Do Charging Stations Benefit from Cryptojacking? A Novel Framework for Its Financial Impact Analysis on Electric Vehicles
Abstract
:1. Introduction
- 1.
- To the best of our knowledge, this is the first work to highlight EV cryptojacking as a real threat to the electric charging infrastructure and describe its behavior in detail.
- 2.
- A novel framework is proposed that incorporates an EV energy model to analyze cryptojacking behavior to allow researchers to study the financial impacts of attacks on different infrastructural configurations. Moreover, various scenarios with different configurations can be tested using the proposed framework.
- 3.
- Our results are significant in that they highlight how cryptojacking can severely impact the EV battery’s residual energy, leading to increased trips to charging stations, incur financial burden on EV owners, and provide significant profits to the attacker. Furthermore, at low levels of mining rate (50% or less), the cryptojacking can proceed quite stealthily while still providing the attacker sizable profits.
- 4.
- A practical set of countermeasures outlined that can mitigate these threats and allow the vision of green energy in reducing climate change to materialize.
2. Related Work
3. System Model
3.1. Energy Model
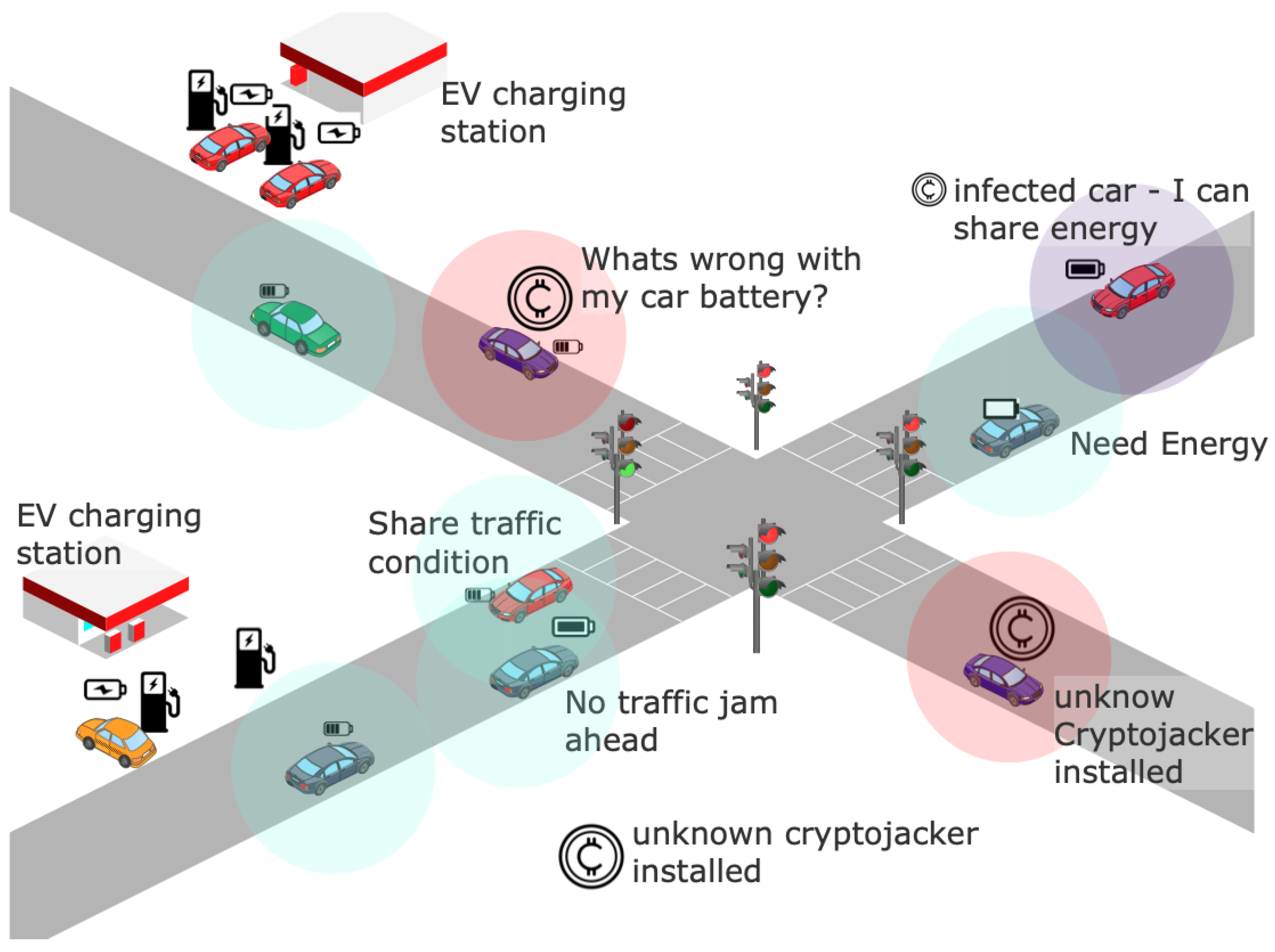
3.2. Cryptojacking Adversary Model
 ) into the requested app. (3) After charging is complete, the driver drives off, unaware that the EV has become a victim “zombie”, allowing the miner to run stealthily as a daemon process. (4) The miner performs computationally complex tasks computing hashes while utilizing EV energy. (5) The hash results are later offloaded by the attacker based on the vehicle information collected in step 2. The battery drainage () due to cryptojacking can then be represented as . Here, is the initial SoC and is energy consumed due to
) into the requested app. (3) After charging is complete, the driver drives off, unaware that the EV has become a victim “zombie”, allowing the miner to run stealthily as a daemon process. (4) The miner performs computationally complex tasks computing hashes while utilizing EV energy. (5) The hash results are later offloaded by the attacker based on the vehicle information collected in step 2. The battery drainage () due to cryptojacking can then be represented as . Here, is the initial SoC and is energy consumed due to  . However, if all the cores/GPU are utilized by the
