Abstract
This study explored risk and protective factors for cyberbullying perpetration and examined whether they independently and interactively predicted cyberbullying perpetration. Based on key propositions of micro-level theories of crime and delinquency, we adopted two risk factors, cyberbullying victimization and association with cyberbullying peers, and two protective factors, morality and self-control. Using a sample of South Korean college students (N = 244; 112 women (45.9%), 132 men (54.1%); Mean (age) = 22), we found that the two risk factors were positively associated with cyberbullying perpetration, while only one of the two protective factors, which is morality, had a negative relationship with cyberbullying perpetration. In addition, the two protective factors partially buffered the effects of both risk factors on cyberbullying perpetration. The implications and limitations of these findings were also discussed.
1. Introduction
As the recent influence of the online domain on our daily lives has increased dramatically, new types of crimes or deviant behavior based on online or information technology have increasingly appeared. As one form of deviant online behavior, cyberbullying has been increasing along with the growth in the use of mobile devices and online social networking services. According to a recent nationally representative survey on cyberbullying among approximately five thousand U.S. adolescents [1], as of 2019, 36.5% of students reported cyberbullying victimization during their lifetime, and 17.4% reported that they had been cyberbullied within the previous 30 days. Regarding cyberbullying perpetration, 14.8% of students admitted that they had perpetrated cyberbullying during their lifetime, and 6.3% reported having done so in the last 30 days. In South Korea, a nationwide survey with 6279 respondents, including 4779 students and 1500 adults, reported that 33.5% of respondents experienced cyberviolence in 2019, which increased from 32.8% in 2018 and 26% in 2017 [2].
Several studies indicate that, although cyberbullying is primarily in the form of an indirect type of aggression, for example, verbal aggression, its adverse effects on victims, such as delinquency, depression, suicidal ideation, and other behavioral/mental problems, are as significant as traditional bullying, which can harm victims’ physical bodies and inflict physical distress [3,4,5,6,7,8,9]. Moreover, such negative consequences can potentially be more harmful than those of traditional bullying victimization given that cyberbullying via mobile instant messenger services has become more prevalent recently due to the increasing use of smartphone devices. In other words, because perpetrators and victims are connected nearly 24/7 in such a setting, the environment enables perpetrators to cyberbully victims more frequently and more constantly, which, in turn, may lead to more adverse effects on victims [10,11,12].
Given that, in general, bullying tends to occur in a school context, most cyberbullying studies to date have focused on cyberbullying among school-aged teenagers. However, as online communication has begun to increase not only in the school context but also in other settings in general, cyberbullying can be a social problem not only for adolescents in a school context but also individuals in various social and demographic groups as well. In South Korea, for example, adults report even more cyberviolence experiences compared to adolescents; according to the national survey on cyberviolence in 2019, more than a half of adult respondents (54.7%) reported that they experienced either cyberviolence perpetration or victimization, while only 26.9% of student respondents did. More specifically, 32.5% and 48.5% of adults experienced cyberviolence perpetration and victimization respectively, while 18% and 19% of students reported them, respectively [2]. Nevertheless, cyberbullying and online aggression among adults have rarely been examined to date (however, see [13,14,15]). Therefore, more research on cyberbullying in non-school contexts is needed.
In addition, there is a need for research focusing on examining interactive mechanisms of risk and protective factors for cyberbullying based on theories of crime and deviance although many prior studies have explored probable risk and protective factors for cyberbullying and examined their associations with cyberbullying. Some cyberbullying studies have examined the applicability of theoretical explanations for cyberbullying derived from major criminological theories, such as self-control, learning, and strain theories [14,16,17,18]. However, less attention has been paid to how these theoretical variables interact with one another, that is, whether their effects on cyberbullying decrease or increase under certain conditions (however, see [19,20]). Drawing on prior empirical findings as well as the propositions of major criminological theories, we first examined the significance of several probable risk and protective factors for cyberbullying. We also examined how they interact, more specifically, whether protective factors significantly reduce the criminogenic effects of risk factors on cyberbullying. To do so, we used survey data collected from South Korean college students on their smartphone use and cyberbullying experiences.
1.1. Risk Factors: Cyberbullying Victimization and Cyberbullying Peers
There are several important risk factors for cyberbullying that can be suggested by major criminological theories. These risk factors may include victimization as a source of an individual’s strain (general strain theory) and differential association with delinquent peers (differential association/social learning theories).
According to general strain theory [21], strain derived from negative life events that individuals experience can be a cause of their criminal and delinquent behavior. When people experience negative life events, they are more likely to experience negative affective states, and crime is one coping strategy that they adopt to release their strain and negative emotions. Empirical findings show that some sources of strain, such as conflict with parents or peers and poor academic performance, are closely associated with negative emotions, including anger, depression, frustration, and fear, and these negative affective states eventually lead to delinquency [22,23,24,25]. The proposed criminogenic mechanism can also be applied to cyberbullying. That is, those exposed to the sources of strain may cyberbully others to cope with their strain and negative emotions. The unique attributes of cyberspace, such as the lack of contact and the anonymity, can be perceived as attractive for coping with one’s stress and negative emotions. For example, Patchin and Hinduja [17] found that both strain and negative emotions, such as anger and frustration, were significantly associated with cyberbullying as well as traditional bullying.
In terms of the effects of strain, Agnew [22,25,26] suggested that some types of strain are more criminogenic than others, particularly when they are seen as unjust, high in magnitude (e.g., severity, frequency, or duration), associated with low social control, and provide some incentive or pressure for criminal coping. Given these attributes of criminogenic strain, criminal or peer victimization was taken as an example of the criminogenic strain, which is assumed to be more likely to be associated with one’s negative emotions and delinquent coping. Thus, if an individual is victimized, they are likely to feel negative emotions, which, in turn, may lead them to perpetrate cyberbullying as a means of retaliating for their victimization and coping with their negative emotions derived from that victimization. Many cyberbullying studies have consistently reported that criminal or peer victimization is significantly associated with cyberbullying perpetration [7,13,15,27,28,29].
In addition to victimization, the association with cyberbullying peers can be another risk factor. According to differential association/social learning theories [30,31], delinquency is learned by others, especially when they have experiences related to crime or rule violations. As an individual frequently socializes with delinquent peers, he or she learns favorable definitions and techniques of crime from those delinquents, accepts pro-criminal attitudes, and can experience reinforcement of conformity to the delinquent peers and peer groups. These social learning processes may eventually lead the person to become involved in crime and delinquency. Cyberbullying perpetration can thus be encouraged by cyberbullying peers, as it is perceived as cool and rewarded among these delinquent peers.
