Intelligent Energy Efficiency Maximization for Wirelessly-Powered UAV-Assisted Secure Sensor Network
Abstract
:1. Introduction
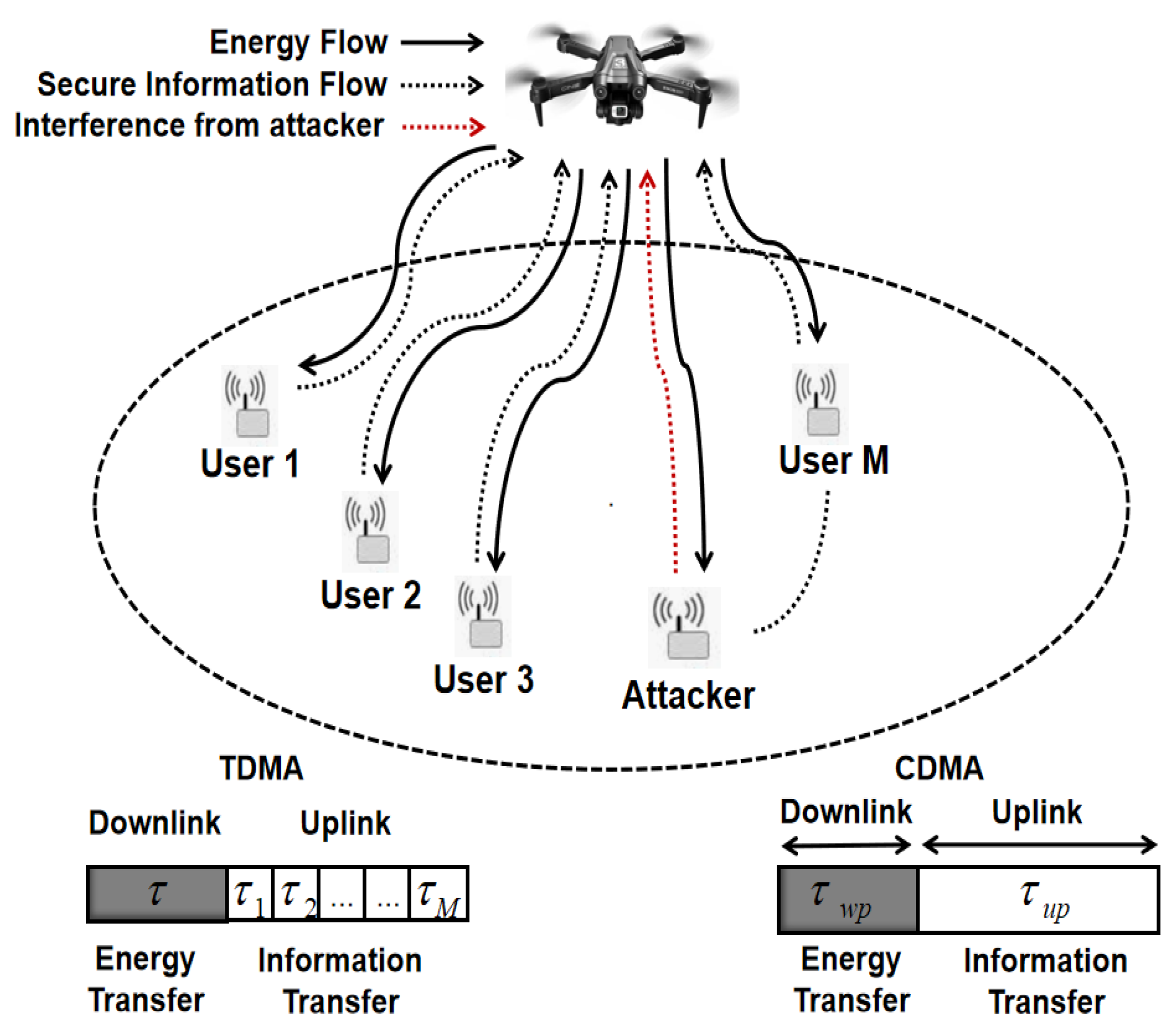
2. System and Channel Model
2.1. TDMA
2.2. CDMA
3. Energy Efficiency Maximization
3.1. TDMA
3.1.1. Optimization Without QoS Constraint
3.1.2. Optimization with QoS Constraint
3.2. CDMA
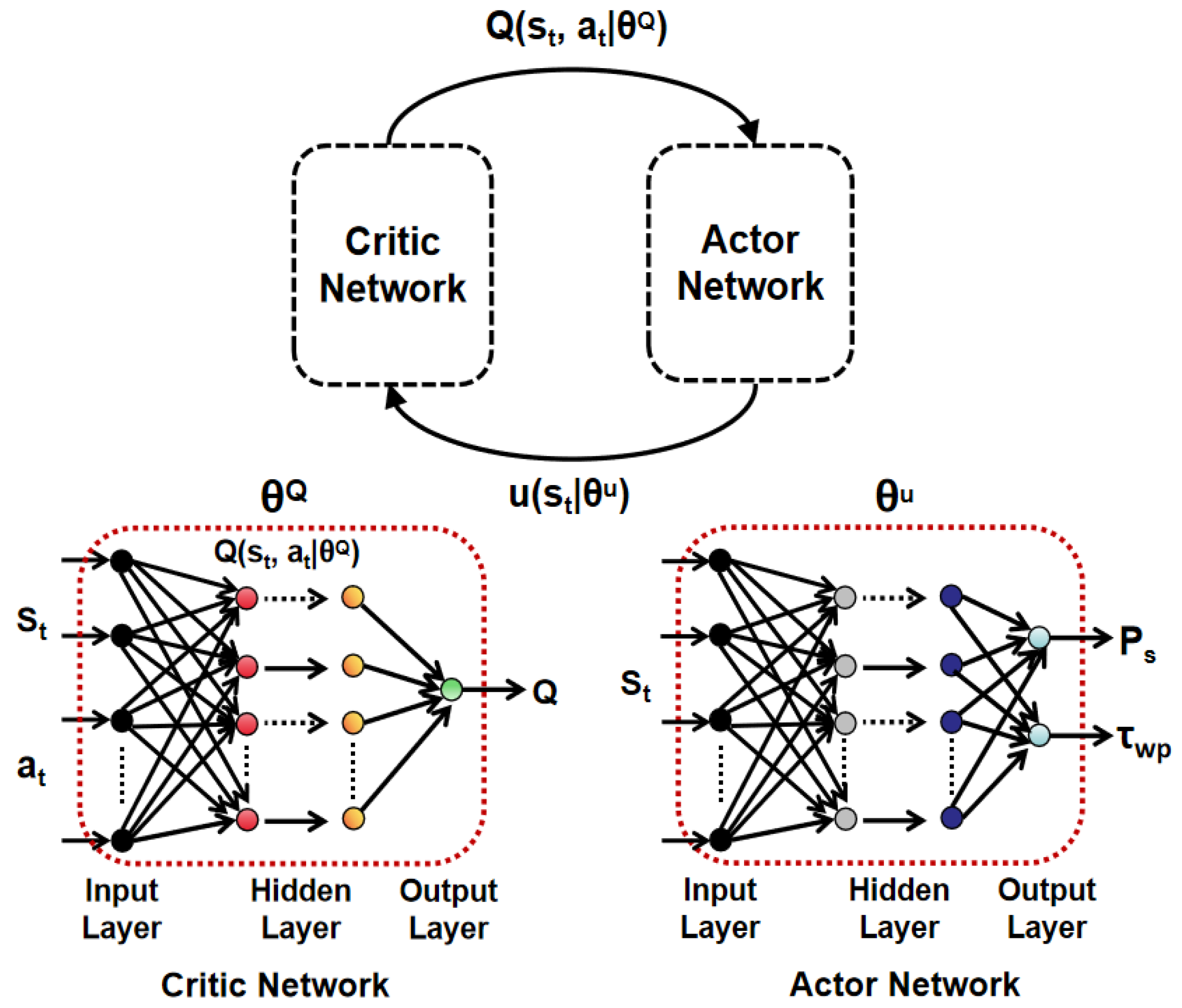
DDPG Solution
| Algorithm 1 pseudo-code for action policy training |
|
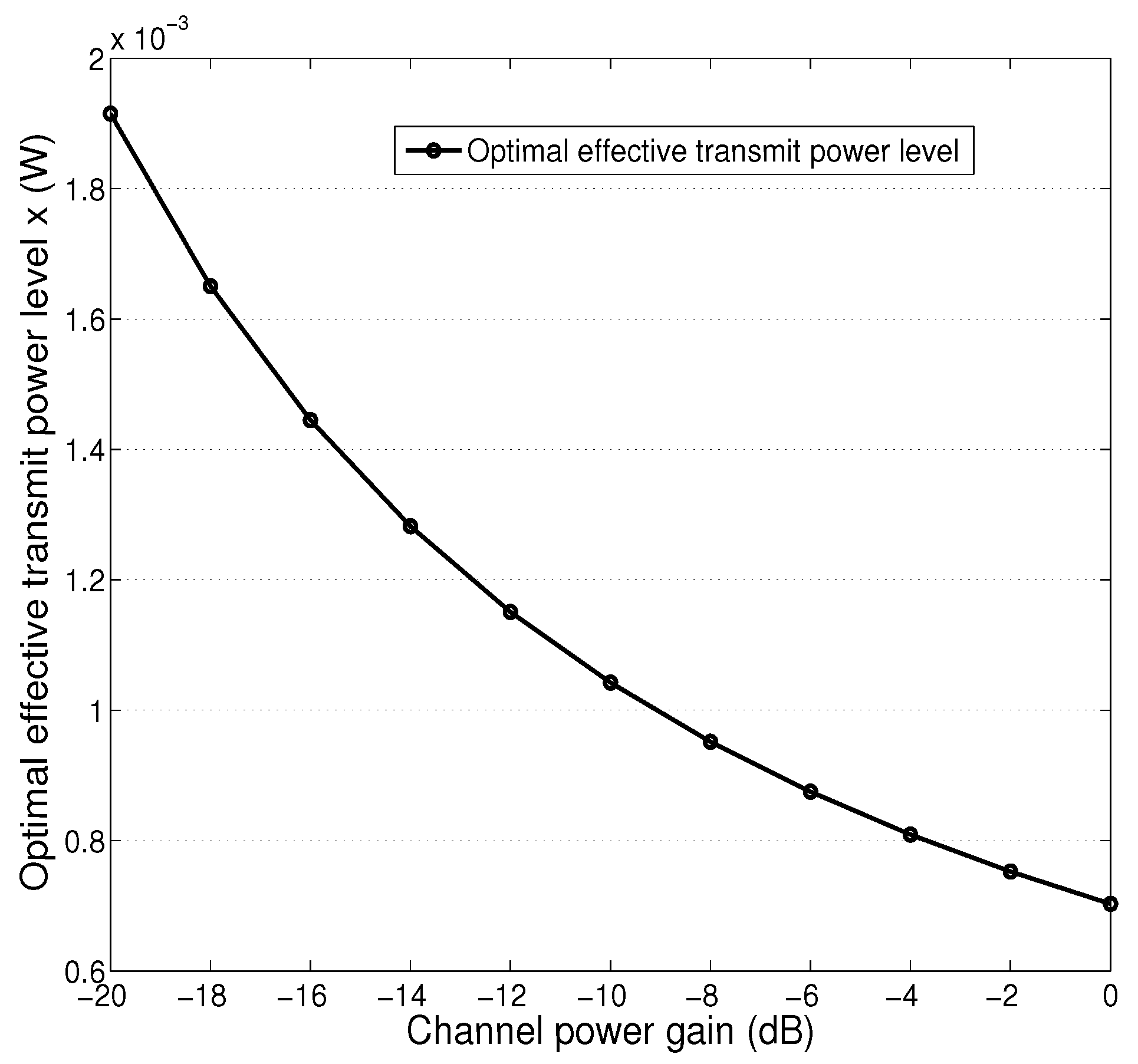
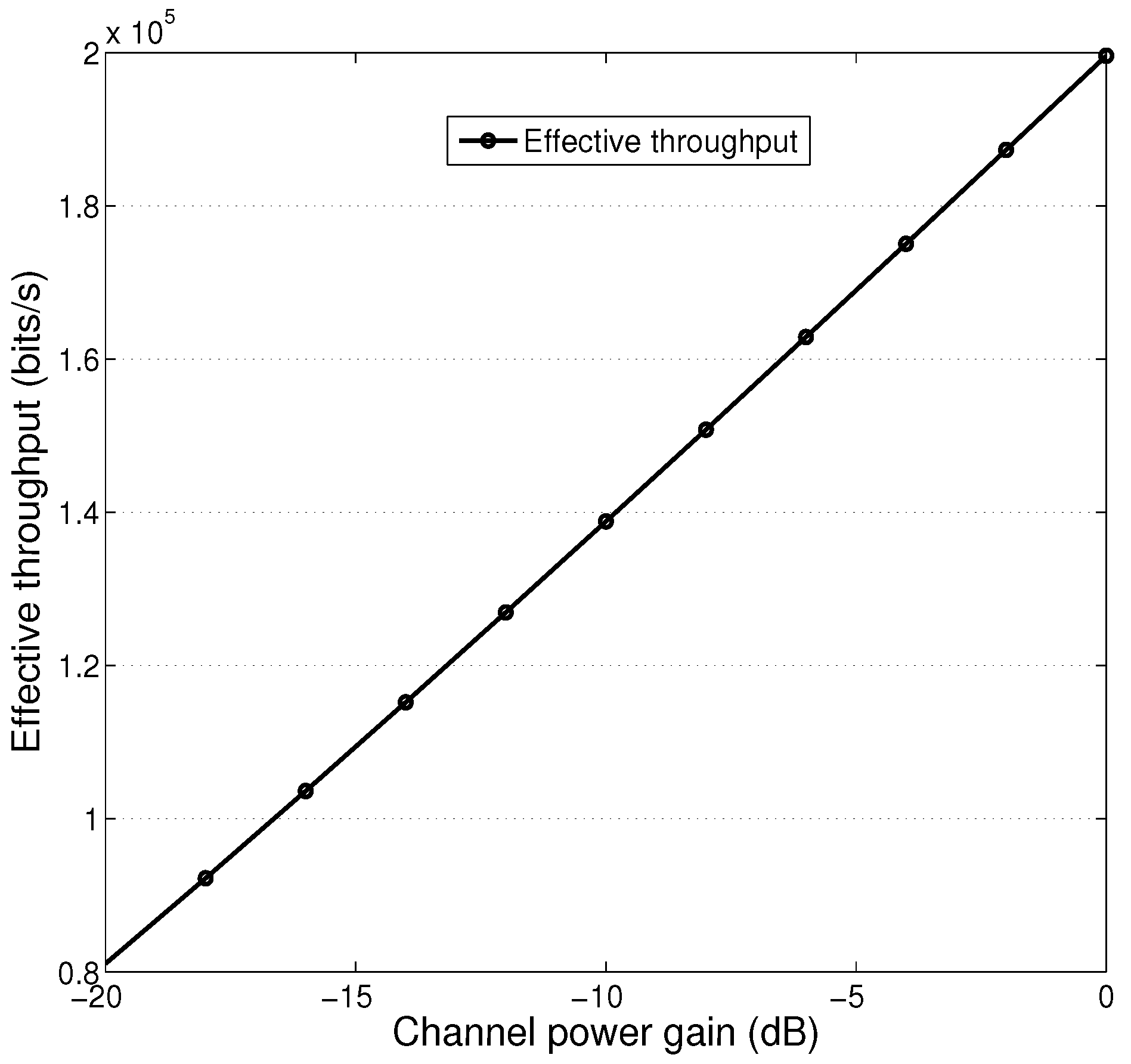
4. Numerical Results
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lu, X.; Luong, N.C.; Hoang, D.T.; Niyato, D.; Xiao, Y.; Wang, P. Secure Wirelessly Powered Networks at the Physical Layer: Challenges, Countermeasures, and Road Ahead. Proc. IEEE 2013, 110, 1410–1423. [Google Scholar] [CrossRef]
- Zhu, T.; Shen, L. Secure and Efficient Certificateless Linearly Homomorphic Signature Scheme for Wireless Sensor Networks. In Proceedings of the International Conference on Big Data and Privacy Computing, Macau, China, 10–12 January 2024; pp. 113–121. [Google Scholar]
- Lei, H.; Luo, H.; Park, K.H.; Ansari, I.S.; Lei, W.; Pan, G.; Alouini, M.S. On Secure Mixed RF-FSO Systems with TAS and Imperfect CSI. IEEE Wirel. Commun. Lett. 2020, 68, 4461–4475. [Google Scholar] [CrossRef]
