Abstract
The proliferation of the Internet of Things (IoT) has worsened the challenge of maintaining data and user privacy. IoT end devices, often deployed in unsupervised environments and connected to open networks, are susceptible to physical tampering and various other security attacks. Thus, robust, efficient authentication and key agreement (AKA) protocols are essential to protect data privacy during exchanges between end devices and servers. The previous work in “Provably Secure ECC-Based Anonymous Authentication and Key Agreement for IoT” proposed a novel AKA scheme for secure IoT environments. They claimed their protocol offers comprehensive security features, guarding against numerous potential flaws while achieving session key security. However, this paper demonstrates through logical and mathematical analyses that the previous work is vulnerable to various attacks. We conducted a security analysis using the extended Canetti and Krawczyk (eCK) model, which is widely employed in security evaluations. This model considers scenarios where an attacker has complete control over the network, including the ability to intercept, modify, and delete messages, while also accounting for the potential exposure of ephemeral private keys. Furthermore, we show that their scheme fails to meet critical security requirements and relies on flawed security assumptions. We prove our findings using the automated validation of internet security protocols and applications, a widely recognized formal verification tool. To strengthen attack resilience, we propose several recommendations for the advancement of more robust and efficient AKA protocols specifically designed for IoT environments.
1. Introduction
The Internet of Things (IoT) is rapidly growing due to advancements in chipset production and embedding technologies. End devices, including sensors and actuators, are now ubiquitous in various fields, such as intelligent transportation, smart grids, healthcare, and intelligent manufacturing [1]. According to recent estimates, the number of IoT connections will reach 39.6 billion by 2033 [2]. In IoT applications, data security and user privacy are paramount concerns, particularly regarding sensitive information, such as consumption habits, locations, and communication activities [3,4]. “Authentication and key agreement” (AKA) schemes are widely adopted for secure mutual authentication and data privacy [5]. However, resource-limited end devices are often deployed in unattended environments and connected to open networks, which pose significant challenges in maintaining secure mutual AKA with servers [6,7].
In 2024, Hu et al. [8] presented a provably robust AKA scheme for IoT environments, claiming that it offers anonymity and high security. However, our analysis reveals that their scheme inadequately addresses physical capture attacks and fails to resist various security threats, including impersonation attacks. Its vulnerability arises from the risk of secret parameters kept in memory to be exposed to attackers through physical capture attacks.
Motivations and Contributions
This work primarily aims to identify significant security vulnerabilities of the previous work scheme. We demonstrate that an attacker can easily compromise the session keys (SKs) between entities through impersonation attacks in this scheme. Consequently, their scheme fails to ensure SK security, as verified via a formal security analysis using the well-established “real-or-random” (ROR) model [9]. We also perform a formal simulation analysis using the “automated validation of internet security protocols and applications” (AVISPA Version 1.6) tool. These formal analysis methods are useful for analyzing protocol security [10,11,12,13]. Finally, we show that the scheme is unsuitable for real IoT environments and present recommendations to address these vulnerabilities and improve its security. IoT devices may be either mobile or fixed in one location, so they are relatively easy to capture. Additionally, embedded devices have resource-limited characteristics, which hinders the implementation of computationally intensive cryptographic methods. Therefore, attackers can easily gain control over compromised IoT devices. Robust security technologies must be in place to ensure the safety of IoT devices, even if they are captured.
The rest of this paper is structured as follows: Section 2 and Section 3 present a review of related works and the required preliminaries, respectively. Section 4 and Section 5 provide a review and cryptanalysis, respectively, of the previous work. Section 6 proposes solutions to improve security and defenses against potential attacks. Section 7 provides our conclusions and outlines directions for future research.
