Abstract
This article presents a novel hardware-assisted distributed ledger-based solution for simultaneous device and data security in smart healthcare. This article presents a novel architecture that integrates PUF, blockchain, and Tangle for Security-by-Design (SbD) of healthcare cyber–physical systems (H-CPSs). Healthcare systems around the world have undergone massive technological transformation and have seen growing adoption with the advancement of Internet-of-Medical Things (IoMT). The technological transformation of healthcare systems to telemedicine, e-health, connected health, and remote health is being made possible with the sophisticated integration of IoMT with machine learning, big data, artificial intelligence (AI), and other technologies. As healthcare systems are becoming more accessible and advanced, security and privacy have become pivotal for the smooth integration and functioning of various systems in H-CPSs. In this work, we present a novel approach that integrates PUF with IOTA Tangle and blockchain and works by storing the PUF keys of a patient’s Body Area Network (BAN) inside blockchain to access, store, and share globally. Each patient has a network of smart wearables and a gateway to obtain the physiological sensor data securely. To facilitate communication among various stakeholders in healthcare systems, IOTA Tangle’s Masked Authentication Messaging (MAM) communication protocol has been used, which securely enables patients to communicate, share, and store data on Tangle. The MAM channel works in the restricted mode in the proposed architecture, which can be accessed using the patient’s gateway PUF key. Furthermore, the successful verification of PUF enables patients to securely send and share physiological sensor data from various wearable and implantable medical devices embedded with PUF. Finally, healthcare system entities like physicians, hospital admin networks, and remote monitoring systems can securely establish communication with patients using MAM and retrieve the patient’s BAN PUF keys from the blockchain securely. Our experimental analysis shows that the proposed approach successfully integrates three security primitives, PUF, blockchain, and Tangle, providing decentralized access control and security in H-CPS with minimal energy requirements, data storage, and response time.
1. Introduction
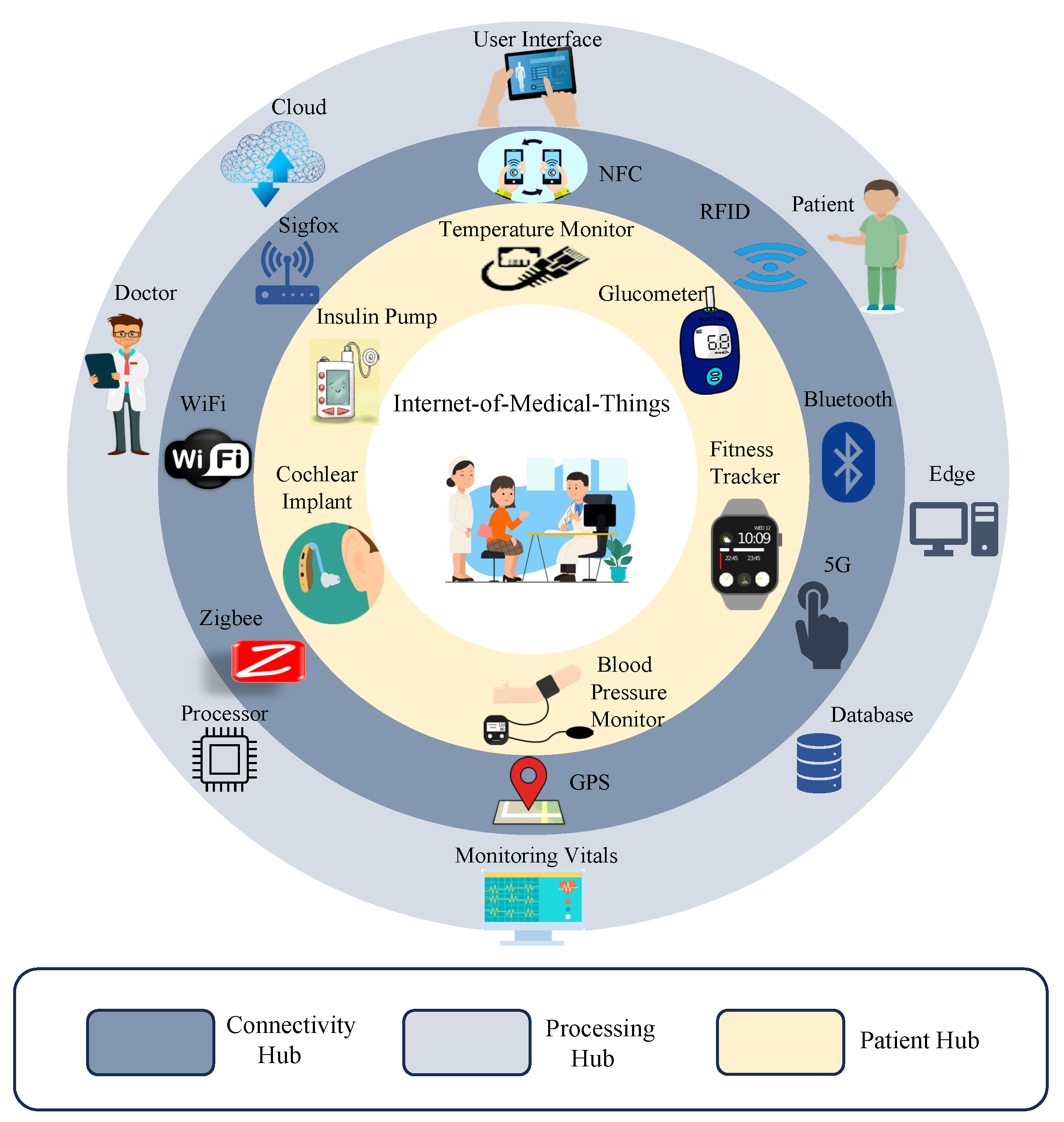
The application of IoMT has made healthcare systems more advanced by integrating various technologies like machine learning (ML), big data, and blockchain [1,2]. Smart e-health service applications are becoming more adaptable through the integration of Medtronic devices for patient physiological metrics monitoring and sensing. Telemedicine, e-health, and connected health are emerging healthcare ecosystems with advanced network communication technologies like 5G, and 6G supporting data sensing, communication, and analysis through AI and ML technologies. Medtronic devices play an important role in realizing the potential of these applications. However, the potential security vulnerabilities have made device integrity, data confidentiality, and privacy pivotal for H-CPS [2]. The architectural overview of healthcare cyber–physical systems is presented in Figure 1.
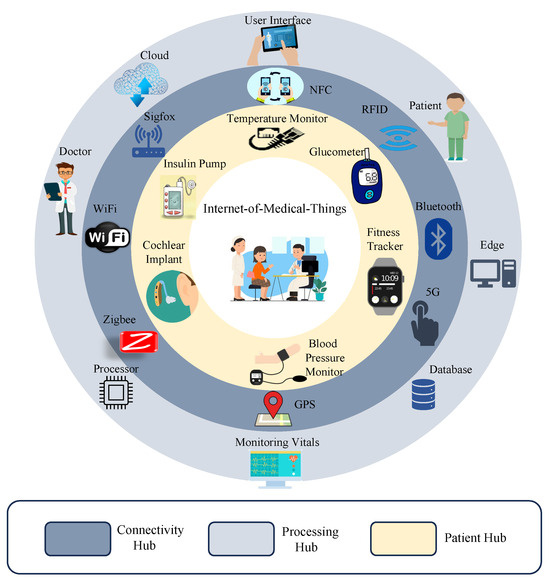
Figure 1.
Healthcare cyber–physical system.
Cybersecurity in Smart Healthcare
IoMT is a collection of heterogeneous smart Medtronic devices with diverse functionalities and capabilities that can sense and process various parameters and are grouped as a hub on the patient to analyze the patient’s physiological parametric data as shown in Figure 2. The data from these heterogeneous devices are analyzed and processed for effective analysis, decision making, and monitoring of patient health [3,4]. These devices are not computationally capable of processing the data and require ML- and AI-supported capabilities for processing and decision making, which can be supported by edge, cloud, and fog computing paradigms. Wearable and implantable medical electronic devices are placed inside and, on the body, to monitor various physiological parameters and generate data. These devices can be smart pumps to deliver insulin dosage, pacemakers that can simulate neurological signals inside the brain, and an active fitness tracker monitoring heart rate and blood pressure [5,6]. Various security attacks are possible through eavesdropping, spoofing, and sniffing to obtain sensitive patients’ physiological information using security vulnerabilities associated with the system. An adversary can intercept the communication between an IoMT device and the health service entity with computing capabilities to obtain access to the system and control it. This can pose a question regarding data integrity and device authenticity in IoMT, which may jeopardize healthcare service applications [7,8].
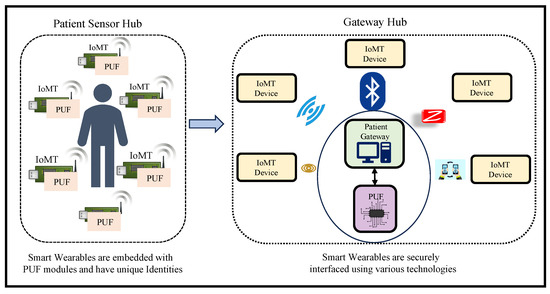
Figure 2.
Patient’s Body Area Network.
To address the data privacy issues in smart healthcare, many researchers have adopted distributed ledger technology (DLT)-based solutions that provide immutability and confidentiality to data [9,10]. DLT can facilitate authorized access to data and can counter any adversarial measure to tamper with the data. These functionalities have made the DLT-based approach for providing security and privacy to data more alluring, specifically in the areas of banking, finance, e-health, and smart cities which demand the utmost secrecy and confidentiality of data in their applications.
IoMT devices are vulnerable to various types of physical attacks [11,12]. Cybersecurity solutions are often based on software-based approaches that work based on symmetric and asymmetric key cryptography schemes. These approaches require non-volatile memory or drives for key storage and retrieval. Using asymmetric keys for encryption and data decryption can sometimes restrict access to medical professionals or patients [13]. This sort of dependence on memory has made these security protocols more vulnerable to various ML attacks, where an attacker can obtain access to the secret key and the system [14]. SbD is one of the new paradigms that has attracted much attention from the research community. This approach focuses on building a security model right from the design stage. PUF is a prominent SbD that is a unique hardware identity generation scheme.
Various hardware-assisted security (HAS) approaches for cybersecurity are being adopted using PUF and Trusted Platform Modules (TPMs) to achieve the objective of SbD [11,15]. PUF-based security solutions include a PUF module that is embedded in a chip and can generate keys from the PUF design using process variations inside an Integrated Circuit (IC) [11,15,16]. The generated keys can be used as security keys or identities for that PUF module on the chip. PUFs do not require a database for key storage, and PUF responses are generated instantly by taking advantage of micro-manufacturing process variations during chip fabrication [15,17,18]. Data confidentiality, integrity, privacy, and device authentication are requirements for sustainable SC. Blockchain has been one of the most widely explored DLTs for financial transactions since its inception in 2008 [19]. However, resource-constrained IoT devices cannot sustain the computational resource requirements of blockchain’s consensus mechanisms like Proof-of-Work (PoW). Data immutability, integrity, and privacy in SC are guaranteed by blockchain through its scalable, decentralized physiological data management using energy-efficient consensus mechanisms [11].
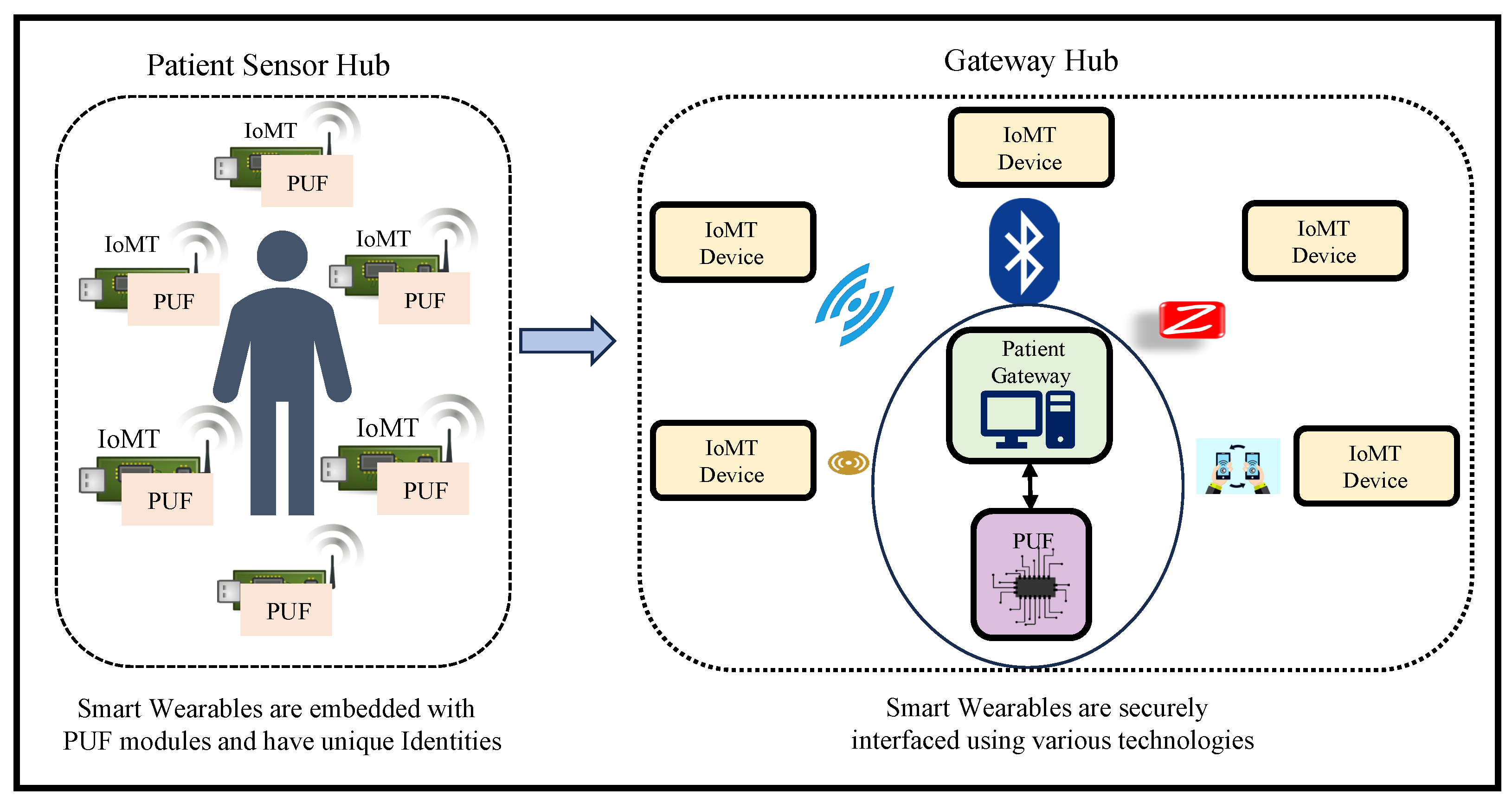
The motivation for this research is to ensure the security of IoMT devices and their data, where the patient’s BAN PUF keys are securely stored inside a global blockchain to provide end-point security. Tangle is used for the secure communication of the patient’s physiological sensor data, and their access is controlled using a unique identity generated by PUF for the patient’s gateway. The proposed architecture works on integrating PUF with a DLT for providing a sustainable security primitive for IoMT-driven smart healthcare as illustrated in Figure 3.
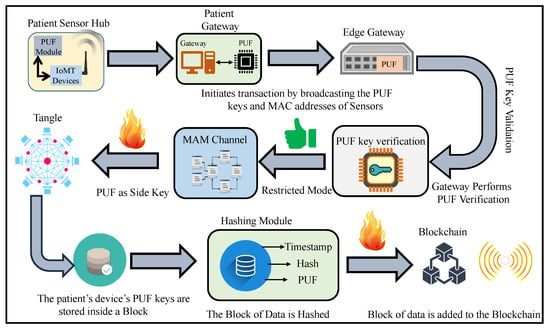
Figure 3.
Architectural overview of proposed SbD approach for H-CPS.
Following the introduction, the rest of the paper is organized as follows: Section 2 presents the novel contributions of this paper. Section 3 discusses various hardware security schemes and DLT-based solutions in SC from the literature. The conceptual overview of SbD and the role of PUF as a formidable security primitive is given in Section 4. Section 5 explains IOTA Tangle, transaction validation, and Masked Authentication Messaging (MAM) concepts. A brief overview of blockchain technology is given in Section 6. The working flow of the device authentication and transaction validation process in the proposed PUFchain 3.0 is explained in Section 7. Section 8 outlines the implementation details, and Section 9 presents the conclusion and directions for future research.
2. Novel Contributions
In this section, we explain the challenges and contributions of the present work in Section 2.1. We present the novelty and significance of our present work PUFchain 3.0 in Section 2.2. Finally, a brief overview of our PUFchain idea, first ever hardware-assisted blockchain, and its variants are given in Section 2.3.
2.1. Research Problems Addressed in the Current Paper
The proposed work was envisioned to address the following questions:
- To the best of our knowledge, very few security primitives work on providing device and data-assisted security simultaneously for e-Health applications;
- Security gaps associated with device integrity, data confidentiality, and authenticity in edge computing-driven H-CPS;
- Lack of scalable and energy-efficient security approach for resource-constrained distributed systems in H-CPS;
- Sustainable approach to the device integrity-based access control mechanism for electronic health records (EHRs) management;
- Energy-efficient PUF architectures that are effective against machine learning and other attacks;
- Lack of sustainable and energy-efficient hardware-assisted access control mechanisms to the distributed ledger;
- A secure communication interface between various stakeholders in H-CPS with defined access and security;
- Presenting a security framework that could be integrated into real-world healthcare applications;
- Providing a cost-effective innovative approach to integrate various technologies for cybersecurity in smart healthcare;
- Enabling a patient to embed smart health devices that are secure and non-vulnerable to security attacks.
