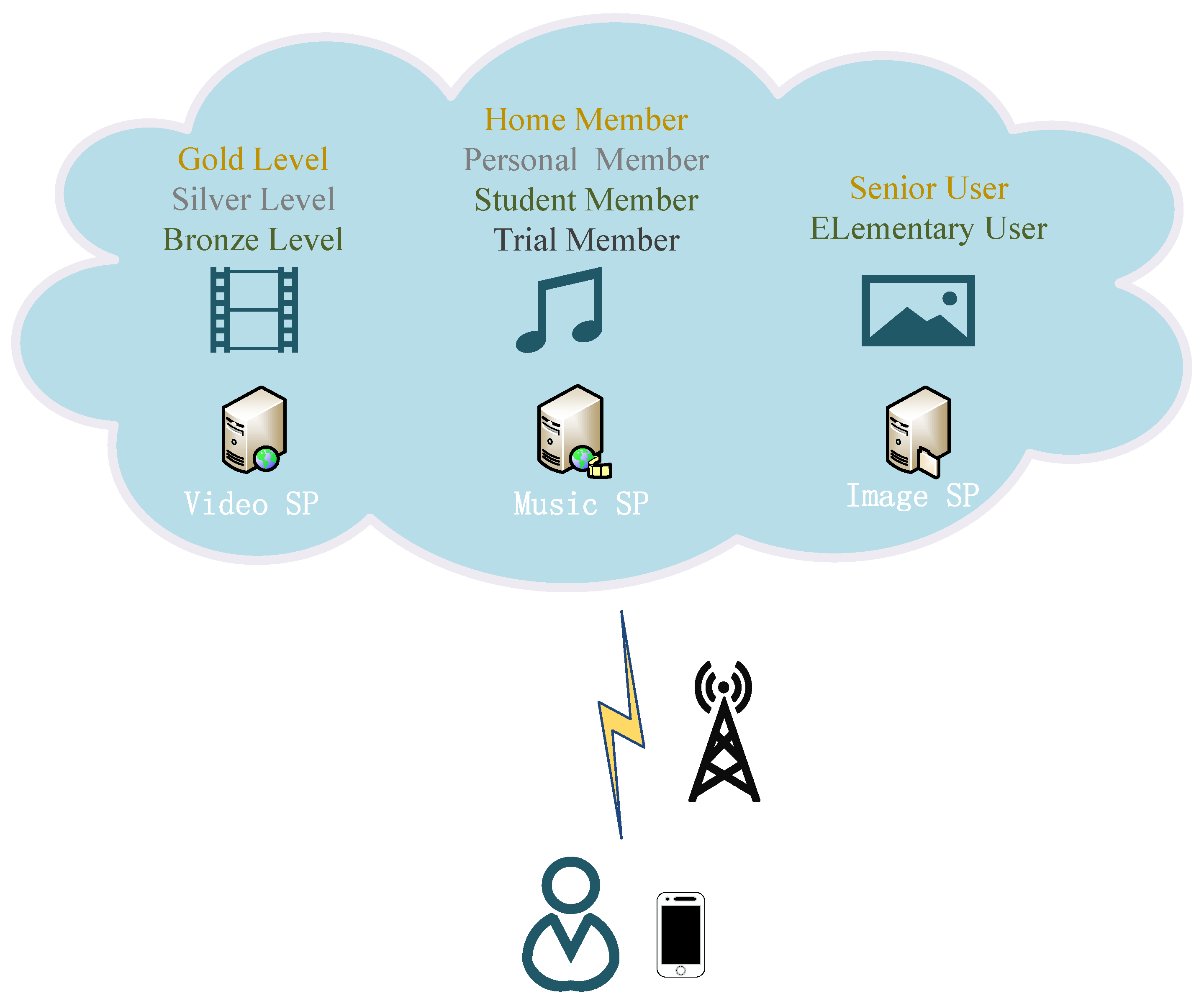
12]. In addition, a kind of cloud service is usually divided into several levels, e.g., ‘Bronze’, ‘Silver’, and ‘Gold’, to satisfy the different subscription demands of users [
13,
14]. Authorization is essential for SPs to determine the access privilege levels of users as they use a hierarchical cloud service [
15]. For example, as shown in
Figure 1, a mobile user subscribes to a ‘Silver’ level of cloud video service from a video SP. When this user accesses the video SP to use the service, the video SP verifies the user’s identity and provides a ‘Silver’-level service based on the user’s access privilege. Therefore, authentication and authorization compose an indispensable security component, i.e., access control, preventing malicious adversaries from accessing resources and low-level users from accessing higher-level services [
16].
Mobile users can subscribe to new types of services or update their service levels anytime and anywhere in the distributed MCC environment. However, when a user intends to subscribe to multiple different types of hierarchical services, the user usually needs to register on different SPs and maintain corresponding credentials inconveniently, e.g., accounts, private keys, or passwords. Instead, it is more convenient for users to use only one certificate to access hierarchical services from different SPs. This security requirement is called single registration [
17]. The obstacle to single registration is that there is generally no trust relationship among isolated SPs to manage user registration information jointly [
18].
In addition to introducing a trusted third party, blockchain is an effective technology for establishing a trust relationship in the distributed environment [
19]. The distributed trust is assured by the immutability of the blockchain, as well as automatic and transparent smart contracts [
20]. Therefore, blockchain is widely used in access control schemes for distributed scenarios, e.g., information-centric networking (ICN) [
21] and Internet of Things (IoT) [
22]. Moreover, there are usually two types of access control designs. One is where a subject (requester) sends a transaction to trigger the smart contract deploying the access policy in order to access resources [
23,
24,
25]. This method is not effective enough for the MCC scenarios since the blockchain needs to store the enormous number of resource-access transactions submitted by mobile users. Another promising approach is where a subject’s access privilege is stored in the transaction for the object (resource) owner to make authorization decisions when the subject accesses resources [
26,
27,
28,
29]. This method is more suitable for the MCC scenarios, since it avoids the mobile user submitting frequent access requests to the blockchain.
