Automotive Cybersecurity: A Survey on Frameworks, Standards, and Testing and Monitoring Technologies
Abstract
1. Introduction
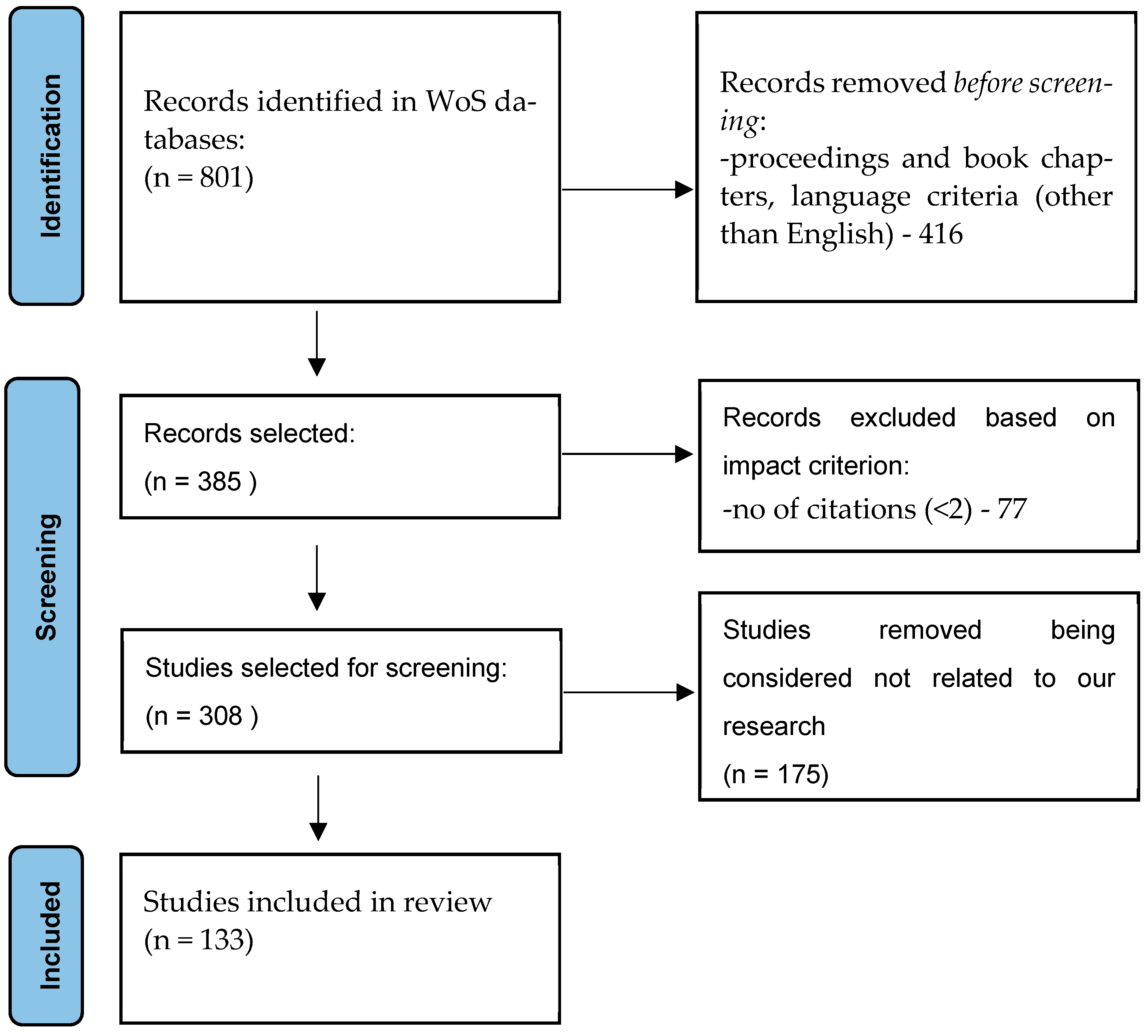
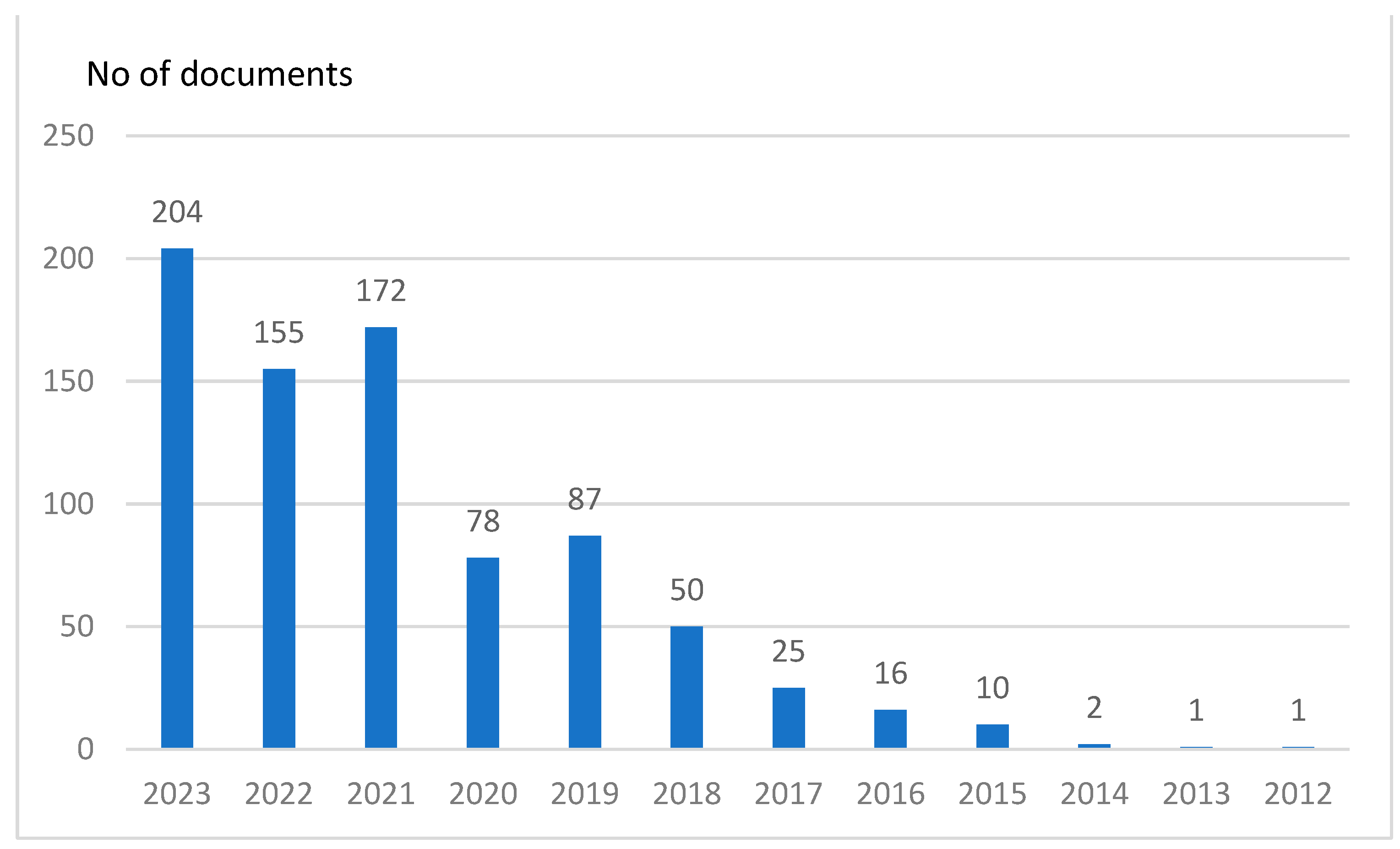
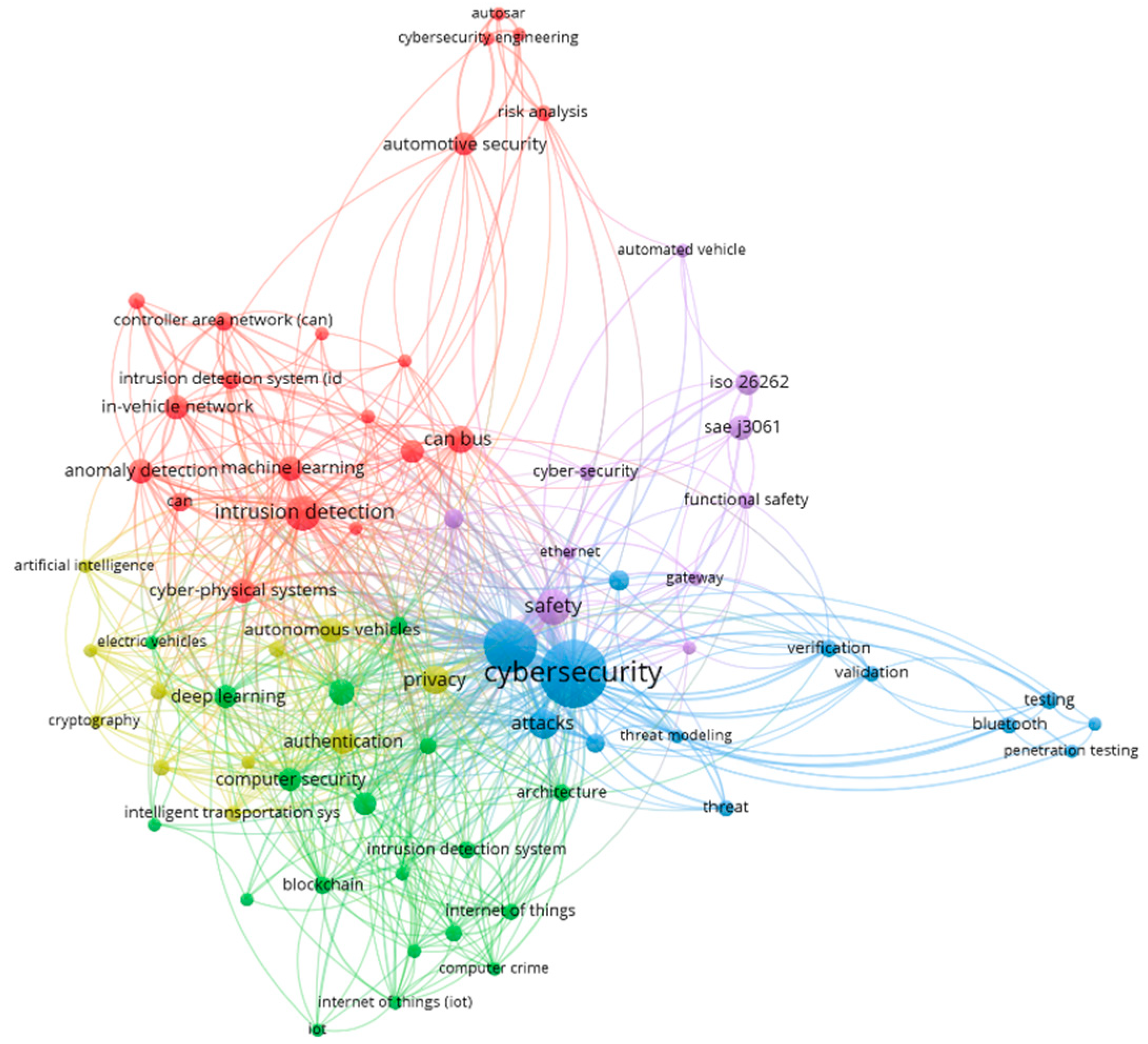
2. Automotive Cybersecurity—A Bibliometric Analysis
3. Literature Review
3.1. Frameworks and Technologies for Cybersecurity
3.1.1. CS Frameworks
3.1.2. CS Technologies
Model-Based Engineering (MBE)
Blockchain
Machine Learning and Deep Learning
Cybersecurity and Safety Relationship
Secure Onboard Communication (SecOC)
Internet of Things (IoT)
Automotive Ethernet (AE)
Data Privacy Challenges
Cloud Cybersecurity Solutions
3.2. CS Standards and Regulations
3.3. CS Monitoring and Vulnerability Management
3.3.1. Intrusion Detection Systems
3.3.2. Security Operation Center
3.3.3. Threat Analysis and Risk Assessment (TARA)
3.3.4. Cybersecurity and Platooning Functions
3.3.5. Secure Communication
3.4. CS Testing and Validation
4. Conclusions and Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bandur, V.; Selim, G.; Pantelic, V.; Lawford, M. Making the Case for Centralized Automotive E/E Architectures. IEEE Trans. Veh. Technol. 2021, 70, 1230–1245. [Google Scholar] [CrossRef]