2.2. Novel Contributions of This Article
- Presenting a novel state-of-the-art integration of PUF, blockchain, and Tangle for SbD of H-CPS. To the best of our knowledge, this is the first work on hardware-assisted security in H-CPS that presents a PUF-based approach for access to DLT for device and data security in H-CPS.
- Presenting a novel PUF-based access control mechanism for Tangle.
- A novel blockchain-integrated framework for security in H-CPS using smart contracts.
- Validating the proposed framework in the MAM “Restricted mode” for secure access control to Tangle using PUF.
- An energy-efficient SbD approach that uses delay Arbiter and XOR PUF architectures.
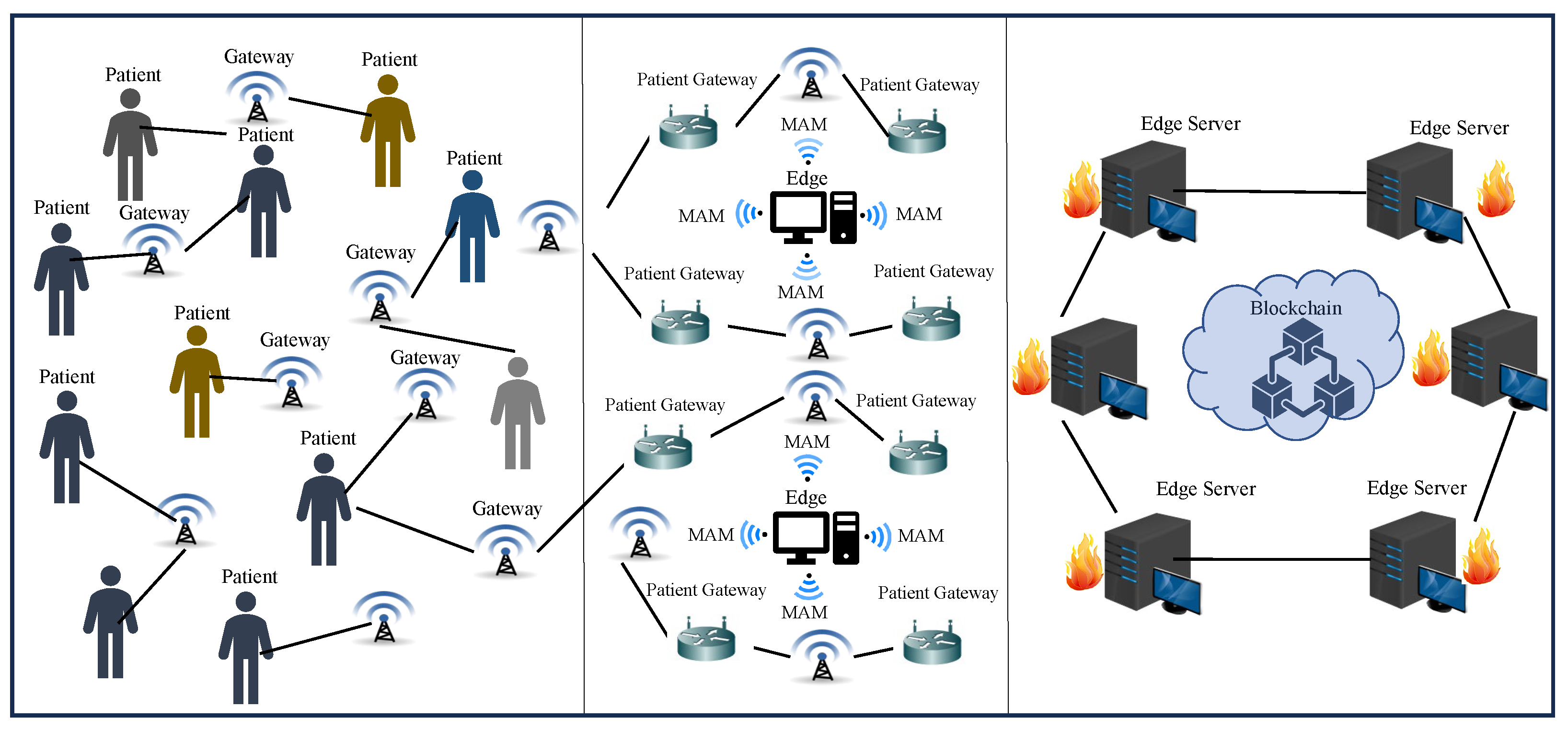
- An edge–cloud-driven approach for resource-constrained systems in H-CPS that has three layers—physical layer, edge layer, and blockchain layer as illustrated in Figure 4.
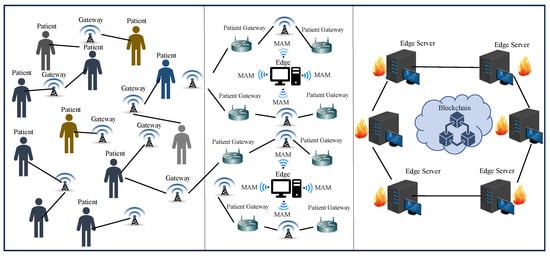 Figure 4. Layered view of PUFchain 3.0 Architecture.
Figure 4. Layered view of PUFchain 3.0 Architecture. - A novel energy-efficient approach that works on blockchain using smart contracts for storing and retrieving PUF keys of IoMT devices inside a patient’s Body Area Network (BAN).
- A security approach that facilitates secure access to patients’ BAN and ensures the integrity of data from IoMT in resource-constrained distributed systems.
2.3. A Comprehensive Evaluation of PUFchain Primitives
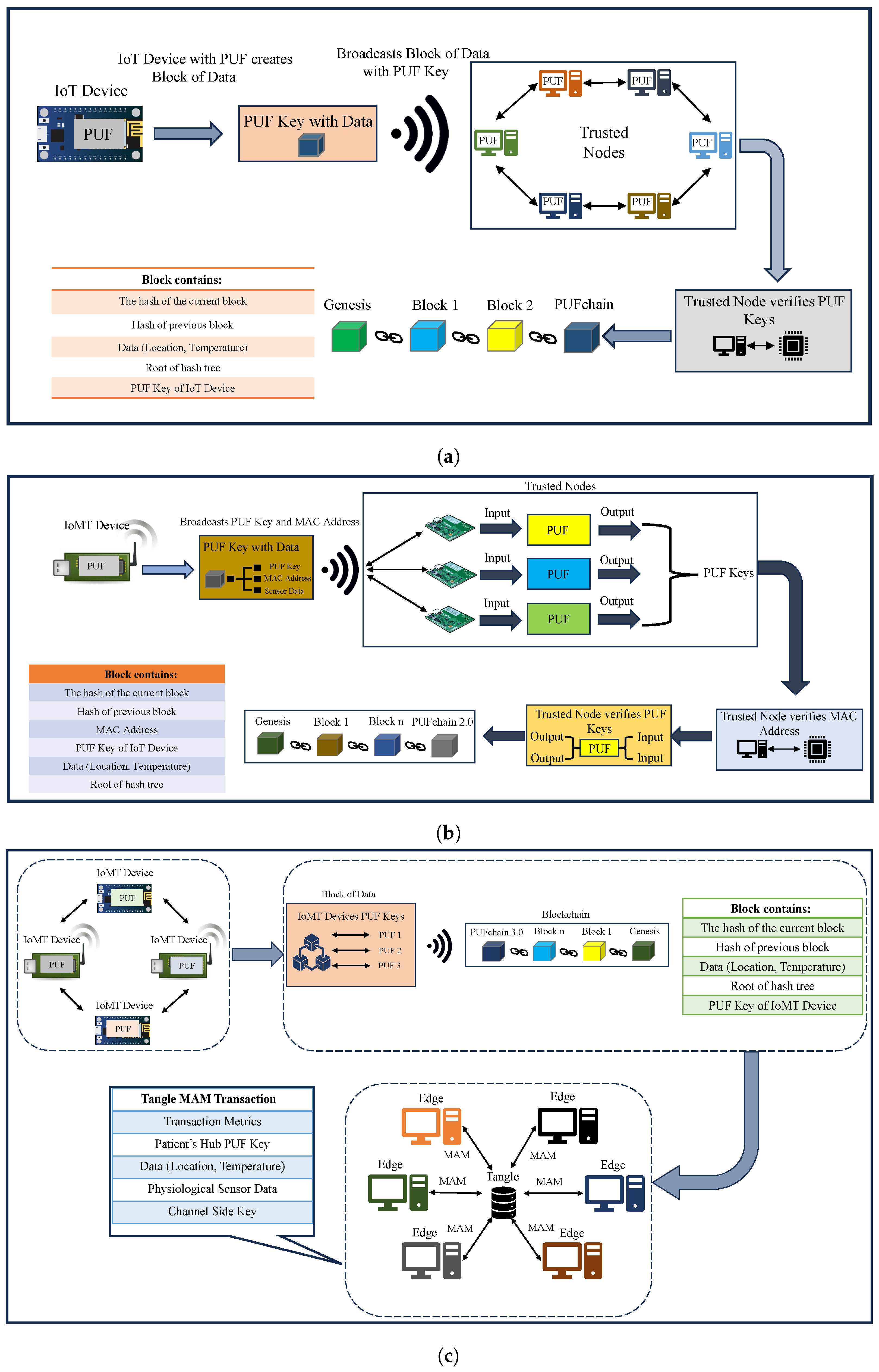
The conceptual idea of PUFchain is presenting a hardware-assisted secure distributed ledger for sustainable device and data security in the emerging Internet of Everything (IoE). Hardware-assisted security involves embedding advanced electronic systems with PUF for device integrity. PUF-embedded security facilitates each electronic system to obtain a unique device identity that can relate to blockchain and other distributed ledgers. Table 1 and Figure 5 present a comparative analysis of our PUFchain variants.

Table 1.
Comparison of PUFchain variants.
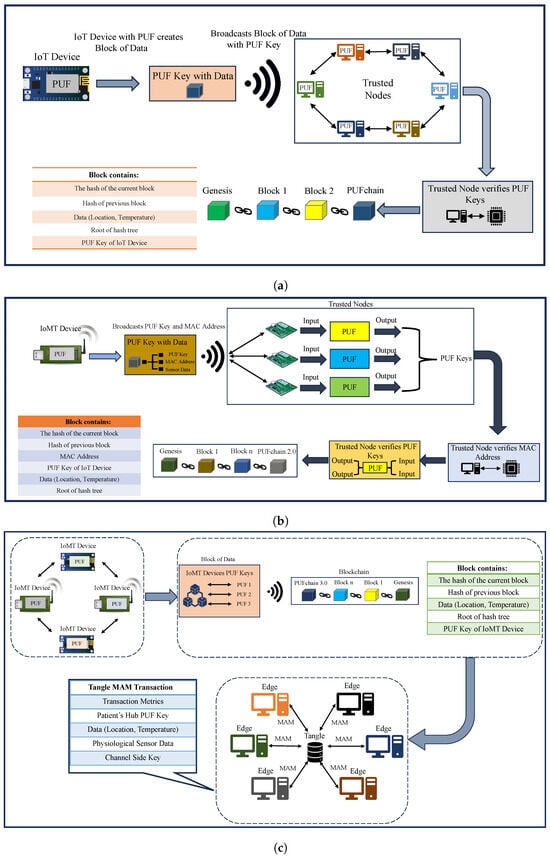
Figure 5.
PUFchain variants. (a) PUFchain; (b) PUFchain 2.0; (c) proposed PUFchain 3.0.
3. Related Works
In this section, we have presented a brief review of related research on various distributed ledger technology-based cybersecurity solutions in smart healthcare. A comparative analysis of the proposed work PUFchain 3.0 with state-of-the-art research is given in Table 2.
Integration of hardware-assisted distributed ledger for SbD of CPS has gained prominence for addressing security gaps in various CPS, which include Healthcare CPS, Agriculture CPS, and Transportation CPS. The authors in [21] presented a scalable blockchain integrated distributed ledger solution for IoT applications. Their architecture has a blockchain running in the backend and a Tangle in the frontend. This approach claims to speed up the data processing from IoT devices by securely integrating with Tangle, which then offloads the data storage to blockchain in the cloud. In [22], the authors proposed an IC supply chain management system using PUF-based blockchain. Their work proposes a PUF-based chip-tracking system that uses blockchain to securely record and trace the ownership of a chip. A consensus mechanism for IoT applications is proposed in [23]. Their work presented a consensus mechanism titled “PoQDB”, which integrates blockchain with the CoBweb ledger to facilitate IoT data storage. The proposed work PUFchain 3.0 is an extension of the initially presented PUFchain [19], which is a novel integration of PUF and blockchain using a Proof-of-PUF-Enabled-Authentication (PoP) consensus mechanism for IoT security.
SbD of H-CPS is a focus area for many researchers since privacy and security issues have direct implications on the patient’s life. A smart, remote patient-monitoring system using IOTA is presented in [24]. The research proposed and validated an IOTA MAM-based approach for patient data access control and security. Using IPFS and MAM, their research validated an approach for patients’ IoT device control and access using a secure web interface. A blockchain-assisted solution for IoMT device security and access control is proposed in [25]. The motivation of their work is to provide security between different entities in healthcare systems. The blockchain-assisted IoMT key exchange mechanism is presented in [26]. Their work aims to address the single-point failure problem in processing data securely from IoMT devices. They presented a private consortium blockchain to validate the work and proposed a scheme for securely establishing communication between authenticated IoMT devices. However, their work uses cryptography to secure the keys of IoMT devices, which can be vulnerable to ML attacks. The authors in [9] proposed a secure IoMT data sharing scheme using IOTA MAM. Different modes of MAM were used to publish data onto Tangle, which included sensor and patient data. A PUF-based approach for the security of low-cost IoT devices in healthcare is proposed in [27], which presents a microcontroller based PUF that has 99% accuracy. The authors in [28] designed a blockchain-enabled IoMT device authentication architecture that presents an approach for encrypted communication and certificate-based identity attestation in IoMT. The detection of IoMT device malfunctioning and behavior is another efficient approach for device security. The authors in [29] presented a privacy-preserving IoMT device behavior detection using blockchain. In the paper, they validated this approach for insulin pumps to monitor patient’s glucose levels.
For sustainable device and data security in smart healthcare, we proposed a PUF-based blockchain solution named PUFchain 2.0 [11]. In this work, we validated and presented a PUF-based blockchain consensus mechanism for simultaneous device and data security. We observed the potential of hardware-assisted distributed ledgers for security in smart healthcare. The proposed PUFchain 3.0 work extends the potential of the PUF-based distributed ledger in smart healthcare by facilitating decentralized security and access control to IoMT devices and their data in H-CPS. In comparison with the related research, our work presents an architecture to address both device and data security with minimal latency and better scalability, thereby facilitating secure access control and security in smart healthcare.

Table 2.
Comparative analysis with state-of-the-art research.
Table 2.
Comparative analysis with state-of-the-art research.
| Research Works | Application | Security Primitive | Platform | Mechanism |
|---|---|---|---|---|
| Hellani et al., 2021 [21] | IoT (Data) | Blockchain and Tangle | Edge–Cloud | Smart Contracts |
| Mohanty et al., 2019 [19] | IoT (Device and Data) | PUF, blockchain | Edge | Proof-of-PUF-Enabled-Authentication |
| Al-Joboury et al., 2021 [23] | IoT (Data) | Blockchain and Cobweb | Cloud | IoT M2M Messaging (MQTT) |
| Wang et al., 2022 [30] | IoMT (Device) | Blockchain | Edge | Smart Contracts |
| Chaudhary et al., 2021 [22] | Hardware Supply Chain | PUF, blockchain | Edge–Cloud | Smart Contracts |
| Venkata et al., 2022 [11] | IoMT (Device) | PUF, blockchain | Edge | Media Access Control (MAC) and PUF-based Authentication |
| Satra et al., 2023 [14] | IoMT (Device) | PUF | Edge | Machine Learning |
| Fotopoulos et al., 2020 [28] | IoMT (Device) | Blockchain | - | Self- Sovereign Identity (SSI) |
| Zheng et al., 2023 [9] | IoMT (Data) | IOTA Tangle and blockchain | Edge | MAM |
| Proposed PUFchain 3.0 [20] | IoMT (Device and Data) | PUF, Tangle, blockchain | Edge–Cloud | Masked Authentication Messaging, smart contracts |
4. Role of Physical Unclonable Functions as SbD Primitive
4.1. Security-by-Design
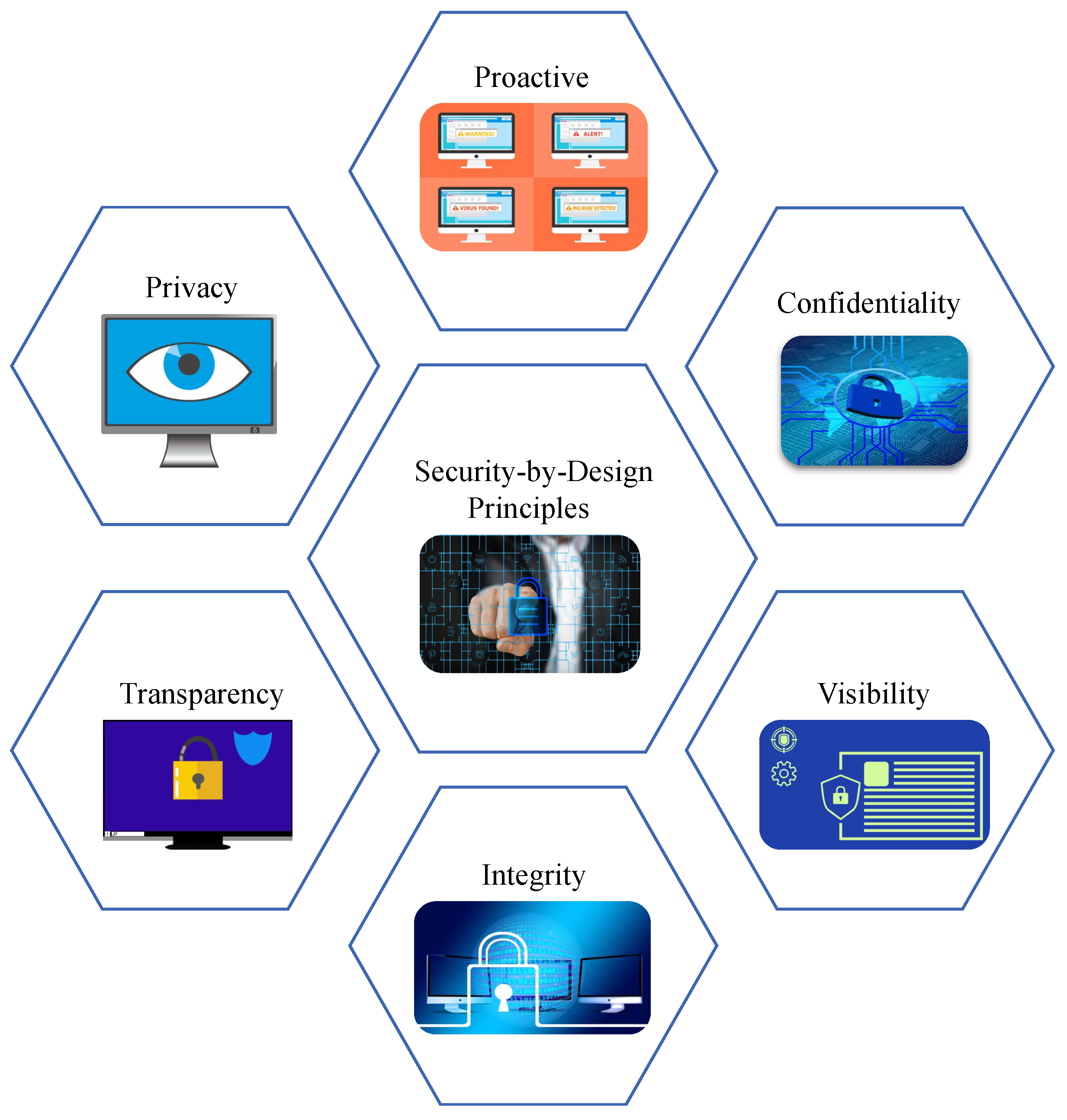
SbD, or Privacy-by-Design (PbD), is a system development paradigm for smart electronics that emphasizes the security of an electronic system at the development stage, considering the intrinsic properties at the design, manufacturing, testing, and implementation. The principles and objectives of SbD as explained in Figure 6 mainly envision to avoid performance trade-offs in security primitives at the application stage of an electronic system [31,32].
