Covert Channel Communication as an Emerging Security Threat in 2.5D/3D Integrated Systems
Abstract
1. Introduction
- A summary of the general threat model and methodology involved in using a covert channel to leak secret information is provided.
- A detailed background on different types of physical covert channel attacks is provided.
- Modern countermeasures against physical covert channel attacks are discussed.
- A perspective on covert channels in emerging 2.5D/3D systems is provided.
- A novel attack model for a power covert channel that exploits the relatively accessible interposer layer in 2.5D systems is proposed.
2. Background
2.1. Covert Channel Methodology
2.1.1. Threat Model
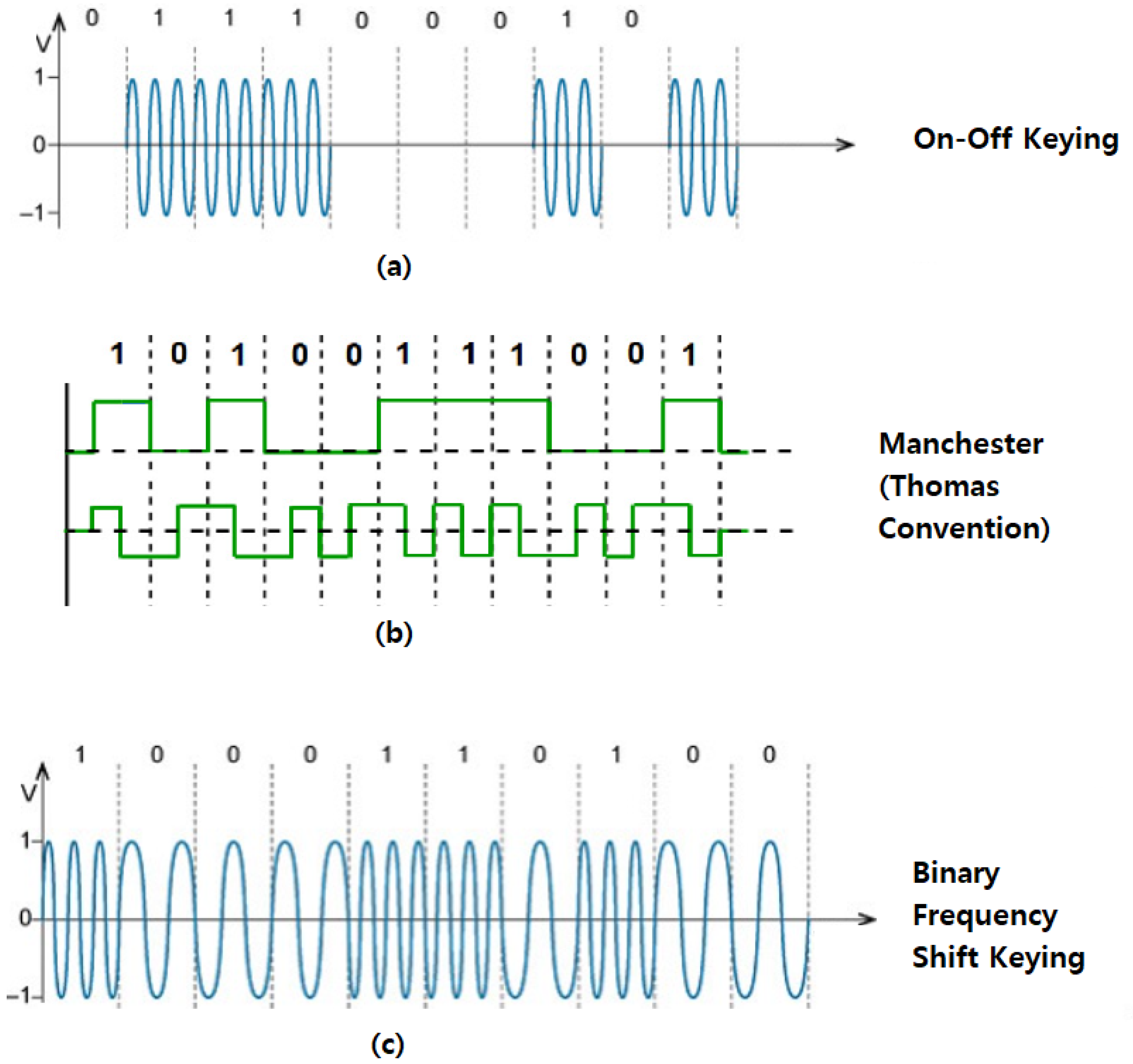
2.1.2. Methods of Encoding Data
2.2. Covert Channel Evaluation
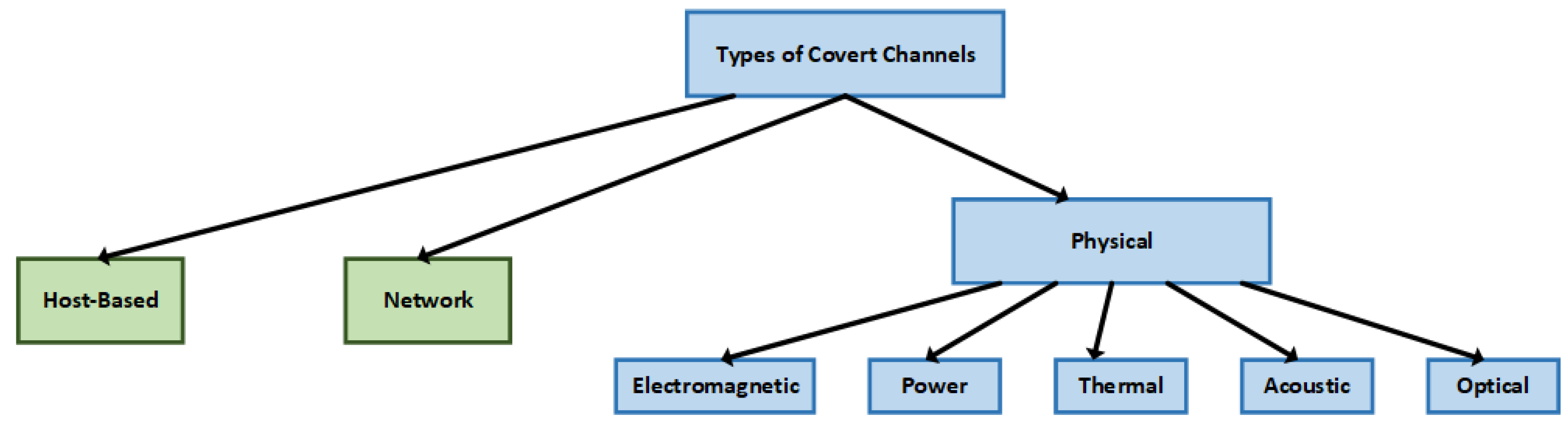
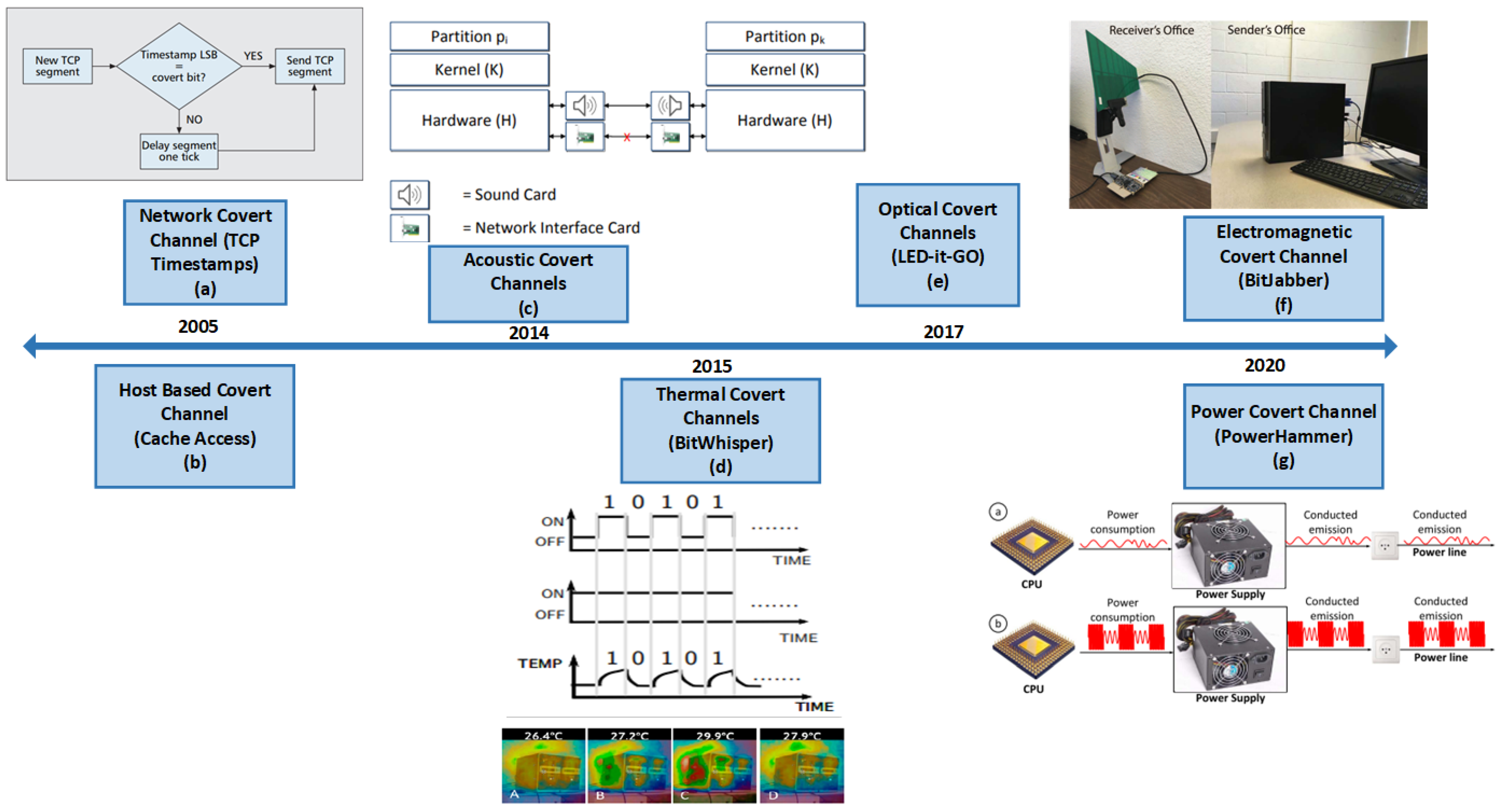
3. Types of Physical Covert Channels
