Abstract
As medical data become increasingly important in healthcare, it is crucial to have proper access control mechanisms, ensuring that sensitive data are only accessible to authorized users while maintaining privacy and security. Ciphertext-Policy Attribute-Based Encryption (CP-ABE) is an attractive access control solution that can offer effective, fine-grained and secure medical data sharing, but it has two major drawbacks: Firstly, decryption is computationally expensive for resource-limited data users, especially when the access policy has many attributes, limiting its use in large-scale data-sharing scenarios. Secondly, existing schemes are based on data users’ attributes, which can potentially reveal sensitive information about the users, especially in healthcare data sharing, where strong privacy and security are essential. To address these issues, we designed an improved CP-ABE scheme that provides efficient and verifiable outsourced access control with fully hidden policy named EVOAC-HP. In this paper, we utilize the attribute bloom filter to achieve policy hiding without revealing user privacy. For the purpose of alleviating the decryption burden for data users, we also adopt the technique of outsourced decryption to outsource the heavy computation overhead to the cloud service provider (CSP) with strong computing and storage capabilities, while the transformed ciphertext results can be verified by the data user. Finally, with rigorous security and reliable performance analysis, we demonstrate that EVOAC-HP is both practical and effective with robust privacy protection.
1. Introduction
The rapid advancement of medical technology has revolutionized the healthcare industry, and one of its most significant impacts is the increasing prevalence of electronic health record (EHR) systems, replacing traditional paper-based medical records [1,2]. The adoption of EHRs has facilitated the real-time management and sharing of medical records for both doctors and patients. Additionally, healthcare practitioners can now access data more easily, enabling them to make more comprehensive diagnoses. With the emergence of 5G, cloud computing and big data, cloud-assisted EHR systems have become popular for outsourcing medical record management to the CSP and reducing management overhead. However, concerns about security and privacy arise when storing sensitive medical record data on cloud servers. Additionally, traditional encryption methods cannot achieve fine-grained data sharing and access. Access to such data without authorization can result in serious consequences, including identity theft, insurance fraud, and even the endangering of patient lives. Therefore, it is crucial to design robust security mechanisms for protecting medical data stored in the cloud [3]. To ensure data confidentiality and fine-grained access control to sensitive EHR data, Attribute-Based Encryption (ABE) was introduced as an appropriate encryption solution [4].
CP-ABE, proposed by Bethencourt et al. [5], provides a flexible way for data owners to specify their own access control policies. This is achieved by linking a ciphertext to an access policy defined by the user and associating a user’s secret key with a set of attributes. As a result, only users whose attributes satisfy the access policy can decrypt the ciphertext and access the data. However, existing CP-ABE schemes [5,6,7] may not meet security and privacy requirements. Firstly, the access policy that is associated with the ciphertext can be viewed publicly, which means that anyone can obtain useful sensitive private data and expose confidential details regarding the encrypted EHR data, which can result in the exposure of the identity and attributes of medical practitioners or patients, thus compromising their privacy [8]. In addition, those existing schemes have the disadvantage of having a linear increase in ciphertext size and decryption overhead with the number of attributes in the access policy, which can be a significant limitation for resource-limited users [9]. As more attributes are added to the policy, both the ciphertext size and decryption overhead grow proportionally. This can make it difficult or even impossible for users with limited resources to decrypt and access the data that they need in a timely manner. Furthermore, this linear growth in ciphertext size can increase the cost of storing and transmitting the encrypted data, as well as the computational overhead associated with performing encryption and decryption operations. Thus, these CP-ABE schemes may not be suitable for applications that require efficient access control and low computational overhead.
Some existing works have been proposed to address these issues, such as outsourcing decryption technology [9,10,11,12] to reduce computation overhead for data users or proposing fully or partially hidden access structure schemes [8,13,14] to protect the privacy of user attributes embedded in the access policy. However, these solutions fail to offer a large universe and reliable mechanism with adaptive security, or they lack flexibility and have low efficiency. To tackle these issues, we propose an efficient access control scheme with robust privacy protection and outsourced decryption with verifiability, which builds upon the work [15] with further optimizations. Our main contributions are outlined as follows:
- We designed an efficient and secure fine-grained access control scheme named EVOAC-HP for privacy preserving in the medical data scenario, which supports a large universe, adaptive security and flexible access control structure. This scheme uses the attribute bloom filter to achieve policy hiding, which effectively protects data users’ attribute information.
- We adopted outsourcing decryption technology to outsource complex computation to the CSP and support the verification of the outsourcing results, which largely reduces the computation overhead of data users.
- According to security analysis and performance analysis, EVOAC-HP demonstrated enhanced security and efficiency, which is appropriate for medical data-sharing application scenarios with high privacy requirements.
2. Related Work
Traditional identity-based encryption (IBE) schemes associate encryption keys with specific identities, and decryption is only possible for ciphertexts encrypted under the matching identities [16]. In contrast, fuzzy IBE allows partial matches between the encryption key and the access policy to be performed, which means that ciphertexts can be decrypted by users whose identities only partially match the policy. In order to achieve more fine-grained access control, the notion of ABE, which enables secure encryption and decryption to be achieved without the need for exact identity matching, was first conceived by Sahai and Waters [4]. According to different application scenarios, ABE is divided into Key-Policy Attribute-Based Encryption (KP-ABE) and CP-ABE. In 2006, Goyal et al. [17] proposed the first construction of a scheme that associates attributes with the private keys of the users, mainly used in paid video sites and broadcast encryption. The first CP-ABE scheme proposed by the work [5] allows complex access policies in which attributes are associated with the ciphertext to be used, which is suitable for data sharing. Although this scheme is very expressive, it was proved to be safe under the general group model, and the security of this model is relatively weak. Afterwards, a significant amount of research has been conducted on CP-ABE and KP-ABE in recent years, with various constructions and optimizations proposed to enhance their efficiency and security. Waters [18] proposed an improvement to CP-ABE schemes by introducing a linear secret sharing scheme (LSSS) based on the previous work [5], which results in enhanced efficiency and expressiveness of the encryption scheme while maintaining stronger security. Many CP-ABE schemes have since emerged, including some classic works [6,7,15]. However, as the access policy becomes more complex and the number of user attributes increases, the size of the ciphertext and the computational overhead required for decryption also increase. Since the decryption process can be expensive due to the large size of the ciphertext and the required pairing operations, resource-limited devices may experience significant delay or even have to abort the decryption process.