1.1. Motivation and Contributions
Single registration has been widely considered in multi-server authentication schemes. Some centralized multi-server authentication and authorization schemes, using a registration center (RC), also inherit this advantage [
9,
15]. However, all users and SPs need to fully trust the RC, leading to expensive trust costs and single-point failure [
12,
30,
31]. In the distributed MCC hierarchical service scenarios, we believe that achieving single registration without a trusted third party has the following characteristic: a mobile user just needs to register on an arbitrarily selected SP once and can subscribe to hierarchical services on other SPs concurrently; then, the mobile user can use one credential to access multiple SPs to use services with different levels. In order to make this idea work, the following three security issues need to be considered: (1) when a mobile user registers, identity forgery should be prevented; (2) the mobile user’s subscription request should be checked in a trusted way, and not by the user’s selected registration SP; (3) subscription fees paid by a mobile user belonging to other SPs cannot be embezzled by the selected registration SP. This paper uses the non-interactive zero-knowledge (NIZK) proof of knowledge and blockchain technology to solve the above issues: (1) the registration SP verifies NIZK proof of knowledge to confirm the validity of user identities; (2) the smart contract checks the user’s subscription request and decides whether to complete the registration; (3) other SPs ask for their deserved fees from the selected registration SP based on the tamper-proof distributed ledger. In these ways, all SPs trust that a mobile user registered on an arbitrary SP is also their legitimate subscription user, enabling the single registration.
Using blockchain to design an authentication and authorization scheme possesses the advantages of a low trust cost and single-point-of-failure resistance. However, it is also faces some issues, especially storage overhead [
32,
33]. In other distributed scenarios, generally, an object owner generates a transaction to record a subject’s access privilege [
26,
27,
28,
29]. Afterwards, the object or owner make access control decisions by reading the authorization transaction. However, when a subject requests access privileges from multiple object owners, it means that multiple transactions are required to be stored in blockchain, since each transaction only loads one authorization relationship between a subject and an object owner. A subject’s multiple authorization transactions aggravate the storage burden of the blockchain. Especially in the MCC scenarios, it is hard to ignore the blockchain storage pressure caused by a numerous number of mobile users and SPs. Therefore, the proposed scheme consolidates multiple authorization relationships between a mobile user (subject) and multiple SPs (object owners) into one transaction. In this way, when a user registers, even if there is a large number of SPs, the different access privileges of a mobile user only need to be stored in one transaction. This reduces the storage overhead of blockchain and improves the system scalability.
In practical applications, user access privileges updates should be considered for user convenience. This enables mobile users to subscribe to new levels of hierarchical services at any time. User access privileges updates, in our scheme, can follow the feature of the registration phase: a mobile user can update access privilege levels on multiple SPs at once, and all updated access privileges only need to be stored in one transaction. However, it requires two additional considerations. First, mobile users should not pay repeatedly when updating their unexpired access privileges. In other words, mobile users can inherit the service time that has not been used up before. Second, the immutability of the blockchain makes it impossible to delete and modify privileges, causing mobile users to reuse previously expired privileges, i.e., double-spending attack [
34]. The proposed scheme uses the smart contract deploying flexible update strategies and the world state to solve the above two issues, respectively [
35]. The contributions of this work are mainly summarized as follows:
This paper proposes a blockchain-based authentication and authorization scheme for distributed mobile cloud services that enables the mobile user to access different SPs with different access levels by using the same identity and credential. In addition, the mobile user just needs to register on an arbitrary SP once to apply for access privileges from different SPs with the participation of the smart contract.
Each time a mobile user registers or updates, only one transaction needs to be stored in blockchain to record the user’s access privileges on multiple SPs. The detailed theoretical and experimental analysis indicates that the proposed scheme alleviates the storage burdens on the blockchain and provides scalability when the number of SPs and users increases.
The proposed scheme utilizes the smart contract to achieve efficient and flexible user access privilege updates, and uses the world state to resist the double-spending attack. We implemented the smart contract algorithms for the registration phase and update phase on Hyperledger Fabric.
1.2. Organization
The rest of this paper is organized as follows.
Section 2 reviews the related works.
Section 3 describes the system model and security model.
Section 4 explains the system building block of the blockchain and the transaction structure. In
Section 5, we present the details of our proposed scheme. We perform the smart contract experiment in
Section 6.
Section 7 demonstrates the security analysis of our proposed scheme. The performance analysis is introduced in
Section 8.
Section 9 discusses our work in depth. And
Section 10 summarizes our work and prospects for future work.
The abbreviations and symbols used in this paper are defined in
Table 1.
4. System Building Blocks
This section will introduce zero-knowledge proof of knowledge, Hyperledger Fabric, the transaction process, the structure of transactions, the service subscription list, and the smart contracts in our scheme.
4.1. Zero-Knowledge Proof of Knowledge
In a zero-knowledge proof of knowledge (ZkPoK) protocol [
39], a prover can convince a verifier that a statement is true, and the verifier only learns the validity of the statement (without disclosing much else). Following the notation in [
40,
41], let
indicate a ZkPoK protocol that proves the knowledge of
such that
. The ZkPoK protocol is able to be transformed into being noninteractive by using the Fiat–Shamir heuristics [
42].
4.2. Hyperledger Fabric
The proposed scheme uses Hyperledger Fabric, or Fabric for short. Fabric focuses on the distributed storage of data in ledgers, which is different from other cryptocurrency blockchain platforms. The smart contract, also called chaincode in Fabric, implements the application logic of the modification, writing, and check, and Fabric deploys a key-value database to store the world state that is the most recent value of transactions. In addition, a modular membership service provider (MSP) used in Fabric makes it more convenient to manage the access rights of organizations. MSP also issues credentials and manages the identities of all nodes in the organizations. The organizations that are joined into the blockchain can own four types of nodes with different functions (
,
,
, and
) [
35]. The structure of Fabric is shown in
Figure 3.
