Intelligent Buildings in Smart Grids: A Survey on Security and Privacy Issues Related to Energy Management
Abstract
:1. Introduction
- Proposition of a perspective of IBs as an SoS, composed of cyber and physical parts, which is also a part of the SG, another SoS. This global concept is then applied to BEMS and communications to analyze the close relationship and bidirectional connection between IBs and the SG;
- Overview of the most relevant security objectives and requirements from a CPS perspective, along with a study of attacks and privacy issues concerning the communication protocols and metering infrastructure of IBs;
- Identification of different open issues, including both technical and human factors, with respect to reinforced security of the SG.
2. From the Smart Grid to Intelligent Buildings
2.1. The Smart Grid, a System of Systems
- Traditional electrical system, composed of power plants, transmission grid and distribution grid;
- Customer-side system, including several elements located at the end of the distribution network, like electrical microgrids (MGs), intelligent buildings (IBs) and smart homes (SHs), and electrical vehicles (EVs);
- Communication system, which gives the SG its intelligent nature, mainly composed of communication networks and data storage and processing centers.
2.2. The Intelligent Building, a System of Systems
3. Main Features of Intelligent Buildings as Part of Smart Grids
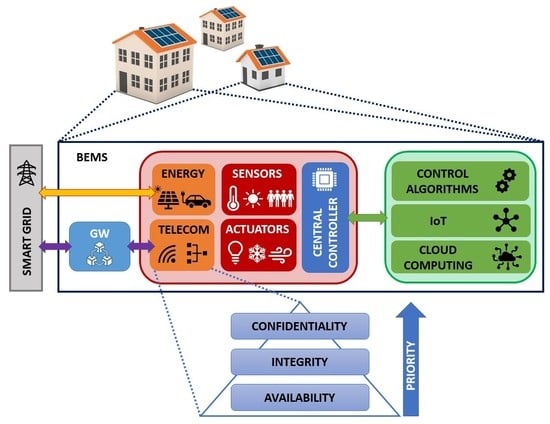
- Smart metering, a part of the whole advanced metering infrastructure (AMI) of the SG;
- Management and control methods to guarantee the energy efficiency in the building and the power balance in the electrical grid.
3.1. Energy Management in Intelligent Buildings
3.1.1. Building Energy Management System Architecture
3.1.2. Making the Energy Management Systems More Intelligent
- General management methods
- Reactive agents, with a stimulus–response behavior based on sending and receiving messages;
- Cognitive agents, with a high level of intelligence and autonomy. These agents can memorize their history and develop a learning ability by adopting ML behavior. An example of an MAS with a “learning” phase for better managing a large and complex microgrid was proposed in [92];
- Hybrid agents, offering combined behavior: reactive with respect to some properties and cognitive with respect to other properties. The main properties to consider here are autonomy, cooperation, and adaptation.
- Contribution of computing tools in intelligent energy management
- The Internet of Things and related computing solutions
3.2. Communication Networks and Intelligent Buildings
3.2.1. Communication Technologies for Interconnecting IBs to the SG
3.2.2. Communication Infrastructure Requirements for IBs as a Part of the SG
4. Security Protocols and Privacy Issues
4.1. Cyber-Physical Security Objectives and Requirements
- Interruptions of communications, avoiding delivery of data to their destinations. The QoS is disrupted and, at the same time, attackers try to tamper with data during the interruptions;
- Exhaustion, where attackers try to drain the constrained resources of SM such as computing units;
- Identification, employed by attackers that want to appear to be legitimate in order to join the network;
- Authorization, the objective of which is to counter the access control mechanisms in order to access data or security secrets.
4.2. Overview of Attacks Against the Smart Grid Security
4.2.1. Multilayer Attacks
4.2.2. Physical Layer Attacks
4.2.3. MAC Layer Attacks
4.2.4. Network Layer Attacks
4.2.5. Application Layer Attacks
4.3. Privacy Issues
- External, where the attacker does not belong to the network. This attacker does not participate in communications or routing, and does not interact with legitimate participants, realizing passive attacks;
- Internal, where the attacker is able to take control of network equipment or resources. Since such attackers are perceived as legitimate users, they can participate in even secured communications, gaining access to all the traffic passing across them. Such attackers, qualified as active, have, however, a limited view of the network;
- Global, where the attacker is internal and possesses an entire view of the network. Consequently, they are able to control and observe all the communications, and, therefore, to gather any available information regarding the whole network. Frequently, this attacker is also the network administrator.
- Activity correlation. As long as an address stays valid, even if a device changes its network, an attacker can associate communications, and thus the activity, of this address;
- Location. An attacker can try to probe a network to look for a previously observed address, recovering the topology and observing movements, mainly in wireless scenarios. By leading an eavesdropping attack on a network implementing the KNX protocol, an attacker can list the devices present in the network [185]. Later, by analyzing the traffic on these identifiers, the hacker can track the people in the building. Tracking of network users can also be done in a simple way by means of the WiFi protocol [186];
- Address scan. Once the protocol used to generate the addresses in the network has been identified, an attacker can reduce the potential addresses in order to carry out attacks;
- Exploitation of specific equipment vulnerabilities. A MAC address, referred to a an organizationally unique identifier (OUI), is composed of 24 bits assigned by the IEEE. The OUI not only identifies the equipment manufacturer, but also allows a hacker to know the hardware’s weakness in order to conduct a targeted attack, such as against the AMI infrastructure.
4.4. Solutions for Improving Security and Privacy
4.4.1. Prevention Mechanisms Defined in Standards
4.4.2. Detection Systems
4.4.3. Dedicated Solutions
5. Perspectives
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Acronyms
| AI | Artificial Intelligence |
| AMI | Advanced metering infrastructure |
| ANN | Artificial neural network |
| BAS | Building Automation System |
| BEMS | Building Energy Management System |
| CNN | Convolutional neural network |
| CPS | Cyber-Physical System |
| CPSoS | Cyber-Physical System of Systems |
| DL | Deep learning |
| DoS | Denial of Service |
| DR | Demand response |
| DSM | Demand Side Management |
| EC | Edge computing |
| EV | Electrical vehicle |
| FLA | Fuzzy logic algorithm |
| FLC | Fuzzy logic controller |
| GW | Gateway |
| HAN | Home Area Network |
| HEMS | Home Energy Management System |
| HMI | Human-Machine Interface |
| IB | Intelligent building |
| ICT | Information and communications technology |
| IDPS | Intrusion detection and prevention system |
| IDS | Intrusion Detection System |
| IoE | Internet of energy |
| MAC | Medium access control |
| MAS | Multiagent system |
| MG | Electrical microgrid |
| MITM | Man-in-the-Middle |
| ML | Machine learning |
| MPC | Model-based predictive control |
| NAN | Neighborhood Area Network |
| NZEB | Net-Zero Energy Building |
| OUI | Organizationally Unique Identifier |
| PEB | Positive Energy Building |
| PMU | Phasor measurement unit |
| PV | Photovoltaic |
| QoS | Quality of service |
| RNN | Recurrent neural network |
| RTS | Request to Send |
| SCADA | Supervisory control and data acquisition |
| SG | Smart Grid |
| SH | Smart home |
| SM | Smart meter |
| SoS | System of Systems |
| WAN | Wide Area Network |
| ZEB | Zero Energy Building |
References
- Ipakchi, A.; Albuyeh, F. Grid of the future. IEEE Power Energy Mag. 2009, 7, 52–62. [Google Scholar] [CrossRef]
- Gharavi, H.; Ghafurian, R. Smart Grid: The electric energy system of the future [Scanning the issue]. Proc. IEEE 2011, 99, 917–921. [Google Scholar] [CrossRef]
- Dileep, G. A survey on smart grid technologies and applications. Renew. Energy 2020, 146, 2589–2625. [Google Scholar] [CrossRef]
- Joseph, A.; Balachandra, P. Smart grid to energy internet: A systematic review of transitioning electricity systems. IEEE Access 2020, 8, 215787–215805. [Google Scholar] [CrossRef]
- Mahmud, K.; Khan, B.; Ravishankar, J.; Ahmadi, A.; Siano, P. An internet of energy framework with distributed energy resources, prosumers and small-scale virtual power plants: An overview. Renew. Sustain. Energy Rev. 2020, 127, 109840. [Google Scholar] [CrossRef]