In line with this proposition, prior studies found that association with delinquent peers was an important predictor of online deviant behavior as well [32,33], and recent cyberbullying studies also reported that the effects of delinquent peers on cyberbullying perpetration were significant [16,18]. Furthermore, because cyberbullying involves verbal and indirect aggression, it tends to be perceived less seriously than other deviant behaviors; hence, it is likely that a favorable definition of cyberbullying is more easily accepted through the social learning mechanism. Therefore, differential association with delinquent peers, including cyber-deviant peers, can also be an important risk factor for cyberbullying perpetration.
1.2. Protective Factors: Morality and Self-Control
In addition to risk factors for cyberbullying, protective factors for cyberbullying must also be discussed that can prevent someone from engaging in cyberbullying offenses despite the individual being exposed to risk factors. These protective factors may be directly associated with a lower risk of committing cyberbullying. In addition, they may also condition the effects of risk factors for cyberbullying, buffering the criminogenic effects of strain and delinquent peers.
One protective factor of cyberbullying is morality. If one’s morality is high, they are less likely to commit cyberbullying. Morality has to do with whether a person perceives crime as an alternative when they are exposed to criminal opportunities. People with a high level of morality believe that crime is never the right approach and cannot be an alternative regardless of pressure and opportunistic temptation to commit crime; thus, morality prevents them from breaking the rules and laws. However, if an individual has weak moral beliefs, crime can be perceived as an alternative when it is seen as attractive [34,35,36]. Research findings also show that the protective effect of morality on criminal and delinquent behaviors is significant [37,38,39]. Cybercrime is also likely to be perceived as an alternative to weak morality [40]. Similarly, some studies have reported that moral attitudes toward cyberbullying are closely related to cyberbullying perpetration [41,42].
An individual’s self-control can be another important protective factor for cyberbullying. Gottfredson and Hirschi’s general theory of crime [43] focuses on the fact that most crimes are committed impulsively and spontaneously. They pointed out that individuals’ self-control as an ability to control immediate gratification and impulsivity was a cause of crime. That is, people with high self-control are more likely to behave with a long-term perspective for achievement and success rather than pursuing immediate gratification and pleasure, which prevents deviant behaviors. The protective role of self-control can also be applied to deviance in cyberspace, and research findings suggest that self-control is an important protective factor for several types of cybercrime [44,45,46]. Because cyberspace provides a setting in which people behave more impulsively without deliberation due to anonymity and the lack of physical contact, it can be more difficult for people with low self-control to manage their temper and impulsive behavior, which may lead them to commit deviant behavior more easily in cyberspace environments. Furthermore, compared to other types of offense, violence is more closely related to impulsivity rather than being behavior based on a deliberated plan. Self-control is thus an important protective factor for cyberbullying, one form of cyberviolence [14,15,47,48].
1.3. Interplay between Risk and Protective Factors for Cyberbullying
Although each of the major theories of crime and delinquency suggests their own risk and protective factors, there is also increasing attention on whether these factors interact. Thus, a factor may have different effects on crime depending on the influence of other factors. Cyberbullying can also be understood by considering the interplay between risk and protective factors, which indicates the conditions that increase the likelihood of cyberbullying perpetration. This approach is based on recent efforts toward theoretical integration focusing on the interplay between risk and protective factors, which has been discussed in general strain theory [22,25] and situational action theory [34,35,36].
According to general strain theory, for instance, strain is suggested to be a cause of crime, but its effect on crime can be moderated by other variables, such as self-control, social bonds, and association with delinquent peers [49,50,51,52]. Situational action theory also suggests that several types of interaction effects can be examined to understand the mechanism of crime, considering that both person and environment interact with one another. For example, associating with delinquent peers indicates an environment in which weak moral rules are justified and even rewarded, but its criminogenic effects may not be identical between those with weak morality and those with strong morality. In other words, an individual’s moral disengagement may enhance the effect of delinquent peers, while it can be buffered by one’s high morality. In addition, it has been reported that the negative effect of criminogenic environments and self-control interact [53,54,55], which is the case for cyber-deviance as well [32]. Therefore, the likelihood of cyberbullying perpetration increases when an individual has delinquent peers and low self-control, while it decreases when their self-control is high.
1.4. Current Focus
The current study thus aims to examine the interactions between risk and protective factors for cyberbullying as well as their independent associations with cyberbullying. Risk factors refer to a necessary condition that directly triggers cyberbullying perpetration, including strain and association with delinquent peers at the initial stage, while the protective factors are an individual’s propensity to reduce the effects of these motivators. Therefore, we can expect that individuals with risk factors for cyberbullying are more likely to cyberbully others, and among the risk group, those with protective factors are less likely to commit cyberbullying than those with no protective factors, as the effects of risk factors are attenuated by the protective factors.
As previously discussed, both cyberbullying victimization and association with cyberbullying peers can be considered risk factors for cyberbullying perpetration, while both morality and self-control can be considered protective factors. Thus, our three research hypotheses are as follows:
Hypothesis 1.
The two risk factors for cyberbullying, cyberbullying victimization and association with cyberbullying peers, predict an increased likelihood of cyberbullying perpetration.
Hypothesis 2.
The two protective factors for cyberbullying, morality and self-control, predict a decreased likelihood of cyberbullying perpetration.
Hypothesis 3.
The two protective factors for cyberbullying buffer the effects of the risk factors for cyberbullying.
2. Participants and Methods
2.1. Particiapants
One of the primary foci in the current study was to examine whether the proposed mechanism, which is the interplay between risk and protective factors for cyberbullying, is applicable to young adults. Therefore, in 2017, we conducted a survey of 266 South Korean college students from seven randomly selected colleges in Seoul, South Korea. Drawing on the quota-sampling method, we recruited participants based on the following criteria: (1) assign 30 to 40 participants to each university and (2) balance the ratios of gender (males to females) and major (the humanities/social sciences to engineering/natural sciences). Out of 266 students, 115 and 143 were women and men, respectively, while eight declined to report their gender. Regarding participants’ majors, 135 selected their majors in the humanities or social sciences, 96 in engineering or natural sciences majors, and 22 in arts or sports. Thirteen participants declined to report their majors. The average age of original participants was approximately 22 years. Through the data-cleaning process, 22 incomplete responses, such as those with missing information regarding gender, age, or cyberbullying perpetration, were excluded; thus, a total of 244 responses were finally used for data analysis. The final sample consists of 132 men (54.1%) and 112 women (45.9%). Their ages ranged from 18 to 27 years, and the average age was 22. For their family socioeconomic status, 125 participants reported that their family held the “middle” socioeconomic status, which is more than the half (51.2%), followed by “high” (30.3%), “low” (11.5%), “extremely high” (4.5%), and “extremely low” (see Table 1).

