Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids: Techniques, Design Challenges, and Future Trends
Abstract
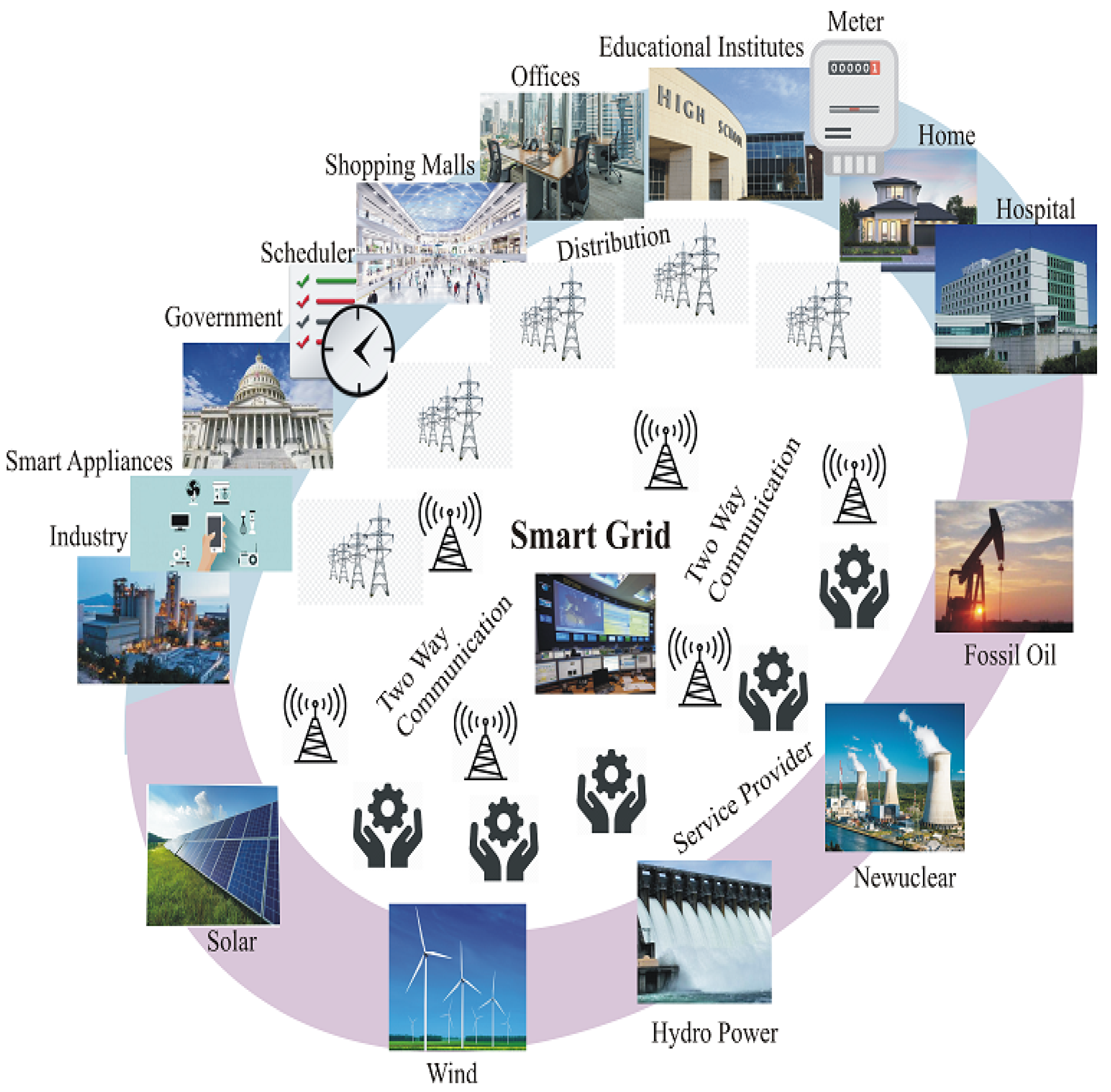
:1. Introduction
- We identify the key security and performance characteristics of SDA schemes in SGs that enable users to share their data with SG operators with confidence.
- A detailed taxonomy of FTSDA schemes in SG schemes is provided.
- We provide a discussion on how FTSDA can be achieved by using asymmetric and symmetric cryptography techniques.
- We identify future directions and trends in SDA that should be focused on by the research community.
2. Requirements
2.1. Fault Tolerance
- The DCC should be efficient and capable of decrypting the aggregation of working SMs. If there are some faulty SMs, this has no big impact on the overall usage calculation.