- Bie, Z.; Lin, Y.; Li, G.; Li, F. Battling the extreme: A study on the power system resilience. Proc. IEEE 2017, 105, 1253–1266. [Google Scholar] [CrossRef]
- Gellings, C.W.; Samotyj, M. Smart Grid as advanced technology enabler of demand response. Energy Effic. 2013, 6, 685–694. [Google Scholar] [CrossRef]
- Wormuth, B.; Wang, S.; Dehghanian, P.; Barati, M.; Estebsari, A.; Filomena, T.P.; Kapourchali, M.H.; Lejeune, M.A. Electric power grids under high-absenteeism pandemics: History, context, response, and opportunities. IEEE Access 2020, 8, 215727–215747. [Google Scholar] [CrossRef]
- de C Henshaw, M.J. Systems of systems, cyber-physical systems, the internet-of-things…whatever next? Insight 2016, 19, 51–54. [Google Scholar] [CrossRef]
- Yu, X.; Xue, Y. Smart grids: A cyber–physical systems perspective. Proc. IEEE 2016, 104, 1058–1070. [Google Scholar] [CrossRef]
- Chapurlat, V.; Daclin, N. System interoperability: Definition and proposition of interface model in MBSE Context. IFAC Proc. Vol. 2012, 45–46, 1523–1528. [Google Scholar] [CrossRef]
- Masior, J.; Schneider, B.; Kürümlüoglu, M.; Riedel, O. Beyond Model-Based Systems Engineering towards Managing Complexity. Procedia CIRP 2020, 91, 325–329. [Google Scholar] [CrossRef]
- Penya, Y.K.; Borges, C.E.; Haase, J.; Bruckner, D. Smart Buildings and the Smart Grid. In Proceedings of the 39th Annual Conference of the IEEE Industrial Electronics Society (IECON), Vienna, Austria, 10–13 November 2013. [Google Scholar] [CrossRef]
- Mofidi, F.; Akbari, H. Intelligent buildings: An overview. Energy Build. 2020, 223, 110192. [Google Scholar] [CrossRef]
- Tang, H.; Wang, S.; Li, H. Flexibility categorization, sources, capabilities and technologies for energy-flexible and grid-responsive buildings: State-of-the-art and future perspective. Energy 2021, 219, 119598. [Google Scholar] [CrossRef]
- Llaria, A.; Terrasson, G.; Curea, O.; Jiménez, J. Application of wireless sensor and actuator networks to achieve intelligent microgrids: A promising approach towards a global smart grid deployment. Appl. Sci. 2016, 6, 61. [Google Scholar] [CrossRef] [Green Version]
- Adu-Kankam, K.O.; Camarinha-Matos, L.M. Towards collaborative Virtual Power Plants: Trends and convergence. Sustain. Energy Grids Netw. 2018, 16, 217–230. [Google Scholar] [CrossRef]
- Jia, M.; Komeily, A.; Wang, Y.; Srinivasan, R.S. Adopting Internet of Things for the development of smart buildings: A review of enabling technologies and applications. Autom. Constr. 2019, 101, 111–126. [Google Scholar] [CrossRef]
- Ahmad, T.; Zhang, D. Using the internet of things in smart energy systems and networks. Sustain. Cities Soc. 2021, 68, 102783. [Google Scholar] [CrossRef]
- Llaria, A.; Jiménez, J.; Curea, O. Study on communication technologies for the optimal operation of smart grids. Trans. Emerg. Tel. Tech. 2014, 25, 1009–1019. [Google Scholar] [CrossRef]
- Kabalci, Y. A survey on smart metering and smart grid communication. Renew. Sustain. Energy Rev. 2016, 57, 302–318. [Google Scholar] [CrossRef]
- Wang, S. Making buildings smarter, grid-friendly, and responsive to smart grids. Sci. Technol. Built Environ. 2016, 22, 629–632. [Google Scholar] [CrossRef] [Green Version]
- Taveres-Cachat, E.; Grynning, S.; Thomsen, J.; Selkowitz, S. Responsive building envelope concepts in zero emission neighborhoods and smart cities—A roadmap to implementation. Build. Environ. 2019, 149, 446–457. [Google Scholar] [CrossRef]
- Kim, H.; Choi, H.; An, J.; Yeom, S.; Hong, T. A systematic review of the smart energy conservation system: From smart homes to sustainable smart cities. Renew. Sustain. Energy Rev. 2021, 140, 110755. [Google Scholar] [CrossRef]
- Moslehi, K.; Kumar, R. A reliability perspective of the smart grid. IEEE Trans. Smart Grid 2010, 1, 57–64. [Google Scholar] [CrossRef]
- Chen, T.M.; Abu-Nimeh, S. Lessons from Stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- Nguyen, T.; Wang, S.; Alhazmi, M.; Nazemi, M.; Estebsari, A.; Dehghanian, P. Electric power grid resilience to cyber adversaries: State of the art. IEEE Access 2020, 8, 87592–87608. [Google Scholar] [CrossRef]
- Tan, S.; Wu, Y.; Xie, P.; Guerrero, J.M.; Vasquez, J.C.; Abusorrah, A. New challenges in the design of microgrid systems: Communication networks, cyberattacks, and resilience. IEEE Electrif. Mag. 2020, 8, 98–106. [Google Scholar] [CrossRef]
- Mylrea, M.; Gourisetti, S.N.G.; Nicholls, A. An Introduction to Buildings Cybersecurity Framework. In Proceedings of the IEEE Symposium Series on Computational Intelligence (SSCI), Honolulu, HI, USA, 27 November–1 December 2017. [Google Scholar] [CrossRef]
- Lopes, A.J.; Lezama, R.; Pineda, R. Model Based Systems Engineering for Smart Grids as Systems of Systems. Procedia Comput. Sci. 2011, 6, 441–450. [Google Scholar] [CrossRef] [Green Version]
- NIST—National Institute of Standard and Technology. NIST—National Institute of Standard and Technology. NIST Framework and Roadmap for Smart Grid Interoperability Standards Release 1.0. In Special Publication (NIST SP)–1108; Locke, G., Gallagher, P.D., Eds.; Office of the National Coordinator for Smart Grid Interoperability: Gaithersburg, MD, USA, 2010. [Google Scholar] [CrossRef]
- Nielsen, C.B.; Larsen, P.G.; Fitzgerald, J.; Woodcock, J.; Peleska, J. Systems of Systems Engineering: Basic concepts, model-based techniques, and research directions. ACM Comput. Surv. 2015, 48, 18. [Google Scholar] [CrossRef]
- Maier, M.W. Architecting principles for systems-of-systems. Syst. Eng. 1998, 1, 267–284. [Google Scholar] [CrossRef]
- Merlo, C.; Girard, P. Information system modelling for engineering design co-ordination. Comput. Ind. 2004, 55, 317–334. [Google Scholar] [CrossRef]
- Marashi, K.; Sarvestani, S.S.; Hurson, A.R. Consideration of cyber-physical interdependencies in reliability modeling of smart grids. IEEE Trans. Sustain. Comput. 2018, 3, 73–83. [Google Scholar] [CrossRef]
- Hossain, M.M.; Peng, C. Cyber–physical security for on-going smart grid initiatives: A survey. IET Cyber Phys. Syst. Theor. Appl. 2020, 5, 233–244. [Google Scholar] [CrossRef]
- Monostori, L. Cyber-physical production systems: Roots, Expectations and R&D challenges. Procedia CIRP 2014, 17, 9–13. [Google Scholar] [CrossRef]
- Rudtsch, V.; Gausemeier, J.; Gesing, J.; Mittag, T.; Peter, S. Pattern-based business model development for cyber-physical production systems. Procedia CIRP 2014, 25, 313–319. [Google Scholar] [CrossRef] [Green Version]
- Al-Mhiqani, M.N.; Ahmad, R.; Abdulkareem, K.H.; Ali, N.S. Investigation study of cyber-physical systems: Characteristics, application domains, and security challenges. ARPN J. Eng. Appl. Sci. 2017, 12, 6557–6567. [Google Scholar]
- Nunes, D.S.; Zhang, P.; Sá Silva, J. A survey on Human-in-the-Loop applications towards an Internet of All. IEEE Commun. Surv. Tutor. 2015, 17, 944–965. [Google Scholar] [CrossRef]
- Cimini, C.; Pirola, F.; Pinto, R.; Cavalieri, S. A human-in-the-loop manufacturing control architecture for the next generation of production systems. J. Manuf. Syst. 2020, 54, 258–271. [Google Scholar] [CrossRef]
- Zhao, J.; Wen, F.; Xue, Y.; Li, X.; Dong, Z. Cyber-physical power systems Architecture, implementation techniques and challenges. Autom. Electr. Power Syst. 2010, 34, 1–7. [Google Scholar]
- Masera, M.; Bompard, E.F.; Profumo, F.; Hadjsaid, N. Smart (electricity) grids for smart cities: Assessing roles and societal impacts. Proc. IEEE 2018, 106, 613–625. [Google Scholar] [CrossRef]
- Wong, J.K.W.; Li, H.; Wang, S.W. Intelligent building research: A review. Autom. Constr. 2005, 14, 143–159. [Google Scholar] [CrossRef]
- Manic, M.; Amarasinghe, K.; Rodriguez-Andina, J.J.; Rieger, C. Intelligent buildings of the future: Cyberaware, deep learning powered, and human interacting. IEEE Ind. Electron. Mag. 2016, 10, 32–49. [Google Scholar] [CrossRef]
- Dakheel, J.A.; Del Pero, C.; Aste, N.; Leonforte, F. Smart buildings features and key performance indicators: A review. Sustain. Cities Soc. 2020, 61, 102328. [Google Scholar] [CrossRef]
- Lee, E.A. Cyber-Physical Systems—Are Computing Foundations Adequate? In Proceedings of the Position Paper for NSF Workshop on Cyber-Physical Systems: Research Motivation, Techniques and Roadmap, Austin, TX, USA, 16–17 October 2006. [Google Scholar]
