A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook
Abstract
1. Introduction
1.1. Emerging Smart Grids
1.2. Rise of Internet of Things (IoT) Devices in Smart Grids
- Localized and large-scale power outages.
- Significant business loss to the utilities and electricity markets.
- Social security threats to customers by publicizing their information.
- Manipulation of energy consumption records.
- Interrupting the process of transactive energy systems.
1.3. Motivational Factors and Contributions
- The concept of an IoT-enabled smart grid and recent practical advances are investigated, especially the application, challenges, and opportunities of communication technologies in modern power systems.
- The study examines the use of 5G-based IoT technologies for smart grids, considering the technology’s fast data transfer speed for remote control, strong security for preserving customer privacy, and high dependability for guaranteeing smart grid efficacy.
- This study investigated and classified energy grid IoT security vulnerabilities, and it also included mitigating strategies. We concentrated on how a cyber adversary might take advantage of vulnerabilities in IoT systems and conduct malicious attacks that could jeopardize the security of the IoT energy system. Energy theft in smart meter data, injection attacks in IoT home automation systems, denial-of-service attacks on IoT data analytics, manipulation attacks on transactive energy systems and the electricity market, etc., are only a few of the threats that have been researched. Potential lightweight intrusion-detection technologies for IoT systems and prospective solutions to mitigate threat and device-level vulnerabilities have also been studied. Although they were not given much attention in the past, these issues will soon rank among the most important. Moreover, it is significant to mention that, to our knowledge, no study has ever conducted such a precise survey on the cybersecurity architecture of IoT-enabled smart grids.
- The study covered the potential for end-users of distributed ledger systems based on blockchain. The protection of data privacy during peer-to-peer energy trade and information exchange was also underlined. To examine the potential prospects and applications in an IoT context, emerging machine learning methods for IoT-enabled energy systems were also explored.
- A detailed future work recommendation is made to achieve the application of 5G-based IoT devices and their security protection equipment and software to smart grids. Future research also recommends several approaches to improve the effectiveness and dependability of IoT-enabled smart grids, including ubiquitous data acquisition, data visualization, real-time state awareness, intelligent distribution networks, precise load control, edge computing, network security, and new business models.
1.4. Paper Organization
2. Motivation behind Implementation of IoT-Enabled Smart Grids
- Self-healing capability enables grid operators to intelligently detect the exact location of faults while assessing their impacts on the entire grid and responding promptly.
- Large-scale integration of renewable energy resources.
- Further implementation of state estimation devices, phasor measurement units (PMUs), and smart devices (AI-enabled devices) to enhance the power quality, coordination monitoring, and resilience of smart grids.
- Providing an interactive platform for utility and consumers to exchange information instantly. Moreover, consumers would have control over their energy use and tariff selection based on the time-of-use (ToU).
- Providing operational and managerial services for real-time charging, such as vehicle-to-grid, vehicle-to-home, and home-to-grid (prosumers) solutions and easing additional growth of electrification levels.
- Avoiding/responding to most cyber and physical attacks by real-time monitoring of the grid components’ behavior.
3. Description of IoT Technologies: Architecture and Protocols
3.1. Clearing the Confusion—IOE, IoT, and IoE
3.2. Architecture of IoT Technologies
3.2.1. IoT Layered Slicing
- (1)
- Physical layer: The physical layer is the foundation of the architecture of the IoT-enabled smart grid and includes the grid’s physical facilities and executors. All distributed and decision-making instructions are carried out at this layer to provide the system’s desired functionality. Additionally, the bidirectional energy flow between power generation, transmission, distribution, and customers happens inside this layer.
- (2)
- Communication network layer: The key layer of the IoT-enabled smart grid architecture is the communication network layer, which serves as a link between the lower physical and upper cyber layers. It covers the general activities of the information network, such as the interaction between electrical facilities and heterogeneous components and transferring the higher layer’s control instructions and the lower layer’s collected data.
- (3)
- Cyber layer: The cyber layer, or more accurately, the decision-making layer, is the core of the portrayed architecture, which comprises a cloud-based central processing mechanism and distributed computing intelligence to optimize both computing and control techniques. This decision-making layer serves as the system’s executive brain, providing a human–computer interface to the top layer to enable it to coordinate all lower levels by developing and issuing suitable orders.
- (4)
- Application layer: The highest level of decision-making layer is the application layer, also known as the management and control layer, which encompasses service providers, markets, and operations. To conduct power generation and consumption in the physical world, decision-makers analyze all concerns from the economic, social, and environmental viewpoints by considering market regulation, pricing, and incentive measures. The optimum operations are carried out based on two-way information and value flows between markets and service providers, which is a distinguishing feature of this layer.
3.2.2. IoTs, from the Perspective of Information and Communications Technology
- (1)
- Cloud computing: Cloud computing can handle big data’s networking, storage, and computational needs and offers extensive application services. Cloud computing, with the help of virtualization technology, can combine hardware and software resources from several geographical areas to establish a virtual platform with powerful storage and processing capabilities. It is important to emphasize that cloud computing is critical for enabling common, suitable, and on-demand network access to a distributed group of configurable computing resources, which can be automatically provisioned and released with minimal effort on the part of service providers. The term “cloud” is often used to characterize data centers that are scattered across several geographic areas and can be made available to many customers over the Internet. Cloud computing allows large data storage and extremely dependable, scalable, and autonomous processing. Cloud services are used to aggregate data and information from various elements, such as sensors, appliances, and other devices. They also process and analyze the collected data and provide the results to consumers and service providers for more insights. Different features of cloud computing are shown in Figure 5 [31].
- (2)
- Communication network: Communication networks consist of data transmission links between the physical and cyber layers that connect user terminals, edge devices, and cloud computing resources to build the smart grid’s omnipresent information network. Since each electrical service has unique communication, computation, and storage requirements, establishing specialized physical facilities for different types of applications in the IoT-enabled smart grid architecture is costly and may undermine grid connectivity and interoperability [32]. Therefore, the precise selection of communication technologies is an essential aspect of IoT-enabled smart energy grids. Table 2 and Table 3 classify and compare the widely used wired and wireless communication network technologies in smart grid systems [33,34,35,36,37].
- (3)
- Edge computing: Edge computing refers to the deployment of distributed intelligent agents at the edges of the network and closer to IoT-enabled devices to provide computation, storage, and application services near data sources. Although cloud computing can provide the required computational capabilities to the smart grid, the central cloud is located at a large distance from the data source, resulting in lengthy latency. However, many electricity applications and services could benefit from offloading computational and storage tasks to the proximity of IoT-enabled devices, which results in much lower service response latency and a reduction in communication overhead and traffic load to the central network, and an improvement in context-awareness. The offloading of computational tasks to the embedded resources available on IoT devices is known as edge computing. However, for some applications, the computational power in embedded devices is not sufficient, and the latency of the cloud is intolerable, which brings in the necessity for a processing layer between the network’s edges and the cloud, known as the fog server. Nevertheless, the computational capacity of fog servers is far less than that of cloud servers. To overcome this limitation, the architectural standard of multi-access edge computing (MEC) has been proposed for IoT applications, aiming to move cloud resources to the edge of a network. The edge computing classifications are depicted in Figure 6 [38,39]. Peak-load shifting and real-time load–demand balancing to provide optimal options for power generation scheduling are examples of using edge computing proposed in smart grid applications [40].
- (4)
- Physical entities: The term “physical entities” refers to different electrical components of the power grid, spread across the power grid as basic components of the power system, conducting distributed sensing, and acting. In the IoT-enable smart grid, physical entities could benefit from AI methods to gain the ability to learn from their experiences and environments, react to new inputs and execute human-like activities. Moreover, through device-to-device (D2D) communication, neighboring entities can create direct communication among themselves, without using a third party, to exchange information directly [41].
3.2.3. Operating Software for IoT Devices
3.3. Standards and Protocols for IoT Technologies
- ISO 11784: regulation of data structure.
- ISO 15459: identification of transport product.
- ISO 18000: goods tracking systems.
- ISO 18047: equipment performance testing.
- ISO/IEC 18092: near-field communication (NFC).
- ISO/IEC 20248: fog and edge computing.
- ISO 29182: sensor network reference architecture (SNRA).
- ISO/IEC 30118: UPnP.
- IEEE 802.15.4: communication standard.
- IEEE 802.15: short-range communication.
- IEEE 802.15.1: Bluetooth.
- IEEE 802.11., 802.11a, 802.11b, 802.11g, 802.11n, 802.11h, 802.11i, 802.11-2007, 802.11- 2012, 802.11ac, 802.11ad, 802.11af, 802.11-2016, 802.11ah, 802.11ai, 802.11aj, 802.11aq, 802.11ax, 802.11ay: Wi-fi, Wi-Fi 4, Wi-Fi 5 and Wi-Fi 6.
