A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids
Abstract
:1. Introduction
- Developing a data-driven detection and mitigation framework for the real-time monitoring and detecting malicious system activities in DCMGs.
- The proposed framework can detect not only the presence of a cyber-attack but also the place of the intrusion, which could occur in either the current or voltage sensors of each DG unit, making the mitigation process easier.
- Proposing an online change point detection mechanism, which eliminates the need for a use-defined static or dynamic threshold for the residual analysis of the generated error signal.
- Proposing an online attack mitigation mechanism, which maintains the system performance in an acceptable range without the need for plugging out attacked units during intrusion.
- The proposed framework can distinguish between different types of FDIAs and regular load changes, which is one of the most complicated design challenges for FDI detection and mitigation schemes, which reduces the rate of mis-alarms.
2. ANFIS Design and FDIA Modeling
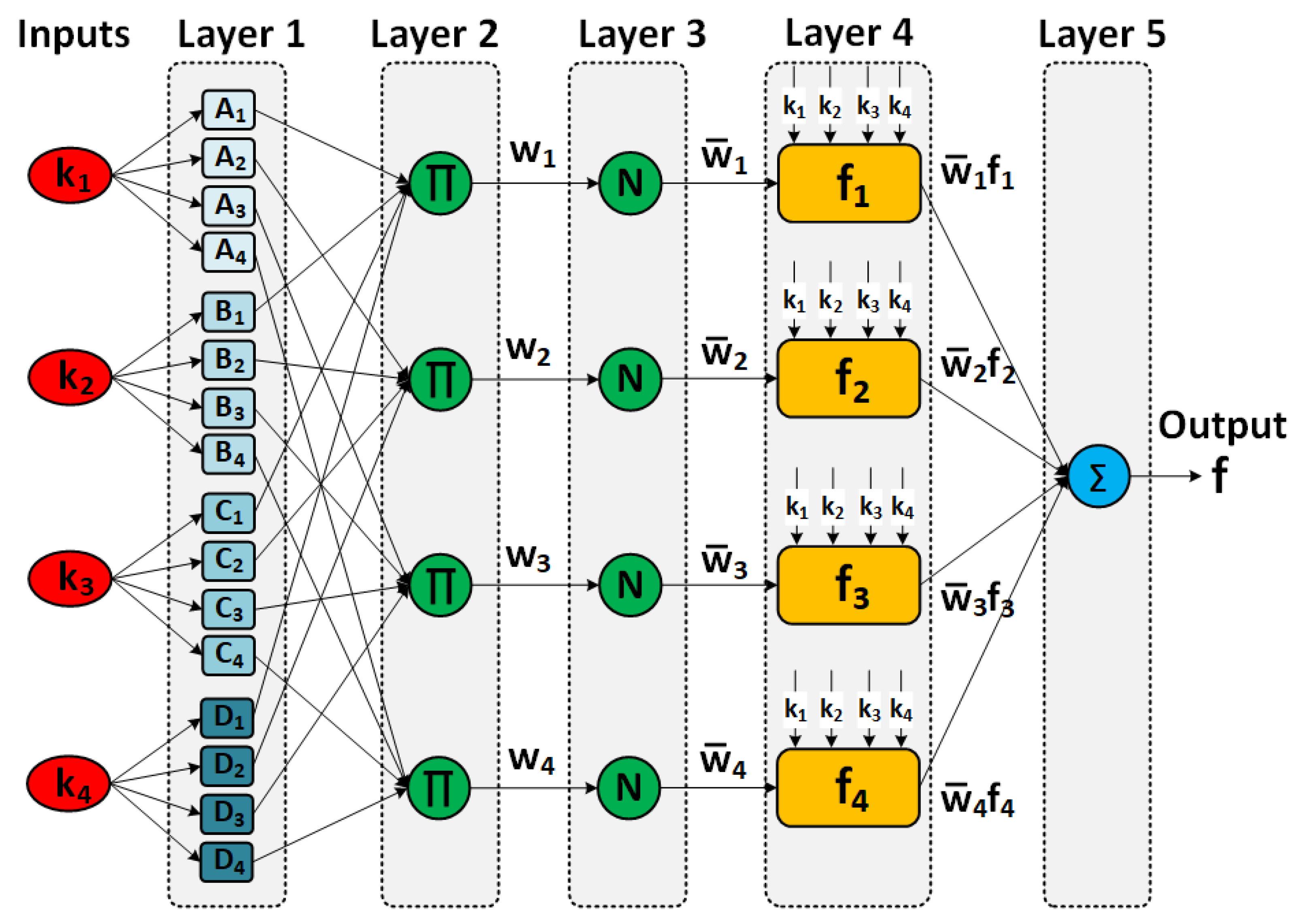
2.1. ANFIS Design
2.2. FDIA Modeling
3. Proposed Method
3.1. Pre-Data Acquisition Phase
3.2. Offline Training Phase
3.3. Online Output Prediction Phase
3.4. Online Change Point Detection Phase
3.5. Mitigation Phase
4. Simulation Results
4.1. Scenario 1: Abrupt Load Change and FDIA
4.2. Scenario 2: Time-Varying FDIA in Transmitted Current Sensor Measurement
4.3. Scenario 3: Hijacking Attack
4.4. Scenario 4: Gaussian Distributed Attack
5. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Nomenclature
| InIndices | |
| j | Index of DG units |
| n | Index of ANFIS inputs |
| l | Index of membership functions |
| Parameters | |
| Al, Bl, Cl | lth Membership functions for each ANFIS inputs |
| Weighting factor | |
| The normalized value of the weighting factor | |
| 𝑃nominal j | Nominal power output of unit jth |
| Place of attack intrusion in voltage sensor for DG unit jth | |
| Place of attack intrusion in current sensor for DG unit jth | |
| The maximum output current of DG unit jth | |
| p | Input-memory order for training sets |
| m | Output-memory order for training sets |
| h | Inputs sample number for training sets |
| ts | Sampling time for training sets |
| Variables | |
| The final crisp output of the defuzzification layer for nth inputs | |
| Measured output voltage signal of DG unit jth | |
| Measured output current signal of DG unit jth | |
| The predicted output voltage of DG unit jth | |
| The predicted output current of DG unit jth | |
| Attack value in the voltage sensor for DG unit jth | |
| Attack value in the current sensor for DG unit jth | |
| Attack value’s approximation in voltage sensor for DG unit jth | |
| Attack value’s approximation in current sensor for DG unit jth | |