- Reinhardt, D.; Kaule, D.; Kucera, M. Achieving a Scalable E/E-Architecture Using AUTOSAR and Virtualization. SAE Int. J. Passeng. Cars—Electron. Electr. Syst. 2013, 6, 489–497. [Google Scholar] [CrossRef]
- Verstegen, A.; Verdult, R.; Bokslag, W. Hitag 2 Hell—Brutally Optimizing Guess-and-Determine Attacks. In Proceedings of the 12th USENIX Workshop on Offensive Technologies, WOOT 2018, Baltimore, MD, USA, 13–14 August 2018. [Google Scholar]
- Verdult, R.; Garcia, F.D.; Balasch, J. Gone in 360 Seconds: Hijacking with Hitag2. In Proceedings of the 21st USENIX Security Symposium, Bellevue, WA, USA, 8–10 August 2012. [Google Scholar]
- Chen, H.; Liu, J.; Yang, C.F. Design of Intelligent Locks Based on the Triple KeeLoq Algorithm. Adv. Mech. Eng. 2016, 8. [Google Scholar] [CrossRef]
- Miller, C.; Valasek, C. Remote Exploitation of an Unaltered Passenger Vehicle. Defcon 23 2015, 9, 1–91. [Google Scholar]
- Oka, D. Building Secure Cars: Assuring the Software Development Lifecycle; John Wiley & Sons: Hoboken, NJ, USA, 2021; ISBN 9781119710745 and 9781119710783. [Google Scholar]
- SAE J3061; Cybersecurity Guidebook for Cyber-Physical Vehicle Systems. SAE International: Warrendale, PA, USA, 2016.