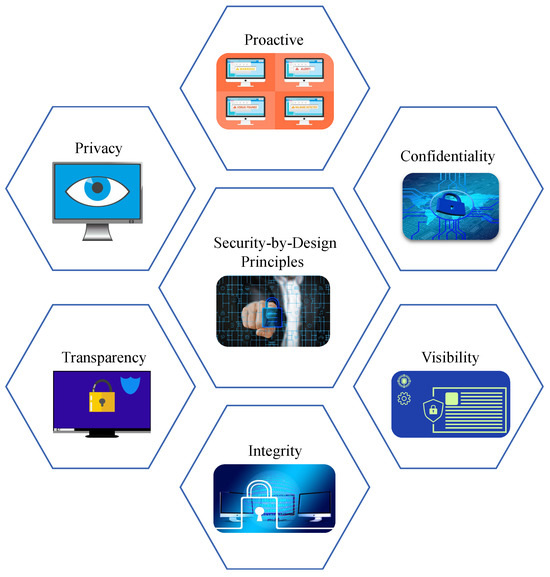
Figure 6.
Security-by-Design principles.
The principles of SbD are as follows:
- Proactive but not reactive: Existing cybersecurity solutions for smart electronics mostly focus on the security at application level. SbD promotes security as a design stage metric that is enabled by default.
- End-to-end security: The security of the system should be considered right from the design stage to manufacturing, deployment, application, and maintenance.
- Security as default: The security primitive should be enabled by default in the system and cannot be an optional primitive for the users to choose from.
- Least privilege: Users of an electronic system should have the privilege of running the applications and should not have access to tamper with the system’s security specifications.
- Transparency: The security principles should be clearly transparent and easily understandable. The users of an SbD-enabled system should have access to change their security level based on their choice and should be able to clearly understand its functionality.
- User centricity: The ease of security principles and deployment is an essential aspect of SbD. The security primitives should not be burdensome for the users.
- Full functionality: The security primitive should have efficient performance and should not have performance trade-offs that might impact the system’s functionality and applications.
4.2. PUF for SbD of H-CPS
PUF is a hardware security primitive that uses device inherent manufacturing imperfections and generates a unique cryptographic identity. Each electronic device has a unique topology due to the manufacturing variations during the fabrication of an Integrated Circuit (IC), which is the building block of a consumer electronic system [33]. As each device has a distinct topology, unique keys can be derived based on its device property variations, such as frequency, delay, or the startup phase of a volatile memory cell. Process variations can be observed during various stages of an IC fabrication process, such as lithography, ion implantation, metallization, and packaging [20]. The variations introduced during these processes will slightly differentiate each device from the corresponding ones, even if they have the same fab, processes, and design. PUF works by deriving a key of random zeros and ones using the device’s intrinsic properties. PUFs can be classified based on the mapping of physical properties. PUF modules that work based on the propagation delays and frequency variations in an IC to build a unique bit stream are delay-based PUFs. Arbiter and Ring oscillator, XOR, and Butterfly PUF are widely used delay PUFs. These are also referred to as strong PUFs that can support the extraction of many random zeros and ones as a bit stream, which is essential for security applications. Similarly, Static Random Access Memory (SRAM) and Dynamic Random Access Memory (DRAM) are prominent memory PUF modules that work by generating a unique response based on the variations in the memory structures such as Flip Flops and an SRAM cell. The structure of Arbiter and XOR PUF used for experimental validation in this work is presented in Figure 7. The PUF module works on the physical randomness of devices by mapping a challenge input to a unique response output string. The uniqueness of this primitive is that it does not generate the same responses for varying challenge inputs. Also, two different PUF modules tested against the same challenge input will have varying bits of random zeros and ones as responses [19,34]. The responses from PUF are evaluated against various metrics to verify the strength of the keys. Some of the figures-of-merit (FoMs) of PUF are illustrated as follows:
- Uniqueness: Verifying the extent of variation of the responses from a PUF circuit on two devices is referred to as uniqueness. This is measured by calculating the average inter-Hamming distances of responses from the PUF module on two devices tested with the same set of challenges.
- Reliability: The stability of a PUF is determined by determining the variation of the responses under different environmental conditions. This is an essential metric in evaluating a PUF strength since the responses of the PUF must be stable under noise as well as under varying operating conditions.
- Randomness: The randomness of a PUF is its ability to produce a response key with an equal number of randomly distributed ones and zeros. Ideally, a PUF response should have exactly an equal number of ones and zeros in the response bit stream.
- Diffuseness: The diffuseness of a PUF is obtained by calculating the average intra-Hamming distance of PUF responses to verify the extent of variation of responses for varying challenge inputs in the same PUF.
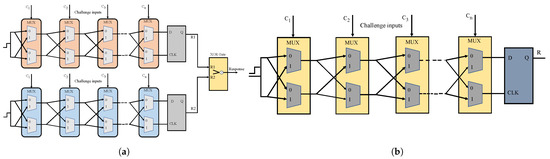
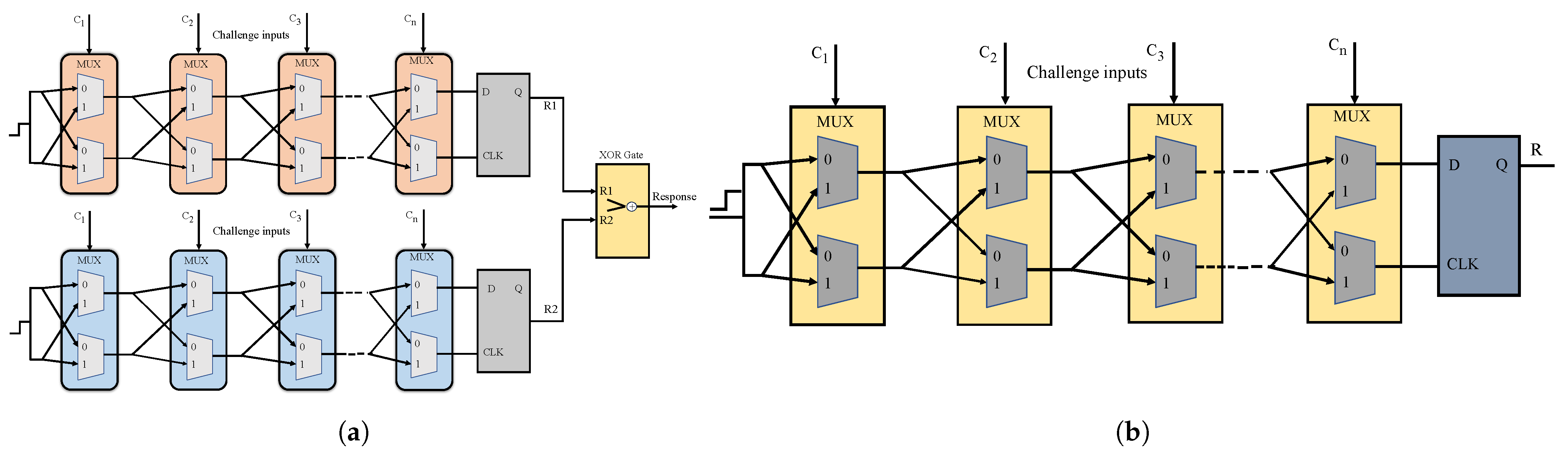
Figure 7.
Architectures of delay PUFs experimentally validated in the proposed work. (a) XOR Arbiter PUF; (b) Arbiter PUF instance generating 1-bit output.
Figure 7.
Architectures of delay PUFs experimentally validated in the proposed work. (a) XOR Arbiter PUF; (b) Arbiter PUF instance generating 1-bit output.
5. IOTA Tangle: A DAG Blockchain
IOTA Tangle is a DAG-based blockchain that has a Tangle structure. It is a distributed ledger from IOTA and one of the most suitable DLT-based solutions in IoT applications due to its miner and feeless functionality. All the transactions in Tangle are part of the directed acyclic graph (DAG) structure. The major advantage of this structure is that it increases the transaction validation rate exponentially when compared with the traditional blockchain structure that has all the transactions aligned sequentially [24]. Every new transaction on Tangle from a node validates the unconfirmed transactions called “Tips” to become part of the structure. Every incoming transaction validates tips using Proof-of-Work, and therefore increasing the number of incoming transactions substantially increases the rate of validated transactions. Tips are selected using the ‘Markov Chain Monte Carlo (MCMC)’ random walk algorithm which traverses the DAG and determines the transactions to be validated [35,36]. Proof-of-Work (PoW) validates a transaction by calculating the nonce and solving cryptographic puzzles. Once the tips are validated by an incoming transaction, then these transactions become confirmed in Tangle. PoW in Tangle is computationally resource efficient in comparison with blockchain’s PoW consensus mechanism [37].
Each transaction node in Tangle has a cumulative weight, which is calculated by adding its initial weight, and the cumulative weight of all the transactions directly or indirectly approve it [38,39]. In this DLT, a coordinator is responsible for overall transaction validation and approval. At present, the IOTA foundation is the coordinator that releases the milestones defining transaction validation rules. Simply, a coordinator is responsible for the overall functioning of the transaction validation approval process in Tangle [40]. A milestone is a stage where confirmed transactions become irreversible and final on Tangle [41].
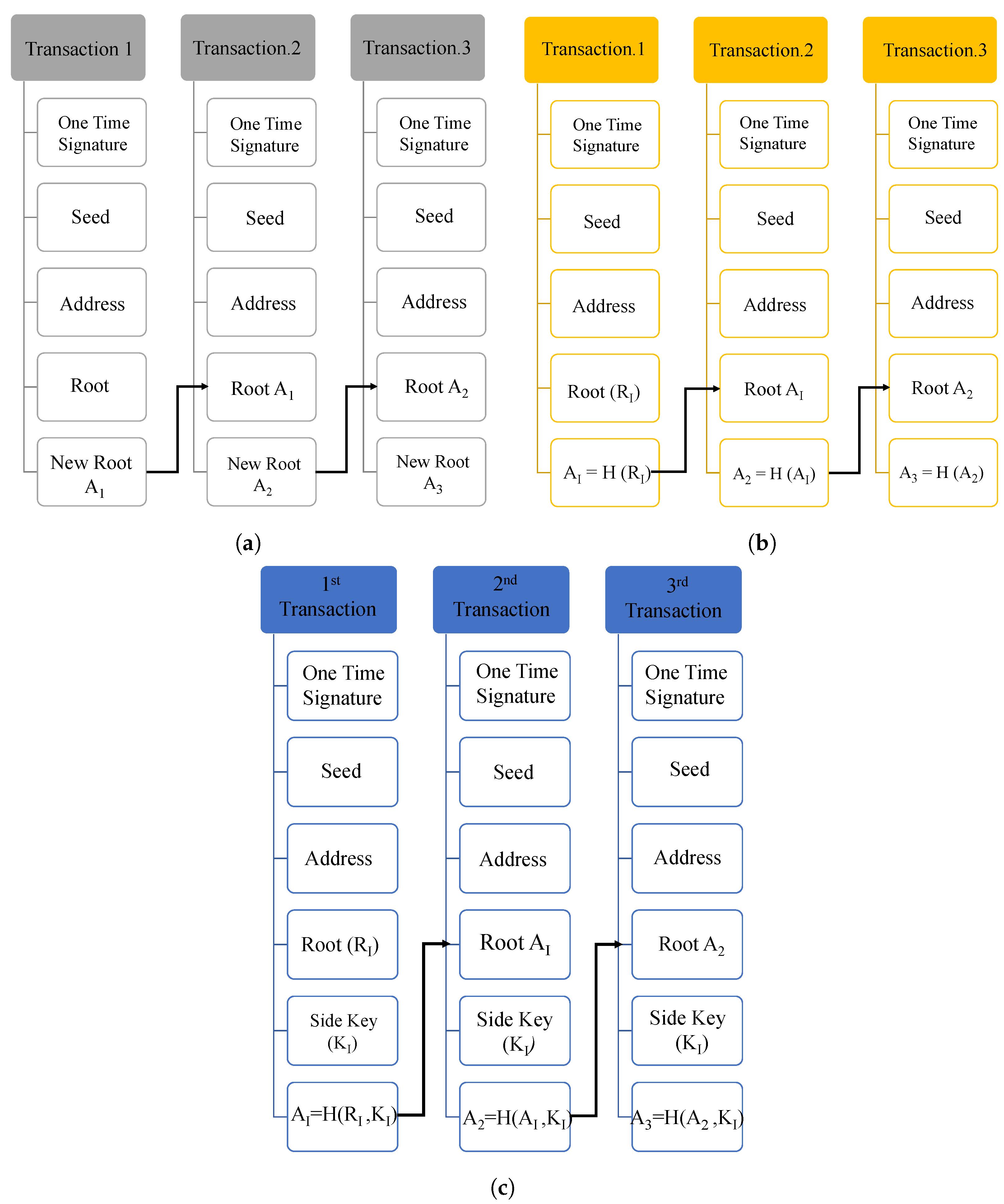
IOTA MAM is a secure messaging protocol that operates on the IOTA main network for sending and receiving the encrypted information in Tangle through a channel by signing the message using the Merkle Hash Tree (MHT) signature algorithm. The message can be accessed by the receiver using the channel’s address, and whenever a new message of any length and size is uploaded on Tangle, a channel is created, and the receivers can immediately access the data using the root of the MHT. MAM operates in three different communication modes: public, private, and restricted [24].
Each channel mode has a distinct functionality and security level based on the application. Each transaction on the MAM channel has a reference to the next transaction address, which links all the transactions on that channel. However, each MAM mode has a different way of working to access the new transaction address as illustrated below: [42,43,44]. MAM works mainly in three modes: public, private, and restricted. The working flow of MAM in public, private, and restricted modes is illustrated in Figure 8.
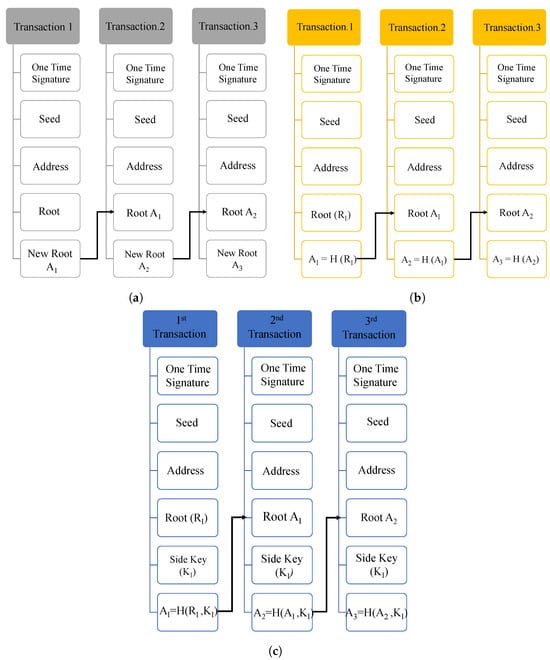
Figure 8.
Masked authentication messaging. (a) Public mode; (b) private mode; (c) restricted mode.
Public mode: In the public channel mode, the Merkle tree root is used as the MAM transaction address. A MAM channel with an address is generated to secure the information exchange. The address of the channel will be the root of the Merkle tree. The subsequent transaction must be submitted to the MAM channel using this fetched root, and anyone with the channel ID or address can access the channel and receive the messages.
Private mode: In the private mode, the address of a MAM transaction is obtained by hashing the root of the Merkle root. For applications requiring privacy and confidentiality, as in the case of health record management, the private mode is suitable and efficient since only the subscribers with the root can decrypt the messages.