Table 1.
Descriptive Statistics.
2.2. Measures
Cyberbullying perpetration. Cyberbullying perpetration is the dependent variable of this study. Six items were created and asked based on Willard’s study [56] and the cyber-violence survey conducted by the Korea Internet and Security Agency. Respondents were asked the following: “For the last year, through your smartphone, have you (1) committed verbal abuse against and humiliated someone else, (2) spread rumors about someone else, (3) spread private information about someone else, (4) stalked someone else by continually sending them emails or texts and posting comments on their blogs or Facebook pages, (5) sexually harassed someone else by sending obscene photos and video clips, or (6) ostracized someone else in a group chat room while using mobile instant messengers?” Participants responded to the items with five response options, “not at all”, “once”, “two to three times”, “four to nine times”, and “ten or more times”. Each response was scored from 0 to 4, and the sum of the scores was used (alpha = 0.890).
Cyberbullying victimization. As one of the risk factors, cyberbullying victimization was measured with the same six items as those for cyberbullying perpetration mentioned above, with the items modified to cyberbullying victimization. The same five response options were applied, and the sum of the scores was also used (alpha = 0.811).
Association with cyberbullying peers. The other risk factor, association with cyberbullying peers, was measured with the same six items as those used for cyberbullying perpetration as mentioned above, but the items were modified, asking respondents if they had any cyberbullying peers who were engaged in those offenses and, if so, how many. Five response options were applied: “none”, “one”, “two to three peers”, “four to nine peers”, and “ten or more peers”. Scores from 0 to 4 were assigned to five responses (alpha = 0.867).
Morality. As one of the protective factors, an individual’s morality regarding cyberbullying perpetration was measured with six items related to whether respondents would think that the six forms of cyberbullying perpetration mentioned above are morally wrong. A five-point Likert scale was used, with the responses “strongly disagree” (=1), “disagree” (=2), “neutral” (=3), “agree” (=4), and “strongly agree” (=5), and the sum of the scores for all six items was used (alpha = 0.957).
Self-control. The other protective factor, self-control, was measured using a modified and shortened version of the Grasmick and colleagues’ scale [57]; as applied in a previous study [58], a single indicator was used to measure each of the six aspects of low self-control traits, such as impulsivity, risk-seeking, simple task, physical activity, self-centeredness, and volatile temper; thus, a total of six items were applied, and those six items were measured through a five-point Likert scale, ranging from “strongly disagree” (=1) to “strongly agree” (=5). The scores for the six items were reversed and added (alpha = 0.632) so that the higher the scores, the higher the self-control.
Control variables. Finally, gender, age, and perceived family socioeconomic status were controlled for in all analytic models. For gender, men and women were coded as 0 and 1, respectively. Respondents were asked for the year of birth, which was then recoded as their age. Regarding perceived family socioeconomic status, respondents were also asked to assess their family income and to select a response from among “extremely low” (=1), “low” (=2), “middle” (=3), “high” (=4), and “extremely high” (=5). Table 1 displays the descriptive statistics of the variables in this study.
2.3. Plan of Analysis
To examine the three research hypotheses, we applied three ordinary least square regression models. First, the two risk factors, cyberbullying victimization and cyberbullying peers, were included in Model 1 along with the control variables, such as gender, age, and perceived family socioeconomic status, to examine whether both risk factors independently and significantly increase the likelihood of perpetrating cyberbullying. In Model 2, we then added the two protective factors, morality and self-control, to Model 1 to examine whether both protective factors independently and significantly reduce the likelihood of perpetrating cyberbullying. In Model 3, we created and added four interaction terms using the two risk and two protective factors, (1) cyberbullying victimization * morality, (2) cyberbullying victimization * self-control, (3) association with cyberbullying peers * morality, and (4) association with cyberbullying peers * self-control, to examine the proposed buffering role of protective factors in the associations between risk factors and cyberbullying perpetration. For interaction terms, each risk and protective factor was mean centered to reduce multicollinearity. All statistical analyses were executed using Stata 15.
3. Results
Table 2 shows the three different models for cyberbullying perpetration. In Model 1, the independent associations of the two risk factors with cyberbullying perpetration controlling for sociodemographic variables, including gender, age, and perceived family SES, are reported. As shown in Model 1, both cyberbullying victimization and association with cyberbullying peers significantly increased the likelihood of cyberbullying (p < 0.01). The standardized coefficient of the variable of cyberbullying victimization (B = 0.493) was larger than that of association with cyberbullying peers (B = 0.319), and approximately 59.9% of the variance was explained by the two risk factors and the three control variables (R2 = 0.599).

Table 2.
Ordinary Least Square Regression Models Predicting Cyberbullying Perpetration.
Model 2 includes the two protective factors, morality and self-control, in addition to the variables in Model 1. In Model 2, both risk factors remained significant despite the addition of the two protective factors (p < 0.01), and the standardized coefficient for the variable of cyberbullying victimization (B = 0.482) was also larger than that of association with cyberbullying peers (B = 0.315). Regarding the independent associations of protective factors with cyberbullying perpetration, higher morality was significantly associated with a lower chance of cyberbullying (B = −0.118, p < 0.01), while self-control was not significantly associated with cyberbullying (B = 0.055, ns). The explained variance of the model increased slightly to 61.4% (R2 = 0.614) compared to Model 1.
