Hybrid-AI-Based iBeacon Indoor Positioning Cybersecurity: Attacks and Defenses
Abstract
:1. Introduction
1.1. iBeacon-Related Mechanisms
1.1.1. iBeacon
1.1.2. Eddystone Protocol
1.1.3. LINE Beacon
1.1.4. Advanced Encryption Standard (AES)
1.2. Related Work
1.2.1. Recent Applications of RFID
1.2.2. Safety Promotion of iBeacon
1.2.3. Information Security Challenges of iBeacon
2. Materials and Methods
2.1. iBeacon System Design Architecture
2.2. Positioning Algorithms
2.2.1. Initial Stage
2.2.2. Estimate Stage
2.2.3. Regression Stage
2.3. Hybrid-AI-Based Positioning Algorithm
3. Results
3.1. Possible Attacks
3.1.1. Recording and Use
- Any mobile phone which has a BLE protocol can receive and decode the message from the iBeacon system, meaning any mobile application that can obtain the Beacon broadcasts is able to position the mobile phone. Therefore, hackers may use such a channel to leak the positioning information. That is, a hacker may walk in the field holding a smartphone to fetch field Beacon codes (ID). Any attacker may enter the field open to the public to obtain data without obtaining any permission beforehand.
- By writing this information into the APP, identification may be mounted to nearby devices without the owner’s agreement. This may leak the user’s location information to the public, making the entire system a target vulnerable to hacker attacks.
- Company A, investing a huge amount of capital in the deployment of 1000 Beacons at an airport, would like to recover its investment from the location-based service (LBS) provided. However, it is unable to achieve this once the system is utilized by Company A’s competitor. In fact, Company A’s competitor may assign one person to walk into the field holding a smartphone. Then, this person can gain access to this system without prior notice to Company A or without receiving usage agreement from Company A.
3.1.2. Impersonation Attack
3.1.3. Obfuscation Attack
3.1.4. Recording and Limited Reproduction
3.2. Beacon System Defense Methods
3.2.1. Data Encryption/Decryption
sent is converted to AES Code AES(fa).
indicating location A).
code indicating location B).
- a.
- Impersonation: Assuming that the user only wants to create the illusion of “I am somewhere” (such as for roll call at work, or for the application location service, which is used at Taipei Main Station), a hacker only needs to copy one iBeacon to confuse the system. Assuming that there is no protection, the hacker only takes 1.5 min to copy the position of one iBeacon and carry out an impersonation attack.
- b.
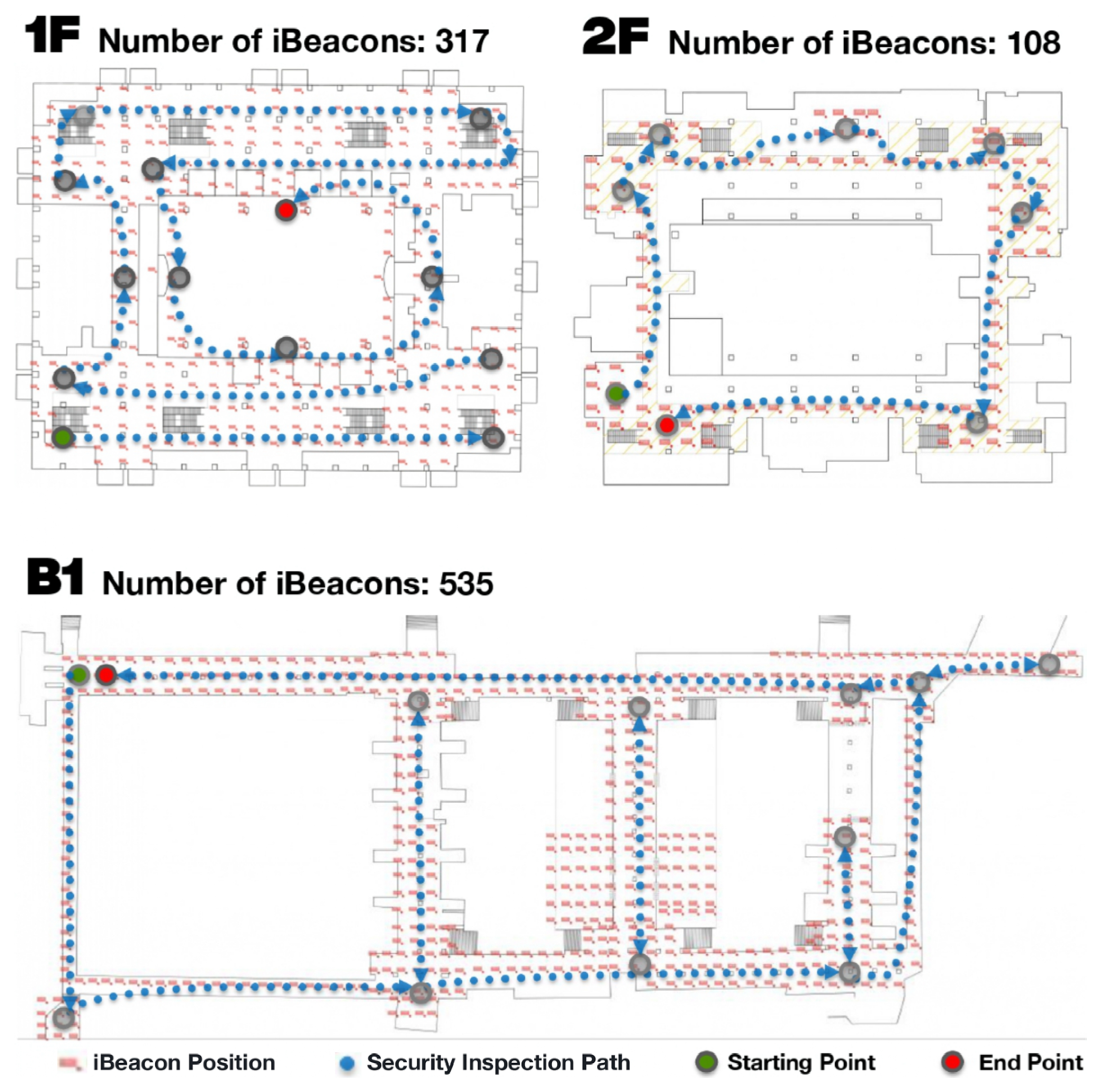