Restricted mode: The restricted mode of MAM works by using a channel authorization key or side key along with the Merkle root. In this channel mode, along with the root, the side key is also hashed to obtain the transaction address on the channel. This mode provides the highest level of security for the transactions on MAM since only subscribers with an authorization key can access the transactions on the channel.
6. Overview of Blockchain Technology
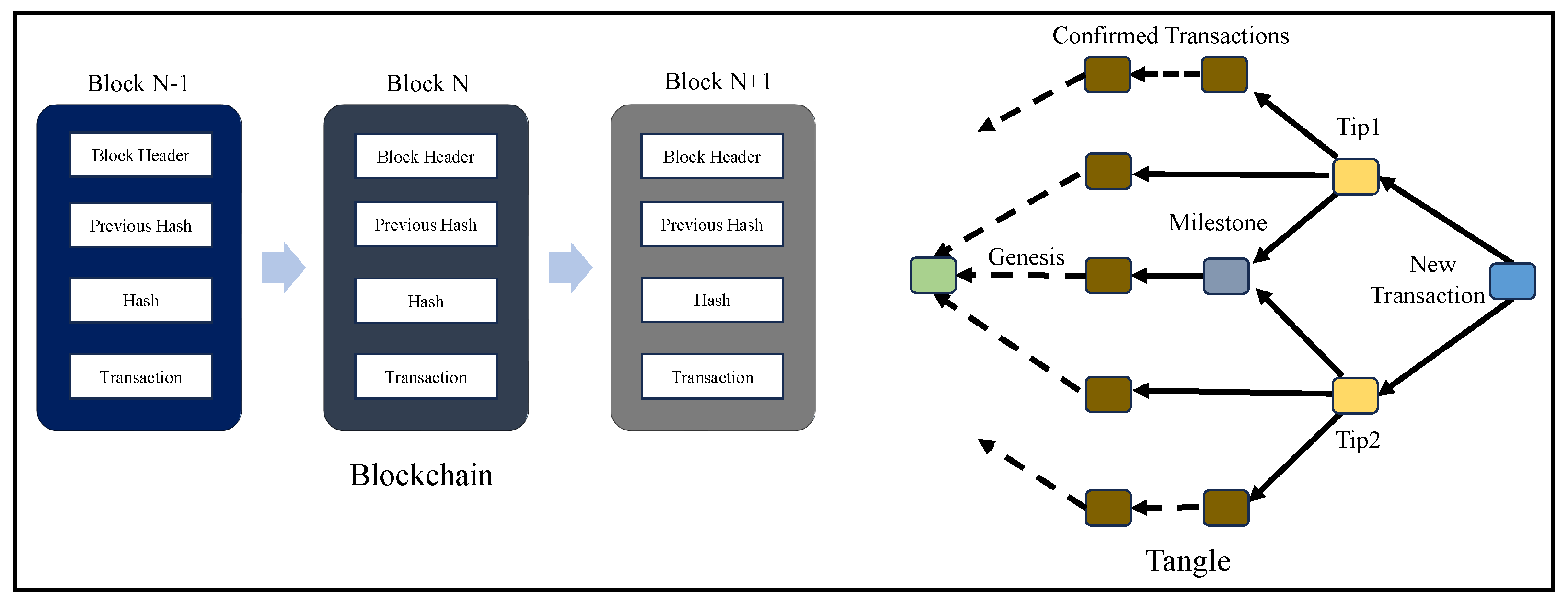
The success of blockchain in providing integrity and authenticity to data is not just limited to H-CPS but also in other areas of CPS, like smart transportation, Industrial IoT, and Agriculture CPS. A simple decentralized data validation and verification system provided by blockchain has made it the most alluring research area in the 21st century. Each transaction in blockchain is stored inside a block of data, which is hashed and has reference to the previous block’s hash. Miners are responsible for block validation in blockchain [11]. The validation of a block is performed through a consensus mechanism that defines rules for choosing the miners and validating the transactions. Research on blockchain consensus mechanisms has become a focus area for the research community. In all the blockchain consensus mechanisms, a miner is required to validate the transaction, and various checks and balances are in place to negate the probability of fake block generation and validation. The 51% percent attack is one of the challenges of blockchain where fake nodes could control 51% of the block addition process [19]. Blockchain technology has been perceived to be a breakthrough in realizing the potential of digital ledger technology (DiLT) for IoT-based applications. Blockchain’s robustness and features have made integration with various technologies like AI and ML an important area to work on. As various security solutions using blockchain for data have already been proposed, more emphasis is being laid on exploring the possibilities for hardware-assisted blockchain for security [12,45]. Blockchain and Tangle have varied data structures. In blockchain, the transactions are validated and added inside blocks which are aligned sequentially. Tangle is based on the Merkle tree, and it does not take much time to check whether a transaction is fake since it is a tree-based structure generation scheme [10,43]. Tangle transactions are signed using a one-time signature scheme (OTS). The Merkle tree consists of private keys as leaves which are hashed and consolidated to obtain the root address. Figure 9 presents a comparative perspective of blockchain and Tangle.
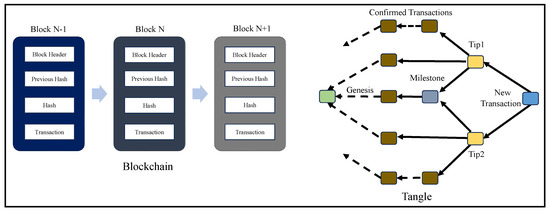
Figure 9.
Blockchain vs. Tangle.
PoW, proof-of-stake (PoS), and proof-of-authentication (PoAh) are prominent consensus mechanisms. Each consensus mechanism has unique advantages and challenges that ensure a sustainable block validation process in the blockchain. Blockchain’s prime working principles are confidentiality, integrity, and authenticity. All the advanced applications such as smart cities, healthcare, agriculture, and transportation have blockchain-assisted security solutions, as they guarantee and provide integrity and immutability to data and facilitate decentralized access control. The PoW consensus mechanism involves block validation, which works based on solving a mathematical puzzle to obtain the hash value of a transaction. However, it has more computational and energy resource requirements. PoS includes a stake-based miner selection approach, which works by selecting a miner with a large amount of stake. This approach can centralize the block validation to the nodes with a higher amount of stake. For hardware-assisted IoT-based applications, PoAh presents a device authentication mechanism that verifies the integrity of IoT devices to accept the data and validate transactions in IoT applications. Blockchain has been classified into public, private, and consortium based on the number of nodes in the network. Public blockchains have many nodes, whereas private blockchains have a limited number of nodes. Public blockchain has privacy issues since the copy of each transaction is shared globally among various stakeholders in the network. A consortium blockchain is a hybrid one that has features of both public and private blockchain.
EHR management is one of the most important applications of blockchain in healthcare. EHR stores the data, provides access only to authorized individuals, and can restrict unauthorized access. Private, public, and consortium blockchain architectures achieve data confidentiality depending on the access control. Decentralized ledger technology (DeLT) is a database accessible to all trusted parties in the network to read and access the data. DLT, on the other hand, enables the trusted parties to upload and update the changes to data in the database.
7. PUFchain 3.0: Proposed Security-by-Design (SbD) approach for Smart Healthcare
In this section, we briefly illustrate the architectural overview of the proposed SbD approach and its working in different phases in Section 7.1. The notations used for each of the components and their associated operations are given in Table 3.

Table 3.
Notations.
7.1. Design and Analysis of Proposed Framework
The proposed work explores the scope of hardware-assisted distributed ledger and blockchain for robust security in H-CPS. The proposed framework uses blockchain’s smart contracts, IOTA MAM, and PUF primitives for the security of devices and data in smart healthcare. In the proposed approach, the PUF-embedded smart sensors in the patient’s health network or BAN could securely connect to the patient’s gateway that is further connected to an edge for the secure verification of PUF keys of IoMT devices. Once the verification is successful, the edge node initiates a MAM channel creation and uses the patient’s gateway PUF key as the MAM channel side key for that hub. MAM is used to securely transfer data and upload data on Tangle. Therefore, each patient’s physiological sensor data could be shared globally among various stakeholders in the H-CPS through a PUF-based integrity-checking scheme. Blockchain in the proposed framework works on storing each patient’s PUF-generated device identities in a hub and can only be accessed by authorized stakeholders globally. This approach reduces the exposure of PUF keys of IoMT devices and reduces the need to store the PUF keys of all the devices inside a patient’s hub. MAM can work on the patient’s gateway key to securely access and upload data from these devices. Blockchain is operated by the stakeholders when a patient’s sensor hub must be accessed and the devices’ integrity must be verified.
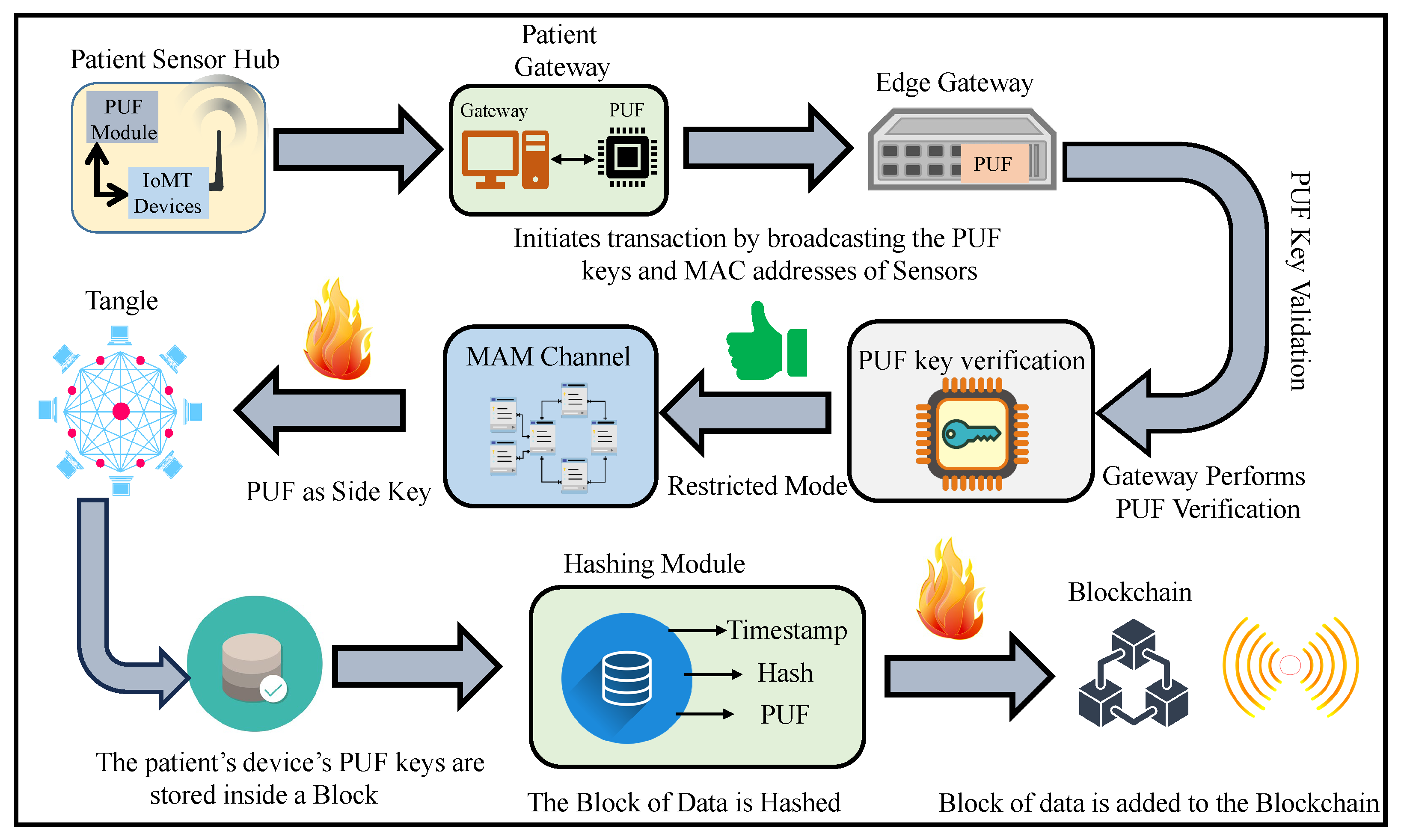
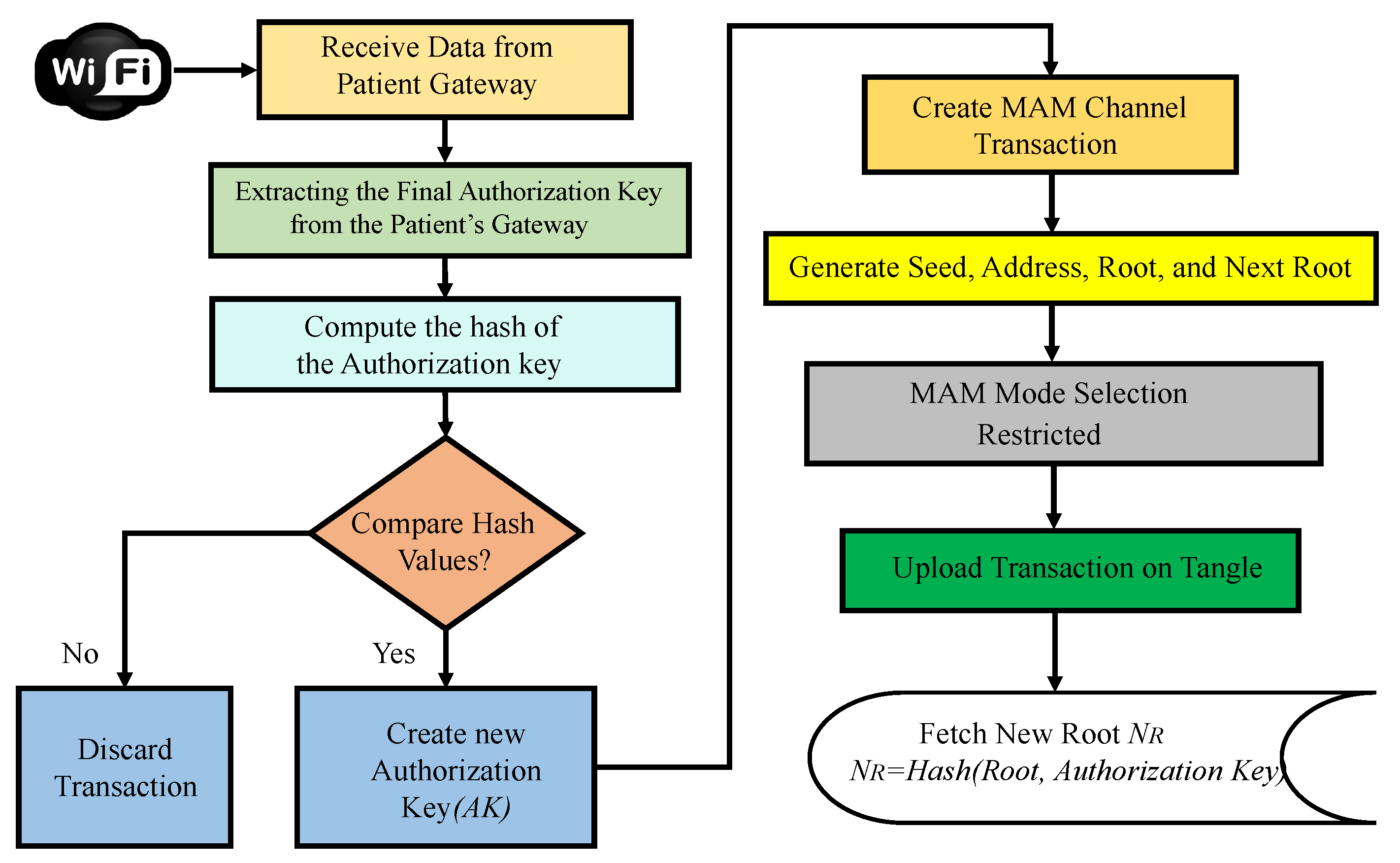
- Patient’s sensors and gateway registration phase: Initially, all the smart wearable and implantable medical devices are connected to a patient’s gateway. These devices are connected to the gateway through various technologies like NFC, ZigBee, and BLE. All these devices have a PUF-embedded key as their pseudo-identity. The gateway also has a unique PUF-generated identity which acts as the address for this hub of devices. When the edge gateway receives an initiation request from the patient’s gateway, it securely verifies the gateway’s integrity by performing PUF key extraction and validation. Once the validation is successful, the Tangle transaction validation process starts. Initially, the edge gateway connects to a public IOTA node for securely interfacing with IOTA Tangle. The IOTA node then creates a MAM channel to upload and share data. In the proposed approach, the MAM channel operates in the restricted mode, which requires an authorization key for uploading and receiving data onto Tangle. The patient’s gateway transaction is securely uploaded onto the channel. Uploaded transactions could be shared among various stakeholders, who can only access in the restricted mode. The procedural flow of transaction initiation, PUF key validation, and its metric evaluation process are illustrated in Figure 10. Only after verifying the PUF reliability, uniqueness, and randomness are the PUF module keys assigned as pseudo identities to devices.
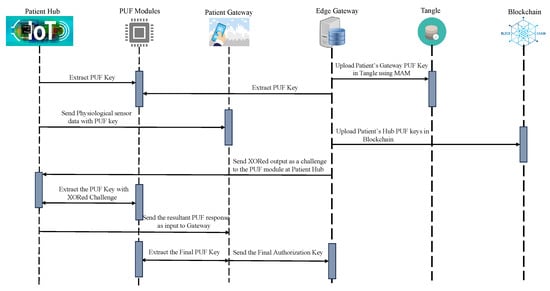 Figure 10. Procedural flow of PUFchain 3.0.
Figure 10. Procedural flow of PUFchain 3.0.
The microcontroller connected to the client broadcasts the PUF keys to the edge server (ES). Algorithms 1 and 2 illustrate the working flow of the device registration phase in PUFchain 3.0.
- 2.
