Formal Modeling of IoT and Drone-Based Forest Fire Detection and Counteraction System
Abstract
:1. Introduction
2. Related Work
Failure Detection Review
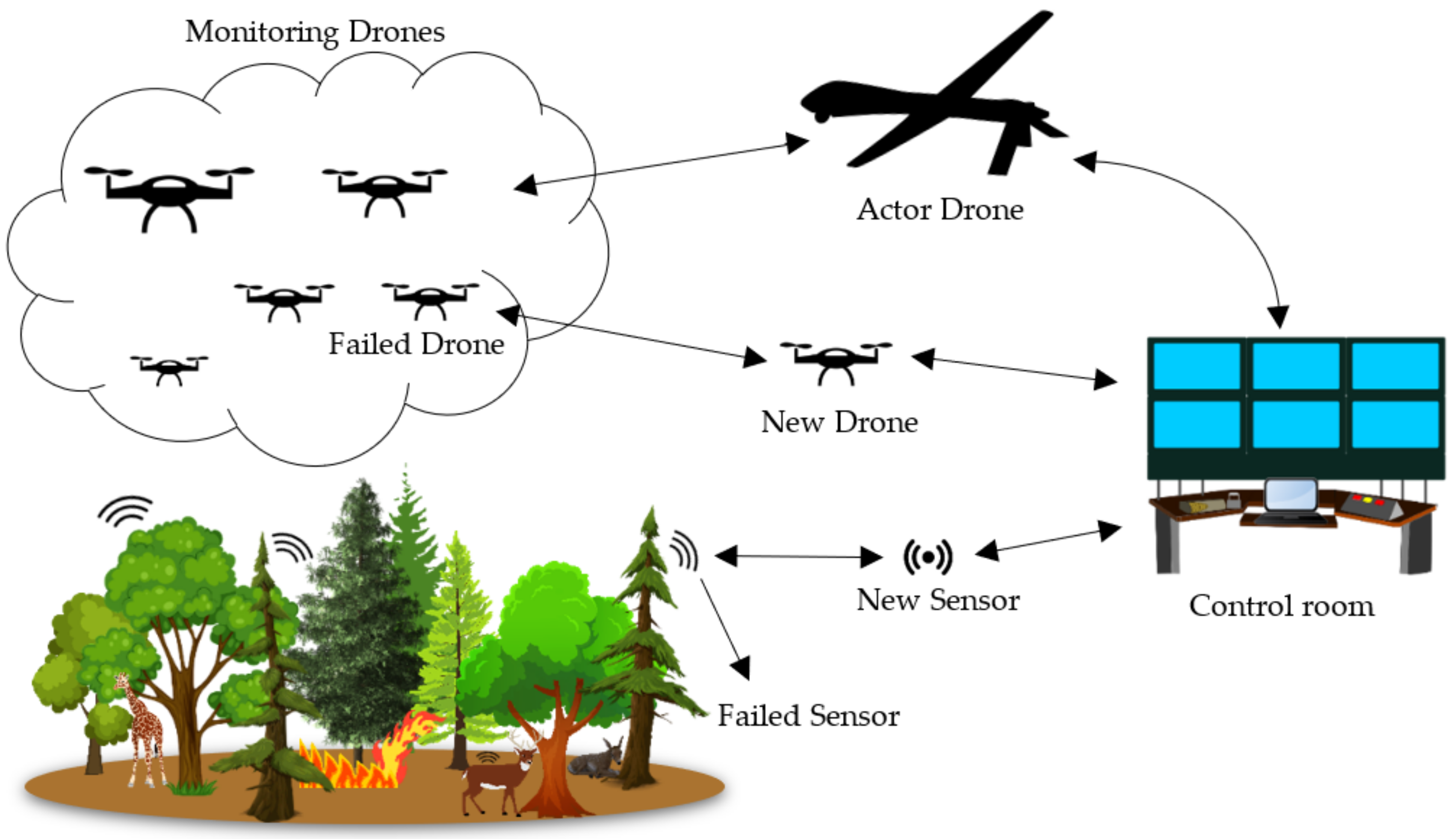
3. Problem Statement & System Model
3.1. Sequence Diagram
3.2. Graph-Based Model
4. Specifying Model Formally Using VDM-SL
4.1. Static Model



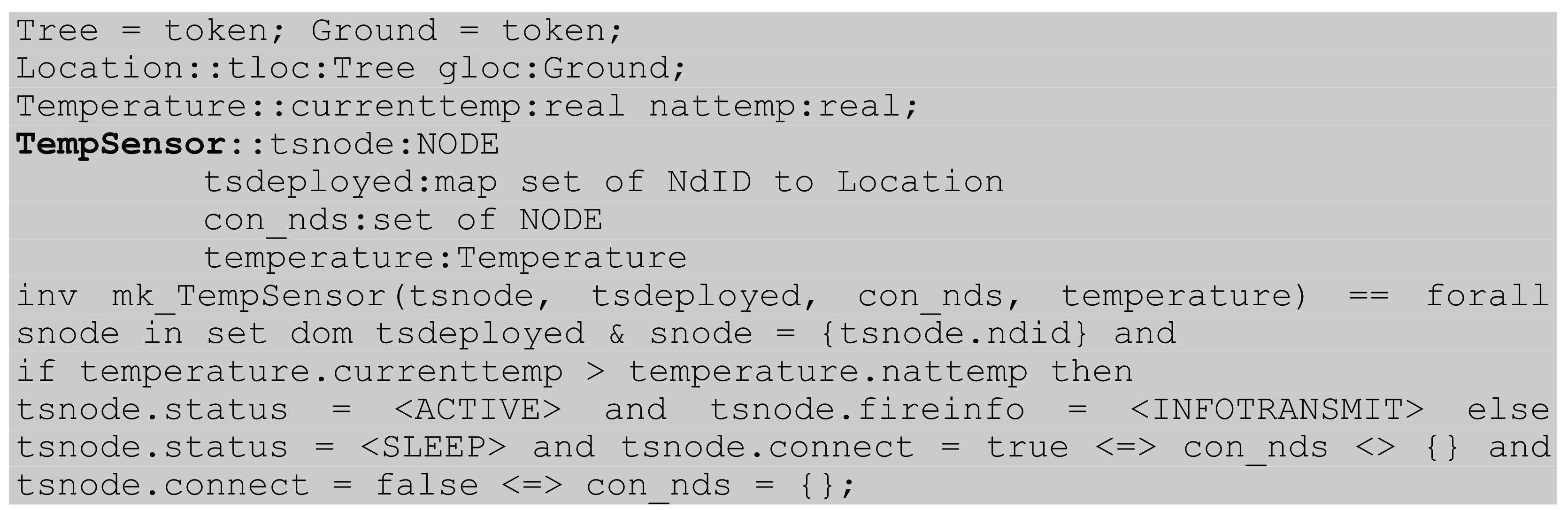










4.2. Dynamic Model








5. Failure Detection and Recovery
| Algorithm 1: Failure detection and recovery |
| NFDR(NT) |
| Network is deployed in the subnet mechanism which are connected to Control room nominated as |
| 1. For each subnet gateways are described as where i = 1, 2, …, k |
| 2. There exists |
| 3. If PathGWCR ( ) = True, Then |
| 4. Subnets are connected to Control Room Else disconnected |
| 5. Forall subnet , where i = 1, 2, …, k |
| 6. If PathSS ( {}) and PathSA ({}) = True, then |
| 7. Nodes are connected in Subnets Else disconnected |
| 8. Forall Nodes N in subnet |
| 9. Crucial(N)= False |
| 10. If subnet is distributed without any N, then |
| 11. Crucial(N)= True |
| 12. EndIf |
| 13. If (sensor S fails) Then |
| 14. Replaced(S) |
| 15. Else If (Alarm A fails) Then |
| 16. Replaced(A) |
| 17. Else If (Gateway GW fails) Then |
| 18. Replaced (GW) |
| 19. EndIf |
| 20. Forall Drones where i = 1, 2, …, k |
| 21. If PathDD () and PathDCR ({}) = True, then |
| 22. Drones are connected to control room Else not connected |
| 23. Forall drones D |
| 24. Crucial(D)= False |
| 25. If network is distributed without D, then |
| 26. Crucial(D)= True |
| 27. EndIf |
| 28. If (Drone D fails) = true, then |
| 29. Replaced(D) |
| 30. EndIf |
6. Formal Modeling of Failure Detection Algorithm
6.1. Static Model








6.2. Dynamic Model












7. Analysis Model
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Talavera, J.M.; Tobon, L.; Gómez, J.A.; Culman, M.; Aranda, J.; Parra, D.T.; Quiroz, L.A.; Hoyos, A.; Garreta, L.E. Review of IoT applications in agro-industrial and environmental fields. Comput. Electron. Agric. 2017, 142, 283–297. [Google Scholar] [CrossRef]
- Neumann, G.B.; de Almeida, V.P.; Endler, M. Smart Forests: Fire detection service. In Proceedings of the 2018 IEEE Symposium on computers and communications (ISCC), Natal, Brazil, 25–28 June 2018. [Google Scholar]
- Jayaram, K.; Janani, K.; Jeyaguru, R.; Kumaresh, R.; Muralidharan, N. Forest Fire Alerting System With GPS Co-ordinates Using IoT. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), Coimbatore, India, 15–16 March 2019. [Google Scholar]