2. Related Works
Numerous IoT AKA schemes based on elliptic curve cryptosystems (ECCs) have been developed [14,15,16,17,18,19,20,21,22,23]. In 2020, Fang et al. [14] proposed an IoT AKA scheme that uses a trust model to deploy heterogeneous IoT smart devices. However, this scheme incurs higher operation and network costs and is vulnerable to ephemeral secret leakage (ESL) attacks [15]. ESL attacks occur when ephemeral secrets are compromised, allowing an adversary to obtain private keys and determine SKs from intercepted messages. Also in 2020, Abbasinezhad-Mood et al. [16] proposed an AKA protocol for secure group applications, addressing some of the above-mentioned issues, such as ESL attacks and private key leakage. Despite these improvements, their scheme allows a trusted authority (TA) to impersonate a smart meter and establish SKs with service provider (SP) [17]. Additionally, this protocol requires significant computational and communication resources due to its need for bilinear pairing computations. In 2021, Srinivas et al. [18] developed an anonymous AKA scheme using Schnorr’s signature. However, Baruah et al. [17] later revealed that this protocol is vulnerable to “man-in-the-middle” (MITM) and “impersonation attacks”. Further crypt-analysis showed that it also suffers from “key escrow” (KE) issues and ESL attacks. Yang et al. [19] showed that Shen et al.’s scheme [20] is insecure against MITM and “key compromise impersonation” (KCI) attacks and fails to ensure “perfect forward secrecy” (PFS), subsequently proposing an enhanced cloud-based solution. However, this enhanced scheme also faces KE problems and does not provide user anonymity. Chaudhry et al. [21] proposed an AKA scheme for secure group applications using ECC and symmetric encryption; however, this scheme also suffers from KE issues and is vulnerable to MITM attacks. Hajian et al. [22] assessed the shortcomings of four existing AKA schemes and proposed an improved device-to-device AKA scheme for IoT. However, this improved scheme is still vulnerable to MITM and KCI attacks and fails to provide PFS. In 2023, Chen et al. [23] developed an AKA scheme tailored for industrial control systems, but it incurs high operation and network costs, is vulnerable to ESL attacks, and cannot offer PFS. Rajkumar et al. [24] proposed an ECC-based certificateless signature aggregation scheme for vehicular ad hoc networks. Hu et al. [8] recently proposed an ECC-based AKA scheme for IoT environments, but it does not resist “physical capture attacks”.
To resolve these challenges, researchers have been developing physically secure AKA schemes for various environments. In 2023, Ma et al. [25] proposed a “physical-unclonable-function” (PUF)-based AKA scheme for smart grids that enables user anonymity. In 2024, Yu and Park [26] introduced a robust, anonymous AKA scheme using PUFs for vehicle-to-grid (V2G) networks, whereas Awais et al. [27] proposed a physically robust AKA scheme for vehicular ad hoc networks. Building on these advancements, we present suggestions that incorporate efficient, physically robust ways to enhance security in IoT environments. A comparative summary of previous works and the abbreviations used in this paper are defined in Table 1 and Table 2, respectively.

Table 1.
A comparative summary of existing AKA scheme for IoT.

Table 2.
Abbreviations.
3. Preliminaries
3.1. Threat Model
In the previous work, the security analysis is conducted using the “extended Canetti and Krawczyk (eCK) model” [28]. This “threat model” allows an adversary to remove, modify, inject, and access all messages exchanged among the communicating entities. Moreover, the attacker can compromise and extract information from any number of devices. Through such captures, the attacker can retrieve secret information stored in the IoT node’s memory using “power analysis attacks” [29,30], as these devices typically lack physical security measures [8]. We conducted a security analysis using the same threat models as those employed by the previous work [8].
3.2. Elliptic Curve Cryptosystem (ECC)
Let represent a large prime and let be a nonsingular elliptic curve defined over the finite field . Let P denote a generator point on this curve. The operation of group is the standard point addition on , and G is a subgroup of order p, where . Therefore, the following holds:
Definition 1.
Elliptic curve decisional Diffie–Hellman problem (ECDDHP): Given three elliptic curve points , , and on , determine whether equals the product or is a random value.
Definition 2.
Elliptic curve discrete logarithm problem (ECDLP): Given two points , with , where , find x.
3.3. Physical Unclonable Function
PUF [31] is a powerful solution for safeguarding resource-constrained smart devices against various types of security attacks. It produces unique outputs, similar to fingerprints, which are determined by the device’s distinct physical characteristics. Since PUF does not store secret keys, it is extremely difficult to replicate. This makes PUF particularly valuable for securing IoT devices, as it defends against threats like tampering, cloning, and side-channel attacks. The outputs are generated by nanoscale irregularities in the device’s manufacturing process, meaning that any modification made to the device will change its output. PUF is used to verify the authenticity of a device before establishing a secure session key. The procedures of PUF operation are outlined below:
- (1)
- A random input challenge C is provided to the PUF.
- (2)
- The challenge C interacts with the unique physical attributes of the device.
- (3)
- The PUF generates a corresponding response R based on these attributes.
- (4)
- The response R is then verified to authenticate the device and ensure secure communication.
4. Review of Hu et al.’s Scheme [8]
This section provides a concise overview of the previous [8] work and a threat model used for its crypt-analysis. The previous scheme is divided into three phases: initialization, registration, and AKA. Table 3 presents the relevant notations.

Table 3.
Notations used in this work.