To address this inefficiency issue, Green et al. [9] introduced the innovative notion of ABE with outsourced decryption (ABE-OD), which allows a CSP to transform any ABE ciphertext of any size into an ElGamal-type ciphertext with a constant size, so that the user only needs to obtain the decrypted message with one exponentiation. One limitation of outsourcing decryption to the CSP is that they may not perform the transformation operations honestly. To address this concern, the work [10] proposed the concept of ABE verifiable outsourced decryption (ABE-VOD), which enables data users to check whether the transformation results are correct. However, this scheme needs to encrypt additional random messages, which doubles the computing overhead of the data user, resulting in twice the size of the ciphertext. This undoubtedly increases the user’s bandwidth requirements and computing costs. Afterward, several efficient and generic ABE-VOD schemes have been proposed [11,19,20,21,22,23,24]. Some works [19,20] also considered performing outsourced key issuing and outsourced decryption operations by introducing two cloud service providers. Mao et al. [11] and Lin et al. [21] proposed an efficient construction using a commitment scheme and an encapsulation mechanism. These ABE schemes have shown great promise in enabling the secure and verifiable outsourced decryption of ciphertexts to be performed in cloud-based environments. While these ABE schemes are well suited to flexible and fine-grained data-sharing systems, they may not be suitable for applications with high privacy requirements, such as EHR systems. This is because the access policy, which typically includes sensitive attribute information, such as the patient’s medical condition and medical history, is directly exposed in the ciphertext. Anyone can obtain some sensitive information with the ciphertext. As a result, malicious adversaries are likely to infer sensitive information about the patient’s health status, potentially leading to privacy breaches and other security risks.
In order to improve the above privacy protection issues, CP-ABE with policy hiding has been researched to address sensitive attribute information exposure in the access policy of traditional CP-ABE schemes. The concept of partially hidden access structures was proposed by Nishide et al. [8] and splits the attribute into an attribute name exposed to the ciphertext and sensitive attribute values hidden within the ciphertext. Nevertheless, this solution only supports the less expressive “AND gates” access structure. Lai et al. [25] proposed a CP-ABE scheme with adaptive security and policy hiding under the standard model, but this scheme is constructed based on bilinear groups of composite order, resulting in low efficiency. Subsequently, several works based on [8,25] have since been proposed to enhance the security, efficiency, flexibility and availability of partially hidden access structure CP-ABE [14,26,27,28,29,30]. However, all these existing schemes can only hide the attribute value but cannot hide the attribute name, and the attribute name itself still leaks some useful information. Therefore, CP-ABE schemes with fully hidden policy are also available, where the access policy is invisible to the data user, ensuring that their attribute sets are not revealed in plaintext. Recently, most of the solutions hide the whole attribute by employing the specified garbled bloom filter [31] to eliminate the attribute mapping function embedded in the access structure and achieve full policy hiding [32,33,34,35,36]. This strategy of policy hiding is well suited to applications with strong privacy requirements. However, these schemes either do not support verifiable outsourced decryption or do not support flexible access structures under the standard model.
Inspired by the works [11,15,32], we propose EVOAC-HP to be applied in EHR systems. Consider a healthcare scenario where a data owner, such as a patient, wants to share their medical records with a data user, such as a doctor, but does not want to allow other doctors or unauthorized users to access the records. To protect privacy, the patient first establishes an access policy for who is allowed to access the records and encrypts the records using CP-ABE before uploading them to a CSP. Then, doctors who meet the defined access policy can successfully decrypt the ciphertext. Note that the private attributes embedded in the access policy do not reveal the identity of the doctors. Since the doctor’s device may be resource-limited, they can request the CSP to transform the ciphertext and obtain the transformed ciphertext for decryption. Finally, the doctor can locally confirm whether the transformed ciphertext is correct to ensure the integrity of the decryption result.
3. Preliminary
In this section, we mainly review the fundamental knowledge about the CP-ABE definition, the security model for the CP-ABE, the commitment scheme, the attribute bloom filter and the decisional linear assumption.
3.1. CP-ABE Definition
A classic CP-ABE scheme is given by the following four algorithms:
- : This algorithm takes the security parameter and attribute universe description U as input, and it outputs a master public key and a master key .
- : This algorithm takes the master key and a set of attributes S, and it outputs a secret decryption key .
- : This algorithm takes the master public key , an access structure over the universe of attributes and a message M, and it outputs a ciphertext .
- : This algorithm takes the master public key , a ciphertext and a secret decryption key , and it outputs a message M or a special symbol ⊥.
3.2. Security Model for CP-ABE
We introduce the security model for the CP-ABE scheme. The security between adversary and challenger is given as follows:
- : defines the challenge access structure and gives it to .
- : runs to obtain the master public key and returns it to .
- : has the ability to request secret keys corresponding to collections of user attributes , . For each , runs and returns to . The queried sets must not meet the access structure requirements of the challenge phase above each query, i.e., .
- : submits two messages, and , with equal length and returns them to . chooses random number and invokes to obtain , which is given to .
- : Phase 1 is reiterated under the same constraint. can continue to query the secret keys for the sets , .
- : outputs his guess value for b.
Definition 1.
A CP-ABE scheme Π is secure if all polynomial-time attackers have at most a negligible advantage in the above security game. The advantage of an attacker for breaking this confidentiality game is defined as .
3.3. Commitment
A commitment scheme has three algorithms: , and .
- : This algorithm takes a security parameter as input and outputs the public commitment key .
- : This algorithm takes a message M and an additional random number r as input and outputs a commitment .
- : This algorithm takes a message M, an additional random number r and a commitment as input and outputs a bit value . If , it indicates that is a valid commitment to M; otherwise, it indicates that is not a commitment to M.
A correct commitment scheme satisfies for all output by the algorithm and for any message M and an additional random number r. If a commitment scheme satisfies the hiding property and the binding property, it is considered secure. The commitment to M satisfies the hiding property, which ensures that no information about M can be inferred from . The binding property ensures that it is computationally infeasible to reveal a commitment to a value other than the original value M.
3.4. Attribute Bloom Filter
The attribute bloom filter (ABF) is a data structure that can efficiently query a large dataset [32]. It is a variant of the bloom filter, where each element is assigned one or more attributes so that it can be filtered and queried by the attribute. During the search stage, one or more attributes can be specified, and only elements with the specified attributes are returned. Unlike traditional bloom filters, the ABF stores an additional attribute vector, where each element corresponds to an attribute vector. Each position in the attribute vector corresponds to an attribute, and if the element has that attribute, the position is set to 1; otherwise, 0. The element is returned during the query stage if all specified attribute positions are 1.
To construct the ABF, a sequence of bits in length is joined with two constant strings: one that includes the row number with bits and another that contains the attribute with bits, where the security parameter . The ABF can be divided into two components: and . These two components are detailed below:
- : This algorithm takes as input an access policy . The attributes and their corresponding row number i involved in access matrix are concatenated, where each row i maps to attribute according to the mapping function , and they are left-padded with zeros to achieve a maximum bit length. The resulting set of elements is used as input in the garbled BF building algorithm to create , as described in [31].When an element needs to be inserted into , this algorithm randomly produces -bit strings and adopts the XOR-based secret sharing scheme to distribute element . It then assigns . Afterward, x independent and uniform hash functions are used to hash attribute to obtain for , where represents the specific index position in . The i-th share of the element is then stored in at the position indicated by the hash function . When adding more elements to , it is possible that a location has already been filled by an element added earlier. In this case, we can repurpose the existing share assigned as a share for the new element.