4. Applications of IoT Technologies in Smart Energy Grids
4.1. Fog-Based Energy Grids through the Utilization of SCADA
4.2. AMI-Connected Distribution Networks
4.3. IoT for Smart Meters
4.4. Application of 5G in IoT-Based Demand Response Programs (DRPs)
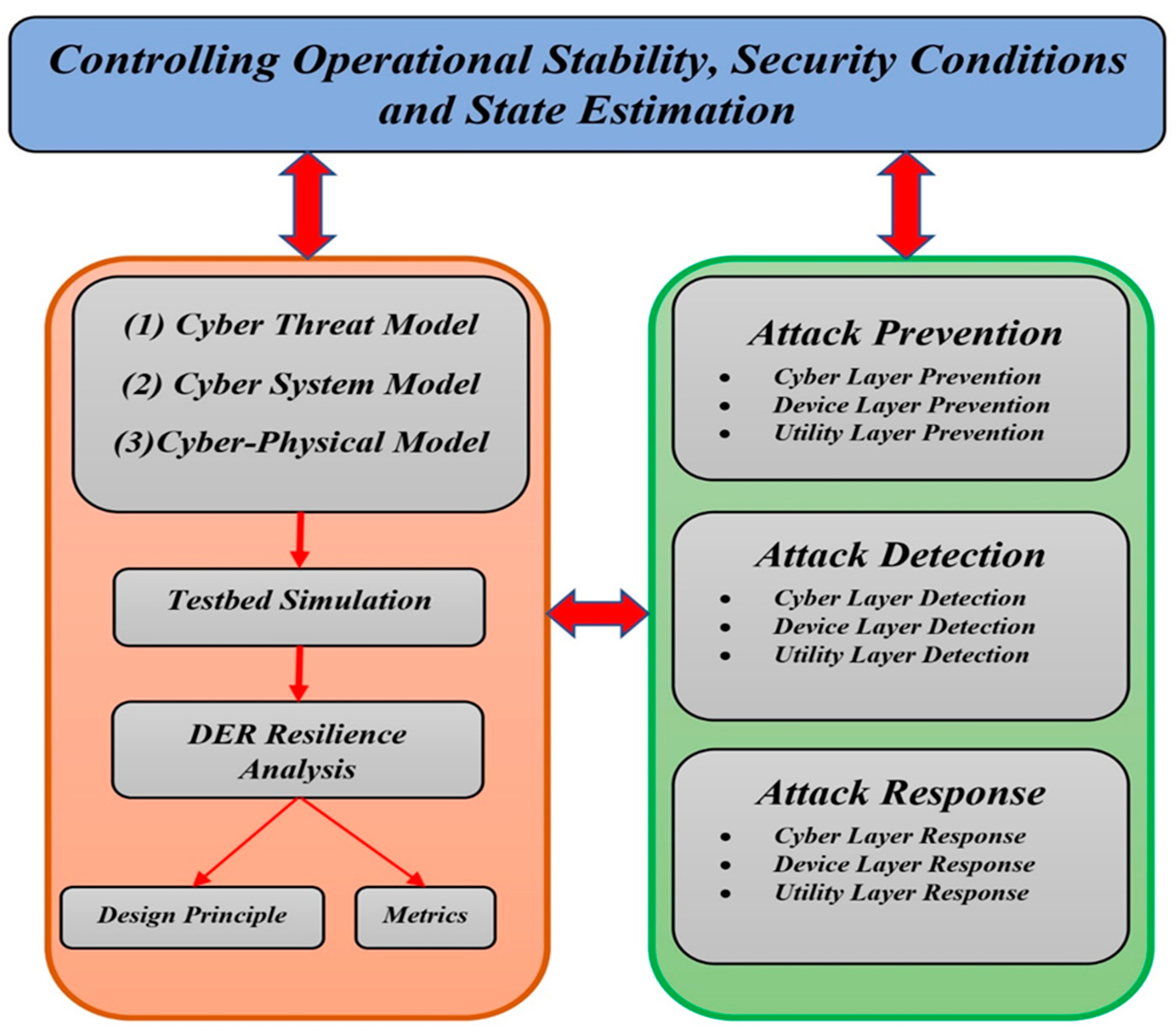
5. Cyber-Physical Security Vulnerabilities and Challenges in IoT-Enabled Smart Grids
5.1. General Definitions, Framework, and Guidelines
- (1)
- Ever-increasing development of intelligent electronic devices (IEDs): The number of attack sites grows in lockstep with the number of devices in the network. Even if a single point’s security is breached, the entire network system is affected.
- (2)
- Unregulated installation of third-party components: Experts advise against using third-party components because they make the network more vulnerable to hacking. These devices might be infected with Trojans, which could then spread to other network devices.
- (3)
- Insufficient personal training: To use any technology, appropriate training is required. When employees are not properly trained, they are more likely to fall prey to phishing scams.
- (4)
- Insecure Internet protocols: In terms of data transfer, not all protocols are secure. Unencrypted data transport is used by several protocols. As a result, they are easy targets for man-in-the-middle attacks that extract data.
- (5)
- Maintenance: The primary objective of maintenance is to keep things running smoothly. It can also be used as a vector for cyberattacks. Operators frequently deactivate a security system during maintenance to undertake tests.
- (1)
- Authentication: The ability to verify the identity of any smart grid communication device. For example, to bill the relevant user, the energy provider must validate each smart meter.
- (2)
- Authorization: Ensures that an authenticated person or an object is authorized to accomplish certain tasks or has been granted the necessary privileges to access a certain category of resources. For example, an agent requires authorization to access and conduct manual configuration on a smart meter.
- (3)
- Availability: Ensures that when a user needs some resources and/or data, they are always available for usage.
- (4)
- Confidentiality: Guarantees that only the intended recipients have access to data that have been stored or transmitted. For example, only smart grid operators and energy providers should be aware of the end users’ consumption patterns and data.
- (5)
- Integrity: Certifies that received data have not been tampered with in any manner. For example, smart meters must ensure the integrity of software updates as well as the source origin.
- (1)
- Staff awareness training.
- (2)
- Access control and configuration management.
- (3)
- Physical and environmental security.
- (4)
- Continuous audit and accountability.
- (5)
- Security assessment and authorization.
- (6)
- Continuity of operations (individual and systematic).
- (7)
- Development and maintenance planning.
- (8)
- Well-implemented identification and authentication procedures.
- (9)
- Document and information management processes.
- (10)
- Incident response plan.
- (11)
- Media management and protection.
- (12)
- Security management program (personnel and premises).
- (13)
- Risk assessment and management.
- (14)
- Smart grid information system, services acquisition, communication protection, and information integrity.
