Client-Aware Negotiation for Secure and Efficient Data Transmission
Abstract
:1. Introduction
1.1. Background and Motivation
1.2. Related Work
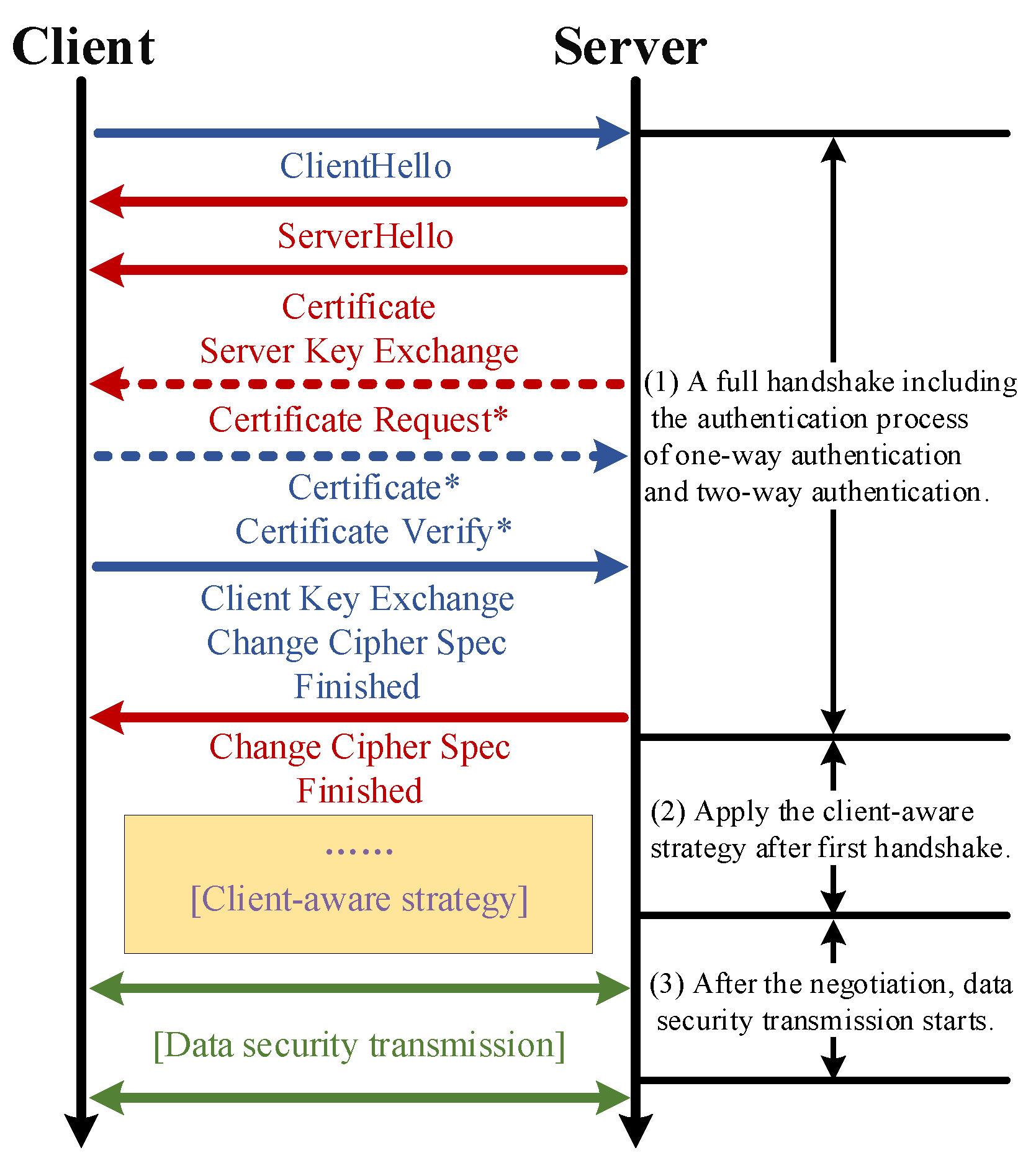
2. System Description
2.1. Message Exchange
2.2. Encryption Algorithm
2.3. Security Strength
3. Methodology
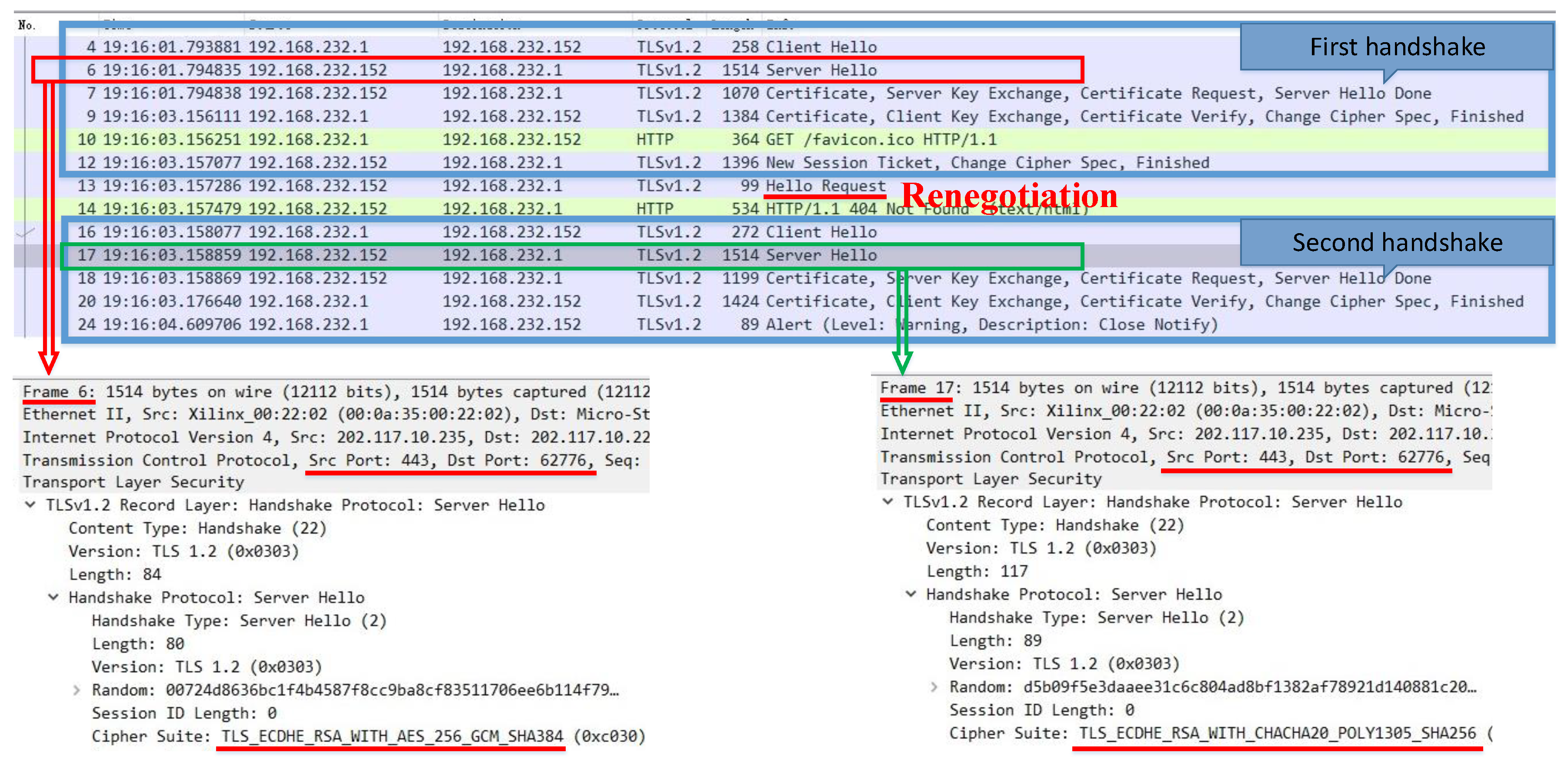
3.1. CAN Based on Renegotiation
3.2. CAN Based on Redirection
4. Result and Analysis
4.1. Experimental Environment
4.2. Message Exchange
4.3. Encryption Efficiency
4.4. Encryption Scheme and Security Analysis
4.5. Application
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mehmood, A.; Mauri, J.L.; Noman, M.; Song, H. Improvement of the Wireless Sensor Network Lifetime Using LEACH with Vice-Cluster Head. Ad Hoc Sens. Wirel. Netw. 2015, 28, 1–17. [Google Scholar]
- Kuila, P.; Jana, P.K. Energy efficient clustering and routing algorithms for wireless sensor networks: Particle swarm optimization approach. Eng. Appl. Artif. Intell. 2014, 33, 127–140. [Google Scholar] [CrossRef]
- Wei, Y.; Ma, X.; Yang, N.; Chen, Y. Energy-Saving Traffic Scheduling in Hybrid Software Defined Wireless Rechargeable Sensor Networks. Sensors 2017, 17, 2126. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Fu, L.; Wang, J.; Wang, X.; Chen, G. Multicast Scaling of Capacity and Energy Efficiency in Heterogeneous Wireless Sensor Networks. ACM Trans. Sens. Netw. 2019, 15, 1–32. [Google Scholar] [CrossRef]
- Ebrahimi, D.; Assi, C. Network Coding-Aware Compressive Data Gathering for Energy-Efficient Wireless Sensor Networks. ACM Trans. Sens. Netw. 2015, 11, 1–24. [Google Scholar] [CrossRef]
- Yu, X.; Baek, S.J. Energy-Efficient Collection of Sparse Data in Wireless Sensor Networks Using Sparse Random Matrices. ACM Trans. Sens. Netw. 2017, 13, 1–36. [Google Scholar] [CrossRef]