- Obfuscation: If a hacker wants to interfere with the data, he/she needs to make 5%, that is, 535 × 5% = 27 fake iBeacon positions, which can interfere with the system operation at a large scale. Assuming that there is no protection, the hacker takes 40.5 min to carry out an obfuscation attack.
- c.
- Recording and use: The hacker must record all iBeacon–location relationships before establishing a new system. Assuming that there is no protection, the hacker takes 802.5 min (30 min for one iBeacon) to create a new fake iBeacon system.
3.2.2. Rolling Coding
- Unpredictable Rolling Coding
- Whether the code is shown at a preset reasonable number of digits, e.g., between 1 and 100, which means that the code between 1 and 100 is normal. If the Beacon code exceeds 100, it means that the system has been illegally recorded and is subjected to an impersonation attack or obfuscation attack.
- Random variable being a random value
- Assuming that the hacker has copied three random codes of Beacon location A, if the server S has been hacked and duplicate random in AES (code, random) are found (for example, if the Beacon has 4 codes, all of which are 100), the fake Beacon from the hacker will be found; then, all AES (code, random) is subject to comparison, plus the time stamp T when they are launched, i.e., AES (code, random)∥T, denoted by R, is sent to a mobile phone. On receiving R, this mobile phone sends R to server S to verify whether Τ – Τ′ ≤ ΔΤ, where T′ is the time stamp when S receives R, and ΔT is the longest time for a message to travel from a Beacon to S. The purpose is to confirm whether a replay attack has been triggered.
- (1)
- Recording and use attack: Following the decoding of false messages which are recorded, it can be discovered that its random value is same as the random value in the original message. For example, hackers record all iBeacon system codes and store them for eventual transmission of false information or to broadcast his/her own advertisement using this iBeacon system. The random values of several messages will be the same, and this type of attack may therefore be detected.
- (2)
- Impersonation attack: If an iBeacon issues two messages in which the iBeacon codes are the same, e.g., both are 56, the ciphertexts generated will be different since the random values of the two messages vary. If a recorded ciphertext is broadcast N times, N ≧ 2, it remains unchanged. For example, user C passes by a location and user D, who passes by the same location after 10 min, receives the identical ciphertext AES (code, random) sent by the same iBeacon. This means that what C or D receives is the ciphertext recorded and sent by a hacker. It can therefore be detected that this iBeacon has been subjected to an impersonation attack by a hacker.