- Although the DCCs (servers) are robust and reliable, sometimes, they malfunction or shut down to protect against certain threats.
- Due to the low cost and running in an unprotected environment, SMs are prone to failures. They are also concerns for communicating over an unreliable network channel, and sometimes, they may not forward the user’s data. In order to properly execute the real-time data monitoring and analysis activity at the grid level, the metering system should be able to aggregate the measurements of the remaining functional SMs when one or more of them fail to report.
2.2. Security Requirement
- Integrity: Integrity provides assurance that the data message has not been altered or modified without proper authorization. Without integrity checks, false data may be injected, which leads to incorrect information gathering at the CCC. As a result, the CCC may make the wrong decisions based on the wrong information regarding demand and response, forecasting, and billing [6,17].
- Authentication: During data submission, the SM, FN, and CCC collaborate to receive data packets. Before accepting the data, the data’s source must be validated. The data packet must be rejected if it originates from a malicious source. Authentication can be performed via a digital signature, digital certificate, MAC, or any other recognized identification method [7,8,12,18,19].
- Privacy: The privacy of SG users is important during all the communications. If it is compromised, an adversary can observe an individual’s electricity usage and infer sensitive information about his/her personal lifestyle [3,14,15,16,20]. It reveals information such as when he/she is not available at home or how much power the customer will use in the upcoming period.
- Anonymity: If metering data need to be associated with a particular customer for billing or other purposes, they need to be anonymized before being released to other parties. From these data, the adversary may be unable to find the real identity of an SM [21].
- Differential privacy: Differential privacy is a technique that ensures that the removal or addition of a single item in a statistical database has no effect on the outcome of any query on that database. Differential privacy is a measure of the trade-off between the accuracy of aggregated data and the likelihood of identifying individual data contributions within the aggregate. It is achieved by adding appropriate noise to metering data through a Laplace/Geometric distribution [9].
2.3. Performance Requirements
- Computational cost: In the SG, the computational overhead is distributed across four stages: the individual users (SM), the aggregator (gateway), the CCC, and the TA [3]. Several modular operations are carried out during the encryption and decryption processes. The schemes based on public key infrastructure (PKI) are computationally intensive [6,8,9,16,17,22]. The computational cost also varies depending on how many times SM data are submitted, and aggregation takes place at the GW level.
- Communication overhead: In the SG, data packets are shared between the SM, GW/FN, CCC, and TA. The cost of communication varies according to the number of messages/data packets shared and their size [23]. Security concerns must be addressed in order to avoid interfering with and interrupting data packets in transit or at rest [24]. Concerns about privacy and communication costs could be greatly reduced if the data aggregation process is used on consumption data [11].
- FT: Any component have failed in the SG architecture needs to be found as quickly as is feasible and restored/repaired without causing a significant loss of service or other issues.
- Support temporal aggregation: Temporal aggregation relates to the total electricity usage for a single smart meter in different time periods. It is required for billing purposes [13].
- Support random addition and removal of SMs: SMs can be added or removed as per the requirement. If a new SM is installed, it must be configured before it can be included in the system for the purposes of capturing metering data and billing. An appropriate procedure must be in place to remove the configuration if any SM is damaged or removed. If necessary, an SM can also change areas due to relocation. When the SM is relocated, the appropriate gateway needs to be modified [8,25].
- Robustness: In the SG, when the SM submits its data to the CCC, many cryptographic operations are required at various stages. The data aggregation technique must be robust in terms of security properties, storage costs, computational costs, and fault tolerance.
- Efficiency: In the SG, there is much communication between SM components. Data transmission through those components must be secured using a variety of security techniques, such as public key cryptographic techniques and homomorphic functions. The use of security items at different stages must be efficient and use fewer resources in terms of storage and processing time.
- Storage cost: Storage cost is related to storing the values of the various cryptographic operations generated during communication between different entities. Key length, signature, and hash values have a big impact on the Smart Grid because the SM has limited resources to store data [26].
3. Security Attacks
- Communication attack: This attack is primarily carried out on the SG communication network (Wi-Fi/ZigBee) in order to disrupt or overload communication between the SM and FN/GW and to postpone decision-making activities at the CCC level [6,8,17,19,29,30,31,32]. An adversary can also observe the SG component’s communication to read usage data [7,33].
- Man-in-the-middle (MITM) attack: This is an active type of attack and typically occurs when a malicious user intercepts the communication between SG components. The prime objective is to observe the traffic flow to collect electricity usage preferences and infer customers’ routines and other personal information [17,29].
