Radar Compound Jamming Recognition Based on Image Segmentation and Fused Attention Residual Network
Abstract
:1. Introduction
- A compound jamming segmentation module based on Gabor filtering and k-means clustering is proposed to segment the time–frequency diagram of compound jamming;
- ResNet is optimized using the spatial-channel fused attention mechanism (SCFAM) on a hierarchical scale to extract critical jamming features for recognition;
- The experimental results show that the proposed algorithm has better recognition performance on the validation dataset and can recognize untrained patterns of compound jamming in the test dataset.
2. Radar Jamming Model and Preprocessing
2.1. Single Jamming Model
2.2. Compound Jamming Model
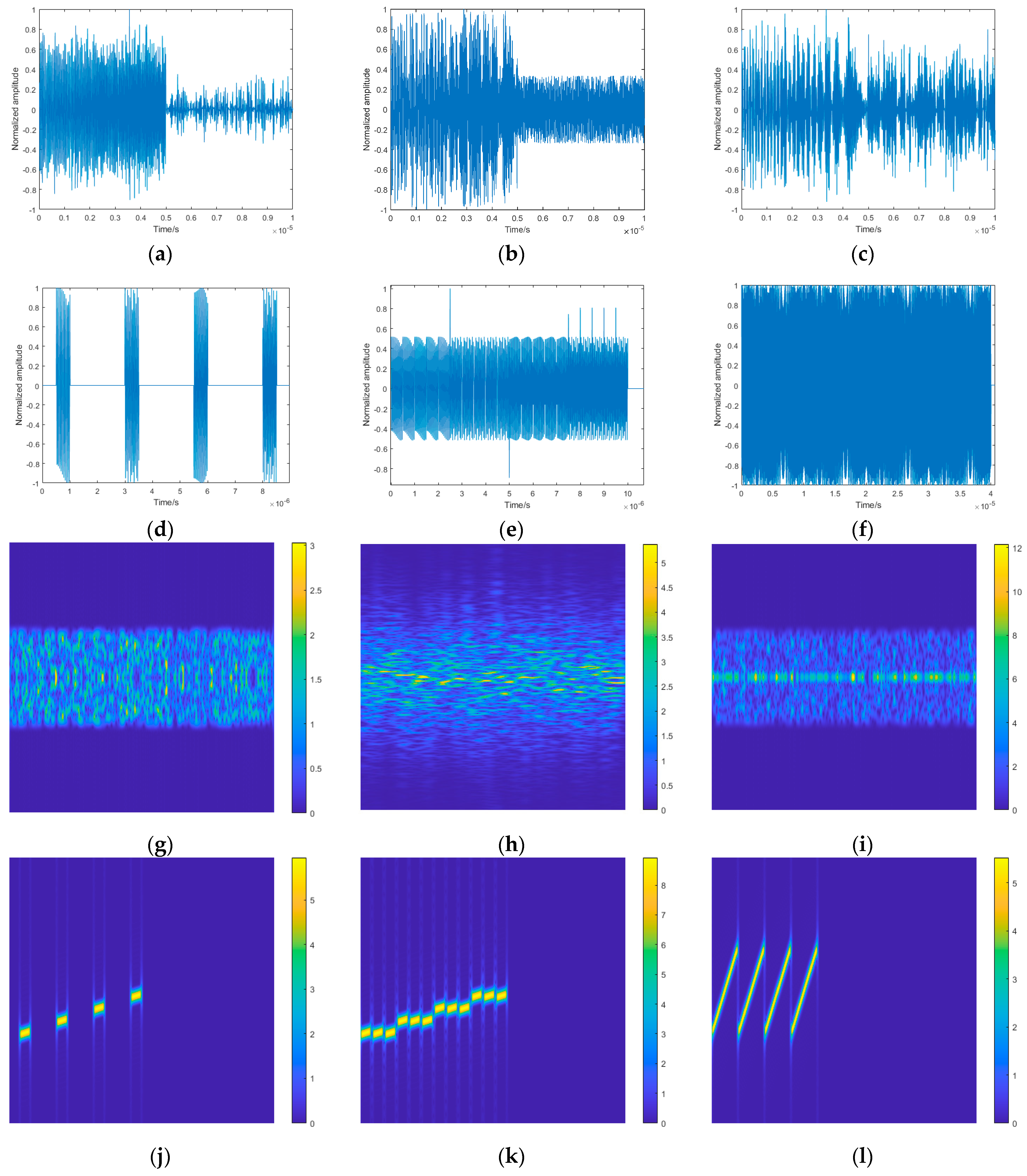
2.3. Time–Frequency Analysis
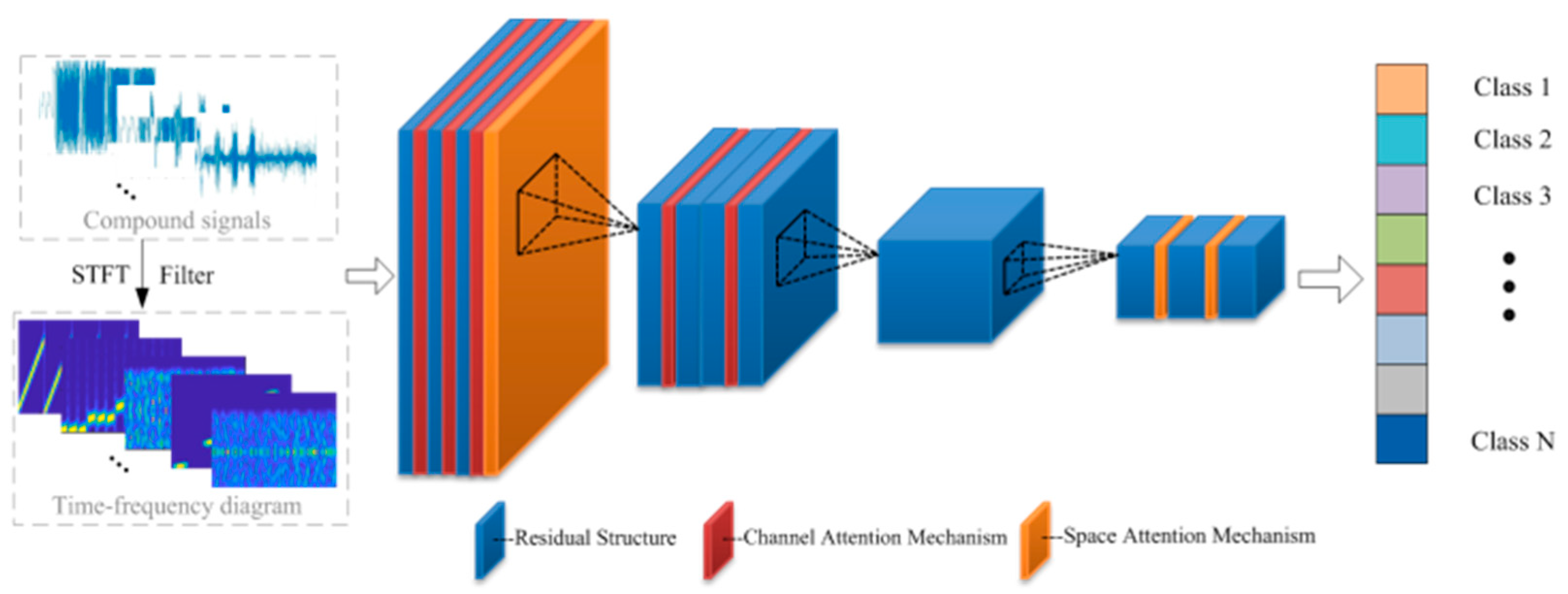
3. Proposed Approach
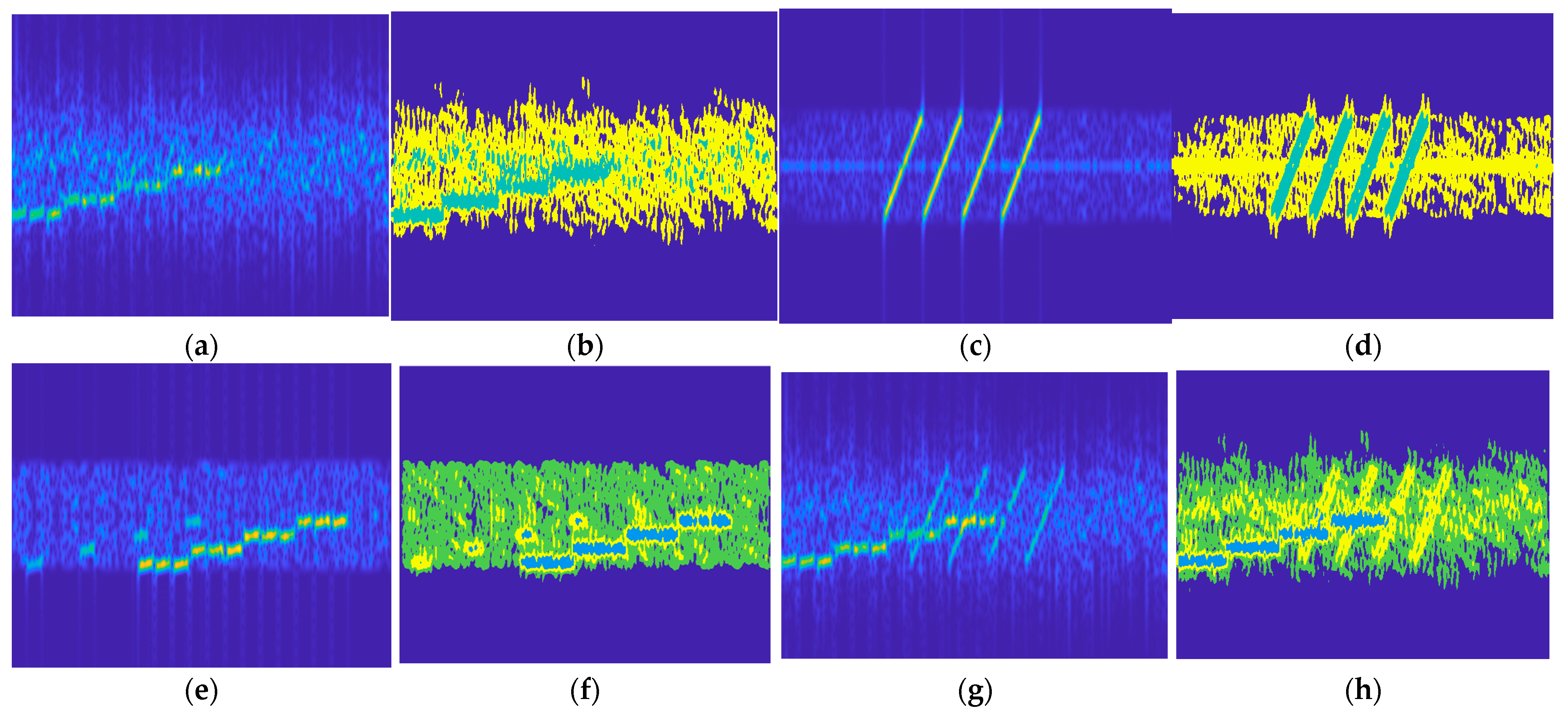
3.1. Compound Jamming Segmentation Module
3.2. Residual Network with Fused Attention Mechanism
3.3. Training Strategy and Optimization Algorithm
4. Experiment and Analysis
4.1. Datasets
4.2. Experimental Settings
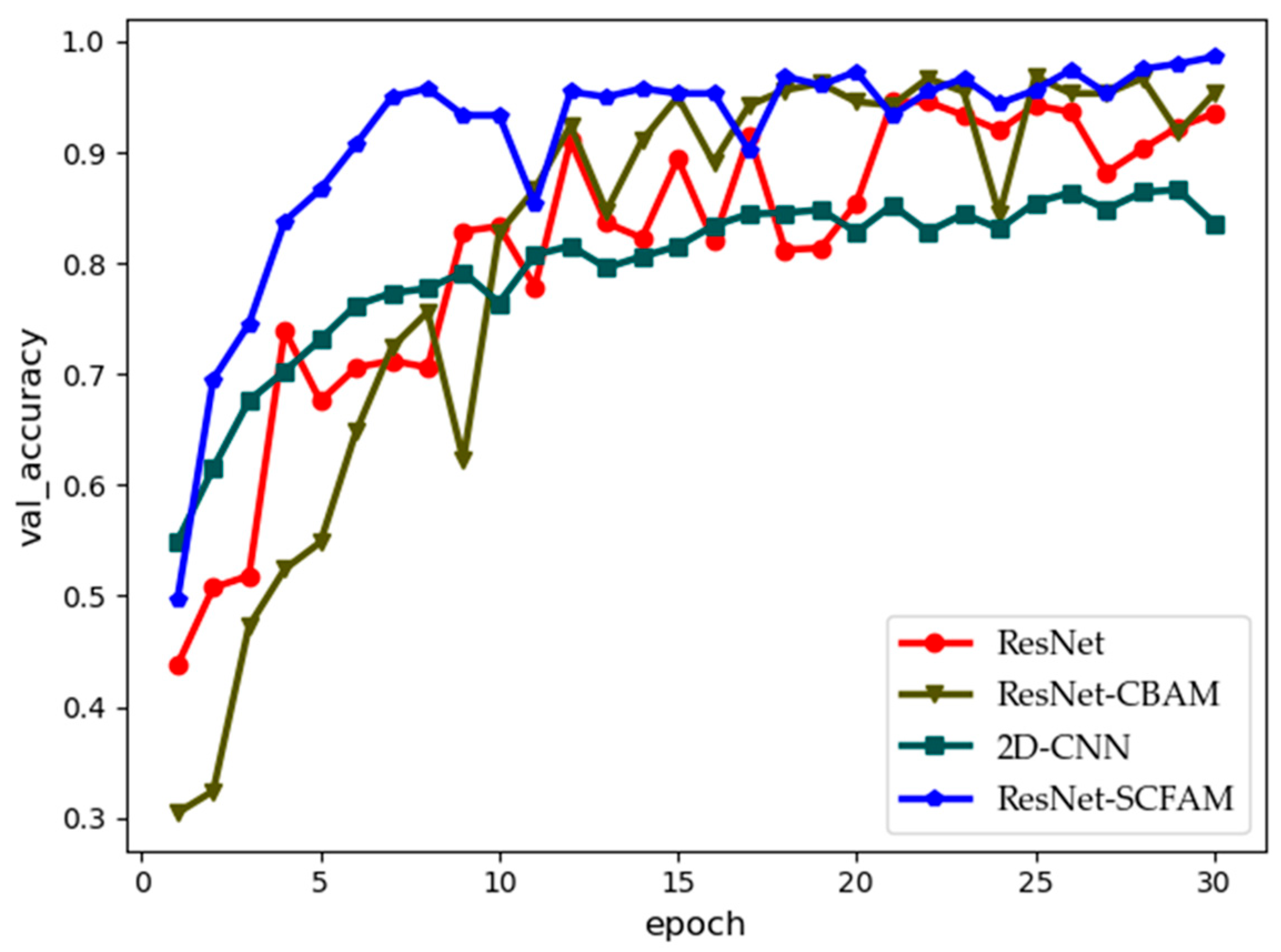
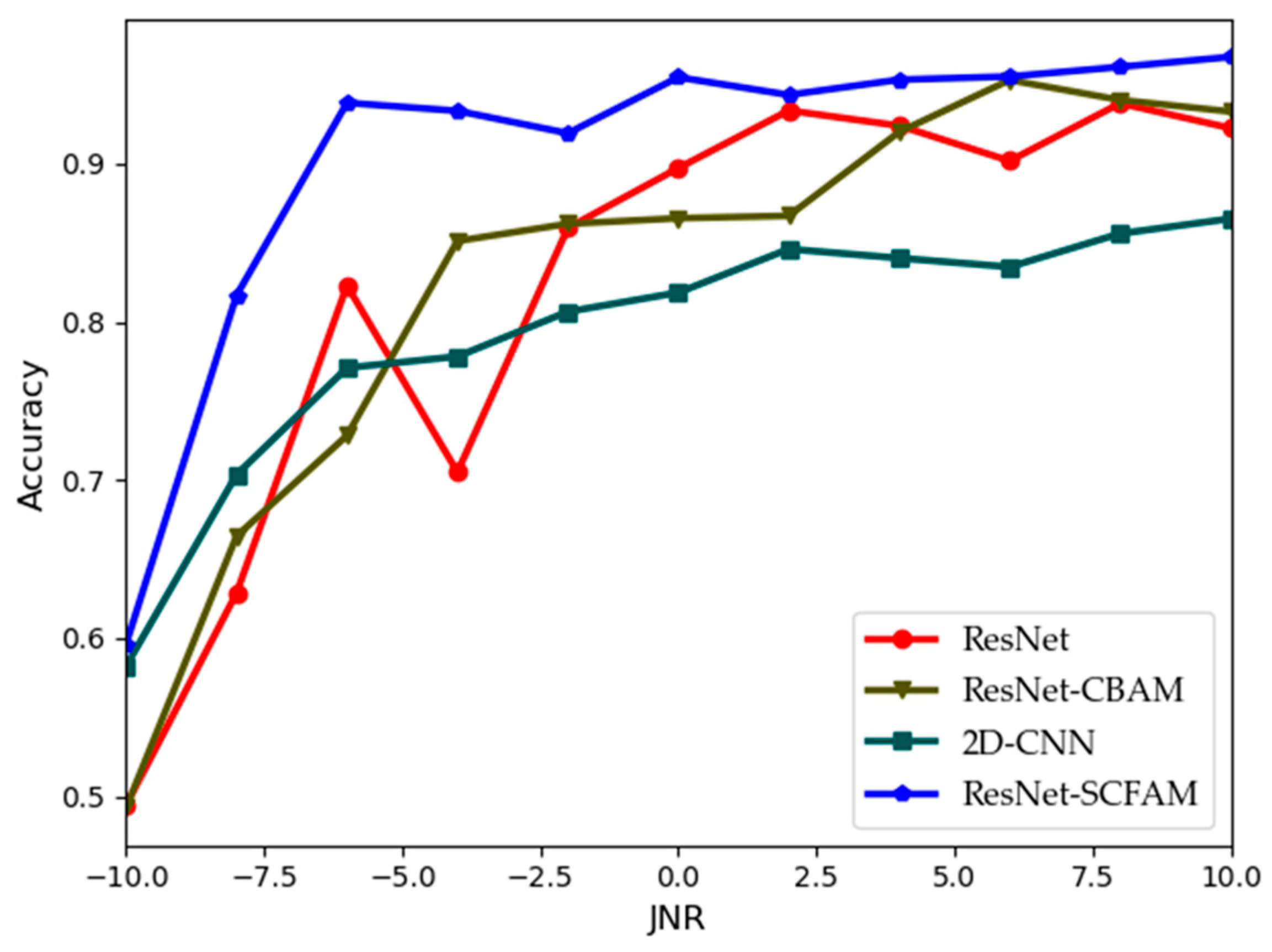