- Qiu, Y.; Li, S.; Xu, X.; Li, Z. Talk more listen less: Energy-efficient neighbor discovery in wireless sensor networks. In Proceedings of the 35th Annual IEEE International Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–14 April 2016; pp. 1–9. [Google Scholar] [CrossRef] [Green Version]
- Yin, C.; Jin, S. An energy-saving strategy based on multi-server vacation queuing theory in cloud data center. J. Supercomput. 2018, 74, 6766–6784. [Google Scholar] [CrossRef]
- Kuehn, P.J.; Mashaly, M.E. Automatic energy efficiency management of data center resources by load-dependent server activation and sleep modes. Ad Hoc Netw. 2015, 25, 497–504. [Google Scholar] [CrossRef]
- Nguyen, B.M.; Tran, D.; Nguyen, G. Enhancing service capability with multiple finite capacity server queues in cloud data centers. Clust. Comput. 2016, 19, 1747–1767. [Google Scholar] [CrossRef]
- Joseph, S.; Hao, Z.; Pasi, E.; Hannes, T. Transport Layer Security (TLS) Session Resumption without Server-Side State. RFC 2008, 5077, 1–20. [Google Scholar] [CrossRef]
- Cremers, C.; Horvat, M.; Hoyland, J.; Scott, S.; van der Merwe, T. A Comprehensive Symbolic Analysis of TLS 1.3. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security (CCS), Dallas, TX, USA, 30 October–3 November 2017; Thuraisingham, B.M., Evans, D., Malkin, T., Xu, D., Eds.; ACM: New York, NY, USA, 2017; pp. 1773–1788. [Google Scholar] [CrossRef]
- Gergely, A.; Lejla, B.; Lynn, M.B.; Veelasha, M.; Antoine, G.; Iynkaran, N. New directions in IoT privacy using attribute-based authentication. In Proceedings of the ACM International Conference on Computing Frontiers (CF’16), Como, Italy, 16–19 May 2016; ACM: New York, NY, USA, 2016; pp. 461–466. [Google Scholar] [CrossRef] [Green Version]