- Dictionary attack: In this attack, an adversary tries to guess the encryption keys by observing and comparing all packets travelling from the SM to the CCC [39].
- Collusive attack: In the SG, the CCC and FN are considered honest-but-curious entities. There is a possibility that they may collude secretly to deceive some SMs. Therefore, protection is required so that if the FN and CC are colluding, they cannot obtain any data usage information about other SMs. A group of SMs can collude, drop their readings, and steal energy [40].
- Malicious data mining attack: Anonymous data can be mined for information using the controllable property of the group signature in the SG, endangering the privacy of the user [41].
- Re-identification attack: In this attack, an adversary observes the customer’s physical presence, records the power usage indicators (which appliances are on or off), and compares these data with statistical information that is readily accessible to the public. These data are used to assess the energy usage level at each given moment [42].
- Privacy divulging: An adversary may jeopardize residential users’ privacy by listening in on communication data from residential users travelling towards the GW/FN and CCC [22].
- False data injection, fake, bad attack: Intruders may attempt to compromise the SM and inject false information to impact the power grid’s assessment status. In the SG, the CCC is treated as fully trusted, but in reality, it may share the user’s consumption data with unauthorized and untrusted entities [43].
- Eclipse attack: The eclipse attack is also related to peer-to-peer distributed networks. In this type of attack, the colluding gateways conspire to alter the construction of the aggregation trees by inducing the honest gateways to select them as their neighbors, to mediate most of the aggregation requests specified by the EEs.
- Distributed denial-of-service (DoS) Attack: This targets the AMI communication network to sabotage the communication flow between the wide area network (WAN) and neighborhood area network (NAN) [44].
- Data privacy attack: Data privacy attack is related to observing or sharing customer data with malicious parties without their consent. Protection needs to be provided if external attackers, the CCC, and the FN/GW try to infer any knowledge about users from their usage data [43].
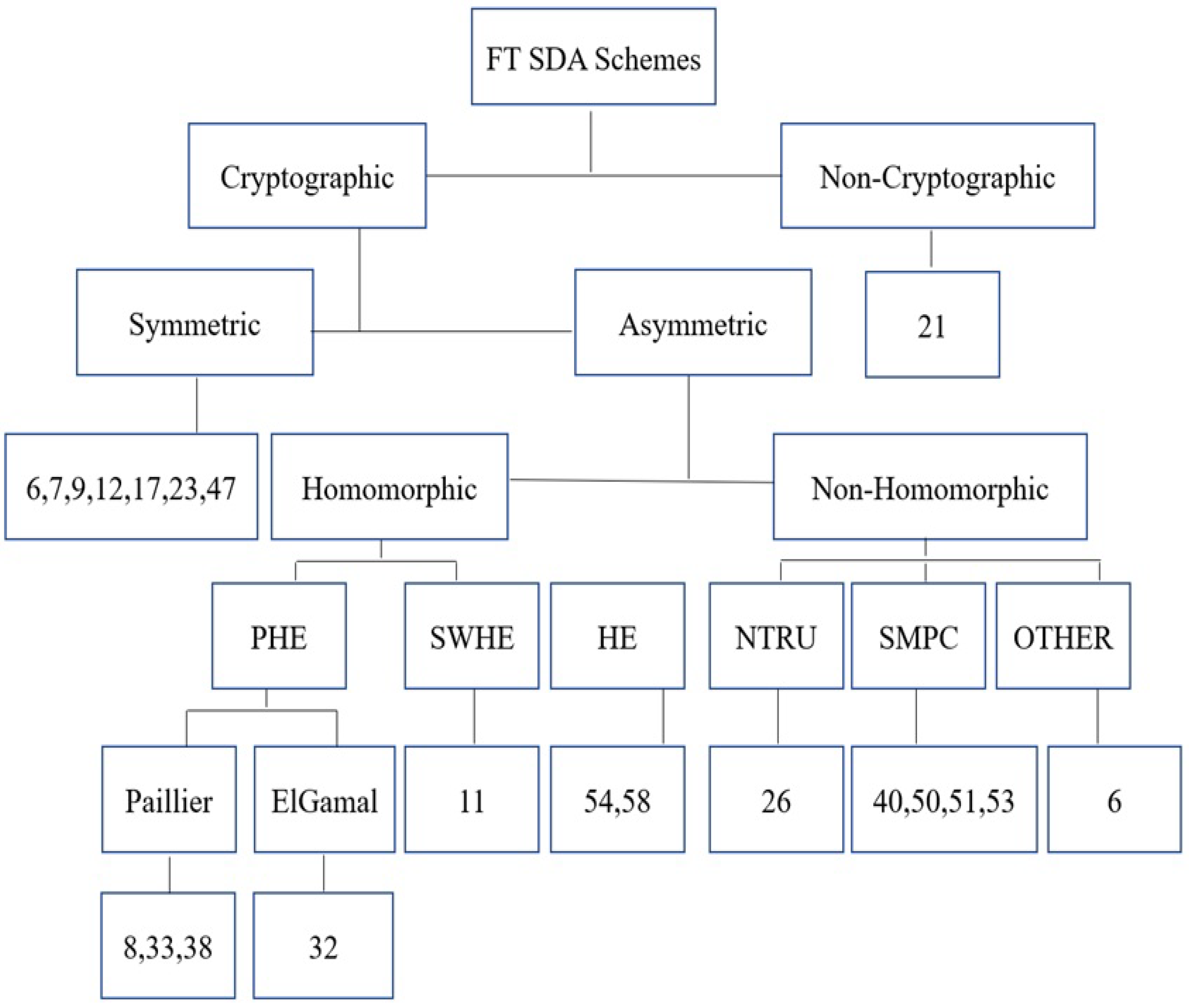
4. Fault-Tolerant SDA Schemes in SGs
Cryptography Based FT SDA Schemes
5. Comparative Analysis of SDA with FT Schemes
5.1. Evaluation with Respect to Security Properties