4.3. Results and Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Chen, F.; Li, R.; Ding, L. A method against DRFM dense false target jamming based on jamming recognization. In Proceedings of the IET International Radar Conference 2015, Hangzhou, China, 14–16 October 2015. [Google Scholar] [CrossRef]
- Zhou, Y.; Cao, R.; Zhang, A.; Li, P. Radio Signal Modulation Recognition Method Based on Hybrid Feature and Ensemble Learning: For Radar and Jamming Signals. Sensors 2024, 24, 4804. [Google Scholar] [CrossRef] [PubMed]
- Guo, X.; Su, J.; Zhu, N. Interference Suppression Algorithm Based on Short Time Fractional Fourier Transform. Sensors 2024, 24, 1785. [Google Scholar] [CrossRef] [PubMed]
- Zhou, H.; Wang, L.; Guo, Z. Recognition of Radar Compound Jamming Based on Convolutional Neural Network. IEEE Trans. Aerosp. Electron. Syst. 2023, 59, 7380–7394. [Google Scholar] [CrossRef]
- Qian, J.; Teng, X.; Qiu, Z. Recognition of radar deception jamming based on convolutional neural network. In Proceedings of the IET International Radar Conference, Online, 4–6 November 2020; pp. 913–918. [Google Scholar]
- Lv, Q.; Quan, Y.; Feng, W.; Sha, M.; Dong, S.; Xing, M. Radar deception jamming recognition based on weighted ensemble CNN with transfer learning. IEEE TANS. Geosci. Remote Sens. 2022, 60, 5107511. [Google Scholar] [CrossRef]