- Pareek, S.; Shrivastava, S.; Jhala, S.; Siddiqui, J.A.; Patidar, S. IoT and Image Processing based Forest Monitoring and Counteracting System. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI) (48184), Tirunelveli, India, 15–17 June 2020. [Google Scholar]
- Cui, F. Deployment and integration of smart sensors with IoT devices detecting fire disasters in huge forest environment. Comput. Commun. 2019, 150, 818–827. [Google Scholar] [CrossRef]
- Sharma, A.; Singh, P.K.; Kumar, Y. An integrated fire detection system using IoT and image processing technique for smart cities. Sustain. Cities Soc. 2020, 61, 102332. [Google Scholar] [CrossRef]
- Varela, N.; Jorge, L.D.-M.; Ospino, A.; Zelaya, N.A.L. Wireless sensor network for forest fire detection. Procedia Comput. Sci. 2020, 175, 435–440. [Google Scholar] [CrossRef]
- Yuan, C.; Liu, Z.; Zhang, Y. Fire detection using infrared images for UAV-based forest fire surveillance. In Proceedings of the 2017 International Conference on Unmanned Aircraft Systems (ICUAS), Miami, FL, USA, 13–16 June 2017. [Google Scholar]
- Tehseen, A.; Zafar, N.A.; Ali, T. Graph Theory-Based Formal Modeling of Forest Fire Management System using IoT and Drone. In Proceedings of the 2021 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 21–22 September 2021. [Google Scholar]
- Stahlke, D. Quantum Zero-Error Source-Channel Coding and Non-Commutative Graph Theory. IEEE Trans. Inf. Theory 2015, 62, 554–577. [Google Scholar] [CrossRef] [Green Version]
- Afzaal, H.; Zafar, N.A. Formalism of network restructuring in flood control system. In Proceedings of the 2017 International Conference on Innovations in Electrical Engineering and Computational Technologies (ICIEECT), Karachi, Pakistan, 5–7 April 2017. [Google Scholar]
- Jameel, F.; Zafar, N.A.; Tehseen, A. Formal Specification Ensuring Security at Entrance and Exit of Smart Parking System. In Proceedings of the 2021 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 21–22 September 2021. [Google Scholar]
- Jameel, F.; Zafar, N.A. Formal Modeling and Automation of E-Payment Smart Parking System. In Proceedings of the 2021 International Conference on Digital Futures and Transformative Technologies (ICoDT2), Islamabad, Pakistan, 20–21 May 2021. [Google Scholar]
- Iqbal, M.; Zafar, N.A.; Alkhammash, E.H. Formally Identifying COVID-19 Patients for Providing Medical Services using Drones. In Proceedings of the 2021 International Conference of Women in Data Science at Taif University (WiDSTaif), Virtual, 30–31 March 2021. [Google Scholar]
- Nawaz, A.; Zafar, N.A.; Alkhammash, E.H. Formal Modeling of Responsive Traffic Signaling System Using Graph Theory and VDM-SL. Sustainability 2021, 13, 11772. [Google Scholar] [CrossRef]