4.3. Transaction Process
The transaction process is shown in the
Figure 3. The SP invokes CLI or SDK (
) to upload the transaction to the
on the blockchain. Each
calls the smart contract to check the correctness of the transaction content, which checks the payment of mobile users in our scheme, and then returns the signed endorsement result to the
. After collecting enough endorsements, the
submits the transaction to the
node. Then, the
node executes a consensus algorithm, e.g., RAFT [
43], to pack the received transactions into blocks, and
broadcasts blocks to
nodes that store these blocks. The latest transactions are stored in a key-value database, which can be queried by an SP using the keyword immediately.
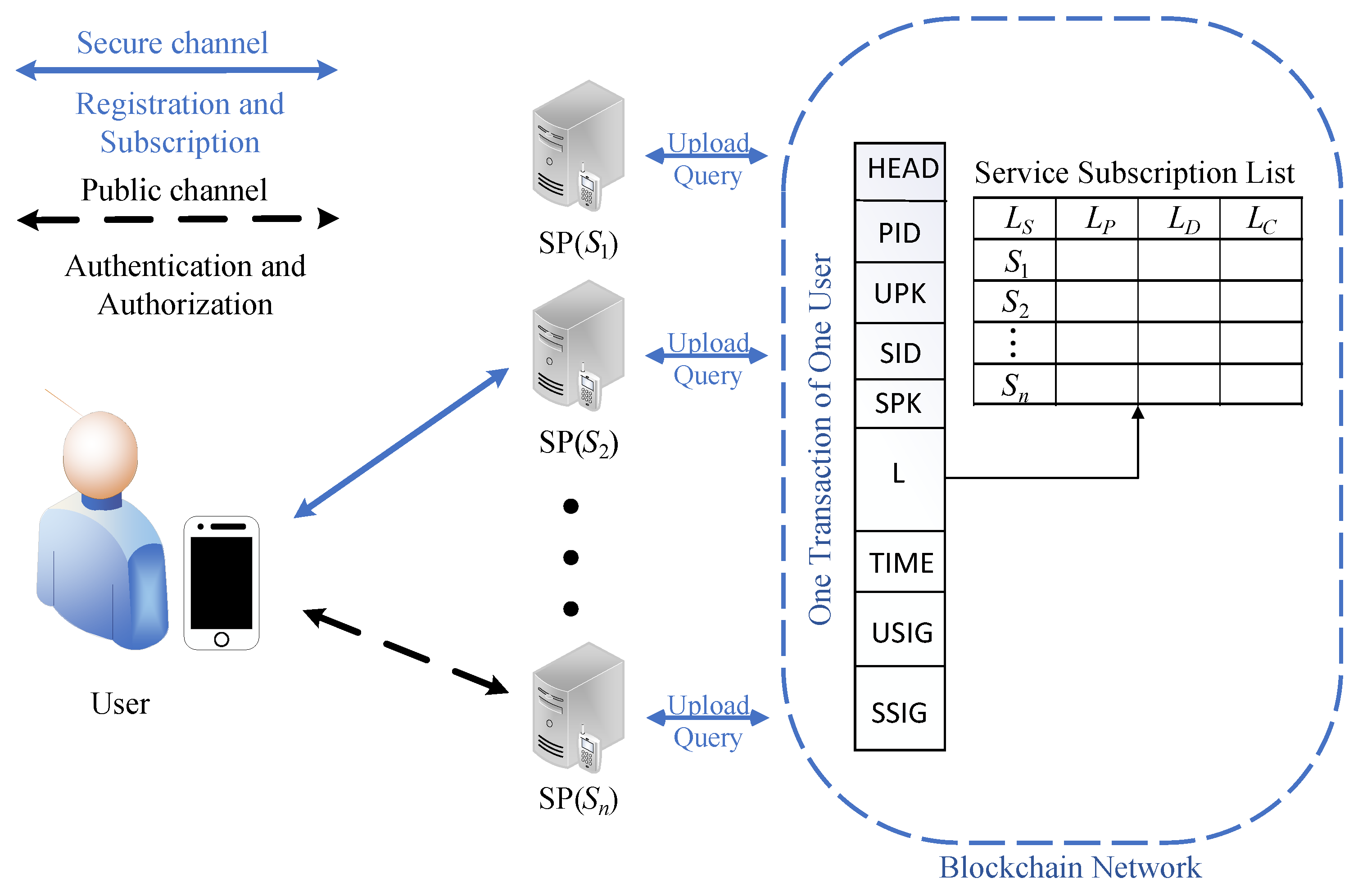
4.4. Transaction Structure
To reduce the number of transactions, a transaction needs to record a user’s identity information and subscription information on multiple SPs. A flexible transaction structure was used in our scheme, which is similar to the tabular structured ledger [
44,
45]. In this way, a transaction records the authorization relationships between a user and multiple SPs. The abstract structure and data structure in the transaction are shown in
Figure 2 and Algorithm 1 separately.
PID: symbolizes pseudonyms of mobile users.
UPK: symbolizes public keys of mobile users.
SID: symbolizes the identity of an SP who accepts the mobile user’s registration information.
SPK: symbolizes the public key of the acceptance SP.
L: symbolizes the service subscription list, which includes four arrays: , , , and .
TIME: symbolizes the user’s registration and update time.
USIG: symbolizes the user’s signature value of the registration information sent to the acceptance SP.
SSIG: symbolizes the acceptance SP’s the signature value of the information sent to the blockchain.
| Algorithm 1 _ |
- 1:
Struct User public { - 2:
JSON:PID; - 3:
JSON:UPK; - 4:
JSON:SID; - 5:
JSON:SPK; - 6:
JSON:CSP; - 7:
JSON:Privilege; - 8:
JSON:Day; - 9:
JSON:Cost; - 10:
T JSON:TIME; - 11:
JSON:USIG; - 12:
JSON:SSIG; - 13:
}%The data structure in the transaction. - 14:
var User = ; - 15:
Storing the initialization transaction in the blockchain; - 16:
return;
|
4.5. Service Subscription List
In our proposed scheme,
is a service subscription list that is used to provide hierarchical access control and subscription during the authentication, registration, and update phase. The detailed structure of
L is illustrated in
Table 2.