4.1. Initialization Phase
In this phase, the TA chooses an over the and its base point P; then, the TA selects “a collision-resistant hash function” . Finally, the TA broadcasts to open networks.
4.2. Registration Phase
This section presents the registration phase of the previous scheme, and its detailed steps are shown below.
- (1)
- The service provider (SP) selects a random number and an identity . Then, the SP computes and sends to the TA.
- (2)
- The TA chooses a random number and computes the public key of the SP . Afterward, the TA sends to the SP through a secure channel.
- (3)
- The SP computes the private key using and then checks whether . If this is correct, then SP generates and stores in a memory. The end device (S) also stores through the same registration procedures.
4.3. AKA Phase
In this phase, the S and SP perform AKA for future communications, as detailed below.
- (1)
- The S first selects a random number and generates a timestamp . Then, the S computes mod and . The S also computes and , and it sends to the SP.
- (2)
- The SP verifies the freshness of timestamp . The S calculates and , computes , and checks .
- (3)
- If the equality is verified, then SP chooses a random number and a timestamp , and the SP generates mod , , the session key , and . Finally, the SP sends to the S.
- (4)
- The S verifies the freshness of timestamp and then computes mod , the session key , and . Finally, the S checks whether . If this is correct, then the SP and S successfully authenticate each other.
5. Security Weaknesses of Hu et al. Scheme [8]
In this section, we show that the previous scheme is vulnerable to “physical capture” and “impersonation attacks”. Additionally, we show that the scheme fails to secure session keys and authentication between entities.
5.1. Formal Security Analysis Using ROR Model
We demonstrate that the previous scheme does not guarantee session key security using mathematical analysis through the ROR model [9], a widely accepted method for formal security verification [10,11]. To assess protocol security, we first present the basics of the ROR model and use it to evaluate the security of the previous protocol.
- Participants: The protocol instances for the S and the SP are denoted as and , respectively.
- Accepted state: Once the message exchange process is completed, the oracle transitions to an accepted state, where its session identifier is defined by the sequence of all messages exchanged during the interaction.
- Partnering: Two instances, and , are considered partners if they share the same , reach the accepted state, and successfully complete the AKA procedure.
- Freshness: The instances (, ) are regarded as fresh if the session key exchanged between the S and SP remains secure and unexposed to the adversary A.
- Adversary: In the threat model of the previous protocol [8], an adversary A can fully manage the networks and use the ROR queries outlined in Table 4 to attempt to breach the protocol security.
- Semantic security: The adversary A seeks to extract the session key of an instance by manipulating an arbitrary nonce. Initially, A makes a guess about a bit c using ROR queries. If A accurately predicts the bit c, it wins, thereby undermining the semantic security of the protocol. The event where A wins is denoted as , and the session-key-breaking advantage for the previous protocol is expressed as .
- Random oracle: Every participant in the protocol is granted access to a random oracle, which is realized through a secure hash function denoted as H.
Through Definitions 1 and 2 and Theorem 1, we prove that the previous scheme does not ensure security.
Theorem 1.
Within the threat model, we define as the number of queries made to the random oracle and as the output length of H. Assuming that the adversary A, running within a polynomial time against the previous protocol P, has an advantage in breaking the security of the session key,

Table 4.
Queries of ROR model.
Table 4.
Queries of ROR model.
| Queries | Explanations |
|---|---|
| This query models an eavesdropping scenario, in which the adversary A can intercept and observe communications occurring over the open network. | |
| This query simulates a “physical capture attack”, enabling the adversary A to retrieve data from the S. | |
| This query represents an active attack simulation, where the adversary A is able to send a message to the oracle and obtain a response in return. | |
| This query tests the freshness security of by presenting an arbitrary choice c; A is given either the actual () or an arbitrary value (), or NULL if it is not fresh. |
This formal proof is executed around several games , where is the occurrence of A winning a game .
- Game : This game represents an active adversary scenario where A targets the scheme with a randomly chosen c at the start of the game and has a particular winning advantage.
- Game : This game depicts an “eavesdropping attack” in which the adversary A can monitor the transmitted messages through queries and then performs a query to differentiate between the real and a random value. In their scheme, is derived as and . Despite accessing all public channel communications, A cannot compute , thereby failing to enhance its probability of winning the game. Then,
- This game simulates an impersonation attack where adversary A impersonates a legitimate S using , , and several queries. According to the assumptions of the previous work, A first performs the query to retrieve from the S memory. A can compromise using the real identity and without needing to solve the ECDLP or ECDDHP. Consequently, games and can be distinguished. Then,
Upon completion of all games (, A tries to guess the c correctly using the query. Therefore,
Finally, we eliminate the term in Equation (7), as the security of the session key can be compromised without needing to solve the ECDDHP and ECDLP. This formal proof demonstrates that it fails to secure session keys.