- Jimada-Ojuolape, B.; Teh, J. Impact of the integration of information and communication technology on power system reliability: A review. IEEE Access 2020, 8, 24600–24615. [Google Scholar] [CrossRef]
- Kolokotsa, D. The role of smart grids in the building sector. Energy Build. 2016, 116, 703–708. [Google Scholar] [CrossRef] [Green Version]
- Lawrence, T.M.; Boudreau, M.C.; Helsen, L.; Henze, G.; Mohammadpour, J.; Noonan, D.; Patteeuw, D.; Pless, S.; Watson, R.T. Ten questions concerning integrating smart buildings into the smart grid. Build. Environ. 2016, 108, 273–283. [Google Scholar] [CrossRef] [Green Version]
- Li, C.Z.; Lai, X.; Xiao, B.; Tam, V.W.Y.; Guo, S.; Zhao, Y. A holistic review on life cycle energy of buildings: An analysis from 2009 to 2019. Renew. Sustain. Energy Rev. 2020, 134, 110372. [Google Scholar] [CrossRef]
- Krarti, M.; Aldubyan, M. Review analysis of COVID-19 impact on electricity demand for residential buildings. Renew. Sustain. Energy Rev. 2021, 110888. [Google Scholar] [CrossRef]
- Takigawa, T.; Wang, B.L.; Sakano, N.; Wang, D.H.; Ogino, K.; Kishi, R. A longitudinal study of environmental risk factors for subjective symptoms associated with sick building syndrome in new dwellings. Sci. Total Environ. 2009, 407, 5223–5228. [Google Scholar] [CrossRef] [PubMed]
- Lee, D.; Cheng, C.C. Energy savings by energy management systems: A review. Renew. Sustain. Energy Rev. 2016, 56, 760–777. [Google Scholar] [CrossRef]
- Yang, T.; Clements-Croome, D.; Marson, M. Building energy management systems. In Encyclopedia of Sustainable Technologies; Abraham, M.A., Ed.; Elsevier: Amsterdam, The Netherlands, 2017; pp. 291–309. [Google Scholar] [CrossRef]
- Domingues, P.; Carreira, P.; Vieira, R.; Kastner, W. Building automation systems: Concepts and technology review. Comp. Stand. Inter. 2016, 45, 1–12. [Google Scholar] [CrossRef]
- Kumar, A.; Singh, A.; Kumar, M.; Singh, M.K.; Mahanta, P.; Mukhopadhyay, S.C. Sensing technologies for monitoring intelligent buildings: A review. IEEE Sens. J. 2018, 18, 4847–4860. [Google Scholar] [CrossRef]
- Hannan, M.A.; Faisal, M.; Ker, P.J.; Mun, L.H.; Parvin, K.; Mahlia, T.M.I.; Blaabjerg, F. A review of internet of energy based building energy management systems: Issues and recommendations. IEEE Access 2018, 6, 38997–39014. [Google Scholar] [CrossRef]
- Sartori, I.; Napolitano, A.; Voss, K. Net zero energy buildings: A consistent definition framework. Energy Build. 2012, 48, 220–232. [Google Scholar] [CrossRef] [Green Version]
- Cao, X.; Dai, X.; Liu, J. Building energy-consumption status worldwide and the state-of-the-art technologies for zero-energy buildings during the past decade. Energy Build. 2016, 128, 198–213. [Google Scholar] [CrossRef]
- Wei, W.; Skye, H.M. Residential net-zero energy buildings: Review and perspective. Renew. Sustain. Energy Rev. 2021, 142, 110859. [Google Scholar] [CrossRef]
- Magrini, A.; Lentini, G.; Cuman, S.; Bodrato, A.; Marenco, L. From nearly zero energy buildings (NZEB) to positive energy buildings (PEB): The next challenge—The most recent European trends with some notes on the energy analysis of a forerunner PEB example. Dev. Built Environ. 2020, 3, 100019. [Google Scholar] [CrossRef]
- Zhou, B.; Li, W.; Chan, K.W.; Cao, Y.; Kuang, Y.; Liu, X.; Wang, X. Smart home energy management systems: Concept, configurations, and scheduling strategies. Renew. Sustain. Energy Rev. 2016, 61, 30–40. [Google Scholar] [CrossRef]
- Leitão, J.; Gil, P.; Ribeiro, B.; Cardoso, A. A survey on home energy management. IEEE Access 2020, 8, 5699–5722. [Google Scholar] [CrossRef]
- Zafar, U.; Bayhan, S.; Sanfilippo, A. Home energy management system concepts, configurations, and technologies for the smart grid. IEEE Access 2020, 8, 119271–119286. [Google Scholar] [CrossRef]
- Hong, T.; Yan, D.; D’Oca, S.; Chen, C. Ten questions concerning occupant behavior in buildings: The big picture. Build. Environ. 2017, 114, 518–530. [Google Scholar] [CrossRef] [Green Version]
- Nguyen, T.A.; Aiello, M. Energy intelligent buildings based on user activity: A survey. Energy Build. 2013, 56, 244–257. [Google Scholar] [CrossRef] [Green Version]
- Palensky, P.; Dietrich, D. Demand side management: Demand response, intelligent energy systems, and smart loads. IEEE Trans. Ind. Inf. 2011, 7, 381–388. [Google Scholar] [CrossRef] [Green Version]
- Mariano-Hernández, D.; Hernández-Callejo, L.; Zorita-Lamadrid, A.; Duque-Pérez, O.; Santos García, F. A review of strategies for building energy management system: Model predictive control, demand side management, optimization, and fault detect & diagnosis. J. Build. Eng. 2021, 33, 101692. [Google Scholar] [CrossRef]
- Chen, Y.; Xu, P.; Gu, J.; Schmidt, F.; Li, W. Measures to improve energy demand flexibility in buildings for demand response (DR): A review. Energy Build. 2018, 177, 125–139. [Google Scholar] [CrossRef]
- Shareef, H.; Ahmed, M.S.; Mohamed, A.; Al Hassan, E. Review on home energy management system considering demand responses, smart technologies, and intelligent controllers. IEEE Access 2018, 6, 24498–24509. [Google Scholar] [CrossRef]
- Beaudin, M.; Zareipour, H. Home energy management systems: A review of modelling and complexity. Renew. Sustain. Energy Rev. 2015, 45, 318–335. [Google Scholar] [CrossRef]
- Shakeri, M.; Pasupuleti, J.; Amin, N.; Rokonuzzaman, M.; Low, F.W.; Yaw, C.T.; Asim, N.; Samsudin, N.A.; Tiong, S.K.; Hen, C.K.; et al. An overview of the building energy management system considering the demand response programs, smart strategies and smart grid. Energies 2020, 13, 3299. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, N.; Wang, W.; Guan, X.; Xu, Z.; Dong, B.; Liu, T. Coordinating the operations of smart buildings in smart grids. Appl. Energy 2018, 228, 2510–2525. [Google Scholar] [CrossRef] [Green Version]
- Liu, N.; Wang, J.; Yu, X.; Ma, L. Hybrid energy sharing for smart building cluster with CHP system and PV prosumers: A coalitional game approach. IEEE Access 2018, 6, 34098–34108. [Google Scholar] [CrossRef]
- Shaikh, P.H.; Nor, N.B.M.; Nallagownden, P.; Elamvazuthi, I.; Ibrahim, T. A review on optimized control systems for building energy and comfort management of smart sustainable buildings. Renew. Sustain. Energy Rev. 2014, 34, 409–429. [Google Scholar] [CrossRef]
- Freire, V.A.; Arruda, L.V.R.; Bordons, C.; Teno, G. Home Energy Management for a AC/DC Microgrid Using Model Predictive Control. In Proceedings of the International Conference on Smart Energy Systems and Technologies (SEST), Porto, Portugal, 9–11 September 2019. [Google Scholar] [CrossRef]
- Novickij, I.; Joós, G. Model Predictive Control-Based Approach for Microgrid Energy Management. In Proceedings of the IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019. [Google Scholar] [CrossRef]
- Hamidi, M.; Bouattane, O. Commercial Building Energy Management Design for HVAC System Based on Fuzzy Logic. In Proceedings of the 7th International Renewable and Sustainable Energy Conference (IRSEC), Agadir, Morocco, 27–30 November 2019. [Google Scholar] [CrossRef]
- Ghaffar, M.; Naseer, N.; Sheikh, S.R.; Naved, M.; Aziz, U.; Koreshi, Z.U. Electrical Energy Management of Building Using Fuzzy Control. In Proceedings of the International Conference on Robotics and Automation in Industry (ICRAI), Rawalpindi, Pakistan, 21–22 October 2019. [Google Scholar] [CrossRef]
- Tingting, H.; Abhisek, U. Design of Fuzzy Logic Based Controller for Energy Efficient Operation in Building. In Proceedings of the 42nd Annual Conference of the IEEE Industrial Electronics Society IECON, Florence, Italy, 23–26 October 2016. [Google Scholar] [CrossRef]
- Kontogiannis, D.; Bargiotas, D.; Daskalopulu, A. Fuzzy control system for smart energy management in residential buildings based on environmental data. Energies 2021, 14, 752. [Google Scholar] [CrossRef]
- Aung, H.N.; Khambadkone, A.M.; Srinivasan, D.; Logenthiran, T. Agent-based intelligent control for real-time operation of a microgrid. In Proceedings of the 2010 Joint International Conference on Power Electronics, Drives and Energy Systems & 2010 Power India, New Delhi, India, 20–23 December 2010. [Google Scholar] [CrossRef]