- : This algorithm takes as input the master public key , an attribute set S and the attribute bloom filter . For each attribute within the attribute set S, the algorithm calculates the position index in with x hash functions. The value stored in the corresponding position can then be retrieved.Once the element shares the that have been stored in , element can be reconstructed using the formula , where is represented as and attribute is derived from the rightmost bits of element . If there are redundant zeros in , they are removed. When matches the attribute specified in the access policy, this implies that attribute exists in the access control policy. Otherwise, attribute is not present in the access policy. Similarly, the row number i is derived from the leftmost L bits of element , and redundant zeros are removed if present. Once and i have been obtained, the attribute mapping can be rebuilt as .
Above all, the algorithm hides the attribute mapping, while the algorithm reconstructs it. This access control structure can allow full policy hiding to be achieved.
3.5. Decisional Linear Assumption
Suppose we have two multiplicative groups, and , of prime number order q and two generators, and . We randomly select and define a tuple . We randomly choose a random number and define another tuple . The assumption then is that no polynomial-time adversary can distinguish tuple from tuple with negligible advantage.
4. Access Control System
In this section, we introduce our system model and the concrete EVOAC-HP, which is composed of five stages, including system parameter initialization, key generation, EHR data encryption, ciphertext transformation, and EHR data decryption and verification.
4.1. System Model
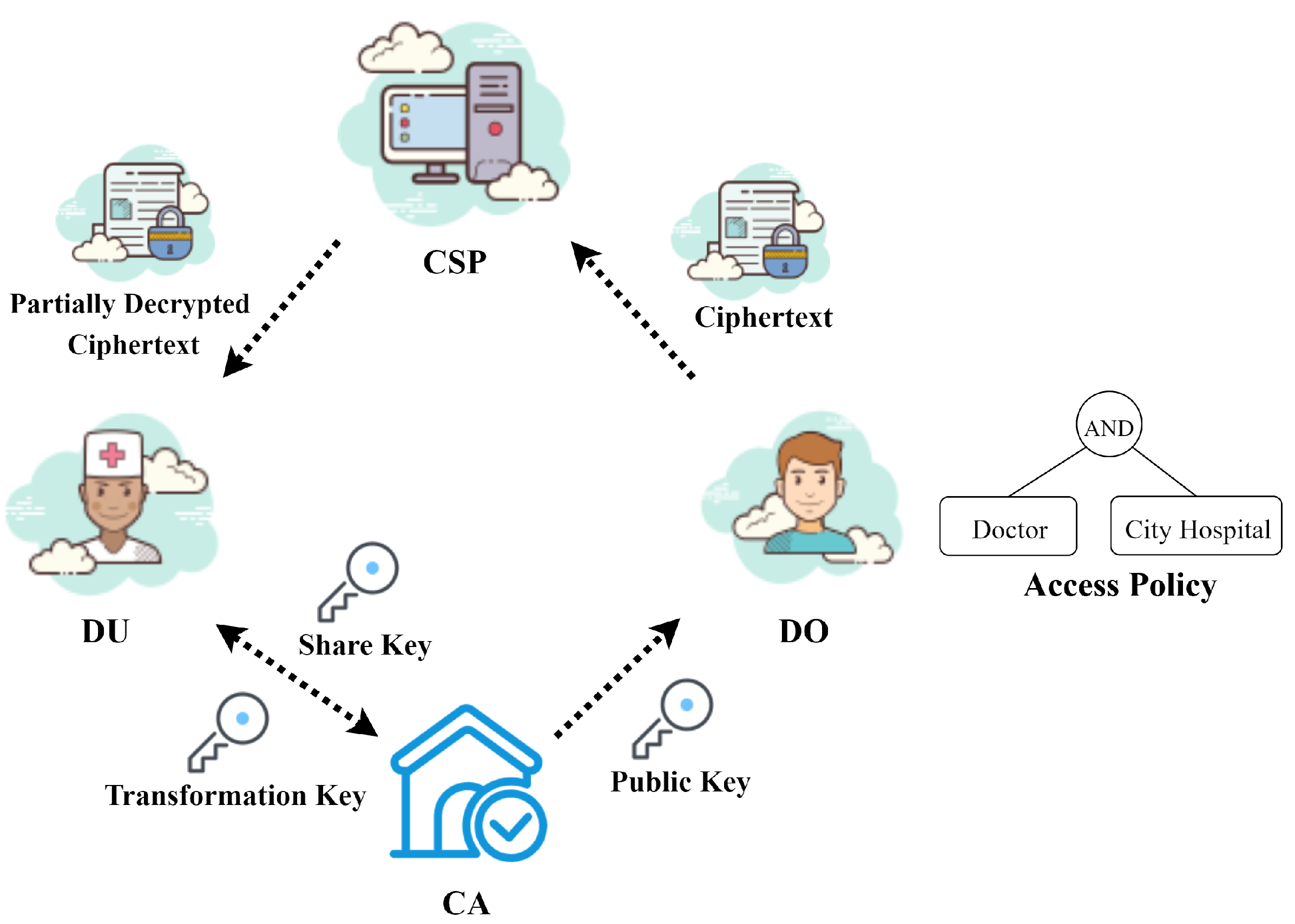
As shown in Figure 1, the system model of EVOAC-HP comprises four entities: a certificate authority (CA), many data owners (DOs), many data users (DUs) and a cloud service provider (CSP). The following provides the definition and functions of each participant:
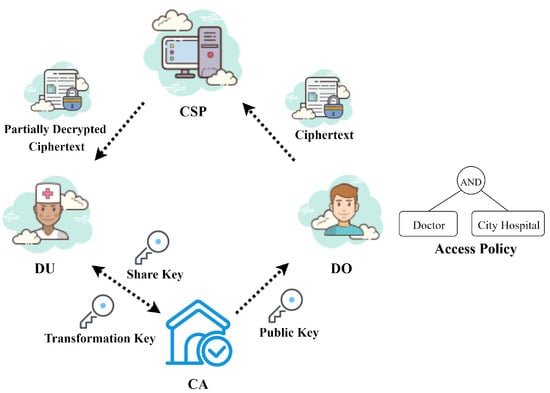
Figure 1.
The system model of EVOAC-HP.
- Certificate authority (CA): The central component of the entire system is the CA, which is in charge of the initialization of the system. The CA is responsible for creating the master private key and public parameters. Additionally, the CA generates transformation keys for users based on their attribute set when requested. It is assumed that the CA is a trusted entity.
- Data owners (DOs): DOs are the producers of medical data. When they need to share their data, they first establish a custom access policy that allows users to access and encrypt the data using our proposed encryption scheme. The resulting ciphertext is then uploaded to the CSP. It is worth noting that the access policy in the ciphertext does not reveal the sensitive attributes of the data owner. In a medical scenario, the data owners are the patients.
- Data users (DUs): In the healthcare scenario, the DUs play the role of a doctor or a nurse. They need to retrieve the corresponding ciphertext from the CSP and request it to assist in the transformation of the ciphertext. When obtaining the transformed decrypted ciphertext from the CSP, the data user locally decrypts it to access the EHR data and checks whether the transformation result is correct. Considering that the data user is likely to use resource-limited devices such as conventional desktop computers, the decryption operation is delegated to simplify the computation.