The entry
in
Table 2 is explained as follows.
subscribes to a service with the level of
on
for
days used, and costs the service fee
.
Assume that there are j existing SPs and n-j unjoined SPs. = [,...,,...,] is an array of all SPs.
is a non-negative integer array that indicates the user’s access privileges on all SPs. In , the access privileges published on the website are mapped onto non-negative integers. For instance, the levels [] represent the access privileges separately. In addition, represents the access privilege of the user on .
is a non-negative array that indicates the days where intends to use the privilege service on all SPs. Furthermore, represents the number of days where the user uses the privilege service on .
is a non-negative integer array that indicates service fees for all privilege services paid by . Moreover, the service fee that pays to is (unit price for a day of privilege service can be found on the website of ).
Furthermore, it is flexible for the new SP to join our system. The sub-array [] indicates the unjoined new SPs, whose values in , and are all initialized to 0. After a new SP is added to the MCC system, can use the trial privilege service of the new SP, even if the user is not registered on it. However, as wants to access higher privilege services on the new SP, the mobile user must update their access privileges.
4.6. Smart Contracts in Our Scheme
Our scheme uses four smart contract algorithms, namely Init_Ledger(), Check_
registration&subscription(),
Read(), and
Check_user_update() in Algorithms 1–4. Algorithm 1
Init_Ledger() is called only once when deploying the smart contract. Algorithm 2 is called to check the validity of user registration and subscription information. Algorithm 3 is called to read the most recent value of transactions (world state) from the blockchain. Algorithm 4 is called to check the validity of the user access privilege update.
| Algorithm 2 Check_registration&subscription() |
- 1:
var U User = ; - 2:
Take out the latest transaction about key from key-value database to check the uniqueness of user identity. - 3:
ifthen - 4:
return Error(“user is registered"); - 5:
end if - 6:
Take out the service subscription list L from U. - 7:
fordo %Traverse all SPs in L - 8:
is one-day unit price of the access privilege [j] on ; - 9:
[j]; - 10:
if [j] then - 11:
return Error(“L is not correct or user did not pay enough"); - 12:
end if - 13:
end for%Finishing checking user subscription information. - 14:
Storing the transaction U in the blockchain. - 15:
Finishing user registration and subscription. - 16:
return Success(“Mobile user is successfully registered !");
|
| Algorithm 3 Read() |
- 1:
var User = Get_WorldState(); - 2:
%The key-value database stores the world state, which is the last transaction data about the key . - 3:
if == then - 4:
return, fmt.Errorf(“ is not in the blockchain”); - 5:
end if - 6:
return;
|
| Algorithm 4 Check_user_update() |
| Check user update |
- 1:
var N User = ; - 2:
Take out the old transaction O from the blockchain. - 3:
ifthen - 4:
return Error(“user is not registered"); - 5:
end if%Report an error and exit the program. - 6:
Take out the new service subscription list from N. - 7:
Take out the old service subscription list L from O. - 8:
fordo - 9:
() is unit price of the new (old) access privilege [j] ([j]) on the SP . - 10:
Remaining usage time [j]; - 11:
if then ; - 12:
end if - 13:
Extension of time [j]; - 14:
if then - 15:
check [j], [j], [j]; - 16:
end if - 17:
if then - 18:
check ; - 19:
end if - 20:
if [j][j] then return Error; - 21:
end if%Cannot downgrade in unexpired service. - 22:
if [j][j] then - 23:
check [j], [j]; - 24:
end if - 25:
if [j][j] then - 26:
check [j], [j]; - 27:
end if - 28:
if [j][j] then - 29:
check [j], [j]; - 30:
end if - 31:
if [j][j] then - 32:
check [j], [j]; - 33:
end if - 34:
end for%Finish checking the new service subscription list . - 35:
Storing the updated transaction N in the blockchain. - 36:
return Success(“Mobile user is successfully updated !");
|
5. The Proposed Scheme
The proposed scheme consists of five phases: an initialization phase, user registration and subscription phase, authentication and authorization phase, user-friendly password update phase, and user access privilege update phase.
5.1. Initialization Phase
In the initialization phase, the authorized SPs will be joined into the identical blockchain network as nodes. MSP, i.e., the manager of consortium blockchain, selects an additive group of point G with order q, where P is a generator of G, and six hash secure functions , , , , , , where , , , are the output bit length of the hash functions. Each SP generates a private key , calculates its public key , and stores the private key into its secret memory. registers on MSP with a public key . On the website, publishes its own privilege unit price list, which records the current one-day unit price of each different privilege service. On the blockchain, all smart contracts Algorithms 1–4 are initialized and deployed. MSP publishes the parameters .
5.2. User Registration and Subscription Phase
Each SP shares the identical ledger of the blockchain, so users can select the currently closest SP for registration and subscribing services. The
Table 3 illustrates the phase of user registration and subscription.
Step 1:
chooses an SP
closest to the mobile device
, selects a random number
, and generates a service subscription list
L that records users’ desired privileges, service periods, and amount of payment. In addition,
calculates the public key
and
, where
is the pseudonym of
. Then,
generates a signature
, where
is the current timestamp, and generates a NIZK proof of knowledge
:
Finally, transmits to and the fees paid to purchase services to through a secure channel, where is the registration requirement.
Step 2: After receiving the message from at the time , checks an inequality , where is the maximum allowable transmission delay. If the inequality is satisfied, validates to determine the validity of . If it holds, confirms whether the signature is correct. If it is correct, checks whether the fees paid by are equivalent to the sum of all costs in array . If they are equivalent, calculates a signature . Then, submits the user registration transaction to the blockchain. Here, is the registration time of .