- Oliveira, P.; Gomes, L.; Pinto, T.; Faria, P.; Vale, Z.; Morais, H. Load Control Timescales Simulation in a Multi-Agent Smart Grid Platform. In Proceedings of the IEEE PES ISGT Europe, Lyngby, Denmark, 6–9 October 2013. [Google Scholar] [CrossRef] [Green Version]
- McArthur, S.D.J.; Davidson, E.M.; Catterson, V.M.; Dimeas, A.L.; Hatziargyriou, N.D.; Ponci, F.; Funabashi, T. Multi-agent systems for power engineering applications—Part I: Concepts, approaches, and technical challenges. IEEE Trans. Power Syst. 2007, 22, 1743–1752. [Google Scholar] [CrossRef] [Green Version]
- Khamphanchai, W.; Pipattanasomporn, M.; Rahman, S. A Multi-Agent System for Restoration of an Electric Power Distribution Network with Local Generation. In Proceedings of the Power and Energy Society General Meeting, San Diego, CA, USA, 22–26 July 2012. [Google Scholar] [CrossRef]
- Chen, M.; McArthur, S.D.J.; Kockar, I.; Pitt, J. Evaluating a MAS Architecture for Flexible Distribution Power Flow Management. In Proceedings of the 18th International Conference on Intelligent System Application to Power Systems, Porto, Portugal, 11–16 September 2015. [Google Scholar] [CrossRef]
- Lagorse, J.; Paire, D.; Miraoui, A. A multi-agent system for energy management of distributed power sources. Renew. Energy 2010, 35, 174–182. [Google Scholar] [CrossRef]
- Ferber, J. Multi-Agent Systems. An Introduction to Distributed Artificial Intelligence; Addison Wesley: London, UK, 1999. [Google Scholar]
- Cirrincione, M.; Cossentino, M.; Gaglio, S.; Hilaire, V.; Koukam, A.; Pucci, M.; Sabatucci, L.; Vitale, G. Intelligent Energy Management System. In Proceedings of the 7th IEEE International Conference on Industrial Informatics, Cardiff, UK, 23–26 June 2009. [Google Scholar] [CrossRef] [Green Version]
- Boussaada, Z.; Curea, O.; Camblong, H.; Mrabet, N.B.; Hacala, A. Multi-agent systems for the dependability and safety of microgrids. Int. J. Interact. Des. Manuf. 2016, 10, 1–13. [Google Scholar] [CrossRef]
- Dimeas, A.L.; Hatziargyriou, N.D. A MAS Architecture for Microgrids Control. In Proceedings of the 13th International Conference on Intelligent Systems Application to Power Systems, Arlington, VA, USA, 6–10 November 2005. [Google Scholar] [CrossRef]
- Iksan, N.; Udayanti, E.D.; Arfriandi, A.; Widodo, D.A. Automatic Control Using Fuzzy Techniques for Energy Management on Smart Building. In Proceedings of the International Conference on Computer Engineering, Network and Intelligent Multimedia (CENIM), Surabaya, Indonesia, 26–27 November 2018. [Google Scholar] [CrossRef]
- Feng, C.; Wang, Y.; Chen, Q.; Ding, Y.; Strbac, G.; Kang, C. Smart grid encounters edge computing: Opportunities and applications. Adv. Appl. Energy 2021, 1, 100006. [Google Scholar] [CrossRef]
- Runge, J.; Zmeureanu, R. A review of deep learning techniques for forecasting energy use in buildings. Energies 2021, 14, 608. [Google Scholar] [CrossRef]
- Boussaada, Z.; Curea, O.; Camblong, H.; Mrabet, N.B. Energy management for embedded microgrid using multi agent system. In Proceedings of the 7th International Conference on Automation, Control Engineering & Computer Science (ACECS), Sousse, Tunisia, 12–13 October 2020; pp. 26–31. Available online: http://ipco-co.com/PET_Journal/ACECS%20Proceedings/A-3.pdf (accessed on 25 March 2021).
- Khan, Z.A.; Hussain, T.; Ullah, A.; Rho, S.; Lee, M.; Baik, S.W. Towards efficient electricity forecasting in residential and commercial buildings: A novel hybrid CNN with a LSTM-AE based framework. Sensors 2020, 20, 1399. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Verma, A.; Prakash, S.; Srivastava, V.; Kumar, A.; Mukhopadhyay, S.C. Sensing, controlling, and IoT infrastructure in smart building: A review. IEEE Sens. J. 2019, 19, 9036–9046. [Google Scholar] [CrossRef]
- Yaïci, W.; Krishnamurthy, K.; Entchev, E.; Longo, M. Recent advances in Internet of Things (IoT) infrastructures for building energy systems: A review. Sensors 2021, 21, 2152. [Google Scholar] [CrossRef]
- Iqbal, J.; Khan, M.; Talha, M.; Farman, H.; Jan, B.; Muhammad, A.; Khattak, H.A. A generic internet of things architecture for controlling electrical energy consumption in smart homes. Sustain. Cities Soc. 2018, 43, 443–450. [Google Scholar] [CrossRef]
- Karthick, T.; Charles Raja, S.; Jeslin Drusila Nesamalar, J.; Chandrasekaran, K. Design of IoT based smart compact energy meter for monitoring and controlling the usage of energy and power quality issues with demand side management for a commercial building. Sustain. Energy Grids Netw. 2021, 26, 100454. [Google Scholar] [CrossRef]
- Hossain, M.; Weng, Z.; Schiano-Phan, R.; Scott, D.; Lau, B. Application of IoT and BEMS to visualise the environmental performance of an educational building. Energies 2020, 13, 4009. [Google Scholar] [CrossRef]
- Usman, A.; Haider Shami, S. Evolution of Communication Technologies for Smart Grid applications. Renew. Sustain. Energy Rev. 2013, 19, 191–199. [Google Scholar] [CrossRef]
- Ancillotti, E.; Bruno, R.; Conti, M. The role of communication systems in smart grids: Architectures, technical solutions and research challenges. Comput. Commun. 2013, 36, 1665–1697. [Google Scholar] [CrossRef] [Green Version]
- Shaukat, N.; Ali, S.M.; Mehmood, C.A.; Khan, B.; Jawad, M.; Farid, U.; Ullah, Z.; Anwar, S.M.; Majid, M. A survey on consumers empowerment, communication technologies, and renewable generation penetration within Smart Grid. Renew. Sustain. Energy Rev. 2018, 81, 1453–1475. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergüt, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart Grid Technologies: Communication Technologies and Standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef] [Green Version]
- Saleem, Y.; Crespi, N.; Rehmani, M.H.; Copeland, R. Internet of things-aided smart grid: Technologies, architectures, applications, prototypes, and future research directions. IEEE Access 2019, 7, 62962–63003. [Google Scholar] [CrossRef]
- Zhu, Z.; Lambotharan, S.; Chin, W.H.; Fan, Z. Overview of demand management in smart grid and enabling wireless communication technologies. IEEE Wirel. Commun. 2012, 19, 48–56. [Google Scholar] [CrossRef]
- Ahmed, S.; Gondal, T.M.; Adil, M.; Malik, S.A.; Qureshi, R. A Survey on Communication Technologies in Smart Grid. In Proceedings of the IEEE PES GTD Grand International Conference and Exposition Asia (GTD Asia), Bangkok, Thailand, 19–23 March 2019. [Google Scholar] [CrossRef]
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Review of communication technologies for smart homes/building applications. In Proceedings of the IEEE Innovative Smart Grid Technologies—Asia (ISGT ASIA), Bangkok, Thailand, 3–6 November 2015. [Google Scholar] [CrossRef]
- Vega, A.M.; Santamaria, F.; Rivas, E. Modeling for home electric energy management: A review. Renew. Sustain. Energy Rev. 2015, 52, 948–959. [Google Scholar] [CrossRef]
- Emmanuel, M.; Rayudu, R. Communication technologies for smart grid applications: A survey. J. Netw. Comput. Appl. 2016, 74, 133–148. [Google Scholar] [CrossRef]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar] [CrossRef] [Green Version]
- Lohia, K.; Jain, Y.; Patel, C.; Doshi, N. Open Communication Protocols for Building Automation Systems. Procedia Comput. Sci. 2019, 160, 723–727. [Google Scholar] [CrossRef]
- Gungor, V.; Hancke, G. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef] [Green Version]
- Risteska Stojkoska, B.L.; Trivodaliev, K.V. A review of Internet of Things for smart home: Challenges and solutions. J. Clean. Prod. 2017, 140, 1454–1464. [Google Scholar] [CrossRef]
- Lobaccaro, G.; Carlucci, S.; Löfström, E. A review of systems and technologies for smart homes and smart grids. Energies 2016, 9, 348. [Google Scholar] [CrossRef] [Green Version]
- Mocrii, D.; Chen, Y.; Musilek, P. IoT-based smart homes: A review of system architecture, software, communications, privacy and security. Internet Things 2018, 1–2, 81–98. [Google Scholar] [CrossRef]
- De Almeida, L.F.F.; Dos Santos, J.R.; Melo Pereira, L.A.; Cerqueira Sodré, A., Jr.; Leonel Mendes, L.; Rodrigues, J.J.P.C.; Rabelo, R.A.L.; Alberti, A.M. Control networks and smart grid teleprotection: Key aspects, technologies, protocols, and case-studies. IEEE Access 2020, 8, 174049–174079. [Google Scholar] [CrossRef]
- Komninos, N.; Philippou, E.; Pitsillides, A. Survey in smart grid and smart home security: Issues, challenges and countermeasures. IEEE Commun. Surv. Tutor. 2014, 16, 1933–1954. [Google Scholar] [CrossRef]