- Cloud service provider (CSP): The CSP is a powerful server with storage and computing services. Its main responsibilities include storing ciphertext corresponding to medical data and providing ciphertext transformation service. It should be noted that the CSP is honest but curious, which means that it may attempt to extract useful information from the ciphertext.
4.2. The Proposed Scheme
System parameter initialization. The entire process of system initialization is performed by the CA. It runs to generate . This process is shown in Algorithm 1. This algorithm takes as input the security parameter and a large attribute universe description U, and it outputs the master public key and the master key . In this process, the CA executes the initialization stage of the FAME scheme [15] and the commitment scheme. In addition, the attribute bloom filter is parameterized. Finally, the master public key is , and the master key is .
| Algorithm 1 Setup (Invoked by CA). |
| Input Security parameter , attribute universe description U Output: The master public key , the master key
|
Key generation. This stage has two steps: Firstly, the data user randomly selects as a secret decryption key and produces a shared public key . When the data user needs to apply for the transformation key, the data user sends the shared public key to the CA responsible for issuing transformation keys. The CA runs to generate the transformation key , and this process is shown in Algorithm 2. This algorithm takes as input the master key , a set of the data user attributes S and a shared public key , and it outputs the transformation key
| Algorithm 2 TkGen (Invoked by CA). |
| Input The master key , attribute set S, a shared public key Output: Transformation key
|
EHR data encryption. When encrypting sensitive EHR data under the defined access structure , the data owner first randomly picks a value r and uses a concatenation operation represented by “” to encrypt the combination of EHR data and the random number . This means that the encrypted result contains both the original EHR data and the random value. That is, it runs . This algorithm takes the master public key , the EHR data , the random number r and the access structure as input, and it outputs the encrypted EHR data . This process is shown in Algorithm 3. To hide the access structure , we adopt the attribute bloom filter to achieve this property. It invokes to obtain . This algorithm takes as input the access structure , and it outputs the attribute bloom filter . The concrete process is detailed in Section 3.5. In order to commit to using the value r, it runs . The data owner calculates a commitment of the EHR data . The final ciphertext is .
| Algorithm 3 Encrypt (Invoked by DO). |
| Input Master public key , the combination of the message and random number , access structure , attribute set S Output: Encrypted message
|
Ciphertext transformation. In this stage, the CSP invokes . This algorithm takes as input the encrypted EHR data and the transformation key and outputs the partially decrypted ciphertext . This process is shown in Algorithm 4. Notice that the CSP might be malicious or lazy, so the transformation result is not necessarily true.
| Algorithm 4 Transform (Invoked by CSP). |
| Input Ciphertext , transformation key Output: Partially-decrypted ciphertext
|
EHR data decryption and verification. When the data user requests the full ciphertext from the CSP, it firstly decomposes the ciphertext into and runs . The concrete process is detailed in Section 3.5. This algorithm takes as input the master public key , a set of data user attributes S and attribute bloom filter and outputs the rebuilt attribute mapping . When recovering the corresponding access structure , the resource-constrained data user is able to delegate the ciphertext to the CSP for decryption; the CSP transforms the ciphertext into partially decrypted ciphertext and gives it to the data user. Then, the data user runs . This algorithm takes as input the full ciphertext , the partially decrypted ciphertext and decryption key and outputs the final result . The result is the combination of the message and the random number . Aiming to check the correctness of the transformation result, the data user runs . This process checks whether . If it passes verification, the data user finally obtains the true message, . Otherwise, the transformation result is wrong.
5. Security Analysis
Theorem 1.
EVOAC-HP can guarantee the confidentiality of data under the random oracle model.
Lemma 1.
If FAME [15] can guarantee the confidentiality of data, the proposed scheme can also guarantee the confidentiality of data.
Proof.
Suppose that there is an adversary that solves the difficult decisional linear problem in probabilistic polynomial time, whose advantage cannot be ignored. With the help of adversary , an algorithm can be constructed so that the algorithm can break the confidentiality of FAME in probabilistic polynomial time, and the advantages are not negligible.
Let be the challenger of a safe game in the FAME scheme, and let be the adversary of the game. Algorithm can break FAME’s confidentiality by performing the following:
- System initialization: Adversary sends the access structure that needs to be challenged to algorithm . Algorithm gives to challenger . Challenger generates public parameter with the algorithm in FAME and sends to algorithm . Algorithm calls the algorithm in EVOAC-HP to complete public parameter and send it to adversary .
- Query phase 1: Algorithm receives the decryption key query request submitted by adversary . Let adversary ask for the decryption key of the attribute set , and let algorithm forward this query request to challenger . Challenger calls the algorithm in the FAME scheme to output the decryption key given to algorithm , and algorithm forwards its key to adversary .
- Challenge phase: Adversary submits two equal-length plaintexts, and , to algorithm . Algorithm sends them to challenger and asks for the challenge ciphertext. Challenger randomly selects and calls the algorithm in the FAME scheme to encrypt the message . Finally, challenger sends the ciphertext to algorithm . After receiving the challenge ciphertext , algorithm completes according to the ciphertext form of EVOAC-HP and then sends it to adversary .
- Query phase 2: This phase is the same as Query phase 1.
- Guess phase: If adversary outputs a bit , then algorithm also outputs .
If adversary can break the FAME scheme, it means that adversary can calculate the ciphertext according to algorithm . With the help of adversary , algorithm can calculate in the FAME algorithm, thereby breaking the FAME scheme. □
Theorem 2.
If the decisional linear assumption is correct, FAME is adaptively secure under the random oracle model.
Lemma 2.
FAME [15] has proved that the decisional linear assumption is adaptively secure under the random oracle model. EVOAC-HP is constructed based on FAME, so EVOAC-HP can guarantee the confidentiality of data under the random oracle model.
Theorem 3.
EVOAC-HP can guarantee the confidentiality of ciphertext transformation.
Proof.
The proposed scheme guarantees transformation result confidentiality with the discrete logarithm problem. Specifically, EVOAC-HP generates a transformation key using a shared public key provided by the data user. Even if an adversary gains access to the transformation key and the intermediate ciphertext from the CSP, they cannot compute without the user’s secret decryption key z. Thus, the adversary does not have the ability to decrypt the combination of the EHR data and the random number () and gain access to sensitive data . This adds an extra layer of security to the scheme, ensuring that confidential information remains protected even if the adversary gains access to some of the intermediate data. □
Theorem. 4
EVOAC-HP can guarantee the privacy of the access policy.
Proof.