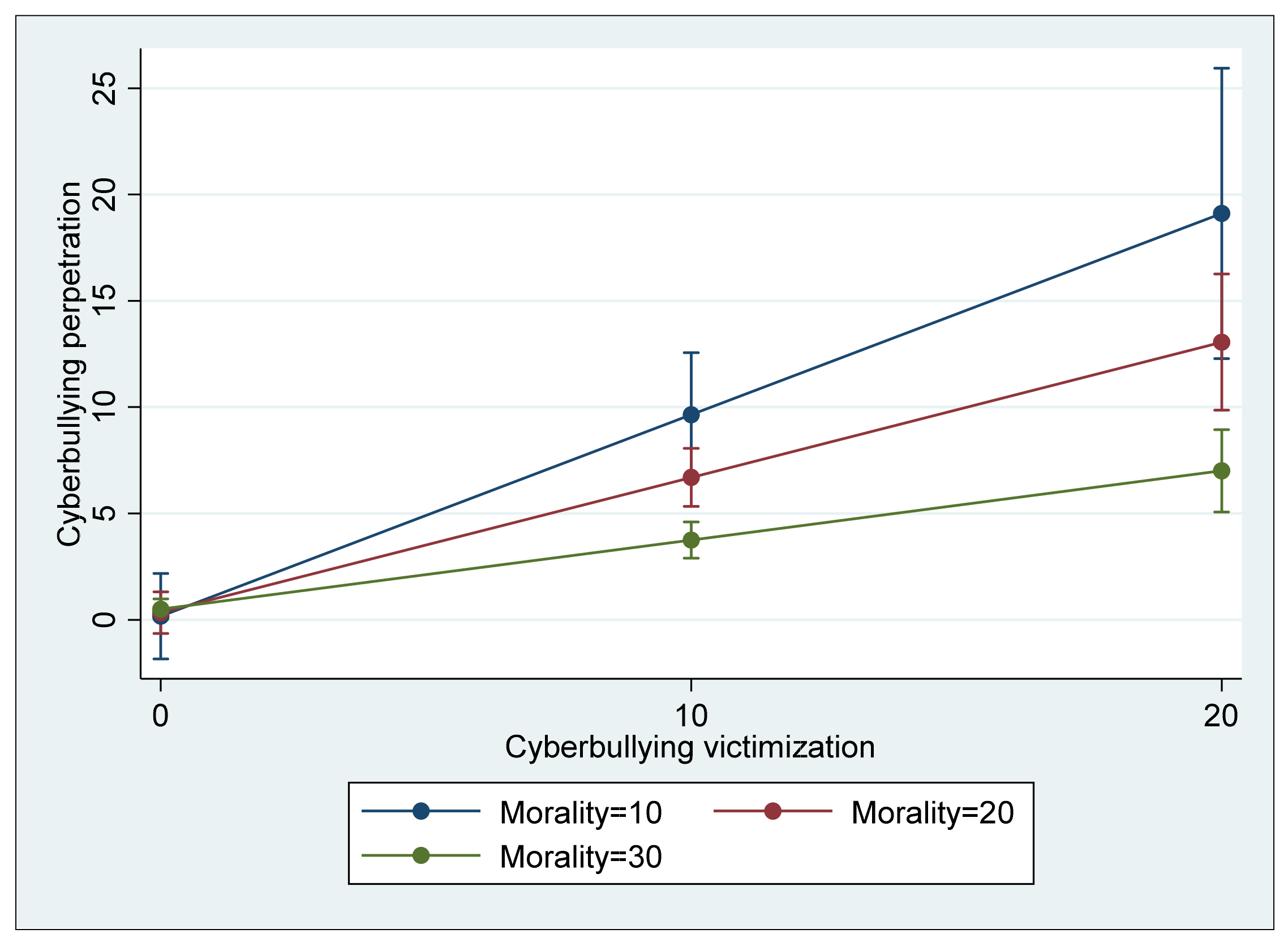
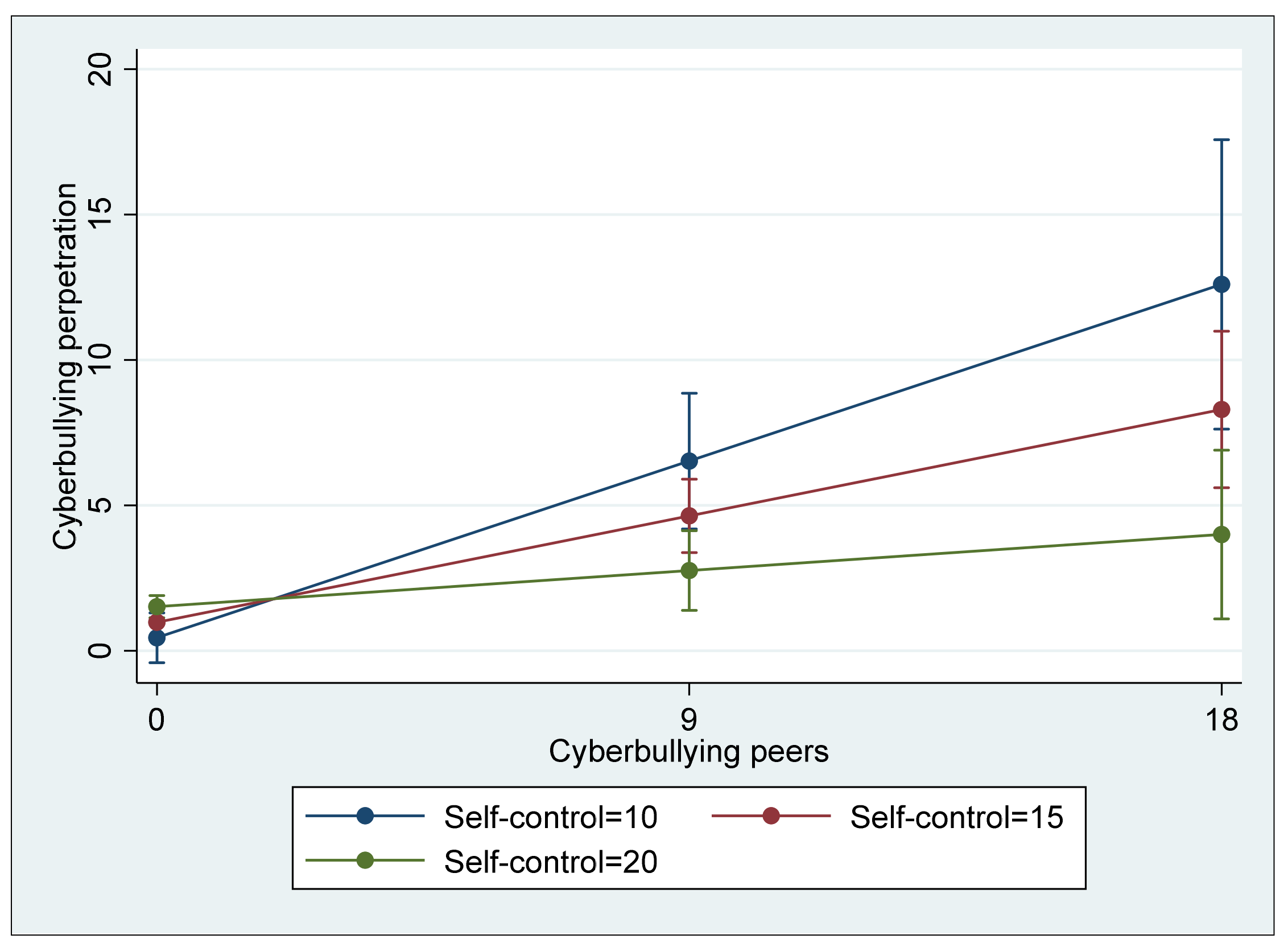
In Model 3, four different interaction terms between the risk and protective factors were included to examine whether the protective factors significantly reduce the effect of risk factors on cyberbullying perpetration. As in the two previous models, cyberbullying perpetration was significantly and positively associated with the two risk factors, cyberbullying victimization (B = 0.427, p < 0.01) and association with cyberbullying peers (B = 0.189, p < 0.01). Similar to Model 2, morality was significantly and negatively associated with cyberbullying (B = −F0.097, p < 0.05); however, self-control was insignificant (B = 0.018, ns). Regarding the four interaction terms, two terms, cyberbullying victimization * morality and association with cyberbullying peers * self-control, showed a negative direction, and they were statistically significant at p < 0.01. That is, morality in addition to its direct association with cyberbullying perpetration significantly buffered the direct effect of cyberbullying victimization on cyberbullying (see Figure 1), and self-control was also a significant moderator that buffered the direct effect of association with cyberbullying peers (see Figure 2) although its direct association with cyberbullying perpetration was not significant. In terms of the explained variance of Model 3, the model accounted for 65.6% of the total variance (R2 = 0.656), a 4.2 percent increase from the explained variance of Model 2, which is a significant increase (ΔR2 = 0.042, F(4,232) = 7.03, p < 0.05).
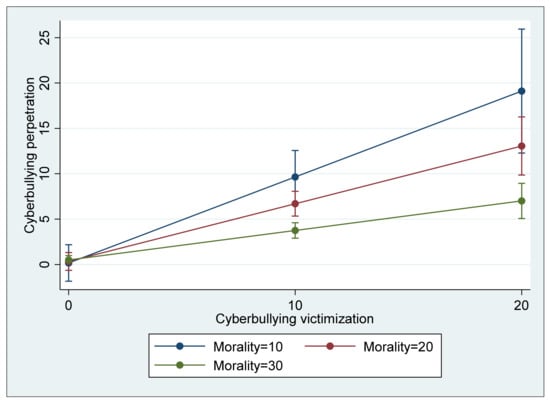
Figure 1.
Interaction between cyberbullying victimization and morality predicting cyberbullying perpetration (with 95% confidence intervals).
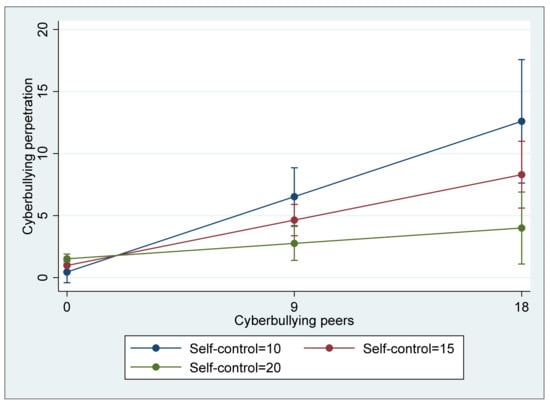
Figure 2.
Interaction between association with cyberbullying peers and self-control predicting cyberbullying perpetration (with 95% confidence intervals).
4. Discussion
The current study focused on examining whether risk and protective factors suggested by some criminological theories account for cyberbullying perpetration among South Korean young adults. Furthermore, this study also examined whether the criminogenic effects of risk factors, cyberbullying victimization, and association with cyberbullying peers were significantly buffered by protective factors, specifically morality and self-control.