- (3)
- Obfuscation attack: As per that described for the impersonation attack, N AES (code, random) that S received via the same or different mobile phones are identical, N ≧ 2, indicating that the random values of multiple false Beacons are the same as under an impersonation attack. For example, if N iBeacon-code AES (code, random) received by user E passing by a location is identical to that received by user F, who passed by the same location 10 min later, it shows that this iBeacon has been subjected to an obfuscation attack.The contents of legal messages are constantly changing due to the change in the random variable. In fact, the impersonation and obfuscation attacks mentioned above only record “the same group of messages” or “N groups of messages, where N ≥ 2”. Therefore, the server would detect that the Beacon is under the abovementioned attack and disable this iBeacon’s false message broadcast.
- (4)
- Recording and limited reproduction: Assuming that the user, without knowing the coding mechanism, directly recorded m groups of messages, m < n, where n is the number of iBeacons, if the unpredictable and encrypted rolling coding method was adopted, the data received by the server S of this system could not be applied to identify whether the message was false or legal. However, as the server may detect duplicate random values from the decoded message, S will discover that the Beacon has been subjected to an impersonation or obfuscation attack.
- a.
- Impersonation: Hacker takes 1500 min to copy the location of one iBeacon and carry out an impersonation attack.
- b.
- Obfuscation: Hacker takes 40,500 min to crack 27 iBeacons and interfere with the iBeacon system.
- c.
- Recording and Use: Hacker takes 802,500 min (30 min for one iBeacon) to crack 535 iBeacons to create a new fake iBeacon system.
- 2.
- Predictable and Encrypted Rolling Coding Method
- a.
- Impersonation: Hacker takes 1500 min to copy the location of one iBeacon and carry out an impersonation attack.
- b.
- Obfuscation: Hacker takes 40,500 min to crack 27 iBeacons and interfere with the iBeacon system.
- c.
- Recording and use: Hacker takes 802,500 min (30 min for one iBeacon) to crack 535 iBeacons to create a new fake iBeacon system.
- 3.
- Personnel Inspection
- 4.
- App Active Monitoring
- (1)
- Recording and Use Experiment
- (2)
- Impersonation Attack Experiment
- (3)
- Obfuscation Attack Experiment
- (4)
- Recording and Limited Reproduction Experiment
- 5.
- iBeacon Attack and Defense Comparison Experiment
4. Conclusions and Future Studies
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kao, C.L. The Application of Beacon Micro Positioning Technology. Arch. Semiannu. 2021, 20, 88–97. [Google Scholar]
- Verified Market Research, Bluetooth Beacon and iBeacon Market Size, Opportunities & Forecast. Available online: https://www.verifiedmarketresearch.com/product/bluetooth-beacon-and-ibeacon-market/ (accessed on 16 July 2022).