- UN-ECE R155—Cyber Security and Cyber Security Management System. Available online: https://eur-lex.europa.eu/legal-content/DE/TXT/?uri=OJ:L:2021:082:TOC (accessed on 19 September 2024).
- ISO/SAE 21434:2021; Road Vehicles—Cybersecurity Engineering. ISO: Geneva, Switzerland, 2021.
- ISO 26262-1:2018; Road Vehicles—Functional Safety. ISO: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/68383.html (accessed on 19 September 2024).
- Khatun, M.; Wagner, F.; Jung, R.; Glass, M. An Approach of a Safety Management System for Highly Automated Driving System. In Proceedings of the 2021 5th International Conference on System Reliability and Safety (ICSRS 2021), Palermo, Italy, 24–26 November 2021; IEEE: New York, NY, USA, 2021; pp. 222–229. [Google Scholar]
- ISO 21448:2022; Road Vehicles—Safety of the Intended Functionality. ISO: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/77490.html (accessed on 19 September 2024).
- Macher, G.; Schmittner, C.; Veledar, O.; Brenner, E. ISO/SAE DIS 21434 Automotive Cybersecurity Standard—In a Nutshell. In Computer Safety, Reliability, and Security. SAFECOMP 2020 Workshops, Proceedings of the International Conference on Computer Safety, Reliability, and Security, Lisbon, Portugal, 15–18 September 2020; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Luo, F.; Jiang, Y.; Wang, J.; Li, Z.; Zhang, X. A Framework for Cybersecurity Requirements Management in the Automotive Domain. Sensors 2023, 23, 4979. [Google Scholar] [CrossRef] [PubMed]
- VOXViewer; Leiden University: Leiden, The Netherlands, 2024; Available online: https://www.vosviewer.com/ (accessed on 19 September 2024).
- Wang, P.; Wu, X.; He, X. Modeling and Analyzing Cyberattack Effects on Connected Automated Vehicular Platoons. Transp. Res. Part C-Emerging Technol. 2020, 115, 102625. [Google Scholar] [CrossRef]
- Palaniswamy, B.; Camtepe, S.; Foo, E.; Pieprzyk, J. An Efficient Authentication Scheme for Intra-Vehicular Controller Area Network. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3107–3122. [Google Scholar] [CrossRef]
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity Challenges in Vehicular Communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Kukkala, V.K.; Thiruloga, S.V.; Pasricha, S. Roadmap for Cybersecurity in Autonomous Vehicles. IEEE Consum. Electron. Mag. 2022, 11, 13–23. [Google Scholar] [CrossRef]
- Abu Elkhail, A.; Refat, R.U.D.; Habre, R.; Hafeez, A.; Bacha, A.; Malik, H. Vehicle Security: A Survey of Security Issues and Vulnerabilities, Malware Attacks and Defenses. IEEE Access 2021, 9, 162401–162437. [Google Scholar] [CrossRef]
- Khalid, A.; Sundararajan, A.; Hernandez, A.; Sarwat, I.A. Facts Approach to Address Cybersecurity Issues in Electric Vehicle Battery Systems. In Proceedings of the 2019 IEEE Technology & Engineering Management Conference (TEMSCON), Atlanta, GA, USA, 11–14 June 2019; IEEE: New York, NY, USA, 2019. [Google Scholar]
- Khalid Khan, S.; Shiwakoti, N.; Stasinopoulos, P. A Conceptual System Dynamics Model for Cybersecurity Assessment of Connected and Autonomous Vehicles. Accid. Anal. Prev. 2022, 165, 106515. [Google Scholar] [CrossRef] [PubMed]
- Aldhyani, T.H.H.; Alkahtani, H. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360. [Google Scholar] [CrossRef] [PubMed]
- Chandwani, A.; Dey, S.; Mallik, A. Cybersecurity of Onboard Charging Systems for Electric Vehicles-Review, Challenges and Countermeasures. IEEE Access 2020, 8, 226982–226998. [Google Scholar] [CrossRef]
- Hafeez, A.; Topolovec, K.; Awad, S. ECU Fingerprinting through Parametric Signal Modeling and Artificial Neural Networks for In-Vehicle Security against Spoofing Attacks. In Proceedings of the 2019 15th International Computer Engineering Conference (ICENCO 2019), Cairo, Egypt, 29–30 December 2019; IEEE: New York, NY, USA, 2019; pp. 29–38. [Google Scholar]
- Sabaliauskaite, G.; Bryans, J.; Jadidbonab, H.; Ahmad, F.; Shaikh, S.; Wooderson, P. TOMSAC—Methodology for Trade-off Management between Automotive Safety and Cyber Security. Comput. Secur. 2024, 140, 103798. [Google Scholar] [CrossRef]
- Lo Bello, L.; Mariani, R.; Mubeen, S.; Saponara, S. Recent Advances and Trends in On-Board Embedded and Networked Automotive Systems. IEEE Trans. Ind. Inform. 2019, 15, 1038–1051. [Google Scholar] [CrossRef]
- Sommer, F.; Kriesten, R.; Kargl, F. Survey of Model-Based Security Testing Approaches in the Automotive Domain. IEEE Access 2023, 11, 55474–55514. [Google Scholar] [CrossRef]
- Mahmood, S.; Fouillade, A.; Nguyen, H.N.; Shaikh, S.A. A Model-Based Security Testing Approach for Automotive Over-the-Air Updates. In Proceedings of the 2020 IEEE 13th International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Porto, Portugal, 24–28 October 2020; IEEE: New York, NY, USA, 2020; pp. 6–13. [Google Scholar]
- Mahmood, S.; Nguyen, H.N.; Shaikh, S.A. Systematic Threat Assessment and Security Testing of Automotive Over-the-Air (OTA) Updates. Veh. Commun. 2022, 35, 100468. [Google Scholar] [CrossRef]
- Kirk, R.; Nguyen, H.N.; Bryans, J.; Shaikh, S.; Evans, D.; Price, D. Formalising UPTANE in CSP for Security Testing. In Proceedings of the 2021 21st International Conference on Software Quality, Reliability and Security Companion (QRS-C 2021), Hainan, China, 6–10 December 2021; IEEE Computer Soc: Los Alamitos, CA, USA, 2021; pp. 816–824. [Google Scholar]
- Kirk, R.; Nguyen, H.N.; Bryans, J.; Shaikh, S.A.; Wartnaby, C. A Formal Framework for Security Testing of Automotive Over-the-Air Update Systems. J. Log. Algebr. Methods Program. 2023, 130, 100812. [Google Scholar] [CrossRef]