| Voltage error signal for DG unit jth | |
| Current error signal for DG unit jth | |
| Amended output voltage signal for DG unit jth | |
| Amended output current signal for DG unit jth | |
| Variable run-length in the BCPD method | |
| Probability distribution in the BCPD method | |
| Hazard function in the BCPD method | |
| Discrete exponential probability distribution | |
| The amplitude of the attack signal | |
| The frequency of the attack signal | |
| DC gain of the attack signal | |
| 𝐿j | Inductance value of the DC/DC converter for DG unit jth |
| 𝐶𝑑𝑐j | Capacitance value of the DC/DC converter for DG unit jth |
| 𝑃𝑙j | Connected local load power for DG unit jth |
| Sets | |
| ANFIS training set for output voltage for DG unit jth | |
| ANFIS training set for output current for DG unit jth | |
| Abbreviations | |
| DCMG | DC Microgrid |
| ACMG | AC Microgrid |
| ANFIS | Adaptive Neuro-Fuzzy Inference System |
| DG | Distributed Generation |
| DD | Data Driven |
| OCPD | Online Change Point Detection |
| RES | Renewable Energy Source |
| PV | Photovoltaic |
| FDIA | False Data Injection attack |
| DoS | Denial of Service |
| MITM | Man in the Middle |
| SCADA | Supervisory Control and Data Acquisition |
| ANN | Artificial Neural Network |
| FIS | Fuzzy Inference System |
| BCPD | Bayesian Change Point Detection |
| VSC | Voltage Sourced Converter |
| MC | Monitoring Center |
| SVE | State Vector Estimation |
| FFNN | Feedforward Neural Network |
| DT | Decision Tree |
References
- Bajwa, A.A.; Mokhlis, H.; Mekhilef, S.; Mubin, M. Enhancing Power System Resilience Leveraging Microgrids: A Review. J. Renew. Sustain. Energy 2019, 11, 035503. [Google Scholar] [CrossRef]
- Dragičević, T.; Lu, X.; Vasquez, J.C.; Guerrero, J.M. DC Microgrids—Part I: A Review of Control Strategies and Stabilization Techniques. IEEE Trans. Power Electron. 2016, 31, 4876–4891. [Google Scholar]
- Dragičević, T.; Lu, X.; Vasquez, J.C.; Guerrero, J.M. DC Microgrids—Part II: A Review of Power Architectures, Applications, and Standardization Issues. IEEE Trans. Power Electron. 2016, 31, 3528–3549. [Google Scholar] [CrossRef] [Green Version]
- Maknouninejad, A.; Qu, Z.; Lewis, F.L.; Davoudi, A. Optimal, Nonlinear, and Distributed Designs of Droop Controls for DC Microgrids. IEEE Trans. Smart Grid 2014, 5, 2508–2516. [Google Scholar] [CrossRef]
- Hao, L.; Ji, J.; Xie, D.; Wang, H.; Li, W.; Asaah, P. Scenario-based unit commitment optimization for power system with large-scale wind power participating in primary frequency regulation. J. Mod. Power Syst. Clean Energy 2020, 8, 1259–1267. [Google Scholar] [CrossRef]
- Rayati, M.; Sheikhi, A.; Ranjbar, A.M.; Sun, W. Optimal Equilibrium Selection of Price-maker Agents in Performance-based Regulation Market. J. Mod. Power Syst. Clean Energy 2020, 10, 204–212. [Google Scholar] [CrossRef]