Consistent with Hypothesis 1, the two risk factors, cyberbullying victimization and association with cyberbullying peers, were positively correlated with cyberbullying even when controlling for the protective factors as well as other control variables. That is, college students who were more cyberbullied and had more cyberbullying peers were more likely to perpetrate cyberbullying. The findings imply that the suggested mechanisms of deviant behavior derived from general strain theory and differential association/social learning theories can be applied to cyberbullying as well. As suggested by general strain theory, cyberbullying victimization can be perceived as a more direct, unfair, and serious negative life experience for cyberbullying victims compared to other types of negative life events that heighten one’s strain. This, in turn, may lead them to negative affective states such as anger and frustration and eventually result in cyberbullying perpetration. Association with cyberbullying peers can also lead to cyberbullying, as suggested in differential association/social learning theories, as individuals learn a favorable definition and techniques of cyberbullying from their peers, and they want to be recognized and accepted by their cyberbullying peers for their cyberbullying perpetration. This suggests that the risk factors in this study play an important role as a necessary condition for cyberbullying and that we should consider how to decrease the negative influence of cyberbullying victimization and cyberbullying peers, particularly in regard to developing effective policies to reduce cyberbullying perpetration. As general strain theory suggests, for instance, cyberbullying victimization may lead to high levels of strain and negative feelings closely related to deviant behaviors. Thus, implementing counseling programs that can help cyberbullying victims cope with their strain derived from their victimization in legitimate and healthy ways and developing educational programs on effective techniques or tips for cyberbullying prevention are recommended. In addition, we should consider adopting intervention programs designed to block the differential association and social learning processes for those who reported associating with cyberbullying peers as well as for their cyberbullying peers.