. However, if all the cores/GPU are utilized by the  , the factor increases such as . Let us assume that is the time required to recover the charge, and W = . Here, is the power consumed when cryptojacking is active in . Assuming that is the cost of electricity in kWh then the total battery loss—the additional money in USD that all the EV owners pay due to cryptojacking—can be computed as
, the factor increases such as . Let us assume that is the time required to recover the charge, and W = . Here, is the power consumed when cryptojacking is active in . Assuming that is the cost of electricity in kWh then the total battery loss—the additional money in USD that all the EV owners pay due to cryptojacking—can be computed as
3.3. Efficiency
4. Simulation-Based Cryptojacking Framework
5. Evaluation
5.1. Recharging Demand
 ryptojacking is occurring. In this figure, consider the case where . Initially, the charging rate noted for the normal case is approximately 9.14 (the gray bar), which increases to 16.38 when cryptojacking is employed (the blue bar). The rate difference is computed as the ratio of the difference to the new value i.e., . Therefore, 44% more EVs request a recharge. Further, when the arrival rate increases, the recharge request rejection rate at the nearby charging stations swells to 46%.
ryptojacking is occurring. In this figure, consider the case where . Initially, the charging rate noted for the normal case is approximately 9.14 (the gray bar), which increases to 16.38 when cryptojacking is employed (the blue bar). The rate difference is computed as the ratio of the difference to the new value i.e., . Therefore, 44% more EVs request a recharge. Further, when the arrival rate increases, the recharge request rejection rate at the nearby charging stations swells to 46%.5.2. Total Charging Cost
5.3. Efficiency
5.4. ![Energies 15 05773 i001]() rypto Energy Consumption
rypto Energy Consumption
5.5. Cryptojacking Impact under Stealth Mode
5.6. ![Energies 15 05773 i001]() ryptojacking Attack through Charging Station
ryptojacking Attack through Charging Station
6. Discussion
7. Conclusions
Future Directions
Author Contributions
Funding
Conflicts of Interest
References
- Sigalos, M. This Tesla Owner Says He Mines Up to $800 a Month in Cryptocurrency with His Car. 2022. Available online: https://www.cnbc.com/2022/01/08/tesla-owner-mines-bitcoin-ethereum-with-his-car.html (accessed on 1 August 2022).
- Robertson, H. An EV Company Is Planning a Crypto-Mining Car That Will Dig for Bitcoin While Parked. 2021. Available online: www.businessinsider.in/cryptocurrency/news/an-ev-company-is-planning-a-crypto-mining-car-that-will-dig-for-bitcoin-and-dogecoin-while-parked/articleshow/83171598.cms (accessed on 29 July 2022).