- Confidentiality: The authors in [15] used a private stream aggregation (PSA) scheme to encrypt smart metering data. In the scheme in [17], ECC was used for key sharing between the data aggregator and collector. Scheme [22] uses pairwise private stream aggregation (PPSA) to encrypt smart metering data. In the scheme in [12], confidentiality was achieved through private key encryption. To support confidentiality, the authors of the schemes in [8,33] used Paillier encryption. In the schemes in [20,34], encryption is performed through the BGN cryptosystem. The authors of [30] used modular-based additive encryption to generate ciphertexts. In the scheme in [31], private stream aggregation is used to set up noisy encryption.
- Differential privacy: To support DP, the scheme presented in [9] uses a randomized function to add noise to aggregated data before submitting them to the untrusted aggregator. The schemes in [7,9,34] use a geometric distribution to add noise at the GW level to achieve DP. The authors of the schemes in [19,20,30] added noise to SM data through a Laplace distribution and supported DP. The authors in [12] used the binomial distribution to add noise to SM data.
- Authenticity: The authors in [17] used the Needham–Schroeder protocol for SM and GW/FN authentication. The scheme in [6] uses the BLS signature scheme to authenticate SMs. A tree-based structure is used to verify each packet from an SM. In the scheme in [20], the Diffie–Hellmann key exchange protocol is used for authentication.
- Availability: To achieve FT, the schemes mentioned in [15,19] use the quad tree. The authors in [7] introduced the auxiliary text to cater to faulty SM identification. In [12], the authors divided each SM into two groups of two members. If one of them fails, the decryption activity will fail. The working SM will be moved to another group where its member is working. The faulty SM will be taken care of accordingly. In the scheme in [8], if some servers at the CCC are compromised, the CCC can perform the decryption activity for the remaining servers. The scheme discussed in [20] is more robust against any rational number of malfunctioning SMs. Future ciphertext was used to handle FT in [30]. The scheme proposed in [34] supports both the CCC and SM failure scenarios. The scheme described in [33] provides FT via a substitution strategy.
- Protection against malware: The scheme of [20] supports security against internal malware attacks. If the malware can infect the CCC, it can only reveal the aggregated value, but could not reveal individual users’ data.
- Malicious data consumer: Data consumers were deemed malicious in the scheme presented in [38]. Data security was achieved using the freshness key.