5.2. Historical Cybersecurity Attacks (in the Context of IoT-Enabled Smart Grids)
5.2.1. Tram Hack Lodz, Poland (2008)
5.2.2. Texas Power Company (2009)
5.2.3. Iran Nuclear Facility Attack (2010)
5.2.4. Bowman Avenue Dam Cyberattack (2013)
5.2.5. Ukraine Power Grid Attack (2015)
5.2.6. Dyn Distributed Denial-of-Service (DDoS) Cyberattack (2016)
5.2.7. Attack on the Smart Building Facilities in Lappeenranta, Finland (2016)
5.2.8. Cyberattack on the UK Electrical Grid (2017)
5.2.9. Cyberattack at the Petrochemical Plant in Saudi Arabia (2017)
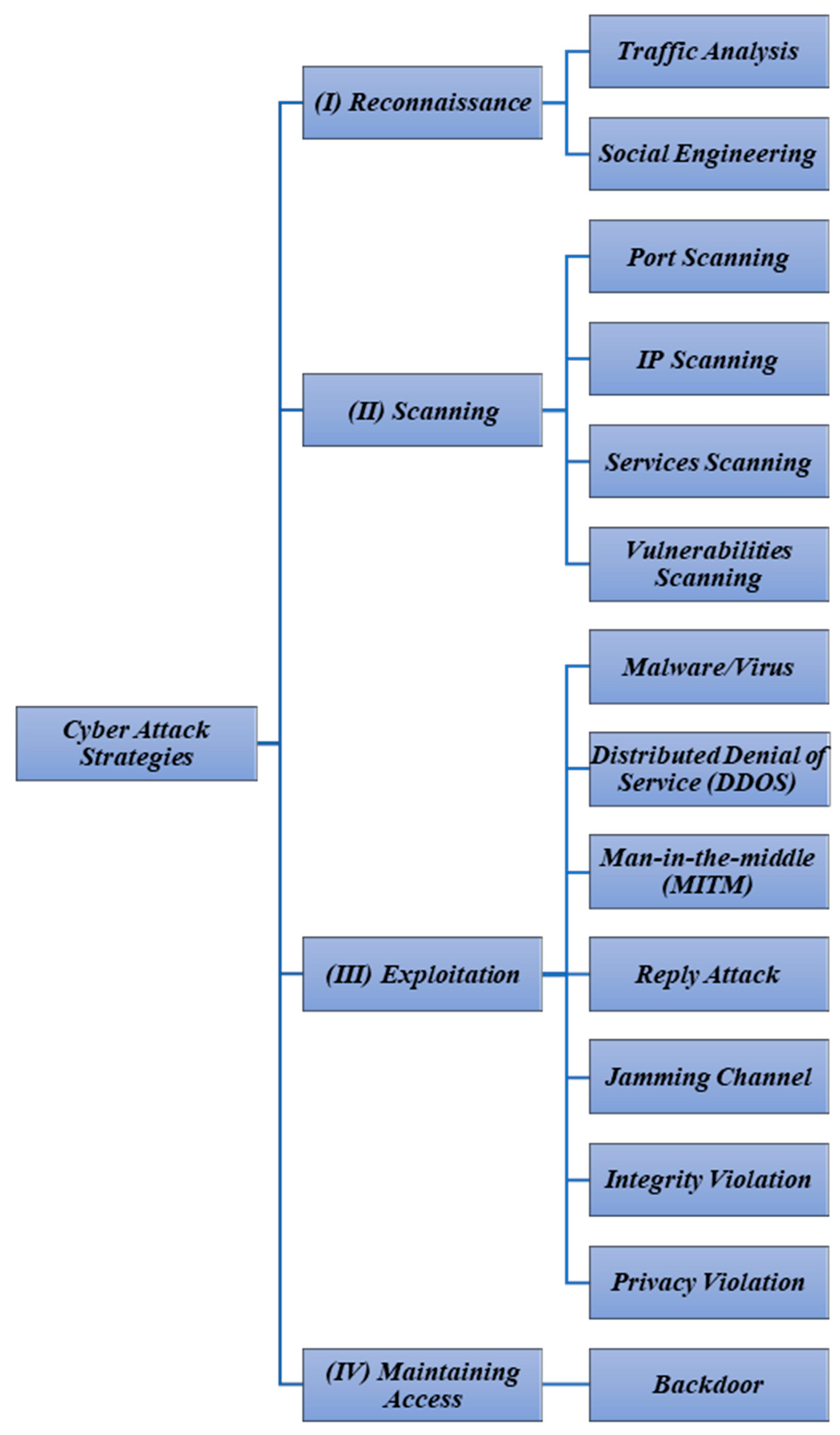
5.3. Main Cyberattack Strategies in IoT-Enabled Smart Grids
5.3.1. Reconnaissance Definition and Strategies
5.3.2. Scanning Strategies
5.3.3. Exploitation Strategies
5.3.4. Maintaining Access
5.4. Adverse Impacts of Cyberattacks on Smart Grids
5.4.1. Electricity Market Losses
5.4.2. Power System Stability
5.4.3. Energy Theft
5.4.4. Disruption of Service in Critical and Non-Critical Facilities
- (1)
- To gain initial access, for example, via hacking smart lights, to gain Wi-Fi authentication and eventually control of Wi-Fi network devices.
- (2)
- To cause an indirect service disruption, for example, by using a thermostat to manage the building’s air conditioning system from afar.
- (3)
- To obtain and disseminate information. Use an application that hacks smart gadgets, such as smart televisions, to make them act as though they are turned off and then use the microphone to record and leak conversations surrounding them.
- (4)
- For system abuse, such as producing light flashing at a certain frequency that might trigger epileptic seizures in individuals.
- (5)
- To initiate an intensified attack against critical facilities such as hospitals through a number of targeted smart devices. To deactivate smart home automation systems by targeting a large number of IoT-enabled smart home automation devices in a short amount of time.
5.4.5. Disruption of Transactive Energy Systems
- (1)
- Malware injection in the system can result in a large-scale power outage or data theft.
- (2)
- Cybercriminals can tamper with or damage smart meters for several purposes.
- (3)
- To interrupt the transactive system by manipulating the control signals of the relay and circuit breaker.
5.4.6. Environmental Security
5.5. Detection and Mitigation of IoT-Enabled Cyberattacks
5.5.1. Non-Human-Centric Methods
Machine-Learning-Based Methods
Cloud-Computing-Based Methods
Blockchain-Based Methods
5.5.2. Human-Centric Methods
- Multifactor Authentication
- Employee Training
- Password Strength
- Operating System (OS) Protection
- Customers Protection against Third-Party Applications
- Reporting of Malicious Behavior
6. Conclusions and Future Directions
- The framework and modeling of smart energy grids should be improved, and suitable reconfiguration technologies must be developed for the restoration aspect of electrical grids.
- Secure AMI technologies must be widely deployed in combination with advanced cloud and edge-computing facilities and 5G telecommunication technologies to enhance the functionality and security of the smart grids.
- Smart grids must be equipped with more secure communication protocols that consider the heterogeneity of IoT devices while enabling the deployment of AI algorithms onto the device itself instead of being controlled from afar to reduce the likelihood of communication breaches.
- Advanced secure and data communication systems based on blockchain methods must be extensively implemented in IoT-based smart energy systems.
- Game-theoretic models (specifically for the energy markets), and cognitive and deep-learning methods (for system behavioral modeling and forecasts) must be used effectively for the smooth and reliable operation of electrical grids.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Ref | IoT | 5G | Blockchain | Cyber Attacks | Edge Computing | Cloud Computing | Demand Response | Smart Energy Management | RESs | Smart Homes | Grid Restoration |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [30] | X | X | X | ||||||||
| [141] | X | X | |||||||||
| [36] | X | ||||||||||
| [142] | X | X | |||||||||
| [143] | X | X | |||||||||
| [3] | X | X | |||||||||
| [144] | X | X | X | ||||||||
| [149] | X | X | |||||||||
| [150] | X | X | X | ||||||||
| [57] | X | X | |||||||||
| [151] | X | X | |||||||||
| [29] | X | X | |||||||||
| [152] | X | X | X | ||||||||
| [58,64,153] | X | X | X | ||||||||
| [33] | X | ||||||||||
| [17] | X | X | |||||||||
| [154] | X | X | |||||||||
| [43] | X | X | |||||||||
| This Study | X | X | X | X | X | X | X | X | X |
References
- Amin, M. A smart self-healing grid: In pursuit of a more reliable and resilient system [in my view]. IEEE Power Energy Mag. 2013, 12, 110–112. [Google Scholar] [CrossRef]
- Goudarzi, A.; Li, Y.; Xiang, J. Efficient energy management of renewable resources in microgrids. In Renewable Energy Microgeneration Systems; Elsevier: Amsterdam, The Netherlands, 2021; pp. 285–321. [Google Scholar]
- Fan, D.; Ren, Y.; Feng, Q.; Liu, Y.; Wang, Z.; Lin, J. Restoration of smart grids: Current status, challenges, and opportunities. Renew. Sustain. Energy Rev. 2021, 143, 110909. [Google Scholar] [CrossRef]
- Abir, S.A.A.; Anwar, A.; Choi, J.; Kayes, A. IoT-enabled smart energy grid: Applications and challenges. IEEE Access 2021, 9, 50961–50981. [Google Scholar] [CrossRef]
- Espe, E.; Potdar, V.; Chang, E. Prosumer communities and relationships in smart grids: A literature review, evolution and future directions. Energies 2018, 11, 2528. [Google Scholar] [CrossRef]
- Tuballa, M.L.; Abundo, M.L. A review of the development of Smart Grid technologies. Renew. Sustain. Energy Rev. 2016, 59, 710–725. [Google Scholar] [CrossRef]
- Ullah, A.; Azeem, M.; Ashraf, H.; Alaboudi, A.A.; Humayun, M.; Jhanjhi, N. Secure healthcare data aggregation and transmission in IoT—A survey. IEEE Access 2021, 9, 16849–16865. [Google Scholar] [CrossRef]
- Pau, M.; Patti, E.; Barbierato, L.; Estebsari, A.; Pons, E.; Ponci, F.; Monti, A. A cloud-based smart metering infrastructure for distribution grid services and automation. Sustain. Energy Grids Netw. 2018, 15, 14–25. [Google Scholar] [CrossRef]
- Makkar, A.; Garg, S.; Kumar, N.; Hossain, M.S.; Ghoneim, A.; Alrashoud, M. An efficient spam detection technique for IoT devices using machine learning. IEEE Trans. Ind. Inform. 2020, 17, 903–912. [Google Scholar] [CrossRef]
- Doan, Q.-T.; Kayes, A.; Rahayu, W.; Nguyen, K. Integration of iot streaming data with efficient indexing and storage optimization. IEEE Access 2020, 8, 47456–47467. [Google Scholar] [CrossRef]
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Proc. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Geneiatakis, D.; Kounelis, I.; Neisse, R.; Nai-Fovino, I.; Steri, G.; Baldini, G. Security and privacy issues for an IoT based smart home. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1292–1297. [Google Scholar]
- Chang, J.; Kadry, S.N.; Krishnamoorthy, S. Review and synthesis of Big Data analytics and computing for smart sustainable cities. IET Intell. Transp. Syst. 2020, 14, 1363–1370. [Google Scholar] [CrossRef]
- Li, W.; Au, M.H.; Wang, Y. A fog-based collaborative intrusion detection framework for smart grid. Int. J. Netw. Manag. 2021, 31, e2107. [Google Scholar] [CrossRef]
- Hammad, E.; Nag, A.K.; Chennamaneni, A.; Aghashahi, M.; Dogdu, E. A Deep-Defense Approach for Next-Gen Cyber-Resilient Inter-Dependent Critical Infrastructure Systems. In Proceedings of the 2021 Resilience Week (RWS), Salt Lake City, UT, USA, 18–21 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–7. [Google Scholar]
- Lázaro, J.; Astarloa, A.; Rodríguez, M.; Bidarte, U.; Jiménez, J. A Survey on Vulnerabilities and Countermeasures in the Communications of the Smart Grid. Electronics 2021, 10, 1881. [Google Scholar] [CrossRef]