- Zhang, D.; Sun, J.; Yi, W.; Yang, C. Joint Jamming Beam and Power Scheduling for Suppressing Netted Radar System. In Proceedings of the 2021 IEEE Radar Conference (RadarConf21), Atlanta, GA, USA, 7–14 May 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, Y.; Huang, Y.; Chen, Z. Complicated Interference Identification via Machine Learning Methods. In Proceedings of the International Conference on Electronic Information and Communication Technology (ICEICT), Xi’an, China, 18–20 August 2021. [Google Scholar] [CrossRef]
- Zhu, T.B.; Zhang, G.; Li, Q. Radar active blanket jamming sorting based on resemblance coefficient cluster. In Proceedings of the 2013 IEEE International Conference on Signal Processing, Kunming, China, 5–8 August 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, J.; Bai, Z.; Hu, J.; Yang, Y.; Xian, Z.; Hao, X.; Kwak, K. Time-frequency Analysis and Convolutional Neural Network Based Fuze Jamming Signal Recognition. In Proceedings of the 2023 25th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 19–22 February 2023; pp. 277–282. [Google Scholar] [CrossRef]
- Song, Y.; Dong, G.; Wang, Z. A New Method for Joint Recognition and Location of Radar Jamming. In Proceedings of the IGARSS 2022—2022 IEEE International Geoscience and Remote Sensing Symposium, Kuala Lumpur, Malaysia, 17–22 July 2022; pp. 7587–7590. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhao, Z.; Bu, Y. Radar Active Jamming Recognition Under Open World Setting. Remote Sens. 2023, 15, 4107. [Google Scholar] [CrossRef]
- Zhou, Y.; Shang, S.; Song, X.; Zhang, S.; You, T.; Zhang, L. Intelligent Radar Jamming Recognition in Open Set Environment Based on Deep Learning Networks. Remote Sens. 2022, 14, 6220. [Google Scholar] [CrossRef]
- Zhang, M.; Chen, Y.; Zhang, Y. Weakly Supervised Transformer for Radar Jamming Recognition. Remote Sens. 2024, 16, 2541. [Google Scholar] [CrossRef]
- Kong, Y.; Wang, X.; Wu, C. Active Deception Jamming Recognition in the Presence of Extended Target. IEEE Geosci. Remote Sens. Lett. 2022, 19, 4024905. [Google Scholar] [CrossRef]
- Chen, H.; Chen, H.; Lei, Z.; Zhang, L.; Li, B.; Zhang, J.; Wang, Y. Compound Jamming Recognition Based on a Dual-Channel Neural Network and Feature Fusion. Remote Sens. 2024, 16, 1325. [Google Scholar] [CrossRef]
- Qu, Q.; Wei, S.; Liu, S.; Liang, J.; Shi, J. JRNet: Jamming Recognition Networks for Radar Compound Suppression Jamming Signals. IEEE Trans. Veh. Technol. 2020, 69, 15035–15045. [Google Scholar] [CrossRef]