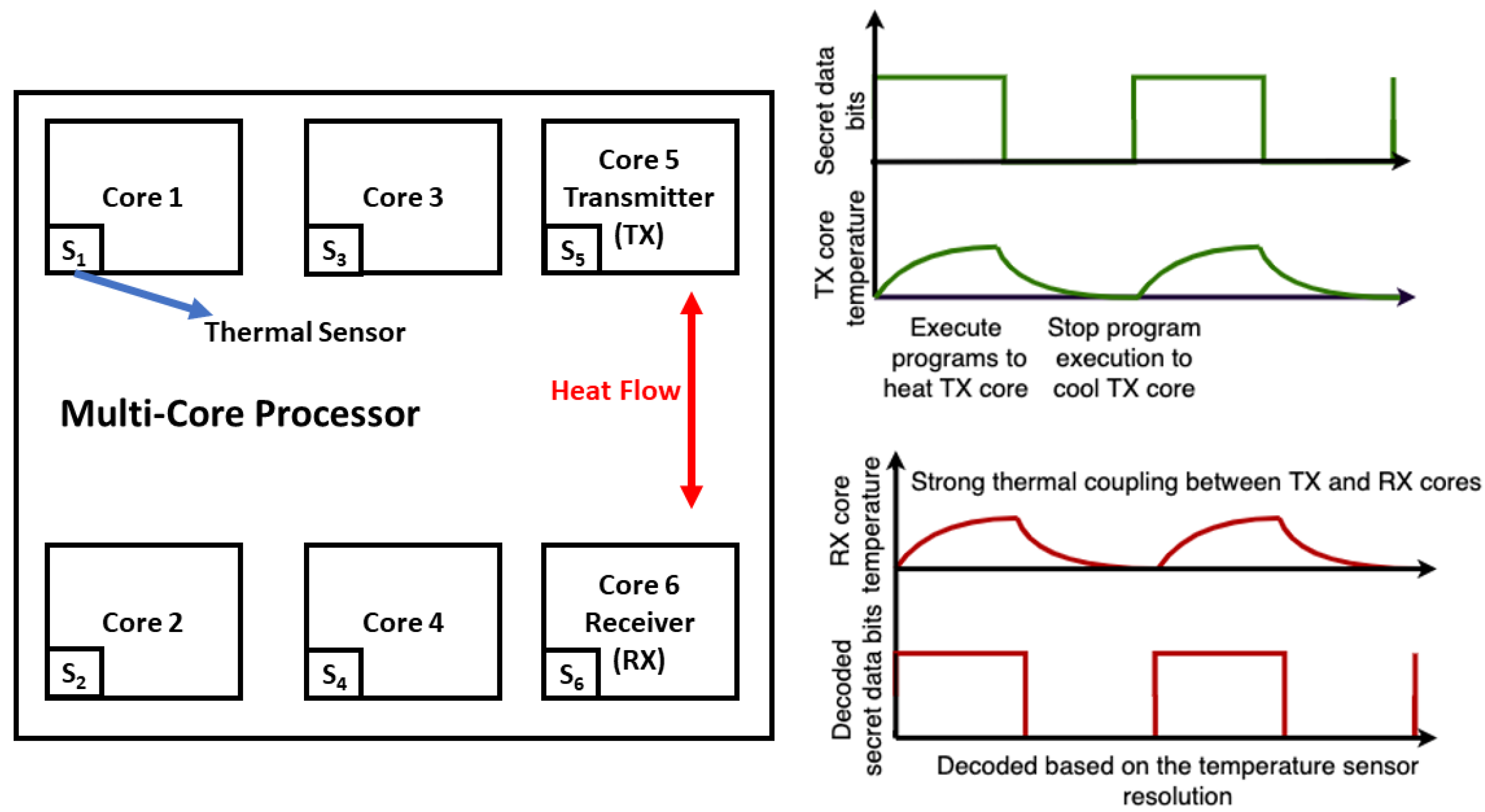
3.1. Temperature-Based Channels
BitWhisper
3.2. Power-Based Channels
3.2.1. PowerHammer
3.2.2. CAPSULe
3.3. Electromagnetic Radiation-Based Channels
4. Countermeasures against Covert Channel Attacks
4.1. Shielding
4.2. Jamming
4.3. Runtime Detection of Covert Channels
4.3.1. Threshold-Based Monitoring
4.3.2. Leveraging Machine Learning Techniques
5. Covert Channel Attacks in 2.5D/3D ICs
5.1. 2.5D/3D Integration
5.2. Existing Works
