A Comprehensive Survey on Security and Privacy for Electronic Health Data
Abstract
:1. Introduction
- A comprehensive survey on the security and privacy issues for e-health data, medical devices, medical networks, edge, fog, and cloud computing;
- Identification and taxonomies of the security concerns, security requirements, and security solutions for e-health data, medical devices, medical networks, and edge/fog/cloud computing;
- Analysis and identification of the strengths and weaknesses of the surveyed studies;
- Identification of the research trends and open challenges for each component (i.e., e-health data, medical devices, medical networks, edge, fog, and cloud computing) of e-health systems.
2. Background
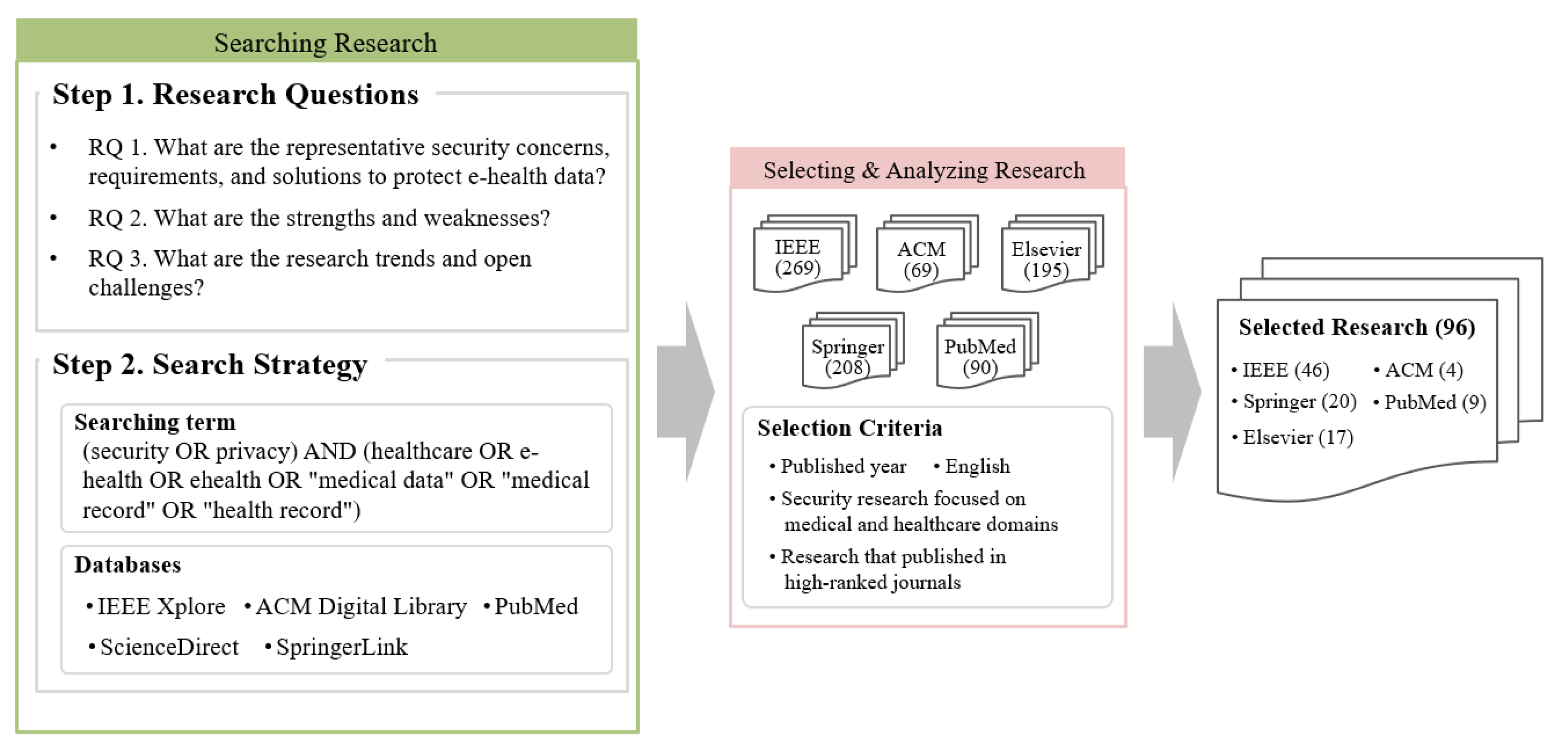
2.1. Method
- RQ 1: What are the representative security concerns, requirements, and solutions to protect e-health data for each target domain?
- RQ 2: What are the strengths and weaknesses of the surveyed studies for each target domain?
- RQ 3: What are the research trends and open challenges for each target domain?
- SC 1: Studies must have been published within five years;
- SC 2: Studies must use English;
- SC 3: Studies must focus on medical or healthcare domains. There were various security and privacy studies in diverse environments such as Internet of Things (IoT), edge, fog, and cloud; however, we excluded studies that did not focus on the medical or healthcare domains;
- SC 4: Studies must focus on technical research. we excluded some studies regarding medical policies, social sciences, etc.;
- SC 5: Journals should be ranked top 15% in Journal Citation Reports (JCR). If journals were not ranked in the JCR, it should have around 0.8 or higher SCImago Journal Rank (SJR). However, medical journals were selected even if they were ranked around the top 50% in JCR or had 0.4 or higher SJR because of their expertise.
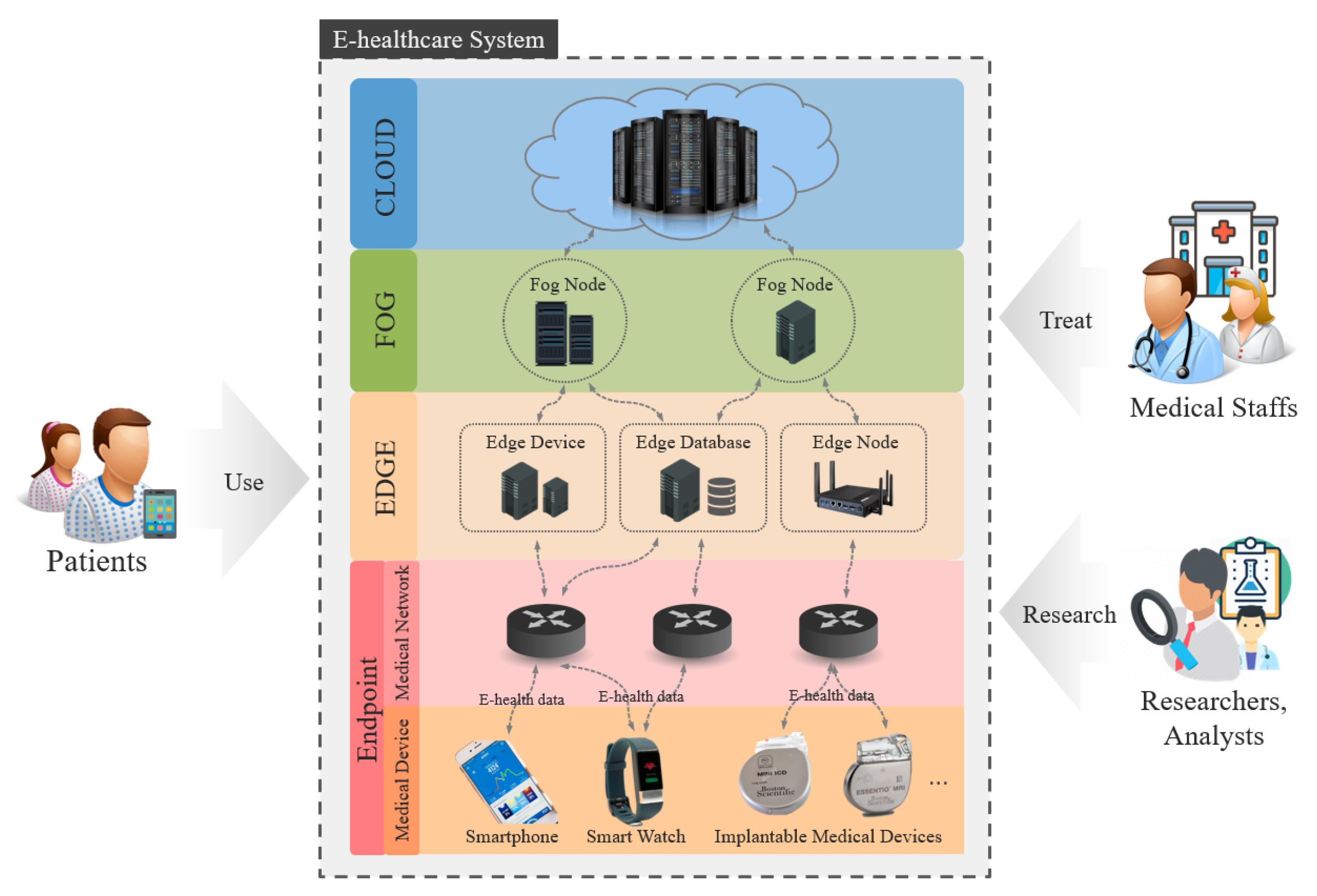
2.2. Target Domain
2.3. Related Work
3. E-Health Data
3.1. Overview
3.2. Security Concern, Requirement, and Solution
3.2.1. Security Concern
3.2.2. Security Requirement
3.2.3. Security Solution
4. Medical Device
4.1. Overview
4.2. Security Concern, Requirement, and Solution
4.2.1. Security Concern
4.2.2. Security Requirement
4.2.3. Security Solution
5. Medical Network
5.1. Overview
5.2. Security Concern, Requirement, and Solution
5.2.1. Security Concerns
5.2.2. Security Requirements
5.2.3. Security Solution
6. Edge, Fog, and Cloud
6.1. Overview
6.2. Security Concern, Requirement, and Solution
6.2.1. Security Concern
6.2.2. Security Requirement
6.2.3. Security Solution
7. Research Trend and Open Challenge
7.1. E-Health Data
7.2. Medical Device
7.3. Medical Network
7.4. Edge, Fog, and Cloud
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- HIPPA. Available online: https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html (accessed on 5 July 2021).