- Hasan, M.K.; Alkhalifah, A.; Islam, S.; Babiker, N.; Habib, A.; Aman, A.H.M.; Hossain, M. Blockchain Technology on Smart Grid, Energy Trading, and Big Data: Security Issues, Challenges, and Recommendations. Wirel. Commun. Mob. Comput. 2022, 2022, 9065768. [Google Scholar] [CrossRef]
- Goudarzi, A.; Kazemi, M. In DC Optimal Power Flow through the Linear Programming–in Context of Smart Grid. In Proceedings of the 24th Southern African Universities Power Engineering Conference, Vereeniging, South Africa, 26–28 January 2016. [Google Scholar]
- Moreno Escobar, J.J.; Morales Matamoros, O.; Tejeida Padilla, R.; Lina Reyes, I.; Quintana Espinosa, H. A Comprehensive Review on Smart Grids: Challenges and Opportunities. Sensors 2021, 21, 6978. [Google Scholar] [CrossRef]
- Pal, R.; Chavhan, S.; Gupta, D.; Khanna, A.; Padmanaban, S.; Khan, B.; Rodrigues, J.J. A comprehensive review on IoT-based infrastructure for smart grid applications. IET Renew. Power Gener. 2021, 15, 3761–3776. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Shaari, N.; Ibrahim, R. Internet of things energy system: Smart applications, technology advancement, and open issues. Int. J. Energy Res. 2021, 45, 8389–8419. [Google Scholar] [CrossRef]
- Ghasempour, A. Internet of things in smart grid: Architecture, applications, services, key technologies, and challenges. Inventions 2019, 4, 22. [Google Scholar] [CrossRef]
- Cao, J.; Yang, M. Energy internet--towards smart grid 2.0. In Proceedings of the 2013 Fourth International Conference on Networking and Distributed Computing, Los Angeles, CA, USA, 21–24 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 105–110. [Google Scholar]
- Wu, J.; Guo, S.; Li, J.; Zeng, D. Big data meet green challenges: Big data toward green applications. IEEE Syst. J. 2016, 10, 888–900. [Google Scholar] [CrossRef]
- Wang, K.; Yu, J.; Yu, Y.; Qian, Y.; Zeng, D.; Guo, S.; Xiang, Y.; Wu, J. A survey on energy internet: Architecture, approach, and emerging technologies. IEEE Syst. J. 2017, 12, 2403–2416. [Google Scholar] [CrossRef]
- Shahinzadeh, H.; Moradi, J.; Gharehpetian, G.B.; Nafisi, H.; Abedi, M. IoT architecture for smart grids. In Proceedings of the 2019 International Conference on Protection and Automation of Power System (IPAPS), Tehran, Iran, 8–9 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 22–30. [Google Scholar]
- Liu, Y.; Yang, X.; Wen, W.; Xia, M. Smarter Grid in the 5G Era: Integrating Power Internet of Things with Cyber Physical System. Front. Commun. Netw. 2021, 2, 23. [Google Scholar] [CrossRef]
- Kabalci, Y.; Kabalci, E.; Padmanaban, S.; Holm-Nielsen, J.B.; Blaabjerg, F. Internet of things applications as energy internet in smart grids and smart environments. Electronics 2019, 8, 972. [Google Scholar] [CrossRef]
- Tufail, A.; Namoun, A.; Alrehaili, A.; Ali, A. A Survey on 5G Enabled Multi-Access Edge Computing for Smart Cities: Issues and Future Prospects. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 107–118. [Google Scholar]
- Hui, H.; Ding, Y.; Shi, Q.; Li, F.; Song, Y.; Yan, J. 5G network-based Internet of Things for demand response in smart grid: A survey on application potential. Appl. Energy 2020, 257, 113972. [Google Scholar] [CrossRef]
- Ray, P.P. A survey of IoT cloud platforms. Future Comput. Inform. J. 2016, 1, 35–46. [Google Scholar] [CrossRef]
- Liu, Q.; Han, T.; Ansari, N. Learning-assisted secure end-to-end network slicing for cyber-physical systems. IEEE Netw. 2020, 34, 37–43. [Google Scholar] [CrossRef]
- Abrahamsen, F.E.; Ai, Y.; Cheffena, M. Communication technologies for smart grid: A comprehensive survey. Sensors 2021, 21, 8087. [Google Scholar] [CrossRef]
- Faheem, M.; Shah, S.B.H.; Butt, R.A.; Raza, B.; Anwar, M.; Ashraf, M.W.; Ngadi, M.A.; Gungor, V.C. Smart grid communication and information technologies in the perspective of Industry 4.0: Opportunities and challenges. Comput. Sci. Rev. 2018, 30, 1–30. [Google Scholar] [CrossRef]
- Bian, D.; Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Analysis of communication schemes for Advanced Metering Infrastructure (AMI). In Proceedings of the 2014 IEEE PES General Meeting|Conference & Exposition, National Harbor, MD, USA, 27–31 July 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–5. [Google Scholar]
- Dragičević, T.; Siano, P.; Prabaharan, S. Future generation 5G wireless networks for smart grid: A comprehensive review. Energies 2019, 12, 2140. [Google Scholar]
- De Sanctis, M.; Cianca, E.; Araniti, G.; Bisio, I.; Prasad, R. Satellite communications supporting internet of remote things. IEEE Internet Things J. 2015, 3, 113–123. [Google Scholar] [CrossRef]
- Pflanzner, T.; Kertész, A. A survey of IoT cloud providers. In Proceedings of the 2016 39th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 30 May–3 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 730–735. [Google Scholar]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An overview on edge computing research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Slama, S.B. Prosumer in smart grids based on intelligent edge computing: A review on Artificial Intelligence Scheduling Techniques. Ain Shams Eng. J. 2021, 13, 101504. [Google Scholar] [CrossRef]
- Savazzi, S.; Nicoli, M.; Rampa, V. Federated learning with cooperating devices: A consensus approach for massive IoT networks. IEEE Internet Things J. 2020, 7, 4641–4654. [Google Scholar] [CrossRef]
- Khan, S.A.; Liu, C.; Ansari, J.A. Centralized fuzzy logic based optimization of pi controllers for VSC control in MTDC network. J. Electr. Eng. Technol. 2020, 15, 2577–2585. [Google Scholar] [CrossRef]
- Mocrii, D.; Chen, Y.; Musilek, P. IoT-based smart homes: A review of system architecture, software, communications, privacy and security. Internet Things 2018, 1, 81–98. [Google Scholar] [CrossRef]
- Tightiz, L.; Yang, H. A comprehensive review on IoT protocols’ features in smart grid communication. Energies 2020, 13, 2762. [Google Scholar] [CrossRef]
- Avancini, D.B.; Rodrigues, J.J.; Rabêlo, R.A.; Das, A.K.; Kozlov, S.; Solic, P. A new IoT-based smart energy meter for smart grids. Int. J. Energy Res. 2021, 45, 189–202. [Google Scholar] [CrossRef]
- Trappey, A.J.; Trappey, C.V.; Govindarajan, U.H.; Chuang, A.C.; Sun, J.J. A review of essential standards and patent landscapes for the Internet of Things: A key enabler for Industry 4.0. Adv. Eng. Inform. 2017, 33, 208–229. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S.; Rodrigues, J.J. Fog computing for smart grid systems in the 5G environment: Challenges and solutions. IEEE Wirel. Commun. 2019, 26, 47–53. [Google Scholar] [CrossRef]
- Repo, S.; Pylvanainen, J.; Kauppinen, M.; Repo, S.; Jarventausta, P. Automatic Meter Infrastructure (AMI) as a part of flexibility market. In Proceedings of the 2018 15th International Conference on the European Energy Market (EEM), Lodz, Poland, 27–29 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Agalgaonkar, Y.P.; Hammerstrom, D.J. Evaluation of smart grid technologies employed for system reliability improvement: Pacific northwest smart grid demonstration experience. IEEE Power Energy Technol. Syst. J. 2017, 4, 24–31. [Google Scholar] [CrossRef]
- Al Dakheel, J.; Del Pero, C.; Aste, N.; Leonforte, F. Smart buildings features and key performance indicators: A review. Sustain. Cities Soc. 2020, 61, 102328. [Google Scholar] [CrossRef]
- Avancini, D.B.; Rodrigues, J.J.; Martins, S.G.; Rabêlo, R.A.; Al-Muhtadi, J.; Solic, P. Energy meters evolution in smart grids: A review. J. Clean. Prod. 2019, 217, 702–715. [Google Scholar] [CrossRef]
- Nižetić, S.; Djilali, N.; Papadopoulos, A.; Rodrigues, J.J. Smart technologies for promotion of energy efficiency, utilization of sustainable resources and waste management. J. Clean. Prod. 2019, 231, 565–591. [Google Scholar] [CrossRef]
- Switch, S. The Pros and Cons of Smart Meters. Available online: https://www.simplyswitch.com/energy/guides/smart-meters-pros-cons/ (accessed on 1 April 2022).