- Li, Z.; Jiang, W.; Liu, X.; Tan, K.; Jin, X.; Yang, M. GAN Model Using Field Fuzz Mutation for In-Vehicle CAN Bus Intrusion Detection. Math. Biosci. Eng. 2022, 19, 6996–7018. [Google Scholar] [CrossRef]
- Yang, Y.; Xie, G.; Wang, J.; Zhou, J.; Xia, Z.; Li, R. Intrusion Detection for In-Vehicle Network by Using Single GAN in Connected Vehicles. J. Circuits Syst. Comput. 2021, 30, 2150007. [Google Scholar] [CrossRef]
- Alfardus, A.; Rawat, D.B. Intrusion Detection System for CAN Bus In-Vehicle Network Based on Machine Learning Algorithms. In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 1–4 December 2021; Paul, R., Ed.; IEEE: New York, NY, USA, 2021; pp. 944–949. [Google Scholar]
- Fraga-Lamas, P.; Fernandez-Carames, T.M. A Review on Blockchain Technologies for an Advanced and Cyber-Resilient Automotive Industry. IEEE Access 2019, 7, 17578–17598. [Google Scholar] [CrossRef]
- Dibaei, M.; Zheng, X.; Xia, Y.; Xu, X.; Jolfaei, A.; Bashir, A.K.; Tariq, U.; Yu, D.; Vasilakos, A. V Investigating the Prospect of Leveraging Blockchain and Machine Learning to Secure Vehicular Networks: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 683–700. [Google Scholar] [CrossRef]
- Di Francesco Maesa, D.; Mori, P.; Ricci, L. A Blockchain Based Approach for the Definition of Auditable Access Control Systems. Comput. Secur. 2019, 84, 93–119. [Google Scholar] [CrossRef]
- Jiang, T.; Fang, H.; Wang, H. Blockchain-Based Internet of Vehicles: Distributed Network Architecture and Performance Analysis. IEEE Internet Things J. 2019, 6, 4640–4649. [Google Scholar] [CrossRef]
- Li, L.; Liu, J.; Cheng, L.; Qiu, S.; Wang, W.; Zhang, X.; Zhang, Z. CreditCoin: A Privacy-Preserving Blockchain-Based Incentive Announcement Network for Communications of Smart Vehicles. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2204–2220. [Google Scholar] [CrossRef]
- Kim, T.; Ochoa, J.; Faika, T.; Mantooth, H.A.; Di, J.; Li, Q.; Lee, Y. An Overview of Cyber-Physical Security of Battery Management Systems and Adoption of Blockchain Technology. IEEE J. Emerg. Sel. Top. POWER Electron. 2022, 10, 1270–1281. [Google Scholar] [CrossRef]
- Salek, M.S.; Khan, S.M.; Rahman, M.; Deng, H.-W.; Islam, M.; Khan, Z.; Chowdhury, M.; Shue, M. A Review on Cybersecurity of Cloud Computing for Supporting Connected Vehicle Applications. IEEE Internet Things J. 2022, 9, 8250–8268. [Google Scholar] [CrossRef]
- Xu, X.J.; Tatge, L.; Xu, X.L.; Liu, Y. Blockchain Applications in the Supply Chain Management in German Automotive Industry. Prod. Plan. Control 2024, 35, 917–931. [Google Scholar] [CrossRef]
- Yassin, A.M.; Aslan, H.K.; Halim, I.T.A. Smart Automotive Diagnostic and Performance Analysis Using Blockchain Technology. J. Sens. Actuator Netw. 2023, 12, 32. [Google Scholar] [CrossRef]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey. ACM Comput. Surv. 2023, 55, 237. [Google Scholar] [CrossRef]
- Zang, M.; Yan, Y. Machine Learning-Based Intrusion Detection System for Big Data Analytics in Vanet. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-SPRING), Virtual Event, 25 April–19 May 2021; IEEE: New York, NY, USA, 2021. [Google Scholar]
- Bari, B.S.; Yelamarthi, K.; Ghafoor, S. Intrusion Detection in Vehicle Controller Area Network (CAN) Bus Using Machine Learning: A Comparative Performance Study. Sensors 2023, 23, 3610. [Google Scholar] [CrossRef] [PubMed]
- Suwwan, R.; Alkafri, S.; Elsadek, L.; Afifi, K.; Zualkernan, I.; Aloul, F. Intrusion Detection for CAN Using Deep Learning Techniques. In Proceedings of the International Conference on Applied Cyber Security (ACS) 2021, Dubai, United Arab Emirates, 13–14 November 2021; Hassen, H.R., Batatia, H., Eds.; Springer International Publishing AG: Cham, Switzerland, 2022; Volume 378, pp. 13–19. [Google Scholar]
- Al-Jarrah, O.Y.; El Haloui, K.; Dianati, M.; Maple, C. A Novel Detection Approach of Unknown Cyber-Attacks for Intra-Vehicle Networks Using Recurrence Plots and Neural Networks. IEEE Open J. Veh. Technol. 2023, 4, 271–280. [Google Scholar] [CrossRef]
- Stang, M.; Sommer, M.; Kraus, D.; Sax, E.; Machinery, A.C. Improving the Validation of Automotive Self-Learning Systems through the Synergy of Scenario-Based Testing and Metamorphic Relations. In Proceedings of the IEEE/ACM 10th International Conference on BIG DATA Computing, Applications and Technologies BDCAT, Messina, Italy, 4–7 December 2023. [Google Scholar]
- Lee, C.W.; Madnick, S. Cybersafety Approach to Cybersecurity Analysis and Mitigation for Mobility-as-a-Service and Internet of Vehicles. Electronics 2021, 10, 1220. [Google Scholar] [CrossRef]
- Viadero-Monasterio, F.; Nguyen, A.T.; Lauber, J.; Boada, M.J.L.; Boada, B.L. Event-Triggered Robust Path Tracking Control Considering Roll Stability Under Network-Induced Delays for Autonomous Vehicles. IEEE Trans. Intell. Transp. Syst. 2023, 24, 14743–14756. [Google Scholar] [CrossRef]
- AUTOSAR. AUTomotive Open System ARchitecture (AUTOSAR). Available online: https://www.autosar.org/ (accessed on 19 September 2024).
- AUTOSAR. Specification of Secure Onboard Communication—CP Release 22-11. Available online: https://www.autosar.org/fileadmin/standards/R22-11/CP/AUTOSAR_SWS_SecureOnboardCommunication.pdf (accessed on 6 July 2023).
- AUTOSAR. Specification of Secure Diagnostic. Available online: https://www.autosar.org/fileadmin/standards/R23-11/AP/AUTOSAR_AP_SWS_Diagnostics.pdf (accessed on 1 July 2024).
- AUTOSAR. Specification of Intrusion Detection System Manager. Available online: https://www.autosar.org/fileadmin/standards/R22-11/CP/AUTOSAR_SWS_IntrusionDetectionSystemManager.pdf (accessed on 6 July 2023).