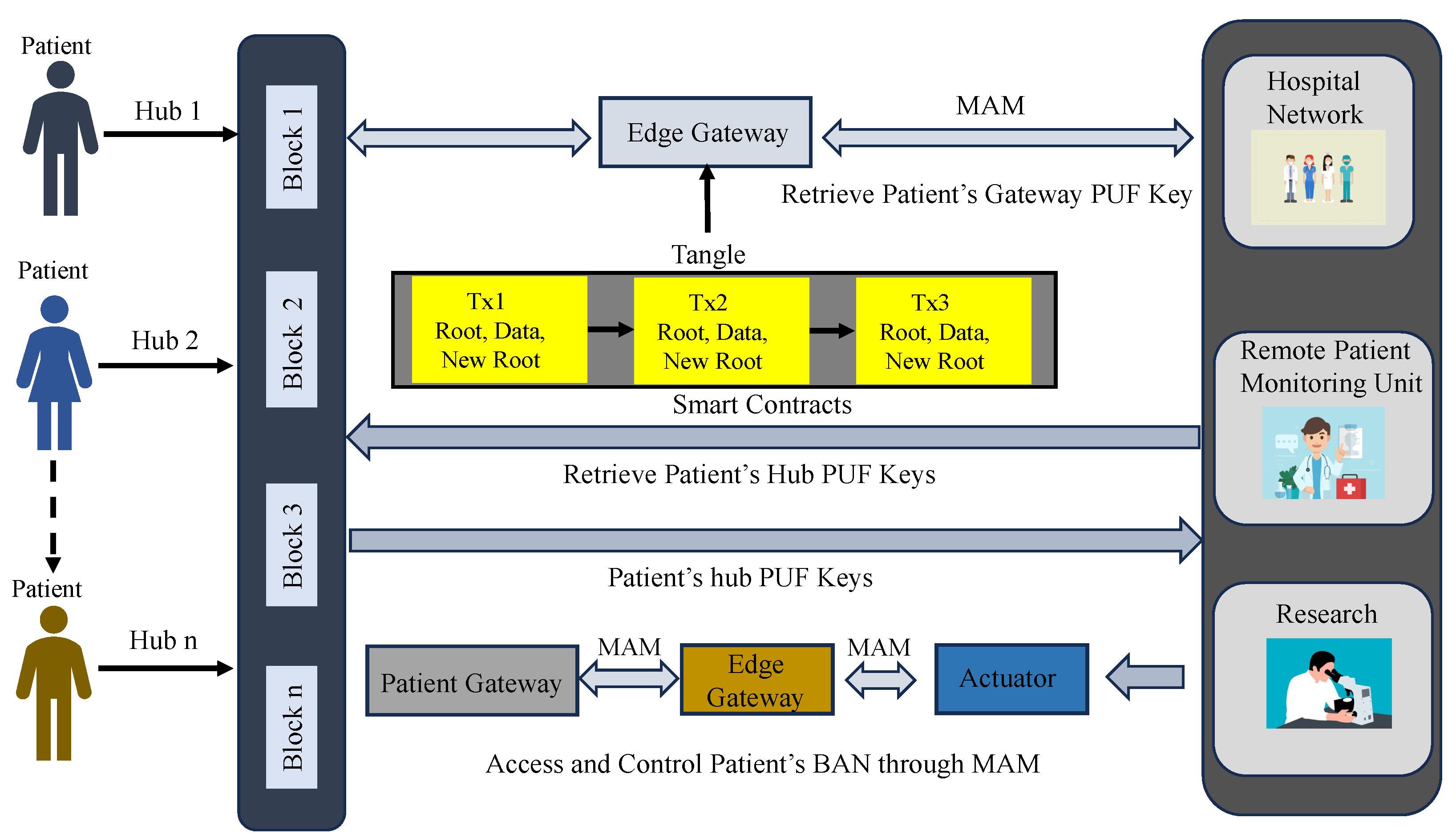
- Patient’s gateway access and control phase In MAM, while validating a transaction, a new root address is generated, which is the subsequent transaction’s hash. This is shared only with the intended recipient to successfully upload a new transaction. Using the side key, the new transaction’s root is obtained by hashing the existing transaction’s root with the side key [10,43,46]. Once the gateway’s key is verified, its details are shared on the MAM channel by creating a transaction. The recipient can be either a server at a hospital, physician, or any other healthcare provider who can access the channel to receive it only after their PUF pseudo-identity verification. Figure 11 and Algorithm 3 outline the validation and verification details. Now each administrative server at any hospital network around the world looking to access the patient’s sensitive physiological data and access the IoMT devices on patients can securely connect to the patient’s gateway hub from Tangle. A global blockchain in the cloud having all the patient’s hub PUF keys can be accessed by the corresponding hospital network or healthcare provider to obtain the individual device’s PUF key in a patient’s BAN as explained in Figure 12. The pseudo-PUF identities and challenges of all the devices are stored inside a blockchain and can be shared globally.
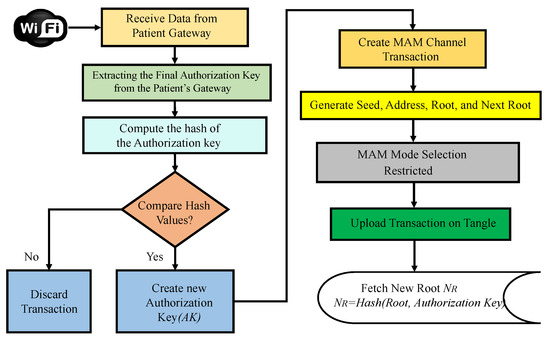 Figure 11. Procedural flow of MAM channel creation and transaction initiation.
Figure 11. Procedural flow of MAM channel creation and transaction initiation.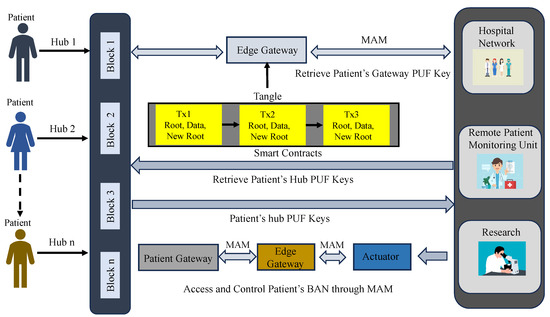 Figure 12. Blockchain-based access control.
Figure 12. Blockchain-based access control.
| Algorithm 1: Enrolling a patient’s Body Area Network devices. |
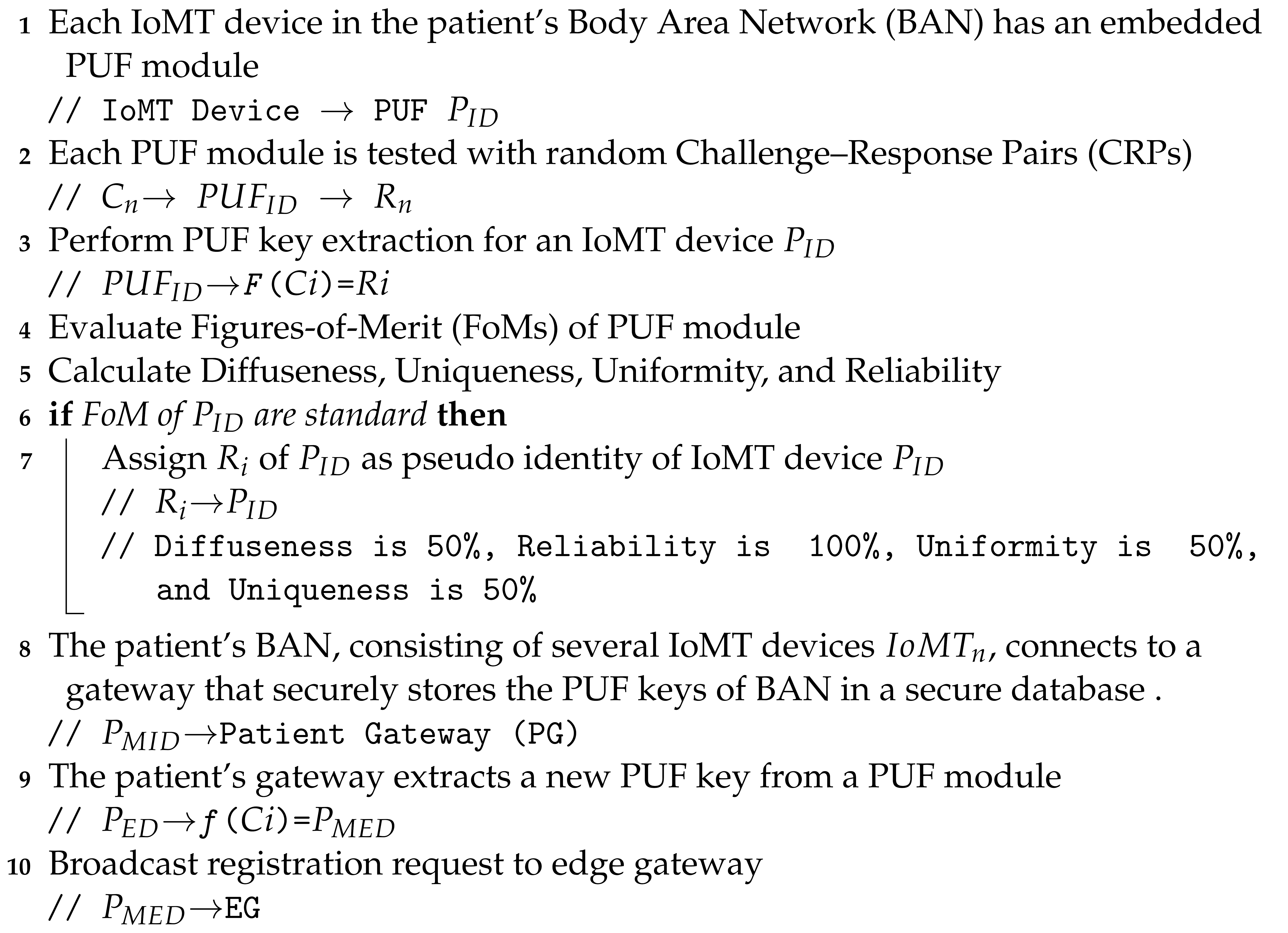 |
| Algorithm 2: Patient’s gateway pseudo identity verification phase. |
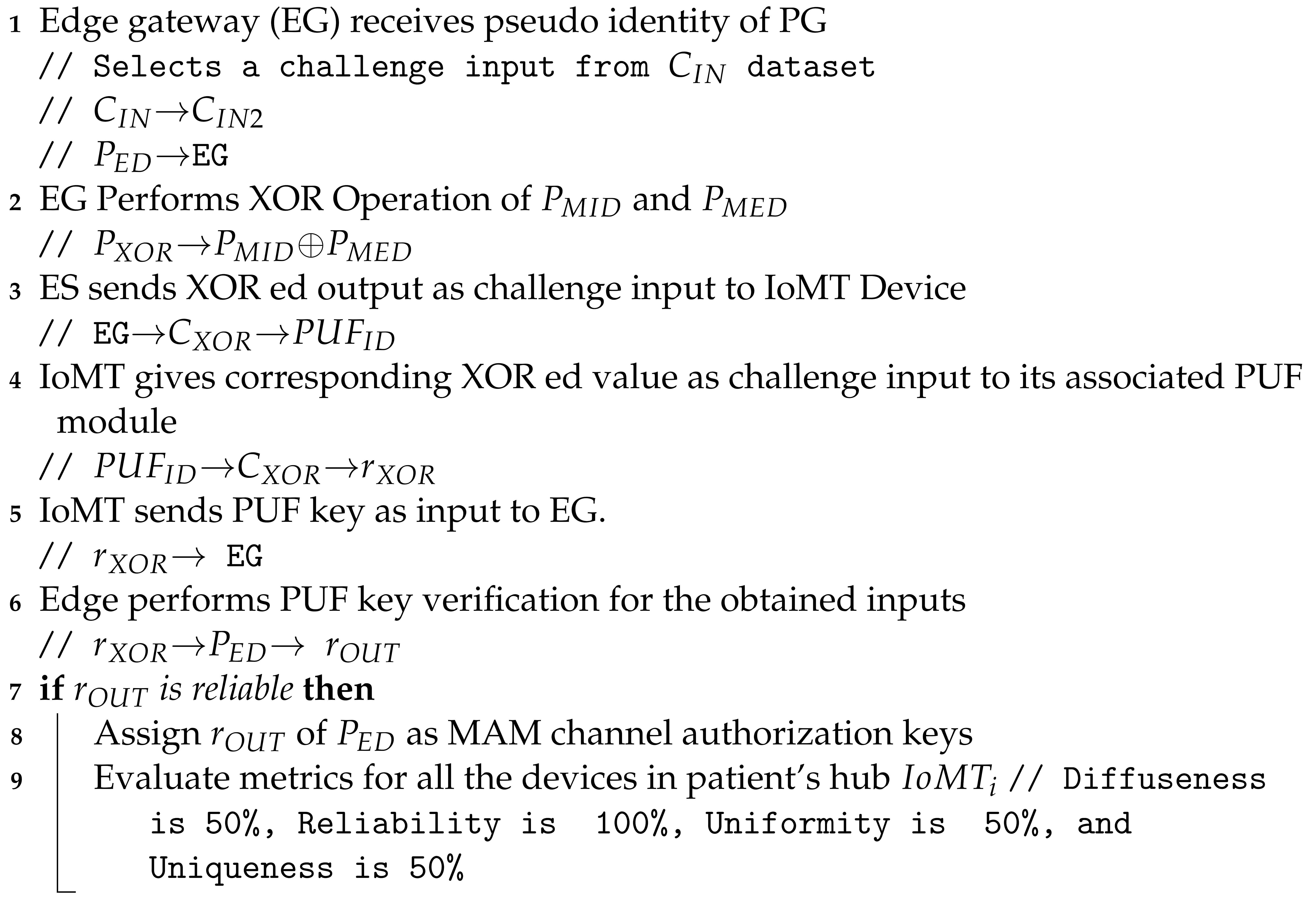 |
| Algorithm 3: MAM channel and blockchain validation phase. |
| 1 EG initiates MAM channel |
| 2 Assign authorization key |
| // MAM Channel→ |
| // MAM Mode →Restricted(2), Public(0) ,private(1) |
| 3 Choose Restricted Mode (2) |
| 4 Upload Pseudo Identity of patient’s hub and patient’s gateway. //→ |
| Streams v0 (Channel) |
| 5 Choose patient’s gateway key as the channel side key |
| // → |
| 6 Fetch Next root |
| // MAM Channel →New Root() |
| 7 Perform hash on side key and root |
| // →H(,) |
| 8 Broadcast new fetched root and new side key |
| // --------EG initiates blockchain transaction------- |
| 9 EG initiates a smart contract with different roles: doctor, patient |
| 10 EG uploads the patient’s hub PUF data set |
| // ---------- |
| // →H(,) |
| // →H(,) |
| // →H(,) |
| // | |
| // | |
| // →H(,) |
| 11 Deploy smart contract |
| 12 Obtain mined and validated block |
| 13 Broadcast validated block globally to various stakeholders |
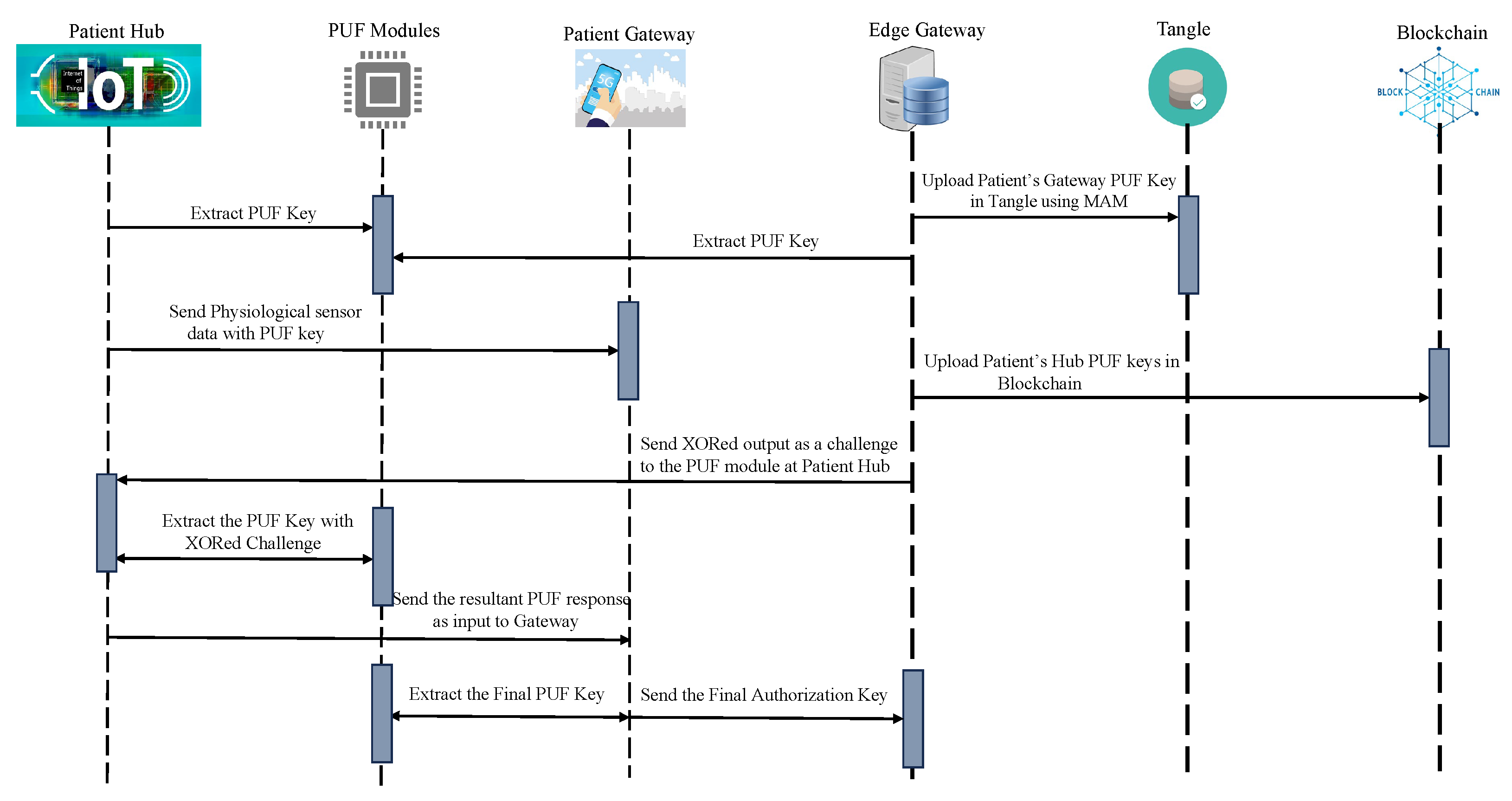
The patient’s gateway key is verified by the edge gateway, which then initiates a new transaction on the IOTA MAM channel. After uploading the transaction, it is shared on the channel, and the intended receiver can access the data in restricted mode. The working and procedural flow of the uploading transaction on MAM channel creation and its validation inside a node in the proposed PUFchain 3.0 is presented in Figure 13.