- Saxena, V.N.; Gupta, J.; Dwivedi, V.K. Secured End-to-End FSO-VLC-Based IoT Network with Randomly Positioned VLC: Known and Unknown CSI. IEEE Internet Things J. 2023, 10, 1347–1357. [Google Scholar] [CrossRef]
- He, D.; Liu, C.; Wang, H.; Quek, T.Q.S. Learning-Based Wireless Powered Secure Transmission. IEEE Wirel. Commun. Lett. 2019, 8, 600–603. [Google Scholar] [CrossRef]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust Secure Transmission in MISO Simultaneous Wireless Information and Power Transfer System. IEEE Trans. Veh. Technol. 2015, 64, 400–405. [Google Scholar] [CrossRef]
- Limbasiya, T.; Das, D.; Das, S.K. MComIoV: Secure and Energy-Efficient Message Communication Protocols for Internet of Vehicles. IEEE/ACM Trans. Netw. 2021, 29, 1349–1361. [Google Scholar] [CrossRef]
- Nghia, N.T.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. MIMO Beamforming for Secure and Energy-Efficient Wireless Communication. IEEE Signal Process. Lett. 2017, 24, 236–239. [Google Scholar] [CrossRef]
- Cai, Y.; Wei, Z.; Li, R.; Ng, D.W.K.; Yuan, J. Joint Trajectory and Resource Allocation Design for Energy-Efficient Secure UAV Communication Systems. IEEE Trans. Commun. 2020, 68, 4536–4553. [Google Scholar] [CrossRef]
- Guo, S.; Wang, F.; Yang, Y.; Xiao, B. Energy-Efficient Cooperative Transmission for Simultaneous Wireless Information and Power Transfer in Clustered Wireless Sensor Networks. IEEE Trans. Commun. 2015, 63, 4405–4417. [Google Scholar] [CrossRef]