- El-Rewini, Z.; Sadatsharan, K.; Sugunaraj, N.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity Attacks in Vehicular Sensors. IEEE Sens. J. 2020, 20, 13752–13767. [Google Scholar] [CrossRef]
- Prantl, T.; Iffländer, L.; Herrnleben, S.; Engel, S.; Kounev, S.; Krupitzer, C. ACM Performance Impact Analysis of Securing MQTT Using TLS. In Proceedings of the ACM/SPEC International Conference on Performance Engineering (ICPE ’21), Virtual Event, 19–23 April 2021; pp. 241–248. [Google Scholar]
- Shin, Y.; Jeon, S. MQTree: Secure OTA Protocol Using MQTT and MerkleTree. Sensors 2024, 24, 1447. [Google Scholar] [CrossRef]
- Rodriguez, E.; Otero, B.; Canal, R. A Survey of Machine and Deep Learning Methods for Privacy Protection in the Internet of Things. Sensors 2023, 23, 1252. [Google Scholar] [CrossRef]
- Elsisi, M.; Tran, M.-Q. Development of an IoT Architecture Based on a Deep Neural Network against Cyber Attacks for Automated Guided Vehicles. Sensors 2021, 21, 8467. [Google Scholar] [CrossRef]
- IEEE 802.3bw-2015; IEEE Standard for Ethernet Amendment 1: Physical Layer Specifications and Management Parameters for 100 Mb/s Operation over a Single Balanced Twisted Pair Cable (100BASE-T1). IEEE Standards Association: Piscataway, NJ, USA, 2016. Available online: https://standards.ieee.org/ieee/802.3bw/5969/ (accessed on 1 July 2024).
- De Vincenzi, M.; Costantino, G.; Matteucci, I.; Fenzl, F.; Plappert, C.; Rieke, R.; Zelle, D. A Systematic Review on Security Attacks and Countermeasures in Automotive Ethernet. ACM Comput. Surv. 2024, 56, 135. [Google Scholar] [CrossRef]
- De Vincenzi, M.; Bodei, C.; Matteucci, I. Securing Automotive Ethernet: Design and Implementation of Security Data Link Solutions. In Proceedings of the 2023 20th ACS/IEEE International Conference on Computer Systems and Applications AICCSA, Giza, Egypt, 4–7 December 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- Lo Bello, L.; Patti, G.; Leonardi, L. A Perspective on Ethernet in Automotive Communications—Current Status and Future Trends. Appl. Sci. 2023, 13, 1278. [Google Scholar] [CrossRef]
- Benyahya, M.; Collen, A.; Kechagia, S.; Nijdam, N.A. Automated City Shuttles: Mapping the Key Challenges in Cybersecurity, Privacy and Standards to Future Developments. Comput. Secur. 2022, 122, 102904. [Google Scholar] [CrossRef]
- Wan, Z.; Zhou, Y.; Ren, K. Zk-AuthFeed: Protecting Data Feed to Smart Contracts with Authenticated Zero Knowledge Proof. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1335–1347. [Google Scholar] [CrossRef]
- Pape, S.; Syed-Winkler, S.; Garcia, A.M.; Chah, B.; Bkakria, A.; Hiller, M.; Walcher, T.; Lombard, A.; Abbas-Turki, A.; Yaich, R. A Systematic Approach for Automotive Privacy Management. In Proceedings of the 7th ACM Computer Science in Cars Symposium CSCS, Darmstadt, Germany, 5 December 2023. [Google Scholar]
- Kong, Q.L.; Lu, R.X.; Yin, F.; Cui, S.G. Blockchain-Based Privacy-Preserving Driver Monitoring for MaaS in the Vehicular IoT. IEEE Trans. Veh. Technol. 2021, 70, 3788–3799. [Google Scholar] [CrossRef]
- ISO 26262-1:2011; Road Vehicles—Functional Safety. ISO: Geneva, Switzerland, 2018. Available online: https://www.iso.org/standard/43464.html (accessed on 1 July 2024).
- AUTOSAR Overview of Functional Safety Measures in AUTOSAR. Available online: https://www.autosar.org/fileadmin/standards/R22-11/CP/AUTOSAR_EXP_FunctionalSafetyMeasures.pdf (accessed on 1 July 2024).
- VDA QMC Working Group 13/Automotive SIG. Automotive SPICE 3.1 The Process Reference and Assessment Model. Available online: http://vda-qmc.de/wp-content/uploads/2023/02/Automotive_SPICE_PAM_31_EN.pdf (accessed on 1 July 2024).
- Manufacturing Standards Committee. TR 68: Autonomous Vehicles—Part 1: Basic Behaviour, 1st ed.; Enterprise: Singapore, 2019; ISBN 978-981-48-3558-9. [Google Scholar]
- ISO/TR 4804:2020; Road Vehicles—Safety and Cybersecurity for Automated Driving Systems—Design, Verification and Validation. ISO: Geneva, Switzerland, 2020. Available online: https://www.iso.org/standard/80363.html (accessed on 1 July 2024).
- SAE International Cybersecurity Guidebook for Cyber-Physical Vehicle Systems. SAE Int. J. Connect. Autom. Veh. 2021, 129. [CrossRef]
- VDA QMC Project Group 13 Automotive SPICE Process Reference and Assessment Model for Cybersecurity Engineering. Available online: http://vda-qmc.de/wp-content/uploads/2023/02/Automotive_SPICE_for_Cybersecurity_EN.pdf (accessed on 1 July 2024).
- UN-ECE UN Regulation No. 156—Software Update and Software Update Management System. Available online: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-156-software-update-and-software-update (accessed on 1 July 2024).
- UNECE UN Regulation No. 157—Automated Lane Keeping Systems (ALKS). Available online: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-157-automated-lane-keeping-systems-alks (accessed on 1 July 2024).
- AUTOSAR AUTOSAR Explanation of Security Overview. Available online: https://www.autosar.org/fileadmin/standards/R22-11/FO/AUTOSAR_EXP_SecurityOverview.pdf (accessed on 1 July 2024).
- ISO/PAS 5112:2022; Road Vehicles—Guidelines for Auditing Cybersecurity Engineering. ISO: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/80840.html (accessed on 1 July 2024).
- ISO 24089:2023; Road Vehicles—Software Update Engineering. ISO: Geneva, Switzerland, 2023. Available online: https://www.iso.org/standard/77796.html (accessed on 1 July 2024).