- Becker, D.J.; Sonnenberg, B.J. DC microgrids in buildings and data centers. In Proceedings of the IEEE 33rd International Telecommunications Energy Conference (INTELEC), Amsterdam, The Netherlands, 9–13 October 2011. [Google Scholar]
- Xu, L.; Guerrero, J.M.; Lashab, A.; Wei, B.; Bazmohammadi, N.; Vasquez, J.; Abusorrah, A.M. A Review of DC Shipboard Microgrids Part I: Power Architectures, Energy Storage and Power Converters. IEEE Trans. Power Electron. 2021, 37, 5155–5172. [Google Scholar] [CrossRef]
- Magne, P.; Nahid-Mobarakeh, B.; Pierfederici, S. Active stabilization of DC microgrids without remote sensors for more electric aircraft. IEEE Trans. Ind. Appl. 2013, 49, 2352–2360. [Google Scholar] [CrossRef]
- Basati, A.; Fakharian, A.; Guererro, J.M. An intelligent droop control for improve voltage regulation and equal power sharing in islanded DC microgrids. In Proceedings of the 2017 5th Iranian Joint Congress on Fuzzy and Intelligent Systems (CFIS), Qazvin, Iran, 7–9 March 2017. [Google Scholar]
- Basati, A.; Wu, J.; Guerrero, J.M.; Vasquez, J.C. Internal Model-based Voltage Control for DC Microgrids Under Unknown External Disturbances. In Proceedings of the 5th International Conference on Smart Energy Systems and Technologies, Eindhoven, The Netherlands, 5–7 September 2022. [Google Scholar]
- Bagheri Rouch, T.; Fakharian, A. Robust Control of Islanded DC Microgrid for Voltage Regulation Based on Polytopic Model and Load Sharing. Iran. J. Sci.Technol. Trans. Electr. Eng. 2022, 46, 171–186. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S. A Distributed Finite-Time Secondary Average Voltage Regulation and Current Sharing Controller for DC Microgrids. IEEE Trans. Smart Grid 2019, 10, 282–292. [Google Scholar] [CrossRef]
- Basati, A.; Menhaj, M.B.; Fakharian, A. GA-based optimal droop control approach to improve voltage regulation and equal power sharing for islanded DC microgrids. In Proceedings of the Electric Power Quality and Supply Reliability (PQ), Tallin, Estonia, 29–31 August 2016. [Google Scholar]
- Shafiee, Q.; Dragičević, T.; Vasquez, J.C.; Guerrero, J.M. Hierarchical control for multiple DC-microgrids clusters. IEEE Trans. Energy Convers. 2014, 29, 922–933. [Google Scholar] [CrossRef]
- Guerrero, J.M.; Chandorkar, M.; Lee, T.-L.; Loh, P.C. Advanced Control Architectures for Intelligent Microgrids—Part I: Decentralized and Hierarchical Control. IEEE Trans. Ind. Electron. 2013, 60, 1254–1262. [Google Scholar] [CrossRef] [Green Version]
- Tan, S.; Guerrero, J.M.; Xie, P.; Han, R.; Vasquez, J.C. Brief Survey on Attack Detection Methods for Cyber-Physical Systems. IEEE Syst. J. 2020, 14, 5329–5339. [Google Scholar] [CrossRef]
- Tan, S.; Xie, P.; Guerrero, M.J.; Vasquez, C.J. False Data Injection Cyber-Attacks Detection for Multiple DC Microgrid Clusters. Appl. Energy 2022, 310, 118425. [Google Scholar] [CrossRef]