- GDPR. Available online: https://gdpr-info.eu/ (accessed on 5 July 2021).
- Yaqoob, T.; Abbas, H.; Atiquzzaman, M. Security vulnerabilities, attacks, countermeasures, and regulations of networked medical devices—A review. IEEE Commun. Surv. Tutor. 2019, 21, 3723–3768. [Google Scholar] [CrossRef]
- Available online: https://healthitsecurity.com/news/the-10-biggest-healthcare-data-breaches-of-2020-so-far (accessed on 5 July 2021).
- Kruse, C.S.; Smith, B.; Vanderlinden, H.; Nealand, A. Security techniques for the electronic health records. J. Med. Syst. 2017, 41, 127. [Google Scholar] [CrossRef] [Green Version]
- Abouelmehdi, K.; Beni-Hessane, A.; Khaloufi, H. Big healthcare data: Preserving security and privacy. J. Big Data 2018, 5, 1. [Google Scholar] [CrossRef]
- Chen, Y. Ensuring privacy and security of genomic data and functionalities. Brief. Bioinform. 2019, 21, 511–526. [Google Scholar]
- Aziz, M.M.A.; Sadat, M.N.; Alhadidi, D.; Wang, S.; Jiang, X.; Brown, C.L.; Mohammed, N. Privacy-preserving techniques of genomic data—A survey. Brief. Bioinform. 2019, 20, 887–895. [Google Scholar] [CrossRef] [PubMed]
- Zheng, G.; Shankaran, R.; Orgun, M.A.; Qiao, L.; Saleem, K. Ideas and challenges for securing wireless implantable medical devices: A review. IEEE Sens. J. 2016, 17, 562–576. [Google Scholar] [CrossRef]
- Wu, L.; Du, X.; Guizani, M.; Mohamed, A. Access control schemes for implantable medical devices: A survey. IEEE Internet Things J. 2017, 4, 1272–1283. [Google Scholar] [CrossRef]
- Kintzlinger, M.; Nissim, N. Keep an eye on your personal belongings! The security of personal medical devices and their ecosystems. J. Biomed. Inform. 2019, 95, 103233. [Google Scholar] [CrossRef]
- AlTawy, R.; Youssef, A.M. Security tradeoffs in cyber physical systems: A case study survey on implantable medical devices. IEEE Access 2016, 4, 959–979. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, M.; Noura, H.N.; Salman, O.; Yaacoub, E.; Couturier, R.; Chehab, A. Securing internet of medical things systems: Limitations, issues and recommendations. Future Gener. Comput. Syst. 2020, 105, 581–606. [Google Scholar] [CrossRef]
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems: A survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Chenthara, S.; Ahmed, K.; Wang, H.; Whittaker, F. Security and privacy-preserving challenges of e-health solutions in cloud computing. IEEE Access 2019, 7, 74361–74382. [Google Scholar] [CrossRef]
- Yüksel, B.; Küpçü, A.; Özkasap, Ö. Research issues for privacy and security of electronic health services. Future Gener. Comput. Syst. 2017, 68, 1–13. [Google Scholar] [CrossRef]
- Wazid, M.; Zeadally, S.; Das, A.K.; Odelu, V. Analysis of security protocols for mobile healthcare. J. Med. Syst. 2016, 40, 229. [Google Scholar] [CrossRef] [PubMed]
- Razaque, A.; Amsaad, F.; Khan, M.J.; Hariri, S.; Chen, S.; Siting, C.; Ji, X. Survey: Cybersecurity vulnerabilities, attacks and solutions in the medical domain. IEEE Access 2019, 7, 168774–168797. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Amato, F.; Casola, V.; Cozzolino, G.; De Benedictis, A.; Mazzocca, N.; Moscato, F. A Security and Privacy Validation Methodology for e-Health Systems. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2021, 17, 67. [Google Scholar]
- Dankar, F.K.; Badji, R. A risk-based framework for biomedical data sharing. J. Biomed. Inform. 2017, 66, 231–240. [Google Scholar] [CrossRef]
- Rajput, A.R.; Li, Q.; Ahvanooey, M.T.; Masood, I. EACMS: Emergency access control management system for personal health record based on blockchain. IEEE Access 2019, 7, 84304–84317. [Google Scholar] [CrossRef]
- Shahnaz, A.; Qamar, U.; Khalid, A. Using blockchain for electronic health records. IEEE Access 2019, 7, 147782–147795. [Google Scholar] [CrossRef]
- Xu, J.; Xue, K.; Li, S.; Tian, H.; Hong, J.; Hong, P.; Yu, N. Healthchain: A blockchain-based privacy preserving scheme for large-scale health data. IEEE Internet Things J. 2019, 6, 8770–8781. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. Reijndael: The Advanced Encryption Standard. Dr. Dobb’S J. Softw. Tools Prof. Program. 2001, 26, 137–139. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Elhoseny, M.; Ramírez-González, G.; Abu-Elnasr, O.M.; Shawkat, S.A.; Arunkumar, N.; Farouk, A. Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 2018, 6, 20596–20608. [Google Scholar] [CrossRef]
- Dzwonkowski, M.; Papaj, M.; Rykaczewski, R. A new quaternion-based encryption method for DICOM images. IEEE Trans. Image Process. 2015, 24, 4614–4622. [Google Scholar] [CrossRef] [PubMed]
- Parvees, M.M.; Samath, J.A.; Bose, B.P. Secured medical images-a chaotic pixel scrambling approach. J. Med. Syst. 2016, 40, 232. [Google Scholar] [CrossRef] [PubMed]
- Sei, Y.; Okumura, H.; Takenouchi, T.; Ohsuga, A. Anonymization of sensitive quasi-identifiers for l-diversity and t-closeness. IEEE Trans. Dependable Secur. Comput. 2017, 16, 580–593. [Google Scholar] [CrossRef]
- Sweeney, L. k-anonymity: A model for protecting privacy’International Journal on Uncertainty. Fuzziness Knowl.-Based Syst. 2002, 10, 557–570. [Google Scholar] [CrossRef] [Green Version]
- Machanavajjhala, A.; Kifer, D.; Gehrke, J.; Venkitasubramaniam, M. l-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data TKDD 2007, 1. [Google Scholar] [CrossRef]
- Li, N.; Li, T.; Venkatasubramanian, S. t-closeness: Privacy beyond k-anonymity and l-diversity. In Proceedings of the 2007 IEEE 23rd International Conference on Data Engineering, Istanbul, Turkey, 11–15 April 2007; pp. 106–115. [Google Scholar]
- Dwork, C.; McSherry, F.; Nissim, K.; Smith, A. Calibrating noise to sensitivity in private data analysis. In Proceedings of the Theory of Cryptography Conference, New York, NY, USA, 4–7 March 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 265–284. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar] [CrossRef]
- Li, H.; Zhu, L.; Shen, M.; Gao, F.; Tao, X.; Liu, S. Blockchain-based data preservation system for medical data. J. Med. Syst. 2018, 42, 141. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 1–11. [Google Scholar] [CrossRef]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef]
- Karakış, R.; Güler, İ.; Capraz, I.; Bilir, E. A novel fuzzy logic-based image steganography method to ensure medical data security. Comput. Biol. Med. 2015, 67, 172–183. [Google Scholar] [CrossRef] [PubMed]
- Mantos, P.L.; Maglogiannis, I. Sensitive patient data hiding using a ROI reversible steganography scheme for DICOM images. J. Med. Syst. 2016, 40, 156. [Google Scholar] [CrossRef]
- Turuk, M.; Dhande, A. A novel reversible multiple medical image watermarking for health information system. J. Med. Syst. 2016, 40, 269. [Google Scholar] [CrossRef] [PubMed]
- Shehab, A.; Elhoseny, M.; Muhammad, K.; Sangaiah, A.K.; Yang, P.; Huang, H.; Hou, G. Secure and robust fragile watermarking scheme for medical images. IEEE Access 2018, 6, 10269–10278. [Google Scholar] [CrossRef]
- Tan, C.K.; Ng, J.C.; Xu, X.; Poh, C.L.; Guan, Y.L.; Sheah, K. Security protection of DICOM medical images using dual-layer reversible watermarking with tamper detection capability. J. Digit. Imaging 2011, 24, 528–540. [Google Scholar] [CrossRef] [Green Version]
- Liu, S.H.; Yao, H.X.; Gao, W.; Liu, Y.L. An image fragile watermark scheme based on chaotic image pattern and pixel-pairs. Appl. Math. Comput. 2007, 185, 869–882. [Google Scholar] [CrossRef]
- Sametinger, J.; Rozenblit, J.; Lysecky, R.; Ott, P. Security challenges for medical devices. Commun. ACM 2015, 58, 74–82. [Google Scholar] [CrossRef]
- Burns, A.; Johnson, M.E.; Honeyman, P. A brief chronology of medical device security. Commun. ACM 2016, 59, 66–72. [Google Scholar] [CrossRef] [Green Version]
- Hei, X.; Du, X.; Wu, J.; Hu, F. Defending resource depletion attacks on implantable medical devices. In Proceedings of the 2010 IEEE Global Telecommunications Conference GLOBECOM 2010, Miami, FL, USA, 6–10 December 2010; pp. 1–5. [Google Scholar]
- Mendenhall, G.S. The challenges of implanted cardiac device security: Lessons from recent compromises. EP Eur. 2019, 21, 535–538. [Google Scholar] [CrossRef]
- Liu, H.; Ning, H.; Yue, Y.; Wan, Y.; Yang, L.T. Selective disclosure and yoking-proof based privacy-preserving authentication scheme for cloud assisted wearable devices. Future Gener. Comput. Syst. 2018, 78, 976–986. [Google Scholar] [CrossRef]