- Step 1:
- The IoMT device’s integrity is verified by performing PUF key extraction from a set of challenges on the device’s PUFs.
- Step 2:
- The challenge inputs (, ) are tested on the PUF modules at both the gateway’s and device’s PUF modules in the hub.
- Step 3:
- The obtained keys are evaluated by checking the reliability, randomness, Hamming distance, and other metrics.
- Step 4:
- XOR operation is performed on the obtained PUF keys (, ). The XOR output is sent as a challenge input to PUF at IoMT.
- Step 5:
- The obtained key is again tested as input to the PUF module at the gateway.
- Step 6:
- Finally, the obtained key from the gateway is hashed and compared during the verification process by following all the above steps. The obtained final key is hashed. The obtained hash value is compared with the initially obtained hash during registration.
- Step 7:
- Once the device authentication is considered successful by the edge gateway, it then creates a MAM channel to upload the transaction, fetch the address, and broadcast it to the authenticated client to upload its data.
- Step 8:
- The working mode of MAM is chosen as the restricted mode (2). An authorization or side key is defined to access the channel in restricted mode.
- Step 9:
- The authorization key for the MAM channel in the proposed security protocol is the patient’s gateway pseudo identity , which is required to store, share, and access data on IOTA Tangle.
- Step 10:
- Once the new root is fetched, an access link is obtained and broadcasted to all the working nodes in H-CPS to access the transaction data from Tangle.
- Step 11:
- Finally, the root of the transaction and of the MAM channel are hashed to fetch the address () of the new transaction. The new side key is of the patient’s BAN gateway.
- Step 12:
- The subsequent transaction address () is used for data transfer from all the other stakeholders to the intended recipient on the MAM channel, thereby creating a secure communication channel for the patient–doctor interface in H-CPS.
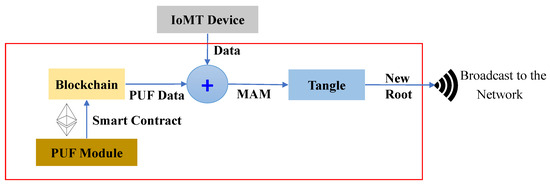
Figure 13.
Working flow of PUFchain 3.0.
Figure 13.
Working flow of PUFchain 3.0.
7.2. Assumptions
The proposed experimental validation is based on the following assumption.
- All the IoMT devices have embedded PUF.
- A secure network communication exists between the IoMT node and the patient’s and edge gateways during the enrollment and verification process.
- All the IoMT devices have a secure interface with the patient’s gateway using BLE, ZigBee, or other technologies.
- The edge gateway has a running blockchain instance locally.
8. Experimental Results
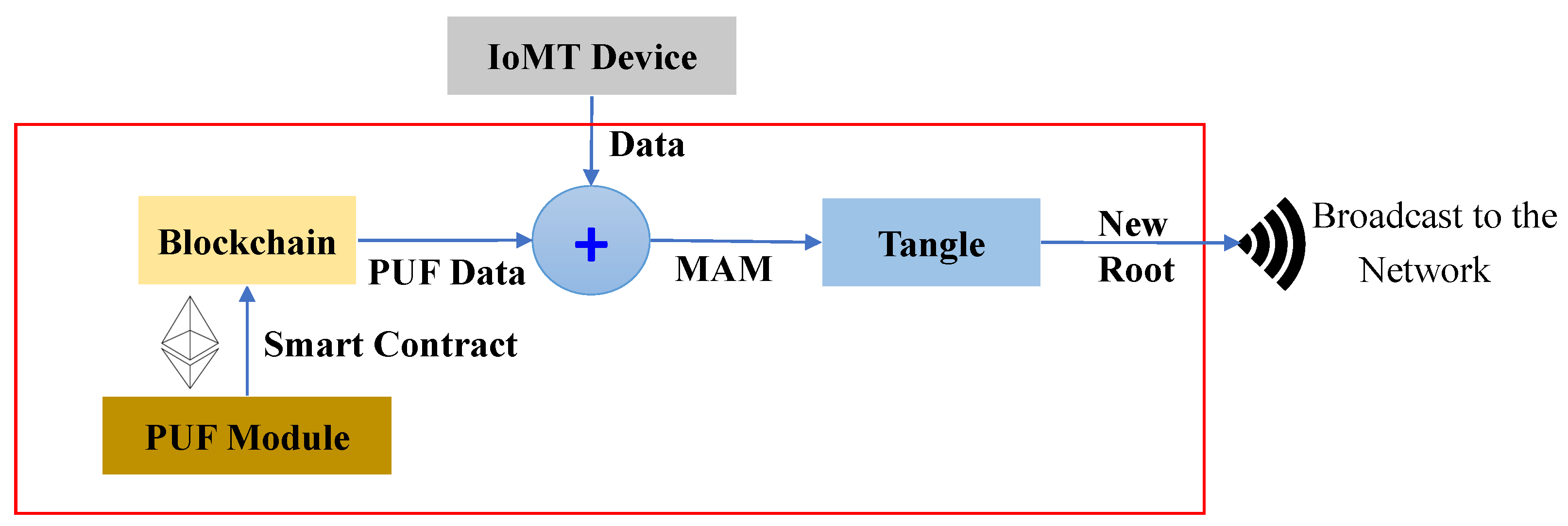
For experimental evaluation, all smart health devices inside the patient’s BAN are interfaced with the patient’s gateway, and all the data processing can be performed at the edge gateway. Two FPGA boards are used for PUF module deployment on the patient and edge gateway side. The patient’s gateway has an Arbiter PUF generated key, and the edge has an XOR PUF Key as unique identities. Arbiter PUF can generate many keys for patients’ BAN smart health devices. The proposed methodology was written in JavaScript to publish and fetch transactions on Tangle. We used the Chrysalis public IOTA node to access and upload transactions on the MAM channel. MAM channel in “restricted mode” was considered for the proposed approach to ensure higher security. The whole methodology was evaluated on the IOTA Main net on Streams v0 Channel [47,48]. The hardware and software specifications of the experimental validation in this work are given in Table 4. The time taken to upload a transaction on Tangle is the total time to generate Tip, validate the transaction using PoW, and generate a MAM channel and corresponding transaction metrics—seed, address, root. Our experimental evaluation has shown that the overall time to perform transaction validation in the proposed work is comparatively faster than that of block addition in PoW, which is approximately 10 min [19]. The transaction evaluation and validation results are presented in Figure 14.

Table 4.
System specifications.
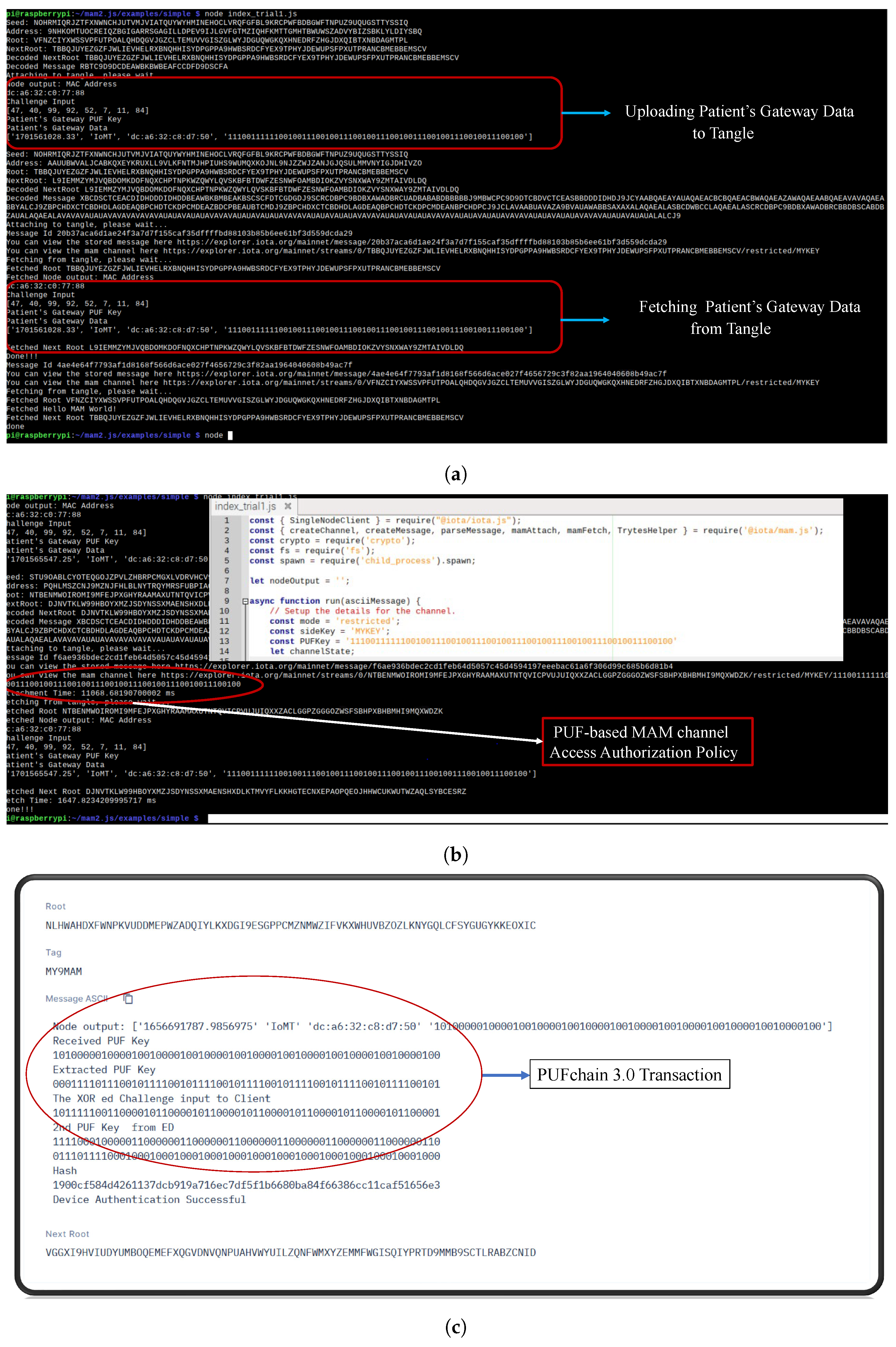
Figure 14.
IOTA Tangle transaction validation. (a) Validating PUF key and creating MAM channel; (b) PUF-Based MAM channel access authorization policy; (c) fetching transaction from IOTA explorer.
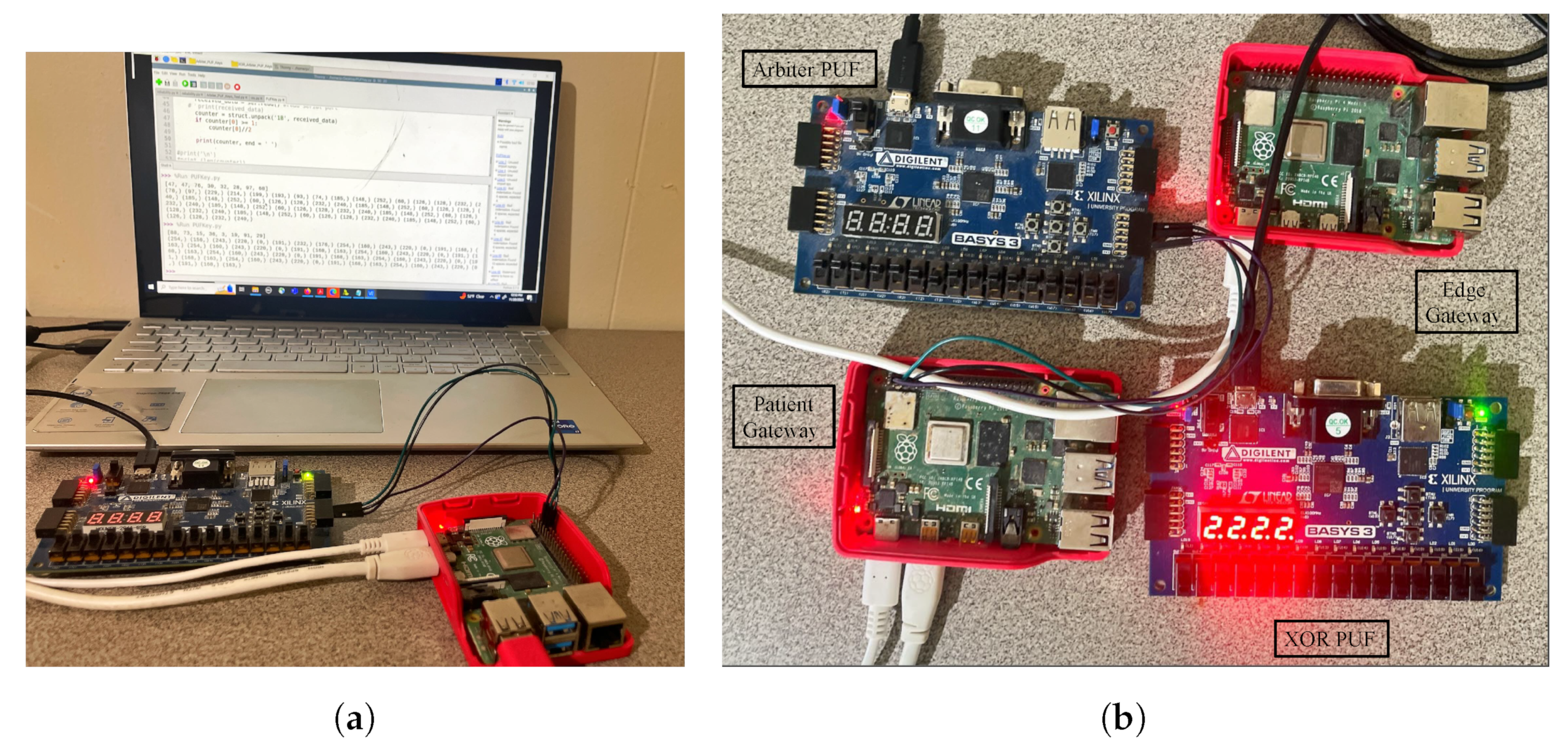
A Ganache local test net blockchain was set up and connected to a MetaMask account for gas cost estimation and analysis. A smart contract was deployed to securely store the generated PUF Challenge–Response Pair (CRP) dataset inside the blockchain. The Ganache blockchain was configured on an Intel i7 2.8 GHz processor with 16 GB RAM (Intel, Santa Clara, CA, USA). Xilinx (AMD, Satnta Clara, CA, UUSA) FPGAs were used for evaluating the Arbiter and XOR PUF modules for PUF key extraction as shown in Figure 15. The FPGA boards used for evaluation are Xilinx Artix-7 Basys 3 (xc7a35tcpg236-1). Xilinx Vivado was used to test the PUF design, and the PUF logic was programmed onto the FPGA board at a baud rate of 9600 bits using a Universal asynchronous receiver and transmitter (UART). The 64-bit instances of Arbiter and XOR PUF elements were generated to create 64-bit PUF keys for each one of the modules. Table 5 presents the Arbiter and XOR PUF evaluation results.
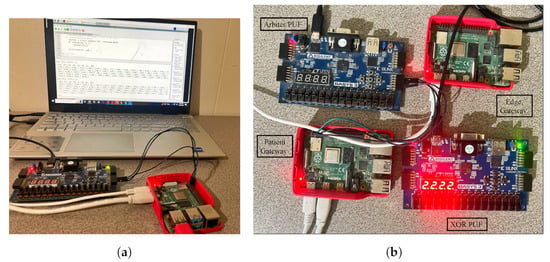
Figure 15.
PUFchain 3.0 Experimental Setup. (a) Extracting PUF keys; (b) prototype.

Table 5.
PUF Evaluation results.
Single board computers were used as edge nodes for distributed data processing from the IoMT devices. Raspberry Pi 4 2.0 GB boards were used as the edge and patient’s gateway in the proposed system. These devices act as local nodes to perform device integrity verification and for creating MAM channel and uploading transactions on Tangle. The edge gateway’s power consumption was evaluated using an energy meter, which showed power consumption in the range of (2.7–3.4) watts, which is approximately the average consumption range of a pi. The PUF keys of each of the devices were initially verified before creating a new MAM channel and uploading the transaction onto Tangle.