- Habibi, M.R.; Sahoo, S.; Rivera, S.; Dragičević, T.; Blaabjerg, F. Decentralized Coordinated Cyberattack Detection and Mitigation Strategy in DC Microgrids Based on Artificial Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4629–4638. [Google Scholar] [CrossRef]
- Sahoo, S.; Mishra, S.; Peng, J.C.; Dragičević, T. A Stealth Cyber-Attack Detection Strategy for DC Microgrids. IEEE Trans. Power Electron. 2019, 34, 8162–8174. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.; Peng, Y.; Wang, B.; Yao, S.; Liu, Z. Review on cyber-physical systems. IEEE/CAA J. Autom. Sin. 2017, 4, 27–40. [Google Scholar] [CrossRef]
- Hu, S.; Yuan, P.; Yue, D.; Dou, C.; Cheng, Z.; Zhang, Y. Attack-Resilient Event-Triggered Controller Design of DC Microgrids Under DoS Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2020, 67, 699–710. [Google Scholar] [CrossRef]
- Sahoo, S.; Peng, J.C.; Mishra, S.; Dragičević, T. Distributed Screening of Hijacking Attacks in DC Microgrids. IEEE Trans. Power Electron. 2020, 35, 7574–7582. [Google Scholar] [CrossRef]
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems: Designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control. Syst. 2015, 35, 93–109. [Google Scholar]
- Irita, T.; Namerikawa, T. Detection of replay attack on smart grid with code signal and bargaining game. In Proceedings of the American Control Conference (ACC), Seattle, WA, USA, 24–26 May 2017. [Google Scholar]
- Yang, Y.; Wei, X.; Xu, R.; Peng, L.; Zhang, L.; Ge, L. Man-in-the-Middle Attack Detection and Localization Based on Cross-Layer Location Consistency. IEEE Access 2020, 8, 103860–103874. [Google Scholar] [CrossRef]
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Multilayer Resilience Paradigm Against Cyber Attacks in DC Microgrids. IEEE Trans. Power Electron. 2021, 36, 2522–2532. [Google Scholar] [CrossRef]
- Ahmed, M.; Pathan, A.S. False data injection attack (FDIA): An overview and new metrics for fair evaluation of its countermeasure. Complex Adapt. Syst. Model. 2020, 8, 4. [Google Scholar] [CrossRef] [Green Version]
- Hao, J.; Kang, E.; Sun, J.; Wang, Z.; Meng, Z.; Li, X.; Ming, Z. An Adaptive Markov Strategy for Defending Smart Grid False Data Injection From Malicious Attackers. IEEE Trans. Smart Grid 2018, 9, 2398–2408. [Google Scholar] [CrossRef]
- Chaojun, G.; Jirutitijaroen, P.; Motani, M. Detecting False Data Injection Attacks in AC State Estimation. IEEE Trans. Smart Grid 2015, 6, 2476–2483. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine Learning Methods for Attack Detection in the Smart Grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wilson, D.; Tang, Y.; Yan, J.; Lu, Z. Deep Learning-Aided Cyber-Attack Detection in Power Transmission Systems. In Proceedings of the IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–9 August 2018; pp. 1–5. [Google Scholar]