| Ref. | SR1 | SR2 | SR3 | SR4 | SR5 | SR6 |
|---|---|---|---|---|---|---|
| [15] | √ | ✗ | ✗ | √ | √ | ✗ |
| [17] | √ | ✗ | ✗ | √ | ✗ | ✗ |
| [6] | ✗ | ✗ | ✗ | √ | √ | ✗ |
| [38] | ✗ | √ | ✗ | ✗ | ✗ | √ |
| [9] | ✗ | √ | ✗ | ✗ | √ | ✗ |
| [22] | √ | √ | √ | √ | √ | ✗ |
| [7] | √ | √ | √ | √ | √ | ✗ |
| [19] | √ | √ | √ | √ | √ | ✗ |
| [12] | √ | √ | ✗ | ✗ | √ | ✗ |
| [8] | √ | √ | √ | √ | √ | ✗ |
| [20] | √ | √ | ✗ | ✗ | √ | √ |
| [30] | √ | √ | ✗ | ✗ | √ | √ |
| [31] | √ | √ | ✗ | ✗ | ✗ | ✗ |
| [34] | √ | √ | ✗ | ✗ | √ | ✗ |
| [33] | √ | ✗ | ✗ | ✗ | √ | ✗ |
5.2. Evaluation with Respect to Performance Properties
- Computational cost: In existing state-of-the-art schemes in SGs, the computational cost is measured in terms of the number of cryptographic operations or the time required to perform the encryption and decryption activities. In the schemes in [15,19], encryption takes seconds using an elliptic curve for the complete depth of the tree. In the scheme in [9], the encryption and decryption costs are approximately 9 s for 1000 SMs and , respectively. In the scheme in [9], for the best case, if there are no failing meters, decryption will be performed in one round, and in the worst case, rounds will be required to perform decryption. In the scheme in [7], most of the computations are performed at the aggregator level. At the SM level, encryption requires 1 multiplication, 3 hash calculations, and 4 exponential operations. In the scheme in [12], cryptographic operations consist of 1 hash function calculation, 2 modular exponentiations, and a 1 multiplication operation. In the scheme in [34], encryption for a single user requires 2 modular exponential operations and 1 modular multiplication. In all schemes, The modular exponentiation operation takes most of the execution time compared to other operations.
- Communication overhead: In the scheme in [6], the authors claimed that, through signature aggregation, the communication costs are reduced by 50% during message authentication. The authors of [9] claimed that the total communication cost of their scheme was O(nlogn). In the scheme in [22], the SM submits its encrypted data to the CCC in a single round of communication, and the total communication cost is . In the scheme in [7], communication is involved when data move from the SM to the cluster head, from the cluster head to the GW, and from the GW to the CCC. For one cluster, the communication cost is 1685 bits, and for the cluster to the GW, the overall communications cost is bits for w pairs of communication. In the scheme in [12], each SM has to send its encrypted data to the CCC in a single round of communication. The total communication in the SG is . In the scheme in [8], the communication overhead is divided into two parts: at the SM level and the overall communication. For user-level communication, if for Paillier cryptosystem, parameter k is considered as 512 bits, the size of the user report is 1024 bits for one-time report submission to the GW. For overall communication, the GW collects data from all n users, aggregates them into one single value, and submits them to the CCC. In the scheme in [31], with a cryptographic setup, the encryption operation consists of a hash function using SHA-256, 1 multiplication, and 2 modular exponentiation operations.
- FT: The authors of the scheme in [15,19] supported detecting malfunctioning SMs by scanning the complete tree structure. The working SM blocks are separated from malfunctioning users’ blocks. In the scheme in [16], the authors used a cloud model for ensuring redundancy in case of component failure during data processing. The authors of the scheme in [9] used a binary tree approach to find failed SMs. In the scheme in [22], FT is achieved through a pairing mechanism. If any SM fails to submit data, the remaining working SMS are moved to another working pair. In the scheme in [7], FT is achieved through the substitution of subtle strings. Each SM has to add this subtle string of text to its data. During decryption, SMs that have submitted this string are considered working SMs. The scheme presented in [8] supports FT through replica servers at the CCC. If one of the servers is compromised, the others can keep the setup working. In the scheme in [30], FT is achieved through the addition of future ciphertext to the current round of data. In this scheme, all SMs are paired. During data collection, the aggregator broadcasts the list of failed SMs who have not reported their data. In response to this, the working SM of a pair submits data on behalf of the faulty SM.
- Differential privacy: In the schemes in [15,19], noise is added from a geometric distribution during data report generation by the user. The authors of the scheme in [38] claimed that they achieved differential privacy by introducing an O(1) error in the accuracy of the aggregation activity when there are failed SMs. The authors of the scheme in [9] used a geometric distribution to add noise to perturb the metering data. During the decryption process, if all noises cancel each other, the final estimate contains a noise of roughly O(logn). In the scheme in [7], to achieve differential privacy, noise is added from a geometric distribution to aggregated data at the gateway level. The authors calculated the root-mean-squared error (RMSE) for all the SMs and the malfunctioning SMs and claimed that their proposed scheme achieved better utility with lower errors. The binomial distribution is used in the scheme presented in [12] to achieve differential privacy. Every SM perturbs its data with generated noise and encrypts them with its private key.