- Sovacool, B.K.; Kivimaa, P.; Hielscher, S.; Jenkins, K. Vulnerability and resistance in the United Kingdom’s smart meter transition. Energy Policy 2017, 109, 767–781. [Google Scholar] [CrossRef]
- Goudarzi, A.; Li, Y.; Fahad, S.; Xiang, J. A game theory-based interactive demand response for handling dynamic prices in security-constrained electricity markets. Sustain. Cities Soc. 2021, 72, 103073. [Google Scholar] [CrossRef]
- Waseem, M.; Lin, Z.; Liu, S.; Jinai, Z.; Rizwan, M.; Sajjad, I.A. Optimal BRA based electric demand prediction strategy considering instance-based learning of the forecast factors. Int. Trans. Electr. Energy Syst. 2021, 31, e12967. [Google Scholar] [CrossRef]
- Waseem, M.; Lin, Z.; Liu, S.; Sajjad, I.A.; Aziz, T. Optimal GWCSO-based home appliances scheduling for demand response considering end-users comfort. Electr. Power Syst. Res. 2020, 187, 106477. [Google Scholar] [CrossRef]
- Waseem, M.; Lin, Z.; Liu, S.; Zhang, Z.; Aziz, T.; Khan, D. Fuzzy compromised solution-based novel home appliances scheduling and demand response with optimal dispatch of distributed energy resources. Appl. Energy 2021, 290, 116761. [Google Scholar] [CrossRef]
- Strielkowski, W.; Dvořák, M.; Rovný, P.; Tarkhanova, E.; Baburina, N. 5G wireless networks in the future renewable energy systems. Front. Energy Res. 2021, 9, 714803. [Google Scholar] [CrossRef]
- Khan, T.; Yu, M.; Waseem, M. Review on recent optimization strategies for hybrid renewable energy system with hydrogen technologies: State of the art, trends and future directions. Int. J. Hydrogen Energy 2022, 47, 25155–25201. [Google Scholar] [CrossRef]
- Agnew, D.; Aljohani, N.; Mathieu, R.; Boamah, S.; Nagaraj, K.; McNair, J.; Bretas, A. Implementation Aspects of Smart Grids Cyber-Security Cross-Layered Framework for Critical Infrastructure Operation. Appl. Sci. 2022, 12, 6868. [Google Scholar] [CrossRef]
- Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A Survey on Cybersecurity Challenges, Detection, and Mitigation Techniques for the Smart Grid. Energies 2021, 14, 5894. [Google Scholar] [CrossRef]
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014.
- Agarkar, A.; Agrawal, H. A review and vision on authentication and privacy preservation schemes in smart grid network. Secur. Priv. 2019, 2, e62. [Google Scholar] [CrossRef]
- Shuaib, K.; Trabelsi, Z.; Abed-Hafez, M.; Gaouda, A.; Alahmad, M. Resiliency of smart power meters to common security attacks. Procedia Comput. Sci. 2015, 52, 145–152. [Google Scholar] [CrossRef]
- Kimani, K.; Oduol, V.; Langat, K. Cyber security challenges for IoT-based smart grid networks. J. Crit. Infrastruct. Prot. 2019, 25, 36–49. [Google Scholar] [CrossRef]
- Kenney, M. Cyber-terrorism in a post-stuxnet world. Orbis 2015, 59, 111–128. [Google Scholar] [CrossRef]
- Libicki, M.C. Correlations between cyberspace attacks and kinetic attacks. In Proceedings of the 2020 12th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 26–29 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 199–213. [Google Scholar]
- Abdella, J.A.; Shuaib, K. An architecture for blockchain based peer to peer energy trading. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 412–419. [Google Scholar]
- Dileep, G. A survey on smart grid technologies and applications. Renew. Energ 2020, 146, 2589–2625. [Google Scholar] [CrossRef]
- Chen, X.; Li, Y.; Goudarzi, A.; Xiang, J. Leaderless Consensus of a Hierarchical Cyber-Physical System. arXiv 2020, arXiv:2004.07411. [Google Scholar]
- Faquir, D.; Chouliaras, N.; Sofia, V.; Olga, K.; Maglaras, L. Cybersecurity in smart grids, challenges and solutions. AIMS Electron. Electr. Eng. 2021, 5, 24–37. [Google Scholar]
- Zhang, F.; Mahler, M.; Li, Q. Flooding attacks against secure time-critical communications in the power grid. In Proceedings of the 2017 IEEE International Conference on Smart Grid Communications (SmartGridComm), Dresden, Germany, 23–27 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 449–454. [Google Scholar]
- Lu, Z.; Lu, X.; Wang, W.; Wang, C. Review and evaluation of security threats on the communication networks in the smart grid. In Proceedings of the 2010-Milcom 2010 Military Communications Conference, San Jose, CA, USA, 31 October–3 November 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 1830–1835. [Google Scholar]
- Huseinovic, A.; Mrdovic, S.; Bicakci, K.; Uludag, S. A taxonomy of the emerging Denial-of-Service attacks in the smart grid and countermeasures. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20–21 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–4. [Google Scholar]
- Kurt, M.N.; Yılmaz, Y.; Wang, X. Real-time detection of hybrid and stealthy cyber-attacks in smart grid. IEEE Trans. Inf. Forensics Secur. 2018, 14, 498–513. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Sun, X. A survey on FinTech. J. Netw. Comput. Appl. 2018, 103, 262–273. [Google Scholar] [CrossRef]
- Sakhnini, J.; Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G. Security aspects of Internet of Things aided smart grids: A bibliometric survey. Internet Things 2021, 14, 100111. [Google Scholar] [CrossRef]
- Cui, L.; Qu, Y.; Gao, L.; Xie, G.; Yu, S. Detecting false data attacks using machine learning techniques in smart grid: A survey. J. Netw. Comput. Appl. 2020, 170, 102808. [Google Scholar] [CrossRef]
- Riggs, H.; Tufail, S.; Khan, M.; Parvez, I.; Sarwat, A.I. Detection of False Data Injection of PV Production. In Proceedings of the 2021 IEEE Green Technologies Conference (GreenTech), Denver, CO, USA, 7–9 April 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 7–12. [Google Scholar]
- El Mrabet, Z.; Kaabouch, N.; El Ghazi, H.; El Ghazi, H. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Rajendran, G.; Sathyabalu, H.V.; Sachi, M.; Devarajan, V. Cyber Security in Smart Grid: Challenges and Solutions. In Proceedings of the 2019 2nd International Conference on Power and Embedded Drive Control (ICPEDC), Chennai, India, 21–23 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 546–551. [Google Scholar]
- Peng, C.; Sun, H.; Yang, M.; Wang, Y.-L. A survey on security communication and control for smart grids under malicious cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1554–1569. [Google Scholar] [CrossRef]
- Huang, X.; Qin, Z.; Liu, H. A survey on power grid cyber security: From component-wise vulnerability assessment to system-wide impact analysis. IEEE Access 2018, 6, 69023–69035. [Google Scholar] [CrossRef]
- Wang, X.; Shi, D.; Wang, J.; Yu, Z.; Wang, Z. Online identification and data recovery for PMU data manipulation attack. IEEE Trans. Smart Grid 2019, 10, 5889–5898. [Google Scholar] [CrossRef]
- Alohali, B.; Kifayat, K.; Shi, Q.; Hurst, W. Replay attack impact on advanced metering infrastructure (AMI). In Smart Grid Inspired Future Technol; Springer: Cham, Switzerland, 2017; pp. 52–59. [Google Scholar]
- Liu, Z.; Wang, Q.; Ye, Y.; Tang, Y. A GAN Based Data Injection Attack Method on Data-Driven Strategies in Power Systems. IEEE Trans. Smart Grid 2022, 13, 3203–3213. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Lam, K.-Y.; Zhang, X.; Ghias, A.M.; Koh, L.H.; Yang, L. Blockchain for future smart grid: A comprehensive survey. IEEE Internet Things J. 2020, 8, 18–43. [Google Scholar] [CrossRef]
- Kurt, M.N.; Yılmaz, Y.; Wang, X. Distributed quickest detection of cyber-attacks in smart grid. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2015–2030. [Google Scholar] [CrossRef]
- Burg, A.; Chattopadhyay, A.; Lam, K.-Y. Wireless communication and security issues for cyber–physical systems and the Internet-of-Things. Proc. IEEE 2017, 106, 38–60. [Google Scholar] [CrossRef]
- Aldwairi, M.; Alansari, D. n-Grams exclusion and inclusion filter for intrusion detection in Internet of Energy big data systems. Trans. Emerg. Telecommun. Technol. 2022, 33, e3711. [Google Scholar] [CrossRef]