- He, Y.; Mendis, G.J.; Wei, J. Real-Time Detection of False Data Injection Attacks in Smart Grid: A Deep Learning-Based Intelligent Mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičcevi’c, T.; Blaabjerg, F. Detection of False Data Injection Cyber-Attacks in DC Microgrids based on Recurrent Neural Networks. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 9, 5294–5310. [Google Scholar] [CrossRef]
- Bayati, N.; Hajizadeh, A.; Soltani, M. Blockchain-based protection schemes of DC microgrids. In Blockchain-Based Smart Grids; Academic Press: Cambridge, MA, USA, 2020; pp. 195–214. [Google Scholar]
- Basati, A.; Bazmohammadi, N.; Guererro, J.M.; Vasquez, J.C. Real-Time Estimation in Cyber Attack Detection and Mitigation Framework for DC Microgrids. In Proceedings of the 2022 Interdisciplinary Conference on Mechanics, Computers and Electrics (ICMECE), Barcelona, Spain, 6–7 October 2022. [Google Scholar]
- Jang, J.R. ANFIS: Adaptive-network-based fuzzy inference system. IEEE Trans. Syst. Man Cybern. 1993, 23, 665–685. [Google Scholar] [CrossRef]
- Zhang, J.; Sahoo, S.; Peng, J.C.-H.; Blaabjerg, F. Mitigating Concurrent False Data Injection Attacks in Cooperative DC Microgrids. IEEE Trans. Power Electron. 2021, 36, 9637–9647. [Google Scholar] [CrossRef]
- Adams, R.P.; MacKay, D.J. Bayesian online changepoint detection. arXiv 2007, arXiv:0710.3742. [Google Scholar]
- Aminikhanghahi, S.; Cook, D.J. A survey of methods for time series change point detection. Knowl. Inf. Syst. 2017, 51, 339–367. [Google Scholar] [CrossRef] [PubMed]






| DGs | DG 1 | DG 2 | DG 3 | DG 4 |
| 𝑃nominal1,2 ≃ 4.7 kW | 𝑃nominal3,4 ≃ 3.1 kW | |||
| Converter | 𝐿𝑖 = 300 μH, 𝐶𝑑𝑐𝑖 = 250 μF | |||
| Line | T12 | T23 | T34 | T14 |
| R = 0.5 Ω L = 80 μH | R = 2.5 Ω L = 85 μH | R = 3.3 Ω L = 95 μH | R = 2.3 Ω L = 70 μH | |
| Load | Laod 1 | Laod 2 | Laod 3 | Laod 4 |
| 𝑃𝑙1 ≃ 3.4 kW | 𝑃𝑙2 ≃ 3.7 kW | 𝑃𝑙3 ≃ 2.9 kW | 𝑃𝑙4 ≃ 3.1 kW | |
| Scenario No. | Place of Intrusion | Type of Attack (Sine Waves 1, 2, 3 and Gaussian 4) | Period of Attack |
|---|---|---|---|
| 1 | t = [5.1, 7.3] s | ||
| 2 | t = [4.0, 6.0] s | ||
| 3 | t = [5.0, 7.0] s | ||
| 4 | t = [3.0, 5.5] s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Basati, A.; Guerrero, J.M.; Vasquez, J.C.; Bazmohammadi, N.; Golestan, S. A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids. Energies 2022, 15, 8539. https://doi.org/10.3390/en15228539
Basati A, Guerrero JM, Vasquez JC, Bazmohammadi N, Golestan S. A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids. Energies. 2022; 15(22):8539. https://doi.org/10.3390/en15228539
Chicago/Turabian StyleBasati, Amir, Josep M. Guerrero, Juan C. Vasquez, Najmeh Bazmohammadi, and Saeed Golestan. 2022. "A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids" Energies 15, no. 22: 8539. https://doi.org/10.3390/en15228539






