The Effect of SMiShing Attack on Security of Demand Response Programs
Abstract
:1. Introduction
- We determined that SMiShing attacks can damage the power grid through customer behavior by victimizing customers even if the attacker has no access to the power grid communication domain. We show the effects of DDRS attacks on the LV grid which is the first evaluation of this kind.
- We performed the risk assessment and enhanced the methodology as it is needed: The SGIS risk assessment methodology does not provide any likelihood analysis method; rather, it refers to the HM/IS1 standard’s [12] method. It gives suggestions on the threat factors in [9] without considering vulnerability. To improve this deficiency, both the SGIS methodology and OWASP (Open Web Application Security Project) [13] methodology are combined and adopted into a five-scale approach that considers the likelihood analysis in a broader sense.
- Risk assessment of the DR use case for the SMiShing attack is performed: In order to understand how a SMiShing attack would affect the grid asset, what the probability of a specific threat scenario to happen is, and how to react if that attack occurs, we carried out a risk assessment on the DR use case for SMiShing attacks, shown in the background section.
- SMiShing attacks for SMS notification-based DR programs are modeled: We reveal that DDRS attacks are geared toward outages on the power grid. Attacks are simulated on a test system to analyze the reaction of the system under attack. The European Low Voltage Feeder Test System provided by IEEE [14] is utilized for deterministic and randomized attack models.
- We provide possible countermeasures for the identified risk, for both the utility and customer perspective: we provide some solutions on how the utilities should handle the attack, how they should interact with the customer to prevent DDRS attacks, what kind of preventive actions they can take on the power grid to mitigate the DDRS attacks, and what the customer should do to protect themselves from SMiShing attacks.
2. Related Work
3. Background
3.1. SMS Usage for DR
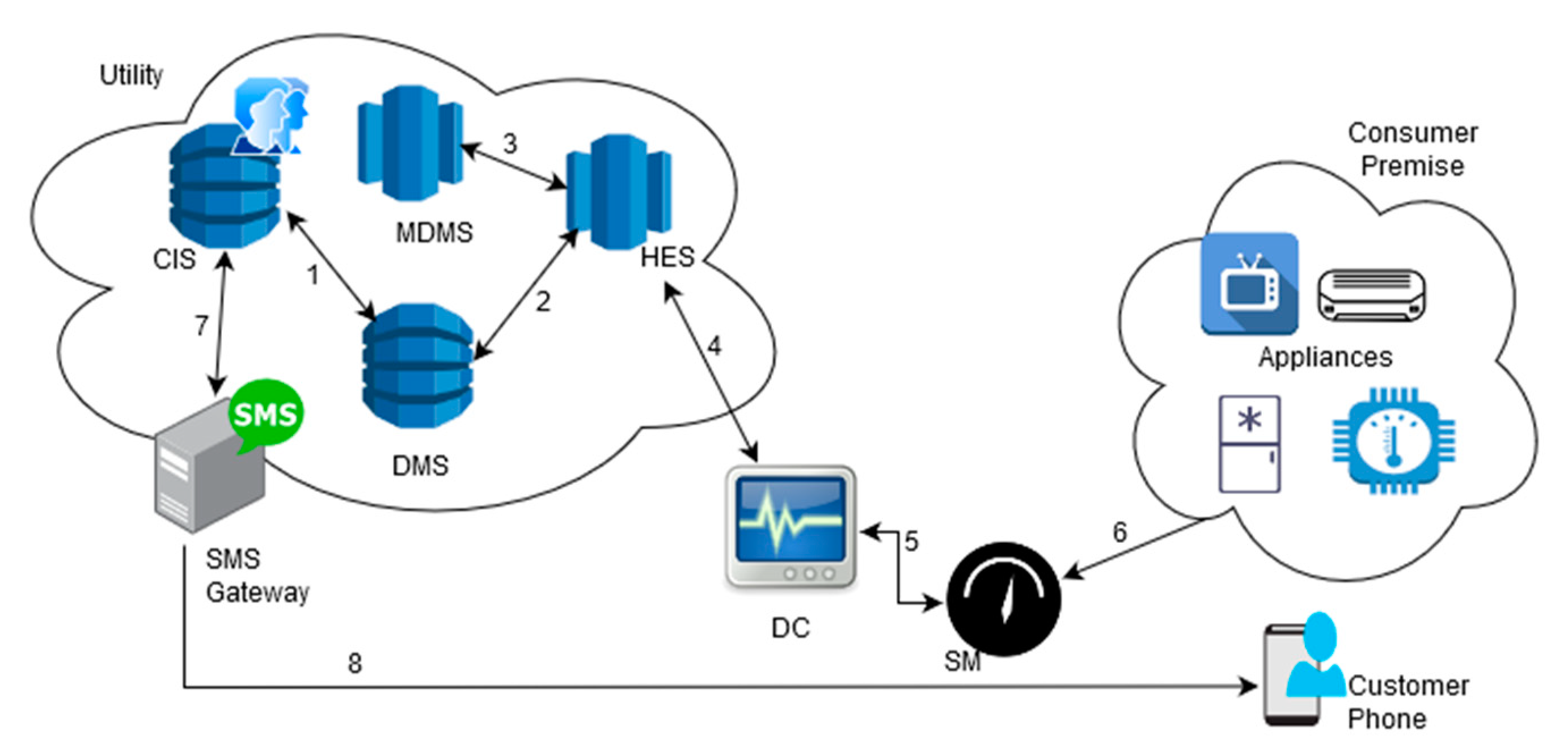
3.1.1. Use Case Information Flow
3.1.2. SMiShing Attacks
4. Risk Assessment
4.1. Identifying Assets