- Al_Janabi, S.; Al_Shourbaji, I.; Salman, M.A. Assessing the suitability of soft computing approaches for forest fires prediction. Appl. Comput. Inform. 2018, 14, 214–224. [Google Scholar] [CrossRef]
- Garcia-Jimenez, S.; Jurio, A.; Pagola, M.; De Miguel, L.; Barrenechea, E.; Bustince, H. Forest fire detection: A fuzzy system approach based on overlap indices. Appl. Soft Comput. 2017, 52, 834–842. [Google Scholar] [CrossRef]
- Zhao, Y.; Li, Q.; Gu, Z. Early smoke detection of forest fire video using CS Adaboost algorithm. Opt. Int. J. Light Electron Opt. 2015, 126, 2121–2124. [Google Scholar] [CrossRef]
- Prema, C.E.; Vinsley, S.S.; Suresh, S. Efficient Flame Detection Based on Static and Dynamic Texture Analysis in Forest Fire Detection. Fire Technol. 2018, 54, 255–288. [Google Scholar] [CrossRef]
- Aslan, Y.E.; Korpeoglu, I.; Ulusoy, Ö. A framework for use of wireless sensor networks in forest fire detection and monitoring. Comput. Environ. Urban Syst. 2012, 36, 614–625. [Google Scholar]
- Han, X.-F.; Jin, J.S.; Wang, M.-J.; Jiang, W.; Gao, L.; Xiao, L.-P. Video fire detection based on Gaussian Mixture Model and multi-color features. Signal Image Video Process. 2017, 11, 1419–1425. [Google Scholar]
- Merino, L.; Caballero, F.; Martínez-De-Dios, J.R.; Maza, I.; Ollero, A. An Unmanned Aircraft System for Automatic Forest Fire Monitoring and Measurement. J. Intell. Robot. Syst. 2012, 65, 533–548. [Google Scholar] [CrossRef]
- Kong, S.G.; Jin, D.; Li, S.; Kim, H. Fast fire flame detection in surveillance video using logistic regression and temporal smoothing. Fire Saf. J. 2016, 79, 37–43. [Google Scholar] [CrossRef]
- Yuan, C.; Liu, Z.; Zhang, Y. Aerial Images-Based Forest Fire Detection for Firefighting Using Optical Remote Sensing Techniques and Unmanned Aerial Vehicles. J. Intell. Robot. Syst. 2017, 88, 635–654. [Google Scholar] [CrossRef]
- Pan, H.; Badawi, D.; Zhang, X.; Cetin, A.E. Additive neural network for forest fire detection. Signal Image Video Process. 2019, 14, 675–682. [Google Scholar] [CrossRef]
- Muhammad, K.; Khan, S.; Elhoseny, M.; Ahmed, S.H.; Baik, S.W. Efficient Fire Detection for Uncertain Surveillance Environment. IEEE Trans. Ind. Inform. 2019, 15, 3113–3122. [Google Scholar] [CrossRef]
- Muhammad, K.; Ahmad, J.; Lv, Z.; Bellavista, P.; Yang, P.; Baik, S.W. Efficient Deep CNN-Based Fire Detection and Localization in Video Surveillance Applications. IEEE Trans. Syst. Man Cybern. Syst. 2018, 49, 1419–1434. [Google Scholar] [CrossRef]