- Granzer, W.; Praus, F.; Kastner, W. Security in Building Automation Systems. IEEE Trans. Ind. Electron. 2010, 57, 3622–3630. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocess. Microsyst. 2020, 77, 103201. [Google Scholar] [CrossRef]
- Kumar, P.; Lin, Y.; Bai, G.; Paverd, A.; Dong, J.S.; Martin, A. Smart grid metering networks: A survey on security, privacy and open research issues. IEEE Commun. Surv. Tutor. 2019, 21, 2886–2927. [Google Scholar] [CrossRef] [Green Version]
- Ciholas, P.; Lennie, A.; Sadigova, P.; Such, J.M. The security of smart buildings: A systematic literature review. arXiv 2019, arXiv:1901.05837, under review. [Google Scholar]
- Deshmukh, A.P.A.G.; Qureshi, D. Transparent data encryption-Solution for security of database contents. IJACSA 2011, 2, 25–28. [Google Scholar] [CrossRef]
- Lombardi, F.; Aniello, L.; De Angelis, S.; Margheri, A.; Sassone, V. A Blockchain-Based Infrastructure for Reliable and Cost-effective IoT-aided Smart Grids. In Proceedings of the Living in the Internet of Things Conference: Cybersecurity of the IoT, London, UK, 28–29 March 2018. [Google Scholar] [CrossRef]
- Butun, I.; Lekidis, A.; Dos Santos, D. Security and Privacy in Smart Grids: Challenges, Current Solutions and Future Opportunities. In Proceedings of the 6th International Conference on Information Systems Security and Privacy (ICISSP), Valletta, Malta, 25–27 February 2020. [Google Scholar] [CrossRef]
- Pöhls, H.C.; Angelakis, V.; Suppan, S.; Fischer, K.; Oikonomou, G.; Tragos, E.Z.; Mouroutis, T. RERUM: Building a reliable IoT upon privacy-and security-enabled smart objects. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Istanbul, Turkey, 6–9 April 2014. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Alromaihi, S.; Elmedany, W.; Balakrishna, C. Cyber Security Challenges of Deploying IoT in Smart Cities for Healthcare Applications. In Proceedings of the 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, 6–8 August 2018. [Google Scholar] [CrossRef]
- Osisiogu, U. A review on Cyber-Physical Security of Smart Buildings and Infrastructure. In Proceedings of the 15th International Conference on Electronics, Computer and Computation (ICECCO), Abuja, Nigeria, 10–12 December 2019. [Google Scholar] [CrossRef]
- Znaidi, W. Quelques Propositions de Solutions Pour la Sécurité des Réseaux de Capteurs Sans Fil. Ph.D. Thesis, Institut National des Sciences Appliquées (INSA), Lyon, France, 10 October 2010. [Google Scholar]
- Khaund, K. Cybersecurity in Smart Buildings Inaction is not Option any More. Frost Sullivan Collab. Ind. Perspect. 2015, 9835-19, 1–37. [Google Scholar]
- Huseinović, A.; Mrdović, S.; Bicakci, K.; Uludag, S. A Survey of Denial-of-Service attacks and solutions in the smart grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Zheng, J.; Lee, M.J.; Anshel, M. Toward secure low rate wireless personal area networks. IEEE Trans. Mob. Comput. 2006, 5, 1361–1373. [Google Scholar] [CrossRef]
- Dhunna, G.S. Low Power MAC Security Mechanisms for WSNs in a Smart Grid Environment. Ph.D. Thesis, Faculty of Graduate Studies and Research, University of Regina, Regina, SK, Canada, 4 August 2017. [Google Scholar]
- Zhang, Z.; Gong, S.; Dimitrovski, A.D.; Li, H. Time synchronization attack in smart grid: Impact and analysis. IEEE Trans. Smart Grid 2013, 4, 87–98. [Google Scholar] [CrossRef]
- Zhang, Z.; Wu, J.; Deng, J.; Qiu, M. Jamming ACK Attack to Wireless Networks and a Mitigation Approach. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), New Orleans, LA, USA, 30 November–4 December 2008. [Google Scholar] [CrossRef]
- Sajjad, S.M.; Yousaf, M. Security analysis of IEEE 802.15. 4 MAC in the context of Internet of Things (IoT). In Proceedings of the Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, Pakistan, 12–13 June 2014. [Google Scholar] [CrossRef]
- Ghildiyal, S.; Mishra, A.K.; Gupta, A.; Garg, N. Analysis of denial of service (dos) attacks in wireless sensor. IJRET 2014, 3, 140–143. [Google Scholar] [CrossRef]
- Dos Santos, J.; Terrasson, G.; Llaria, A. Improving Low Power Listening (LPL) Mechanism to Save Energy Consumption. In Proceedings of the IEEE Sensors, Rotterdam, The Netherlands, 25–28 October 2020. [Google Scholar] [CrossRef]
- Raymond, D.R.; Marchany, R.C.; Brownfield, M.I.; Midkiff, S.F. Effects of denial-of-sleep attacks on wireless sensor network MAC protocols. IEEE Trans. Veh. Technol. 2009, 58, 367–380. [Google Scholar] [CrossRef] [Green Version]
- Hijazi, S.; Obaidat, M.S. Address resolution protocol spoofing attacks and security approaches: A survey. Secur. Priv. 2019, 2. [Google Scholar] [CrossRef] [Green Version]
- Sundararajan, A.; Chavan, A.; Saleem, D.; Sarwat, A.I. A survey of protocol-level challenges and solutions for distributed energy resource cyber-physical security. Energies 2018, 11, 2360. [Google Scholar] [CrossRef] [Green Version]
- Kulkarni, S.; Rahul, R.K.; Shreyas, R.; Nagasundari, S.; Honnavalli, P.B. MITM Intrusion Analysis for Advanced Metering Infrastructure Communication in a Smart Grid Environment. In Proceedings of the 3rd International Conference on Computational Intelligence, Security and Internet of Things, Agartala, India, 29–30 December 2020. [Google Scholar] [CrossRef]
- Darwish, I.; Igbe, O.; Celebi, O.; Saadawi, T.; Soryal, J. Smart Grid DNP3 Vulnerability Analysis and Experimentation. In Proceedings of the IEEE 2nd International Conference on Cyber Security and Cloud Computing, New York, NY, USA, 3–5 November 2015. [Google Scholar] [CrossRef]
- Malik, R.; Sehrawat, H.; Singh, Y. Comprehensive study of selective forwarding attack in wireless sensor networks. Int. J. Adv. Res. Comput. Sci. 2017, 8, 1–10. [Google Scholar] [CrossRef]
- Ali, S.; Khan, M.A.; Ahmad, J.; Malik, A.W.; ur Rehman, A. Detection and Prevention of Black Hole Attacks in IOT & WSN. In Proceedings of the Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018. [Google Scholar] [CrossRef]
- Ibhaze, A.E.; Akpabio, M.U.; John, S.N. A Review on Smart Grid Network Security Issues over 6LoWPAN. In Proceedings of the Second International Conference on Internet of things, Data and Cloud Computing (ICC’17), Cambridge, UK, 22–23 March 2017. [Google Scholar] [CrossRef]
- Holmberg, D.G.; Evans, D. BACnet wide area network security threat assessment. NIST Interag. Intern. Rep. (NISTIR) 2003, 7009. [Google Scholar] [CrossRef]
- Swathi, B.H.; Gururaj, H.L. A critical analysis on network layer attacks in wireless sensor network. IRJET 2018, 5, 377–384. [Google Scholar]
- Kumari, D.; Singh, K.; Manjul, M. Performance evaluation of sybil attack in cyber physical system. Procedia Comput. Sci. 2020, 167, 1013–1027. [Google Scholar] [CrossRef]
- Kaur, J.; Tonejc, J.; Wendzel, S.; Meier, M. Securing BACnet’s Pitfalls. In Proceedings of the IFIP International Information Security and Privacy Conference, Hamburg, Germany, 26–28 May 2015. [Google Scholar] [CrossRef] [Green Version]
- Prakash, R.A.; Jeyaseelan, W.S.; Jayasankar, T. Detection, prevention and mitigation of wormhole attack in wireless adhoc network by coordinator. Appl. Mat. 2018, 12, 233–237. [Google Scholar] [CrossRef]
- Yi, P.; Zhu, T.; Zhang, Q.; Wu, Y.; Pan, L. Puppet attack: A denial of service attack in advanced metering infrastructure network. J. Netw. Comput. Appl. 2016, 59, 325–332. [Google Scholar] [CrossRef] [Green Version]
- Mahjabin, T.; Xiao, Y.; Sun, G.; Jiang, W. A survey of distributed denial-of-service attack, prevention, and mitigation techniques. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef] [Green Version]
- Wood, A.D.; Stankovic, J.A. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef] [Green Version]
- Suciu, G.; Sachian, M.A.; Dobrea, M.; Istrate, C.I.; Petrache, A.L.; Vulpe, A.; Vochin, M. Securing the smart grid: A blockchain-based secure smart energy system. In Proceedings of the 54th International Universities Power Engineering Conference (UPEC), Bucharest, Romania, 3–6 September 2019. [Google Scholar] [CrossRef]
- Rajesh, L.; Satyanarayana, P. Vulnerability analysis and enhancement of security of communication protocol in industrial control systems. Helix 2019, 9, 5122–5127. Available online: https://helixscientific.pub/index.php/home/article/view/6 (accessed on 28 March 2021).