- Skoglund, M.; Warg, F.; Sangchoolie, B. In Search of Synergies in a Multi-Concern Development Lifecycle: Safety and Cybersecurity. In Proceedings of the Computer Safety, Reliability, and Security, Safecomp, Vasteras, Sweden, 19–21 September 2018; Gallina, B., Skavhaug, A., Schoitsch, E., Bitsch, F., Eds.; SPRINGER International Publishing AG: Cham, Switzerland, 2018; Volume 11094, pp. 302–313. [Google Scholar]
- Skoglund, M.; Warg, F.; Hansson, H.; Punnekkat, S. Synchronisation of an Automotive Multi-Concern Development Process. In Proceedings of the Computer Safety, Reliability, and Security (SAFECOMP 2021), York, UK, 7 September 2021; Habli, I., Sujan, M., Gerasimou, S., Schoitsch, E., Bitsch, F., Eds.; Springer International Publishing AG: Cham, Switzerland, 2021; Volume 12853, pp. 63–75. [Google Scholar]
- Schwarzl, C.; Marko, N.; Martin, H.; Expósito Jiménez, V.; Castella Triginer, J.; Winkler, B.; Bramberger, R. Safety and Security Co-Engineering for Highly Automated Vehicles. Elektrotech. Inf. 2021, 138, 469–479. [Google Scholar] [CrossRef]
- Schmittner, C.; Macher, G.; Shaaban, A.; Stolfa, S.; Stolfa, J.; Plucar, J.; Spanyik, M.; Salamun, A.; Messnarz, R.; Ekert, D.; et al. Automotive Cybersecurity Standards—Relation and Overview. In Proceedings of the Communications in Computer and Information Science, Turku, Finland, 10 September 2019. [Google Scholar]
- Cheng, B.H.C.; Doherty, B.; Polanco, N.; Pasco, M. Security Patterns for Automotive Systems. In Proceedings of the 2019 ACM/IEEE 22ND International Conference on Model Driven Engineering Languages and Systems Companion (Models-C 2019), Munich, Germany, 15–20 September 2019; Burgueno, L., Pretschner, A., Voss, S., Chaudron, M., Kienzle, J., Volter, M., Gerard, S., Zahedi, M., Rensink, A., Polack, F., et al., Eds.; IEEE: Los Alamitos, CA, USA, 2019; pp. 54–63. [Google Scholar]
- Dobaj, J.; Macher, G.; Ekert, D.; Riel, A.; Messnarz, R. Towards a Security-Driven Automotive Development Lifecycle. J. Softw. Evol. Process 2021, 35, e2407. [Google Scholar] [CrossRef]
- Schober, T.; Griessnig, G. Cybersecurity Regulations and Standards in the Automotive Domain. In Systems, Software and Services Process Improvement, Proceedings of the 29th European Conference, EuroSPI 2022, Salzburg, Austria, 31 August–2 September 2022; Springer: Cham, Switzerland, 2022; Volume 1646, CCIS; pp. 530–539. [Google Scholar]
- Lee, T.-Y.; Lin, I.-A.; Liao, R.-H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors 2020, 20, 641. [Google Scholar] [CrossRef]
- Jo, W.; Kim, S.; Kim, H.; Shin, Y.; Shon, T. Automatic Whitelist Generation System for Ethernet Based In-Vehicle Network. Comput. Ind. 2022, 142, 103735. [Google Scholar] [CrossRef]
- Shrivastwa, R.-R.; Bouakka, Z.; Perianin, T.; Dislaire, F.; Gaudron, T.; Souissi, Y.; Karray, K.; Guilley, S. An Embedded AI-Based Smart Intrusion Detection System for Edge-to-Cloud Systems. In Proceedings of the Cryptography, Codes and Cyber Security, First Proceedings of the International Conference, I4CS 2022, Casablanca, Morocco, 27–28 October 2022; Nitaj, A., Zkik, K., Eds.; Springer International Publishing AG: Cham, Switzerland, 2022; Volume 1747, pp. 20–39. [Google Scholar]
- Casino, M.; Coppola, S.; De Santo, M.; Pascale, F.; Santonicola, E. Embedded Intrusion Detection System for Detecting Attacks over CAN-BUS. In Proceedings of the 2019 4th International Conference on System Reliability and Safety (ICSRS 2019), Rome, Italy, 20–22 November 2022; IEEE: New York, NY, USA, 2019; pp. 136–141. [Google Scholar]
- Aliwa, E.; Rana, O.; Perera, C.; Burnap, P. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2021, 54, 21. [Google Scholar] [CrossRef]
- Bhatia, R.; Kumar, V.; Serag, K.; Celik, Z.B.; Payer, M.; Xu, D. Evading Voltage-Based Intrusion Detection on Automotive CAN. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, Virtual Event, 21–25 February 2021. [Google Scholar]
- Cheng, P.; Han, M.; Li, A.; Zhang, F. STC-IDS: Spatial–Temporal Correlation Feature Analyzing Based Intrusion Detection System for Intelligent Connected Vehicles. Int. J. Intell. Syst. 2022, 37, 953–9561. [Google Scholar] [CrossRef]
- Vitale, C.; Piperigkos, N.; Laoudias, C.; Ellinas, G.; Casademont, J.; Escrig, J.; Kloukiniotis, A.; Lalos, A.S.; Moustakas, K.; Diaz Rodriguez, R.; et al. CARAMEL: Results on a Secure Architecture for Connected and Autonomous Vehicles Detecting GPS Spoofing Attacks. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 115. [Google Scholar] [CrossRef]
- Wu, W.; Li, R.; Xie, G.; An, J.; Bai, Y.; Zhou, J.; Li, K. A Survey of Intrusion Detection for In-Vehicle Networks. IEEE Trans. Intell. Transp. Syst. 2020, 21, 919–933. [Google Scholar] [CrossRef]
- Sharma, S.; Kaul, A. A Survey on Intrusion Detection Systems and Honeypot Based Proactive Security Mechanisms in VANETs and VANET Cloud. Veh. Commun. 2018, 12, 138–164. [Google Scholar] [CrossRef]
- Al-Jarrah, O.Y.; Maple, C.; Dianati, M.; Oxtoby, D.; Mouzakitis, A. Intrusion Detection Systems for Intra-Vehicle Networks: A Review. IEEE Access 2019, 7, 21266–21289. [Google Scholar] [CrossRef]
- Olufowobi, H.; Young, C.; Zambreno, J.; Bloom, G. SAIDuCANT: Specification-Based Automotive Intrusion Detection Using Controller Area Network (CAN) Timing. IEEE Trans. Veh. Technol. 2020, 69, 1484–1494. [Google Scholar] [CrossRef]
- Mansourian, P.; Zhang, N.; Jaekel, A.; Kneppers, M. Deep Learning-Based Anomaly Detection for Connected Autonomous Vehicles Using Spatiotemporal Information. IEEE Trans. Intell. Transp. Syst. 2023, 24, 16006–16017. [Google Scholar] [CrossRef]
- Ed Huang, S.; Feng, Y.; Liu, H.X. A Data-Driven Method for Falsified Vehicle Trajectory Identification by Anomaly Detection. Transp. Res. Part C-Emerging Technol. 2021, 128, 103196. [Google Scholar] [CrossRef]
- Park, S.; Choi, J.-Y. Malware Detection in Self-Driving Vehicles Using Machine Learning Algorithms. J. Adv. Transp. 2020, 1, 3035741. [Google Scholar] [CrossRef]
- Rumez, M.; Grimm, D.; Kriesten, R.; Sax, E. An Overview of Automotive Service-Oriented Architectures and Implications for Security Countermeasures. IEEE Access 2020, 8, 221852–221870. [Google Scholar] [CrossRef]
- Hofbauer, J.; Gomez, K.; Hof, H.-J. From SOC to VSOC: Transferring Key Requirements for Efficient Vehicle Security Operations In Proceedings of 21th escar Europe: The World’s Leading Automotive Cyber Security, Hamburg, Germany, 15–16 November 2023.