- Allauddin, M.S.; Kiran, G.S.; Kiran, G.R.; Srinivas, G.; Mouli GU, R.; Prasad, P.V. Development of a Surveillance System for Forest Fire Detection and Monitoring using Drones. In Proceedings of the IGARSS 2019—2019 IEEE International Geoscience and Remote Sensing Symposium, Yokohama, Japan, 28 July–2 August 2019. [Google Scholar]
- Antunes, M.; Ferreira, L.M.; Viegas, C.; Coimbra, A.P.; de Almeida, A.T. Low-Cost System for Early Detection and Deployment of Countermeasures Against Wild Fires. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019. [Google Scholar]
- Divya, A.; Kavithanjali, T.; Dharshini, P. IoT enabled forest fire detection and early warning system. In Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 29–30 March 2019. [Google Scholar]
- Yang, S.; Lupascu, M.; Meel, K.S. Predicting Forest Fire Using Remote Sensing Data And Machine Learning. arXiv Preprint 2021, arXiv:2101.01975. [Google Scholar]
- Díaz-Ramírez, A.; Tafoya, L.A.; Atempa, J.A.; Mejía-Alvarez, P. Wireless Sensor Networks and Fusion Information Methods for Forest Fire Detection. Procedia Technol. 2012, 3, 69–79. [Google Scholar] [CrossRef]
- Liu, Y.; Gu, Y.; Chen, G.; Ji, Y.; Li, J. A novel accurate forest fire detection system using wireless sensor networks. In Proceedings of the 2011 Seventh International Conference on Mobile Ad-hoc and Sensor Networks, Beijing, China, 16–18 December 2011. [Google Scholar]
- Di Biase, V.; Laneve, G. Geostationary Sensor Based Forest Fire Detection and Monitoring: An Improved Version of the SFIDE Algorithm. Remote Sens. 2018, 10, 741. [Google Scholar] [CrossRef] [Green Version]
- Cruz, H.; Eckert, M.; Meneses, J.M.; Martínez, J.-F. Efficient Forest Fire Detection Index for Application in Unmanned Aerial Systems (UASs). Sensors 2016, 16, 893. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Afzaal, H.; Zafar, N.A. Formal analysis of subnet-based failure recovery algorithm in wireless sensor and actor and network. Complex Adapt. Syst. Model. 2016, 4, 27. [Google Scholar] [CrossRef] [Green Version]
- Imran, M.; Zafar, N.A. Formal Specification and Validation of a Hybrid Connectivity Restoration Algorithm for Wireless Sensor and Actor Networks. Sensors 2012, 12, 11754–11781. [Google Scholar] [CrossRef] [Green Version]
- Afzaal, H.; Zafar, N.A.; Alhumaidan, F. Hybrid subnet-based node failure recovery formal procedure in wireless sensor and actor networks. Int. J. Distrib. Sens. Networks 2017, 13, 1550147717704417. [Google Scholar] [CrossRef]
- Younis, M.; Senturk, I.; Akkaya, K.; Lee, S.; Senel, F. Topology management techniques for tolerating node failures in wireless sensor networks: A survey. Comput. Networks 2014, 58, 254–283. [Google Scholar] [CrossRef]