- Pycroft, L.; Aziz, T.Z. Security of implantable medical devices with wireless connections: The dangers of cyber-attacks. Expert Rev. Med. Devices 2018, 15, 403–406. [Google Scholar] [CrossRef]
- Zheng, G.; Yang, W.; Valli, C.; Qiao, L.; Shankaran, R.; Orgun, M.A.; Mukhopadhyay, S.C. Finger-to-heart (F2H): Authentication for wireless implantable medical devices. IEEE J. Biomed. Health Inform. 2018, 23, 1546–1557. [Google Scholar] [CrossRef] [PubMed]
- Belkhouja, T.; Du, X.; Mohamed, A.; Al-Ali, A.K.; Guizani, M. Biometric-based authentication scheme for Implantable Medical Devices during emergency situations. Future Gener. Comput. Syst. 2019, 98, 109–119. [Google Scholar] [CrossRef]
- Halperin, D.; Heydt-Benjamin, T.S.; Ransford, B.; Clark, S.S.; Defend, B.; Morgan, W.; Fu, K.; Kohno, T.; Maisel, W.H. Pacemakers and implantable cardiac defibrillators: Software radio attacks and zero-power defenses. In Proceedings of the 2008 IEEE Symposium on Security and Privacy (sp 2008), Oakland, CA, USA, 18–21 May 2008; pp. 129–142. [Google Scholar]
- Zheng, G.; Fang, G.; Shankaran, R.; Orgun, M.A. Encryption for implantable medical devices using modified one-time pads. IEEE Access 2015, 3, 825–836. [Google Scholar] [CrossRef]
- Guo, P.; Wang, J.; Ji, S.; Geng, X.H.; Xiong, N.N. A lightweight encryption scheme combined with trust management for privacy-preserving in body sensor networks. J. Med. Syst. 2015, 39, 190. [Google Scholar] [CrossRef]
- Latif, R.; Abbas, H.; Latif, S.; Masood, A. Distributed denial of service attack source detection using efficient traceback technique (ETT) in cloud-assisted healthcare environment. J. Med. Syst. 2016, 40, 161. [Google Scholar] [CrossRef]
- Shen, J.; Chang, S.; Shen, J.; Liu, Q.; Sun, X. A lightweight multi-layer authentication protocol for wireless body area networks. Future Gener. Comput. Syst. 2018, 78, 956–963. [Google Scholar] [CrossRef]
- Peng, H.; Tian, Y.; Kurths, J.; Li, L.; Yang, Y.; Wang, D. Secure and energy-efficient data transmission system based on chaotic compressive sensing in body-to-body networks. IEEE Trans. Biomed. Circuits Syst. 2017, 11, 558–573. [Google Scholar] [CrossRef]
- Lounis, A.; Hadjidj, A.; Bouabdallah, A.; Challal, Y. Healing on the cloud: Secure cloud architecture for medical wireless sensor networks. Future Gener. Comput. Syst. 2016, 55, 266–277. [Google Scholar] [CrossRef] [Green Version]
- Ji, S.; Gui, Z.; Zhou, T.; Yan, H.; Shen, J. An efficient and certificateless conditional privacy-preserving authentication scheme for wireless body area networks big data services. IEEE Access 2018, 6, 69603–69611. [Google Scholar] [CrossRef]
- Saeed, M.E.S.; Liu, Q.Y.; Tian, G.; Gao, B.; Li, F. Remote authentication schemes for wireless body area networks based on the Internet of Things. IEEE Internet Things J. 2018, 5, 4926–4944. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C.; Weng, C.Y. A secure cloud-assisted wireless body area network in mobile emergency medical care system. J. Med. Syst. 2016, 40, 117. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.; Zheng, X.; Guo, W.; Liu, X.; Chang, V. Privacy-preserving fusion of IoT and big data for e-health. Future Gener. Comput. Syst. 2018, 86, 1437–1455. [Google Scholar] [CrossRef] [Green Version]
- Tang, W.; Ren, J.; Deng, K.; Zhang, Y. Secure data aggregation of lightweight e-healthcare iot devices with fair incentives. IEEE Internet Things J. 2019, 6, 8714–8726. [Google Scholar] [CrossRef]
- Fan, K.; Jiang, W.; Li, H.; Yang, Y. Lightweight RFID protocol for medical privacy protection in IoT. IEEE Trans. Ind. Inform. 2018, 14, 1656–1665. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Conti, M.; Kumar, M. Opportunities in opportunistic computing. Computer 2010, 43, 42–50. [Google Scholar] [CrossRef]
- Jin, C.; Xu, C.; Zhang, X.; Li, F. A secure ECC-based RFID mutual authentication protocol to enhance patient medication safety. J. Med. Syst. 2016, 40, 12. [Google Scholar] [CrossRef] [PubMed]
- Omala, A.A.; Robert, N.; Li, F. A provably-secure transmission scheme for wireless body area networks. J. Med. Syst. 2016, 40, 247. [Google Scholar] [CrossRef] [PubMed]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 457–473. [Google Scholar]
- Zheng, D.; Wu, A.; Zhang, Y.; Zhao, Q. Efficient and privacy-preserving medical data sharing in Internet of Things with limited computing power. IEEE Access 2018, 6, 28019–28027. [Google Scholar] [CrossRef]
- Even, S.; Goldreich, O.; Micali, S. On-line/off-line digital signatures. In Proceedings of the Conference on the Theory and Application of Cryptology, Houthalen, Belgium, 10–13 April 1989; Springer: Berlin/Heidelberg, Germany, 1989; pp. 263–275. [Google Scholar]
- Ara, A.; Al-Rodhaan, M.; Tian, Y.; Al-Dhelaan, A. A secure privacy-preserving data aggregation scheme based on bilinear ElGamal cryptosystem for remote health monitoring systems. IEEE Access 2017, 5, 12601–12617. [Google Scholar] [CrossRef]
- Huang, H.; Gong, T.; Ye, N.; Wang, R.; Dou, Y. Private and secured medical data transmission and analysis for wireless sensing healthcare system. IEEE Trans. Ind. Inform. 2017, 13, 1227–1237. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, Z. Data division scheme based on homomorphic encryption in WSNs for health care. J. Med. Syst. 2015, 39, 188. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Paris, France, 9–11 April 1984; Springer: Berlin/Heidelberg, Germany, 1984; pp. 47–53. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) ≪ cost (signature)+ cost (encryption). In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Barbosa, M.; Farshim, P. Certificateless signcryption. In Proceedings of the 2008 ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 18–20 March 2008; pp. 369–372. [Google Scholar]
- Li, F.; Han, Y.; Jin, C. Cost-effective and anonymous access control for wireless body area networks. IEEE Syst. J. 2016, 12, 747–758. [Google Scholar] [CrossRef]
- Barreto, P.S.; Libert, B.; McCullagh, N.; Quisquater, J.J. Efficient and provably-secure identity-based signatures and signcryption from bilinear maps. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Beijing, China, 2–6 December 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 515–532. [Google Scholar]
- Zhang, A.; Wang, L.; Ye, X.; Lin, X. Light-weight and robust security-aware D2D-assist data transmission protocol for mobile-health systems. IEEE Trans. Inf. Forensics Secur. 2016, 12, 662–675. [Google Scholar] [CrossRef]
- Cheng, X.; Chen, F.; Xie, D.; Sun, H.; Huang, C. Design of a secure medical data sharing scheme based on blockchain. J. Med. Syst. 2020, 44, 52. [Google Scholar] [CrossRef] [PubMed]
- Ibrahim, M.H.; Kumari, S.; Das, A.K.; Wazid, M.; Odelu, V. Secure anonymous mutual authentication for star two-tier wireless body area networks. Comput. Methods Programs Biomed. 2016, 135, 37–50. [Google Scholar] [CrossRef] [PubMed]
- Rahman, F.; Bhuiyan, M.Z.A.; Ahamed, S.I. A privacy preserving framework for RFID based healthcare systems. Future Gener. Comput. Syst. 2017, 72, 339–352. [Google Scholar] [CrossRef] [Green Version]
- Attarian, R.; Hashemi, S. An anonymity communication protocol for security and privacy of clients in IoT-based mobile health transactions. Comput. Netw. 2021, 190, 107976. [Google Scholar] [CrossRef]
- Maw, H.A.; Xiao, H.; Christianson, B.; Malcolm, J.A. BTG-AC: Break-the-glass access control model for medical data in wireless sensor networks. IEEE J. Biomed. Health Inform. 2015, 20, 763–774. [Google Scholar] [CrossRef] [Green Version]
- Wang, L.; Li, L.; Li, J.; Li, J.; Gupta, B.B.; Liu, X. Compressive sensing of medical images with confidentially homomorphic aggregations. IEEE Internet Things J. 2018, 6, 1402–1409. [Google Scholar] [CrossRef]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Green, M.; Ateniese, G. Identity-based proxy re-encryption. In Proceedings of the International Conference on Applied Cryptography and Network Security, Zhuhai, China, 5–8 June 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 288–306. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 213–229. [Google Scholar]
