Abstract
The smart meters in electricity grids enable fine-grained consumption monitoring. Thus, suppliers could adjust their tariffs. However, as smart meters are deployed within the smart grid field, authentication and key establishment between smart grid parties (smart meters, aggregators, and servers) become an urgency. Besides, as privacy is becoming a big concern for smart meters, smart grid parties are reluctant to leak their real identities during the authentication phase. In this paper, we analyze the recent authentication schemes in smart grids and other applied fields, and propose an anonymous authentication and key establishment scheme between smart grid parties: FAuth. The proposed scheme is based on bilinear maps and the computational Diffie–Hellman problem. We changed the way the smart meter parties registered at Key Generation Center, making the proposed scheme robust against various potential attacks that could be launched by the Key Generation Center, as the scheme could avoid the private key of the smart meter parties from leaking to the Key Generation Center. Besides, the proposed scheme reduced the computational load, both at the smart meter side and at the aggregator side, which make it perfectly suitable for computation-constrained devices. Security proof results show the proposed scheme is secure under the BAN logic and random oracle model.
1. Introduction
The internet of things is now applied into many parts of our daily life. Smart meters are one of these. The European Commission has formulated the goal to provide 80% of all households with smart electricity meters by the year 2020 [1]. As a smart meter can report its measurements periodically to the utility supplier instantaneously, the utility supplier can dynamically change the supplement according to the reported data. With more and more smart meters applied, authentication and key establishment have become an important issue in the smart grid area. According to Sanjab et al. (2016) [2], “a robust authentication protocol is needed while communicating between smart grid parties.” According to the Report on Workshop on Security & Privacy in IoT of Europe (2016) [3], “identification and authentication of end-devices, gateways and servers as very first requirement.” is considered to help manage scalability, evolutivity and risk assessment of the overall IoT system. Authentication enables the parties in the smart grid to authenticate each other and establish a shared key. But as privacy becomes a concern, people start trying to find ways that smart grid parties could authenticate each other without leaking their identity to adversaries.
First, as a smart meter is installed beside the house of inhabitants, as stated in [4], “this malicious attacker might be able to forge sensed data such as the amount of electricity usage at this house before sending these forged data back to the corresponding service server.” Passive attacks are easily launched by an attacker, such as eavesdrop attack, and some other attacks launched by the attackers. Authentication and encryption methods should be applied in this scenario.
Second, electricity usage naturally includes personal information of the inhabitants, according to the electricity consumption, it is easy to judge if inhabitants are at home or not, and with fine-grained electricity consumption reporting instantly, privacy-sensitive information, regarding which appliances are active, can be obtained. Also, by data mining or static methods, according to the electricity consumption, the status and income of the inhabitants may be revealed, so anonymous authentication is needed; in FAuth, the identity of the smart meter is encrypted before sending.
Third, as smart meters have constrained computability compared to aggregators, it is necessary to try to lower the computation cost at the smart meter side; in FAuth, the computation cost at the smart meter side is the lowest compared to other schemes.
So, in this paper, we proposed an anonymous authentication scheme based on bilinear maps and the computational Diffie–Hellman problem: FAuth, which totally meets the above three requirements as stated. The contributions of this paper include the following three points:
- We changed the way smart meter parties register at the Key Generation Center, detailed in Section 6.3, and prevent the Key Generation Center from knowing the private key of the smart grid parties. Thus, some security problems are prevented, detailed in Section 8.
- Based on the methods of Tsai-Lo [4] and Odelu [5], we proposed FAuth, and the comparison results show that the proposed scheme greatly reduced the computation costs of smart grid parties at the authentication phase.
- Security analyses of BAN logic and random oracle model are conducted to show that the proposed scheme is safe.
This paper is organized as follows: We discuss the related works in Section 2. Some preliminary knowledge is described in Section 3. A review of Odelu’s scheme is presented in Section 4. The security limitations of Odelu’s scheme are discussed at Section 5. The scheme: FAuth is proposed in Section 6. We conduct two separate security analyses using BAN logic and random oracle model in Section 7 and Section 8. We provide a comparison with the related schemes in Section 9. A brief introduction of the I3RES Project is given in Section 10. We conclude the paper with a summary of the contributions in Section 11.
2. Related Work
Tsai-Lo and Nai-Wei Lo proposed an authentication scheme based on bilinear map, and the computational Diffie–Hellman problem [4]. The advantage of their scheme is that a smart meter can be quickly authenticated without involving the trust anchor because of the two identity based cryptosystems. Odelu et al. (2016) provide a scheme with security functionalities, including strong credentials’ privacy and SK-security under the CK-adversary model [5]. Their scheme provided a variety of security functionalities, and reduced computational costs for both the smart meter and service provider. Xia and Wang proposed a key distribution scheme for smart grid network [6]. They used a trusted third party which can conduct key revocation, and the third party can be easily duplicated in case power outages occur. Jo et al. (2016) proposed efficient and privacy-preserving protocols for a smart grid in [7]. The proposed protocols were shown to be robust against attacks of data collection unit (DCU) compromise attacks. Further, in their protocol, the response of messages were more efficient by the adoption of the distributed verification method.