- CIS and MDMS are grouped as Utility Corporate Network (UCN),
- DMS and HES are grouped as Utility Operational Network (UON),
- SM and Appliances are grouped as Customer Network (CN),
- SMS Gateway, Mobile Network, and Mobile Phone are grouped as SMS Network,
- DC is considered as a separate component.
4.2. Impact Analysis
- Publicly disclosing the private information (consumer’s power signature) on the communication channel by eavesdropping on the network.
- Modifying or spoofing messages (e.g., smart meter last gasp message) on the communication link which may cause power loss.
- Preventing legitimate DR messages from being retrieved and transmitted by tampering with the communication or bursting channel by other messages.
- Compromising one or more DR system devices causing inappropriate DR messages at undesired times to be sent to unintended devices/customers.
- Malware injection to the one or more DR system device causing malicious use of system resources (slowing down the system, sending unwanted DR messages, etc.), and unauthorized access to customer data.
4.3. Likelihood Analysis
4.4. Risk Level
5. Attack Scenario and Simulation Results
5.1. Simulation Environment
5.2. Threat Model and Attack Variations
5.3. Simulation of the System without Attacking
5.4. Simulation of the System under Attack
| Algorithm 1: DDRS attack simulation |
| 1: function: simulate_DDRS_attack() |
| 2: load_count = 1, multiplier = 2 |
| 3: load_profile [1..55]=read(load_profile_files) |
| 4: while (load_count ! = 55) |
| 5: number_of_loads_to_be_attacked = poisson_rnd() |
| 6: for (1: number_of_loads_to_be_attacked) |
| 7: pick_load = rnd (1..55) |
| 8: for (attack_start_time: attack_end_time) |
| 9: new_load_profile[pick_load] = multiplier*load_profile[pick_load] |
| 10: end for |
| 11: end for |
| 12: write (new_load_profile [1..55]) |
| 13: load_count = load_count + 1 |
| 14: end while |
| 15: run_GridLab-D(new_load_profiles[1..55]) |
| 16: plot_results() |
| 17: end function |
5.4.1. Voltage Stability
5.4.2. Line Failures
5.4.3. Phase Balance
6. Discussion on Countermeasures
- The way of communicating,
- Structure of legitimate messages as well as possible SMiShing messages,
- When and how to respond to the messages,
- What to do if a suspicious message is received.