- Wang, X.A.; Ma, J.; Xhafa, F.; Zhang, M.; Luo, X. Cost-effective secure E-health cloud system using identity based cryptographic techniques. Future Gener. Comput. Syst. 2017, 67, 242–254. [Google Scholar] [CrossRef] [Green Version]
- Wang, S.; Zhou, J.; Liu, J.K.; Yu, J.; Chen, J.; Xie, W. An efficient file hierarchy attribute-based encryption scheme in cloud computing. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1265–1277. [Google Scholar] [CrossRef]
- Eom, J.; Lee, D.H.; Lee, K. Patient-controlled attribute-based encryption for secure electronic health records system. J. Med. Syst. 2016, 40, 253. [Google Scholar] [CrossRef]
- Liu, J.; Huang, X.; Liu, J.K. Secure sharing of personal health records in cloud computing: Ciphertext-policy attribute-based signcryption. Future Gener. Comput. Syst. 2015, 52, 67–76. [Google Scholar] [CrossRef]
- Rao, Y.S. A secure and efficient ciphertext-policy attribute-based signcryption for personal health records sharing in cloud computing. Future Gener. Comput. Syst. 2017, 67, 133–151. [Google Scholar] [CrossRef]
- Emura, K.; Miyaji, A.; Rahman, M.S. Dynamic attribute-based signcryption without random oracles. Int. J. Appl. Cryptogr. 2012, 2, 199–211. [Google Scholar] [CrossRef]
- Chen, C.; Chen, J.; Lim, H.W.; Zhang, Z.; Feng, D. Combined public-key schemes: The case of ABE and ABS. In Proceedings of the International Conference on Provable Security, Chengdu, China, 26–28 September 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 53–69. [Google Scholar]
- Raisaro, J.L.; Troncoso-Pastoriza, J.R.; Misbach, M.; Sousa, J.S.; Pradervand, S.; Missiaglia, E.; Michielin, O.; Ford, B.; Hubaux, J.P. M ed C o: Enabling Secure and Privacy-Preserving Exploration of Distributed Clinical and Genomic Data. IEEE/ACM Trans. Comput. Biol. Bioinform. 2018, 16, 1328–1341. [Google Scholar] [CrossRef] [Green Version]
- Alabdulatif, A.; Khalil, I.; Yi, X.; Guizani, M. Secure edge of things for smart healthcare surveillance framework. IEEE Access 2019, 7, 31010–31021. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Searchable encryption for healthcare clouds: A survey. IEEE Trans. Serv. Comput. 2017, 11, 978–996. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy (S&P 2000), Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Yang, Y.; Ma, M. Conjunctive keyword search with designated tester and timing enabled proxy re-encryption function for e-health clouds. IEEE Trans. Inf. Forensics Secur. 2015, 11, 746–759. [Google Scholar] [CrossRef]
- Xu, C.; Wang, N.; Zhu, L.; Sharif, K.; Zhang, C. Achieving searchable and privacy-preserving data sharing for cloud-assisted E-healthcare system. IEEE Internet Things J. 2019, 6, 8345–8356. [Google Scholar] [CrossRef]
- Chen, L.; Lee, W.K.; Chang, C.C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Yao, X.; Lin, Y.; Liu, Q.; Zhang, J. Privacy-preserving search over encrypted personal health record in multi-source cloud. IEEE Access 2018, 6, 3809–3823. [Google Scholar] [CrossRef]
- Li, C.T.; Shih, D.H.; Wang, C.C. Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput. Methods Programs Biomed. 2018, 157, 191–203. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Ma, W.; Cao, H. NPMA: A novel privacy-preserving mutual authentication in TMIS for mobile edge-cloud architecture. J. Med. Syst. 2019, 43, 318. [Google Scholar] [CrossRef]
- Liu, X.; Ma, W.; Cao, H. MBPA: A medibchain-based privacy-preserving mutual authentication in TMIS for mobile medical cloud architecture. IEEE Access 2019, 7, 149282–149298. [Google Scholar] [CrossRef]
- Liu, H.; Yao, X.; Yang, T.; Ning, H. Cooperative privacy preservation for wearable devices in hybrid computing-based smart health. IEEE Internet Things J. 2018, 6, 1352–1362. [Google Scholar] [CrossRef]
- Mehmood, A.; Natgunanathan, I.; Xiang, Y.; Poston, H.; Zhang, Y. Anonymous authentication scheme for smart cloud based healthcare applications. IEEE Access 2018, 6, 33552–33567. [Google Scholar] [CrossRef]
- Liu, X.; Ma, W. ETAP: Energy-efficient and traceable authentication protocol in mobile medical cloud architecture. IEEE Access 2018, 6, 33513–33528. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Karati, A.; Biswas, G.; Khan, M.K. A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 2017, 41, 50. [Google Scholar] [CrossRef]
- Yan, Z.; Li, X.; Wang, M.; Vasilakos, A.V. Flexible data access control based on trust and reputation in cloud computing. IEEE Trans. Cloud Comput. 2015, 5, 485–498. [Google Scholar] [CrossRef]
- Yeh, L.Y.; Chiang, P.Y.; Tsai, Y.L.; Huang, J.L. Cloud-based fine-grained health information access control framework for lightweightiot devices with dynamic auditing andattribute revocation. IEEE Trans. Cloud Comput. 2015, 6, 532–544. [Google Scholar] [CrossRef]
- Roy, S.; Das, A.K.; Chatterjee, S.; Kumar, N.; Chattopadhyay, S.; Rodrigues, J.J. Provably secure fine-grained data access control over multiple cloud servers in mobile cloud computing based healthcare applications. IEEE Trans. Ind. Inform. 2018, 15, 457–468. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, Y.; Ling, J.; Liu, Z. Secure and fine-grained access control on e-healthcare records in mobile cloud computing. Future Gener. Comput. Syst. 2018, 78, 1020–1026. [Google Scholar] [CrossRef]
- Li, W.; Liu, B.M.; Liu, D.; Liu, R.P.; Wang, P.; Luo, S.; Ni, W. Unified fine-grained access control for personal health records in cloud computing. IEEE J. Biomed. Health Inform. 2018, 23, 1278–1289. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R. A novel reference security model with the situation based access policy for accessing ephr data. J. Med. Syst. 2016, 40, 242. [Google Scholar] [CrossRef]
- Ying, Z.; Wei, L.; Li, Q.; Liu, X.; Cui, J. A lightweight policy preserving EHR sharing scheme in the cloud. IEEE Access 2018, 6, 53698–53708. [Google Scholar] [CrossRef]
- Rezaeibagha, F.; Mu, Y. Distributed clinical data sharing via dynamic access-control policy transformation. Int. J. Med. Inform. 2016, 89, 25–31. [Google Scholar] [CrossRef]
- Ying, Z.; Jang, W.; Cao, S.; Liu, X.; Cui, J. A lightweight cloud sharing PHR system with access policy updating. IEEE Access 2018, 6, 64611–64621. [Google Scholar] [CrossRef]
- Wang, X.; Wang, L.; Li, Y.; Gai, K. Privacy-aware efficient fine-grained data access control in Internet of medical things based fog computing. IEEE Access 2018, 6, 47657–47665. [Google Scholar] [CrossRef]
- Saha, R.; Kumar, G.; Rai, M.K.; Thomas, R.; Lim, S.J. Privacy Ensured e-healthcare for fog-enhanced IoT based applications. IEEE Access 2019, 7, 44536–44543. [Google Scholar] [CrossRef]
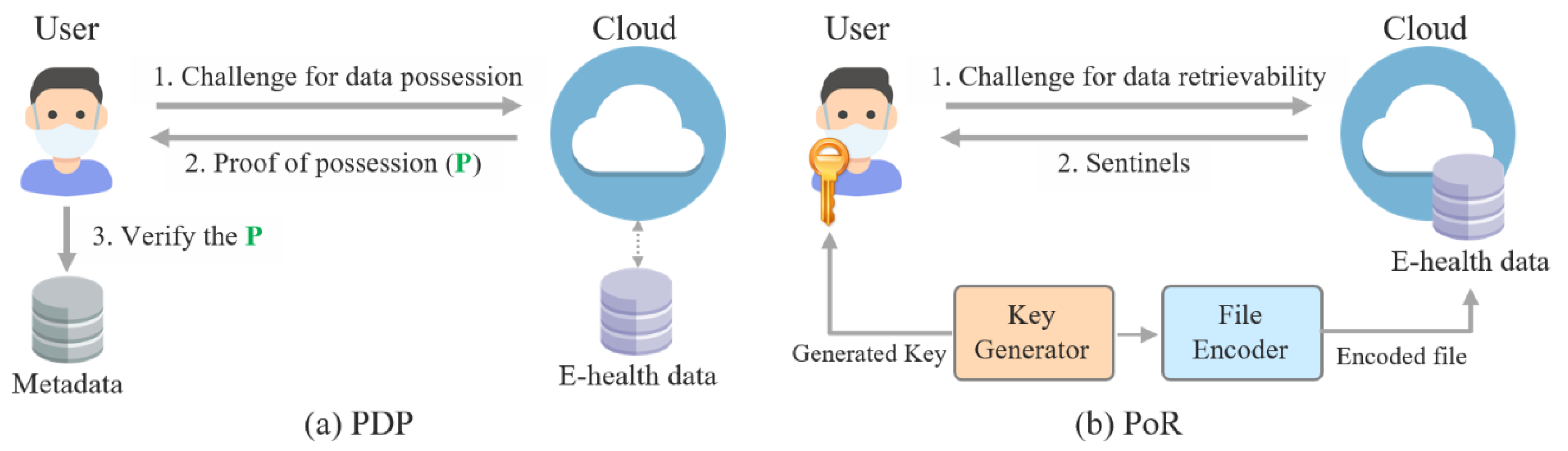
- Ateniese, G.; Burns, R.; Curtmola, R.; Herring, J.; Kissner, L.; Peterson, Z.; Song, D. Provable data possession at untrusted stores. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 2 November–31 October 2007; pp. 598–609. [Google Scholar]
- Juels, A.; Kaliski Jr, B.S. PORs: Proofs of retrievability for large files. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 2 November–31 October 2007; pp. 584–597. [Google Scholar]
- Wang, Y.; Wu, Q.; Qin, B.; Shi, W.; Deng, R.H.; Hu, J. Identity-based data outsourcing with comprehensive auditing in clouds. IEEE Trans. Inf. Forensics Secur. 2016, 12, 940–952. [Google Scholar] [CrossRef]
- Fan, Y.; Liao, Y.; Li, F.; Zhou, S.; Zhang, G. Identity-based auditing for shared cloud data with efficient and secure sensitive information hiding. IEEE Access 2019, 7, 114246–114260. [Google Scholar] [CrossRef]
- Shi, H.; Guo, R.; Jing, C.; Feng, S. Efficient and Unconditionally Anonymous Certificateless Provable Data Possession Scheme With Trusted KGC for Cloud-Based EMRs. IEEE Access 2019, 7, 69410–69421. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for secure ehrs sharing of mobile cloud based e-health systems. IEEE Access 2019, 7, 66792–66806. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, A.; Zhang, P.; Wang, H. Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain. IEEE Access 2019, 7, 136704–136719. [Google Scholar] [CrossRef]
- Al Omar, A.; Bhuiyan, M.Z.A.; Basu, A.; Kiyomoto, S.; Rahman, M.S. Privacy-friendly platform for healthcare data in cloud based on blockchain environment. Future Gener. Comput. Syst. 2019, 95, 511–521. [Google Scholar] [CrossRef]