Zhang et al. (2017) proposed a new, efficient, certificate-less, generalized signcryption (CLGSC) scheme, and a lightweight and robust security-aware (LRSA) D2D-assist data transmission protocol that was proposed based on CLGSC [8]. Their security analysis demonstrated that the LRSA protocol can achieve data confidentiality and integrity, mutual authentication, contextual privacy, anonymity, and so on. Their experimental results show that the LRSA protocol outperforms the existing schemes in terms of computational and communication overhead. Liu et al. (2014) proposed a certificate-less signature scheme based on bilinear pairings [9]. And based on this scheme, they proposed two certificate-less remote anonymous schemes for wireless body area networks. A client could anonymously be authenticated and establish a key with the application provider. He et al. (2016) provided an improved scheme where the application provider does not have to store any information for the authenticating users [10]. Li et al. (2013) also proposed an authentication scheme based on bilinear pairings [11]. Tsai-Lo and Lo proposed a new anonymous authentication scheme based on nonce and bilinear pairing [12], which supports mutual authentication, key exchange, user anonymity, and user untraceability. It is claimed that their scheme withstands all major security threats and meets general security requirements. In addition, no verification table is required to be implemented at service providers or the trusted SCG service.
He et al. (2017) proposed a data aggregation scheme [13] that can thwart internal attacks for the smart grid environment. They claimed their scheme is provably secure and can meet the security requirements, and incurs lower communication costs.
H. Xiong briefly described the work of [9] in [14], and according to their opinion, certificate managements, scalability, and forward security are the three parts that can be improved in the scheme of the work of [9]. In his scheme, only registered users can authenticate each other and build a shared key, besides, this shared key is only known by the two registered users and the network manager would not know this shared key. Also, according to the public information transmitted between the two users, an adversary is unable to learn this shared key. However, in this scheme, the server does not check the validity of incoming users. Li and J. Hong proposed a modified BDCPS scheme [15], which is an efficient certificate-less access control for wireless body area networks. In this scheme, every user first generates a public key pair (), and then registers at a key generating center (KGC), to get a partial private key . After the user gets this partial private key, he can generate his public key pair (). As only registered user could generate this public key pair, this public key pair can be used as a measure to test if a user is legal or not, as only the public key is transferred, so the identity of the user is hidden.
Liu et al. (2016) proposed an authentication scheme [16] which could well protect the identity and privacy of the user, while the scheme is very cost-effective compared to [9]. Islam and Khan proposed a partial public key method [17], where a user registers at the server several times in order to get more than one authentication keys, then the user uses different keys for authentication to achieve anonymity. He et al. (2015) applied the partial key concept to the vehicular ad hoc networks, and proposed an efficient identity-based privacy preserving authentication scheme, and their scheme enables batch verification of multiple messages [18]. Further, they applied a similar method into public auditing in cloud-based body area networks in [19], by D. He, S. Zeadally, and L. Wu.
Porambage et al. (2014) proposed a pervasive authentication protocol and key establishment scheme [20], their scheme is also based on a partial public key method. But in their scheme, is a fixed value, so the user in this scheme could be tracked by . The registration phase of FAuth is similar to those of [13,20].
Zhang et al. (2014) proposed a scheme based on ECC public key infrastructure [21], but they do not take into account the anonymity of the user, as the user names are sent directly. In [22], Tu et al. (2015) improved the scheme [21], but the username is sent without processing, too. Odelu et al. (2015) [23] proposed an authentication scheme between two users, with the help of a server node, the scheme is also based on a partial public key by elliptic curve cryptography (ECC). They also proposed a similar authentication scheme between two users, but their scheme does not need there to be a trusted server to help the two users to finish the authentication process, as the scheme uses the ECC based El-Gammal type signature [24].
The scheme in [25] is the first one that defines a formal model to capture the feature of user untraceability, and that highlights the damaging threat of de-synchronization attacks on privacy-preserving two-factor authentication schemes.
The schemes in [26,27,28,29], and [30] use elliptic curve cryptography (ECC) to generate a shared key with the server. The scheme in [30] suffers from impersonation attacks in the registration phase, offline password guessing attacks in the login phase, and offline password guessing attacks in the password change phase. The schemes in [31,32] provide a lightweight scheme based on ECC, but they do not protect the privacy of the user, since the user names are sent transparently. Huang et al. (2015) provides an ECC-based authentication scheme between user and server [33], while their scheme is found to be vulnerable to inner side impersonate attacks by [34] by Chaudhry et al. (2016). Li et al. (2015) [35] provide an authentication between user and cloud server, as they use a symmetric key as a way of authentication, and an asymmetric key to establish the shared key, but the of a user is transferred transparently, so a user could be tracked. The method in [11] is similar to [35], only their shared key is based on a symmetric key, and the scheme in [11] suffers from inner side user attacks, as they shared a same key. Jiang et al. (2016) built their scheme based on the knowledge of chaotic maps [27].
The proposed scheme: FAuth is an improvement of the schemes of [4,5,36], which specially focused on the smart meter authentication problem. The second scheme of [36] could not provide smart meter anonymity at the authentication phase, and suffers from “unknown key share attacks” according to [4]. According to [5], scheme [4] fails to protect the smart secret credentials if the ephemeral secret is revealed as an adversary. The registration manner of smart meters and aggregators in the proposed scheme are changed to provide better security endurance, compared to [5]; besides, a detailed computation of computation and communication costs were conducted, and all the results show the proposed scheme is more suitable for smart grid environments.
3. Preliminary
In this section, an introduction to basic knowledge bilinear maps and the computational Diffie–Hellman problem is introduced.
3.1. Bilinear Map
Central to pairing-based cryptosystems is a bilinear nondegenerate map, originally given as , where , are both cyclic groups of prime order , and the discrete log problem is hard in . is a cyclic additive group, and is a cyclic multiplicative group. Bilinear maps have the following properties:
- Bilinearity: for , for .
- Computability: there is an efficient algorithm to compute , for .
- Non-degeneracy: with , where is the multiplicative identity of .
3.2. Computational Diffie-Hellman Problem
Given , for . It is infeasible to compute .
4. Review of Odelu’s Scheme
In this section, the authentication scheme proposed by Vanga Odelu, Ashok Kumar Das, Mohammad Wazid, and Mauro Conti for smart grids is evaluated. Some notions used in their scheme are listed in Table 1.