- Tang, J.; Shojaeifard, A.; So, D.K.C.; Wong, K.K.; Zhao, N. Energy Efficiency Optimization for CoMP-SWIPT Heterogeneous Networks. IEEE Trans. Commun. 2018, 66, 6368–6383. [Google Scholar] [CrossRef]
- Yang, K.; Yu, Q.; Leng, S.; Fan, B.; Wu, F. Data and Energy Integrated Communication Networks for Wireless Big Data. IEEE Access 2016, 4, 713–723. [Google Scholar] [CrossRef]
- Sun, Q.; Li, L.; Mao, J. Simultaneous Information and Power Transfer Scheme for Energy Efficient MIMO Systems. IEEE Trans. Veh. Technol. 2014, 18, 600–603. [Google Scholar] [CrossRef]
- Akbar, S.; Deng, Y.; Nallanathan, A.; Elkashlan, M.; Aghvami, A. Simultaneous Wireless Information and Power Transfer in K-Tier Heterogeneous Cellular Networks. IEEE Trans. Wireless Commun. 2016, 15, 5804–5818. [Google Scholar] [CrossRef]
- Huang, H.; Li, C.; Wu, C.; Wu, F.; Li, L. Energy Efficiency Optimization Method under the Scene of Wireless Information and Energy Simultaneous Transmission. In Proceedings of the International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, Zhengzhou, China, 18–20 October 2018; pp. 321–328. [Google Scholar]
- Ju, H.; Zhang, R. A Novel Mode Switching Scheme Utilizing Random Beamforming for Opportunistic Energy Harvesting. IEEE Trans. Wirel. Commun. 2014, 13, 2150–2162. [Google Scholar] [CrossRef]