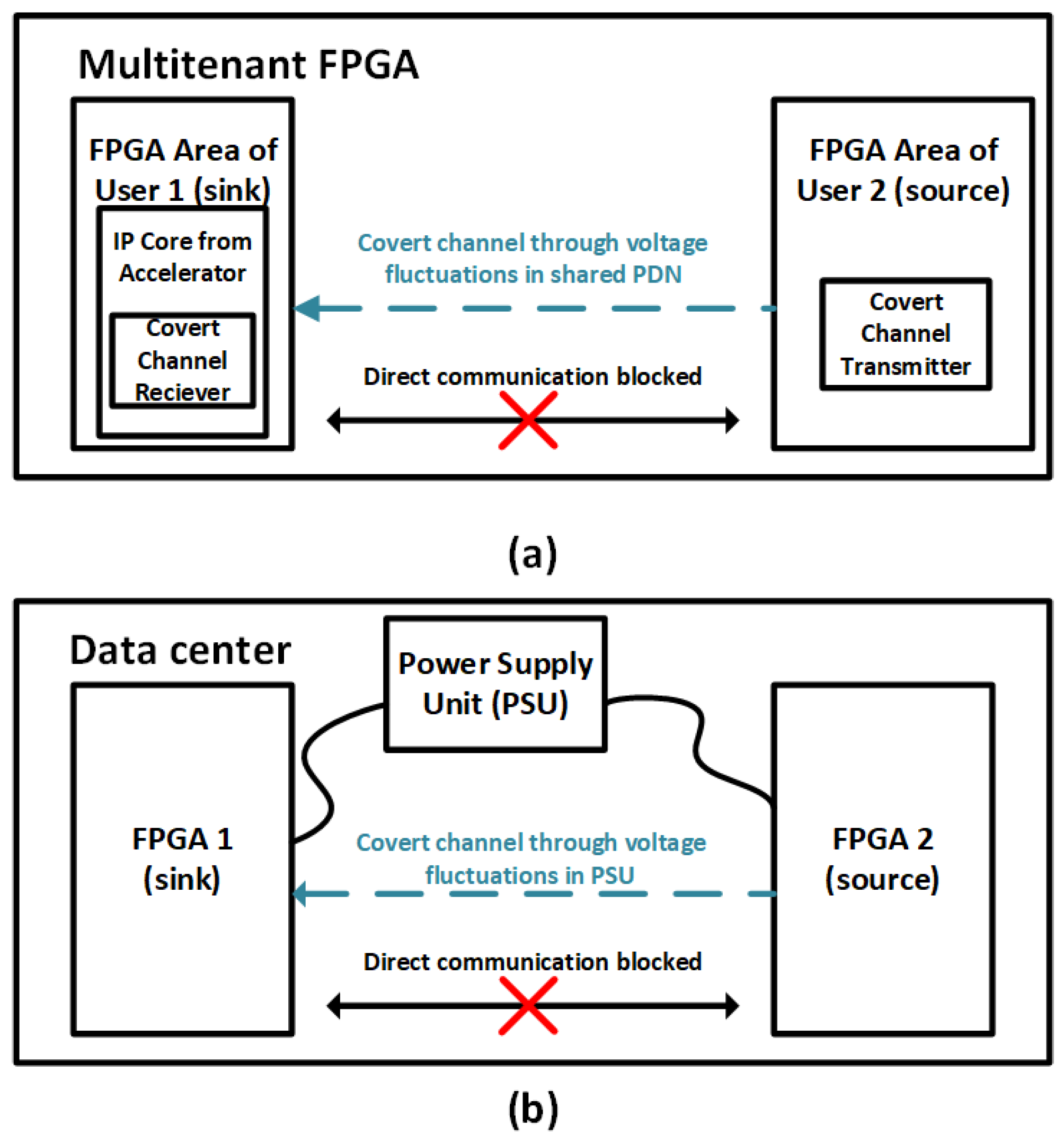
5.2.1. Power Covert Channels in 2.5D FPGAs
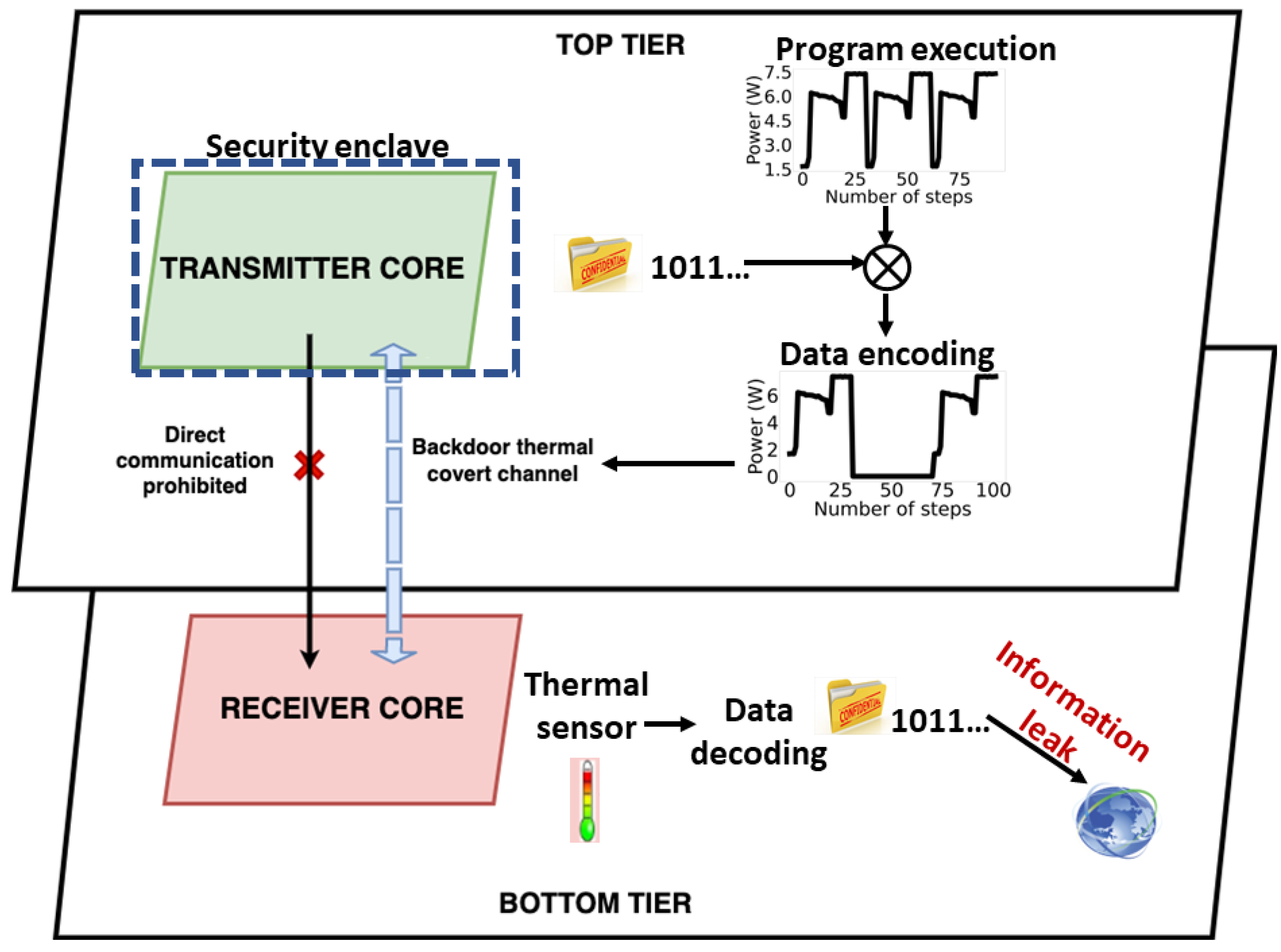
5.2.2. Thermal Covert Channels in 3D ICs
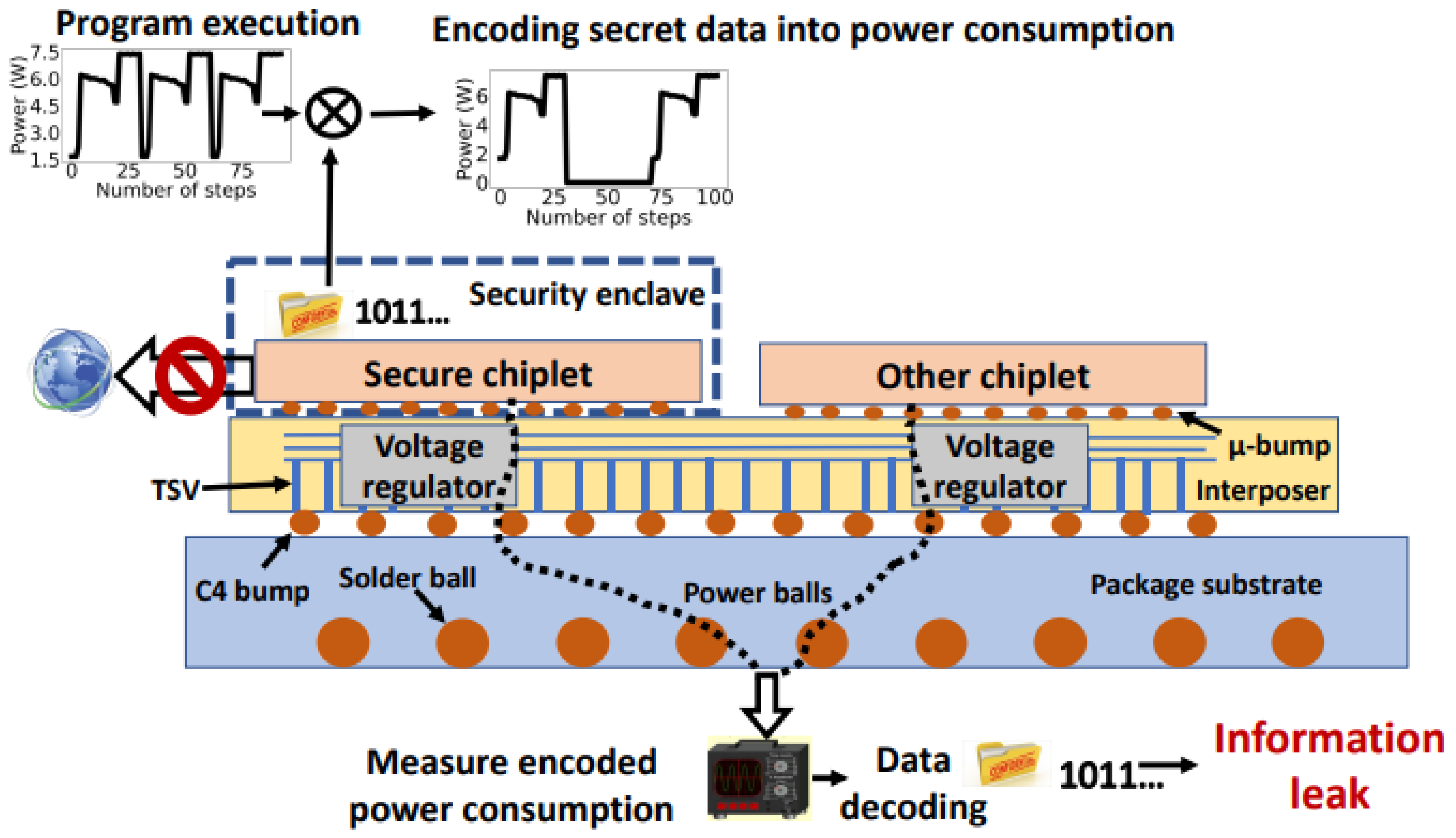
5.3. Potential Covert Channel Attack Model in 2.5D ICs
5.4. Discussion on Mitigation Strategies
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- ARM TrustZone. Available online: https://developer.arm.com/ip-products/security-ip/trustzone (accessed on 20 December 2022).