Table 1.
Symbols used in Odelu’s scheme.
4.1. Setup Phase of Odelu’s Scheme
In this phase, which is a trust key generation center, sets up the parameters using the following steps:
- Step 1
- chooses bilinear map groups with a prime order, and generators , and , where is the bilinear map.
- Step 2
- chooses the cryptographic one way hash functions , , where , and is a constant and it is also fixed during the setup phase as in [37], which is based on the input length of an encryption algorithm used in our authentication and key agreement phase. Note that in their proposed scheme, is calculated such that bits, where denotes the bit length of string .
- Step 3
- then chooses its master private key and computes the corresponding public key .
- Step 4
- finally, declares the public parameter .
4.2. Smart Meter Registration of Their Scheme
First, we have to make it clear that the registration phase is under a secure channel. Suppose a smart meter wants to register with the . sends its identity, , to via secure channel. After receiving the identity , conducts the following steps:
- Selects a random number ,
- Computes (El-Gamal type signature on )
- Sends to
When smart meter receives , it stores them in the tamper-proof module. The whole process is depicted in Table 2.

Table 2.
Registration phase of smart meter in Odelu’s scheme.
4.3. Service Provider Registration of Their Scheme
When a service provider wants to join the system, it has to first register at . sends its identity, , to . After receiving the identity , calculates the private key , and sends to . When smart meter receives , it computes , and stores into the tamper-proof module. The whole process is depicted in Table 3.

Table 3.
Registration phase of service provider in Odelu’s scheme.
4.4. Authentication and Key Establishment Phase of Their Scheme
In the authentication phase of their scheme, smart meter and service provider could authenticate each other without the help of .
- chooses two random numbers , and then computes , , and . sends request message to .
- Upon receiving the message from , derives , using its own private key . Then, it computes . then checks if ; if it does not hold, terminates the session, otherwise, chooses a random number and computes , the session key and , and then sends to .
- After receiving from , computes the session key . Next checks if . If it does not hold, terminates the session. Otherwise, authenticates as a valid target server, and sets as the session key. then computes and sends to .
- Upon receiving , checks if . It this does not hold, terminates the session. Otherwise, confirms that is a legitimate registered smart meter, and agrees with the session key .
Now both and agree on the shared key, , and the information flow is depicted in the following Table 4.

Table 4.
Authentication phase of Odelu’s scheme.
5. Security Limitations of Odelu’s Scheme
In the registration phase of Odelu’s scheme, the private key of the smart meter is , which is generated by , so knows this private key of the smart meter . It is the same with the private key of the service provider . So as knows the private keys of the smart meter parties, although is trust worthy, a curious can launch various attacks.
5.1. Impersonate Attack by
It is obviously that with the private key of smart meters or service provider , could easily impersonate as a smart meter or a service provider .
5.2. Tracked by
Besides, the private key of the smart meter and the service provider are all known by . This means in the authentication phase, the smart meter could be tracked by . For a smart meter, it would send to a service provider , and has the private key of , so could decrypt to get the identity of , which is . In this way, smart meter could tracked by .
6. The Proposed Authentication Protocol for Smart Grid
In this section, an introduction of the structure of the system was given, and then we propose FAuth. A detailed description of the registration phase and the authentication phase is given in this section.
6.1. Structure of the Scheme
The model is depicted in Figure 1. The structure is divided into three layers, the first layer is the server layer, the second layer is the aggregator layer, and the third layer is the smart meter layer, the smart meters report their reading to the aggregator, the aggregator adds all the smart meters’ reading in its range and reports that to the server.
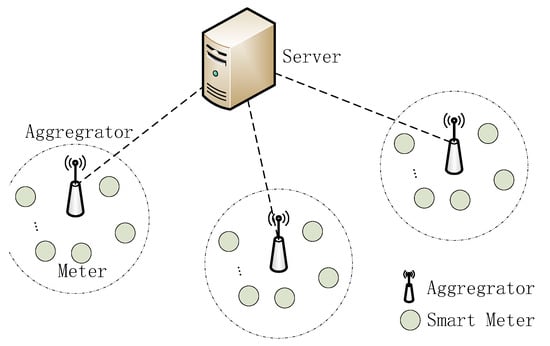
Figure 1.
The structure of the model.
In order for the smart meters and aggregators to authenticate each other, we introduce a Key Generation Center, which works like the Trusted Anchor in [5], which is in charge of the registration of the smart meter and the aggregators.
The abstract structure is depicted in Figure 2. The Key Generation Center is in charge of the key generation for the smart meter parties, the smart meters, and the aggregators, and the server has to register to the KGC before they enter the network.