In terms of Hypothesis 2, our findings indicate that only one of the protective factors, morality, had a significantly negative relationship with cyberbullying perpetration, while the other one, self-control, did not have a significant association with the dependent variable. In other words, college students with higher morality on cyberbullying were less likely to perpetrate cyberbullying, but their levels of self-control seemed to be irrelevant to preventing their cyberbullying behavior or, at least, its independent association. Regarding morality, young adults who believed that cyberbullying was wrong were less likely to perpetrate cyberbullying regardless of variations in other risk factors, such as cyberbullying victimization and association with cyberbullying peers. Thus, we can see the possibility that the protective mechanism of moral belief may be applicable to cyberbullying as well as being an important protective factor for other forms of delinquency. In terms of the insignificancy of self-control, it may imply that the expected protective mechanism of self-control is not applicable to cyberbullying perpetration. That is, self-control is expected to prevent many forms of delinquency as it allows individuals to deliberate and pursue long-term consequences and goals rather than seeking after short-term gratification or immediate pleasure that can be fulfilled by delinquency. Therefore, the insignificant association between self-control and cyberbullying may be partially derived from how serious people would perceive cyberbullying in that cyberbullying may be taken less seriously compared to other traditional forms of delinquency. In other words, since cyberbullying is often not a form of physical attack or fight, young adults, even those with higher self-control, may perceive it as a minor or trivial deviance that rarely ensues any adverse consequences, such as official punishment and informal social disadvantages. Thus, some educational programs targeting people’s perception of cyberbullying may be recommended, for example, for those aiming to change their perception that cyberbullying is not trivial and can be more harmful than traditional bullying, and thus, more severe responses should follow.
As for Hypothesis 3, two protective factors, higher morality and higher self-control, were shown to play a moderating role, as expected, partially buffering the criminogenic effect of cyberbullying risk factors. Specifically, it was found that morality buffered the effect of cyberbullying victimization on cyberbullying perpetration, while self-control played a role in attenuating the effect of association with cyberbullying peers. From the perspective of criminological theories, this is consistent with the aspect that is emphasized in the integrated theories of crime, such as general strain theory and situational action theory: an individual’s criminal behavior can be better explained through the interactions between risk factors derived from environmental and contextual settings and protective factors based on the individual’s traits. That is, the mechanisms of an individual’s criminal behavior can be specified as depending on the circumstances/context and individual traits that cause an increase or decrease in the likelihood of one’s involvement in crime. Although cyberbullying is often committed by those who were cyberbullied themselves because their victimization can be a source of criminogenic strain, the possibility of being involved in cyberbullying can be minimized when a cyberbullying victim has a strong moral belief that cyberbullying others is wrong, as it buffers the criminogenic effect of strain derived from his or her cyberbullying victimization. In addition, although association with cyberbullying peers increases the likelihood of cyberbullying perpetration, it can also be decreased when an individual with cyberbullying peers has a high level of self-control, which is an individual’s ability to restrain their impulsive behavior in regard to immediate or short-term gratification, such as cyberbullying, as it can be a means to immediately reduce their stress given that self-control buffers the criminogenic effect of association with cyberbullying peers. These findings have both practical and theoretical implications. Regarding an effective future response to cyberbullying perpetration, although some policies that help potential perpetrators not to be exposed to the risk factors should be prioritized, it is also important to consider policies that strengthen one’s traits related to morality, conscience, deliberation, and self-constraint. For instance, we should consider providing more resources for educational programs on cyber ethics, which is expected to enhance one’s morality in cyberspace. In addition, we should also consider expanding programs or interventions that help parents provide their children with effective parenting with affection, consistency, and discipline, which is eventually associated with children’s development of self-control.
5. Conclusions
The current study found that the two proposed risk factors, cyberbullying victimization and association with cyberbullying peers, were significantly and positively related to cyberbullying perpetration, while only one of the two proposed protective factors, morality, was significantly and negatively associated with cyberbullying perpetration as expected. Self-control was not a significant protective factor. As for the proposed buffering role of protective factors, our findings partially supported it. Morality successfully attenuated the criminogenic effect of cyberbullying victimization but not for that of association with cyberbullying peers. On the other hand, self-control significantly buffered the effect of cyberbullying peers, while it did not play a buffering role for the relationship between cyberbullying victimization and cyberbullying perpetration. Our findings show that not only those risk and protective factors but their interactions as well play an important role in predicting cyberbullying perpetration even in the South Korean context and among young adults. Given that cyberviolence perpetrated by adults is even more prevalent than that by adolescents in South Korea [2], the findings of the present study may be considered when developing more effective strategies for cyberbullying prevention.
The limitations of the current study should also be discussed. First, because the data used in this study are cross-sectional, it is difficult to examine the causality of the cyberbullying perpetration mechanism suggested in this study. Although it was found that some risk and protective factors were influential and some of the interactions between both risk and protective factors were significant, as suggested by theories of crime and delinquency, it is also possible that involvement in cyberbullying affects cyberbullying victimization and association with cyberbullying peers rather than the opposite direction hypothesized in this study. Thus, future studies applying longitudinal data are needed to examine the causal mechanism by which these risk and protective factors and their interactions precede cyberbullying perpetration.
Second, although the present study shows the results of non-Western young adults, who have been relatively less studied to date, which is the strength of the current study, the features of the participants in this study may have some limitations related to external validity. That is, because the participants only included college students who were actively enrolled at seven colleges in Seoul, South Korea, it is not representative of South Korea’s entire population of young adults. In other words, the sample did not include groups such as those who did not live in Seoul and those who did not go to college. Thus, the theoretical implications of the current study may be limited, and the policy implications may not be applicable to these groups who were excluded from the sample. Therefore, we anticipate future studies with more representative samples, particularly for non-Western young adults.
Author Contributions
Writing—original draft, S.-S.L. and H.S.; writing—review and editing, S.-S.L., H.S. and J.H.P. All authors have read and agreed to the published version of the manuscript.
Funding
The authors declare no funding.
Institutional Review Board Statement
The study was conducted according to the guidelines of the Declaration of Helsinki and approved by the Institutional Review Board of Soongsil University (ssu-202109-HR-354-1).
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Hinduja, S.; Patchin, J.W. Cyberbullying Identification, Prevention, and Response. 2021. Available online: https://cyberbullying.org/Cyberbullying-Identification-Prevention-Response-2021.pdf (accessed on 16 December 2021).
- National Information Society Agency (NIA). 2019 Cyberviolence Report. 2019. Available online: https://www.korea.kr/common/download.do?tblKey=EDN&fileId=192732636 (accessed on 16 December 2019).