- Support dynamic meters’ addition/removal: The scheme presented in [9] supports dynamic joiners and leavers without rekeying operations. In the scheme in [12], when a new SM joins, it will contact the KMC. The KMC will place the SM in a specific group based on its properties and assign it a private key. The CCC is also updated to extend the decryption activity due to the addition of a new SM. In the scheme in [20], as only the TA knows the private key, when a new user joins, the TA generates its private key and updates the secret polynomial. Similarly, when an existing user leaves, its secret key is removed. In the scheme in [30], when the SM leaves, the GW needs to be informed. The GW will broadcast its ID to all SMs. The leaving decision will impact two types of SMs: the one that chose the leaving SM as its partner and the other who was chosen by the leaving SM as its partner.
- Storage cost: In the scheme in [12], the number of keys stored depends on the number of SMs, the rounds of random grouping, and the size of each group. In the scheme in [30], the authors added future ciphertext in addition to current metering data to support FT. The authors claimed that the additional storage required to store future ciphertext is very small. However, for a small number of users, this can be ignored, but when the number of users increases to a large number, this brings large storage requirements to the grid. Patients in the scheme cited in S31 can visit mobile hospitals and are easily added to the system. Similarly, if a patient dies, his/her information can be removed.
6. Design Challenges and Future Trends
- An efficient privacy-preserving aggregation protocol with enhanced error detection support should be designed [22,32,58]. Schemes shall be designed in such a way that they support the tracing of malfunctioning SMs. If malfunctioning SMs are present, they can be isolated in such a way that their absence has less impact on the data estimation at the CCC level. The impact of differential privacy noise addition should be lessened if large numbers of SMs are compromised or not participating in the aggregation protocol.
- A scheme is required that can efficiently identify data forgery attacks and support the generation of provenance records to trace abnormal footprints [8,59,60]. The should be support for rich statistics [8,31]. A fault-tolerant solution in the SG that supports grace degradation if failures occur in SMs, controllers, or communication mediums should be designed.
- The SG’s internal infrastructure’s security needs to be enhanced against physical or cyberattacks. Redundancy for critical components needs to be ensured [2].
- A dynamic pricing model in SGs should be designed and implemented [62]. Based on the usage data, customers can be categorized into different categories, such as gold, silver, and bronze. Incentives can be offered on the basis of usage data. Furthermore, customers can also generate electricity; therefore, a pricing model can be developed so that customers can sell their extra electricity in a competitive manner.
- Schemes based on advanced machine learning techniques to detect anomalies in the SM readings should be designed [65].
Funding
Data Availability Statement
Conflicts of Interest
References
- Farhangi, H. The path of the Smart Grid. IEEE Power Energy Mag. 2009, 8, 18–28. [Google Scholar] [CrossRef]
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An efficient and privacy-preserving aggregation scheme for secure Smart Grid communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]
- Li, X.; Liang, X.; Lu, R.; Shen, X.; Lin, X.; Zhu, H. Securing Smart Grid: Cyber attacks, countermeasures, and challenges. IEEE Commun. Mag. 2012, 50, 38–45. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the Smart Grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. A systematic review of data protection and privacy preservation schemes for Smart Grid communications. Sustain. Cities Soc. 2018, 38, 806–835. [Google Scholar] [CrossRef]
- Li, D.; Aung, Z.; Williams, J.R.; Sanchez, A. Efficient authentication scheme for data aggregation in Smart Grid with fault tolerance and fault diagnosis. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012; pp. 1–8. [Google Scholar]