Figure 2.
The abstract structure of the model.
- All the members of the scheme, i.e., server, smart meter, and aggregator, have to register at KGC to get their public key pairs.
- The aggregator and smart meters have to authenticate each other and build a shared key for the smart meters to report their reading to the aggregator. The same process happens between the aggregator and the server. In this paper, we only analyze the first part, because the mutual authentication process between the aggregator and the server is the same.
The proposed scheme is an anonymous mutual authentication scheme between the smart meter and the aggregator, or the aggregator and the server, and by the proposed scheme, the two parties could build a shared key for farther communication.
6.2. Setup of the Scheme
The setup phase in the proposed scheme is the same as that in [5], as we have discussed in 4.1. generates its public key pair and sends these parameters to all the members of the scheme. The symbols we will use in the next section are summarized in Table 5.

Table 5.
Symbols used in the proposed scheme.
6.3. Registration Phase of Smart Meter
The registration phase of in the proposed scheme is similar to that of the scheme [20], as depicts in Table 6. When a smart meter wants to join, it has to register first. A smart meter with identity first generates a random number . Then, sends the registration request to , and generates a random number, , and calculates , , , . Then, sends back to the smart meter. The smart meter calculates its own private , and public key . Now the registration phase of the smart meter is finished, and the private key of the smart meter is only known by the smart meter itself.

Table 6.
Registration phase of the smart meter.
6.4. Registration Phase of Aggregator
The registration phase of an aggregator, , is the same as with the smart meter , the process is depicts in Table 7. Finally, an aggregator will get a public key pair: private key , and public key .

Table 7.
Registration phase of the aggregator.
6.5. Request and Authentication Phase
Smart meter, , with identity, , first has to perform the following steps to be anonymously authenticated by an aggregator. Only after mutual authentication, can the smart meter then report its reading to the aggregator.
- Smart meter, , with identity, , chooses a random number , and calculates .
- Using the hashed value of to encrypt its identity, , and : .
- Gets the timestamp .
- Calculates the hashed value: .
- Sends Message 1 = {} to the aggregator.
When aggregator receives the data {} from a smart meter, , will conduct the following steps to authenticate the meter :
- Checks the freshness of the , if is not fresh, abandons the message.
- Calculates using its private key .
- Decrypts to get .
- Checks if ; if they are not equal, aborts here.
- Calculates the public key of .
- Chooses a random number .
- Calculates .
- Calculates .
- Calculates .
- Calculates .
- Sends Message 2 = {} to the client .
When smart meter gets the data {}, will do the following steps to authenticate this message.
- 6.
- computes the shared key using its private key : .
- 7.
- checks if ; if they are not equal, aborts here, otherwise calculates ; now has accepted the shared key .
- 8.
- Sends Message 3 = {} to .
When aggregator gets the data {}, will check if ; if they are equal, , accepts the key . Now the smart meter , and aggregator , have authenticated each other and build a shared key. The whole process is depicted in Table 8.

Table 8.
Request and authentication phase of the proposed scheme.
7. Security Analysis Using BAN Logic
A security analysis of the proposed scheme by using Burrows–Abadi–Needham logic (BAN logic) [38] was conducted. With the help of BAN logic, we can determine whether the exchanged information is trustworthy, and secured against eavesdropping. Now we are going to give a brief overview of the BAN logic. First some symbols used in the BAN logic are described in the Table 9, and some primary BAN logic postulates are given in Table 10. We suppose there are only two entities, smart meter , and aggregator , in the scheme.

Table 9.
Symbols of BAN logic.

Table 10.
Some primary BAN logic postulates.
7.1. The Goal of the Proposed Scheme
The goals of the proposed scheme in BAN logic are depicted in the following, and these goals could ensure and agree on the shared key, , between them.
1.
2.
3.
4.
7.2. Idealization of the Message
The messages of the proposed scheme, in idealized form in terms of the messages exchanged, is given in Table 11.