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. Secure and Energy-Efficient Beamforming for Simultaneous Information and Energy Transfer. IEEE Trans. Wirel. Commun. 2017, 16, 7523–7537. [Google Scholar] [CrossRef]
- Zhang, X.; Zhang, X.; Han, L. An Energy Efficient Internet of Things Network Using Restart Artificial Bee Colony and Wireless Power Transfer. IEEE Access 2019, 7, 12686–12695. [Google Scholar] [CrossRef]
- Sheng, M.; Wang, L.; Wang, X.; Zhang, Y.; Xu, C.; Li, J. Energy Efficient Beamforming in MISO Heterogeneous Cellular Networks with Wireless Information and Power Transfer. IEEE J. Sel. Areas Commun. 2016, 34, 954–968. [Google Scholar] [CrossRef]
- Chen, X.; Wang, X.; Chen, X. Energy-Efficient Optimization for Wireless Information and Power Transfer in Large-Scale MIMO Systems Employing Energy Beamforming. IEEE Wirel. Commun. Lett. 2013, 2, 667–670. [Google Scholar] [CrossRef]
- He, S.; Huang, Y.; Jin, S.; Yu, F.; Yang, L. Max-Min Energy Efficient Beamforming for Multicell Multiuser Joint Transmission Systems. IEEE Commun. Lett. 2013, 17, 1956–1959. [Google Scholar] [CrossRef]
- Wang, C.; Li, J.; Yang, Y.; Ye, F. Combining Solar Energy Harvesting with Wireless Charging for Hybrid Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2018, 17, 560–576. [Google Scholar] [CrossRef]