- Bao, H.; Lu, R. A lightweight data aggregation scheme achieving privacy preservation and data integrity with differential privacy and fault tolerance. Peer-to-Peer Netw. Appl. 2017, 10, 106–121. [Google Scholar] [CrossRef]
- Chen, L.; Lu, R.; Cao, Z. PDAFT: A privacy-preserving data aggregation scheme with fault tolerance for Smart Grid communications. Peer-to-Peer Netw. Appl. 2015, 8, 1122–1132. [Google Scholar] [CrossRef]
- Chan, T.H.H.; Shi, E.; Song, D. Privacy-preserving stream aggregation with fault tolerance. In Proceedings of the International Conference on Financial Cryptography and Data Security; Springer: Cham, Switzerland, 2012; pp. 200–214. [Google Scholar]
- Won, J.; Ma, C.Y.; Yau, D.K.; Rao, N.S. Privacy-assured aggregation protocol for smart metering: A proactive fault-tolerant approach. IEEE/ACM Trans. Netw. 2015, 24, 1661–1674. [Google Scholar] [CrossRef]
- Khan, H.M.; Khan, A.; Jabeen, F.; Rahman, A.U. Privacy preserving data aggregation with fault tolerance in fog-enabled Smart Grids. Sustain. Cities Soc. 2021, 64, 102522. [Google Scholar] [CrossRef]
- Shi, Z.; Sun, R.; Lu, R.; Chen, L.; Chen, J.; Shen, X.S. Diverse grouping-based aggregation protocol with error detection for Smart Grid communications. IEEE Trans. Smart Grid 2015, 6, 2856–2868. [Google Scholar] [CrossRef]
- Dwork, C. Differential privacy: A survey of results. In Proceedings of the International Conference on Theory and Applications of Models of Computation; Springer: Cham, Switzerland, 2008; pp. 1–19. [Google Scholar]
- Sridhar, S.; Hahn, A.; Govindarasu, M. Cyber–physical system security for the electric power grid. Proc. IEEE 2011, 100, 210–224. [Google Scholar] [CrossRef]
- Lu, M.; Shi, Z.; Lu, R.; Sun, R.; Shen, X.S. PPPA: A practical privacy-preserving aggregation scheme for smart grid communications. In Proceedings of the 2013 IEEE/CIC International Conference on Communications in China (ICCC), Xi’an, China, 12–14 August 2013; pp. 692–697. [Google Scholar]
- Rusitschka, S.; Eger, K.; Gerdes, C. Smart grid data cloud: A model for utilizing cloud computing in the Smart Grid domain. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 483–488. [Google Scholar]
- Wu, D.; Zhou, C. Fault-tolerant and scalable key management for Smart Grid. IEEE Trans. Smart Grid 2011, 2, 375–381. [Google Scholar] [CrossRef]
- Alamatsaz, N.; Boustani, A.; Jadliwala, M.; Namboodiri, V. Agsec: Secure and efficient cdma-based aggregation for smart metering systems. In Proceedings of the 2014 IEEE 11th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2014; pp. 489–494. [Google Scholar]
- Bao, H.; Lu, R. Ddpft: Secure data aggregation scheme with differential privacy and fault tolerance. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7240–7245. [Google Scholar]
- Bao, H.; Lu, R. A new differentially private data aggregation with fault tolerance for Smart Grid communications. IEEE Internet Things J. 2015, 2, 248–258. [Google Scholar] [CrossRef]
- Yang, L.; Li, F. Detecting false data injection in Smart Grid in-network aggregation. In Proceedings of the 2013 IEEE International Conference on Smart Grid Communications (SmartGridComm), Vancouver, BC, Canada, 21–24 October 2013; pp. 408–413. [Google Scholar]
- Sun, R.; Shi, Z.; Lu, R.; Lu, M.; Shen, X. APED: An efficient aggregation protocol with error detection for Smart Grid communications. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 432–437. [Google Scholar]
- Saleem, A.; Khan, A.; Malik, S.U.R.; Pervaiz, H.; Malik, H.; Alam, M.; Jindal, A. FESDA: Fog-enabled secure data aggregation in Smart Grid IoT network. IEEE Internet Things J. 2019, 7, 6132–6142. [Google Scholar] [CrossRef] [Green Version]
- Jung, T.; Li, X.Y.; Wan, M. Collusion-tolerable privacy-preserving sum and product calculation without secure channel. IEEE Trans. Dependable Secur. Comput. 2014, 12, 45–57. [Google Scholar] [CrossRef] [Green Version]
- Nitaj, A. Cryptanalysis of NTRU with Two Public Keys. Cryptology ePrint Archive 2011. Available online: https://eprint.iacr.org/2011/477 (accessed on 22 October 2022).