Table 11.
The idealized form of the messages.
7.3. The Initial State Assumptions
In order to prove the proposed scheme, we first have to make the following initial state assumptions:
- A1
- A2
- A3
- A4
- A5
- A6
7.4. The Proof of the Proposed Scheme
7.4.1. Analysis of Message 1
1. According to Message 1, we get:
2. According to the “Elimination of multipart messages” rule and (1), we get:
3. According to the “ introduction rule”, (2), and A4, we get:
4. According to the “Freshness rule”, (3), and A2, we get:
5. According to the “Elimination of multipart messages rule”, and (4), we get:
6. According to the “ elimination rule”, (4), and (3), we get:
7. According to the “Elimination of multipart messages rule”, and (6), we get:
8. According to the “Jurisdiction rule”, (7), and A6, we get:
9. As “” is a random number generated by , we get:
10. According to “#()- promotion rule”, (5), and (9), we get:
11. According to the “ introduction rule”, (10) and (7), we get:
7.4.2. Analysis of Message 2
12. According to Message 2, we get:
13. According to the “Elimination of multipart messages rule”, and (12), we get:
14. According to the “ introduction rule”, (13), and A3, we get:
15. According to “Freshness rule”, (14), and A1, we get:
16. According to the “ rule”, (15), we get:
17. According to the “ elimination rule”, (15), and (14), we get:
18. According to the “Elimination of multipart messages rule”, and (17), we get:
19. According to the “Jurisdiction rule”, (18), and A5, we get:
20. As “” is a random number generated by , we get:
21. According to the “#()- promotion rule”, (16), and (20), we get:
22. According to the “ introduction rule”, (21) and (18) we get:
23. According to the “Elimination of multipart messages rule”, and (17), we get:
7.4.3. Analysis of Message 3
24. According to Message 3 we get:
25. According to the “ introduction rule”, (24), and A4, we get:
26. According to “Freshness rule”, (10), and (25) we get:
27. According to the “ elimination rule”, (25), and (26), we get:
28. According to the “Elimination of multipart messages rule”, and (27), we get:
Now we have accomplished all the goals of our proof; based on (11), (22), (23), and (28), we can say the proposed scheme is provably safe under BAN logic.
8. Security Analysis Using Random Oracle
In this section, a security proof of random oracle is provided, based on the model of [5,30]. In order to simplify, it is supposed that only two entities are in FAuth: a smart meter , and an aggregator .
While each entity has many instances, using stands for the ith smart meter, and for the jth aggregator. can be used as or . An instance is considered as an oracle, and a simulator is used to answer the input message. Under this model, is considered as a participant or an oracle [5]. To crack the scheme, an adversary could use a simulator to ask for the following queries:
Send (): this oracle receives a message, , from an entity, and answers this query with the corresponding message.
Execute (): this query simulates the passive attack, and the adversary, A, can learn the message transmitted between .
ReveralSerrsion (): the adversary A can learn the session specific information, and the answer of this query doesn’t include the private key of or .
ReveralSk (): the adversary, A, can learn the session key of the oracle .
Corrupt (): the adversary, A, can learn the private key of the entity .
Expire (): this query erases the session key of a completed session held by the oracle .
Test (): returns a session key or a random key, only before any of the ReveralSerrsion (), ReveralSk () and Corrupt () have been asked.
Lemma 1 (Difference Lemma).
Let represent the events defined in some probability distribution. If , we have .
Theorem 1.
Let A be a t polynomial time adversary against the semantic security, and make no more than send queries, execute queries, and hash queries. The advantage of A in our scheme is given by , where , and is the time for multiplication operation in group.
In order to prove Theorem 1, we introduce four games, , and the first game represents the real attack, is the event that in Game the adversary correctly guesses the result of the Test ().
Game : This game simulates the real scheme under random oracle, according to sematic security, and it is clear that:
Game : This game simulates all the oracles, stores all the answers to hash queries, if the hash query is asked by adersary, then the answer is sotred in , and stores the transcripts of all the messages, all oracles are demonstrated in in Table 12 and Table 13, and an adversary is unable to distinguish between the two games:

Table 12.
Simulation of send queries.