- Bonanno, R.A.; Hymel, S. Cyber Bullying and Internalizing Difficulties: Above and Beyond the Impact of Traditional Forms of Bullying. J. Youth Adolesc. 2013, 42, 685–697. [Google Scholar] [CrossRef] [PubMed]
- Hay, C.; Meldrum, R. Bullying victimization and adolescent self-harm: Testing hypotheses from general strain theory. J. Youth Adolesc. 2010, 39, 446–459. [Google Scholar] [CrossRef]
- Hinduja, S.; Patchin, J.W. Offline consequences of online victimization: School violence and delinquency. J. Sch. Violence 2007, 6, 89–112. [Google Scholar] [CrossRef]
- Hinduja, S.; Patchin, J.W. Bullying, cyberbullying, and suicide. Arch. Suicide Res. 2010, 14, 206–221. [Google Scholar] [CrossRef] [PubMed]
- Kowalski, R.M.; Giumetti, G.W.; Schroeder, A.N.; Lattanner, M.R. Bullying in the digital age: A critical review and meta-analysis of cyberbullying research among youth. Psychol. Bull. 2014, 140, 1073–1137. [Google Scholar] [CrossRef]
- Ramos Salazar, L. Cyberbullying Victimization as a Predictor of Cyberbullying Perpetration, Body Image Dissatisfaction, Healthy Eating and Dieting Behaviors, and Life Satisfaction. J. Interpers Violence 2021, 36, 354–380. [Google Scholar] [CrossRef]
- Smokowski, P.R.; Evans, C.B.R.; Cotter, K.L. The Differential Impacts of Episodic, Chronic, and Cumulative Physical Bullying and Cyberbullying: The Effects of Victimization on the School Experiences, Social Support, and Mental Health of Rural Adolescents. Violence Vict. 2014, 29, 1029–1046. [Google Scholar] [CrossRef]
- Hinduja, S.; Patchin, J.W. Bullying Beyond the Schoolyard: Preventing and Responding to Cyberbullying, 2nd ed.; Corwin: Thousands Oaks, CA, USA, 2014. [Google Scholar]
- Kowalski, R.M.; Limber, S.P.; Agatston, P.W. Cyberbullying: Bullying in the Digital Age, 2nd ed.; Wiley-Blackwell: Malden, MA, USA, 2012. [Google Scholar]
- Slonje, R.; Smith, P.K.; Frisén, A. The nature of cyberbullying, and strategies for prevention. Comput. Hum. Behav. 2013, 29, 26–32. [Google Scholar] [CrossRef]
- Gibb, Z.G.; Devereux, P.G. Who does that anyway? Predictors and personality correlates of cyberbullying in college. Comput. Hum. Behav. 2014, 38, 8–16. [Google Scholar] [CrossRef]
- Lianos, H.; McGrath, A. Can the General Theory of Crime and General Strain Theory Explain Cyberbullying Perpetration? Crime Delinq. 2018, 64, 674–700. [Google Scholar] [CrossRef] [Green Version]
- Marcum, C.D.; Higgins, G.E.; Freiburger, T.L.; Ricketts, M.L. Exploration of the Cyberbullying Victim/Offender Overlap by Sex. Am. J. Crim. Justice 2014, 39, 538–548. [Google Scholar] [CrossRef] [Green Version]
- Li, C.K.W.; Holt, T.J.; Bossler, A.M.; May, D.C. Examining the Mediating Effects of Social Learning on the Low Self-Control—Cyberbullying Relationship in a Youth Sample. Deviant Behav. 2016, 37, 126–138. [Google Scholar] [CrossRef]
- Patchin, J.W.; Hinduja, S. Traditional and nontraditional bullying among youth: A test of general strain theory. Youth Soc. 2011, 43, 727–751. [Google Scholar] [CrossRef]
- Shadmanfaat, S.M.; Howell, C.J.; Muniz, C.N.; Cochran, J.K.; Kabiri, S.; Fontaine, E.M. Cyberbullying perpetration: An empirical test of social learning theory in Iran. Deviant Behav. 2020, 41, 278–293. [Google Scholar] [CrossRef]
- Kabiri, S.; Shadmanfaat, S.M.S.; Choi, J.; Yun, I. The impact of life domains on cyberbullying perpetration in Iran: A partial test of Agnew’s general theory of crime. J. Crim. Justice 2020, 66, 101633. [Google Scholar] [CrossRef]
- Song, H.; Lee, S.S. Motivations, Propensities, and Their Interplays on Online Bullying Perpetration: A Partial Test of Situational Action Theory. Crime Delinq. 2020, 66, 1787–1808. [Google Scholar] [CrossRef]
- Agnew, R. Foundation for a general strain theory of crime and delinquency. Criminology 1992, 30, 47–88. [Google Scholar] [CrossRef]
- Agnew, R. General strain theory: Current status and directions for further research. In Taking Stock: The Status of Criminological Theory; Cullen, F.T., Wright, J.P., Blevins, K.R., Eds.; Transaction: New Brunswick, NJ, USA, 2006; pp. 101–123. [Google Scholar]
- Agnew, R.; White, H.R. An Empirical Test of General Strain Theory. Criminology 1992, 30, 475–500. [Google Scholar] [CrossRef]
- Piquero, N.L.; Sealock, M.D. Generalizing general strain theory: An examination of anoffending population. Justice Q. 2000, 17, 449–484. [Google Scholar] [CrossRef]
- Agnew, R. Pressured Into Crime: An Overview of General Strain Theory; Roxbury: Los Angeles, CA, USA, 2006. [Google Scholar]
- Agnew, R. Building on the foundation of general strain theory: Specifying the types of strain most likely to lead to crime ands delinquency. J. Res. Crime Delinq. 2001, 38, 319–361. [Google Scholar] [CrossRef] [Green Version]
- Wright, M.F.; Li, Y. The Association Between Cyber Victimization and Subsequent Cyber Aggression: The Moderating Effect of Peer Rejection. J. Youth Adolesc. 2013, 42, 662–674. [Google Scholar] [CrossRef] [PubMed]
- Ybarra, M.L.; Mitchell, K.J. Youth engaging in online harassment: Associations with caregiver-child relationships, internet use, and personal characteristics. J. Adolesc. 2004, 27, 319–336. [Google Scholar] [CrossRef]
- Ybarra, M.L.; Mitchell, K.J. Prevalence and Frequency of Internet Harassment Instigation: Implications for Adolescent Health. J. Adolesc. Heal. 2007, 41, 189–195. [Google Scholar] [CrossRef] [PubMed]
- Akers, R.L. Deviant Behavior: A Social Learning Approach, 3rd ed.; Wadsworth: Belmont, CA, USA, 1985. [Google Scholar]