- Zhou, H.P.; Wang, L.; Ma, M.H.; Guo, Z.Y. Compound radar jamming recognition based on signal source separation. Signal Process. 2024, 214, 109246. [Google Scholar] [CrossRef]

| Layer Name | Kernel Size | Stride | Padding | Activation Function | Down Sampling | Attention Mechanism |
|---|---|---|---|---|---|---|
| Conv1 | 7 × 7 | 2 | 3 | RELU | / | / |
| maxpool | 3 × 3 | 2 | 1 | / | / | / |
| layer1-block1 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | CAM |
| layer1-block2 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | CAM |
| layer1-block3 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | CAM, SAM |
| layer2-block1 | 3 × 3 (conv1, conv2) | 2 | 1 | RELU | Yes | CAM |
| layer2-block2 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | / |
| layer2-block3 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | CAM |
| layer2-block4 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | / |
| layer3-block1 | 3 × 3 (conv1, conv2) | 2 | 1 | RELU | Yes | / |
| layer3-block2,3,4,5,6 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | / |
| layer4-block1 | 3 × 3 (conv1, conv2) | 2 | 1 | RELU | Yes | SAM |
| layer4-block2 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | SAM |
| layer4-block3 | 3 × 3 (conv1, conv2) | 1 | 1 | RELU | / | / |
| Global Pooling Layer | Adaptive averaging pooling processing | |||||