5.2. Informal Security Analysis
In this section, we perform logical security analysis to prove that the previous scheme cannot withstand “physical capture and impersonation attacks”.
5.2.1. Physical Capture Attack
As discussed in Section 4.2, the TA stores the data in the S memory without using cryptographic techniques. Within the security analysis in the previous scheme [8], the authors considered physical capture attacks. Therefore, an adversary A can retrieve stored values through “power analysis attacks” [29,30]. This vulnerability allows A to execute impersonation attacks and breach user privacy.
5.2.2. End Device Impersonation Attack
An impersonation attack occurs when an attacker masquerades as a legitimate user to gain unauthorized benefits. The attack is considered successful if the attacker obtains secret parameters and makes AKA requests that are undetected by legitimate entities.
In Hu et al.’s scheme [8], security is assessed using their proposed assumptions. However, by obtaining an end device and retrieving its stored data through physical capture attacks, A can easily compute a login request and calculate the correct session key . This vulnerability arises because the secret parameters stored in the S memory lack cryptographic protection. Therefore, the previous scheme fails to defend against end device impersonation attacks. Figure 1 shows a process affected by this issue.
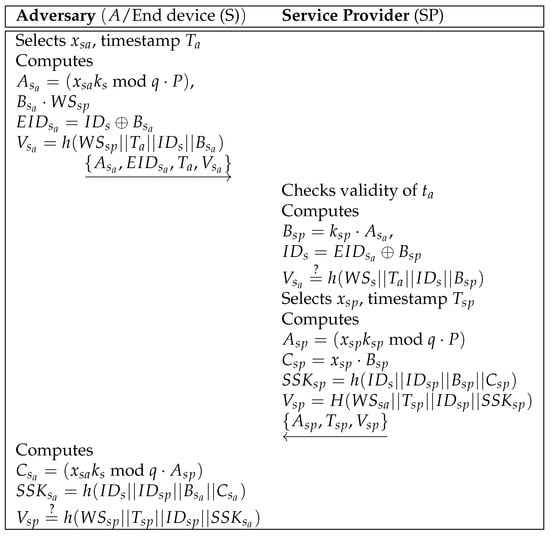
Figure 1.
End device impersonation attack in the previous scheme.
5.2.3. Insecure Mutual Authentication
According to Section 5.2.1 and Section 5.2.2, A can effortlessly masquerade as a legal vehicle to gain entry into the IoT networks described in the previous scheme and successfully authenticate with the participating nodes. A can also compromise the session key between an end device and the SP. Thus, it fails to achieve secure mutual AKA.
5.2.4. Correctness of Threat Model
The authors asserted that the overall system remains secure because only a single device is captured in a physical capture attack. However, the capture of a medical device or another critical component of the system could present serious security risks. Therefore, a method that guarantees the security of all end devices against physical capture attacks should be developed. We propose three solutions (1–3) to enhance security and privacy in Section 6.
5.3. AVISPA: Simulation Analysis
The security of cryptographic protocols is rigorously verified using AVISPA, a prominent tool for evaluating security schemes [12,13]. AVISPA checks schemes for vulnerabilities, such as replay and MITM attacks. It uses the “high-level protocol specification language” (HLPSL) [32] to specify the security aspects of protocols. This tool leverages four back-end models [33]: the “constraint-logic-based attack searcher” (CL-AtSE), “on-the-fly model checker” (OFMC), “SAT-based model checker” (SATMC), and “tree-automata-based protocol analyzer” (TA4SP). The HLPSL code is converted into an intermediate format with the HLPSL2IF translator, which is then evaluated using these back-end models to determine the protocol security properties. Figure 2 depicts this workflow, and further details on HLPSL are provided in [13,32].
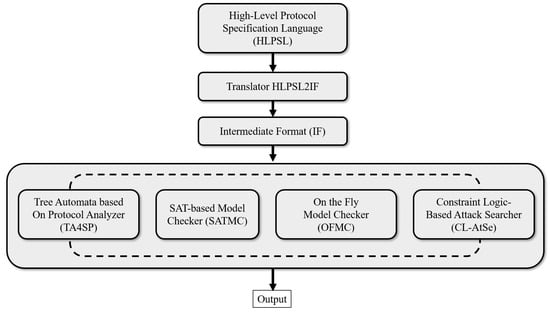
Figure 2.
AVISPA simulation procedure.