- Ngabonziza, B.; Martin, D.; Bailey, A.; Cho, H.; Martin, S. Trustzone explained: Architectural features and use cases. In Proceedings of the 2016 IEEE 2nd International Conference on Collaboration and Internet Computing (CIC), Pittsburgh, PA, USA, 1–3 November 2016; pp. 445–451. [Google Scholar]
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. Hasp@ isca 2013, 10. [Google Scholar] [CrossRef]
- Shu, R.; Wang, P.; Gorski, S.A., III; Andow, B.; Nadkarni, A.; Deshotels, L.; Gionta, J.; Enck, W.; Gu, X. A study of security isolation techniques. ACM Comput. Surv. (CSUR) 2016, 49, 1–37. [Google Scholar] [CrossRef]
- Carrara, B.; Adams, C. A survey and taxonomy aimed at the detection and measurement of covert channels. In Proceedings of the 4th ACM Workshop on Information Hiding and Multimedia Security, Vigo, Spain, 20–22 June 2016; pp. 115–126. [Google Scholar]
- Mansfield-Devine, S. Security through isolation. Comput. Fraud Secur. 2010, 2010, 8–11. [Google Scholar] [CrossRef]
- Byres, E. The air gap: SCADA’s enduring security myth. Commun. ACM 2013, 56, 29–31. [Google Scholar] [CrossRef]
- Johnson, R.E. Survey of SCADA security challenges and potential attack vectors. In Proceedings of the 2010 International Conference for Internet Technology and Secured Transactions, London, UK, 8–11 November 2010; pp. 1–5. [Google Scholar]
- Perez, R.L.; Adamsky, F.; Soua, R.; Engel, T. Forget the myth of the air gap: Machine learning for reliable intrusion detection in SCADA systems. EAI Endorsed Trans. Secur. Saf. 2019, 6, e3. [Google Scholar] [CrossRef]
- Zander, S.; Armitage, G.; Branch, P. A survey of covert channels and countermeasures in computer network protocols. IEEE Commun. Surv. Tutor. 2007, 9, 44–57. [Google Scholar] [CrossRef]
- Szefer, J. Survey of microarchitectural side and covert channels, attacks, and defenses. J. Hardw. Syst. Secur. 2019, 3, 219–234. [Google Scholar] [CrossRef]
- Standaert, F.X. Introduction to side-channel attacks. In Secure Integrated Circuits and Systems; Springer: Boston, MA, USA, 2010; pp. 27–42. [Google Scholar]
- Randolph, M.; Diehl, W. Power side-channel attack analysis: A review of 20 years of study for the layman. Cryptography 2020, 4, 15. [Google Scholar] [CrossRef]
- Spreitzer, R.; Moonsamy, V.; Korak, T.; Mangard, S. Systematic classification of side-channel attacks: A case study for mobile devices. IEEE Commun. Surv. Tutor. 2017, 20, 465–488. [Google Scholar] [CrossRef]
- Sayakkara, A.; Le-Khac, N.A.; Scanlon, M. A survey of electromagnetic side-channel attacks and discussion on their case-progressing potential for digital forensics. Digit. Investig. 2019, 29, 43–54. [Google Scholar] [CrossRef]
- Javed, A.R.; Beg, M.O.; Asim, M.; Baker, T.; Al-Bayatti, A.H. Alphalogger: Detecting motion-based side-channel attack using smartphone keystrokes. J. Ambient. Intell. Humaniz. Comput. 2020, 1–14. [Google Scholar] [CrossRef]
- Das, D.; Golder, A.; Danial, J.; Ghosh, S.; Raychowdhury, A.; Sen, S. X-DeepSCA: Cross-device deep learning side channel attack. In Proceedings of the 56th Annual Design Automation Conference 2019, Las Vegas, NV, USA, 2–6 June 2019; pp. 1–6. [Google Scholar]
- Wang, Z.; Lee, R.B. Covert and side channels due to processor architecture. In Proceedings of the 2006 22nd Annual Computer Security Applications Conference (ACSAC’06), Miami Beach, FL, USA, 11–15 December 2006; pp. 473–482. [Google Scholar]
- Aljuffri, A.; Zwalua, M.; Reinbrecht, C.R.W.; Hamdioui, S.; Taouil, M. Applying thermal side-channel attacks on asymmetric cryptography. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 1930–1942. [Google Scholar] [CrossRef]
- Lou, X.; Zhang, T.; Jiang, J.; Zhang, Y. A survey of microarchitectural side-channel vulnerabilities, attacks, and defenses in cryptography. ACM Comput. Surv. (CSUR) 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Lipp, M.; Kogler, A.; Oswald, D.; Schwarz, M.; Easdon, C.; Canella, C.; Gruss, D. PLATYPUS: Software-based power side-channel attacks on x86. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 355–371. [Google Scholar]
- Carrara, B.; Adams, C. Out-of-band covert channels—A survey. ACM Comput. Surv. (CSUR) 2016, 49, 1–36. [Google Scholar] [CrossRef]
- Xu, Y.; Bailey, M.; Jahanian, F.; Joshi, K.; Hiltunen, M.; Schlichting, R. An exploration of L2 cache covert channels in virtualized environments. In Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop, Chicago, IL, USA, 21 October 2011; pp. 29–40. [Google Scholar]
- Percival, C. Cache Missing for Fun and Profit. 2005. Available online: https://www.daemonology.net/papers/htt.pdf (accessed on 20 December 2022).
- Maurice, C.; Neumann, C.; Heen, O.; Francillon, A. C5: Cross-cores cache covert channel. In Detection of Intrusions and Malware, and Vulnerability Assessment: 12th International Conference, DIMVA 2015, Milan, Italy, 9–10 July 2015, Proceedings 12; Springer: Cham, Switzerland, 2015; pp. 46–64. [Google Scholar]
- Alagappan, M.; Rajendran, J.; Doroslovački, M.; Venkataramani, G. DFS covert channels on multi-core platforms. In Proceedings of the 2017 IFIP/IEEE International Conference on Very Large Scale Integration (VLSI-SoC), Abu Dhabi, United Arab Emirates, 23–25 October 2017; pp. 1–6. [Google Scholar]
- Wendzel, S.; Zander, S.; Fechner, B.; Herdin, C. Pattern-based survey and categorization of network covert channel techniques. ACM Comput. Surv. (CSUR) 2015, 47, 1–26. [Google Scholar] [CrossRef]
- Giffin, J.; Greenstadt, R.; Litwack, P.; Tibbetts, R. Covert messaging through TCP timestamps. In Privacy Enhancing Technologies: Second International Workshop, PET 2002 San Francisco, CA, USA, 14–15 April 2002, Revised Papers 2; Springer: Berlin/Heidelberg, Germany, 2002; pp. 194–208. [Google Scholar]