| Fully Connected Layer | Number of trainable parameters: 512 × 6 | |||||
| Dataset | Jamming | Parameters | Value Range |
| Training and validation dataset | FM | Bandwidth | 10~20 MHz |
| Carrier frequency | 8~12 GHz | ||
| Frequency-modulation slope | 10~20 MHz/s | ||
| JNR | −10~10 dB | ||
| AM | Bandwidth | 10~20 MHz | |
| Carrier frequency | 8~12 GHz | ||
| JNR | −10~10 dB | ||
| RF | Bandwidth | 5~10 MHz | |
| Carrier frequency | 8~12 GHz | ||
| JNR | −10~10 dB | ||
| ISRJ | Sampling period | 4~10 us | |
| Sampling time | 1~5 us | ||
| JNR | −10~10 dB | ||
| CI | Number of sub-pulses | 2~8 | |
| Number of pulse-forwarding | 2~4 | ||
| JNR | −10~10 dB | ||
| SMSP | Bandwidth | 10~30 MHz | |
| Sampling multiple | 2~4 | ||
| JNR | −10~10 dB | ||
| FM + ISRJ | Same as corresponding jamming components | Same as corresponding jamming components | |
| AM + CI | |||
| RF + SMSP | |||
| ISRJ + CI | |||
| Test dataset | FM + CI | Same as corresponding jamming components | Same as corresponding jamming components |
| AM + SMSP | |||
| RF + ISRJ + CI | |||
| FM + CI + SMSP |
| Signal Processing Technique | Accuracy (%) | Processing Time (s) |
|---|---|---|
| Mel | 78.46 | 0.115 |
| CWT | 92.37 | 0.204 |
| STFT | 98.60 | 0.079 |
| Algorithms | OA (%) | Kappa (%) | Processing Time (s) | Response Time (s) |