5.3.1. AVISPA Simulation Environments
The simulation was carried out on a machine running Ubuntu 10.10, featuring 2 GB of RAM, and driven by an Intel Core i9-11900K processor operating at 3.50 GHz, with a total of 64 GB of RAM.
5.3.2. HLPLS Specifications
The previous scheme was assessed through this simulation by modeling all phases of their scheme using HLPSL codes. We evaluated it by analyzing the authentication procedures between the involved entities. It includes three primary roles: trusted third party (TA), service provider (SP), and end device (S). The HLPSL codes of these entities are depicted in Figure 3 (TA), Figure 4 (SP) and Figure 5 (S). The environment and session details are illustrated in Figure 6.

Figure 3.
HLPSL description: TA’s role.

Figure 4.
HLPSL description: SP’s role.
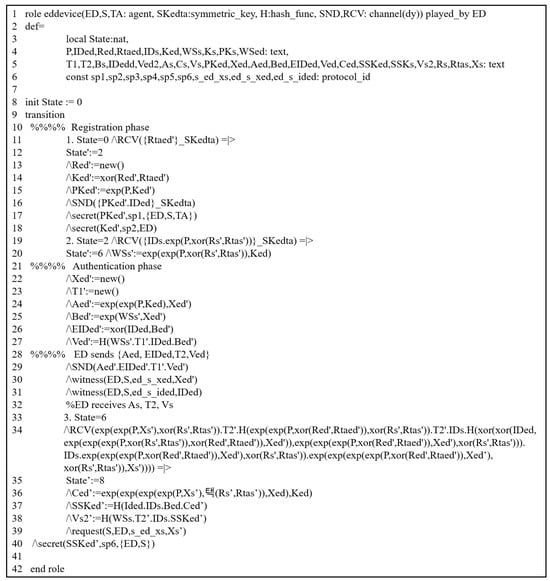
Figure 5.
HLPSL description: end device’s role.

Figure 6.
HLPSL description: session and environment.
5.3.3. Simulation Results
To demonstrate that the previous scheme is susceptible to replay and MIMT attacks, we used OMFC and CL-AtSe using the provided HLPSL codes (Figure 3, Figure 4, Figure 5 and Figure 6).
- OFMC: The total search time was 0.07 s, and the reached states are described in Figure A1 in Appendix A.
- CL-AtSe: For CL-AtSe, the translation time was 0.03 s, during which five states were analyzed.
The OFMC and CL-AtSe results in Figure A1 indicate an “unsafe” status. Hence, the previous scheme failed to thwart replay and MIMT attacks.
6. Security Fixes
The previous scheme [8] has notable security flaws, primarily due to the storage of secret information in end devices without cryptographic techniques. These flaws allow an attacker to access the private data in the memory of devices easily, enabling them to masquerade as legitimate entities and compromise the session keys between participating nodes. These critical security weaknesses are detailed in Section 5.
Many AKA schemes proposed in recent decades involve storing secret data in device memory for authentication between communicating entities. Hu et al. [8] claimed that the overall system remains secure in their scheme because only one device is captured through a physical capture attack. However, the capture of medical devices or devices critical to the system could pose significant security risks. Therefore, a method that secures all end devices against physical capture attacks should be designed. To address the security problems identified in a previous protocol, we propose the following key guidelines.
- Sol. 1.
- According to Section 4.2, the TA avoids storing secret data as plaintext to resist “physical capture attacks”. According to their security analysis, an attacker can easily compromise the memory of end devices and obtain their data. Thus, end devices should securely store these data using masked techniques, such as exclusive OR (XOR) operations combined with a hash function. For example, instead of directly storing and on an end device, these values can be stored by performing an XOR operation with certain parameters, such as and , or by generating values based on the hash of , like -. This solution can prevent the adversary from easily obtaining , as these values are not stored in the memory as plaintext.
- Sol. 2.
- The use of PUFs on end devices is recommended to resist physical capture attacks. In a previous scheme, the identity of an end device and a secret parameter can be easily extracted, potentially facilitating impersonation attacks. However, a PUF-based AKA scheme protects against physical capture attacks by generating unique secret parameters using a physical semiconductor structure [26,27]. For example, the session key can be computed using unique random values produced by a PUF. The user sends their challenge C to the PUF, which then generates the corresponding response R. Since the R is based on the PUF’s physical characteristics, it cannot be reproduced by any other device. Therefore, this response can be used in the key establishment process to ensure security. In a previous scheme, the adversary can easily generate the session key by knowing the secret values and . Therefore, by incorporating the value into session key generation (), an adversary cannot compromise the session key without breaking the difficulty of the PUF. This suggestion resolves the above-mentioned security weaknesses and other potential flaws.