Step 3: An overview of the transaction processing process is presented in
Section 4.3. The transaction belonging to
is verified by a smart contract Algorithm 2. Algorithm 2 checks whether
has not registered, recalculates the entire cost, and confirms whether
is correct for each SP, i.e., whether
pays enough service fees for each hierarchical service. If both conditions are satisfied, one transaction that records the user identity and subscription information is stored in the blockchain. If any of the judgment conditions in Steps 2 and 3 above are not satisfied,
will interrupt the session and refund service fees to users. Finally,
sends
to
through a secure channel.
Step 4: Upon receipt of the message, inputs into the mobile device . Then, chooses a random number and computes , , . Finally, stores , V, , , , and L into the secret memory of the mobile device.
Step 5: All SPs detecting the generation of a new transaction in blockchain ask for their deserved user subscription service fees from off chain according to the identity of the acceptance SP and the list L in the transaction.
5.3. Authentication and Authorization Phase
Before accessing an SP
,
needs to implement mutual authentication with
. At the same time,
also refers to the service subscription list
L to determine which level of service
the user can access within the validity service period
.
Table 4 illustrates the phase of authentication and authorization.
Step 1: inputs and into the mobile device . computes , , and , and checks whether and V are equal. If they are not equal, interrupts the operation. Otherwise, extracts the private key . Then, determines the user’s access privilege on according to the list L. If the privilege of has expired or is not paid for, can only access the trial privilege service, . Otherwise, can access the unexpired privilege service, . Next, generates a random number and computes , q, , where denotes the current timestamp in . Then, sends the messages to through a public channel.
Step 2: Upon receipt of the message, verifies whether , where is the timestamp when messages were received from . If the inequality is satisfied, calculates . Using , the latest transaction belonging to can be queried by . calls the smart contract Algorithm 3 (PIDi) to extract the transaction from blockchain. Then, obtains from the transaction, and verifies whether the equation is satisfied. If it is satisfied, confirms that is a legal user.
Step 3: Then, checks the user’s access privilege and the validity period of service requested by the . If , this indicates that the is within the validity period for using the privilege service at level , . If , this indicates that has expired or the privilege service () on has not been paid for, and that only the trial privilege service, , can be used. Then, checks whether . If the equation is satisfied, provides level of service for . generates a random number and computes , , . If any of the judgment conditions in Steps 2 and 3 above are not satisfied, will interrupt the session. After that, sends to via a public channel.
Step 4: After receiving the message from at the time , verifies whether . If it holds, sets . computes , . Then, checks whether matches with the received . If holds, authenticates with . Meanwhile, is also allowed to access the service with the privilege level on in the service period. Otherwise, fails to authenticate with the .
5.4. User-Friendly Password Update Phase
When wants to update , the user just needs to perform the following steps in the mobile device.
Step 1: inputs and into . Then, computes , , and , and checks whether and V are equal. If they are not equal, interrupts the phase of the password update. Otherwise, inputs a new password .
Step 2: computes , , and .
Step 3: Finally, stores and in to replace and V, respectively.
5.5. User Access Privilege Update Phase
The mobile user can select the closest SP to flexibly update the access privileges on n SPs in or not in the validity periods, and the mobile user can inherit the service periods that have not been used up before. Our scheme applies two arrays, p and t, to record the new privileges applied by and the extended service periods of , respectively, on all SPs.
Step 1: First, chooses an SP closest to the mobile device , inputs its and , obtains , , , and , and sets two arrays, p and t, to determine the new levels of services desired and the extended service periods. Then, chooses the current timestamp and uses Algorithm 5 to obtain the new service subscription list with the input of L, , , p, and t. After that, calculates . Finally, submits and service fees to through the secure channel, where is the updated requirement.
Step 2: After receiving the message, checks the inequality , where denotes the timestamp of when received the updated message. If the inequality is satisfied, validates to determine the validity of . If it holds, confirms whether the signature is correct. If it is correct, checks whether fees paid by are equivalent to the sum of all costs in array . If they are equivalent, calculates . Then, submits update transaction to the blockchain.
Step 3: The overview of the transaction processing process is presented in
Section 4.3. The update transaction belonging to the
is verified by a smart contract Algorithm 4. Algorithm 4 checks whether the
has been registered and whether the cost
of the
is set correctly. If both conditions are satisfied, one transaction that records the user update information is stored in the blockchain. If any of the above conditions in Steps 2 and 3 are not satisfied,
interrupts the session and refunds fees to users. Finally,
sends
to
through the secure channel.
Step 4: After receiving the message, computes , , and . Finally, stores , , and in the secret memory of to replace , V, and L, respectively.
Step 5: All SPs, detecting the generation of a new transaction in blockchain ask for their deserved user update service fees from
off chain according to the identity
of the acceptance SP and the list
in the transaction.
| Algorithm 5 User updating the service subscription list L |
| Input: Old service subscription list L, Current timestamp , Previous registration time , New access privileges p[] set by the user, Extension of periods t[] set by the user. |
| Output: New service subscription list . |
- 1:
Update user’s access privileges and service periods on all n SPs in turn. - 2:
fordo - 3:
remaining service periods [j]; - 4:
if then ; - 5:
end if - 6:
() is unit price of the new (old) access privilege p[j] ([j]) on the SP . - 7:
if then % has expired or the service on has not been bought. - 8:
if then % do not buy the service period on this time. - 9:
, ; - 10:
end if - 11:
if then % buy the service period on . - 12:
; - 13:
end if% buy new privilege services. - 14:
end if - 15:
if then % has not expired on . - 16:
if then return Error; - 17:
end if%Privileges cannot be reduced during service periods. - 18:
if then %Do not extend the use period on . - 19:
if then ; - 20:
end if%Update the use period on . - 21:
if then ; - 22:
end if%Increase privileges needed to make up the difference. - 23:
end if - 24:
if then %Extend the use period on . - 25:
if then ; - 26:
end if%Continue to buy the previous privilege service. - 27:
if ] then ; - 28:
end if%Increase privileges needed to make up the difference. - 29:
end if - 30:
end if - 31:
end for - 32:
return;
|
7. Security Analysis of the Proposed Scheme
This section proves that the proposed scheme satisfies the security requirements defined in
Section 3 using the random oracle model. Since the authentication phase is executed in an insecure public channel, and other phases are implemented in the secure channel, this section shows the resistance to security threats in the authentication phase.