Table 13.
Simulation of other queries.
Game : This game simulates all the oracles in Game , but two kinds of collisions are trying to be avoided here, and the results are obtained by the birthday paradox:
- Random numbers of and should be different in different sessions, and the probability is bounded by: .
- The probability of a hash result collision is bounded by , where is the length of a result of a hash function.
These two kinds of collisions should be avoided, so the two games differ by:
Game : This game simulates the situation where an adversary may guess the result of a hash function and without asking the random oracle.
For a Send , , ) query, has to check if belongs to the transcripts, and check if ; if either of them fails, terminates the session, the probability is bounded by ; for the checking of if , and the probability is bounded by , so for a Send , , ) query, the probability is bounded by . For a Send (, , ) or Send (, , ) query, the probability is bounded by , too.
This game and the previous one are indistinguishable unless the smart meter and aggregator reject valid authentication information:
Game : The CDH problem is brought in this game. In order to win the game, A should ask the query and broke the CDH problem; the adversary’s goal is to compute the session key by asking Execute (,) query and the corresponding hash query, and the adversary can also get the transcripts. The proposed scheme fits the SK-security [5] in the following four cases.
Case 1 RevealSession () and RevealSession ():
Adversary can get the session state information of , and for the matching instance . Where and .
Case 2 RevealSession () and Corrupt ():
Adversary can get the session state information of , the private key for the matching instance without session information.
Case 3 Corrupt () and RevealSession ():
Adversary can get the private key of , but could not get the session information of , and can get for the matching instance .
Case 4 Corrupt () and Corrupt ():
Adversary can get the private key of , but could not get the session information, and can get the private key for the matching instance without session information, too.
However, in all the above four cases, adversary A is unable to solve the CDH problem given the information it gets in the four cases. The shared key sk can be gotten with the probability in the list of , be the running time in all, then it is not hard to get:
Until now, through the games and using the lemma 1, theorem 1 is proven.
9. Comparison
9.1. Computational Performance Analysis
In this section, we compared the computation cost of the proposed scheme with [4,5], and the second scheme in [36], and we use the following symbols to stand for different time costs. In order for comparison, we use the experimental results from [41], the same as in Odelu’s scheme, and the results are shown in Table 14. We also “omit the modular multiplication . as it requires very low execution time than that for execution time of a modular exponentiation operation” [41]. We also ignore the point addition and XOR operations, as the time consumption is marginal, at the same time, we “assume ”. The final results are shown in Table 15 and Table 16.

Table 14.
Time comparison of various cryptographic operations.

Table 15.
Computation cost of different types of calculations at the authentication phase.

Table 16.
Computation cost at the authentication phase.
- the execution time of a modular exponentiation operation in
- the execution time of a scalar multiplication operation in
- the execution time of bilinear map pairing
- the execution time of a symmetric encryption/decryption
- the execution time of map to point
- the execution time of general one-way hash function
9.2. Communication Performance Analysis
In this section, we compared the proposed scheme’s computation cost with Tsai-Lo’s scheme [4], Odelu’s scheme [5], and Y. Wang et al. [36]. According to Odelu et al., “the random number/nonce is 128 bits, the identity and hash output of all hash functions , , and (except the hash function ) are 160 bits each, the elements in group and are 320 bits and 512 bits, respectively, and the timestamp is 32 bits” [5]. We get the following computation cost in Table 17, and for , its length is calculated as the length of , which is 480 bits.

Table 17.
Communication comparison.
9.3. Comparison of the Schemes
In this part, we compare the security features with the other schemes [4,5,36]. As we discussed in Section 5, Odelu’s scheme [5] suffers from impersonate attacks and track attacks; in Tsai-Lo’s scheme [4], the private key of the smart meter and service provider is also known by , so their scheme suffers from these two attacks, too. Besides, as knows the private key, could find out the shared key, so could launch an eavesdrop attack. The second scheme of [36] does not have a , but instead, a card maker, and the card maker knows the private key of the card owner. Besides, according to [4], the second scheme of [36] “does not support anonymity as it uses (smart meter) identity through its authentication process” and suffers from “unknown key share attack”.
According to [5], Tsai-Lo scheme in [4] “fails to protect the smart secret credentials when the ephemeral secret is revealed to (adversary).” We name this attack “session exposure attacks when ephemeral secrets leaked”. We get Table 18 based on the security analysis in Section 5, Table 15 and Table 16.

Table 18.
System comparison.
10. I3RES Project
Our work is part of the I3RES project (ICT-based intelligent management of integrated RES for the optimal operation of smart grid), which manages the grid capabilities, supports the deployment of services, and eases the development of user applications. The computational view of the I3RES is defined by the development of an open platform based on standardized and commercial off-the-shelf technologies, supporting the deployment of new services and decision-making mechanisms (1) to support tasks associated to monitoring in the context of the medium and low voltage network; (2) to manage the distribution of RES production in the distribution network associated to the stakeholders; and (3) to manage and control generation–consumption balance from the consumer point of view (DSM).
Our research group proposed a common middleware architecture for smart grids [42], which contributed to the standardization of designing and implementation of semantic middle architecture. It has been proven that sematic middleware architecture is a key element to create business models where new actors can join a new scenario, and where energy access and trade are democratized and more distributed than before. The general structure is depicted in Figure 3. The security component is a key part of the middleware, since it provides the required security mechanisms for the different application domains. The proposal presented in this paper was embedded within this security component, offering the security mechanisms needed for a smart grid application in an efficient way. Thus, it was feasible to deploy the security component in the different devices in smart grid.