- Defining the optimum DR participation-level thresholds and limiting the participation based on the threshold so that even if the attack is launched, the balance of the grid cannot be disrupted, and keep the grid robust
- Continuously monitoring the behavior of the grid, and if an anomaly is detected, then the sheddable loads should be isolated if necessary,
- Balancing the grid through energy storage devices. Depending on the behavior of the grid, utilities may install energy storage solutions as a source to balance the load since batteries can both take in and supply energy.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mirzaei, M.A.; Yazdankhah, A.S.; Mohammadi-ivatloo, B. Stochastic security-constrained operation of wind and hydrogen energy storage systems integrated with price-based demand response. Int. J. Hydrogen Energy 2019, 44, 14217–14227. [Google Scholar] [CrossRef]
- Wang, Y.; Pordanjani, I.R.; Xu, W. An Event-Driven Demand Response Scheme for Power System Security Enhancement. IEEE Trans. Smart Grid 2011, 2, 23–29. [Google Scholar] [CrossRef]
- Wang, D.; Parkinson, S.; Miao, W.; Jia, H.; Crawford, C.; Djilali, N. Online voltage security assessment considering comfort-constrained demand response control of distributed heat pump systems. Appl. Energy 2012, 96, 104–114. [Google Scholar] [CrossRef]
- FERC. A National Assessment of Demand Response Potential. Available online: https://www.smartgrid.gov/document/national_assessment_demand_response_potential_0 (accessed on 20 June 2020).
- 2018 Utility Demand Response Market Snapshot. Available online: https://sepapower.org/resource/2018-demand-response-market-snapshot/ (accessed on 20 June 2020).
- GSM Technical Specification 3.40. Available online: http://www.etsi.org/deliver/etsi_gts/03/0340/05.03.00_60/gsmts_0340v050300p.pdf (accessed on 20 June 2020).
- Jain, M.; Chandan, V.; Minou, M.; Thanos, G.A.; Wijaya, T.K.; Lindt, A.; Gylling, A. Methodologies for effective demand response messaging. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Miami, FL, USA, 2–5 November 2015; pp. 453–458. [Google Scholar]
- Curb Your Power, Powershop Demand Response Program—Project Report—May 2018. Available online: https://arena.gov.au/assets/2017/12/powershop-demand-response-program.pdf (accessed on 20 June 2020).
- NISTIR 7628, Guidelines for Smart Grid Cyber Security. Available online: https://www.nist.gov/sites/default/files/documents/smartgrid/nistir-7628_total.pdf (accessed on 20 June 2020).
- Salahdine, F.; Kaabouch, N. Social Engineering Attacks: A Survey. Future Internet 2019, 11, 89. [Google Scholar] [CrossRef] [Green Version]
- CEN-CENELEC-ETSI Smart Grid Coordination Group. Smart Grid Information Security Report. Available online: ftp://ftp.cencenelec.eu/EN/EuropeanStandardization/HotTopics/SmartGrids/SGCG_SGIS_Report (accessed on 20 June 2020).
- HMG IA Standard No. 1 Technical Risk Assessment Issue 3.51. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.177.1833&rep=rep1&type=pdf (accessed on 20 June 2020).
- OWASP Risk Rating Methodology. Available online: https://www.owasp.org/index.php/OWASP_Risk_Rating_Methodology (accessed on 20 June 2020).
- European Low Voltage Test Feeder, IEEE Test Cases. Available online: http://sites.ieee.org/pes-testfeeders/resources/ (accessed on 20 June 2020).