Security Model. Following the literature [
11,
39,
46] a security model was designed for the proposed scheme, which was demonstrated by a game played by a probabilistic polynomial time (PPT) Turing machine
ℑ and a PPT adversary
. We used the instances
and
to represent the mobile user oracle and the SP oracle, respectively, in session
. The adversary
was allowed to perform the following attack capabilities:
issues this inquiry to simulate registering as a legal mobile user with the identity . ℑ generates the access privilege and the private key and public key of , records them in the list , and returns and to .
issues this inquiry to simulate registering as a legal SP with the identity . ℑ generates the access privilege and the private key and public key of , records them in the list , and returns and to .
issues this inquiry to simulate that the participant transmits the message to the oracle , and ℑ returns an answer specified by the protocol to .
issues this inquiry to simulate using all passive attacks, and ℑ returns all messages transmitted between and .
There are three corruption queries:
- (a)
issues this inquiry to simulate the password leakage attack, and ℑ returns the mobile user password to .
- (b)
issues this inquiry to simulate the mobile device loss attack, and ℑ returns secret parameters stored in to .
- (c)
issues this inquiry to simulate the SP compromise attack.
Definition 1.
Matching sessions: If the session in and the session in are the same session , the peer identity of is , the peer identity of is , and two instances have both been accepted, the two session and are said to be matching.
Definition 2.
Security authentication protocol: The secure authentication scheme needs to satisfy the following properties:
and are matching sessions, and two instances accept each other.
The probability that is accepted as by is negligible.
The probability that is accepted as by is negligible.
Definition 3.
Discrete logarithm (DL) problem hypothesis: Given that , , , it is infeasible to calculate α.
MAC-Game: there exist two participants, the challenger and the MAC oracle , where possesses the . The challenger is able to input any messages to the MAC oracle to obtain an MAC value as many times as needed. The probability for the adversary to win the MAC-Game is assumed to be . The MAC-Game has the following steps:
The adversary transmits two messages and to .
selects a random number . If is selected, returns the MAC value to . If is selected, returns the MAC value to .
The adversary speculates on the value of b and give a . If , can win the MAC-Game.
7.1. Formal Security Analysis
In this section, the adversary and Turing machine ℑ play a game to show that if can successfully impersonate a mobile user or SP to pass authentication with a non-negligible probability, then a PPT ℑ can be constructed to solve the potential hard problems with a non-negligible probability using the abilities of .
Our proposed protocol is reviewed as below:
Lemma 1 (Secure Mobile User Authentication). In our proposed scheme, if is accepted, solving the DL problem is infeasible, all hash functions are ideal random functions, and the probability that a PPT adversary forges a legitimate mobile user authentication message is negligible.
Proof. We assume that a PPT adversary is able to forge a legitimate mobile user authentication message to pass authentication with a non-negligible probability. Afterwards, a PPT Turing machine ℑ is able to win the DL problem with a non-negligible probability by using the abilities of . The probability that the advantage for wins the DL problem is assumed to be . □
Giving an example of a DL problem, the Turing machine ℑ needs to calculate the using the known values and P. In addition, all oracle queries of must be answered by ℑ to simulate an environment where cannot distinguish from the real proposed scheme. Therefore, all initialization parameters should be generated and published by ℑ. The private key of the challenger is assumed to be , and ℑ answers all oracle queries of as follows:
: In this query, ℑ maintains a list initialized to empty, and i = 0, 1, 2, 3, 4, 5. After receiving the message , ℑ inspects whether [] is kept in . If it is kept, ℑ returns h to . Otherwise, ℑ randomly generates a number h, maintains the tuple in the list , and returns h to .
: In this query, ℑ maintains a list initialized to empty. ℑ inspects if [] is kept in . If it is kept, ℑ returns and to . Otherwise, ℑ operates as follows:
- (a)
If = , ℑ sets and obtains the public key and access privilege from the mobile user oracle . Then, ℑ maintains the tuple [] in the list , and returns and to .
- (b)
If , ℑ generates an access privilege , randomly selects a number , and computes the public key . Then, the tuple [] is maintained in the list , and ℑ returns and to .
In this query, transmits the first message to ℑ. is decrypted by ℑ to obtain , and . Then, ℑ is executed following the specification of the proposed protocol and returns .
In this query, first checks whether = is satisfied. If not, ℑ is executed following the specification of the proposed protocol and returns to . Otherwise, ℑ asks for , and then returns to .
: In this query, ℑ returns all messages transmitted between and to .
: In this query, ℑ asks for the password and returns it to .
: In this query, ℑ asks for the secret parameters in mobile devices and returns it to .
In this query, ℑ returns the private key of the SP to .
If
can successfully falsify an authentication message
sent to
ℑ, the adversary will pass user authentication, where
, and
q. Due to the forking lemma [
47], a counterfeit authentication message
is forged by
using the repeat of the simulation with the value of
. Therefore, two Equations (
2) and (
3) are shown as follows:
Calculating the two equations, the following Equation (
4) is obtained:
According to the above analysis,
is the solution of the DL problem. A further analysis of the probability is shown below. If
successfully forges a legitimate authentication message with the non-negligible probability
,
ℑ can solve the DL problem. If
cannot achieve forgery,
represents the probability that
wins the DL problem. Hence, the probability that the advantage for
wins the DL problem is computed as the following Equation (
5), similar to that of the paper [
46]:
where
represents the number of queries sent by
. Since the probability
is non-negligible and the probability
is negligible,
is also non-negligible. Thus,
ℑ has a non-negligible probability of winning the DL problem using the abilities of
. However, this is a contradiction to our assumption. In our scheme, there is no PPT
that can successfully forge a legal authentication message of mobile users with a non-negligible probability.