- Shin, I.; Cho, M. On Localized Countermeasure against reactive jamming attacks in smart grid wireless mesh networks. Appl. Sci. 2018, 8, 2340. [Google Scholar] [CrossRef] [Green Version]
- Song, T.; Zhou, K.; Li, T. CDMA system design and capacity analysis under disguised jamming. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2487–2498. [Google Scholar] [CrossRef]
- Al-Kahtani, M.S.; Karim, L. A survey on attacks and defense mechanisms in smart grids. Int. J. Comput. Eng. Inf. Technol. 2019, 11, 94–100. [Google Scholar]
- Liu, H.; Ma, H.; El Zarki, M.; Gupta, S. Error control schemes for networks: An overview. Mobile Netw. Appl. 1997, 2, 167–182. [Google Scholar] [CrossRef]
- Falconer, D.D.; Adachi, F.; Gudmundson, B. Time division multiple access methods for wireless personal communications. IEEE Commun. Mag. 1995, 33, 50–57. [Google Scholar] [CrossRef]
- Meghana, J.S.; Subashri, T.; Vimal, K.R. A Survey on ARP Cache Poisoning and Techniques for Detection and Mitigation. In Proceedings of the Fourth International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 16–18 March 2017. [Google Scholar] [CrossRef]
- Khan, W.Z.; Xiang, Y.; Aalsalem, M.Y.; Arshad, Q. The selective forwarding attack in sensor networks: Detections and countermeasures. IJWMT 2012, 2, 33. [Google Scholar] [CrossRef] [Green Version]
- Xin-Sheng, W.; Yong-Zhao, Z.; Shu-ming, X.; Liang-min, W. Lightweight Defense Scheme against Selective forwarding Attacks in Wireless Sensor Networks. In Proceedings of the International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, Zhangjiajie, China, 10–11 October 2009. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad. Hoc. Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Coppolino, L.; D’Antonio, S.; Romano, L.; Spagnuolo, G. An Intrusion Detection System for Critical Information Infrastructures using Wireless Sensor Network Technologies. In Proceedings of the 5th International Conference on Critical Infrastructure (CRIS), Beijing, China, 20–22 September 2010. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil Attack in Sensor Networks: Analysis & Defenses. In Proceedings of the Third International Symposium on Information Processing in Sensor Networks (IPSN), Berkeley, CA, USA, 27 April 2004. [Google Scholar] [CrossRef]
- Arjuman, N.; Manickam, S.; Karuppayah, S.; Rehman, S.U. Review of Security Issues in IPv6 Router Discovery. In Proceedings of the 4th International Conference on Mathematical Sciences and Computer Engineering (ICMSCE), Langkawi, Malaysia, 4–5 May 2017. [Google Scholar]
- Hu, L.; Evans, D. Using Directional Antennas to Prevent Wormhole Attacks. In Proceedings of the 11th Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 5–6 February 2004. [Google Scholar]
- Znaidi, W.; Minier, M.; Babau, J.P. Detecting Wormhole Attacks in Wireless Networks Using Local Neighborhood Information. In Proceedings of the IEEE 19th International Symposium on Personal, Indoor and Mobile Radio Communications, Cannes, France, 15–18 September 2008. [Google Scholar] [CrossRef]
- Gonzalez, H.; Gosselin-Lavigne, M.A.; Stakhanova, N.; Ghorbani, A.A. Chapter 13—The Impact of Application-Layer Denial-of-Service Attacks. In Case Studies in Secure Computing: Achievements and Trends; Issac, B., Israr, N., Eds.; CRC Press: Boca Raton, FL, USA, 2014. [Google Scholar] [CrossRef]
- Hasankhani, A.; Hakimi, S.M.; Shafie-khah, M.; Asadolahi, H. Blockchain technology in the future smart grids: A comprehensive review and frameworks. Int. J. Electr. Power Energy Syst. 2021, 129, 106811. [Google Scholar] [CrossRef]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef] [Green Version]
- Hollick, M.; Nita-Rotaru, C.; Papadimitratos, P.; Perrig, A.; Schmid, S. Toward a taxonomy and attacker model for secure routing protocols. ACM Sigcomm. Comp. Com. 2017, 47, 43–48. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Analysis of Cyber-Attacks on Smart Grid Applications. In Proceedings of the International Conference on Artificial Intelligence and Data Processing (IDAP), Malatya, Turkey, 28–30 September 2018. [Google Scholar] [CrossRef]
- Lisovich, M.A.; Mulligan, D.K.; Wicker, S.B. Inferring personal information from demand-response systems. IEEE Secur. Priv. 2010, 8, 11–20. [Google Scholar] [CrossRef]
- Dos Santos, J.; Hennebert, C.; Lauradoux, C. Preserving privacy in secured ZigBee wireless sensor networks. In Proceedings of the IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015. [Google Scholar] [CrossRef]
- Luo, X.; Ji, X.; Park, M.S. Location privacy against traffic analysis attacks in wireless sensor networks. In Proceedings of the International Conference on Information Science and Applications, Seoul, Korea, 21–23 April 2010. [Google Scholar] [CrossRef]
- Kamat, P.; Zhang, Y.; Trappe, W.; Ozturk, C. Enhancing source-location privacy in sensor network routing. In Proceedings of the 25th IEEE international conference on distributed computing systems (ICDCS’05), Columbus, OH, USA, 6–10 June 2005. [Google Scholar] [CrossRef] [Green Version]
- Deng, J.; Han, R.; Mishra, S. Countermeasures against traffic analysis attacks in wireless sensor networks. In Proceedings of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM’05), Athens, Greece, 5–9 September 2005. [Google Scholar] [CrossRef]
- Cooper, A.; Gont, F.; Thaler, D. Security and privacy considerations for ipv6 address generation mechanisms. Netw. Work. Group RFC 2016, 7721, 1–18. Available online: https://tools.ietf.org/html/rfc7721 (accessed on 28 March 2021).
- Mundt, T.; Wickboldt, P. Security in building automation systems-a first analysis. In Proceedings of the International Conference on Cyber Security And Protection Of Digital Services (Cyber Security), London, UK, 13–14 June 2016. [Google Scholar] [CrossRef]
- Bonné, B.; Barzan, A.; Quax, P.; Lamotte, W. WiFiPi: Involuntary tracking of visitors at mass events. In Proceedings of the IEEE 14th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Madrid, Spain, 4–7 June 2013. [Google Scholar] [CrossRef]
- Wallgren, L.; Raza, S.; Voigt, T. Routing attacks and countermeasures in the RPL-based internet of things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar] [CrossRef]
- Sharma, V.; You, I.; Andersson, K.; Palmieri, F.; Rehmani, M.H.; Lim, J. Security, privacy and trust for smart mobile-Internet of Things (M-IoT): A survey. IEEE Access 2020, 8, 167123–167163. [Google Scholar] [CrossRef]
- Kong, J.H.; Ang, L.M.; Seng, K.P. A comprehensive survey of modern symmetric cryptographic solutions for resource constrained environments. J. Netw. Comput. Appl. 2015, 49, 15–50. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. AES Proposal: Rijndael; NIST—National Institute of Standard and Technology: Gaithersburg, MD, USA, 1999.
- Saho, N.J.G.; Ezin, E.C. Survey on Asymmetric Cryptographic Algorithms in Embedded Systems. IJISRT 2020, 5, 544–554. [Google Scholar]
- Milanov, E. The RSA algorithm. RSA Lab. 2009, 1–11. Available online: https://sites.math.washington.edu/~morrow/336_09/papers/Yevgeny.pdf (accessed on 28 March 2021).