- Matyunin, N.; Szefer, J.; Biedermann, S.; Katzenbeisser, S. Covert channels using mobile device’s magnetic field sensors. In Proceedings of the 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Macao, China, 25–28 January 2016; pp. 525–532. [Google Scholar]
- Hanspach, M.; Goetz, M. On covert acoustical mesh networks in air. arXiv 2014, arXiv:1406.1213. [Google Scholar] [CrossRef]
- Zhan, Z.; Zhang, Z.; Koutsoukos, X. Bitjabber: The world’s fastest electromagnetic covert channel. In Proceedings of the 2020 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 7–11 December 2020; pp. 35–45. [Google Scholar]
- Guri, M.; Zadov, B.; Bykhovsky, D.; Elovici, Y. PowerHammer: Exfiltrating data from air-gapped computers through power lines. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1879–1890. [Google Scholar] [CrossRef]
- Guri, M.; Monitz, M.; Mirski, Y.; Elovici, Y. Bitwhisper: Covert signaling channel between air-gapped computers using thermal manipulations. In Proceedings of the 2015 IEEE 28th Computer Security Foundations Symposium, Verona, Italy, 13–17 July 2015; pp. 276–289. [Google Scholar]
- Guri, M.; Zadov, B.; Elovici, Y. LED-it-GO: Leaking (a lot of) Data from Air-Gapped Computers via the (small) Hard Drive LED. In Detection of Intrusions and Malware, and Vulnerability Assessment: 14th International Conference, DIMVA 2017, Bonn, Germany, 6–7 July 2017, Proceedings 14; Springer: Cham, Switzerland, 2017; pp. 161–184. [Google Scholar]
- Tuptuk, N.; Hailes, S. Covert channel attacks in pervasive computing. In Proceedings of the 2015 IEEE International Conference on Pervasive Computing and Communications (PerCom), St. Louis, MO, USA, 23–27 March 2015; pp. 236–242. [Google Scholar]
- Guri, M. Magneto: Covert channel between air-gapped systems and nearby smartphones via cpu-generated magnetic fields. Future Gener. Comput. Syst. 2021, 115, 115–125. [Google Scholar] [CrossRef]
- Bartolini, D.B.; Miedl, P.; Thiele, L. On the capacity of thermal covert channels in multicores. In EuroSys’ 16 Proceedings of the Eleventh European Conference on Computer Systems; Association for Computing Machinery (ACM): New York, NY, USA, 2016; pp. 1–16. [Google Scholar]
- Rasmussen, K.; Giechaskiel, I.; Szefer, J. C3apsule: Cross-fpga covert-channel attacks through power supply unit leakage. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 18–21 May 2020; Volume 1. [Google Scholar]
- Forster, R. Manchester encoding: Opposing definitions resolved. Eng. Sci. Educ. J. 2000, 9, 278–280. [Google Scholar] [CrossRef]
- Latham, D.C. Department of defense trusted computer system evaluation criteria. Dep. Def. 1986, 198. [Google Scholar] [CrossRef]
- Guri, M.; Kachlon, A.; Hasson, O.; Kedma, G.; Mirsky, Y.; Elovici, Y. {GSMem}: Data Exfiltration from {Air-Gapped} Computers over {GSM} Frequencies. In Proceedings of the 24th USENIX Security Symposium (USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 849–864. [Google Scholar]
- Guri, M.; Monitz, M.; Elovici, Y. USBee: Air-gap covert-channel via electromagnetic emission from USB. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 264–268. [Google Scholar]
- Guri, M.; Zadov, B.; Bykhovsky, D.; Elovici, Y. Ctrl-alt-led: Leaking data from air-gapped computers via keyboard leds. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), London, UK, 8–11 November 2019; Volume 1, pp. 801–810. [Google Scholar]
- Carrara, B.; Adams, C. On acoustic covert channels between air-gapped systems. In Foundations and Practice of Security: 7th International Symposium, FPS 2014, Montreal, QC, Canada, 3–5 November 2014. Revised Selected Papers 7; Springer: Cham, Switzerland, 2014; pp. 3–16. [Google Scholar]
- Sepetnitsky, V.; Guri, M.; Elovici, Y. Exfiltration of information from air-gapped machines using monitor’s LED indicator. In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference, The Hague, The Netherlands, 24–26 September 2014; pp. 264–267. [Google Scholar]
- Loughry, J.; Umphress, D.A. Information leakage from optical emanations. ACM Trans. Inf. Syst. Secur. (TISSEC) 2002, 5, 262–289. [Google Scholar] [CrossRef]
- Guri, M.; Solewicz, Y.; Daidakulov, A.; Elovici, Y. Fansmitter: Acoustic data exfiltration from (speakerless) air-gapped computers. arXiv 2016, arXiv:1606.05915. [Google Scholar]
- Brooks, D.; Martonosi, M. Dynamic thermal management for high-performance microprocessors. In Proceedings of the HPCA Seventh International Symposium on High-Performance Computer Architecture, Monterrey, Mexico, 19–24 January 2001; pp. 171–182. [Google Scholar]
- Yang, J.; Zhou, X.; Chrobak, M.; Zhang, Y.; Jin, L. Dynamic thermal management through task scheduling. In Proceedings of the ISPASS 2008-IEEE International Symposium on Performance Analysis of Systems and software, Austin, TX, USA, 20–22 April 2008. [Google Scholar]
- Wu, Q.; Wang, X.; Chen, J. Defending against Thermal Covert Channel Attacks by Task Migration in Many-core System. In Proceedings of the 2021 IEEE 3rd International Conference on Circuits and Systems (ICCS), Chengdu, China, 29–31 October 2021; pp. 111–120. [Google Scholar]
- Masti, R.J.; Rai, D.; Ranganathan, A.; Müller, C.; Thiele, L.; Capkun, S. Thermal covert channels on multi-core platforms. In Proceedings of the 24th USENIX Security Symposium (USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 865–880. [Google Scholar]
- FurMark: VGA Stress Test, Graphics Card and GPU Stability Test, Burn-in Test. Available online: http://www.ozone3d.net/benchmarks/fur/ (accessed on 20 December 2022).
- Great Internet Mersenne Prime Search. Available online: http://www.mersenne.org/download/ (accessed on 20 December 2022).