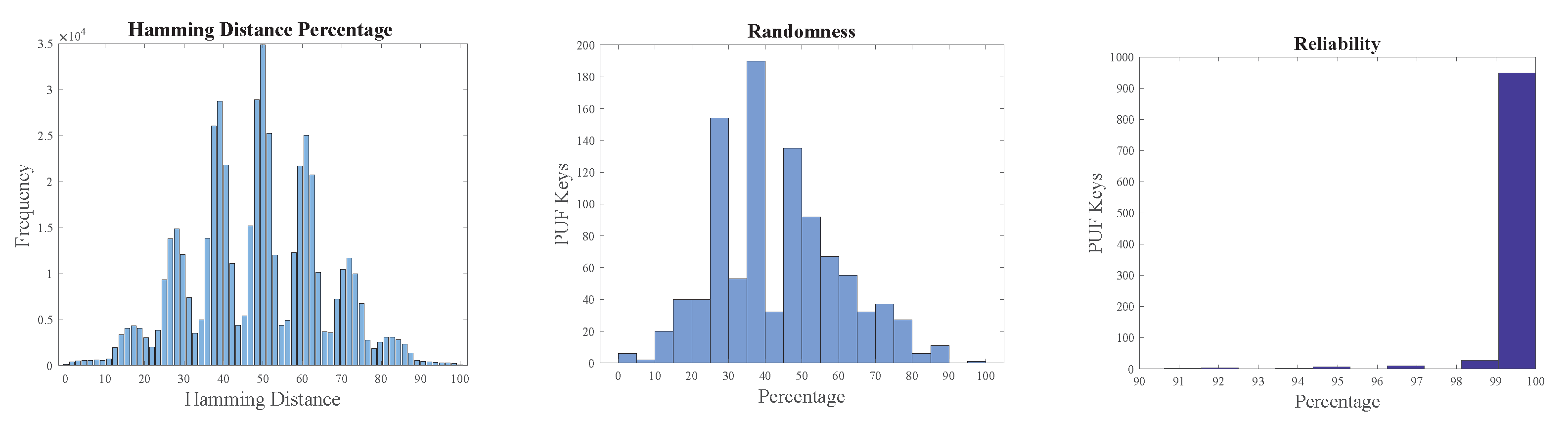
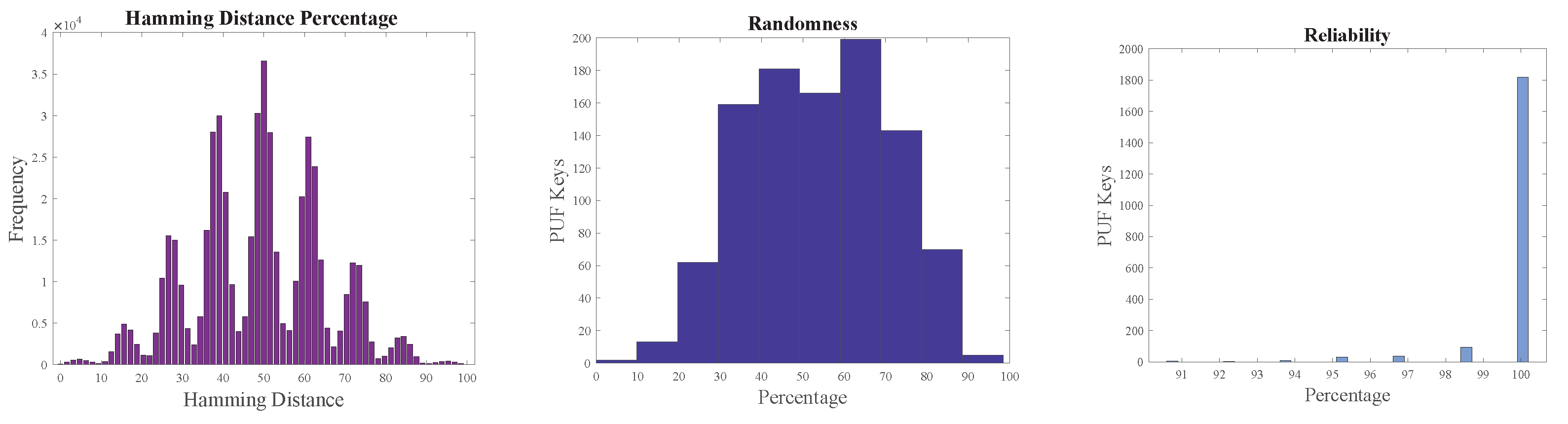
The overall intra-Hamming distance of PUF keys from Arbiter and XOR PUF modules was approximately 50%. The metrics of PUF modules are presented in Figure 16 and Figure 17. Reliability was approximately 100% when the two PUF modules were tested with 1000 PUF keys four times at different instances of time and at varying temperatures.
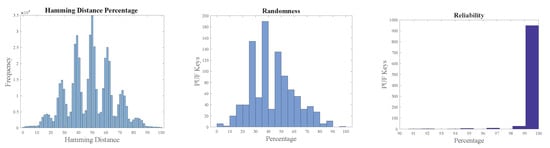
Figure 16.
Arbiter PUF metrics.
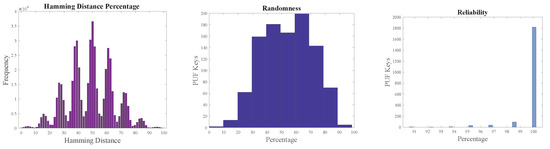
Figure 17.
XOR PUF metrics.
8.1. Why Restricted Mode of MAM for PUFchain 3.0?
MAM as introduced in Section 5, works in public, private, and restricted modes. However, the proposed approach works on MAM in the restricted mode. This is due to the requirement for device and data integrity from smart electronic devices. Restricted mode ensures the utmost level of security and works by generating a transaction address by hashing the hash of the root and an authorization side key. This work aims to leverage this property by using the PUF key of a device as its authorization key to access the channel and upload data to Tangle. In the proposed solution, doctors and medical professionals can access the channel securely and obtain access to the data from Tangle. This can ensure the integrity and authenticity of data, as the data can only be uploaded onto Tangle after successfully validating the PUF keys of respective Medtronic devices.
The overall time to perform device authentication in PUFchain 3.0 is between 2.7 and 3.6 s. Once the device authentication is complete, the average time to upload the transaction onto Tangle Main net is 28 s, while the mean time to fetch the transaction is approximately 1–2 s. The tabulated results of PUFchain 3.0 are given in Table 6. The transaction upload time includes the time taken to perform seed, address, root, and other Tangle transaction metrics. Also, it includes the waiting time for the IOTA public node to attach the transaction to Tangle and the time taken to perform PoW to validate the unconfirmed transactions on Tangle.

Table 6.
Tangle transaction evaluation results: analysis of 10 sample transactions.
8.2. Block Creation and Validation
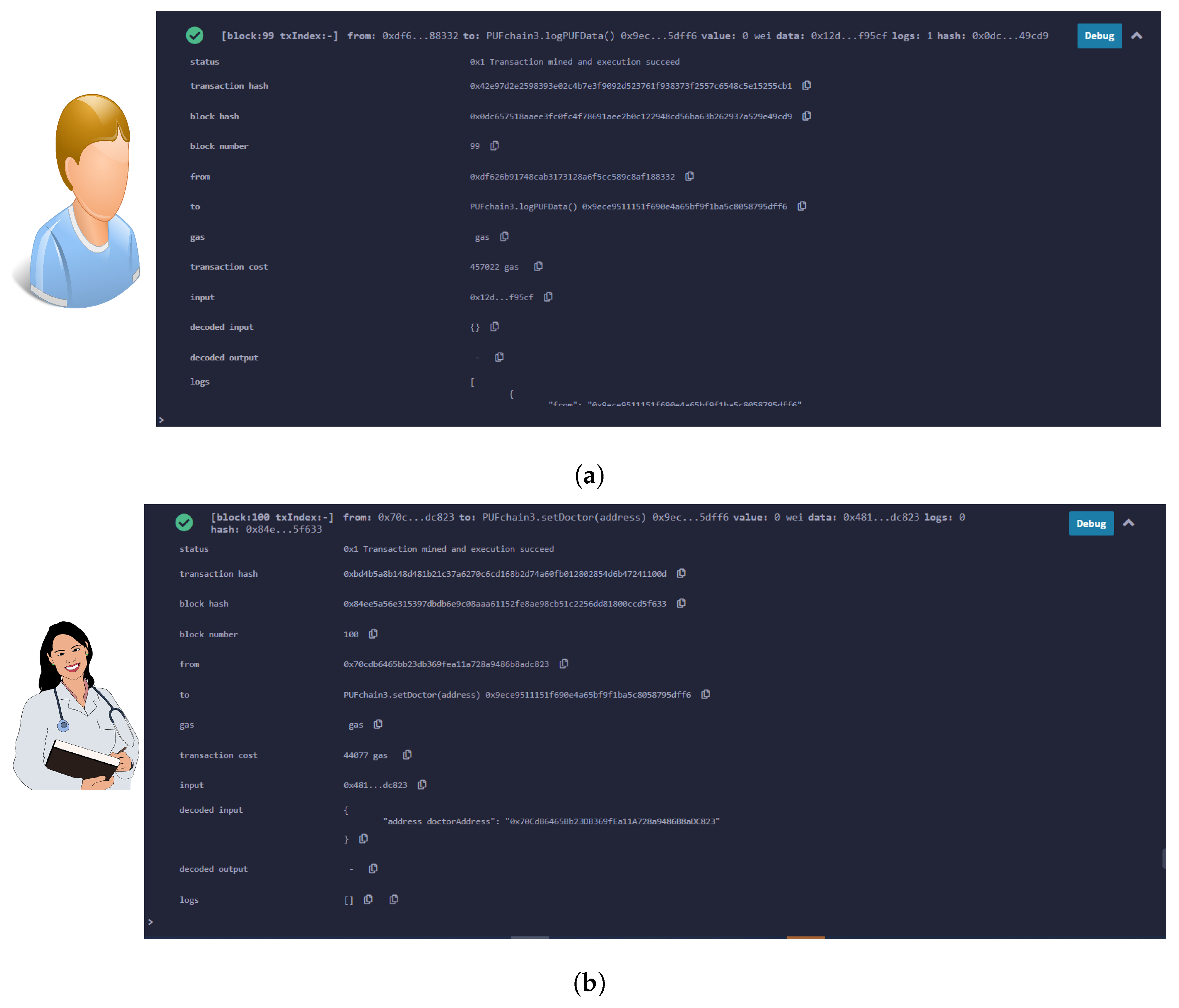
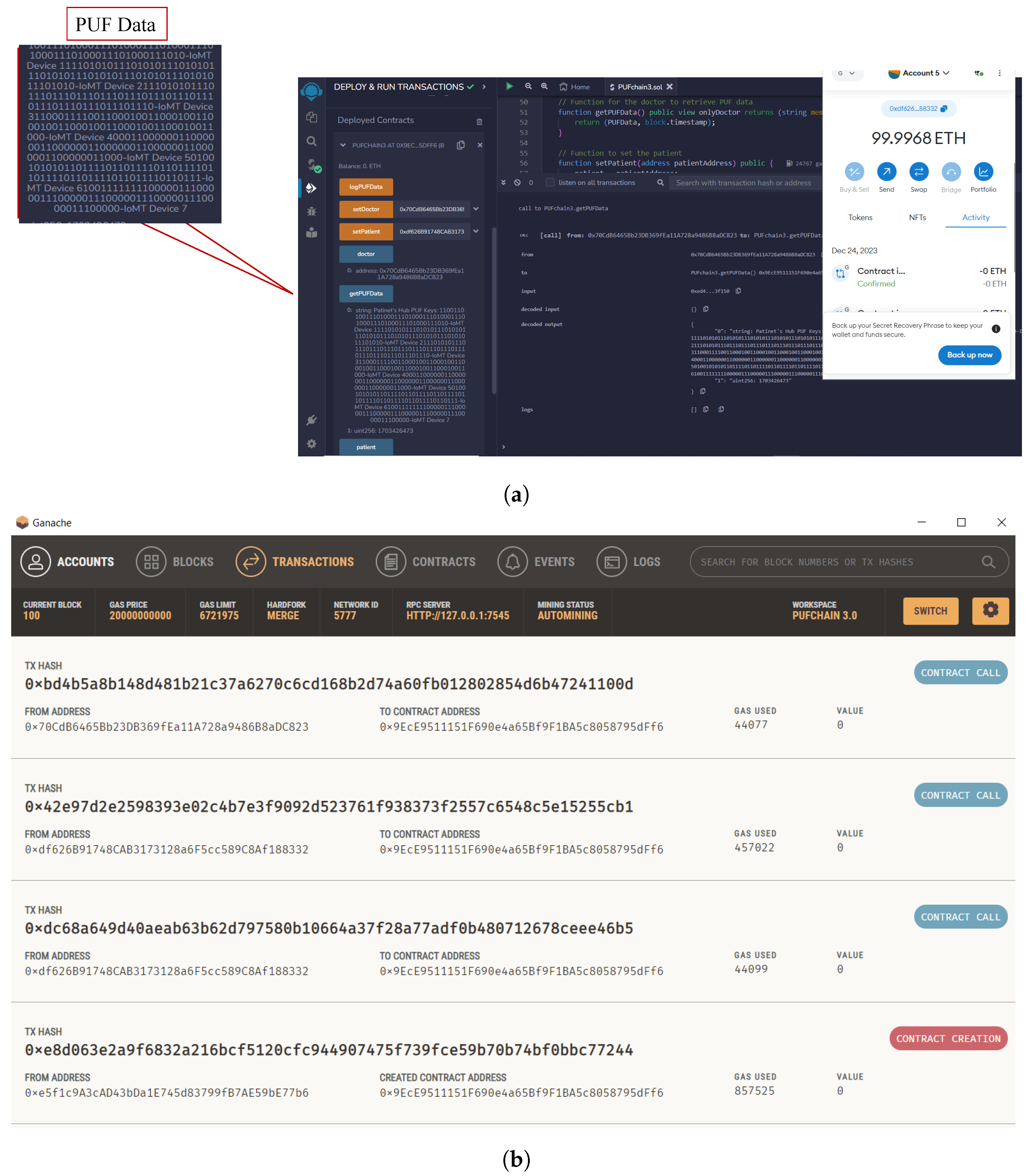
A smart contract was deployed on Remix Ethereum IDE connected to a MetaMask wallet. Ganache blockchain running on a local host was connected to MetaMask, and one of the ten accounts was selected and connected to the MetaMask wallet. A simple smart contract to store the Patient’s PUF data set consisting of PUF keys was executed and deployed onto the Ganache test network [49]. The block creation, hashing, and transaction validation results are presented in Figure 18 and Figure 19. Our prototype system worked on the local Ganache test net using network ID 5777 and smart contract address “0xe5f1c9A3cAD43bDa1E74 5d83799fB7AE59bE77b6”. Two accounts were assigned, one for healthcare professionals with contract address “0x70CdB6465Bb23D B369 fEa11A728a9486B8aDC823”, and one for the patient using the address “0xdf626B91748C AB3173 128a6F5cc 589C8Af18 8332”. The “logPUFData” function is initiated from the patient’s side which securely logs the PUF keys of IoMT devices. The doctor or health professional initiates the “PUFData” function to securely retrieve the PUF keys of IoMT in the patient’s BAN. The smart contract validation results of the proposed framework are given in Table 7.
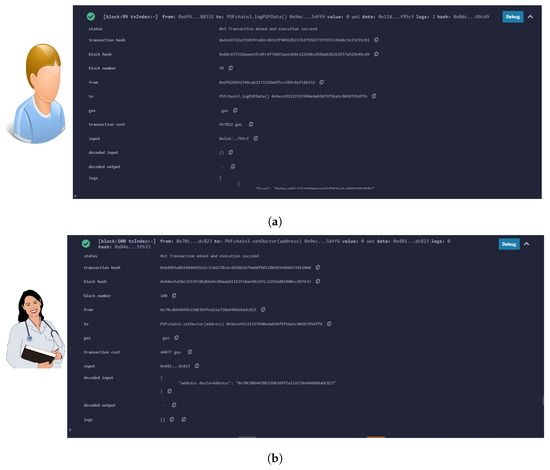
Figure 18.
Smart contract deployment and role assignment. (a) Assigning patient’s role and logging PUF data; (b) assigning doctor’s role and retrieving PUF keys of patient’s BAN.
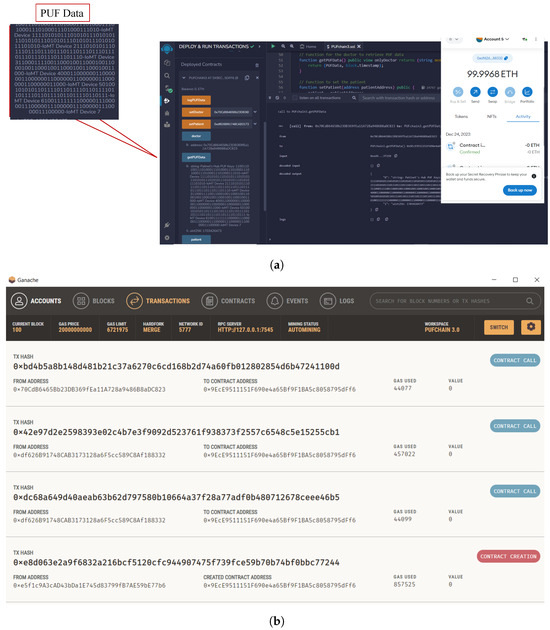
Figure 19.
Formal verification of PUFchain 3.0. (a) Transaction details of PUFchain 3.0 on Remix IDE; (b) Validated PUFchain 3.0 transactions on Ganache.

Table 7.
Smart contract deployment details.
9. Discussion and Conclusions
9.1. Principal Findings
This work explored the potential of hardware-assisted distributed ledger technology-based security solutions in smart healthcare. We proposed a cybersecurity solution for H-CPS by integrating PUF, IOTA Tangle, and blockchain. Tangle, being a distributed lightweight ledger, offers great potential in smart healthcare, as it is a minerless, feeless primitive while offering robust security as blockchain. We experimentally demonstrated a security solution that uses blockchain for securely storing the PUF keys of each of the IoMT devices in a patient’s BAN. The patient’s gateway, having a unique pseudo identity from the PUF, can communicate on MAM for sharing physiological sensor data globally.
This work demonstrated and evaluated two PUF modules: Arbiter and machine learning attack-resistant XOR Arbiter PUF. One thousand PUF keys were extracted from these PUFs for five instances, showing promising results with a reliability of approximately 100%. Our analysis of related works shows that most of these works do not focus on PUF metrics and hardware-assisted access control to the distributed ledger. Our work presents a hardware secure access control policy to DLT with the effective evaluation of PUF metrics to facilitate an attack-resistant security framework. Table 8 illustrates the comparative analysis of this work with related works.