Lemma 2 (Secure SP Authentication). In our proposed scheme, if is accepted, solving the DL problem is infeasible, all hash functions are ideal random functions, and the probability that a PPT adversary forges a legal SP authentication message is negligible.
Proof. We assume that a PPT adversary is able to forge a legitimate SP authentication message to pass authentication with a non-negligible probability. Afterwards, a PPT Turing machine ℑ is able to win the latent game of MAC (MAC-Game) with a non-negligible probability by using the abilities of without knowing the . □
All oracle queries of must be answered by ℑ to simulate an environment where cannot distinguish from the real proposed scheme. Therefore, all initialization parameters need to be generated and published by ℑ, except the private key of the challenger . The oracle queries , , , and are answered by ℑ operating in the proof of Lemma 1, and ℑ answers other oracle queries of as follows:
: In this query, ℑ maintains a list initialized to empty. ℑ inspects if [, ] is kept in . If it is kept, ℑ returns and to . Otherwise, ℑ operates as follows:
- (a)
If = , ℑ sets and obtains the public key and the access privilege from the SP oracle . Then, ℑ maintains the tuple [, ] in the list and returns and to .
- (b)
If , ℑ randomly selects a number , sets , and computes the public key . Then, ℑ maintains the tuple [, ] in the list and returns and to .
: In this query, transmits the first message to ℑ. Then, ℑ is executed following the specification of the proposed protocol and returns . After receiving from , ℑ asks to test and check the received MAC value in , and returns the result of verification.
: In this query, first checks whether = is satisfied. If not, ℑ is executed following the specification of the proposed protocol and returns to . Otherwise, ℑ terminates the MAC-Game.
: In this query, ℑ checks whether = is satisfied. If it is not satisfied, ℑ returns the private key of the SP to . Otherwise, ℑ terminates the MAC-Game.
If
can successfully falsify an SP authentication message
sent to
ℑ, the adversary will pass SP authentication, where
. After receiving
,
ℑ transmits the message
and a random
whose bit length is equal to
to
.
returns an MAC value
to
ℑ. According to the value of
,
ℑ is able to inspect whether the value of
is
or
to obtain
or
. If
successfully forges a legitimate SP authentication message with a non-negligible probability
,
ℑ can win the MAC-Game. If
cannot achieve forgery,
ℑ has a probability of 1/2 to win the MAC-Game. Hence, the probability that the advantage for
wins the MAC-Game is computed as the following formula
6, similar to that of the paper [
46]:
Since the probability is non-negligible, is also non-negligible. Thus, ℑ has a non-negligible probability of winning the MAC-Game using the abilities of . However, this is a contradiction to our assumption. In our scheme, there is no PPT that can successfully forge a legal SP authentication message with a non-negligible probability.
Theorem 1.
If: (A) and has been accepted, (B) solving the DL problem is infeasible, and (C) all hash functions i = 0,…,5 are ideal random functions, the proposed scheme is secure.
Proof. Lemma 1 and Lemma 2 can confirm that there is no PPT that is able to successfully forge a legitimate mobile user or SP authentication message with a non-negligible probability if solving the DL problem is infeasible and MAC is the ideal random function. Thus, our proposed scheme is secure based on Definition 2. □
7.2. Informal Security Analysis
7.2.1. Single Registration
A mobile user, interested in multiple services, just needs to selects the arbitrary (nearest) SP to submit the identity, subscription information, and service fees. (1) validates to determine that the user is the owner of , ensuring the validity of the user identity. In addition, the smart contract Algorithm 2 checks the uniqueness of the user identity by reading the information about on the blockchain. (2) Algorithm 2 inspects the correctness of the user’s subscription information in the list L and decides whether to store the transaction in the blockchain to accomplish the single registration for the mobile user. (3) Other SPs can ask for their deserved user registration service fees from off chain according to the identity of the acceptance SP and the list L in the transaction. The three phases are secure under the ZkPoK protocol, the automatic and transparent smart contract, and the tamper-proof distributed ledger.
7.2.2. Mutual Authentication
Based on Theorem 1, there is no PPT adversary that is able to successfully forge a legitimate mobile user or SP authentication message with a non-negligible probability if solving the DL problem is infeasible and MAC is the ideal random function. Hence, mutual authentication between mobile users and SPs can be guaranteed.
7.2.3. User Anonymity and Un-Traceability
To provide user anonymity on the blockchain, the pseudonym is used in the transaction. is only bound to the user’s subscription information, and not the real identity. In the public channel, is protected by . The random number will change for each authentication session. is calculated by , but is confidentially stored in the memory of SP. After intercepting the message , either guesses the value of or solves the DL problem. Both operations are practically infeasible. Thus, cannot obtain the mobile user’s true identity and track the communication process of a mobile user.
7.2.4. Two-Factor Security
There exist two security factors in our scheme. One is
, and the other is the mobile device. When only having the password without a mobile device, the adversary cannot accurately generate each cryptographic parameter to forge the mobile user authentication message. On the other hand, when the mobile device is lost or stolen by an adversary, then
is able to extract the secret parameters from the mobile device. During offline dictionary attacks, the password space
is divided into 1024 candidate passwords
[
48,
49]. Consequently,
is still unable to obtain the correct password.
7.2.5. Resistance to Reply Attack
The timestamp and challenge0-response mechanism are used in our proposed scheme to prevent the replay attack. Mobile user authentication message and SP authentication message are protected by timestamps and . After an SP or the mobile user receives the timestamp, the validity of or will be checked. Hence, the user and SP will only accept each other in the current session.