To prevent the potential leakage of attribute information, EVOAC-HP eliminates the attribute mapping function embedded in the access policy using the and procedures. Adversaries without knowledge of the attribute string cannot carry out a successful brute-force attack within polynomial time, so they are incapable of accessing and inferring confidential information from the access policy. Furthermore, data users are only able to check whether they possess the required attributes for accessing the data. It is impossible for a single data user to verify all the attributes from the attribute universe description U unless they possess all of the attributes or multiple data users work together to achieve it. Therefore, EVOAC-HP provides protection for policy privacy by concealing attribute information in the access policy. □
6. Performance Analysis
In this section, the performance of EVOAC-HP is analyzed from functional, theoretical and experimental perspectives.
6.1. Functional Analysis
When it comes to the comparisons of functional analysis, we compare related works in terms of five functionalities: security model, large universe, hidden policy, outsourced decryption and verifiability. Note that in the security model, adaptive security provides stronger security guarantees than selective security. As shown in Table 1, most schemes support only two or three of these features, while the work [18] only supports large universe, and the work [8] only achieves hidden policy. For better security, only schemes [15,25] and EVOAC-HP achieve adaptive security. The schemes [10,11] both support large universe, outsourced decryption and verifiability. According to the above comparison, EVOAC-HP simultaneously achieves large universe, adaptive security, hidden policy, outsourced decryption and verifiability, thus showing functional advantages.

Table 1.
Comparisons of functionality 1.
6.2. Theoretical Analysis
Here, we only consider some expensive operations and use the symbols , and to denote exponentiation, pairing and hashing operation, respectively. As shown in Table 2, we evaluate EVOAC-HP and compare it with other similar schemes based on the computational complexity of their encryption and decryption algorithms. Regarding the encryption process, although the scheme [32] and EVOAC-HP incur high computational overhead, most of the computational overhead is attributed to the construction of the attribute bloom filter, which requires additional hashing operations to achieve policy hiding. On the other hand, it is obvious that in the decryption stage, existing schemes [15,18,32] need to perform pairing operations, which is expensive for data users, while EVOAC-HP only requires operations. Due to outsourced decryption, EVOAC-HP outperforms other existing schemes that require pairing operations in the decryption stage with regard to performance.