- Fenzl, F.; Plappert, C.; Rieke, R.; Zelle, D.; Costantino, G.; De Vincenzi, M.; Matteucci, I. Collaborative Security Patterns for Automotive Electrical/Electronic Architectures. In Advanced Sciences and Technologies for Security Applications; Springer International Publishing: Cham, Switzerland, 2023. [Google Scholar]
- Barletta, V.S.; Caivano, D.; Catalano, C.; De Vincentiis, M.; Machinery, A.C. Quantum-Based Automotive Threat Intelligence and Countermeasures. In Proceedings of the 28th International Conference on Evaluation and Assessment in Software Engineering EASE, Salerno, Italy, 18–21 June 2024; pp. 548–554. [Google Scholar]
- Wang, Y.; Wang, Y.; Qin, H.; Ji, H.; Zhang, Y.; Wang, J. A Systematic Risk Assessment Framework of Automotive Cybersecurity. Automot. Innov. 2021, 4, 253–261. [Google Scholar] [CrossRef]
- Zhang, Y.; Shi, P.; Dong, C.; Liu, Y.; Shao, X.; Ma, C. Test and Evaluation System For Automotive Cybersecurity. In Proceedings of the 2018 21st IEEE International Conference on Computational Science and Engineering (CSE 2018), Bucharest, Romania, 29–91 October 2018; Pop, F., Negru, C., GonzalezVelez, H., Rak, J., Eds.; IEEE: New York, NY, USA, 2018; pp. 201–207. [Google Scholar]
- Dobaj, J.; Ekert, D.; Stolfa, J.; Stolfa, S.; Macher, G.; Messnarz, R. Cybersecurity Threat Analysis, Risk Assessment and Design Patterns for Automotive Networked Embedded Systems: A Case Study. J. Univers. Comput. Sci. 2021, 27, 830–849. [Google Scholar] [CrossRef]
- Khatun, M.; Glass, M.; Jung, R. An Approach of Scenario-Based Threat Analysis and Risk Assessment Over-the-Air Updates for an Autonomous Vehicle. In Proceedings of the 2021 7th International Conference on Automation, Robotics and Applications (ICARA 2021), Virtual Event, 4–6 February 2021; IEEE: New York, NY, USA, 2021; pp. 122–127. [Google Scholar]
- ISO/IEC JTC 1/SC 27 ISO/IEC 27001:2022 Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. Available online: https://www.iso.org/standard/27001 (accessed on 1 July 2024).
- ENX Association Trusted Information Security Assessment Exchange. Available online: https://enx.com/en-us/tisax/ (accessed on 1 July 2024).
- Królikowski, T.; Ubowska, A. TISAX—Optimization of IT Risk Management in the Automotive Industry. Procedia Comput. Sci. 2021, 192, 4259–4268. [Google Scholar] [CrossRef]
- Taylor, S.J.; Ahmad, F.; Nguyen, H.N.; Shaikh, S.A.; Evans, D.; Price, D. Vehicular Platoon Communication: Cybersecurity Threats and Open Challenges. In Proceedings of the 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN-W 2021), Taipei, Taiwan, 21–24 June 2021; IEEE Computer Society: Los Alamitos, CA, USA, 2021; pp. 19–26. [Google Scholar]
- Viadero-Monasterio, F.; Meléendez-Useros, M.; Jiméenez-Salas, M.; Boada, B.L.; Boada, M.J.L. What Are the Most Influential Factors in a Vehicle Platoon? In Proceedings of the IEEE Conference on Evolving and Adaptative Intelligent Systems, Madrid, Spain, 23–24 May 2024; pp. 375–381. [Google Scholar]
- Khattak, Z.H.; Smith, B.L.; Fontaine, M.D. Impact of Cyberattacks on Safety and Stability of Connected and Automated Vehicle Platoons under Lane Changes. Accid. Anal. Prev. 2021, 150, 105861. [Google Scholar] [CrossRef]
- Malik, S.; Bandi, P.; Sun, W. An Experimental Study of Denial of Service Attack Against Platoon of Smart Vehicles. In Proceedings of the 2021 Fourth International Conference on Connected and Autonomous Driving (METROCAD 2021), Detroit, MI, USA, 28–29 April 2021; IEEE Computer Soc: Los Alamitos, CA, USA, 2021. [Google Scholar]
- Wang, Y.; Zhang, R.; Masoud, N.; Liu, H.X. Anomaly Detection and String Stability Analysis in Connected Automated Vehicular Platoons. Transp. Res. Part C-Emerging Technol. 2023, 151, 104114. [Google Scholar] [CrossRef]
- Zhao, C.; Gill, J.S.; Pisu, P.; Comert, G. Detection of False Data Injection Attack in Connected and Automated Vehicles via Cloud-Based Sandboxing. IEEE Trans. Intell. Transp. Syst. 2022, 23, 9078–9088. [Google Scholar] [CrossRef]
- Bella, G.; Biondi, P.; Costantino, G.; Matteucci, I. TOUCAN A ProTocol tO SecUre Controller Area Network. In Proceedings of the ACM Workshop on Automotive Cybersecurity (AUTOSEC’19), Richardson, TX, USA, 27 March 2019; Assoc Computing Machinery: New York, NY, USA, 2019; pp. 3–8. [Google Scholar]
- Biondi, P.; Bella, G.; Costantino, G.; Matteucci, I. Demo: Implementing CAN Bus Security by TOUCAN. In Proceedings of the 2019 the Twentieth ACM International Symposium on Mobile Ad Hoc Networking and Computing (MOBIHOC’19), Catania, Italy, 2–5 July 2019; ASSOC Computing Machinery: NEW YORK, NY, USA, 2019; pp. 399–400. [Google Scholar]
- Wu, W.; Kurachi, R.; Zeng, G.; Matsubara, Y.; Takada, H.; Li, R.; Li, K. IDH-CAN: A Hardware-Based ID Hopping CAN Mechanism with Enhanced Security for Automotive Real-Time Applications. IEEE Access 2018, 6, 54607–54623. [Google Scholar] [CrossRef]
- Palaniswamy, B.; Ansari, K.; Reddy, A.G.; Das, A.K.; Shetty, S. Robust Certificateless Authentication Protocol for the SAE J1939 Commercial Vehicles Bus. IEEE Trans. Veh. Technol. 2023, 72, 4493–4509. [Google Scholar] [CrossRef]
- Jadoon, A.K.; Wang, L.; Li, T.; Zia, M.A. Lightweight Cryptographic Techniques for Automotive Cybersecurity. Wirel. Commun. Mob. Comput. 2018, 1, 1640167. [Google Scholar] [CrossRef]
- Bella, G.; Biondi, P.; Costantino, G.; Matteucci, I. CINNAMON: A Module for AUTOSAR Secure Onboard Communication. In Proceedings of the 2020 16th European Dependable Computing Conference (EDCC 2020), Munich, Germany, 7–10 September 2020; IEEE Computer Soc: Los Alamitos, CA, USA, 2020; pp. 103–110. [Google Scholar]
- Bella, G.; Biondi, P.; Costantino, G.; Matteucci, I. Designing and Implementing an AUTOSAR-Based Basic Software Module for Enhanced Security. Comput. Netw. 2022, 218, 109377. [Google Scholar] [CrossRef]
- Groza, B.; Murvay, S.; Van Herrewege, A.; Verbauwhede, I. LiBrA-CAN: Lightweight Broadcast Authentication for Controller Area Networks. ACM Trans. Embed. Comput. Syst. 2017, 16, 90. [Google Scholar] [CrossRef]