Figure 3.
Components of the common middleware architecture [42].
11. Conclusions
In this paper, we introduced an anonymous authentication scheme based on bilinear pairing and the computational Diffie–Hellman problem. First, we improved the registration phase, so that a smart meter’s private key will not be leaked to the Key Generation Center. Thus, the proposed scheme is immune to various potential attacks launched by the Key Generation Center. Besides, we greatly improved the efficiency of the scheme, the computation cost at both the smart meter side and aggregator side is much lower compared to the existing schemes. We also use the BAN logic and random oracle model to prove that the proposed scheme is secure. As data privacy of the smart meter is becoming an urgency, in future, we want to focus on data aggregation methods in smart grids to protect the privacy of the smart meter consumption. Finally, the proposal was fitted into the security component of a common middleware architecture, in order to provide the required security mechanisms for a smart grid application.
Acknowledgments
The work presented in this paper is part of the work made in the I3RES (ICT-based Intelligent management of Integrated RES for the Smart Grid optimal operation) research project, an FP7 initiative (reference number 318184) that targets the seamless integration of Renewable Energy Sources and development of management tools for the Smart Grid. This work has also been supported by the Chinese Scholarship Council (CSC) with File No.: 201507040027.
Author Contributions
Yuwen Chen and José-Fernán Martínez conceived and designed the protocol; Yuwen Chen conducted the security analysis of the protocol, Yuwen Chen, Pedro Castillejo, and Lourdes López analyzed the computation and communication cost of the protocol; Yuwen Chen wrote the paper, Pedro Castillejo and Lourdes López did the proof reading of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Concerning Common Rules for the Internal Market in Electricity and Repealing Directive 2003/54/EC. Available online: https://www.mi.government.bg/en/library/directive-2009-72-ec-of-the-european-parliament-and-of-the-council-of-13-july-2009-concerning-common-445-c80-m262-4.html (accessed on 5 September 2017).
- Sanjab, A.; Saad, W.; Guvenc, I.; Sarwat, A.; Biswas, S. Smart Grid Security: Threats, Challenges, and Solutions. arXiv 2016, arXiv:1606.06992. [Google Scholar]
- Report on Workshop on Security and Privacy in the Hyper Connected World. Available online: https://docbox.etsi.org/SmartM2M/Open/AIOTI/!!20160616AIOTIWorkshopOnSecurity/AIOTI-Workshop-on-Security-and-Privacy-in-the-Hyper-connected-World-Report-20160616_vFinal.pdf (accessed on 5 September 2017).
- Tsai, J.L.; Lo, N.W. Secure Anonymous Key Distribution Scheme for Smart Grid. IEEE Trans. Smart Grid 2016, 7, 906–914. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Wazid, M.; Conti, M. Provably Secure Authenticated Key Agreement Scheme for Smart Grid. IEEE Trans. Smart Grid 2016, PP, 1. [Google Scholar] [CrossRef]
- Xia, J.; Wang, Y. Secure Key Distribution for the Smart Grid. IEEE Trans. Smart Grid 2012, 3, 1437–1443. [Google Scholar] [CrossRef]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Efficient and Privacy-Preserving Metering Protocols for Smart Grid Systems. IEEE Trans. Smart Grid 2016, 7, 1732–1742. [Google Scholar] [CrossRef]
- Zhang, A.; Wang, L.; Ye, X.; Lin, X. Light-Weight and Robust Security-Aware D2D-Assist Data Transmission Protocol for Mobile-Health Systems. IEEE Trans. Inf. Forensics Secur. 2017, 12, 662–675. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, Z.; Chen, X.; Kwak, K.S. Certificateless Remote Anonymous Authentication Schemes for WirelessBody Area Networks. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 332–342. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Lee, J.H. Anonymous Authentication for Wireless Body Area Networks with Provable Security. IEEE Syst. J. 2016, PP, 1–12. [Google Scholar] [CrossRef]
- Li, X.; Ma, J.; Wang, W.; Xiong, Y.; Zhang, J. A novel smart card and dynamic ID based remote user authentication scheme for multi-server environments. Math. Comput. Model. 2013, 58, 85–95. [Google Scholar] [CrossRef]
- Tsai, J.L.; Lo, N.W. A Privacy-Aware Authentication Scheme for Distributed Mobile Cloud Computing Services. IEEE Syst. J. 2015, 9, 805–815. [Google Scholar] [CrossRef]
- Lightweight Data Aggregation Scheme against Internal Attackers in Smart Grid Using Elliptic Curve Cryptography. Available online: https://www.hindawi.com/journals/wcmc/2017/3194845/ (accessed on 30 June 2017).
- Xiong, H. Cost-Effective Scalable and Anonymous Certificateless Remote Authentication Protocol. IEEE Trans. Inf. Forensics Secur. 2014, 9, 2327–2339. [Google Scholar] [CrossRef]