Table 2.
Comparisons of computation cost 1.
6.3. Experimental Analysis
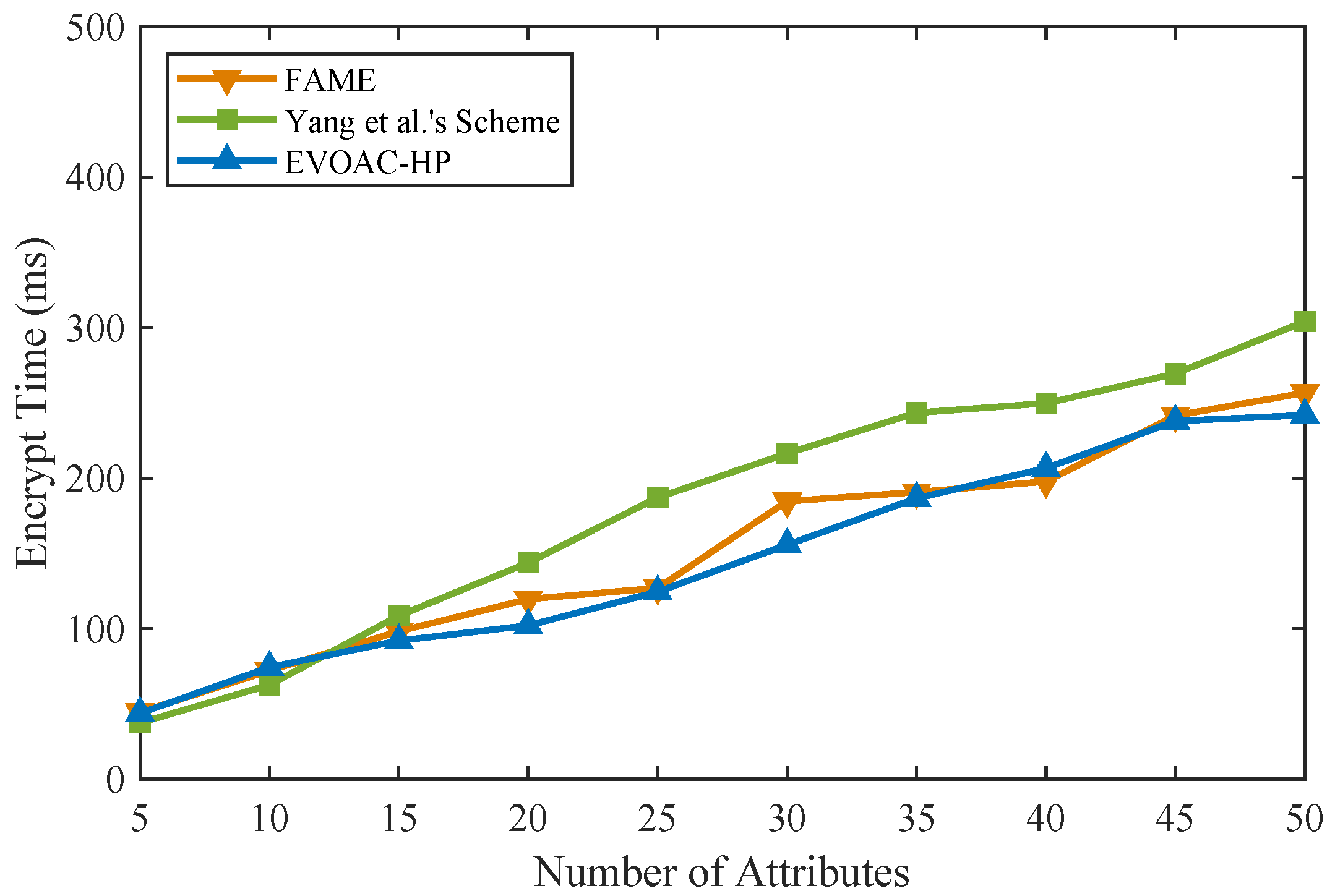
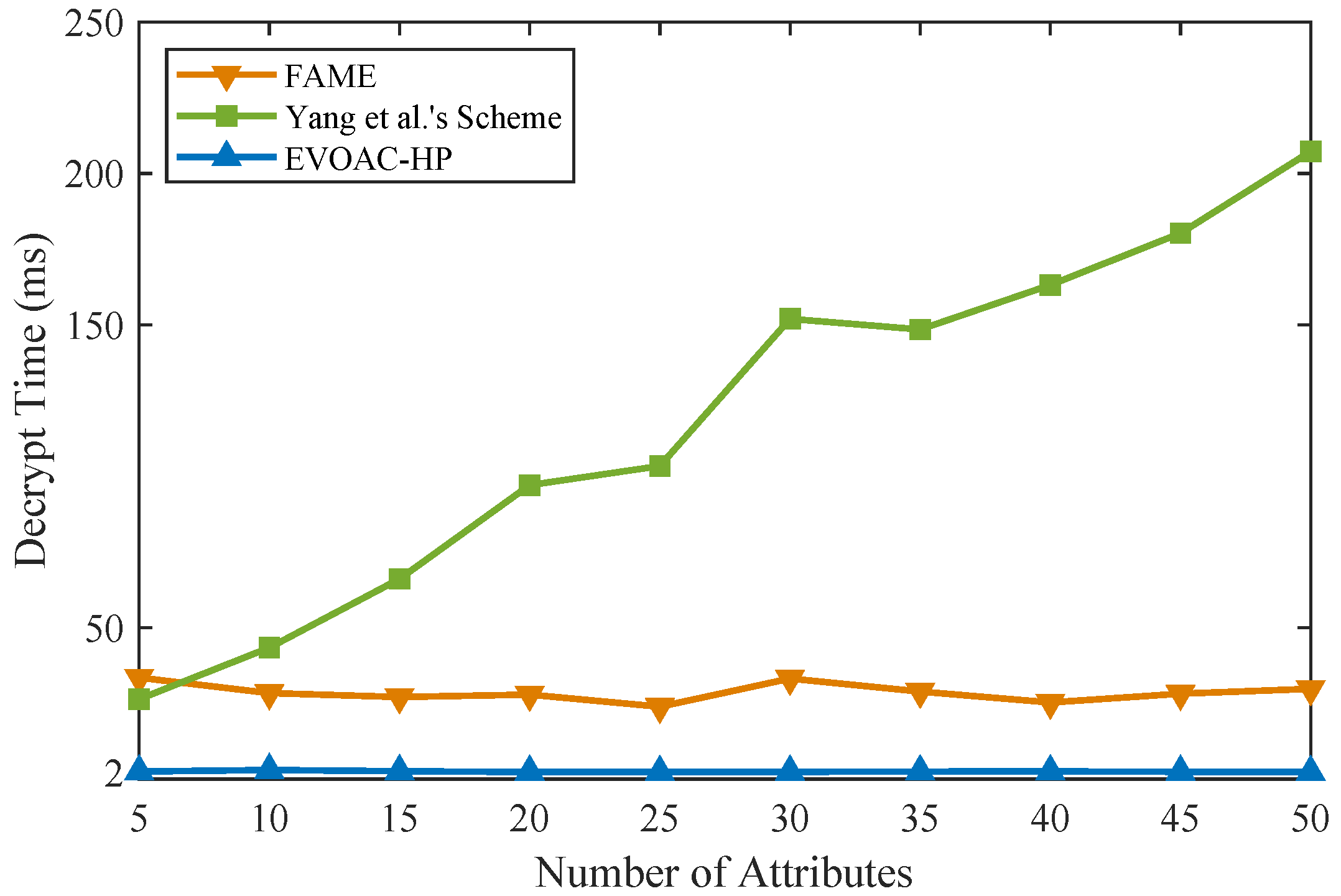
We implemented similar schemes in Python 3.8 in the same experimental environment (Ubuntu-20.04 with Intel Core i7 and 16 G RAM) on top of the Charm framework [37] and MNT224 curve for pairing. The double-hash technique [38] based on 128-bit MurmurHash and SpookyHash was used to construct x hash functions for the attribute bloom filter. We compared the computational time of data encryption and data decryption with schemes [15,32] and EVOAC-HP. We evaluated all the schemes using access policies and attribute sets of sizes ranging from 5 to 50, and the number of hash functions for the ABF was 10. Those schemes were tested in 10 trials, so that the experimental results were averaged. As shown in Figure 2, as the number of attributes increases, the encryption overhead of all three schemes shows a linear growth trend. However, our scheme, EVOAC-HP, has significantly smaller encryption overhead than the scheme proposed in [32], while it has time overhead similar to that of the scheme proposed in [15]. It is worth noting that the scheme proposed in [15] does not consider policy privacy, while our scheme requires the construction of the ABF during the encryption phase to achieve fully hidden policy, resulting in additional computational overhead depending on the number of hash functions used. As shown in Figure 3, the data decryption overhead of scheme [32] shows a linear growth trend as the number of attributes increases, which leads to an increased computational burden for data users. In contrast, EVOAC-HP and scheme [15] maintain constant data decryption overhead. Moreover, EVOAC-HP adopts outsourcing decryption techniques, which further reduces decryption overhead to 2 ms.
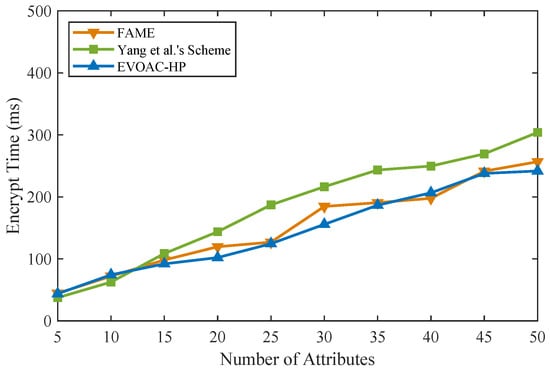
Figure 2.
Computation time comparison of data encryption among FAME [15], Yang et al.’s scheme [32] and our scheme.
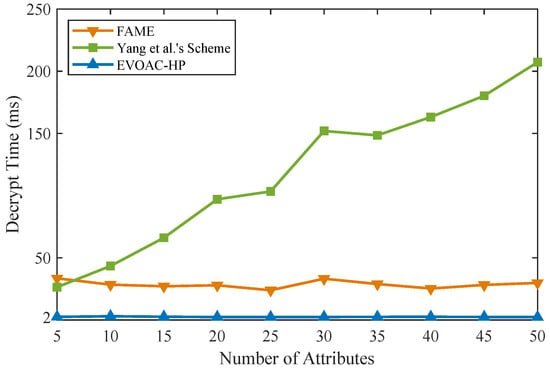
Figure 3.
Computation time comparison of data decryption among FAME [15], Yang et al.’s scheme [32] and our scheme.