- Google Play and Microsoft Stores Delete Suspected Compromised Apps. 2019. Available online: https://news.trendmicro.com/2019/04/15/google-play-and-microsoft-stores-delete-suspected-compromised-apps/ (accessed on 29 July 2022).
- Clark, M. Here’s the Truth about the Crypto Miner That Comes with Norton Antivirus. 2022. Available online: www.theverge.com/2022/1/7/22869528/norton-crypto-miner-security-software-reaction (accessed on 29 July 2022).
- Newman, L. Hackers Enlisted Tesla’s Public Cloud to Mine Cryptocurrency. 2018. Available online: www.wired.com/story/cryptojacking-tesla-amazon-cloud/ (accessed on 1 August 2022).
- Stumpf, R. Researchers Used a Drone and a WiFi Dongle to Break into a Tesla. 2021. Available online: www.thedrive.com/tech/40438/researchers-used-a-drone-and-a-wifi-dongle-to-break-into-a-tesla (accessed on 1 August 2022).
- Nasr, T.; Torabi, S.; Bou-Harb, E.; Fachkha, C.; Assi, C. Power jacking your station: In-depth security analysis of electric vehicle charging station management systems. Comput. Secur. 2022, 112, 102511. [Google Scholar] [CrossRef]
- Knott, M. Russia’s Great Firewall: As Putin Clamps Down, Activists Get Creative. 2022. Available online: www.smh.com.au/world/europe/russia-s-great-firewall-as-putin-clamps-down-activists-get-creative-20220308-p5a2n7.html (accessed on 15 July 2022).
- Corfield, G. Security Flaws Leaves Electric Cars at Risk of Cyber Hacks. 2022. Available online: www.telegraph.co.uk/business/2022/03/29/security-flaws-leaves-electric-cars-risk-cyber-hacks/ (accessed on 28 July 2022).
- David, B. Electric Vehicle Chargers Hacked to Show Porn. 2022. Available online: www.infosecurity-magazine.com/news/electric-vehicle-chargers-hacked/ (accessed on 28 July 2022).
- Alamalhodaei, A. Security Flaws Found in Popular EV Chargers. 2021. Available online: https://techcrunch.com/2021/08/03/security-flaws-found-in-popular-ev-chargers/ (accessed on 20 July 2022).
- City of New York. ETLC Trip Record Data. 2022. Available online: www1.nyc.gov/site/tlc/about/tlc-trip-record-data.page (accessed on 30 June 2022).
- Bijmans, H.L.; Booij, T.M.; Doerr, C. Inadvertently making cyber criminals rich: A comprehensive study of cryptojacking campaigns at internet scale. In Proceedings of the USENIX Security, Santa Clara, CA, USA, 14–16 August 2019. [Google Scholar]
- Eskandari, S.; Leoutsarakos, A.; Mursch, T.; Clark, J. A first look at browser-based cryptojacking. In Proceedings of the European Symposium on Security & Privacy Workshops, London, UK, 23–27 April 2018. [Google Scholar]
- Hong, G.; Yang, Z.; Yang, S.; Zhang, L.; Nan, Y.; Zhang, Z.; Yang, M.; Zhang, Y.; Qian, Z.; Duan, H. How you get shot in the back: A systematical study about cryptojacking in the real world. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1701–1713. [Google Scholar]
- Varlioglu, S.; Gonen, B.; Ozer, M.; Bastug, M. Is cryptojacking dead after coinhive shutdown? In Proceedings of the International Conference on Information and Computer Technologies, San Jose, CA, USA, 9–12 March 2020. [Google Scholar]
- Marchetto, V.; Liu, X. An investigation of cryptojacking: Malware analysis and defense strategies. J. Strateg. Innov. Sustain. 2019, 14, 66–80. [Google Scholar]
- Tekiner, E.; Acar, A.; Uluagac, A.S.; Kirda, E.; Selcuk, A.A. SoK: Cryptojacking Malware. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–10 September 2021; pp. 120–139. [Google Scholar]
- Musch, M.; Wressnegger, C.; Johns, M.; Rieck, K. Thieves in the browser: Web-based cryptojacking in the wild. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; pp. 1–10. [Google Scholar]