- Dabrowski, A.; Ullrich, J.; Weippl, E.R. Grid Shock: Coordinated Load-Changing Attacks on Power Grids: The Non-Smart Power Grid is Vulnerable to Cyber Attacks as Well. In Proceedings of the 33rd Annual Computer Security Applications Conference (ACSAC), Orlando, FL, USA, 4–8 December 2017; pp. 303–314. [Google Scholar] [CrossRef]
- Soltan, S.; Mittal, P.; Vincent Poor, H. BlackIoT: IoT Botnet of high wattage devices can disrupt the power grid. In Proceedings of the 27th USENIX Conference on Security Symposium (SEC’18), Baltimore, MD, USA, 15–17 August 2018; pp. 15–32. [Google Scholar]
- Kim, S.K.; Kim, U.; Huh, J. A Study on Improvement of Blockchain Application to Overcome Vulnerability of IoT Multiplatform Security. Energies 2019, 12, 402. [Google Scholar] [CrossRef] [Green Version]
- Irshad, A.; Usman, M.; Chaudhry, S.A.; Naqvi, H.; Shafiq, M. A Provably Secure and Efficient Authenticated Key Agreement Scheme for Energy Internet-Based Vehicle-to-Grid Technology Framework. IEEE Trans. Ind. Appl. 2020, 56, 4425–4435. [Google Scholar] [CrossRef]
- Mohsenian-Rad, A.H.; Leon-Garcia, A. Distributed Internet-Based Load Altering Attacks against Smart Power Grids. IEEE Trans. Smart Grid 2011, 4, 667–674. [Google Scholar] [CrossRef]
- Amini, S.; Rad, H.M.; Pasqualetti, F. Dynamic load altering attacks in smart grid. In Proceedings of the IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–20 February 2015; pp. 1–5. [Google Scholar]
- Amini, S.; Pasqualetti, F.; Mohsenian-Rad, H. Dynamic Load Altering Attacks against Power System Stability: Attack Models and Protection Schemes. In Proceedings of the IEEE Power & Energy Society General Meeting (PESGM), Chicago, IL, USA, 16–20 July 2017. [Google Scholar] [CrossRef]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2009, 14, 1–33. [Google Scholar] [CrossRef]
- Rahman, M.A.; Mohsenian-Rad, H. False Data Injection Attacks against Nonlinear State Estimation in Smart Power Grids. In Proceedings of the IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar] [CrossRef]
- Sandberg, H.; Teixeira, A.M.; Johansson, K.H. On Security Indices for State Estimators in Power Networks. In Proceedings of the First Workshop on Secure Control Systems, Stockholm, Sweden, 12 April 2010. [Google Scholar]
- Soltan, S.; Mittal, P.; Poor, H.V. Protecting the Grid against IoT Botnets of High-Wattage Devices. arXiv 2018, arXiv:1808.03826. [Google Scholar]
- Dvorkin, Y.; Siddharth, G. IoT-enabled distributed cyber-attacks on transmission and distribution grids. In Proceedings of the North American Power Symposium (NAPS), Morgantown, WV, USA, 17–19 September 2017; pp. 1–6. [Google Scholar]
- 2009/72/EC of the European Parliament and of the Council of 13 July 2009 Concerning Common Rules for the Internal Market in Electricity and Repealing Directive 2003/54/EC. Available online: https://eur-lex.europa.eu/legal-content/EN/ALL/?uri=celex%3A32009L0072 (accessed on 20 June 2020).
- Cohen, L.E.; Felson, M. Social change and crime rate trends: A routine activity approach. Am. Sociol. Rev. 1979, 44, 588–608. [Google Scholar] [CrossRef]
- Hutchings, A.; Hayes, H. Routine Activity Theory and Phishing Victimisation: Who Gets Caught in the ‘Net’? Curr. Issues Crim. Justice 2009, 20, 433–452. [Google Scholar] [CrossRef] [Green Version]
- Mobile Phishing 2018: Myths and Facts Facing Every Modern Enterprise Today. Available online: https://info.lookout.com/rs/051-esq-475/images/lookout-phishing-wp-us.pdf (accessed on 20 June 2020).
- Stanford University. The Human Factor Report. Available online: https://seclab.stanford.edu/courses/cs203/lectures/humanfactor.pdf (accessed on 20 June 2020).
- SMiShing: New Age Phishing. Available online: https://www.vanillaplus.com/2017/09/29/30811-smishing-new-age-phishing/ (accessed on 20 June 2020).