- Li, D.; Saad, W.; Guvenc, I.; Mehbodniya, A.; Adachi, F. Decentralized Energy Allocation for Wireless Networks with Renewable Energy Powered Base Stations. IEEE Trans. Commun. 2015, 63, 2126–2142. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Grid Energy Consumption and QoS Tradeoff in Hybrid Energy Supply Wireless Networks. IEEE Trans. Wirel. Commun. 2016, 15, 3573–3586. [Google Scholar] [CrossRef]
- Mnih, V.; Badia, A.P.; Mirza, M.; Graves, A.; Harley, T.; Lillicrap, T.P.; Silver, D.; Kavukcuoglu, K. Asynchronous Methods for Deep Reinforcement Learning. In Proceedings of the 33rd International Conference on Machine Learning, New York, NY, USA, 19–24 June 2016; pp. 1–10. [Google Scholar]
- Liu, C.H.; Chen, Z.; Zhan, Y. Energy-Efficient Distributed Mobile Crowd Sensing: A Deep Learning Approach. IEEE J. Sel. Areas Commun. 2019, 37, 1262–1276. [Google Scholar] [CrossRef]
- Liu, C.H.; Ma, X.; Gao, X.; Tang, J. Distributed Energy-Efficient Multi-UAV Navigation for Long-Term Communication Coverage by Deep Reinforcement Learning. IEEE Trans. Mob. Comput. 2019, 19, 1274–1285. [Google Scholar] [CrossRef]
- Qiu, C.; Hu, Y.; Chen, Y.; Zeng, B. Deep Deterministic Policy Gradient (DDPG)-Based Energy Harvesting Wireless Communications. IEEE Internet Things J. 2019, 6, 8577–8588. [Google Scholar] [CrossRef]
- Smida, B.; Affes, S.; Jamaoui, K.; Mermelstein, P. A Multicarrier-CDMA Space–Time Receiver with Full-Interference-Suppression Capabilities. IEEE Trans. Veh. Technol. 2008, 57, 363–379. [Google Scholar] [CrossRef]