- Liaw, J.J.; Chen, K.L.; Huang, T.C.; Cheng, Y.H. The Simulation of the Indoor Positioning by Panoramic Camera and Point Cloud Scanner. In Mobile and Wireless Technology; Springer: Singapore, 2018; 513p. [Google Scholar] [CrossRef]
- Qiu, C.; Hussain, B.; Yue, C.P. Bluetooth Based Wireless Control for iBeacon and VLC Enabled Lighting. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 15–18 October 2019; pp. 614–615. [Google Scholar] [CrossRef]
- Senthazhai, M.S.; Keerthika, B.; Sathya, S. An Innovative Wearable Device for Women Safety Using IBEACON Technology with BLE. Int. J. Res. Eng. Sci. 2022, 10, 653–657. [Google Scholar]
- Gan, C.C.; Lee, Y.J. enRoute: An Indoor Navigation Application Using Digital Signage. Sens. Mater. 2022, 34, 523–531. [Google Scholar] [CrossRef]
- Liu, Q.; Yang, X.; Deng, L. An IBeacon-Based Location System for Smart Home Control. Sensors 2018, 18, 1897. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.W.; Chen, T.P.; Weng, C.C. iBaby: A Mobile Children Monitoring and Finding System with Stranger Holding Detection Based on IoT Technologies. In Proceedings of the ACM SIGCOMM 2019 Conference Posters and Demos, Beijing China, 19–23 August 2019; pp. 66–68. [Google Scholar] [CrossRef]
- Chantaweesomboon, W. Bluetooth Geo-Fence for Elderly and Patient Care. In Proceedings of the 2021 25th International Computer Science and Engineering Conference (ICSEC), Chiang Rai, Thailand, 18–20 November 2021; pp. 252–255. [Google Scholar] [CrossRef]
- Qu, M.; Sun, Y. An IoT-Based Crowd Sourcing System for Object Tracking and Information Sharing. Int. J. Artif. Intell. Appl. 2019, 10, 47–54. [Google Scholar] [CrossRef]
- Meliones, A.; Sampson, D. Blind MuseumTourer: A System for Self-Guided Tours in Museums and Blind Indoor Navigation. Technologies 2018, 6, 4. [Google Scholar] [CrossRef]
- Kwok, C.Y.T.; Wong, M.S.; Griffiths, S.; Wong, F.Y.Y.; Kam, R.; Chin, D.C.W.; Xiong, G.; Mok, E. Performance Evaluation of iBeacon Deployment for Location-Based Services in Physical Learning Spaces. Appl. Sci. 2020, 10, 7126. [Google Scholar] [CrossRef]
- Zhao, Z.H.; Zhang, M.D.; Yang, C.; Fang, J.; Huang, G.Q. Distributed and collaborative proactive tandem location tracking of vehicle products for warehouse operations. Comput. Ind. Eng. 2018, 125, 637–648. [Google Scholar] [CrossRef]
- Spachos, P.; Plataniotis, K. Beacons and the City: Smart Internet of Things. In Cooperative and Graph Signal Processing: Principles and Applications, 1st ed.; Djurić, P.M., Richard, C., Eds.; Academic Press: Cambridge, MA, USA, 2018; pp. 757–776. [Google Scholar] [CrossRef]
- Chan, A.C.-F.; Chung, R.M.H. Security and Privacy of Wireless Beacon Systems. Cornell University. arXiv 2021, arXiv:2107.05868. [Google Scholar] [CrossRef]
- Huang, K.H. Beacon Application for Museum Indoor Positioning System: A Case Study of National Museum of Taiwan History. J. Mus. Cult. 2018, 15, 5–29. [Google Scholar]
- Yen, P.Y.; Fanjiang, Y.Y.; Hung, C.H.; Zhang, T.M. Design and Implement a Roll Call System with Body Temperature Measurement and the Instant Messaging Software. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–12 January 2021. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, X. Pipelined implementation of AES encryption based on FPGA. In Proceedings of the 2010 IEEE International Conference on Information Theory and Information Security, Beijing, China, 17–19 December 2010; pp. 170–173. [Google Scholar] [CrossRef]
- Biswal, A.K.; Jenamani, M.; Kumar, S.K. Warehouse efficiency improvement using RFID in a humanitarian supply chain: Implications for Indian food security system. Transp. Res. Part E Logist. Transp. Rev. 2018, 109, 205–224. [Google Scholar] [CrossRef]
- Jha, R.K.; Srivastav, V.; Sumbli, V.; Trisha; Gandhi, V.; Jain, S. RFID based food rationing system. HardwareX 2018, 4, 1–13. [Google Scholar] [CrossRef]
- Kant, R.; Samadder, S.; Srivastav, P.P.; Pathak, S.S.; Datta, A.K. Development and evaluation of low-cost frequency based sensor for non-destructive detection of Paneer spoilage. J. Biochem. Technol. 2018, 9, 10–15. [Google Scholar]
- Testud, G.; Vergnes, A.; Cordier, P.; Labarraque, D.; Miaud, C. Automatic detection of small PIT-tagged animals using wildlife crossings. Anim. Biotelemetry 2019, 7, 21. [Google Scholar] [CrossRef]
- Tomanova, S.; Courret, D.; Alric, A.; De Oliveira, E.; Lagarrigue, T.; Tetard, S. Protecting efficiently sea-migrating salmon smolts from entering hydropower plant turbines with inclined or oriented low bar spacing racks. Ecol. Eng. 2018, 122, 143–152. [Google Scholar] [CrossRef]