- Gomes, F.; Correia, M. Cryptojacking detection with cpu usage metrics. In Proceedings of the 2020 IEEE 19th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 24–27 November 2020; pp. 1–10. [Google Scholar]
- Rauchberger, J.; Schrittwieser, S.; Dam, T.; Luh, R.; Buhov, D.; Pötzelsberger, G.; Kim, H. The other side of the coin: A framework for detecting and analyzing web-based cryptocurrency mining campaigns. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 1–10. [Google Scholar]
- Saad, M.; Khormali, A.; Mohaisen, A. End-to-end analysis of in-browser cryptojacking. arXiv 2018, arXiv:1809.02152. [Google Scholar]
- Bajpai, P.; Enbody, R.; Cheng, B.H. Ransomware targeting automobiles. In Proceedings of the Second ACM Workshop on Automotive and Aerial Vehicle Security, New Orleans, LA, USA, 18 March 2020; pp. 23–29. [Google Scholar]
- Giaretta, A.; Dragoni, N.; Massacci, F. S× C4IoT: A Security-by-contract Framework for Dynamic Evolving IoT Devices. ACM Trans. Sens. Netw. 2021, 18, 1–51. [Google Scholar] [CrossRef]
- Gonzalez-Amarillo, C.; Cardenas-Garcia, C.; Mendoza-Moreno, M.; Ramirez-Gonzalez, G.; Corrales, J.C. Blockchain-iot sensor (Biots): A solution to iot-ecosystems security issues. Sensors 2021, 21, 4388. [Google Scholar] [CrossRef] [PubMed]
- Dhar, S.; Bose, I. Securing IoT devices using zero trust and blockchain. J. Organ. Comput. Electron. Commer. 2021, 31, 18–34. [Google Scholar] [CrossRef]
- Dashevskyi, S.; Zhauniarovich, Y.; Gadyatskaya, O.; Pilgun, A.; Ouhssain, H. Dissecting android cryptocurrency miners. In Proceedings of the Tenth ACM Conference on Data and Application Security and Privacy, New Orleans, LA, USA, 16–18 March 2020; pp. 191–202. [Google Scholar]
- Wang, W.; Ferrell, B.; Xu, X.; Hamlen, K.W.; Hao, S. Seismic: Secure in-lined script monitors for interrupting cryptojacks. In Proceedings of the European Symposium on Research in Computer Security, Barcelona, Spain, 3–7 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 122–142. [Google Scholar]
- Yulianto, A.D.; Sukarno, P.; Warrdana, A.A.; Al Makky, M. Mitigation of cryptojacking attacks using taint analysis. In Proceedings of the 2019 4th International Conference on Information Technology, Information Systems and Electrical Engineering (ICITISEE), Yogyakarta, Indonesia, 20–21 November 2019; pp. 234–238. [Google Scholar]
- Lachtar, N.; Elkhail, A.A.; Bacha, A.; Malik, H. An application agnostic defense against the dark arts of cryptojacking. In Proceedings of the 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Taipei, Taiwan, 21–24 June 2021; pp. 314–325. [Google Scholar]
- Romano, A.; Zheng, Y.; Wang, W. Minerray: Semantics-aware analysis for ever-evolving cryptojacking detection. In Proceedings of the 2020 35th IEEE/ACM International Conference on Automated Software Engineering (ASE), Melbourne, VIC, Australia, 21–25 September 2020; pp. 1129–1140. [Google Scholar]
- Iqbal, S.; Malik, A.W.; Rahman, A.U.; Noor, R.M. Blockchain-based reputation management for task offloading in micro-level vehicular fog network. IEEE Access 2020, 8, 52968–52980. [Google Scholar] [CrossRef]
- Fiori, C.; Ahn, K.; Rakha, H.A. Power-based electric vehicle energy consumption model: Model development and validation. Appl. Energy 2016, 168, 257–268. [Google Scholar] [CrossRef]
- Burlig, F.; Bushnell, J.B.; Rapson, D.S.; Wolfram, C. Low Energy: Estimating Electric Vehicle Electricity Use; Working Paper 28451; National Bureau of Economic Research: Cambridge, MA, USA, 2021. [Google Scholar]
- Saad, M.; Khormali, A.; Mohaisen, A. Dine and dash: Static, dynamic, and economic analysis of in-browser cryptojacking. In Proceedings of the APWG Symposium on Electronic Crime Research, Pittsburgh, PA, USA, 13–15 November 2019. [Google Scholar]