- Lara-Nino, C.A.; Diaz-Perez, A.; Morales-Sandoval, M. Elliptic curve lightweight cryptography: A survey. IEEE Access 2018, 6, 72514–72550. [Google Scholar] [CrossRef]
- Fontaine, C.; Galand, F. A survey of homomorphic encryption for nonspecialists. EURASIP J. Inf. Secur. 2007, 013801, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Dutta, I.K.; Ghosh, B.; Bayoumi, M. Lightweight cryptography for internet of insecure things: A survey. In Proceedings of the IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019. [Google Scholar] [CrossRef]
- Krawczyk, H.; Bellare, M.; Canetti, R. HMAC: Keyed-hashing for message authentication. Netw. Work. Group RFC 1997, 2104, 1–11. [Google Scholar]
- Ghosal, A.; Conti, M. Key management systems for smart grid advanced metering infrastructure: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 2831–2848. [Google Scholar] [CrossRef] [Green Version]
- Delaveau, F.; Mueller, A.; Ngassa, C.K.; Guillaume, R.; Molière, R.; Wunder, G. Perspectives of physical layer security (physec) for the improvement of the subscriber privacy and communication confidentiality at the air interface. Perspectives 2016, 27, 1–33. [Google Scholar]
- Hennebert, C.; Dos Santos, J. Security protocols and privacy issues into 6LoWPAN stack: A synthesis. IEEE Internet Things J. 2014, 1, 384–398. [Google Scholar] [CrossRef]
- Unwala, I.; Taqvi, Z.; Lu, J. IoT Security: Z-Wave and Thread. In Proceedings of the IEEE Green Technologies Conference (GreenTech), Austin, TX, USA, 4–6 April 2018. [Google Scholar] [CrossRef]
- Kambourakis, G.; Kolias, C.; Geneiatakis, D.; Karopoulos, G.; Makrakis, G.M.; Kounelis, I. A state-of-the-art review on the security of mainstream IoT wireless PAN protocol stacks. Symmetry 2020, 12, 579. [Google Scholar] [CrossRef] [Green Version]
- Azzouz, L.B.; Aouini, I. A lightweight IPsec-based energy home area networks. Trans. Emerg. Tel. Tech. 2019, 30, e3715. [Google Scholar] [CrossRef]
- Restuccia, G.; Tschofenig, H.; Baccelli, E. Low-Power IoT Communication Security: On the Performance of DTLS and TLS 1.3. In Proceedings of the 2020 9th IFIP International Conference on Performance Evaluation and Modeling in Wireless Networks (PEMWN), Berlin, Germany, 1–3 December 2020. [Google Scholar] [CrossRef]
- Raza, S.; Shafagh, H.; Hewage, K.; Hummen, R.; Voigt, T. Lithe: Lightweight secure CoAP for the internet of things. IEEE Sens. J. 2013, 13, 3711–3720. [Google Scholar] [CrossRef]
- Kohlios, C.P.; Hayajneh, T. A Comprehensive attack flow model and security analysis for Wi-Fi and WPA3. Electronics 2018, 7, 284. [Google Scholar] [CrossRef] [Green Version]
- Padgette, J.; Scarfone, K.; Chen, L. Guide to bluetooth security. NIST Spec. Publ. 2012, 800, 25. [Google Scholar]
- Marksteiner, S.; Jiménez, V.J.E.; Valiant, H.; Zeiner, H. An overview of wireless IoT protocol security in the smart home domain. In Proceedings of the Internet of Things Business Models, Users, and Networks, Copenhagen, Denmark, 23–24 November 2017. [Google Scholar] [CrossRef] [Green Version]
- Liaisons, S.; Hall, R.; Modera, M.; Neilson, C.; Isler, B.; Osborne, M.; Lenart, J. BACnet-A Data communication protocol for building automation and control networks. ANSI/ASHRAE Standard 2012, 135, 404–636. [Google Scholar]
- Huitsing, P.; Chandia, R.; Papa, M.; Shenoi, S. Attack taxonomies for the Modbus protocols. Int. J. Crit. Infrastruct. Prot. 2008, 1, 37–44. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Yang, Y.; McLaughlin, K.; Littler, T.; Sezer, S.; Pranggono, B.; Wang, H.F. Intrusion detection system for IEC 60870-5-104 based SCADA networks. In Proceedings of the IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013. [Google Scholar] [CrossRef]
- Morris, T.H.; Jones, B.A.; Vaughn, R.B.; Dandass, Y.S. Deterministic intrusion detection rules for MODBUS protocols. In Proceedings of the 46th Hawaii International Conference on System Sciences, Wailea, HI, USA, 7–10 January 2013. [Google Scholar] [CrossRef]
- Jose, S.; Malathi, D.; Reddy, B.; Jayaseeli, D. A survey on anomaly based host intrusion detection system. J. Phys. Conf. Ser. 2018, 1000, 012049. [Google Scholar] [CrossRef]
- Al Baalbaki, B.; Pacheco, J.; Tunc, C.; Hariri, S.; Al-Nashif, Y. Anomaly behavior analysis system for ZigBee in smart buildings. In Proceedings of the IEEE/ACS 12th International Conference of Computer Systems and Applications (AICCSA), Marrakech, Morocco, 17–20 November 2015. [Google Scholar] [CrossRef]
- Vijayanand, R.; Devaraj, D.; Kannapiran, B. Support vector machine based intrusion detection system with reduced input features for advanced metering infrastructure of smart grid. In Proceedings of the 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017. [Google Scholar] [CrossRef]
- Jokar, P.; Nicanfar, H.; Leung, V.C.M. Specification-based Intrusion Detection for home area networks in smart grids. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011. [Google Scholar] [CrossRef]
- Liu, X.; Zhu, P.; Zhang, Y.; Chen, K. A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure. IEEE Trans. Smart Grid 2015, 6, 2435–2443. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Abduvaliyev, A.; Pathan, A.S.K.; Zhou, J.; Roman, R.; Wong, W.C. On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2013, 15, 1223–1237. [Google Scholar] [CrossRef]
- Krontiris, I.; Dimitriou, T.; Giannetsos, T.; Mpasoukos, M. Intrusion detection of sinkhole attacks in wireless sensor networks. In Proceedings of the International Symposium on Algorithms and Experiments for Sensor Systems, Wireless Networks and Distributed Robotics (ALGOSENSORS), Wroclaw, Poland, 14 July 2007. [Google Scholar] [CrossRef]
- Krontiris, I.; Giannetsos, T.; Dimitriou, T. LIDeA: A distributed lightweight intrusion detection architecture for sensor networks. In Proceedings of the 4th International Conference on Security and Privacy in Communication Networks, Istanbul, Turkey, 22–25 September 2008. [Google Scholar] [CrossRef]
- Muntwyler, B.; Lenders, V.; Legendre, F.; Plattner, B. Obfuscating IEEE 802.15. 4 communication using secret spreading codes. In Proceedings of the 9th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Courmayeur, Italy, 9–11 January 2012. [Google Scholar] [CrossRef]
- Diaz, C.; Preneel, B. Taxonomy of mixes and dummy traffic. In Information Security Management, Education and Privacy; Deswarte, Y., Cuppens, F., Jajodia, S., Wang, L., Eds.; Springer: Boston, MA, USA, 2004; pp. 217–232. [Google Scholar] [CrossRef] [Green Version]
- Kamat, P.; Xu, W.; Trappe, W.; Zhang, Y. Temporal privacy in wireless sensor networks: Theory and practice. ACM T Sens. Netw. 2009, 5, 1–24. [Google Scholar] [CrossRef]
- Shbair, W.M.; Bashandy, A.R.; Shaheen, S.I. A new security mechanism to perform traffic anonymity with dummy traffic synthesis. In Proceedings of the International Conference on Computational Science and Engineering, Vancouver, BC, Canada, 29–31 August 2009. [Google Scholar] [CrossRef]
- Erdene-Ochir, O.; Minier, M.; Valois, F.; Kountouris, A. Enhancing resiliency against routing layer attacks in wireless sensor networks: Gradient-based routing in focus. Int. J. Adv. Netw. Serv. 2011, 4, 38–54. Available online: http://www.iariajournals.org/networks_and_services/netser_v4_n12_2011_paged.pdf (accessed on 28 March 2021).
- Kelly, D.J. A Taxonomy for and Analysis of Anonymous Communications Networks. Ph.D. Thesis, Air Force Institute of Technology, Dayton, OH, USA, 18 March 2009. Available online: https://scholar.afit.edu/cgi/viewcontent.cgi?article=3540&context=etd (accessed on 28 March 2021).
- Dingledine, R.; Mathewson, N.; Syverson, P. Tor: The second-generation onion router. In Proceedings of the 13th Conference on USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; Available online: https://www.usenix.org/legacy/publications/library/proceedings/sec04/tech/full_papers/dingledine/dingledine.pdf (accessed on 28 March 2021).