- Rahman, M.A.; Hossain, M.S.; Loukas, G.; Hassanain, E.; Rahman, S.S.; Alhamid, M.F.; Guizani, M. Blockchain-based mobile edge computing framework for secure therapy applications. IEEE Access 2018, 6, 72469–72478. [Google Scholar] [CrossRef]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Karekar, S.P.; Vaidya, S.M. Perspective of decoy technique using mobile fog computing with effect to wireless environment. Int. J. Sci. Eng. Technol. Res. 2015, 4, 2620–2626. [Google Scholar]
- Al Hamid, H.A.; Rahman, S.M.M.; Hossain, M.S.; Almogren, A.; Alamri, A. A security model for preserving the privacy of medical big data in a healthcare cloud using a fog computing facility with pairing-based cryptography. IEEE Access 2017, 5, 22313–22328. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy for Healthcare Blockchains. IEEE Trans. Serv. Comput. 2021. [Google Scholar] [CrossRef]
- Rocher, L.; Hendrickx, J.M.; De Montjoye, Y.A. Estimating the success of re-identifications in incomplete datasets using generative models. Nat. Commun. 2019, 10, 3069. [Google Scholar] [CrossRef] [PubMed]
- Gollakota, S.; Hassanieh, H.; Ransford, B.; Katabi, D.; Fu, K. They can hear your heartbeats: Non-invasive security for implantable medical devices. In Proceedings of the ACM SIGCOMM 2011 Conference, Toronto, ON, Canada, 15–19 August 2011; pp. 2–13. [Google Scholar]
- Xu, F.; Qin, Z.; Tan, C.C.; Wang, B.; Li, Q. IMDGuard: Securing implantable medical devices with the external wearable guardian. In Proceedings of the 2011 Proceedings IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1862–1870. [Google Scholar]
- Halperin, D.; Heydt-Benjamin, T.S.; Fu, K.; Kohno, T.; Maisel, W.H. Security and privacy for implantable medical devices. IEEE Pervasive Comput. 2008, 7, 30–39. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef] [Green Version]
- Ren, J.; Zhang, D.; He, S.; Zhang, Y.; Li, T. A survey on end-edge-cloud orchestrated network computing paradigms: Transparent computing, mobile edge computing, fog computing, and cloudlet. ACM Comput. Surv. CSUR 2019, 52, 125. [Google Scholar] [CrossRef] [Green Version]







| Publisher | Journal | IF | SJR |
|---|---|---|---|
| IEEE | IEEE Access | 3.37 | 0.59 |
| IEEE Systems Journal | 3.93 | 0.86 | |
| IEEE Journal of Biomedical and Health Informatics | 5.77 | 1.29 | |
| IEEE Transactions on Information Forensics and Security | 7.18 | 1.61 | |
| IEEE Internet of Things Journal | 9.47 | 2.08 | |
| IEEE Transactions on Industrial Informatics | 10.21 | 2.50 | |
| IEEE Transactions on Image Processing | 10.86 | 1.78 | |
| IEEE Transactions on Parallel and Distributed Systems | 2.69 | 0.76 | |
| IEEE Transactions on Services Computing | 5.7 | 0.97 | |
| IEEE Transactions on Cloud Computing | 8.22 | 1.21 | |
| IEEE Reviews in Biomedical Engineering | - | 1.64 | |
| IEEE Transactions on Biomedical Engineering | 4.54 | 1.15 | |
| IEEE Transactions on Wireless Communications | 7.02 | 2.01 | |
| IEEE Transactions on Biomedical Circuits and Systems | 3.83 | 1.02 | |
| IEEE Journal on Selected Areas in Communications | 9.14 | 2.99 | |
| IEEE Transactions on Dependable and Secure Computing | 7.33 | 1.27 | |
| ACM | Communications of the ACM | 4.65 | 0.97 |
| IEEE/ACM | IEEE/ACM Transactions on Computational Biology and Bioinformatics | 3.71 | 0.75 |
| IEEE/ACM Transactions on Networking | 3.56 | 1.02 | |
| Elsevier | Future Generation Computer Systems | 7.19 | 1.26 |
| Computer Methods and Programs in Biomedicine | 5.43 | 0.92 | |
| International Journal of Medical Informatics | 4.05 | 1.12 | |
| Computers in Biology and Medicine | 4.59 | 0.88 | |
| Springer | Journal of Medical Systems | 4.46 | 0.69 |
| Neural Computing and Applications | 5.61 | 0.71 | |
| Journal of Big Data | - | 1.03 | |
| SAGE | Health Informatics Journal | 2.68 | 0.56 |
| JMIR | Journal of Medical Internet Research | 2.68 | 1.45 |
| JMIR Medical Informatics | 2.96 | - | |
| JMIR mHealth and uHealth | 4.77 | 1.36 | |
| Oxford University Press | Europace | 5.21 | 2.12 |
| Taylor & Francis | Expert Review of Medical Devices | 3.17 | 0.62 |
| Diabetes Technology Society | Journal of diabetes science and technology | - | 1.04 |
| Reference | E-Health Data | Medical Device | Network | Edge | Fog | Cloud |
|---|---|---|---|---|---|---|
| Kruse et al. [5] | ✔ | |||||
| Abouelmehdi et al. [6] | ✔ | |||||
| Mohammed et al. [7] | ✔ | |||||
| Aziz et al. [8] | ✔ | |||||
| Zheng et al. [9] | ✔ | ✔ | ||||
| Wu et al. [10] | ✔ | |||||
| Yaqoob et al. [3] | ✔ | ✔ | ||||
| Kintzlinger et al. [11] | ✔ | ✔ | ||||
| AlTawy et al. [12] | ✔ | ✔ | ||||
| Yaacoub et al. [13] | ✔ | ✔ | ||||
| Sun et al. [14] | ✔ | ✔ | ✔ | ✔ | ||
| Chenthara et al. [15] | ✔ | ✔ | ✔ | |||
| Yüksel et al. [16] | ✔ | ✔ | ||||
| Wazid et al. [17] | ✔ | ✔ | ✔ | |||
| Razaque et al. [18] | ✔ | ✔ | ✔ | ✔ | ||
| Our Survey | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Ref. | Target Security Concern | Target Security Requirement | Security Solution | Strength | Weakness |
|---|---|---|---|---|---|
| [21] | - Unauthorized access - Data disclosure - Data tampering | - Access restriction - Confidentiality - Anonymity - Accountability | - Access Control - Anonymization | Anonymization and access control according to the sensitivity of e-health data | The current anonymization method has some vulnerabilities that could lead to re-identification |
| [22] | - Unauthorized access - Data disclosure - Data loss - Data tampering - Data forgery | - Access restriction - Confidentiality - Integrity - Availability - Accountability | - Access Control - Blockchain (Hyperledger Fabric) | No single point of failure (SPoF) problem and the emergency scenario is considered | Emergency access permission could be abused and access control requires a transaction fee |
| [23] | - Unauthorized access - Data disclosure - Data loss - Data tampering - Data forgery | - Access restriction - Confidentiality - Integrity | - Access Control - Blockchain (Ethereum) | No SPoF problem and employing an off-chain scaling method to solve the scalability problem of blockchain | Lack of fine-grained access control and access control requires a transaction fee |
| [24] | - Unauthorized access - Data disclosure - Data loss - Data tampering - Data forgery | - Access restriction - Confidentiality - Integrity - Accountability | - Access Control - AES - Blockchain | A user can revoke permission to access their e-health data from medical staff at any time | Symmetric key was shared to control access; therefore, once a key has been shared with someone or compromised, the key should be updated and related e-health data should be re-encrypted |
| [27] | - Data disclosure | - Confidentiality | - AES - RSA - Steganography | Discrete wavelet transform is compatible with compression and has resistance to geometric distortions | IoT is a target environment; however, AES and RSA that require high computational power were used |
| [28] | - Data disclosure | - Confidentiality | - Quaternion-based Encryption | Fast computation speed for the encryption of a large volume of e-health data | The computation speed could be increased if the decomposition process were omitted |
| [29] | - Data disclosure | - Confidentiality | - ECEM-based Encryption | Differential attack resistance | Performance should be evaluated on diverse medical images |
| [36] | - Data disclosure - Data tampering - Data loss - Data forgery | - Confidentiality - Integrity - Anonymity - Accountability | - AES - Blockchain | No SPoF problem and medical data can be securely preserved with the blockchain | The transaction fee is relatively high compared to conventional data storage |
| [37] | - Data disclosure - Data tampering - Data loss - Data forgery | - Access restriction - Confidentiality - Integrity - Anonymity - Accountability | - Access Control - Blockchain | Efficient consensus mechanism and access control protocol for e-health data were also proposed | Access should be able to be delegated to related medical staff or other people in a secure manner for flexible data sharing |
| [38] | - Data disclosure - Data tampering - Data loss - Data forgery | - Integrity - Accountability | - Blockchain | Blockchain only records URLs instead of medical images that have a large data size | Since real images are stored in the hospital’s database, both the blockchain and endpoints should be properly protected |