- Alotaibi, B. Utilizing blockchain to overcome cyber security concerns in the internet of things: A review. IEEE Sens. J. 2019, 19, 10953–10971. [Google Scholar] [CrossRef]
- Sani, A.S.; Yuan, D.; Jin, J.; Gao, L.; Yu, S.; Dong, Z.Y. Cyber security framework for Internet of Things-based Energy Internet. Future Gener. Comput. Syst. 2019, 93, 849–859. [Google Scholar] [CrossRef]
- Wang, T.; Hua, H.; Wei, Z.; Cao, J. Challenges of blockchain in new generation energy systems and future outlooks. Int. J. Electr. Power Energy Syst. 2022, 135, 107499. [Google Scholar] [CrossRef]
- Rakas, S.B.; Timčenko, V.; Kabović, M.; Kabović, A. Intrusion Detection Systems in Smart Grid. In Proceedings of the 2022 21st International Symposium Infoteh-Jahorina (INFOTEH), East Sarajevo, Bosnia and Herzegovina, 16–18 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Mohammadi, Z.; Pinto, S.J.; Panda, G.; Thokchom, S. A Survey of Cyber Security in Smart Microgrid. In Sustainable Energy and Technological Advancements; Springer: Singapore, 2022; pp. 687–698. [Google Scholar]
- Badar, A.Q.; Patil, P.; Sanjari, M. Introduction and history of virtual power plants with experimental examples. In Scheduling and Operation of Virtual Power Plants; Elsevier: Amsterdam, The Netherlands, 2022; pp. 1–26. [Google Scholar]
- Li, Y.; Li, T.; Zhang, H.; Xie, X.; Sun, Q. Distributed Resilient Double-Gradient-Descent Based Energy Management Strategy for Multi-Energy System under DoS Attacks. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2301–2316. [Google Scholar] [CrossRef]
- Brown, M.A.; Zhou, S.; Ahmadi, M. Smart grid governance: An international review of evolving policy issues and innovations. Wiley Interdiscip. Rev. Energy Environ. 2018, 7, e290. [Google Scholar] [CrossRef]
- Holik, F.; Flå, L.H.; Jaatun, M.G.; Yayilgan, S.Y.; Foros, J. Threat modeling of a smart grid secondary substation. Electronics 2022, 11, 850. [Google Scholar] [CrossRef]
- Goudarzi, A.; Fahad, S.; Ni, J.; Ghayoor, F.; Siano, P.; Haes Alhelou, H. A sequential hybridization of ETLBO and IPSO for solving reserve-constrained combined heat, power and economic dispatch problem. IET Gener. Transm. Distrib. 2022, 16, 1930–1949. [Google Scholar] [CrossRef]
- Goudarzi, A.; Zhang, C.; Fahad, S.; Mahdi, A.J. A hybrid sequential approach for solving environmentally constrained optimal scheduling in co-generation systems. Energy Rep. 2021, 7, 3460–3479. [Google Scholar] [CrossRef]
- Khezri, R.; Mahmoudi, A.; Aki, H. Optimal planning of solar photovoltaic and battery storage systems for grid-connected residential sector: Review, challenges and new perspectives. Renew. Sustain. Energy Rev. 2022, 153, 111763. [Google Scholar] [CrossRef]
- Ghasemi-Marzbali, A. Fast-charging station for electric vehicles, challenges and issues: A comprehensive review. J. Energy Storage 2022, 49, 104136. [Google Scholar]
- Khan, S.A.; Wang, M.; Su, W.; Liu, G.; Chaturvedi, S. Grid-Forming Converters for Stability Issues in Future Power Grids. Energies 2022, 15, 4937. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-security of smart microgrids: A survey. Energies 2020, 14, 27. [Google Scholar] [CrossRef]
- Fahad, S.; Goudarzi, A.; Xiang, J. Demand management of active distribution network using coordination of virtual synchronous generators. IEEE Trans. Sustain. Energy 2020, 12, 250–261. [Google Scholar] [CrossRef]
- Farraj, A.; Hammad, E.; Kundur, D. On the impact of cyber attacks on data integrity in storage-based transient stability control. IEEE Trans. Ind. Inform. 2017, 13, 3322–3333. [Google Scholar] [CrossRef]
- Khalghani, M.R.; Solanki, J.; Solanki, S.K.; Khooban, M.H.; Sargolzaei, A. Resilient frequency control design for microgrids under false data injection. IEEE Trans. Ind. Electron. 2020, 68, 2151–2162. [Google Scholar] [CrossRef]
- Ibrahim, M.S.; Dong, W.; Yang, Q. Machine learning driven smart electric power systems: Current trends and new perspectives. Appl. Energy 2020, 272, 115237. [Google Scholar] [CrossRef]
- Ali, W.; Din, I.U.; Almogren, A.; Kim, B.-S. A Novel Privacy Preserving Scheme for Smart Grid-Based Home Area Networks. Sensors 2022, 22, 2269. [Google Scholar] [CrossRef]
- Abdullah, A.M.; Ullah, I.; Khan, M.A.; Alsharif, M.H.; Mostafa, S.M.; Wu, J.M.-T. An Efficient Multidocument Blind Signcryption Scheme for Smart Grid-Enabled Industrial Internet of Things. Wirel. Commun. Mob. Comput. 2022, 2022, 7779152. [Google Scholar] [CrossRef]
- Zamani, R.; Moghaddam, M.P.; Haghifam, M.-R. Dynamic Characteristics Preserving Data Compressing Algorithm For Transactive Energy Management Frameworks. IEEE Trans. Ind. Inform. 2022, 18, 7587–7596. [Google Scholar] [CrossRef]
- Lin, Y.; Wang, J. Realizing the Transactive Energy Future with Local Energy Market: An Overview. Curr. Sustain./Renew. Energy Rep. 2022, 9, 1–14. [Google Scholar] [CrossRef]
- Goel, S.; Hong, Y. Security challenges in smart grid implementation. In Smart Grid Security; Springer: London, UK, 2015; pp. 1–39. [Google Scholar]
- Sharifi, A.; Yamagata, Y. Principles and criteria for assessing urban energy resilience: A literature review. Renew. Sustain. Energy Rev. 2016, 60, 1654–1677. [Google Scholar] [CrossRef]
- Kalogridis, G.; Sooriyabandara, M.; Fan, Z.; Mustafa, M.A. Toward unified security and privacy protection for smart meter networks. IEEE Syst. J. 2013, 8, 641–654. [Google Scholar] [CrossRef]
- Mühlberg, J.T.; Cleemput, S.; Mustafa, M.A.; Bulck, J.V.; Preneel, B.; Piessens, F. An implementation of a high assurance smart meter using protected module architectures. In Proceedings of the IFIP International Conference on Information Security Theory and Practice, Heraklion, Greece, 26–27 September 2016; Springer: Cham, Switzerland, 2016; pp. 53–69. [Google Scholar]
- Ma, C. Smart city and cyber-security; technologies used, leading challenges and future recommendations. Energy Rep. 2021, 7, 7999–8012. [Google Scholar] [CrossRef]
- Canaan, B.; Colicchio, B.; Ould Abdeslam, D. Microgrid cyber-security: Review and challenges toward resilience. Appl. Sci. 2020, 10, 5649. [Google Scholar] [CrossRef]
- Gunduz, M.Z.; Das, R. A comparison of cyber-security oriented testbeds for IoT-based smart grids. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security (ISDFS), Antalya, Turkey, 22–25 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Sadik, S.; Ahmed, M.; Sikos, L.F.; Islam, A. Toward a sustainable cybersecurity ecosystem. Computers 2020, 9, 74. [Google Scholar] [CrossRef]
- Yamin, M.M.; Ullah, M.; Ullah, H.; Katt, B. Weaponized AI for cyber attacks. J. Inf. Secur. Appl. 2021, 57, 102722. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Mahajan, V.; Singh, N.K.; Gupta, P.K.; Yadav, A.K.; Mudagal, S. Smart Grid Cyber Security Threats and Solutions. In Deregulated Electricity Structures and Smart Grids; CRC Press: Boca Raton, FL, USA, 2022; pp. 233–258. [Google Scholar]
- Badihi, H. Smart Grid Resilience. In Handbook of Smart Energy Systems; Springer: Cham, Switzerland, 2022; pp. 1–25. [Google Scholar]
- Hudani, D.; Haseeb, M.; Taufiq, M.; Umer, M.A.; Kandasamy, N.K. A Data-Centric Approach to Generate Invariants for a Smart Grid Using Machine Learning. arXiv 2022, arXiv:2202.06717. [Google Scholar]
- Ahmad, T.; Madonski, R.; Zhang, D.; Huang, C.; Mujeeb, A. Data-driven probabilistic machine learning in sustainable smart energy/smart energy systems: Key developments, challenges, and future research opportunities in the context of smart grid paradigm. Renew. Sustain. Energy Rev. 2022, 160, 112128. [Google Scholar] [CrossRef]
- Hink, R.C.B.; Beaver, J.M.; Buckner, M.A.; Morris, T.; Adhikari, U.; Pan, S. Machine learning for power system disturbance and cyber-attack discrimination. In Proceedings of the 2014 7th International symposium on resilient control systems (ISRCS), Denver, CO, USA, 19–21 August 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–8. [Google Scholar]