- Gnad, D.R.; Nguyen, C.D.K.; Gillani, S.H.; Tahoori, M.B. Voltage-Based Covert Channels Using FPGAs. ACM Trans. Des. Autom. Electron. Syst. (TODAES) 2021, 26, 1–25. [Google Scholar] [CrossRef]
- Callan, R.; Zajić, A.; Prvulovic, M. FASE: Finding amplitude-modulated side-channel emanations. In Proceedings of the 2015 ACM/IEEE 42nd Annual International Symposium on Computer Architecture (ISCA), Portland, OR, USA, 13–17 June 2015; pp. 592–603. [Google Scholar]
- Anderson, R.J.; Kuhn, M.G. Soft tempest—An opportunity for NATO. In Protecting NATO Information Systems in the 21st Century; IST Symposium: Washington DC, USA, 1999. [Google Scholar]
- Shen, C.; Liu, T.; Huang, J.; Tan, R. When LoRa meets EMR: Electromagnetic covert channels can be super resilient. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1304–1317. [Google Scholar]
- Wang, J.; Wang, X.; Jiang, Y.; Singh, A.K.; Huang, L.; Yang, M. Combating enhanced thermal covert channel in multi-/many-core systems with channel-aware jamming. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 39, 3276–3287. [Google Scholar] [CrossRef]
- Strasser, M.; Pöpper, C.; Čapkun, S. Efficient uncoordinated FHSS anti-jamming communication. In Proceedings of the Tenth ACM International Symposium on Mobile Ad Hoc Networking and Computing, New Orleans, LA, USA, 18–21 May 2009; pp. 207–218. [Google Scholar]
- Provelengios, G.; Holcomb, D.; Tessier, R. Mitigating voltage attacks in multi-tenant FPGAs. ACM Trans. Reconfig. Technol. Syst. (TRETS) 2021, 14, 1–24. [Google Scholar] [CrossRef]
- Huang, H.; Wang, X.; Jiang, Y.; Singh, A.K.; Yang, M.; Huang, L. On countermeasures against the thermal covert channel attacks targeting many-core systems. In Proceedings of the 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 20–24 July 2020; pp. 1–6. [Google Scholar]
- Huang, H.; Wang, X.; Jiang, Y.; Singh, A.K.; Yang, M.; Huang, L. Detection of and Countermeasure against Thermal Covert Channel in Many-core Systems. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2021, 41, 252–265. [Google Scholar] [CrossRef]
- Long, Z.; Wang, X.; Jiang, Y.; Cui, G.; Zhang, L.; Mak, T. Improving the efficiency of thermal covert channels in multi-/many-core systems. In Proceedings of the 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018; pp. 1459–1464. [Google Scholar]
- Barrow-Williams, N.; Fensch, C.; Moore, S. A communication characterisation of splash-2 and parsec. In Proceedings of the 2009 IEEE International Symposium on Workload Characterization (IISWC), Austin, TX, USA, 4–6 October 2009; pp. 86–97. [Google Scholar]
- Dhananjay, K.; Pavlidis, V.F.; Coskun, A.K.; Salman, E. High Bandwidth Thermal Covert Channel in 3-D-Integrated Multicore Processors. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2022, 30, 1654–1667. [Google Scholar] [CrossRef]
- Wang, X.; Huang, H.; Chen, R.; Jiang, Y.; Singh, A.K.; Yang, M.; Huang, L. Detection of Thermal Covert Channel Attacks Based on Classification of Components of the Thermal Signal Features. IEEE Trans. Comput. 2022, 1–14. [Google Scholar] [CrossRef]
- Dofe, J.; Yu, Q.; Wang, H.; Salman, E. Hardware Security Threats and Potential Countermeasures in Emerging 3D ICs. In Proceedings of the Great Lakes Symposium on VLSI, Boston, MA, USA, 18–20 May 2016; pp. 69–74. [Google Scholar]
- Xie, Y.; Bao, C.; Serafy, C.; Lu, T.; Srivastava, A.; Tehranipoor, M. Security and vulnerability implications of 3D ICs. IEEE Trans. Multi-Scale Comput. Syst. 2016, 2, 108–122. [Google Scholar] [CrossRef]
- Yan, C.; Dofe, J.; Kontak, S.; Yu, Q.; Salman, E. Hardware-efficient logic camouflaging for monolithic 3D ICs. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 799–803. [Google Scholar] [CrossRef]
- Dofe, J.; Yan, J.; Kontak, S.; Salman, E.; Yu, Q. Transistor-level camouflaged logic locking method for monolithic 3D IC security. In Proceedings of the IEEE Asian Hardware-Oriented Security and Trust, Yilan, Taiwan, 19–20 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Gu, P.; Stow, D.; Barnes, R.; Kursun, E.; Xie, Y. Thermal-aware 3D design for side-channel information leakage. In Proceedings of the IEEE International Conference on Computer Design, Scottsdale, AZ, USA, 2–5 October 2016; pp. 520–527. [Google Scholar] [CrossRef]
- Knechtel, J.; Sinanoglu, O. On mitigation of side-channel attacks in 3D ICs: Decorrelating thermal patterns from power and activity. In Proceedings of the ACM/EDAC/IEEE Design Automation Conference, Austin, TX, USA, 18–22 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Xie, Y.; Bao, C.; Liu, Y.; Srivastava, A. 2.5 D/3D integration technologies for circuit obfuscation. In Proceedings of the 2016 17th International Workshop on Microprocessor and SOC Test and Verification (MTV), Austin, TX, USA, 12–13 December 2016; pp. 39–44. [Google Scholar]
- Wang, W.C.; Wu, Y.; Gupta, P. Reverse engineering for 2.5-D split manufactured ICs. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2019, 39, 3128–3133. [Google Scholar] [CrossRef]
- Nabeel, M.; Ashraf, M.; Patnaik, S.; Soteriou, V.; Sinanoglu, O.; Knechtel, J. 2.5 D root of trust: Secure system-level integration of untrusted chiplets. IEEE Trans. Comput. 2020, 69, 1611–1625. [Google Scholar] [CrossRef]
- Dhananjay, K.; Shukla, P.; Pavlidis, V.F.; Coskun, A.; Salman, E. Monolithic 3D Integrated circuits: Recent trends and future prospects. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 837–843. [Google Scholar] [CrossRef]
- Khan, M.S.M.; Xi, C.; Khan, A.A.; Rahman, M.T.; Tehranipoor, M.M.; Asadizanjani, N. Secure Interposer-Based Heterogeneous Integration. IEEE Des. Test 2022, 39, 156–164. [Google Scholar] [CrossRef]
- Zhang, Y.; Hossen, M.O.; Bakir, M.S. Power delivery network benchmarking for interposer and bridge-chip-based 2.5-D integration. IEEE Electron Device Lett. 2017, 39, 99–102. [Google Scholar] [CrossRef]
- Islam, N.; Tan, K.; Yoon, S.W.; Chen, T. High density ultra-thin organic substrates for advanced flip chip packages. In Proceedings of the 2019 IEEE 69th Electronic Components and Technology Conference (ECTC), Las Vegas, NV, USA, 28–31 May 2019; pp. 325–329. [Google Scholar]
- Coudrain, P.; Charbonnier, J.; Garnier, A.; Vivet, P.; Vélard, R.; Vinci, A.; Ponthenier, F.; Farcy, A.; Segaud, R.; Chausse, P.; et al. Active interposer technology for chiplet-based advanced 3D system architectures. In Proceedings of the 2019 IEEE 69th Electronic Components and Technology Conference (ECTC), Las Vegas, NV, USA, 28–31 May 2019; pp. 569–578. [Google Scholar]
- Liu, C.C.; Chen, S.M.; Kuo, F.W.; Chen, H.N.; Yeh, E.H.; Hsieh, C.C.; Huang, L.H.; Chiu, M.Y.; Yeh, J.; Lin, T.S.; et al. High-performance integrated fan-out wafer level packaging (InFO-WLP): Technology and system integration. In Proceedings of the 2012 International Electron Devices Meeting, San Francisco, CA, USA, 10–13 December 2012; pp. 14.1.1–14.1.4. [Google Scholar]
- Lau, J.H. Recent advances and trends in advanced packaging. IEEE Trans. Compon. Packag. Manuf. Technol. 2022, 12, 228–252. [Google Scholar] [CrossRef]
- Hsu, V. 2.5 D & 3DIC Advanced Packaging: An EDA Perspective. In Proceedings of the 2022 International Symposium on VLSI Design, Automation and Test (VLSI-DAT), Hsinchu, Taiwan, 18–21 April 2022; pp. 1–2. [Google Scholar]
- Li, T.; Hou, J.; Yan, J.; Liu, R.; Yang, H.; Sun, Z. Chiplet heterogeneous integration technology—Status and challenges. Electronics 2020, 9, 670. [Google Scholar] [CrossRef]
- Lee, F.J.; Wong, M.; Tzou, J.; Yuan, J.; Chang, D.; Rusu, S. Heterogeneous System-Level Package Integration—Trends and Challenges. In Proceedings of the 2020 IEEE Symposium on VLSI Technology, Honolulu, HI, USA, 16–19 June 2020; pp. 1–2. [Google Scholar]
- Hutner, M.; Sethuram, R.; Vinnakota, B.; Armstrong, D.; Copperhall, A. Special session: Test challenges in a chiplet marketplace. In Proceedings of the 2020 IEEE 38th VLSI Test Symposium (VTS), San Diego, CA, USA, 5–8 April 2020; pp. 1–12. [Google Scholar]
- Stow, D.; Xie, Y.; Siddiqua, T.; Loh, G.H. Cost-effective design of scalable high-performance systems using active and passive interposers. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; pp. 728–735. [Google Scholar]
- Chi, C.C.; Marinissen, E.J.; Goel, S.K.; Wu, C.W. Post-bond testing of 2.5 D-SICs and 3D-SICs containing a passive silicon interposer base. In Proceedings of the 2011 IEEE International Test Conference, Anaheim, CA, USA, 20–22 September 2011; pp. 1–10. [Google Scholar]
- Bolsens, I.; Xilinx, C. 2.5 D ICs: Just a stepping stone or a long term alternative to 3D. Keynote Talk. 2011. Available online: https://www.xilinx.com/publications/about/3-D_Architectures.pdf (accessed on 19 December 2022).