- Fowler, D.S.; Cheah, M.; Shaikh, S.A.; Bryans, J. Towards A Testbed for Automotive Cybersecurity. In Proceedings of the 2017 10th IEEE International Conference on Software Testing, Verification and Validation (ICST), Tokyo, Japan, 19–17 March 2017; IEEE: New York, NY, USA, 2017; pp. 540–541. [Google Scholar]
- Oruganti, P.S.; Appel, M.; Ahmed, Q. Hardware-in-Loop Based Automotive Embedded Systems Cybersecurity Evaluation Testbed. In Proceedings of the ACM Workshop on Automotive Cybersecurity (AUTOSEC’19), Richardson, TX, USA, 27 March 2019; Assoc Computing Machinery: New York, NY, USA, 2019; pp. 41–44. [Google Scholar]
- Fowler, D.S.; Bryans, J.; Cheah, M.; Wooderson, P.; Shaikh, S.A. A Method for Constructing Automotive Cybersecurity Tests, a CAN Fuzz Testing Example. In Proceedings of the 2019 Companion of the 19th IEEE International Conference on Software Quality, Reliability and Security (QRS-C 2019), Sofia, Bulgaria, 22–26 July 2019; IEEE Computer Soc: Los Alamitos, CA, USA, 2019; pp. 1–8. [Google Scholar]
- Anistoroaei, A.; Groza, B.; Murvay, P.-S.; Gurban, H. Security Analysis of Vehicle Instrument Clusters by Automatic Fuzzing and Image Acquisition. In Proceedings of the 2022 IEEE International Conference on Automation, Quality and Testing, Robotics (AQTR 2022), Cluj-Napoca, Romania, 19–21 May 2022; IEEE: New York, NY, USA, 2022; pp. 13–18. [Google Scholar]
- Marksteiner, S.; Bronfman, S.; Wolf, M.; Lazebnik, E. Using Cyber Digital Twins for Automated Automotive Cybersecurity Testing. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy Workshops (EUROS\&PW 2021), Vienna, Austria, 6–10 September 2021; IEEE: New York, NY, USA, 2021; pp. 123–128. [Google Scholar]
- Cui, L.; Hu, J.; Park, B.B.; Bujanovic, P. Development of a Simulation Platform for Safety Impact Analysis Considering Vehicle Dynamics, Sensor Errors, and Communication Latencies: Assessing Cooperative Adaptive Cruise Control under Cyber Attack. Transp. Res. Part C-Emerging Technol. 2018, 97, 1–22. [Google Scholar] [CrossRef]
- Marksteiner, S.; Marko, N.; Smulders, A.; Karagiannis, S.; Stahl, F.; Hamazaryan, H.; Schlick, R.; Kraxberger, S.; Vasenev, A. A Process to Facilitate Automated Automotive Cybersecurity Testing. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-SPRING), Virtual Event, 25–28 April 2021; IEEE: New York, NY, USA, 2021. [Google Scholar]
- Zhang, H.C.; Wang, J.; Wang, Y.J.; Li, M.F.; Song, J.H.; Liu, Z.L. ICVTest: A Practical Black-Box Penetration Testing Framework for Evaluating Cybersecurity of Intelligent Connected Vehicles. Appl. Sci. 2024, 14, 204. [Google Scholar] [CrossRef]
- Wang, Y.; Masoud, N.; Khojandi, A. Real-Time Sensor Anomaly Detection and Recovery in Connected Automated Vehicle Sensors. IEEE Trans. Intell. Transp. Syst. 2021, 22, 1411–1421. [Google Scholar] [CrossRef]
- Toker, O.; Alsweiss, S. Design of a Cyberattack Resilient 77 GHz Automotive Radar Sensor. Electronics 2020, 9, 573. [Google Scholar] [CrossRef]
- Kengo Oka, D. Building Secure Cars; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Kamal, M.; Kyrkou, C.; Piperigkos, N.; Papandreou, A.; Kloukiniotis, A.; Casademont, J.; Porras Mateu, N.; Baos Castillo, D.; Diaz Rodriguez, R.; Gregorio Durante, N.; et al. A Comprehensive Solution for Securing Connected and Autonomous Vehicles. In Proceedings of the 2022 Design, Automation & Test in Europe Conference & Exhibition (DATE 2022), Antwerp, Belgium, 14–23 March 2022; Bolchini, C., Verbauwhede, I., Vatajelu, I., Eds.; IEEE: New York, NY, USA, 2022; pp. 790–795. [Google Scholar]
- Baldini, G. On the Application of Entropy Measures with Sliding Window for Intrusion Detection in Automotive In-Vehicle Networks. Entropy 2020, 22, 1044. [Google Scholar] [CrossRef]
| Standard/Norm/Guideline | Name |
|---|---|
| ISO 26262:2011 [71] | Road vehicles—Functional safety |
| AUTOSAR (2014) [72] | AUTOSAR safety solutions |
| SAE J3061:2016 [8] | Cybersecurity Guidebook for Cyber-Physical Vehicle Systems |
| ASPICE (2017) [73] | Automotive SPICE Process Reference and Assessment Model |
| ISO 26262:2018 [11] | Road vehicles—Functional safety |
| TR-68 (2019) [74] | Technical reference. Autonomous vehicles (Singapore Standards Council) |
| ISO/TR 4804:2020 [75] | Road vehicles—Safety and cybersecurity for automated driving systems—Design, verification and validation |
| SAE J3061:2021 [76] | Cybersecurity Guidebook for Cyber-Physical Vehicle Systems |
| ISO/SAE 21434:2021 [10] | Road vehicles—Cybersecurity engineering |
| ASPICE for Cybersecurity (2021) [77] | Automotive SPICE for Cybersecurity |
| UN R155 (2021) [9] | Cyber security and cyber security management system |
| UN R156 (2021) [78] | Software update and software update management system |
| UN R157 (2021) [79] | Automated Lane Keeping Systems |
| ISO 21448:2022 [13] | Road vehicles—Safety of the intended functionality |
| AUTOSAR (2022) [80] | AUTOSAR cybersecurity solutions |
| ISO/PAS 5112:202) [81] | Road vehicles—Guidelines for auditing cybersecurity engineering |
| ISO/SAE 24089:2023 [82] | Road vehicles—Software update engineering |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kifor, C.V.; Popescu, A. Automotive Cybersecurity: A Survey on Frameworks, Standards, and Testing and Monitoring Technologies. Sensors 2024, 24, 6139. https://doi.org/10.3390/s24186139
Kifor CV, Popescu A. Automotive Cybersecurity: A Survey on Frameworks, Standards, and Testing and Monitoring Technologies. Sensors. 2024; 24(18):6139. https://doi.org/10.3390/s24186139
Chicago/Turabian StyleKifor, Claudiu Vasile, and Aurelian Popescu. 2024. "Automotive Cybersecurity: A Survey on Frameworks, Standards, and Testing and Monitoring Technologies" Sensors 24, no. 18: 6139. https://doi.org/10.3390/s24186139
APA StyleKifor, C. V., & Popescu, A. (2024). Automotive Cybersecurity: A Survey on Frameworks, Standards, and Testing and Monitoring Technologies. Sensors, 24(18), 6139. https://doi.org/10.3390/s24186139