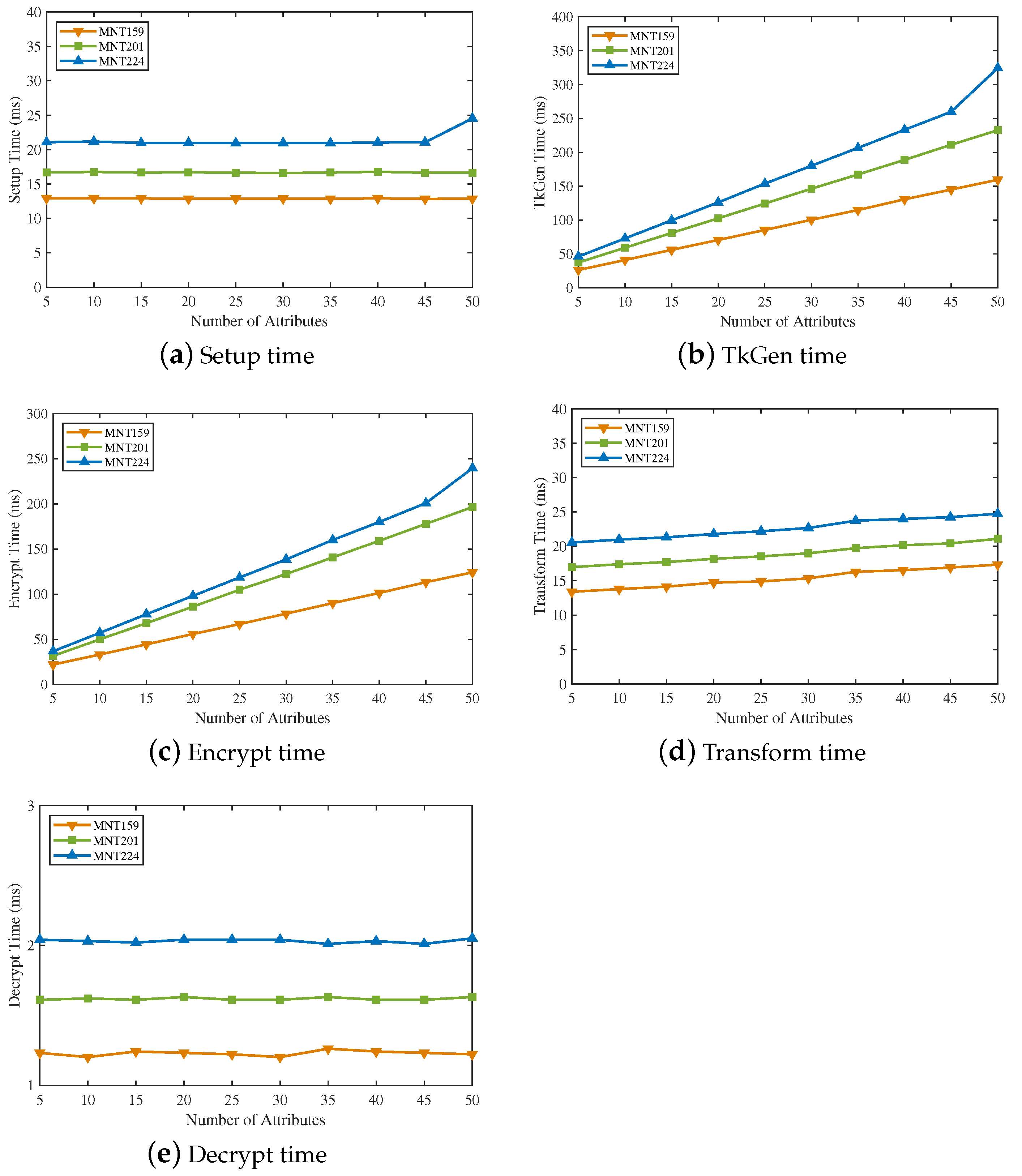
In order to evaluate the time cost of five algorithms in EVOAC-HP, we conducted experiments under three curves, MNT159, MNT201 and MNT224. Figure 4 shows the computational time of each algorithm in our proposed scheme with the number of attributes. Obviously, the MNT224 curve had the highest overhead among all algorithms, while MNT159 had the lowest. The algorithm maintained constant computational overhead, and system initialization was only required once. Except for the algorithm, the computation overhead of all algorithms was proportional to the number of attributes. Due to outsourced decryption, the algorithm only spent a constant time of around 2 ms.
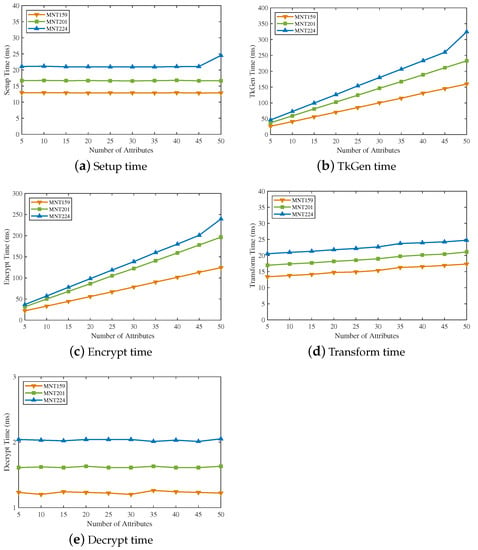
Figure 4.
Computational overhead with the number of attributes.
7. Conclusions and Future Work
In this paper, we introduce a practical and reliable scheme for fine-grained privacy protection and outsourced computation access control for sharing medical data, named EVOAC-HP. We employ CP-ABE as a fundamental building block to encrypt the medical data and outsource the decryption operation to alleviate the computation overhead for data users, which reduces the decryption computation overhead to a constant. Additionally, we achieve policy hiding by utilizing the attribute bloom filter, which prevents any individual from accessing sensitive attribute information from the access policy. The user’s attributes are not disclosed in the access policy, which effectively guarantees the security of our scheme. The proposed scheme is proved to be adaptively secure under the random oracle model under the decisional linear assumption. As demonstrated with performance analysis and comparative analysis, EVOAC-HP has functional advantages, better performance and stronger security, which are suitable for EHR data sharing and complex access control in medical scenarios.
Our scheme also has some limitations. First of all, with our scheme, it is difficult to efficiently deal with the policy update problem. When the access policy needs to be updated, the data owner can complete the update with a small computational cost. In this scheme, the data owner needs to re-encrypt according to the new access policy, which is obviously inefficient. Secondly, in most medical scenarios, users’ identities may often change, which requires a new solution that supports user attribute update and revocation to meet this requirement. Finally, our scheme has the problem of offline dictionary attack, that is, the user can continuously query whether the attribute is in the access policy with the attribute bloom filter, which may expose user attributes. In the future, we plan to focus on incorporating features such as CP-ABE with policy update and user attribute revocation while preventing dictionary attacks to better meet practical application scenarios.