| [39] | - Data disclosure | - Confidentiality | - Rijndael encryption - Steganography | Fast processing time and high embedding capacity based on LSB | Message capacity could be increased with noise cancellation and data reduction |
| [40] | - Data disclosure - Data tampering | - Confidentiality - Integrity | - AES - Steganography | It considered both confidentiality and integrity and had high capacity, robustness, and imperceptibility | An error control mechanism should be adopted for a robust steganography method |
| [41] | - Data disclosure - Data tampering - Data forgery | - Confidentiality - Integrity | - Watermarking | Resistance to sharpening and blurring attacks while maintaining acceptable imperceptibility | A tracking key that makes the proposed scheme reversible has to be transmitted with each medical image |
| [42] | - Data disclosure - Data tampering - Data forgery | - Confidentiality - Integrity | - Watermarking | Proposes an effective scheme to localize and restore tampered pixels and regions | Various tampering attacks on image resizing, skewing, and rotating should be studied |
| Ref. | Target Security Concern | Target Security Requirement | Security Solution | Strength | Weakness |
|---|---|---|---|---|---|
| [49] | - Unauthorized access - Data breach - Network attack | - Access restriction - Confidentiality - Integrity - Resistance to network attack | - Mutual authentication | Both local authentication and remote authentication are considered for cloud-assisted wearable devices | Details of implementation and security analysis against diverse possible attacks are insufficient |
| [51] | - Unauthorized access - Network attack | - Access restriction - Availability - Resistance to network attack | - Biometric-based authentication (fingerprint) | A fingerprint-based authentication model is proposed that would be suitable for IMDs | Fingerprints cannot be re-generated; therefore, fingerprint-based security solutions must consider other solutions to protect fingerprints since fingerprint must then never be leaked |
| [52] | - Unauthorized access - Network attack | - Access restriction - Availability - Resistance tonetwork attack | - Biometric-based authentication (ECG and fingerprint) | A strong authentication scheme is proposed using two-factors, ECG, and fingerprint | A backdoor can be abused by insiders or attackers |
| [54] | - Data breach - Network attack | - Confidentiality | - ECG- and OTP-based encryption | OTP, which is theoretically unbreakable, is used and it does not require key distribution, storage, revocation, or refreshment using random ECG signals as OTP keys | Proposed scheme requires an additional device to capture ECG signals and the ECG- and OTP-based encryption scheme may not be suitable for resource-constrained IMDs |
| Ref. | Target Security Concern | Target Security Requirement | Security Solution | Strength | Weakness |
|---|---|---|---|---|---|
| [59] | - Collusion attack - MITM attack | - Scalability - Confidentiality - Availability - Integrity - Authenticity | - AES - CP-ABE - Access Control | Efficient approach of using ABE by encrypting a symmetric key, RSK, instead of the whole data | Security for e-health data depends on a secure socket layer (SSL) that could not be fully adopted in a resource-constrained WSN environment |
| [55] | - Eavesdropping - Tracking - Spoofing attack | - Confidentiality - Availability (reliability) | - AES - ABE - Authentication - Access Control | Flexible privacy protection strategies according to three trust levels of a user or node | Security could easily be threatened if a node that has a high trust level is compromised |
| [57] | - Eavesdropping - Impersonation attack - Replay attack - DoS attack | - Confidentiality - Integrity - Authenticity - Non-repudiation - Lightweight - Forward security | - ECC - Mutual Authentication | Efficient authentication protocol using a non-pairing operation and ECC-based scheme | The required computation cost is still high for resource constrained WBAN nodes because of the certificateless scheme |
| [60] | - Replay attack - Impersonation attack - MITM attack | - Anonymity - Unlinkability - Forward Secrecy | - ECC - Mutual Authentication | Conditionally anonymous authentication to trace a malicious user and batch authentication for efficiency | Conditional traceability could be abused by an insider; however, there is no mention of this drawback |
| [68] | - Replay attack - Impersonation attack - Spoofing attack - DoS attack - Location tracking - MITM attack | - Confidentiality - Anonymity - Availability - Forward secrecy - Scalability | - ECC - Mutual Authentication | Low computation cost and communication overhead | The communication between tag and reader was insecure |
| [69] | - Eavesdropping - Replay attack | - Confidentiality - Authenticity - Lightweight | - ECC - CLSC - Authentication | Efficient scheme based on ECC and signcryption | Anonymity should be considered to ensure patient privacy |
| [71] | - Eavesdropping - Replay attack | - Confidentiality - Lightweight | - ABE | Efficient ABE based on online/offline encryption techniques and ABF for access control policy to protect the privacy of users’ attributes | ABF could hinder the encryption performance |
| [63] | - Eavesdropping - Replay attack - Impersonation attack - Tracking attack | - Confidentiality - Anonymity - Authenticity | - ABE - Access Control | Low computation cost for EHR encryption/decryption | Pairing operation that cause high computation cost is required |
| [73] | - Eavesdropping - Replay attack | - Confidentiality - Integrity - Authenticity | - Pairing-based HE - Aggregate Signature | Data confidentiality is preserved while data aggregation and batch verification are performed for efficiency | Requires exponentiation and pairing operations that cause a high computation cost |
| [74] | - Eavesdropping - Replay attack - Impersonation attack | - Confidentiality - Forward secrecy - Backward secrecy | - HE - Key Distribution | Direct communication between a patient’s mobile device and medical devices is possible | Diagnosis reliability should be provided |
| [64] | - Eavesdropping - Replay attack - Collusion attack | - Availability (Fault Tolerance) - Collusion resistance | - BGN cryptosystem | Differential attack and privacy are considered | The BGN cryptosystem has a small plaintext space for e-health data |
| [80] | - Eavesdropping - Replay attack | - Anonymity - Confidentiality - Integrity - Non-repudiation | - CLSC - Authentication - Access Control | Key escrow resilience and elimination of certificate management based on certificateless access control | Requires exponentiation and pairing operations that cause high computation cost |
| [82] | - Eavesdropping - Impersonation attack | - Confidentiality - Integrity - Anonymity - Lightweight - Unlinkability - Forward secrecy | - CLGSC | Key escrow resilience and low computation cost by eliminating pairing operations | Requires a relay selection strategy to improve transmission efficiency and reliability |
| [75] | - Eavesdropping | - Confidentiality - Integrity | - HE | Eavesdropping in wireless environments could be mitigated by dividing data | A sensor node in WSNs could not use HE because of the resource constraint |
| [62] | - Eavesdropping - Replay attack - Impersonation attack - MITM attack | - Integrity - Non-repudiation - Forward secrecy | - Mutual Authentication - Key agreement based on Chebyshev chaotic map | The major advantage is that it provides continuous remote patient supervision that can improve patient health | SPoF can be posed because of the centric medical cloud that manages all patients’ health data |
| [83] | - Eavesdropping - Replay attack - Impersonation attack - MITM attack | - Anonymity - Authenticity - Forward secrecy | - Mutual Authentication | Medical data cannot be tampered with and is untraceable by means of a blockchain | Using the cloud as a central database of medical data can cause SPoF. This drawback could weaken the advantages of blockchain |