Table 8.
Security analysis of PUFchain 3.0 in comparison with related works.
Our analysis further proves that even though Tangle MAM has been proposed in various works, it has not been integrated with hardware primitives as a comprehensive cybersecurity solution. To the best of our knowledge, this is the first novel integration of PUF, blockchain, and Tangle for simultaneous device and data security in smart healthcare or other areas in IoT-based applications.
Our security analysis shows that eavesdroppers cannot intercept the communication and PUF keys of the patient’s gateway shared on the MAM channel since the restricted mode channel ensures secure access using the patient’s gateway PUF key. Also, consecutive transactions can be uploaded onto the channel only by sharing the obtained new root address and channel side key with the trusted authorized entities in the system. As a result, the proposed approach can withstand eavesdropping attacks. Additionally, our analysis shows that the message attachment times in restricted MAM mode are comparatively faster in this work as compared to [9], even though the public IOTA node’s processing time may vary subject to network traffic. Also, in this work, the PUF keys of IoMT inside BAN are not shared on the MAM channel but are securely stored in the blockchain, which can be accessed by authorized entities through smart contracts, thereby reducing the exposure of smart health devices’ unique PUF-generated identities. Furthermore, the Arbiter and XOR PUF modules have shown better randomness and reliability in this work as compared to the hybrid oscillator arbiter PUF in [19]. Achieving approximately 100% reliability substantiates the potential of PUF-based security for IoMT devices.
9.2. Limitations and Challenges
Using public IOTA nodes for validation, publishing, and fetching data on Tangle could delay and increase transaction validation and publishing times. Using smart contract-based validation can increase energy consumption and require computational resources. Other challenges also exist with the integration of PUF, Tangle, and blockchain, such as latency in transaction validation, network security issues, and blockchain smart contract validation cost or gas fees. Even though our approach works on the Ganache test net blockchain, the actual deployment on the main net could incur gas costs. For the deployment of transactions on Tangle, MAM has been updated to a new protocol called IOTA streams [50] which is still under the development stage. Furthermore, integrating PUF for hardware security is a challenging process, as the reliability of PUF can be impacted due to the aging of the device and its response to environmental factors. Also, various trade-offs involved in the performance of PUF-embedded devices must be considered such as energy consumption, area, and speed while deploying PUF on smart health devices.
9.3. Conclusions and Future Research Directions
Hardware-assisted security solutions using blockchain and distributed ledger have great potential for cybersecurity in smart healthcare. The privacy and integrity of patients’ sensitive medical data are pivotal in the rapidly evolving remote healthcare monitoring systems facilitated through IoMT devices. Integrating a decentralized hardware–software SbD approach which emphasizes integrating security based on the design of an electronic system in H-CPS is the motivation for this work. The proposed work successfully integrates PUF, blockchain, and IOTA Tangle as a scalable decentralized security primitive that provides sustainable and simultaneous security in H-CPS. The proposed architecture aims to leverage the scope of blockchain technology to store the patient’s BAN PUF keys to avoid the possibility of exposure and adversarial access to these keys. Using Tangle in this work securely facilitates identity-driven access control and data sharing among various stakeholders in H-CPS for processing patients’ critical health data in real time. Furthermore, PUF enhances and focuses on security at the end device in the BAN hub. The possible integration of these three could further facilitate a secure interface between doctor and patient in advanced remote healthcare monitoring systems like telemedicine and e-health.
This work could be extended for sustainable security in autonomous vehicles by embedding PUF inside electronic control units, and it has a blockchain-supported functionality for data security as well. The proposed PUFchain 3.0 could be extended further to other areas of IoT-based applications, particularly in the areas of supply chain management and product tracking in electronics. This includes attaching a PUF-generated cryptographic identity to each product in the supply chain and tracking its movement securely using blockchain. The integration of these primitives for IC supply chain management and Industry 4.0 can also be a direction for future research.
Author Contributions
Conceptualization, S.P.M.; Investigation, V.K.V.V.B.; Writing—original draft, V.K.V.V.B.; Writing—review and editing, S.P.M. and E.K.; Supervision, E.K.; Funding acquisition, V.I. and B.R. All authors have read and agreed to the published version of the manuscript.
Funding
This material is based upon work supported by the National Science Foundation under Grant number HBCU-EiR-2101181. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the authors and do not necessarily reflect the views of the National Science Foundation.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All the data generated or analyzed during this study are included in the published article. Any data related to this study can be provided with reasonable request.
Acknowledgments
A preliminary version of this work is presented in the following conference paper [20].
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Sundaravadivel, P.; Kougianos, E.; Mohanty, S.P.; Ganapathiraju, M.K. Everything You Wanted to Know about Smart Health Care: Evaluating the Different Technologies and Components of the Internet of Things for Better Health. IEEE Consum. Electron. Mag. 2018, 7, 18–28. [Google Scholar] [CrossRef]
- Sun, J.; Khan, F.; Li, J.; Alshehri, M.D.; Alturki, R.; Wedyan, M. Mutual Authentication Scheme for the Device-to-Server Communication in the Internet of Medical Things. IEEE Internet Things J. 2021, 8, 15663–15671. [Google Scholar] [CrossRef]
- Marshal, R.; Gobinath, K.; Rao, V.V. Proactive Measures to Mitigate Cyber Security Challenges in IoT based Smart Healthcare Networks. In Proceedings of the IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021. [Google Scholar] [CrossRef]
- Jia, X.; Luo, M.; Wang, H.; Shen, J.; He, D. A Blockchain-Assisted Privacy-Aware Authentication Scheme for Internet of Medical Things. IEEE Internet Things J. 2022, 9, 21838–21850. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Zolanvari, M.; Unal, D.; Al-Ali, A.; Jain, R. Recent Advances in the Internet-of-Medical-Things (IoMT) Systems Security. IEEE Internet Things J. 2021, 8, 8707–8718. [Google Scholar] [CrossRef]
- Mohd Aman, A.H.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. IoMT amid COVID-19 pandemic: Application, architecture, technology, and security. J. Netw. Comput. Appl. 2021, 174, 102886. [Google Scholar] [CrossRef] [PubMed]
- Jayaraman, I.; Shankar, A.; Ghalib, D.M.; Jayaraman, G.; Hua, Q.; Wen, Z.; Qi, X. Block Chain Based Internet of Medical Things for Uninterrupted, Ubiquitous, User-Friendly, Unflappable, Unblemished, Unlimited Health Care Services (BC IoMT U 6 HCS). IEEE Access 2020, 8, 216856–216872. [Google Scholar] [CrossRef]
- Wazid, M.; Singh, J.; Das, A.K.; Shetty, S.; Khan, M.K.; Rodrigues, J.J.P.C. ASCP-IoMT: AI-Enabled Lightweight Secure Communication Protocol for Internet of Medical Things. IEEE Access 2022, 10, 57990–58004. [Google Scholar] [CrossRef]
- Zheng, X.; Sun, S.; Mukkamala, R.R.; Vatrapu, R.; Meré, J.B.O. Accelerating Health Data Sharing: A Solution Based on the Internet of Things and Distributed Ledger Technologies. J. Med. Internet Res. 2019, 21, e13583. [Google Scholar] [CrossRef]
- Abdullah, S.; Arshad, J.; Khan, M.M.; Alazab, M.; Salah, K. PRISED Tangle: A Privacy-Aware Framework for Smart Healthcare Data Sharing using IOTA Tangle. Complex Intell. Syst. 2022, 9, 3023–3041. [Google Scholar] [CrossRef]
- Bathalapalli, V.K.V.V.; Mohanty, S.P.; Kougianos, E.; Baniya, B.K.; Rout, B. PUFchain 2.0: Hardware-Assisted Robust Blockchain for Sustainable Simultaneous Device and Data Security in Smart Healthcare. SN Comput. Sci. 2022, 3, 344. [Google Scholar] [CrossRef]
- Shi, S.; Luo, M.; Wen, Y.; Wang, L.; He, D. A Blockchain-Based User Authentication Scheme with Access Control for Telehealth Systems. Secur. Commun. Netw. 2022, 2022, 6735003. [Google Scholar] [CrossRef]
- Amintoosi, H.; Nikooghadam, M.; Shojafar, M.; Kumari, S.; Alazab, M. Slight: A lightweight authentication scheme for smart healthcare services. Comput. Electr. Eng. 2022, 99, 107803. [Google Scholar] [CrossRef]
- Satra, S.; Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Octopus: A Novel Approach for Health Data Masking and Retrieving Using Physical Unclonable Functions and Machine Learning. Sensors 2023, 23, 4082. [Google Scholar] [CrossRef]
- Dey, K.; Kule, M.; Rahaman, H. PUF Based Hardware Security: A Review. In Proceedings of the International Symposium on Devices, Circuits and Systems (ISDCS), Higashihiroshima, Japan, 3–5 March 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Razdan, S.; Sharma, S. Internet of Medical Things (IoMT): Overview, Emerging Technologies, and Case Studies. IETE Tech. Rev. 2021, 39, 775–788. [Google Scholar] [CrossRef]
- Hori, Y.; Yoshida, T.; Katashita, T.; Satoh, A. Quantitative and Statistical Performance Evaluation of Arbiter Physical Unclonable Functions on FPGAs. In Proceedings of the International Conference on Reconfigurable Computing and FPGAs, RECONFIG ’10. Cancun, Mexico, 13–15 December 2010; pp. 298–303. [Google Scholar] [CrossRef]
- Lee, Y.S.; Lee, H.J.; Alasaarela, E. Mutual authentication in wireless body sensor networks (WBSN) based on Physical Unclonable Function (PUF). In Proceedings of the 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 1314–1318. [Google Scholar] [CrossRef]
- Mohanty, S.P.; Yanambaka, V.P.; Kougianos, E.; Puthal, D. PUFchain: Hardware-Assisted Blockchain for Sustainable Simultaneous Device and Data Security in the Internet of Everything (IoE). arXiv 2019, arXiv:1909.06496. [Google Scholar] [CrossRef]
- Bathalapalli, V.K.V.V.; Mohanty, S.P.; Kougianos, E.; Baniya, B.K.; Rout, B. PUFchain 3.0: Hardware-Assisted Distributed Ledger for Robust Authentication in the Internet of Medical Things. In Internet of Things. IoT through a Multi-Disciplinary Perspective; Springer: Berlin/Heidelberg, Germany, 2022; pp. 23–40. [Google Scholar] [CrossRef]
- Hellani, H.; Sliman, L.; Samhat, A.E.; Exposito, E. Tangle the Blockchain:Towards Connecting Blockchain and DAG. In Proceedings of the 30th IEEE International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Bayonne, France, 27–29 October 2021; pp. 63–68. [Google Scholar] [CrossRef]
- Chaudhary, C.K.; Chatterjee, U.; Mukhopadhayay, D. Auto-PUFChain: An Automated Interaction Tool for PUFs and Blockchain in Electronic Supply Chain. In Proceedings of the Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Shanghai, China, 16–18 December 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Al-Joboury, I.M.; Al-Hemiary, E.H. A Permissioned Consensus Algorithm Based DAGs-to-Blockchain in Hierarchical Architecture for Decentralized Internet of Things. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Akbulut, S.; Semantha, F.H.; Azam, S.; Pilares, I.C.A.; Jonkman, M.; Yeo, K.C.; Shanmugam, B. Designing a Private and Secure Personal Health Records Access Management System: A Solution Based on IOTA Distributed Ledger Technology. Sensors 2023, 23, 5174. [Google Scholar] [CrossRef] [PubMed]
- Wazid, M.; Gope, P. BACKM-EHA: A Novel Blockchain-enabled Security Solution for IoMT-based E-healthcare Applications. ACM Trans. Internet Technol. 2023, 23, 1–28. [Google Scholar] [CrossRef]
- Tomar, A.; Gupta, N.; Rani, D.; Tripathi, S. Blockchain-assisted authenticated key agreement scheme for IoT-based healthcare system. Internet Things 2023, 23, 100849. [Google Scholar] [CrossRef]
- Vinko, D.; Miličević, K.; Lukić, I.; Köhler, M. Microcontroller-Based PUF for Identity Authentication and Tamper Resistance of Blockchain-Compliant IoT Devices. Sensors 2023, 23, 6769. [Google Scholar] [CrossRef]
- Fotopoulos, F.; Malamas, V.; Dasaklis, T.K.; Kotzanikolaou, P.; Douligeris, C. A Blockchain-enabled Architecture for IoMT Device Authentication. In Proceedings of the IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 23–25 October 2020. [Google Scholar] [CrossRef]
- Rahmadika, S.; Astillo, P.V.; Choudhary, G.; Duguma, D.G.; Sharma, V.; You, I. Blockchain-Based Privacy Preservation Scheme for Misbehavior Detection in Lightweight IoMT Devices. IEEE J. Biomed. Health Inform. 2023, 27, 710–721. [Google Scholar] [CrossRef]
- Wang, W.; Chen, Q.; Yin, Z.; Srivastava, G.; Gadekallu, T.R.; Alsolami, F.; Su, C. Blockchain and PUF-Based Lightweight Authentication Protocol for Wireless Medical Sensor Networks. IEEE Internet Things J. 2022, 9, 8883–8891. [Google Scholar] [CrossRef]
- Pescador, F.; Mohanty, S.P. Guest Editorial Security-by-Design for Electronic Systems. IEEE Trans. Consum. Electron. 2022, 68, 2–4. [Google Scholar] [CrossRef]
- Bathalapalli, V.K.V.V.; Mohanty, S.P.; Kougianos, E.; Iyer, V.; Rout, B. iTPM: Exploring PUF-based Keyless TPM for Security-by-Design of Smart Electronics. In Proceedings of the 2023 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Foz do Iguacu, Brazil, 20–23 June 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Anandakumar, N.N.; Hashmi, M.S.; Chaudhary, M.A. Implementation of Efficient XOR Arbiter PUF on FPGA with Enhanced Uniqueness and Security. IEEE Access 2022, 10, 129832–129842. [Google Scholar] [CrossRef]
- Liu, J.; Zhao, Y.; Zhu, Y.; Chan, C.H.; Martins, R.P. A Weak PUF-Assisted Strong PUF With Inherent Immunity to Modeling Attacks and Ultra-Low BER. IEEE Trans. Circuits Syst. Regul. Pap. 2022, 69, 4898–4907. [Google Scholar] [CrossRef]
- Alshaikhli, M.; Elfouly, T.; Elharrouss, O.; Mohamed, A.; Ottakath, N. Evolution of Internet of Things From Blockchain to IOTA: A Survey. IEEE Access 2022, 10, 844–866. [Google Scholar] [CrossRef]
- Rydningen, E.S.; Åsberg, E.; Jaccheri, L.; Li, J. Advantages and opportunities of the IOTA tangle for health data management. In Proceedings of the 5th International Workshop on Emerging Trends in Software Engineering for Blockchain, Pittsburgh, PA, USA, 21–29 May 2022. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, Y.; Sun, B.; Liu, J. Addressing the Transaction Validation Issue in IOTA Tangle: A Tip Selection Algorithm Based on Time Division. Mathematics 2023, 11, 4116. [Google Scholar] [CrossRef]
- Shabandri, B.; Maheshwari, P. Enhancing IoT Security and Privacy Using Distributed Ledgers with IOTA and the Tangle. In Proceedings of the 6th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 7–8 March 2019; pp. 1069–1075. [Google Scholar] [CrossRef]
- Pinjala, S.K.; Sivalingam, K.M. DCACI: A Decentralized Lightweight Capability Based Access Control Framework using IOTA for Internet of Things. In Proceedings of the IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019. [Google Scholar] [CrossRef]
- Guo, F.; Xiao, X.; Hecker, A.; Dustdar, S. Characterizing IOTA Tangle with Empirical Data. In Proceedings of the IEEE Global Communications Conference GLOBECOM, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Rawat, A.; Daza, V.; Signorini, M. Offline Scaling of IoT Devices in IOTA Blockchain. Sensors 2022, 22, 1411. [Google Scholar] [CrossRef]
- Gangwani, P.; Perez-Pons, A.; Bhardwaj, T.; Upadhyay, H.; Joshi, S.; Lagos, L. Securing Environmental IoT Data Using Masked Authentication Messaging Protocol in a DAG-Based Blockchain: IOTA Tangle. Future Internet 2021, 13, 312. [Google Scholar] [CrossRef]
- Carelli, A.; Palmieri, A.; Vilei, A.; Castanier, F.; Vesco, A. Enabling Secure Data Exchange through the IOTA Tangle for IoT Constrained Devices. Sensors 2022, 22, 1384. [Google Scholar] [CrossRef]
- Lamtzidis, O.; Gialelis, J. An IOTA Based Distributed Sensor Node System. In Proceedings of the IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Mallick, S.R.; Goswami, V.; Lenka, R.K.; Sahoo, T.R.; Kumar, V.; Barik, R.K. Blockchain-based IoMT for an intelligent healthcare system using a drop-offs queue. In Proceedings of the First International Conference on Microwave, Antenna and Communication (MAC), Prayagraj, India, 24–26 March 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Bhandary, M.; Parmar, M.; Ambawade, D. A Blockchain Solution based on Directed Acyclic Graph for IoT Data Security using IoTA Tangle. In Proceedings of the 5th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 10–12 June 2020; pp. 827–832. [Google Scholar] [CrossRef]
- IOTA Foundation. iotaledger/mam.js. 2021. Available online: https://github.com/iotaledger/mam.js (accessed on 7 July 2022).
- IOTA Foundation. iotaledger/mam.client.js. 2021. Available online: https://github.com/iotaledger/mam.client.js/ (accessed on 7 July 2022).
- Truffle Suite. Ganache UI. 2023. Available online: https://github.com/trufflesuite/ganache-ui (accessed on 11 November 2023).
- IOTA Foundation. iotaledger/streams. 2023. Available online: https://github.com/iotaledger/streams (accessed on 11 November 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).