- Li, F.; Hong, J. Efficient Certificateless Access Control for Wireless Body Area Networks. IEEE Sens. J. 2016, 16, 5389–5396. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, L.; Sun, R. 1-RAAP: An Efficient 1-Round Anonymous Authentication Protocol for Wireless Body Area Networks. Sensors 2016, 16, 728. [Google Scholar] [CrossRef] [PubMed]
- Islam, S.H.; Khan, M.K. Provably secure and pairing-free identity-based handover authentication protocol for wireless mobile networks. Int. J. Commun. Syst. 2016, 29, 2442–2456. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Wu, L. Certificateless Public Auditing Scheme for Cloud-Assisted Wireless Body Area Networks. IEEE Syst. J. 2015, PP, 1–10. [Google Scholar] [CrossRef]
- Porambage, P.; Schmitt, C.; Kumar, P.; Gurtov, A.; Ylianttila, M. PAuthKey: A Pervasive Authentication Protocol and Key Establishment Scheme for Wireless Sensor Networks in Distributed IoT Applications. Int. J. Distrib. Sens. Netw. 2014, 10, e357430. [Google Scholar] [CrossRef]
- Zhang, L.; Tang, S.; Cai, Z. Efficient and flexible password authenticated key agreement for Voice over Internet Protocol Session Initiation Protocol using smart card. Int. J. Commun. Syst. 2014, 27, 2691–2702. [Google Scholar] [CrossRef]
- Tu, H.; Kumar, N.; Chilamkurti, N.; Rho, S. An improved authentication protocol for session initiation protocol using smart card. Peer-to-Peer Netw. Appl. 2015, 8, 903–910. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. An efficient biometric-based privacy-preserving three-party authentication with key agreement protocol using smart cards. Secur. Commun. Netw. 2015, 8, 4136–4156. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. SEAP: Secure and efficient authentication protocol for NFC applications using pseudonyms. IEEE Trans. Consum. Electron. 2016, 62, 30–38. [Google Scholar] [CrossRef]
- Wang, D.; Wang, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Jiang, Q.; Wei, F.; Fu, S.; Ma, J.; Li, G.; Alelaiwi, A. Robust extended chaotic maps-based three-factor authentication scheme preserving biometric template privacy. Nonlinear Dyn. 2016, 83, 2085–2101. [Google Scholar] [CrossRef]
- Kumari, S.; Chaudhry, S.A.; Wu, F.; Li, X.; Farash, M.S.; Khan, M.K. An improved smart card based authentication scheme for session initiation protocol. Peer-to-Peer Netw. Appl. 2017, 10, 92–105. [Google Scholar] [CrossRef]
- Jiang, Q.; Khan, M.K.; Lu, X.; Ma, J.; He, D. A privacy preserving three-factor authentication protocol for e-Health clouds. J Sup. Comput. 2016, 72, 3826–3849. [Google Scholar]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client–server networks. Comput. Electr. Eng. 2015, 45, 274–285. [Google Scholar] [CrossRef]
- Farash, M.S. Security analysis and enhancements of an improved authentication for session initiation protocol with provable security. Peer-to-Peer Netw. Appl. 2016, 9, 82–91. [Google Scholar] [CrossRef]
- Farash, M.S.; Attari, M.A. An Enhanced Authenticated Key Agreement for Session Initiation Protocol. Inf. Technol. Control 2013, 42, 333–342. [Google Scholar] [CrossRef]
- Huang, B.; Khan, M.K.; Wu, L.; Muhaya, F.T.B.; He, D. An Efficient Remote User Authentication with Key Agreement Scheme Using Elliptic Curve Cryptography. Wirel. Pers. Commun. 2015, 85, 225–240. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Naqvi, H.; Mahmood, K.; Ahmad, H.F.; Khan, M.K. An Improved Remote User Authentication Scheme Using Elliptic Curve Cryptography. Wirel. Pers. Commun. 2016, 1–19. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Liao, J.; Liang, W. An Enhancement of a Smart Card Authentication Scheme for Multi-server Architecture. Wirel. Pers. Commun. 2015, 80, 175–192. [Google Scholar] [CrossRef]
- Wang, Y. Password Protected Smart Card and Memory Stick Authentication against Off-line Dictionary Attacks. arXiv 2012, arXiv:1207.5497. [Google Scholar]
- Advanced Encryption Standard (AES). Available online: http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf (accessed on 5 September 2017).
- Burrows, M.; Abadi, M.; Needham, R.M. A Logic of Authentication. Proc. R. Soc. Lond. A Math. Phys. Eng. Sci. 1989, 426, 233–271. [Google Scholar] [CrossRef]
- Shoup, V. Sequences of Games: A Tool for Taming Complexity in Security Proofs. 2005. Available online: http://www.shoup.net/papers/games.pdf (accessed on 5 September 2017).
- Lee, T.F. Provably Secure Anonymous Single-Sign-On Authentication Mechanisms Using Extended Chebyshev Chaotic Maps for Distributed Computer Networks. IEEE Syst. J. 2015. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Huang, S.S.; Tsai, T.T.; Ke, J.H. List-Free ID-Based Mutual Authentication and Key Agreement Protocol for Multiserver Architectures. IEEE Trans. Emerg. Top. Comput. 2016, 4, 102–112. [Google Scholar] [CrossRef]
- Rodríguez-Molina, J.; Martínez, J.-F.; Castillejo, P.; de Diego, R. SMArc: A Proposal for a Smart, Semantic Middleware Architecture Focused on Smart City Energy Management. Int. J. Distrib. Sens. Netw. 2013, 9. [Google Scholar] [CrossRef]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).