| [84] | - Replay attack - Eavesdropping - Impersonation attack - MITM attack | - Confidentiality - Integrity - Availability - Anonymity - Lightweight - Unlikability - Forward secrecy - Backward secrecy | - Mutual Authentication | Very low computation cost and energy consumption | Mutual authentication is only considered between the WBAN and controller nodes |
| [85] | - Eavesdropping - DoS attack - Impersonation attack - Tracking attack | - Confidentiality - Anonymity - Authenticity - Unlinkability | - Authentication - Access Control | A lightweight authentication protocol for resource-constrained RFID tags | When an RFID reader gets an authentication response from a tag, all group keys should be used to decrypt the response until it succeeds |
| [68] | - Replay attack - DoS attack - Impersonation attack - MITM attack - Spoofing attack - Tracking attack | - Confidentiality - Availability - Anonymity - Forward secrecy - Scalability | - Mutual Authentication | Low computation cost and communication overhead and solves some security flaws of previous authentication schemes | The session key should be generated for security between a tag and reader because the secure channel between the tag and reader was not established |
| [65] | - Eavesdropping - Replay attack - DoS attack - Tracking attack | - Confidentiality - Anonymity - Forward security | - Mutual Authentication | Low computation cost | Communication cost is a little high compared to other studies |
| [66] | - Eavesdropping - Replay attack - Impersonation attack - Tracking attack | - Confidentiality - Integrity - Forward secrecy - Backward secrecy | - Mutual Authentication | Low computation power requirement for RFID tag based on the proposed lightweight MRot(x,y) function | It could be vulnerable to secret disclosure attack |
| [87] | - Replay attack - DoS attack - Spoofing attack | - Confidentiality - Integrity - Availability - Authenticity - Non-repudiation | - Flexible Access Control | The proposed access control model supports a flexible access control policy based on the BTG concept | ID and password are required when the BTG policy is applied, and the proposed access control model did not provide anti-tampering measures |
| [58] | - Eavesdropping | - Confidentiality | - Compressive sensing | Chaotic CS more energy-efficient and secure than traditional CS | Encrypted data might be easily decrypted if an adversary takes a measurement matrix because the encryption is performed with the same matrix |
| [56] | - DoS attack | - Availability | - Traceback technique | Lightweight to be applied in a WBAN environment | The proposed technique is only based on WBAN and MAC header and the number of bytes in the DPPM label depends on the network topologies |
| Ref. | Target Security Concern | Target Security Requirement | Security Solution | Strength | Weakness |
|---|---|---|---|---|---|
| [92] | - Data disclosure | - Confidentiality - Authenticity | - Identity-based encryption - Proxy re-encryption | Efficient identity-based cryptographic schemes were proposed and adopted in a medical domain to provide implicit authentication of the public key and simple certificate management | There is a key escrow problem because it uses a centralized server |
| [93] | - Unauthorized access - Data disclosure - Malicious insider | - Access restriction - Confidentiality | - File hierarchy CP-ABE | Considered file hierarchy in the CP-ABE for efficient encryption in terms of storage and time cost | Pairing operations consume high computing power |
| [94] | - Unauthorized access - Data disclosure | - Access restriction - Confidentiality | - IBE - CP-ABE | A patient-controlled CP-ABE scheme was proposed considering emergency situations | Identity authority has the capability to generate an emergency key to decrypt a patient’s data, which could be compromised by an attacker or abused by an insider. |
| [95] | - Unauthorized access - Data disclosure | - Access restriction - Confidentiality - Anonymity - Authenticity | - CP-ABE - Signcryption - Access control | Promising cryptographic technology, CP-ABSC, was proposed for fine-grained access control allowing the secure sharing of e-health data in cloud computing | Revocation scheme of a user and attributes should be considered and Rao claimed that it cannot provide confidentiality [76] |
| [96] | - Unauthorized access - Data disclosure | - Access restriction - Confidentiality - Anonymity - Authenticity - Integrity and public verifiability | - CP-ABE - Signcryption - Access control | The proposed CP-ABSC also supports signcryptor privacy and public verifiability, which are important security requirements in cloud environments | A high computation cost is required for designcryption because of the pairing operations |
| [99] | - Data breach - DoS attack - Single point of failure | - Confidentiality - Availability - Anonymity - Flexibility - Scalability | - Homomorphic encryption | A hybrid secure sharing scheme for e-health data is considered to cover both the advantages of centralized and decentralized approaches | Collusion attacks between cloud providers and users should be considered |
| [103] | - Unauthorized access - Data breach - Eavesdropping | - Access restriction - Confidentiality | - Searchable encryption - Proxy re-encryption | The proposed SE scheme allows a patient to delegate access permissions to others to search and decrypt the patient’s data, which is automatically revoked after a time limit | Access permissions are revoked after the time limit expires; however, the delegatee can use the data since they have already obtained it in plaintext by decrypting the data within the time limit |
| [104] | - Unauthorized access - Data breach - Eavesdropping | - Access restriction - Confidentiality - Integrity | - Searchable encryption - Homomorphic encryption | The proposed scheme can perform privacy-preserving data sharing with key range search and multiple keyword search in e-health systems | A post management scheme for e-health data may be required after searching and using the data |
| [105] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Authenticity - Accountability | - Searchable encryption - Blockchain | A searchable encryption scheme was used with the blockchain to provide integrity, anti-tampering, and accountability for e-health data sharing | Since the data are stored in the public cloud, it may require additional security solutions for the data |
| [106] | - Unauthorized access - Data breach | - Access restriction - Confidentiality | - Searchable encryption - Order-preserving symmetric encryption | An efficient query over multiple data providers’ data | The cloud is required since the proposed scheme may not be suitable for resource-limited devices (e.g., smartphones) |
| [107] | - Unauthorized access - Data breach - Eavesdropping | - Access restriction - Anonymity - Authenticity - Resistance to network attacks | - Mutual authentication | A mutual authentication scheme for telecare systems providing patient anonymity | The time required for mutual authentication is slower than the base scheme [114] |
| [108] | - Unauthorized access - Data breach - Malicious insider - Eavesdropping | - Access restriction - Anonymity - Authenticity - Accountability - Resistance to network attacks | - Mutual authentication - Secret sharing | Proposes privacy-preserving mutual authentication for mobile edge-cloud architecture | The communication cost should be reduced for resource-constrained medical networks such as IoMTs and WBANs |
| [109] | - Unauthorized access - Data breach - Malicious insider - Eavesdropping | - Access restriction - Anonymity - Authenticity - Resistance to network attacks | - Mutual authentication - Blockchain | The proposed scheme is suitable for big e-health data because of its cost-efficiency | More practical security threats to the proposed scheme are identified and analyzed |
| [110] | - Unauthorized access - Data breach - Single point of failure - Network attacks | - Access restriction - Confidentiality - Integrity - Resistance to network attacks | - Mutual authentication - Access control | Edge computing is utilized to securely provide local services to users in a certain area (e.g., a hospital) | More security concerns including location tracking attack, which emerge when adopting hybrid computing, should be discussed |