- Bouletreau, S.; Carry, L.; Meyer, E.; Filloux, D.; Menchi, O.; Mataix, V.; Santoul, F. High predation of native sea lamprey during spawning migration. Sci. Rep. 2020, 10, 6122. [Google Scholar] [CrossRef] [PubMed]
- Mohammedi, M.; Omar, M.; Bouabdallah, A. Secure and lightweight remote patient authentication scheme with biometric inputs for mobile healthcare environments. J. Ambient. Intell. Humaniz. Comput. 2018, 9, 1527–1539. [Google Scholar] [CrossRef]
- Mikhailovskaya, A.; Shakirova, D.; Krasikov, S.; Yusupov, I.; Dobrykh, D.; Slobozhanyuk, A.; Bogdanov, A.; Filonov, D.; Ginzburg, P. Anapole-enabled RFID security against far-field attacks. Nanophotonics 2021, 10, 4409–4418. [Google Scholar] [CrossRef]
- Shariq, M.; Singh, K.; Bajuri, M.Y.; Pantelous, A.A.; Ahmadian, A.; Salimi, M. A secure and reliable RFID authentication protocol using digital schnorr cryptosystem for IoT-enabled healthcare in COVID-19 scenario. Sustain. Cities Soc. 2021, 75, 103354. [Google Scholar] [CrossRef] [PubMed]
- Bai, D.T.; Zhang, J.N.; Pan, Y. Research on the principle and technology of indoor positioning navigation escape rescue system. Fire Sci. Technol. 2018, 37, 1560–1563. [Google Scholar]
- Chen, L.W.; Liu, J.X. EasyFind: A Mobile Crowdsourced Guiding System with Lost Item Finding Based on IoT Technologies. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 343–345. [Google Scholar] [CrossRef]
- Chen, L.W.; Liu, J.X. Time-Efficient Indoor Navigation and Evacuation With Fastest Path Planning Based on Internet of Things Technologies. In IEEE Transactions on Systems, Man, and Cybernetics: Systems; IEEE: Piscataway, NJ, USA, 2019; Volume 51, pp. 3125–3135. [Google Scholar] [CrossRef]
- Liu, Y.; Hong, W.; Peng, J.; Xue, Z. Design of childern’s knitting security clothing based on micro-location of iBeacon technology. Wool Text. J. 2017, 45, 47–51. [Google Scholar] [CrossRef]
- Lu, H.K.; Lin, P.C.; Chu, K.C.; Chen, A.N.; Yuan, A. Development and evaluation of a Beacon-based indoor positioning and navigating system for the visually impaired. J. Intell. Fuzzy Syst. 2019, 37, 4665–4675. [Google Scholar] [CrossRef]
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O.B. Internet of Things (IoT): Taxonomy of Security Attacks. In Proceedings of the 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, 11–12 August 2016; pp. 321–326. [Google Scholar] [CrossRef]
- Maitra, S.; Yelamarthi, K. Rapidly Deployable IoT Architecture with Data Security: Implementation and Experimental Evaluation. Sensors 2019, 19, 2484. [Google Scholar] [CrossRef] [PubMed]
- Ang, K.L.M.; Jasmine Kah, P.S.; Ngharamike, E. Towards Crowdsourcing Internet of Things (Crowd-IoT): Architectures, Security and Applications. Future Internet 2022, 14, 49. [Google Scholar] [CrossRef]
- Mukherjee, B.; Neupane, R.L.; Calyam, P. End-to-end IoT security middleware for cloud-fog communication. In Proceedings of the 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud), New York, NY, USA, 26–28 June 2017; pp. 151–156. [Google Scholar] [CrossRef]
- Tay, H.J.; Tan, J.; Narasimhan, P. A Survey of Security Vulnerabilities in Bluetooth Low Energy Beacons; Tech. Report. CMU-PDL-16-109; Parallel Data Laboratory, Carnegie Mellon University: Pittsburgh, PA, USA, 2016. [Google Scholar]
- Lacava, A.; Zottola, V.; Bonaldo, A.; Cuomo, F.; Basagni, S. Securing Bluetooth Low Energy networking: An overview of security procedures and threats. Comput. Netw. 2022, 211, 108953. [Google Scholar] [CrossRef]
- Yang, Q.; Huang, L. Bluetooth Security. In Inside Radio: An Attack and Defense Guide, 1st ed.; Springer: Singapore, 2018; pp. 195–226. [Google Scholar] [CrossRef]
- Campos-Cruz, K.J.; Mancillas-López, C.; Ovilla-Martinez, B. A Lightweight Security Protocol for Beacons BLE. In Proceedings of the 2021 18th International Conference on Electrical Engineering, Computing Science and Automatic Control (CCE), Mexico City, Mexico, 10–12 November 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Na, X.; Guo, X.; He, Y.; Xi, R. Wi-attack: Cross-technology Impersonation Attack against iBeacon Services. In Proceedings of the 2021 18th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Rome, Italy, , 6–9 July 2021; pp. 1–9. [Google Scholar] [CrossRef]
- Department of Budget, Accounting and Statistics, Taipei City Government. Available online: https://dbas.gov.taipei/News_Content.aspx?n=61D456768E73CD92&sms=72544237BBE4C5F6&s=45E047F8D9E61B46 (accessed on 7 July 2022).