- Sol. 3.
- In a previous scheme, end devices rely on one-factor authentication during AKA, which does not require any user input. This mechanism makes physically compromised devices susceptible to attacks. This vulnerability should be mitigated by adopting a two-factor authentication (2FA) or three-factor authentication (3FA) mechanism for end devices, particularly when sessions are refreshed. A 2FA system uses either passwords or biometric data. For enhanced security, a 3FA system can be used, integrating both password and biometric verification. This additional security measure greatly enhances protection against unauthorized access. We recommend implementing a 3FA mechanism incorporating biometric verification through a fuzzy extractor [34] combined with PUF-based secret parameters. A “fuzzy extractor”, which is frequently used in biometric authentication, can be adopted to develop a resilient 3FA-based AKA scheme. In this enhanced mechanism, the security of secret parameters can be reinforced using masking techniques, such as XOR and hash functions, in conjunction with the biometric data generated by the “fuzzy extractor”. Consequently, even if end devices are physically compromised by an adversary, the secret parameters used in the AKA process remain protected and inaccessible without the corresponding biometric data.
The proposed solutions are intended to reduce the risk of impersonation attacks on end devices; they do not address all possible security vulnerabilities. Nonetheless, these improvements significantly enhance system security and raise the difficulty level for potential attackers. The times required to perform XOR and PUF operations on low-specification Arduino devices are 0.95 and 1.22 ms, respectively, indicating minimal computational requirements and demonstrating effective operation on even very small devices. Moreover, by incorporating a PUF module into low-spec devices for key generation, it is possible to implement 3FA without relying on biometrics, thereby enhancing the overall security level. Therefore, the proposed solutions are highly applicable and efficient in numerous IoT environments with low-specification devices [27].
The authors of the previous work exerted considerable effort in designing an IoT AKA scheme. However, a more comprehensive examination of their scheme from various angles would have been beneficial. The progression of research in this field involves various approaches from different studies. The current paper underscores the continuing need for the development of robust, efficient AKA schemes in IoT environments.
7. Conclusions and Future Works
This paper refers to the recent secure ECC-based IoT AKA scheme. We prove that this scheme does not prevent impersonation attacks on end devices, thereby not securing AKA and satisfying the security properties under their security assumptions. By applying formal mathematical analysis with the ROR model, we show that the scheme does not provide sufficient security for the session key. In addition, we perform an AVISPA simulation, a well-established tool for formal verification, to assess the protocol’s vulnerabilities. These identified security flaws render the protocol impractical for real-world implementation. To address these issues, we suggest improvements to enhance security and design a more reliable and efficient AKA scheme tailored for IoT environments. Our future work will involve developing a blockchain-based AKA scheme that is adaptable to various settings with resource-limited devices (Arduino, Raspberry Pi, ARM Boards, etc.), incorporating the proposed solutions. Additionally, given the significance of physical capture attacks in distributed systems, we plan to explore distributed authentication approaches. A key challenge in this area is establishing a secure connection between different types of embedded devices and the PUF module.
Author Contributions
Conceptualization, K.P.; Methodology, K.P.; Validation, K.P., M.K. and Y.P.; Formal analysis, K.P. and M.K.; Writing—original draft, K.P.; Writing—review & editing, Y.P.; Supervision, Y.P. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Institute of Information & communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No. RS-2024-00396797, Development of core technology for intelligent O-RAN security platform).
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A
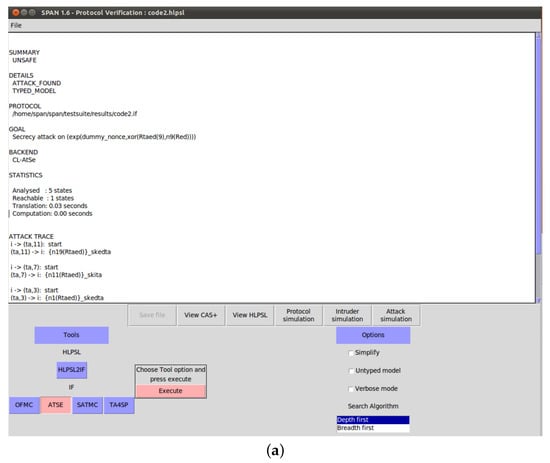
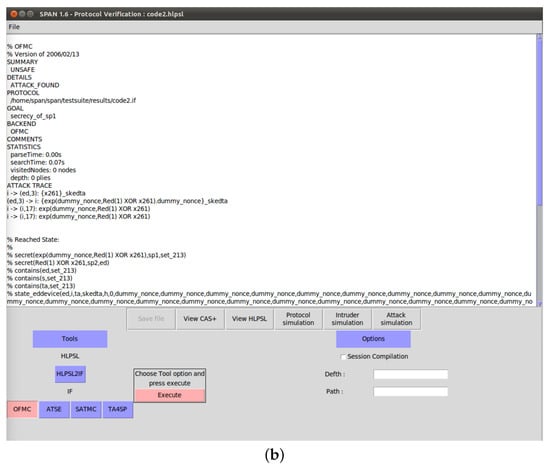
Figure A1.