- Sutherland, E. Principles of Criminology; J.B.Lippincott: Philadelphia, PA, USA, 1947. [Google Scholar]
- Higgins, G.E.; Fell, B.D.; Wilson, A.L. Low self-control and social learning in understanding students’ intentions to pirate movies in the United States. Soc. Sci. Comput. Rev. 2007, 25, 339–356. [Google Scholar] [CrossRef]
- Skinner, W.F.; Fream, A.M. A Social Learning Theory Analysis of Computer Crime among College Students. J. Res. Crime Delinq. 1997, 34, 495–518. [Google Scholar] [CrossRef]
- Wikström, P.-O.H. Explaining crime as moral actions. In Handb. Sociol. Moral.; Hitlin, S., Vaisey, S., Eds.; Springer: New York, NY, USA, 2010; pp. 211–239. [Google Scholar]
- Wikström, P.-O.H. Crime as Alternative: Towards a Cross-Level Situational Action Theory of Crime Causation. In Beyond Empiricism: Institutions and Intentions in the Study of Crime; McCord, J., Ed.; Transaction: New Brunswick, NJ, USA, 2004; pp. 1–38. [Google Scholar]
- Wikström, P.-O.H. Why crime happens: A situaitonal action theory. In Anal. Sociol. Actions Networks; Manzo, G., Ed.; Wiley-Blackwell: Chichester, UK, 2014; pp. 74–94. [Google Scholar] [CrossRef]
- Antonaccio, O.; Tittle, C.R. Morality, self-control, and crime. Criminology 2008, 46, 479–510. [Google Scholar] [CrossRef]
- Brauer, J.R.; Tittle, C.R. When Crime is not an Option: Inspecting the Moral Filtering of Criminal Action Alternatives. Justice Q. 2017, 34, 818–846. [Google Scholar] [CrossRef]
- Kroneberg, C.; Heintze, I.; Mehlkop, G. The interplay of moral norms and instrumental incentives in crime causation. Criminology 2010, 48, 259–294. [Google Scholar] [CrossRef]
- Joinson, A.N. Understanding the Psychology of Internet Behavior: Virtual Worlds, Real Lives; Palgrave Macmillan: London, UK, 2003. [Google Scholar]
- Bussey, K.; Fitzpatrick, S.; Raman, A. The Role of Moral Disengagement and Self-Efficacy in Cyberbullying. J. Sch. Violence 2015, 14, 30–46. [Google Scholar] [CrossRef]
- Perren, S.; Gutzwiller-Helfenfinger, E. Cyberbullying and traditional bullying in adolescence: Differential roles of moral disengagement, moral emotions, and moral values. Eur. J. Dev. Psychol. 2012, 9, 195–209. [Google Scholar] [CrossRef]
- Gottfredson, M.R.; Hirschi, T. A General Theory of Crime; Stanford University Press: Stanford, CA, USA, 1990. [Google Scholar]
- Buzzell, T.; Foss, D.; Middleton, Z. Explaining use of online pornography: A test of self-control theory and opportunities for deviance. J. Crim. Justice Pop. Cult. 2006, 13, 96–116. [Google Scholar]
- Higgins, G.E. Can low self-control help with the understanding of the software piracy problem? Deviant Behav. 2005, 26, 1–24. [Google Scholar] [CrossRef]
- Malin, J.; Fowers, B.J. Adolescent self-control and music and movie piracy. Comput. Hum. Behav. 2009, 25, 718–722. [Google Scholar] [CrossRef]
- Donner, C.M.; Marcum, C.D.; Jennings, W.G.; Higgins, G.E.; Banfield, J. Low self-control and cybercrime: Exploring the utility of the general theory of crime beyond digital piracy. Comput. Hum. Behav. 2014, 34, 165–172. [Google Scholar] [CrossRef]
- Kim, J.; Song, H.; Jennings, W.G. A Distinct Form of Deviance or a Variation of Bullying? Examining the Developmental Pathways and Motives of Cyberbullying Compared with Traditional Bullying in South Korea. Crime Delinq. 2017, 63, 1600–1625. [Google Scholar] [CrossRef]
- Agnew, R.; Brezina, T.; Wright, J.P.; Cullen, F.T. Strain, Personality traits, and Delinquency: Extending General Strain Theory. Criminology 2002, 40, 43–72. [Google Scholar] [CrossRef]
- Cullen, F.T.; Unnever, J.D.; Hartman, J.L.; Turner, M.G.; Agnew, R. Gender, bullying victimization, and juvenile delinquency: A test of general strain theory. Vict. Offenders 2008, 3, 346–364. [Google Scholar] [CrossRef]
- Mazerolle, P.; Maahs, J. General strain and delinquency: An anternative examination of conditioning influences. Justice Q. 2000, 17, 753–788. [Google Scholar] [CrossRef]
- Morash, M.; Moon, B. Gender differences in the effects of strain on the delinquency of South Korean youth. Youth Soc. 2007, 38, 300–321. [Google Scholar] [CrossRef]
- Hirtenlehner, H.; Pauwels, L.; Mesko, G. Is the criminogenic effect of exposure to peer delinquency dependent on the ability to exercise self-control? Results from three countries. J. Crim. Justice 2015, 43, 532–543. [Google Scholar] [CrossRef]
- Meldrum, R.C.; Miller, H.V.; Flexon, J.L. Susceptibility to Peer Influence, Self-Control, and Delinquency. Sociol. Inq. 2013, 83, 106–129. [Google Scholar] [CrossRef]
- Ousey, G.C.; Wilcox, P. The interaction of antisocial propensity and life-course varying predictors of delinquent behavior: Differences by method of estimation and implications for theory. Criminology 2007, 45, 313–354. [Google Scholar] [CrossRef]
- Willard, N.E. Cyberbullying and Cyberthreats: Responding to the Challenge of Online Social Aggression, Threats, and Distress; Research Press: Champaign, IL, USA, 2007. [Google Scholar]
- Grasmick, H.G.; Tittle, C.R.; Bursik, R.J.; Arneklev, B.J. Testing the Core Empirical Implications of Gottfredson and Hirschi’s General Theory of Crime. J. Res. Crime Delinq. 1993, 30, 5–29. [Google Scholar] [CrossRef]
- Gunter, W.D.; Bakken, N.W. The many measurements of self-control: How re-operationalized self-control compares. Eur. J. Criminol. 2012, 9, 309–322. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).