- Bucolo, M.; Buscarino, A.; Fortuna, L.; Gagliano, S. Multidimensional Discrete Chaotic Maps. Front. Phys. 2022, 10, 862376. [Google Scholar] [CrossRef]
- Caponetto, R.; Fortuna, L.; Graziani, S.; Xibilia, M. Genetic algorithms and applications in system engineering: A survey. Trans. Inst. Meas. Control 1993, 15, 143–156. [Google Scholar] [CrossRef]







| Authors | Detection and Mitigation Technique | Focus Area | Financial Impact | Societal Impact | Beneficiary | Efficiency |
|---|---|---|---|---|---|---|
| Tekiner et al. [18] | Review work | System Browser | × | × | H | × |
| Stanislav et al. [27] | Dynamic metrics | Android devices | × | × | NA | × |
| Gomes et al. [20] | Machine learning | Web Browser | × | × | H | × |
| Rauchberger et al. [21] | Monitoring Web Traffic | Web Browser | × | × | H | × |
| Wang et al. [28] | Byte-code inspection | Web Browser | × | × | H | × |
| Yulianto et al. [29] | Taint analysis method | Web Browser | × | × | H | × |
| Nada et al. [30] | Throttling evasion tech. | App. agnostics | × | × | NA | × |
| Romano et al. [31] | WebAssembly, JavaScript | Web Browser | × | × | NA | × |
| Proposed Work | NA | Electric Vehicles | ✓ | ✓ | H/CS | ✓ |
| Description | Value |
|---|---|
| Simulation area | 3 by 3 km2 |
| Total simulation time | 24 h |
| Simulation repetition | 5 (five) times |
| Vehicle speed | 10–60 km/h |
| Vehicle acceleration/deceleration | 1.6/2.6 m/s2 |
| Vehicle arrival rate | 100–400 |
| Mobility model | New York Taxi dataset |
| Charging stations | 9 |
| Road network | Manhattan |
| GPU power | 61.01 MH/s |
| Energy per MH/s | 1.77 W |
| Charging spot per station | 3–6 |
| Charging time | 30–40 time units |
| Crypto Infected vehicles | 10–40% |
| Mining rate | 0–100% |
| System | 1.4 GHz Quad-Core Intel Core i5 |
| RAM | 8 GB |
| OS | macOS Catalina |
| Simulator | AnyLogic PLE v8.5 |
| Category | Description |
|---|---|
| Charging Station Design | 1. Utilize hardware in charging terminals that is resistant to physical attacks and allows for secure boot. 2. The procedure for charging an EV at a public charging point must allow for the identification, authentication, and safeguarding of information that passes between the charger and the vehicle. This will require cryptography. |
| EV Intrusion Detection Mechanisms | 1. EVs should deploy their own intrusion detection systems that monitor apps for spike in CPU usage, decrease in performance, and overheating, using machine learning and AI techniques. 2. Provision of security features in EV apps that allow for overlay protection, root detection, and code integrity checks. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Malik, A.W.; Anwar, Z. Do Charging Stations Benefit from Cryptojacking? A Novel Framework for Its Financial Impact Analysis on Electric Vehicles. Energies 2022, 15, 5773. https://doi.org/10.3390/en15165773
Malik AW, Anwar Z. Do Charging Stations Benefit from Cryptojacking? A Novel Framework for Its Financial Impact Analysis on Electric Vehicles. Energies. 2022; 15(16):5773. https://doi.org/10.3390/en15165773
Chicago/Turabian StyleMalik, Asad Waqar, and Zahid Anwar. 2022. "Do Charging Stations Benefit from Cryptojacking? A Novel Framework for Its Financial Impact Analysis on Electric Vehicles" Energies 15, no. 16: 5773. https://doi.org/10.3390/en15165773
APA StyleMalik, A. W., & Anwar, Z. (2022). Do Charging Stations Benefit from Cryptojacking? A Novel Framework for Its Financial Impact Analysis on Electric Vehicles. Energies, 15(16), 5773. https://doi.org/10.3390/en15165773