- Intel® Stratix® 10 FPGA and SoC FPGA. Available online: https://www.intel.com/content/www/us/en/products/details/fpga/stratix/10.html (accessed on 19 December 2022).
- Giechaskiel, I.; Rasmussen, K.; Szefer, J. Reading between the dies: Cross-SLR covert channels on multi-tenant cloud FPGAs. In Proceedings of the 2019 IEEE 37th International Conference on Computer Design (ICCD), Abu Dhabi, United Arab Emirates, 17–20 November 2019; pp. 1–10. [Google Scholar]
- Shukla, P.; Coskun, A.K.; Pavlidis, V.F.; Salman, E. An overview of thermal challenges and opportunities for monolithic 3D ICs. In Proceedings of the 2019 on Great Lakes Symposium on VLSI, New York, NY, USA, 9–11 May 2019; pp. 439–444. [Google Scholar]
- Bahmani, R.; Brasser, F.; Dessouky, G.; Jauernig, P.; Klimmek, M.; Sadeghi, A.R.; Stapf, E. {CURE}: A Security Architecture with {CUstomizable} and Resilient Enclaves. In Proceedings of the USENIX Security Symposium (USENIX Security 21), Online, 11–13 August 2021; pp. 1073–1090. [Google Scholar]
- Costan, V.; Lebedev, I.; Devadas, S. Secure processors part I: Background, taxonomy for secure enclaves and Intel SGX architecture. Found. Trends® Electron. Des. Autom. 2017, 11, 1–248. [Google Scholar] [CrossRef]
- Brasser, F.; Gens, D.; Jauernig, P.; Sadeghi, A.R.; Stapf, E. SANCTUARY: ARMing TrustZone with User-space Enclaves. In Proceedings of the Network and Distributed Systems Security (NDSS) Symposium 2019, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Vivet, P.; Guthmuller, E.; Thonnart, Y.; Pillonnet, G.; Moritz, G.; Miro-Panades, I.; Fuguet, C.; Durupt, J.; Bernard, C.; Varreau, D.; et al. 2.3 A 220GOPS 96-Core Processor with 6 Chiplets 3D-Stacked on an Active Interposer Offering 0.6 ns/mm Latency, 3Tb/s/mm2 Inter-Chiplet Interconnects and 156 mW/mm 2@ 82%-Peak-Efficiency DC-DC Converters. In Proceedings of the 2020 IEEE International Solid-State Circuits Conference-(ISSCC), San Francisco, CA, USA, 16–20 February 2020; pp. 46–48. [Google Scholar]
- Kim, J.; Murali, G.; Park, H.; Qin, E.; Kwon, H.; Chekuri, V.C.K.; Rahman, N.M.; Dasari, N.; Singh, A.; Lee, M.; et al. Architecture, chip, and package codesign flow for interposer-based 2.5-D chiplet integration enabling heterogeneous IP reuse. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 2424–2437. [Google Scholar] [CrossRef]
- Bhasin, S.; Graba, T.; Danger, J.L.; Najm, Z. A look into SIMON from a side-channel perspective. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014; pp. 56–59. [Google Scholar]
- Das, D.; Maity, S.; Nasir, S.B.; Ghosh, S.; Raychowdhury, A.; Sen, S. High efficiency power side-channel attack immunity using noise injection in attenuated signature domain. In Proceedings of the 2017 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Mclean, VA, USA, 1–5 May 2017; pp. 62–67. [Google Scholar]
- Güneysu, T.; Moradi, A. Generic side-channel countermeasures for reconfigurable devices. In Cryptographic Hardware and Embedded Systems—CHES 2011: 13th International Workshop, Nara, Japan, September 28–1 October 2011. Proceedings 13; Springer: Berlin/Heidelberg, Germany, 2011; pp. 33–48. [Google Scholar]
- Seo, D.H.; Nath, M.; Das, D.; Chatterjee, B.; Ghosh, S.; Sen, S. PG-CAS: Patterned-ground co-planar capacitive asymmetry sensing for mm-range em side-channel attack probe detection. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Republic of Korea, 22–28 May 2021; pp. 1–5. [Google Scholar]
- Seo, D.H.; Nath, M.; Das, D.; Ghosh, S.; Sen, S. Improved EM Side-Channel Analysis Attack Probe Detection Range utilizing Co-planar Capacitive Asymmetry Sensing. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2023. [Google Scholar] [CrossRef]
- Kenarangi, F.; Partin-Vaisband, I. Exploiting machine learning against on-chip power analysis attacks: Tradeoffs and design considerations. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 66, 769–781. [Google Scholar] [CrossRef]
- Utyamishev, D.; Partin-Vaisband, I. Real-time detection of power analysis attacks by machine learning of power supply variations on-chip. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2018, 39, 45–55. [Google Scholar] [CrossRef]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Miketic, I.; Dhananjay, K.; Salman, E. Covert Channel Communication as an Emerging Security Threat in 2.5D/3D Integrated Systems. Sensors 2023, 23, 2081. https://doi.org/10.3390/s23042081
Miketic I, Dhananjay K, Salman E. Covert Channel Communication as an Emerging Security Threat in 2.5D/3D Integrated Systems. Sensors. 2023; 23(4):2081. https://doi.org/10.3390/s23042081
Chicago/Turabian StyleMiketic, Ivan, Krithika Dhananjay, and Emre Salman. 2023. "Covert Channel Communication as an Emerging Security Threat in 2.5D/3D Integrated Systems" Sensors 23, no. 4: 2081. https://doi.org/10.3390/s23042081
APA StyleMiketic, I., Dhananjay, K., & Salman, E. (2023). Covert Channel Communication as an Emerging Security Threat in 2.5D/3D Integrated Systems. Sensors, 23(4), 2081. https://doi.org/10.3390/s23042081