7.2.6. Resistance to Wrong Password Login/Update Attack
If enters the wrong password , the mobile device will calculate a wrong , and check whether and V are equal. This equation is untenable, and the wrong password login/update will be refused.
7.2.7. Hierarchical Access Control
The service provided by each SP is divided into several levels, e.g., ‘Bronze’, ‘Silver’, and ‘Gold’. A mobile user can subscribe to different levels of hierarchical services on multiple SPs. The service subscription list L records service levels (access privileges) and service periods that users want to subscribe to. Users only need to determine service levels that they are interested in and the service usage time in L, and submit L to the blockchain for the inspection of Algorithm 2. Users are not required to interact with SPs in advance. In the authentication and authorization phase, the SP looks up the mobile user’s service level (access privilege) and service period in L to determine which level of service the user can access.
7.2.8. Access within Limits of Permission
In the authentication and authorization phase, sends the access privilege to SP. Then, SP reads the service subscription list L from the blockchain and checks the user’s access privilege and the validity period of service. If has not expired on the with the privilege , , SP sets to allow users to access privilege services. If has expired on the , , SP sets to provide the free trial service. More importantly, SP needs to check whether . If they are not equal, this indicates that is trying to access beyond its authority or has expired, and the SP will reject the access request and interrupt the session. In addition, if the SP sets the wrong privilege , the session will also be interrupted.
7.2.9. Efficient and Flexible Update User Access Privilege
If has expired or the service has not been purchased on an SP, the mobile user can subscribe to all levels of services. Even if is still within the validity period of the service on an SP, the mobile user can also subscribe to the service period of new privilege services, and the user only needs to make up the price difference without having to fully pay again. Moreover, Algorithm 5 will set up the user’s new access privileges and service periods on all SPs simultaneously in order to generate a correct new service subscription list . is sent to and stored in a new transaction after inspection. Hence, our scheme only needs to send an update request, and the user’s service levels on all SPs can be updated concurrently.
7.2.10. Resistance to Double-Spending Attack
The SP reads the world state to obtain the latest transaction to ensure that mobile users can only use the latest access privileges. Each transaction records the registration and update time of user access privileges. Thus, the improper behavior of mobile users using expired privileges can be detected by the SP.
7.3. Security Features Analysis
This section evaluates the proposed scheme by comparing its security features with several related schemes [
8,
12,
13,
15]. Ref. [
8] is the representative multi-server authentication scheme for MCC services. Ref. [
15] is the latest RC-based multi-server authentication and authorization scheme for MCC hierarchical services. Ref. [
12] is the newest blockchain-based multi-server authentication scheme for the mobile cloud environment. Ref. [
13] is the latest distributed multi-authority ABE-based authentication and authorization scheme for cloud hierarchical services.
Table 8 compares the security features among five schemes. The comparison results indicate that our scheme has better security attributes than the above related schemes.
9. Discussion
In this section, we discuss the difference between the RC-based authentication and authorization scheme and our blockchain-based authentication and authorization scheme, single registration, blockchain storage, access privilege updates, and double-spending attack.
In the traditional RC-based multi-server authentication and authorization scheme, the server verifies the identity of the user and concurrently verifies whether the user has correct access privilege or not [
9]. The integration of authentication and authorization at the same stage makes the cloud service system more efficient [
15]. However, such a centralized scheme requires a trusted third party to issue identity and permission credentials for users, which makes it faces a single point of failure and have a high trust overhead. In our blockchain-based multi-server authentication and authorization scheme, the user can register on the arbitrary SP and obtain corresponding identity and permission credentials. It has the fault-tolerant capability to resist a single point of failure. In addition, our scheme uses the blockchain to establish the distributed trust relationship in the MCC environment, which avoids the use of RC, which needs to be completely trusted.
Single registration in the RC-based authentication and authorization scheme is straightforward. The user only needs to register on RC once and obtain one credential. All SPs trust the validity of credentials issued by RC for users and make authorization decisions according to the privileges in the credential. However, it is challenging to achieve single registration in our blockchain-based scheme without a trusted third party that distributes credentials for users. On the one hand, users need to prove the validity of the registration information submitted, e.g., public keys generated by themselves. On the other hand, SPs need to trust that a user registered on an arbitrary SP obtains the credential that can be used to access their services. Therefore, we used the NIZK proof of knowledge to force users to prove the discrete logarithm knowledge of the public key. Moreover, an automatic and transparent smart contract was applied to complete the single registration without the trusted third party.
Although the blockchain can enhance the security of the MCC system and reduce trust overhead, it has the issue of high storage overhead. Each node in the blockchain needs to store the same ledger, which leads to expensive storage overhead and restricts the system’s scalability. In particular, the total storage capacity is transactions, where the blockchain, which is maintained by n servers, needs to store a user’s n transactions that, respectively, record different access rights on n servers. Based on this storage feature, our scheme consolidates the user’s multiple access privileges into one transaction. In this way, the total storage capacity is n transactions since n servers, which maintain the blockchain, just need to store n transactions. In the MCC scenarios, the number of mobile users in the tens of millions emphasizes the importance of reducing the storage pressure on the blockchain.
The proposed scheme enables the mobile user to update access privileges anytime and anywhere. It brings convenience to users as well as the risks of double-spending attacks. In the access privilege update phase, the user submits new transactions that record new privileges to the blockchain. After the smart contract check, new transactions are written to the blockchain to complete the privileges update. However, old transactions that record old privileges cannot be deleted and modified due to the immutability of the blockchain. If no processing is made, the adversary can use the privileges in old transactions to access the service. In this paper, we used the world state to prevent this double-spending attack. The world state is stored in the key-value database and is the last transaction data about the key. In our solution, we used the user’s unique pseudonym “PID” as the key. In the authorization phase, the SP both uses the key “PID” to read the newest transaction content that records the newest privilege of the user and makes corresponding authorization decisions. In this way, the double-spending attack is prevented.