- Tanesh, K.; An, B.; Lynn, M.B.; Madhusanka, L.; Mika, Y. Identity privacy preserving biometric based authentication scheme for Naked healthcare environment. In Proceedings of the IEEE International Conference on Communications (ICC 2017), Paris, France, 21–25 May 2016; pp. 461–466. [Google Scholar] [CrossRef] [Green Version]
- António, P.; Ricardo, C. Hash-Chain Based Authentication for IoT Devices and REST Web-Services. In Advances in Intelligent Systems and Computing, Proceedings of the Ambient Intelligence—Software and Applications-7th International Symposium on Ambient Intelligence (ISAmI 2016), Seville, Spain, 1–3 June 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 189–196. [Google Scholar] [CrossRef] [Green Version]
- Gai, K.; Qiu, L.; Chen, M.; Zhao, H.; Qiu, M. SA-EAST: Security-Aware Efficient Data Transmission for ITS in Mobile Heterogeneous Cloud Computing. ACM Trans. Embed. Comput. Syst. 2017, 16, 60:1–60:22. [Google Scholar] [CrossRef]
- Shang, X.; Liu, A.; Wang, Y.; Xie, Q.; Wang, Y. Energy-Efficient Transmission Based on Direct Links: Toward Secure Cooperative Internet of Things. Wirel. Commun. Mob. Comput. 2018, 2018, 5012096. [Google Scholar] [CrossRef] [Green Version]
- Zhang, M.; Cumanan, K.; Wang, W.; Burr, A.G.; Ding, Z.; Lambotharan, S.; Dobre, O.A. Energy Efficiency Optimization for Secure Transmission in a MIMO-NOMA System. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Chen, W.; Han, Z. Energy efficiency maximization for secure data transmission over DF relay networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 2313–2317. [Google Scholar] [CrossRef]
- Netcraft Ltd. June 2020 Web Server Survey. Available online: https://news.netcraft.com/archives/category/web-server-survey (accessed on 18 July 2020).