- Ashrafuzzaman, M.; Das, S.; Chakhchoukh, Y.; Shiva, S.; Sheldon, F.T. Detecting stealthy false data injection attacks in the smart grid using ensemble-based machine learning. Comput. Secur. 2020, 97, 101994. [Google Scholar] [CrossRef]
- Pei, C.; Xiao, Y.; Liang, W.; Han, X. A Deviation-Based Detection Method Against False Data Injection Attacks in Smart Grid. IEEE Access 2021, 9, 15499–15509. [Google Scholar] [CrossRef]
- He, Y.; Mendis, G.J.; Wei, J. Real-time detection of false data injection attacks in smart grid: A deep learning-based intelligent mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Ali, S.; Li, Y. Learning multilevel auto-encoders for DDoS attack detection in smart grid network. IEEE Access 2019, 7, 108647–108659. [Google Scholar] [CrossRef]
- Califano, A.; Dincelli, E.; Goel, S. Using features of cloud computing to defend smart grid against DDoS attacks. In Proceedings of the 10th Annual Symposium on Information Assurance (ASIA 15), Albany, NY, USA, 2–3 June 2015; pp. 44–50. [Google Scholar]
- Eltayieb, N.; Elhabob, R.; Hassan, A.; Li, F. An efficient attribute-based online/offline searchable encryption and its application in cloud-based reliable smart grid. J. Syst. Archit. 2019, 98, 165–172. [Google Scholar] [CrossRef]
- Chen, L.; Liu, J.; Ha, W. Cloud service security evaluation of smart grid using deep belief network. Int. J. Sens. Netw. 2020, 33, 109–121. [Google Scholar] [CrossRef]
- Bagherzadeh, L.; Shahinzadeh, H.; Shayeghi, H.; Dejamkhooy, A.; Bayindir, R.; Iranpour, M. Integration of cloud computing and IoT (CloudIoT) in smart grids: Benefits, challenges, and solutions. In Proceedings of the 2020 International Conference on Computational Intelligence for Smart Power System and Sustainable Energy (CISPSSE), Keonjhar, India, 29–31 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–8. [Google Scholar]
- Dehalwar, V.; Kolhe, M.L.; Deoli, S.; Jhariya, M.K. Blockchain-based trust management and authentication of devices in smart grid. Clean. Eng. Technol. 2022, 8, 100481. [Google Scholar]
- Mahmood, S.; Chadhar, M.; Firmin, S. Cybersecurity Challenges in Blockchain Technology: A Scoping Review. Hum. Behav. Emerg. Technol. 2022, 2022, 7384000. [Google Scholar] [CrossRef]
- Asif, M.; Aziz, Z.; Bin Ahmad, M.; Khalid, A.; Waris, H.A.; Gilani, A. Blockchain-Based Authentication and Trust Management Mechanism for Smart Cities. Sensors 2022, 22, 2604. [Google Scholar] [CrossRef] [PubMed]
- Zhong, Y.; Zhou, M.; Li, J.; Chen, J.; Liu, Y.; Zhao, Y.; Hu, M. Distributed blockchain-based authentication and authorization protocol for smart grid. Wirel. Commun. Mob. Comput. 2021, 2021, 5560621. [Google Scholar] [CrossRef]
- Kirpes, B.; Mengelkamp, E.; Schaal, G.; Weinhardt, C. Design of a microgrid local energy market on a blockchain-based information system. IT-Inf. Technol. 2019, 61, 87–99. [Google Scholar] [CrossRef]
- Fischer-Hübner, S.; Alcaraz, C.; Ferreira, A.; Fernandez-Gago, C.; Lopez, J.; Markatos, E.; Islami, L.; Akil, M. Stakeholder perspectives and requirements on cybersecurity in Europe. J. Inf. Secur. Appl. 2021, 61, 102916. [Google Scholar] [CrossRef]
- Gope, P. PMAKE: Privacy-aware multi-factor authenticated key establishment scheme for advance metering infrastructure in smart grid. Comput. Commun. 2020, 152, 338–344. [Google Scholar] [CrossRef]
- Dong, H.; Zhao, J.; Yang, X.; Yang, K. Combination of D-AHP and grey theory for the assessment of the information security risks of smart grids. Math. Probl Eng. 2020, 2020, 3517104. [Google Scholar] [CrossRef]
- Sun, C.-C.; Cardenas, D.J.S.; Hahn, A.; Liu, C.-C. Intrusion detection for cybersecurity of smart meters. IEEE Trans. Smart Grid 2020, 12, 612–622. [Google Scholar] [CrossRef]
- El May, Z.; Ayed, H.K.B.; Machfar, D. State of the art on Privacy Risk Estimation Related to Android Applications. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 889–894. [Google Scholar]
- Djenna, A.; Harous, S.; Saidouni, D.E. Internet of things meet internet of threats: New concern cyber security issues of critical cyber infrastructure. Appl. Sci. 2021, 11, 4580. [Google Scholar] [CrossRef]
- Yahaya, A.S.; Javaid, N.; Ullah, S.; Khalid, R.; Javed, M.U.; Khan, R.U.; Wadud, Z.; Khan, M.A. A secure and efficient energy trading model using blockchain for a 5G-deployed smart community. Wirel. Commun. Mob. Comput. 2022, 2022, 6953125. [Google Scholar]
- Shahinzadeh, H.; Mahmoudi, A.; Moradi, J.; Nafisi, H.; Kabalci, E.; Benbouzid, M. Anomaly Detection and Resilience-Oriented Countermeasures against Cyberattacks in Smart Grids. In Proceedings of the 2021 7th International Conference on Signal Processing and Intelligent Systems (ICSPIS), Tehran, Iran, 29–30 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–7. [Google Scholar]
- Leszczyna, R. Standards on cyber security assessment of smart grid. Int. J. Crit. Infrastruct. Prot. 2018, 22, 70–89. [Google Scholar] [CrossRef]
- Allahvirdizadeh, Y.; Moghaddam, M.P.; Shayanfar, H. A survey on cloud computing in energy management of the smart grids. Int. Trans. Electr. Energy Syst. 2019, 29, e12094. [Google Scholar] [CrossRef]
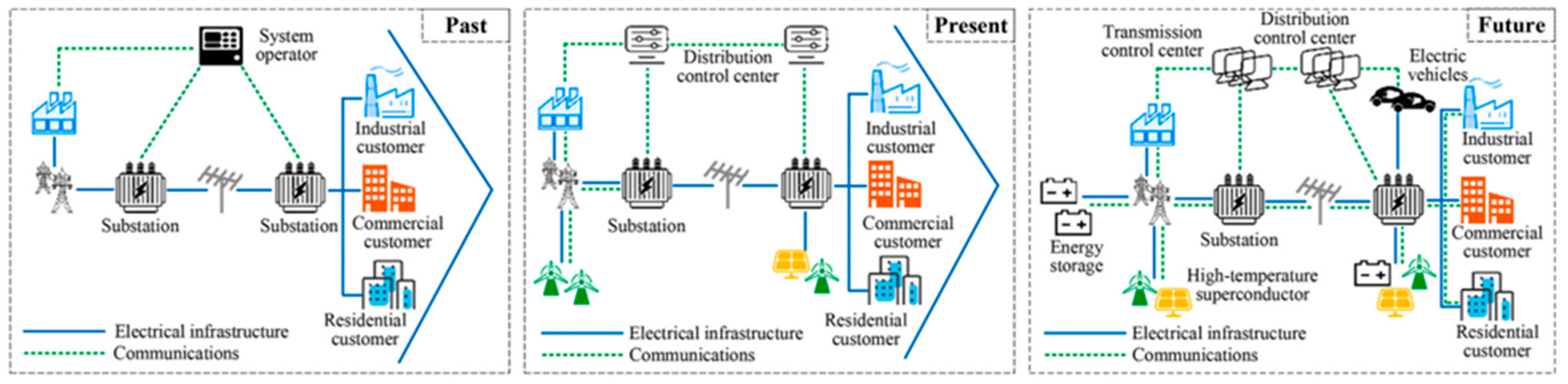







| Features | Traditional Grid | Smart Grid |
|---|---|---|
| Communication | One-way communication | Two-way communication with interaction |
| Power generation | Centralized | Distributed generation, provides support during peak hours when load demand increases |
| Topology | Radial | Different network topology |
| Operation and maintenance | Manual monitoring, periodic equipment maintenance | Real-time monitoring, prognostic, and event-driven maintenance |
| Power restoration | Manual equipment checks and time-based maintenance | Self-healing; smart grid can anticipate, identify, and respond to faults and outages |
| Reliability | Prone to failure and cascading outages | Pro-active, real-time, and islanding |
| Metering | Electro-mechanical | Advanced metering arrangement that drives the facility to track and regulate energy consumption |
| Customer participation | Limited interaction or none | Extensive interaction |
| Power quality control | Less use of sensors and less power quality | Contains numerous modules, for example, sensors, smart meters, and technologies on the distribution grid that aid in managing the parameters, such as voltage and power factor, to improve the power quality |
| Renewable power source integration | Optimized for non-renewable resources | Offers essential insights and enables automation for renewable power resources to supply electricity to grids while their management is being optimized |
| Operational cost and wastage at peak hour | High at peak hours | Low at peak hour due to distributed generation and control over the power consumption |
| Technology | Date Rate | Coverage | Application | Advantages | Disadvantages | Network Type |
|---|---|---|---|---|---|---|
| Ethernet | Up to 100 Gbps | Up to 100 m | In-home communication and backbone communication | Good for short distances | Coverage limitations | Premise Network, NAN, FAN, and WAN |
| Broadband PLC | Up to 300 Mbps | Up to 1500 m | SCADA and backbone communication in power generation sector | Existing infrastructure, standardized and high reliability | Noisy channel environment and disturbance | NAN, FAN, and WAN |
| Narrowband PLC | 10–500 Kbps | Up to 3 km | SCADA and backbone communication in power generation sector | Existing infrastructure, standardized and high reliability | Noisy channel environment and disturbance | NAN, FAN and WAN |
| HomePlug | 4, 5, and 10 Mbps | Up to 200 m | In-home communication and smart appliances | Low cost and energy | Coverage limitations and disturbance | Premise Network |