- Xu, D.; Li, Q. Joint Power Control and Time Allocation for Wireless Powered Underlay Cognitive Radio Networks. IEEE Commun. Lett. 2017, 6, 294–297. [Google Scholar] [CrossRef]
- Blondeau, F.; Monir, A. Evaluation of the Lambert W function and application to generation of generalized Gaussian noise with exponent 1/2. IEEE Trans. Signal Process. 2002, 50, 2610–2615. [Google Scholar]


| Parameter | Meaning | Value |
|---|---|---|
| Noise Power | 1 Watt | |
| B | Available Bandwidth | 10 kHz |
| Path Loss Exponent | 2 | |
| PC | Circuit Power of Source Node | 0.01 Watt |
| DC Conversion Efficiency | 0.8 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, F.; Zhang, X. Intelligent Energy Efficiency Maximization for Wirelessly-Powered UAV-Assisted Secure Sensor Network. Sensors 2025, 25, 1534. https://doi.org/10.3390/s25051534
Xu F, Zhang X. Intelligent Energy Efficiency Maximization for Wirelessly-Powered UAV-Assisted Secure Sensor Network. Sensors. 2025; 25(5):1534. https://doi.org/10.3390/s25051534
Chicago/Turabian StyleXu, Fang, and Xinyu Zhang. 2025. "Intelligent Energy Efficiency Maximization for Wirelessly-Powered UAV-Assisted Secure Sensor Network" Sensors 25, no. 5: 1534. https://doi.org/10.3390/s25051534
APA StyleXu, F., & Zhang, X. (2025). Intelligent Energy Efficiency Maximization for Wirelessly-Powered UAV-Assisted Secure Sensor Network. Sensors, 25(5), 1534. https://doi.org/10.3390/s25051534