|---|---|---|---|---|
| ResNet | 93.18 ± 0.09 | 92.48 ± 0.65 | 599.42 | 0.27 |
| ResNet-CBAM | 92.27 ± 0.42 | 91.61 ± 0.39 | 825.24 | 0.19 |
| 2D-CNN | 92.29 ± 1.39 | 91.09 ± 0.45 | 646.63 | 0.14 |
| ResNet-SCFAM | 98.60 ± 0.24 | 96.96 ± 0.60 | 534.82 | 0.15 |
| Compound Jamming | ResNet-SCFAM |
|---|---|
| FM + CI | 97.0% |
| AM + SMSP | 96.5% |
| RF + ISRJ + CI | 91.5% |
| FM + CI + SMSP | 92.5% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, P.; Yang, J.; Lin, J. Radar Compound Jamming Recognition Based on Image Segmentation and Fused Attention Residual Network. Sensors 2025, 25, 2124. https://doi.org/10.3390/s25072124
Li P, Yang J, Lin J. Radar Compound Jamming Recognition Based on Image Segmentation and Fused Attention Residual Network. Sensors. 2025; 25(7):2124. https://doi.org/10.3390/s25072124
Chicago/Turabian StyleLi, Peishan, Jian Yang, and Jiaao Lin. 2025. "Radar Compound Jamming Recognition Based on Image Segmentation and Fused Attention Residual Network" Sensors 25, no. 7: 2124. https://doi.org/10.3390/s25072124
APA StyleLi, P., Yang, J., & Lin, J. (2025). Radar Compound Jamming Recognition Based on Image Segmentation and Fused Attention Residual Network. Sensors, 25(7), 2124. https://doi.org/10.3390/s25072124