| [111] | - Unauthorized access - Data breach - Eavesdropping | - Access restriction - Anonymity - Authenticity - Resistance to network attacks | - Anonymous authentication | Complete privacy and anonymity are provided to users from adversaries and an authentication server | Traceability may be conditionally provided when security incidents happen to track attackers |
| [112] | - Unauthorized access - Data breach - Malicious insider - Eavesdropping | - Access restriction - Anonymity - Authenticity - Resistance to network attacks | - Traceable authentication | The proposed scheme provides conditional identity traceability and is efficient in terms of communication cost and energy for resource-constrained devices | Providing conditional traceability might be abused; therefore, a prevention method for such abuse is required |
| [114] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Availability - Flexibility | - Proxy re-encryption - Access control - Trust and reputation | The proposed scheme can provide flexible access control based on trust and reputation, even when the data owner is unavailable or cannot make access decisions | The level of trust and reputation might be ambiguous factors to decide access to highly sensitive e-health data |
| [115] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Availability | - Proxy re-encryption - Access control - Dynamic data auditing | It is suitable for resource-constrained devices and solves the cloud reciprocity problem | User anonymity should be considered |
| [116] | - Unauthorized access - Data breach - Malicious insider - Network attacks | - Access restriction - Confidentiality - Anonymity - Authenticity - Resistance to network attacks | - Authentication - Access control | It is designed to be lightweight for resource-constrained devices and the access control scheme | Conditional traceability may be required and the cloud provider can abuse the ability to manage the group key |
| [117] | - Unauthorized access - Data breach | - Access restriction - Confidentiality | - Online/offline CP-ABE - Access control | An efficient online/offline CP-ABE scheme is proposed for resource-constrained devices in mobile cloud computing | Bilinear pairings used in the proposed scheme pose a high cost that hinders efficiency |
| [118] | - Unauthorized access - Data breach | - Access restriction - Confidentiality | - ABE - Access control | An efficient ABE scheme is proposed to reduce the time required to encrypt and decrypt data that has the same access policy | Privacy for access policies should be supported |
| [119] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Flexibility - Scalability | - Access control | A flexible access control model is proposed using situation-based access policy | More fine-grained access control could be considered with an attribute-based access control model |
| [120] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Anonymity - Integrity | - CP-ABE - Access control - LSSS | Privacy for access policy is ensured by hiding the entire access policy with attributes | Resource-constrained medical devices are not suitable for the proposed scheme since hiding the access policy requires greater costs |
| [121] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Flexibility | - Proxy re-encryption - ABE - Access control | A method to transform a private cloud’s access policy to the access policy of a public cloud | The proposed scheme might be implemented to show feasibility, performance, etc. |
| [122] | - Unauthorized access - Data breach | - Access restriction - Confidentiality | - CP-ABE - LSSS | A method for updating an access policy in ciphertext that reduces the computational cost | The proposed scheme incurs additional overhead to cloud |
| [100] | - Data breach - Single point of failure | - Confidentiality - Scalability | - Fully homomorphic encryption | E-health data can be securely aggregated and monitored in real-time using edge computing | A performance evaluation for the fully homomorphic encryption would be helpful and show the feasibility of the proposed framework |
| [123] | - Unauthorized access - Data breach | - Access restriction - Confidentiality | - Access control | Fog computing is adopted to reduce the communication cost of IoMTs | The access control may not be sufficiently fine-grained for diverse e-healthcare systems |
| [124] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Integrity | - ABE - Access control | A consensus-based access control scheme is proposed | If the number of nodes that participate in the consensus is insufficient, an attacker could control access to e-health data |
| [127] | - Data breach | - Integrity and public verifiability | - Identity-based auditing | It provides comprehensive auditing in terms of data origin, type, and consistency | Dynamic data auditing is unsupported |
| [128] | - Data breach - Malicious insider | - Confidentiality - Integrity and public verifiability - Authenticity | - Identity-based auditing | A privacy-preserving identity-based auditing scheme is proposed | A manager who may have malicious purposes can check whether private information exists in the e-health data |
| [129] | - Data breach | - Confidentiality - Integrity and public verifiability - Anonymity | - Certificateless PDP | The proposed scheme is efficient and can prevent the key escrow problem | The true identity of a malicious user or attacker may be identified and traced for accountability |
| [130] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Availability - Accountability - Flexibility | - Access control - Blockchain | The proposed framework was implemented to show feasibility based on Ethereum | An EHR manager manages the keys to decrypt e-health data; therefore, it can be misused or targeted by an attacker |
| [131] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Availability - Accountability | - Searchable encryption - Proxy re-encryption - Authentication - Access control - Blockchain | An efficient and reliable consensus mechanism—proof of authorization—was proposed for this system | The proposed scheme cannot ensure full ownership of outsourced e-health data since data providers exist |
| [132] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Authenticity - Accountability | - ECC - Access control - Blockchain | A user-centric e-health data management system is proposed | Permission delegation for e-health data may be supported to share e-health data and a user must manage the key themself |
| [133] | - Unauthorized access - Data breach - Single point of failure | - Access restriction - Confidentiality - Integrity - Availability - Anonymity - Scalability | - Blockchain - Tor | A secure therapy application utilizing MEC is proposed and implemented | The study did not provide in-depth security analysis for the proposed MEC-based therapy application |
| [136] | - Unauthorized access - Data breach | - Access restriction - Confidentiality - Authenticity | - ECC - Mutual authentication - Decoy | A security model is proposed that utilizes a decoy technique in e-healthcare cloud using fog computing | Diverse network attacks (e.g., MIMT) should be discussed to prove that the proposed key agreement protocol is highly secure |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oh, S.-R.; Seo, Y.-D.; Lee, E.; Kim, Y.-G. A Comprehensive Survey on Security and Privacy for Electronic Health Data. Int. J. Environ. Res. Public Health 2021, 18, 9668. https://doi.org/10.3390/ijerph18189668
Oh S-R, Seo Y-D, Lee E, Kim Y-G. A Comprehensive Survey on Security and Privacy for Electronic Health Data. International Journal of Environmental Research and Public Health. 2021; 18(18):9668. https://doi.org/10.3390/ijerph18189668
Chicago/Turabian StyleOh, Se-Ra, Young-Duk Seo, Euijong Lee, and Young-Gab Kim. 2021. "A Comprehensive Survey on Security and Privacy for Electronic Health Data" International Journal of Environmental Research and Public Health 18, no. 18: 9668. https://doi.org/10.3390/ijerph18189668
APA StyleOh, S.-R., Seo, Y.-D., Lee, E., & Kim, Y.-G. (2021). A Comprehensive Survey on Security and Privacy for Electronic Health Data. International Journal of Environmental Research and Public Health, 18(18), 9668. https://doi.org/10.3390/ijerph18189668