- Matos, A.; Sargento, S.; Aguiar, R.L. Waypoint routing: A network layer privacy framework. In Proceedings of the IEEE Global Telecommunications Conference-GLOBECOM, Houston, TX, USA, 5–9 December 2011. [Google Scholar] [CrossRef]
- Park, S.; Bang, J.; Ahn, M.; Lee, W.; Kwon, T. A method for hiding link layer addresses using bloom filter in wireless sensor networks. J. Internet Serv. Inf. Secur. 2014, 4, 71–81. [Google Scholar]
- Wang, X.; Mu, Y. Addressing and privacy support for 6LoWPAN. IEEE Sens. J. 2015, 15, 5193–5201. [Google Scholar] [CrossRef]
- Oualha, N.; Olivereau, A.; Boudguiga, A. Pseudonymous communications in secure industrial wireless sensor networks. In Proceedings of the 2013 Eleventh Annual Conference on Privacy, Security and Trust, Tarragona, Spain, 10–12 July 2013. [Google Scholar] [CrossRef]
- Narten, T.; Draves, R.; Krishnan, S. Privacy extensions for stateless address autoconfiguration in IPv6. Netw. Work. Group RFC 2007, 4941, 1–23. [Google Scholar]
- Sengupta, S.; Chowdhary, A.; Sabur, A.; Alshamrani, A.; Huang, D.; Kambhampati, S. A survey of moving target defenses for network security. IEEE Commun. Surv. Tutor. 2020, 22, 1909–1941. [Google Scholar] [CrossRef] [Green Version]
- Aura, T. Cryptographically generated addresses (CGA). In Proceedings of the International Conference on Information Security (ISC), Dallas, TX, USA, 13–15 November 2013. [Google Scholar] [CrossRef]
- Cheneau, T.; Laurent, M. Using SEND signature algorithm agility and multiple-key CGA to secure proxy neighbor discovery and anycast addressing. In Proceedings of the Conference on Network and Information Systems Security, La Rochelle, France, 18–21 May 2011. [Google Scholar] [CrossRef] [Green Version]
- Rafiee, H.; Meinel, C. SSAS: A simple secure addressing scheme for IPv6 autoconfiguration. In Proceedings of the Eleventh Annual Conference on Privacy, Security and Trust, Tarragona, Spain, 10–12 July 2013. [Google Scholar] [CrossRef]
- Tunaru, I.; Denis, B.; Uguen, B. Location-based pseudonyms for identity reinforcement in wireless ad hoc networks. In Proceedings of the IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015. [Google Scholar] [CrossRef]
- Dunlop, M.; Groat, S.; Urbanski, W.; Marchany, R.; Tront, J. Mt6d: A moving target ipv6 defense. In Proceedings of the Military Communications Conference (MILCOM), Baltimore, MD, USA, 7–10 November 2011. [Google Scholar] [CrossRef]
- Dos Santos, J.; Hennebert, C.; Fonbonne, J.C.; Lauradoux, C. Ephemeral: Lightweight pseudonyms for 6LoWPAN MAC addresses. In Proceedings of the 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016. [Google Scholar] [CrossRef]
- Leitão, P.; Colombo, A.W.; Karnouskos, S. Industrial automation based on cyber-physical systems technologies: Prototype implementations and challenges. Comput. Ind. 2016, 81, 11–25. [Google Scholar] [CrossRef] [Green Version]
- Bongard-Blanchy, K.; Bouchard, C. Dimensions of user experience-from the product design perspective. J. Interact. Pers. Syst. Assoc. Francoph. Interact. Homme Mach. (AFIHM) 2014, 3, 2. [Google Scholar]
- D’Oca, S.; Hong, T.; Langevin, J. The human dimensions of energy use in buildings: A review. Renew. Sustain. Energy Rev. 2018, 81, 731–742. [Google Scholar] [CrossRef] [Green Version]
- Harputlugil, T.; de Wilde, P. The interaction between humans and buildings for energy efficiency: A critical review. Energy Res. Soc. Sci. 2021, 71, 101828. [Google Scholar] [CrossRef]
- Ciancio, V.; Salata, F.; Falasca, S.; Curci, G.; Golasi, I.; de Wilde, P. Energy demands of buildings in the framework of climate change: An investigation across Europe. Sustain. Cities Soc. 2020, 60, 102213. [Google Scholar] [CrossRef]
- Fonseca, J.A.; Nevat, I.; Peters, G.W. Quantifying the uncertain effects of climate change on building energy consumption across the United States. Appl. Energy 2020, 277, 115556. [Google Scholar] [CrossRef]








| Energy Management Method Classification | Energy Management Method | Kind of Building | Observation |
|---|---|---|---|
| Conventional Methods | On/Off switching | Nonresidential | Based on classic rules algorithms |
| PID controllers | Can be software implemented or use an external device | ||
| Predictive and adaptive methods | |||
| Intelligent Methods | Model predictive control | Nonresidential | Often used for DSM |
| Fuzzy logic | Nonresidential & residential | Supports cloud or edge computing | |
| Multi Agent System | Nonresidential & residential | Distributed nature Supports cloud or edge computing Supports learning ability |
| Communication Technologies | Inward-IB Network | Outward-IB Network | Media | HAN | NAN | WAN |
|---|---|---|---|---|---|---|
| PLC | ✓ | ✓ | Wired | ✓ | ✓ | ✓ |
| Optical fibers | ✓ | Wired | ✓ | |||
| Digital Subscriber Lines | ✓ | Wired | ✓ | ✓ | ||
| Wi-Fi | ✓ | Wireless | ✓ | |||
| Bluetooth | ✓ | Wireless | ✓ | |||
| EnOcean | ✓ | Wireless | ✓ | |||
| ZigBee | ✓ | Wireless | ✓ | ✓ | ||
| Z-Wave | ✓ | Wireless | ✓ | ✓ | ||
| LPWAN | ✓ | Wireless | ✓ | ✓ | ||
| DASH7 | ✓ | Wireless | ✓ | ✓ | ||
| Cellular technologies | ✓ | Wireless | ✓ | ✓ | ||
| WiMax | ✓ | Wireless | ✓ | ✓ | ||
| Cognitive radio | ✓ | Wireless | ✓ | |||
| Satellite communication | ✓ | Wireless | ✓ | |||
| Layers | Attacks | Confidentiality (C), Integrity (I), Availability (A) | Countermeasures |
|---|---|---|---|
| Physical | Jamming | A | [160,161] |
| TSA | A, I | [162] | |
| MAC | Collision | A | [163] |
| Exhaustion | A | [164] | |
| Denial of sleep | A | [142] | |
| Masquerading | C, I, A | [165] | |
| Network | Selective forwarding/blackhole | C, I, A | [166,167] |
| Sinkhole/hello flood | C, I, A | [168,169] | |
| Sybil | C, I | [170] | |
| Router advertisement flooding | A | [171] | |
| Wormhole | A, I | [172,173] | |
| Puppet | A | [155] | |
| Application | Desynchronization/flooding/stack smashing | A | [174] |
| Control command/alert message injection | C, I, A | ||
| Data tampering | C, I | [175] |
| Standard | Ciphering Suite | Authentication/Integrity Suite | Key Management Protocol |
|---|---|---|---|
| IEEE 802.15.4 [199] | AES-CTR 128 bits | AES-CBC-MAC 128 bits | Upper layers |
| Z-Wave [200] | AES 128 bits | AES 128 bits | Elliptic Curve Diffie-Hellman (ECDH) |
| En-Ocean [201] | AES-CBC 128 bits or VAES (recommended) | AES-CMAC | Preshared Key (PSK) |
| ZigBee [180] | AES 128 bits | AES 128 bits | Master, Network (default) or link Key |
| IPsec [202] | Several | Several | IKEv2 |
| DTLS [203,204] | Several | Several | Handshake |
| WiFi [205] | AES-CCMP 128 bits (WPA2) AES-GCMP-256 (WPA3) | EAP (WPA2) HMAC-SHA-384 (WPA3) | PSK (personal)/RADIUS server (Entreprise) ECDH (WP3) |
| Bluetooth [206] | E0 (Bluetooth) AES-CCM (LE) | HMAC-SHA-256 (Bluetooth) AES-CCM (LE) | PIN pairing or ECDH (Bluetooth) Long-Term-Key (LE) |
| DLMS/COSEM [127] | AES-GCM-128 bits | MD5/SHA1/GMAC/SHA256/ECDSA | Preshared |
| KNX [207] | No (old) AES-CCM 128 bits (new) | No (old) AES-CCM 128 bits (new) | No (old) Factory Device Set up Key |
| BACnet [208] | No | No | No |
| ModBus [209] | No | No | No |
| Countermeasures | Suitable | Nwk Perfs. | Main Drawbacks |
|---|---|---|---|
| Spread spectrum [160] | ✗ | - | Heavy protocols |
| Error-correcting code [163] | ✓ | -- | Latency |
| Whitelist [165] | ✗ | - | Table management |
| Dynamic multi path routing [166] | ✗ | -- | Energy consumption |
| DHT [170] | ✓ | - | Not suitable for large network |
| Authenticity [171] | ✗ | -- | Heavy protocols |
| Puppet detection [155] | ✓ | - | Long time to detect |
| Blockchain [175] | ✗ | --- | Heavy cryptographic process |
| Physical obfuscation [222] | ✓ | -- | Dedicated hardware necessary |
| Mixing [223,224,228,229] | ✗ | --- | Header overhead |
| False traffic injection [225] | ✗ | -- | Energy consumption |
| Bloom filter [230] | ✓ | - | Star topology and unidirectional communications |
| Lists [231,232] | ✓ | - | Memory exhaustion |
| RFC 4941 [233] | ✗ | - | Only source addresses hidden |
| CGA [235,236] | ✗ | -- | Heavy |
| SSAS [237] | ✓ | - | Trust parti |
| MT6D [239] | ✓ | - | Synchronization algorithm |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Llaria, A.; Dos Santos, J.; Terrasson, G.; Boussaada, Z.; Merlo, C.; Curea, O. Intelligent Buildings in Smart Grids: A Survey on Security and Privacy Issues Related to Energy Management. Energies 2021, 14, 2733. https://doi.org/10.3390/en14092733
Llaria A, Dos Santos J, Terrasson G, Boussaada Z, Merlo C, Curea O. Intelligent Buildings in Smart Grids: A Survey on Security and Privacy Issues Related to Energy Management. Energies. 2021; 14(9):2733. https://doi.org/10.3390/en14092733
Chicago/Turabian StyleLlaria, Alvaro, Jessye Dos Santos, Guillaume Terrasson, Zina Boussaada, Christophe Merlo, and Octavian Curea. 2021. "Intelligent Buildings in Smart Grids: A Survey on Security and Privacy Issues Related to Energy Management" Energies 14, no. 9: 2733. https://doi.org/10.3390/en14092733
APA StyleLlaria, A., Dos Santos, J., Terrasson, G., Boussaada, Z., Merlo, C., & Curea, O. (2021). Intelligent Buildings in Smart Grids: A Survey on Security and Privacy Issues Related to Energy Management. Energies, 14(9), 2733. https://doi.org/10.3390/en14092733