- Akkaya, K.; Senel, F.; Thimmapuram, A.; Uludag, S. Distributed Recovery from Network Partitioning in Movable Sensor/Actor Networks via Controlled Mobility. IEEE Trans. Comput. 2009, 59, 258–271. [Google Scholar] [CrossRef]
- Abbasi, A.; Younis, M.; Baroudi, U. Restoring connectivity in wireless sensor-actor networks with minimal topology changes. In Proceedings of the 2010 IEEE International Conference on Communications, Capetown, South Africa, 23–27 May 2010. [Google Scholar]
- Imran, M.; Said, A.M.; Younis, M.; Hasbullah, H. Application-centric connectivity restoration algorithm for wireless sensor and actor networks. In International Conference on Grid and Pervasive Computing; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Afzaal, H.; Zafar, N.A. Formal modeling and algorithm of subnet-based backup assigning in WSAN. In Proceedings of the 2015 International Conference on Information and Communication Technologies (ICICT), Karachi, Pakistan, 12–13 December 2015. [Google Scholar]
- Sudhakar, S.; Vijayakumar, V.; Kumar, C.S.; Priya, V.; Ravi, L.; Subramaniyaswamy, V. Unmanned Aerial Vehicle (UAV) based Forest Fire Detection and monitoring for reducing false alarms in forest-fires. Comput. Commun. 2019, 149, 1–16. [Google Scholar] [CrossRef]
- Afzaal, H.; Zafar, N.A. Robot-based forest fire detection and extinguishing model. In Proceedings of the 2016 2nd International Conference on Robotics and Artificial Intelligence (ICRAI), Islamabad, Pakistan, 1–2 November 2016. [Google Scholar]
- Radanliev, P.; De Roure, D. Review of algorithms for artificial intelligence on low memory devices. IEEE Access 2021, 9, 109986–109993. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Burnap, P.; Santos, O. Epistemological Equation for Analysing Uncontrollable States in Complex Systems: Quantifying Cyber Risks from the Internet of Things. Rev. Socionetwork Strat. 2021, 15, 381–411. [Google Scholar] [CrossRef]




| References | Description | Limitations |
|---|---|---|
| [44] | The study focused on effective fire detection and proposed some algorithms to apply them on UAVs for the reduction of false alarms. Using these techniques, color identification, Smoke Motion Recognition, Fire Classification algorithms, and the helicopters cameras in them for visualization. | Using only drones for fire detection can be expensive, there is no mechanism in place to deal with drone failure and the system is not formalized. |
| [45] | A neural network has been trained in this research to conduct forest fire predictions. To predict fire hotspots, this system uses readily available remotely-sensed information in the type of satellite pictures. | This system uses satellite images for fire prediction that can cause late detection of fire. Further, there is no formalization for this system. |