Simulation results. (a) Result: CL-AtSe. (b) Result: OFMC.
References
- Tedeschi, P.; Sciancalepore, S.; Eliyan, A.; Di Pietro, R. LiKe: Lightweight Certificateless Key Agreement for Secure IoT Communications. IEEE Internet Things J. 2020, 7, 621–638. [Google Scholar] [CrossRef]
- Vailshery, L.S. Number of Internet of Things (IoT) Connections Worldwide from 2022 to 2023, with Forecasts from 2024 to 2033. Available online: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide (accessed on 25 August 2024).
- Nicanfar, H.; Hosseininezhad, S.; TalebiFard, P.; Leung, V.C. Robust privacy-preserving authentication scheme for communication between Electric Vehicle as Power Energy Storage and power stations. In Proceedings of the 2013 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Turin, Italy, 14–19 April 2013; pp. 55–60. [Google Scholar] [CrossRef]
- Showkat, D.; Som, S.; Khatri, S.K.; Ahluwalia, A.S. Security Implications in IoT using Authentication and Access Control. In Proceedings of the 2018 7th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 29–31 August 2018; pp. 689–694. [Google Scholar] [CrossRef]
- Zheng, Y.; Hu, S.; Wei, L.; Chen, Y.; Wang, H.; Yang, Y.; Li, Y.; Xu, B.; Huang, W.; Chen, L. Design and Analysis of a Security-Enhanced Three-Party Authenticated Key Agreement Protocol Based on Chaotic Maps. IEEE Access 2020, 8, 66150–66162. [Google Scholar] [CrossRef]
- Cao, Y.; Ke, W.; Cui, E.; Yu, F. A deep recommendation model of cross-grained sentiments of user reviews and ratings. Inf. Process. Manag. 2022, 59, 102842. [Google Scholar] [CrossRef]
- Zhu, P.; Zhang, H.; Shi, Y.; Xie, W.; Pang, M.; Shi, Y. A novel discrete conformable fractional grey system model for forecasting carbon dioxide emissions. Environ. Dev. Sustain. 2024; early access. [Google Scholar] [CrossRef]
- Hu, S.; Jiang, S.; Miao, Q.; Yang, F.; Zhou, W.; Duan, P. Provably Secure ECC-Based Anonymous Authentication and Key Agreement for IoT. Appl. Sci. 2024, 14, 3187. [Google Scholar] [CrossRef]
- Abdalla, M.; Fouque, P.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography (PKC’05), Lecture Notes in Computer Science (LNCS), Les Diablerets, Switzerland, 23–26 January 2005; pp. 65–84. [Google Scholar] [CrossRef]
- Park, K.; Park, Y. MIoT-CDPS: Complete decentralized privacy-preserving scheme for medical internet of things. Internet Things 2024, 27, 101250. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS:Blockchain-Enabled Privacy-Preserving Scheme for Demand-Response Management in Smart Grid Environments. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1719–1729. [Google Scholar] [CrossRef]
- Kim, M.; Park, K.; Park, Y. A reliable and privacy-preserving vehicular energy trading scheme using decentralized identifiers. Mathematics 2024, 12, 1450. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Sutrala, A.K.; Das, A.K.; Park, Y. LAKA-UAV: Lightweight authentication and key agreement scheme for cloud-assisted Unmanned Aerial Vehicle using blockchain in flying ad-hoc networks. Comput. Netw. 2023, 224, 109612. [Google Scholar] [CrossRef]
- Fang, D.; Qian, Y.; Hu, R.Q. A Flexible and Efficient Authentication and Secure Data Transmission Scheme for IoT Applications. IEEE Internet Things J. 2020, 7, 3474–3484. [Google Scholar] [CrossRef]
- Maurya, A.K.; Das, A.K.; Jamal, S.S.; Giri, D. Secure user authentication mechanism for IoT-enabled Wireless Sensor Networks based on multiple Bloom filters. J. Syst. Archit. 2021, 120, 102296. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Nikooghadam, M.; Mazinani, S.M. A Secure and Efficient Key Establishment Scheme for Communications of Smart Meters and Service Providers in Smart Grid. IEEE Trans. Ind. Inform. 2020, 16, 1495–1502. [Google Scholar] [CrossRef]