- Kok, M.; Hol, J.D.; Sch, T.B. Using Inertial Sensors for Position and Orientation Estimation. Found. Trends Signal Process. 2017, 11, 1–153. [Google Scholar] [CrossRef]
- Chang, S.W.; Huang, H.H.; Su, P.C. Taipei Smart Station System Applications. Urban Traffic Biannu. 2018, 33, 27–35. [Google Scholar]
- Hu, J.; Qian, S.; Fang, Q.; Wang, Y.; Zhao, Q.; Zhang, H.; Xu, C. Efficient Graph Deep Learning in TensorFlow with tf_geometric. In Proceedings of the 29th ACM International Conference on Multimedia, New York, NY, USA, 20–24 October 2021; pp. 3775–3778. [Google Scholar] [CrossRef]
- Sun, M.; Kamoto, K.M.; Liu, Q.; Liu, X.; Qi, L. Application of Bluetooth Low Energy Beacons and Fog Computing for Smarter Environments in Emerging Economies. In Proceedings of the Cloud Computing, Smart Grid and Innovative Frontiers in Telecommunications: International Conference on Cloud Computing, Beijing, China, 4–5 December 2019; pp. 101–110. [Google Scholar] [CrossRef]
- LINE Developers. n.d., LINE Beacon Device Specification. Available online: https://developers.line.biz/en/docs/messaging-api/beacon-device-spec/ (accessed on 19 July 2022).
- Anathi, M.; Vijayakumar, K. An intelligent approach for dynamic network traffic restriction using MAC address verification. Comput. Commun. 2020, 154, 559–564. [Google Scholar] [CrossRef]
















| Attack Type/Defense Method | No Defense | Rolling Coding | Predictable and Encrypted Rolling Coding Method |
|---|---|---|---|
| Impersonation (1 iBeacon) | 1.5 min | 1500 min | 1500 min |
| Obfuscation (27 iBeacons) | 40.5 min | 40,500 min | 40,500 min |
| Recording and Use (535 iBeacons) | 802.5 min | 802,500 min | 802,500 min |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, C.-J.; Chi, C.-J.; Hung, W.-T. Hybrid-AI-Based iBeacon Indoor Positioning Cybersecurity: Attacks and Defenses. Sensors 2023, 23, 2159. https://doi.org/10.3390/s23042159
Huang C-J, Chi C-J, Hung W-T. Hybrid-AI-Based iBeacon Indoor Positioning Cybersecurity: Attacks and Defenses. Sensors. 2023; 23(4):2159. https://doi.org/10.3390/s23042159
Chicago/Turabian StyleHuang, Chi-Jan, Cheng-Jan Chi, and Wei-Tzu Hung. 2023. "Hybrid-AI-Based iBeacon Indoor Positioning Cybersecurity: Attacks and Defenses" Sensors 23, no. 4: 2159. https://doi.org/10.3390/s23042159
APA StyleHuang, C.-J., Chi, C.-J., & Hung, W.-T. (2023). Hybrid-AI-Based iBeacon Indoor Positioning Cybersecurity: Attacks and Defenses. Sensors, 23(4), 2159. https://doi.org/10.3390/s23042159