- Bellare, M.; Tackmann, B. The Multi-user Security of Authenticated Encryption: AES-GCM in TLS 1.3. In Lecture Notes in Computer Science, Proceedings of the Advances in Cryptology—CRYPTO 2016: 36th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Robshaw, M., Katz, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9814, pp. 247–276. [Google Scholar] [CrossRef]
- Abdalla, M.; Gierlichs, B.; Paterson, K.G.; Rijmen, V.; Sadeghi, A.R.; Smart, N.P.; Stam, M.; Ward, M.; Warinschi, B.; Watson, G. Algorithms, Key Size and Protocols Report. Available online: https://www.ecrypt.eu.org/csa/documents/D5.4-FinalAlgKeySizeProt.pdf (accessed on 18 July 2020).
- Giry, D. BlueKrypt-Cryptographic Key Length Recommendation: ECRYPT-CSA Recommendations. Available online: https://www.keylength.com/en/3 (accessed on 18 July 2020).
- You, X.; Yang, H.; Luan, Z.; Liu, Y.; Qian, D. Performance Evaluation and Analysis of Linear Algebra Kernels in the Prototype Tianhe-3 Cluster. In Lecture Notes in Computer Science, Proceedings of the Supercomputing Frontiers: 5th Asian Conference (SCFA 2019), Singapore, 11–14 March 2019; Abramson, D., de Supinski, B.R., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; Volume 11416, pp. 86–105. [Google Scholar] [CrossRef] [Green Version]
- Nir, Y.; Langley, A. ChaCha20 and Poly1305 for IETF Protocols. RFC 2018, 8439, 1–46. [Google Scholar] [CrossRef]
- Eric, R.; Marsh, R.; Steve, D.; Nasko, O. Transport Layer Security (TLS) Renegotiation Indication Extension. RFC 2010, 5746, 1–15. [Google Scholar] [CrossRef] [Green Version]
- Florian, G.; Florian, K.; Douglas, S. On the Security of TLS Renegotiation. In Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security (CCS’13), Berlin, Germany, 4–8 November 2013; Ahmad-Reza, S., Virgil, D., Moti, Y., Eds.; ACM: New York, NY, USA, 2013; pp. 387–398. [Google Scholar] [CrossRef] [Green Version]





| Protection | Symmetric | Factoring Modulus | Elliptic Curve | Hash |
|---|---|---|---|---|
| Legacy standard level Should not be used in new systems | 80 | 1024 | 160 | 160 |
| Near-term protection Security for at least 10 years (2020–2028) | 128 | 3072 | 256 | 256 |
| Long-term protection Security for 30 to 50 years (2020–2068) | 256 | 15360 | 512 | 512 |
| Experimental Platform | Xilinx Zynq | FT-2000+: FTC662 | Intel I7-6700 |
|---|---|---|---|
| RSA signature speed | 3.07% | 2.13% | 2.20% |
| RSA authentication speed | 8.79% | 7.35% | 9.95% |
| AES software encryption speed | 76.08% | 76.99% | 74.48% |
| AES hardware encryption speed | 87.12% | 95.48% | 87.49% |
| File Size | 10 KB | 100 KB | 1 MB | 10 MB |
|---|---|---|---|---|
| Scenario 1 | 7410 | 8289 | 15,025 | 78,805 |
| Scenario 2 | 785 | 1456 | 6900 | 66,672 |
| Scenario 3 | 5027 | 5259 | 6969 | 28,137 |
| Scenario 4 | 739 | 952 | 2675 | 21,209 |
| File Size | 10 KB | 100 KB | 1 MB | 10 MB |
|---|---|---|---|---|
| Scenario 1 | 15,105 | 15,770 | 22,478 | 86,297 |
| Scenario 2 | 1689 | 2299 | 7646 | 67,415 |
| Scenario 3 | 10,150 | 10,412 | 12,021 | 32,836 |
| Scenario 4 | 1524 | 1878 | 3565 | 21,984 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Z.; Chen, H.; Wu, W. Client-Aware Negotiation for Secure and Efficient Data Transmission. Energies 2020, 13, 5777. https://doi.org/10.3390/en13215777
Wang Z, Chen H, Wu W. Client-Aware Negotiation for Secure and Efficient Data Transmission. Energies. 2020; 13(21):5777. https://doi.org/10.3390/en13215777
Chicago/Turabian StyleWang, Ziheng, Heng Chen, and Weiguo Wu. 2020. "Client-Aware Negotiation for Secure and Efficient Data Transmission" Energies 13, no. 21: 5777. https://doi.org/10.3390/en13215777