| Fiber Optic | Up to 100 Gbps | Up to 100 km | SCADA and backbone communication in power generation sector | High bandwidth, high data rate and not susceptible to electromagnetic interference | Costly | WAN |
| Technology | Date Rate | Coverage | Application | Advantages | Disadvantages | Network Type |
|---|---|---|---|---|---|---|
| WiMAX | 75 Mbps | Up to 50 km | In-home communication and smart meter reading | Low cost and low energy | Not widespread, coverage highly reduced if loss in line of sight | NAN, FAN, and WAN |
| ZigBee | 20–250 Kbps | Up to 100 m | In-home communication, energy monitoring, smart appliances, and home automation | Mesh capability, simplicity, mobility, low cost and energy | Low data rate, short range and poor interference | Premise Network, NAN, and FAN |
| Z-Wave | 9–40 Kbps | Up to 30 m | Wireless mesh network | Mesh capability, simplicity, mobility, low cost and energy | Low data rate, short range and poor interference | Premise Network |
| Wi-Fi | 2 Mbps–1.7 Gbps | Up to 100 m | In-home communication, smart appliances. Home automation and SCADA | Good for short distances | Security | Premise Network, NAN, and FAN |
| 3G | Up to 42 Mbps | 70 km | SCADA and smart meter reading | Already-existing network, high security, low cost, and large coverage | Network shared with customers may result in congestion | NAN, FAN, and WAN |
| 4G/LTE | Up to979 Mbps | Up to 16 km | SCADA and smart meter reading | Already-existing network, high security, low cost, and large coverage | Network shared with customers may result in congestion | NAN, FAN, and WAN |
| LTE-M | 7 Mbps | Up to 10 km | Smart meter reading | Low cost and energy and scalability | Low data rate | NAN and FAN |
| NB-IoT | 159 Kbps | Up to 10 km | Smart meter reading | Low cost and energy and scalability | Low date rate | NAN and FAN |
| 5G | Up to 20 Gbps | Up to 500 m | SCADA, remote control and smart meter reading | Low energy, low latency, high data rate, and scalability | — | NAN, FAN, and WAN |
| Satellite | 50 Mbps | — | Backup, remote location communication | Good when no other alternative is feasible | High cost | WAN |
| Fog-Based SCADA Parts | Components | Connection Type | Tasks |
|---|---|---|---|
| Terminal devices | Sensors, actuators, and appliances | Wireless sensor network (WSN), Wi-Fi, Bluetooth, and ZigBee | Information collection |
| Fog computing devices | Switches, access points, firewalls, cloudlets, and routers | Local area networks (LANs) and wide area networks (WANs) | Analyze and process the collected data from terminal devices |
| Cloud systems | Cloud data centers, cloud storage, and gateway devices | Local area networks (LANs), wide area networks (WANs), virtual private networks (VPNs), and/or APIs | Aggregate and process the collected statistical information |
| SCADA systems | Field instrumentation, field controllers (RTUs/PLCs), and human–machine interfaces (HMIs) | Combinations of wired and wireless connections | Based on the collected results from the cloud, the system operator takes control decision and regulates different parameters of the energy grid |
| Categories | Itemized Description | Explanation |
|---|---|---|
| Advantages | Free Installation | No payment is required for the meter installation |
| Savings opportunities | Smart meters can help families cut their energy costs by providing insight into their energy usage and assisting them in changing their consumption behavior to save money | |
| Emission reduction | Customers can alter their consumption not only to save money on bills but also to lessen their carbon footprint | |
| Energy consumption monitoring | Smart meters can help energy users to understand how their energy habits convert into costs by displaying their energy consumption not just in kilowatt hours but also in dollars | |
| No meter readings needed | Smart meters transmit information about the customers’ energy usage automatically, eliminating the need for manual readings. | |
| No bill estimation is required | Daily, weekly, and monthly bill projections can be accessed through the users’ accounts | |
| Pre-payment meters option | Households on pay-as-you-go rates can benefit from smart prepayment meters, which can help them keep track of their credit balances and even send out notifications when the meters are running low | |
| Enabling time-of-use (ToU) tariffs | Some service providers have the ability to inform the customers about the ToU tariffs ahead of time with the help of IoT-enabled meters | |
| Auto-switching ability | In the near future, IoT-enabled smart meters could automatically and effortlessly switch energy suppliers for customers | |
| High custumer satisfaction | According to a conducted survey in the UK, 80% of customers indicated that they are happy with smart meters’ functionality [55] | |
| Awareness of deals | This option includes personalized tariffs tailored to a home’s specific energy needs and use | |
| Disadvantages | Requires proactive use for savings | Smart meters do not automatically save you money. Customers must actively engage with the meter and adjust their behavior in response to its data, or their bills will not decrease |
| Smart meters may lose functionality after switching | The majority of smart meters now in use are first-generation devices that frequently “go dumb” or lose functionality once customers switch energy providers | |
| Not available to some consumers on prepayment and time-of-use tariffs | Smart meters are technically available for houses on prepayment and time-of-use tariffs, and while they can make these tariffs easier to monitor and save money with, their use is restricted | |
| Privacy concerns for some customers | Unfortunately, cyber-physical attacks through the breach of information and privacy are increasing day by day |
| Items | Advantages | Challenges |
|---|---|---|
| Massive links among flows for more accurate and fairer DRP control |
|
|
| Fast transfer speed and low latency |
|
|
| Robust security and data privacy |
| Implementing a 5G network slices individual structures |
| High system stability and reliability |
|
|
| Energy-saving and low power consumption |
|
|
| Attack Category | Security Goals | Description | References |
|---|---|---|---|
| Flooding attack | Availability | Deterring users from utilizing resources | [74,75] |
| Denial of service | Availability | Stop serving of user’s request | [76] |
| Jamming channel | Availability | Jamming the network | [77,78] |
| Buffer overflow | Availability and confidentiality | Overwriting the memory of the buffer | [79] |
| False data injection (FDI) | Integrity | Tampering the real data | [80,81] |
| Social engineering | Integrity and confidentiality | Attacking humans instead of machines or networks | [82,83] |
| MITM | Confidentiality | Extracting packet information between sender and receiver | [63,84] |
| Packet sniffing | Confidentiality | Analyzing the packet | [85] |
| Session hijacking | Integrity and confidentiality | Obstructing the user from resources for a particular amount of time | [86] |
| Data manipulation | Integrity | Data tampering | [87] |
| Replay attack | Integrity | Send data continuously | [88,89] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984. https://doi.org/10.3390/en15196984
Goudarzi A, Ghayoor F, Waseem M, Fahad S, Traore I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies. 2022; 15(19):6984. https://doi.org/10.3390/en15196984
Chicago/Turabian StyleGoudarzi, Arman, Farzad Ghayoor, Muhammad Waseem, Shah Fahad, and Issa Traore. 2022. "A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook" Energies 15, no. 19: 6984. https://doi.org/10.3390/en15196984
APA StyleGoudarzi, A., Ghayoor, F., Waseem, M., Fahad, S., & Traore, I. (2022). A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies, 15(19), 6984. https://doi.org/10.3390/en15196984