- Baruah, B.; Dhal, S. An Authenticated Key Agreement Scheme for Secure Communication in Smart Grid. In Proceedings of the 2021 International Conference on COMmunication Systems NETworkS (COMSNETS), Bangalore, India, 5–9 January 2021; pp. 447–455. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Li, X.; Khan, M.K.; Jo, M. Designing Anonymous Signature-Based Authenticated Key Exchange Scheme for Internet of Things-Enabled Smart Grid Systems. IEEE Trans. Ind. Inform. 2021, 17, 4425–4436. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Khalil, I.; Huang, X.; Shen, J. Efficient and Anonymous Authentication for Healthcare Service with Cloud Based WBANs. IEEE Trans. Serv. Comput. 2022, 15, 2728–2741. [Google Scholar] [CrossRef]
- Shen, J.; Gui, Z.; Ji, S.; Shen, J.; Tan, H.; Tang, Y. Cloud-aided lightweight certificateless authentication protocol with anonymity for wireless body area networks. J. Netw. Comput. Appl. 2018, 106, 117–123. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Nebhan, J.; Yahya, K.; Al-Turjman, F. A Privacy Enhanced Authentication Scheme for Securing Smart Grid Infrastructure. IEEE Trans. Ind. Inform. 2022, 18, 5000–5006. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S. A Secure Anonymous D2D Mutual Authentication and Key Agreement Protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Chen, Y.; Yin, F.; Hu, S.; Sun, L.; Li, Y.; Xing, B.; Chen, L.; Guo, B. ECC-Based Authenticated Key Agreement Protocol for Industrial Control System. IEEE Internet Things J. 2023, 10, 4688–4697. [Google Scholar] [CrossRef]
- Rajkumar, Y.; Kumar, S.V.N.S. An elliptic curve cryptography based certificate-less signature aggregation scheme for efficient authentication in vehicular ad hoc networks. Wirel. Netw. 2024, 30, 335–362. [Google Scholar] [CrossRef]
- Ma, H.; Wang, C.; Xu, G.; Cao, Q.; Xu, G.; Duan, L. Anonymous Authentication Protocol Based on Physical Unclonable Function and Elliptic Curve Cryptography for Smart Grid. IEEE Syst. J. 2023, 17, 6425–6436. [Google Scholar] [CrossRef]
- Yu, S.; Park, K. PUF-based robust and anonymous authentication and key establishment scheme for V2G networks. IEEE Internet Things J. 2024, 11, 15450–15464. [Google Scholar] [CrossRef]
- Awais, S.M.; Wu, Y.; Mahmood, K.; Akram, M.W.; Hussain, S.; Das, A.K.; Park, Y. PUF-Based Privacy-Preserving Simultaneous Authentication Among Multiple Vehicles in VANET. IEEE Tran. Veh. Technol. 2024, 73, 6727–6739. [Google Scholar] [CrossRef]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger Security of Authenticated Key Exchange. In Proceedings of the 1st International Conference on Provable Security (ProvSec’07), Wollongong, NSW, Australia, 1–2 November 2007; pp. 1–16. [Google Scholar] [CrossRef]
- Eisenbarth, T.; Kasper, T.; Moradi, A.; Paar, C.; Salmasizadeh, M.; Shalmani, M.T.M. On the power of power analysis in the real world: A complete break of the KEELOQ code hopping scheme. In Advances in Cryptology–CRYPTO; Springer: Berlin/Heidelberg, Germany, 2008; pp. 203–220. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology–CRYPTO; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar] [CrossRef]
- Aman, M.N.; Chua, K.C.; Sikdar, B. Mutual Authentication in IoT Systems Using Physical Unclonable Functions. IEEE Internet Things J. 2017, 4, 1327–1340. [Google Scholar] [CrossRef]
- Von Oheimb, D. The high-level protocol specification language HLPSL developed in the EU project avispa. In Proceedings of the APPSEM 2005 Workshop, Tallinn, Finland, 13–15 September 2005; pp. 1–2. [Google Scholar]
- Vigano, L. Automated Security Protocol Analysis with the AVISPA Tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61. [Google Scholar] [CrossRef]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. SIAM J. Comput. 2008, 38, 97. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).