| [46] | An algorithm named FFDEA has been presented using WSAN for the detection of forest fire and extinguishment system. Temperature sensors are used to detect fire and to combat the fire; robots, as actors, are utilized. This system is formalized using VDM-SL. | In this system, just a temperature sensor is utilized, which is ineffective for precise fire detection and increases the false alert rate. In addition, there is no mechanism for confirmation of fire and no network maintenance available. |
| Specification | Syntax Check | Type Check | Integrity Check | C++ | Pretty Printer |
|---|---|---|---|---|---|
| Static Model | ✓ | ✓ | ✓ | ✓ | ✓ |
| state FFDetection | ✓ | ✓ | ✓ | ✓ | ✓ |
| ForestFireDetected | ✓ | ✓ | ✓ | ✓ | ✓ |
| InfoTransmisstion | ✓ | ✓ | ✓ | ✓ | ✓ |
| ReportToControlRoom | ✓ | ✓ | ✓ | ✓ | ✓ |
| IssueMonOrder | ✓ | ✓ | ✓ | ✓ | ✓ |
| Monreport | ✓ | ✓ | ✓ | ✓ | ✓ |
| CROrderforAction | ✓ | ✓ | ✓ | ✓ | ✓ |
| PerformingAction | ✓ | ✓ | ✓ | ✓ | ✓ |
| Reportback | ✓ | ✓ | ✓ | ✓ | ✓ |
| Specification | Syntax Check | Type Check | Integrity Check | C++ | Pretty Printer |
|---|---|---|---|---|---|
| Static Model | ✓ | ✓ | ✓ | ✓ | ✓ |
| state IOTN | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathSS | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathSAL | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathSGW | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathALGW | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathGWCR | ✓ | ✓ | ✓ | ✓ | ✓ |
| PathDCR | ✓ | ✓ | ✓ | ✓ | ✓ |
| FailureOfSensor | ✓ | ✓ | ✓ | ✓ | ✓ |
| FailureOfAlarm | ✓ | ✓ | ✓ | ✓ | ✓ |
| FailureOfDrone | ✓ | ✓ | ✓ | ✓ | ✓ |
| FailureOfGateway | ✓ | ✓ | ✓ | ✓ | ✓ |
| ReplacementOfNodes | ✓ | ✓ | ✓ | ✓ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tehseen, A.; Zafar, N.A.; Ali, T.; Jameel, F.; Alkhammash, E.H. Formal Modeling of IoT and Drone-Based Forest Fire Detection and Counteraction System. Electronics 2022, 11, 128. https://doi.org/10.3390/electronics11010128
Tehseen A, Zafar NA, Ali T, Jameel F, Alkhammash EH. Formal Modeling of IoT and Drone-Based Forest Fire Detection and Counteraction System. Electronics. 2022; 11(1):128. https://doi.org/10.3390/electronics11010128
Chicago/Turabian StyleTehseen, Aqsa, Nazir Ahmad Zafar, Tariq Ali, Fatima Jameel, and Eman H. Alkhammash. 2022. "Formal Modeling of IoT and Drone-Based Forest Fire Detection and Counteraction System" Electronics 11, no. 1: 128. https://doi.org/10.3390/electronics11010128