Author Contributions
Formal analysis, D.Z., H.M. and P.L.; Methodology, H.M. and P.L.; Supervision, D.Z. and X.W.; Writing—original draft preparation, H.M.; Writing—review and editing, P.L., D.Z. and X.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China under grant number 61932010 and Guangdong Provincial Key Laboratory of Power System Network Security under grant number GPKLPSNS-2022-KF-05.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wang, M.; Guo, Y.; Zhang, C.; Wang, C.; Huang, H.; Jia, X. MedShare: A privacy-preserving medical data sharing system by using blockchain. IEEE Trans. Serv. Comput. 2021, 16, 438–451. [Google Scholar] [CrossRef]
- Li, F.; Liu, K.; Zhang, L.; Huang, S.; Wu, Q. EHRChain: A blockchain-based ehr system using attribute-based and homomorphic cryptosystem. IEEE Trans. Serv. Comput. 2021, 15, 2755–2765. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Cheng, L.; Dai, H.N.; Qiu, M.; Chen, G.; Liu, X.; Huang, G. BlockSense: Towards Trustworthy Mobile Crowdsensing via Proof-of-Data Blockchain. IEEE Trans. Mob. Comput. 2022, 1–17. [Google Scholar] [CrossRef]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar] [CrossRef]
- Lewko, A.; Waters, B. New proof methods for attribute-based encryption: Achieving full security through selective techniques. In Proceedings of the Advances in Cryptology–CRYPTO 2012: 32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; pp. 180–198. [Google Scholar] [CrossRef]
- Rouselakis, Y.; Waters, B. Practical constructions and new proof methods for large universe attribute-based encryption. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 463–474. [Google Scholar] [CrossRef]
- Nishide, T.; Yoneyama, K.; Ohta, K. Attribute-based encryption with partially hidden encryptor-specified access structures. In Proceedings of the International Conference on Applied Cryptography and Network Security, New York, NY, USA, 3–6 June 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 111–129. [Google Scholar] [CrossRef]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the Decryption of ABE Ciphertexts. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 8–12 August 2011. [Google Scholar]
- Lai, J.; Deng, R.H.; Guan, C.; Weng, J. Attribute-based encryption with verifiable outsourced decryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1343–1354. [Google Scholar] [CrossRef]
- Mao, X.; Lai, J.; Mei, Q.; Chen, K.; Weng, J. Generic and efficient constructions of attribute-based encryption with verifiable outsourced decryption. IEEE Trans. Dependable Secur. Comput. 2015, 13, 533–546. [Google Scholar] [CrossRef]
- Liu, X.; Wang, H.; Zhang, B.; Zhang, B. An efficient fine-grained data access control system with a bounded service number. Inf. Sci. 2022, 584, 536–563. [Google Scholar] [CrossRef]
- Lai, J.; Deng, R.H.; Li, Y. Fully secure cipertext-policy hiding CP-ABE. In Proceedings of the Information Security Practice and Experience: 7th International Conference, ISPEC 2011, Guangzhou, China, 30 May–1 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 24–39. [Google Scholar] [CrossRef]
- Hur, J. Attribute-based secure data sharing with hidden policies in smart grid. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 2171–2180. [Google Scholar] [CrossRef]
- Agrawal, S.; Chase, M. FAME: Fast attribute-based message encryption. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 665–682. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Advances in Cryptology: Proceedings of CRYPTO ’84, Santa Barbara, California, USA, 19–22 August 1984; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar] [CrossRef]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Li, J.; Jia, C.; Ma, J.; Lou, W. Fine-grained access control system based on outsourced attribute-based encryption. In Proceedings of the European Symposium on Research in Computer Security, Egham, UK, 9–13 September 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 592–609. [Google Scholar] [CrossRef]
- Li, J.; Huang, X.; Li, J.; Chen, X.; Xiang, Y. Securely outsourcing attribute-based encryption with checkability. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 2201–2210. [Google Scholar] [CrossRef]
- Lin, S.; Zhang, R.; Ma, H.; Wang, M. Revisiting attribute-based encryption with verifiable outsourced decryption. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2119–2130. [Google Scholar] [CrossRef]
- Cui, H.; Wan, Z.; Wei, X.; Nepal, S.; Yi, X. Pay as you decrypt: Decryption outsourcing for functional encryption using blockchain. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3227–3238. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. LBAC: A lightweight blockchain-based access control scheme for the internet of things. Inf. Sci. 2021, 554, 222–235. [Google Scholar] [CrossRef]
- Qin, X.; Yang, Z.; Li, Q.; Pan, H.; Yang, Z.; Huang, Y. Attribute-based encryption with outsourced computation for access control in IoTs. In Proceedings of the 2022 3rd Asia Service Sciences and Software Engineering Conference, Macao, 24–26 February 2022; pp. 66–73. [Google Scholar] [CrossRef]
- Lai, J.; Deng, R.H.; Li, Y. Expressive CP-ABE with partially hidden access structures. In Proceedings of the 7th ACM Symposium on Information, Computer and Communications Security, Seoul, Republic of Korea, 2–4 May 2012; pp. 18–19. [Google Scholar] [CrossRef]
- Cui, H.; Deng, R.H.; Wu, G.; Lai, J. An efficient and expressive ciphertext-policy attribute-based encryption scheme with partially hidden access structures. In Proceedings of the International Conference on Provable Security, Nanjing, China, 10–11 November 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 19–38. [Google Scholar] [CrossRef]
- Zhang, Y.; Zheng, D.; Deng, R.H. Security and privacy in smart health: Efficient policy-hiding attribute-based access control. IEEE Internet Things J. 2018, 5, 2130–2145. [Google Scholar] [CrossRef]
- Cui, H.; Deng, R.H.; Lai, J.; Yi, X.; Nepal, S. An efficient and expressive ciphertext-policy attribute-based encryption scheme with partially hidden access structures, revisited. Comput. Netw. 2018, 133, 157–165. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, G.; Mu, Y.; Rezaeibagha, F. Hidden ciphertext policy attribute-based encryption with fast decryption for personal health record system. IEEE Access 2019, 7, 33202–33213. [Google Scholar] [CrossRef]
- Saidi, A.; Nouali, O.; Amira, A. SHARE-ABE: An efficient and secure data sharing framework based on ciphertext-policy attribute-based encryption and Fog computing. Clust. Comput. 2022, 25, 167–185. [Google Scholar] [CrossRef]
- Dong, C.; Chen, L.; Wen, Z. When private set intersection meets big data: An efficient and scalable protocol. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 789–800. [Google Scholar] [CrossRef]
- Yang, K.; Han, Q.; Li, H.; Zheng, K.; Su, Z.; Shen, X. An efficient and fine-grained big data access control scheme with privacy-preserving policy. IEEE Internet Things J. 2016, 4, 563–571. [Google Scholar] [CrossRef]
- Han, Q.; Zhang, Y.; Li, H. Efficient and robust attribute-based encryption supporting access policy hiding in Internet of Things. Future Gener. Comput. Syst. 2018, 83, 269–277. [Google Scholar] [CrossRef]
- Hao, J.; Huang, C.; Ni, J.; Rong, H.; Xian, M.; Shen, X.S. Fine-grained data access control with attribute-hiding policy for cloud-based IoT. Comput. Netw. 2019, 153, 1–10. [Google Scholar] [CrossRef]
- Zhang, L.; Wang, J.; Mu, Y. Privacy-Preserving Flexible Access Control for Encrypted Data in Internet of Things. IEEE Internet Things J. 2021, 8, 14731–14745. [Google Scholar] [CrossRef]
- Deng, W.; Xiang, T.; Liao, X. STEAC: Towards secure, traceable, and efficient cryptographic access control scheme in smart healthcare. Multimed. Tools Appl. 2022, 81, 30069–30092. [Google Scholar] [CrossRef]
- Akinyele, J.A.; Garman, C.; Miers, I.; Pagano, M.W.; Rushanan, M.; Green, M.; Rubin, A.D. Charm: A framework for rapidly prototyping cryptosystems. J. Cryptogr. Eng. 2013, 3, 111–128. [Google Scholar] [CrossRef]
- Bradford, P.G.; Katehakis, M.N. A probabilistic study on combinatorial expanders and hashing. SIAM J. Comput. 2007, 37, 83–111. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).