- Moon, S.; Park, D. Forensic Analysis of MERS Smishing Hacking Attacks and Prevention. Int. J. Secur. Its Appl. 2016, 10, 181–192. [Google Scholar] [CrossRef]
- Joo, J.W.; Moon, S.Y.; Singh, S.; Park, J.H. S-Detector: An enhanced security model for detecting Smishing attack for mobile computing. Telecommun. Syst. 2017, 66, 29–38. [Google Scholar] [CrossRef]
- Jain, A.K.; Gupta, B.B. Rule-Based Framework for Detection of Smishing Messages in Mobile Environment. Procedia Comput. Sci. 2018, 125, 617–623. [Google Scholar] [CrossRef]
- Sonowal, G.; Kuppusamy, K.S. SmiDCA: An Anti-Smishing Model with Machine Learning Approach. Comput. J. 2018, 61, 1143–1157. [Google Scholar] [CrossRef]
- Prakash, P.; Kumar, M.; Kompella, R.R.; Gupta, M. Phishnet: Predictive Blacklisting to Detect Phishing Attacks. In Proceedings of the 2010 Proceedings IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- ISO/IEC 27005:2011 Information Technology, Security Techniques, Information Security Risk Management (Second Edition). Available online: http://www.27000.org/iso-27005.htm (accessed on 20 June 2020).
- ISO/IEC. ISO 31000:2009, Risk Management—Principles and Guidelines. 2009. Available online: http://www.iso.org/iso/home/standards/iso31000.htm (accessed on 20 June 2020).
- NESCOR. Electric Sector Failure Scenarios and Impact Analyses—Version 3.0. Available online: https://smartgrid.epri.com/doc/NESCOR%20Failure%20Scenarios%20v3%2012-11-15.pdf (accessed on 20 June 2020).
- Gridlab, D. Available online: https://www.gridlabd.org/ (accessed on 20 June 2020).
- Kersting, W. Radial Distribution Test Feeders. In Proceedings of the IEEE Power Engineering Society Winter Meeting, Columbus, OH, USA, 28 January–1 February 2001; Volume 2, pp. 908–912. [Google Scholar]





| Assets | Impact Categories | ||||
|---|---|---|---|---|---|
| Energy | Population | Infrastructure | Human | Reputation | |
| UON | Very High | High | High | N/A | Low |
| DC | Medium | Low | Medium | N/A | Low |
| CN | Low | Low | Medium | Low | Low |
| Assets | Attacker Types | |||
|---|---|---|---|---|
| Customer | Hacker | Dishonest Employee | Terrorist | |
| UON | N/A | High | Very High | Very High |
| DC | N/A | High | Very High | Very High |
| CN | Very High | High | N/A | N/A |
| Assets | Impact Level | Likelihood Level | Risk Level |
|---|---|---|---|
| UON | 4 (Critical) | 4 (Very High) | 4 × 4 (Critical) |
| DC | 2 (Medium) | 4 (Very High) | 2 × 4 (Medium) |
| CN | 2 (Medium) | 4 (Very High) | 2 × 4 (Medium) |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ustundag Soykan, E.; Bagriyanik, M. The Effect of SMiShing Attack on Security of Demand Response Programs. Energies 2020, 13, 4542. https://doi.org/10.3390/en13174542
Ustundag Soykan E, Bagriyanik M. The Effect of SMiShing Attack on Security of Demand Response Programs. Energies. 2020; 13(17):4542. https://doi.org/10.3390/en13174542
Chicago/Turabian StyleUstundag Soykan, Elif, and Mustafa Bagriyanik. 2020. "The Effect of SMiShing Attack on Security of Demand Response Programs" Energies 13, no. 17: 4542. https://doi.org/10.3390/en13174542
APA StyleUstundag Soykan, E., & Bagriyanik, M. (2020). The Effect of SMiShing Attack on Security of Demand Response Programs. Energies, 13(17), 4542. https://doi.org/10.3390/en13174542