- Saxena, N.; Choi, B.J. State of the art authentication, access control, and secure integration in Smart Grid. Energies 2015, 8, 11883–11915. [Google Scholar] [CrossRef] [Green Version]
- Lyu, L.; Nandakumar, K.; Rubinstein, B.; Jin, J.; Bedo, J.; Palaniswami, M. PPFA: Privacy preserving fog-enabled aggregation in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 3733–3744. [Google Scholar] [CrossRef]
- Erkin, Z.; Tsudik, G. Private computation of spatial and temporal power consumption with smart meters. In Proceedings of the International Conference on Applied Cryptography and Network Security; Springer: Cham, Switzerland, 2012; pp. 561–577. [Google Scholar]
- Fu, S.; Ma, J.; Li, H.; Jiang, Q. A robust and privacy-preserving aggregation scheme for secure smart grid communications in digital communities. Secur. Commun. Netw. 2016, 9, 2779–2788. [Google Scholar] [CrossRef]
- Won, J.; Ma, C.Y.; Yau, D.K.; Rao, N.S. Proactive fault-tolerant aggregation protocol for privacy-assured smart metering. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 2804–2812. [Google Scholar]
- Shi, R.; Chow, R.; Chan, T.H.H. Privacy-Preserving Aggregation of Time-Series Data. European Patent Office EP2485430B1, 14 September 2016. [Google Scholar]
- Ni, J.; Zhang, K.; Alharbi, K.; Lin, X.; Zhang, N.; Shen, X.S. Differentially private smart metering with fault tolerance and range-based filtering. IEEE Trans. Smart Grid 2017, 8, 2483–2493. [Google Scholar] [CrossRef]
- Guan, Z.; Si, G.; Du, X.; Liu, P. Protecting User Privacy Based on Secret Sharing with Error Tolerance for Big Data in Smart Grid. arXiv 2018, arXiv:1811.06918. [Google Scholar]
- Han, S.; Zhao, S.; Li, Q.; Ju, C.H.; Zhou, W. PPM-HDA: Privacy-preserving and multifunctional health data aggregation with fault tolerance. IEEE Trans. Inf. Forensics Secur. 2015, 11, 1940–1955. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J. A survey on privacy-preserving schemes for Smart Grid communications. arXiv 2016, arXiv:1611.07722. [Google Scholar]
- Hoepman, J.H. Privacy friendly aggregation of smart meter readings, even when meters crash. In Proceedings of the 2nd Workshop on Cyber-Physical Security and Resilience in Smart Grids, Pittsburgh, PA, USA, 21 April 2017; pp. 3–7. [Google Scholar]
- Chen, J.; Ma, H.; Zhao, D. Private data aggregation with integrity assurance and fault tolerance for mobile crowd-sensing. Wirel. Netw. 2017, 23, 131–144. [Google Scholar] [CrossRef]
- Jawurek, M.; Kerschbaum, F. Fault-tolerant privacy-preserving statistics. In Proceedings of the International Symposium on Privacy Enhancing Technologies Symposium; Springer: Cham, Switzerland, 2012; pp. 221–238. [Google Scholar]
- Bayat, M.; Atashgah, M.B.; Aref, M.R. A secure and efficient chaotic maps based authenticated key-exchange protocol for Smart Grid. Wirel. Pers. Commun. 2017, 97, 2551–2579. [Google Scholar] [CrossRef]
- Khan, H.M.; Khan, A.; Jabeen, F.; Anjum, A.; Jeon, G. Fog-enabled secure multiparty computation based aggregation scheme in Smart Grid. Comput. Electr. Eng. 2021, 94, 107358. [Google Scholar] [CrossRef]
- Shen, H.; Liu, Y.; Xia, Z.; Zhang, M. An efficient aggregation scheme resisting on malicious data mining attacks for Smart Grid. Inf. Sci. 2020, 526, 289–300. [Google Scholar] [CrossRef]
- Yang, L.; Xue, H.; Li, F. Privacy-preserving data sharing in Smart Grid systems. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 878–883. [Google Scholar]
- Dong, X.; Zhou, J.; Alharbi, K.; Lin, X.; Cao, Z. An El Gamal-based efficient and privacy-preserving data aggregation scheme for Smart Grid. In Proceedings of the 2014 IEEE Global Communications Conference, Istanbul, Turkey, 6–9 May 2014; pp. 4720–4725. [Google Scholar]
- Mendel, J. Smart grid cyber security challenges: Overview and classification. e-Mentor 2017, 55–66. [Google Scholar] [CrossRef] [Green Version]
- Li, B.; Lu, R.; Xiao, G.; Su, Z.; Ghorbani, A. PAMA: A proactive approach to mitigate false data injection attacks in Smart Grids. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Sun, A.; Wu, A.; Zheng, X.; Ren, F. Efficient and privacy-preserving certificateless data aggregation in Internet of things–enabled Smart Grid. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719842062. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Zhao, C.; Zhao, S.; Zhao, M.; Chen, Z.; Gao, C.Z.; Li, H.; Tan, Y.a. Secure multiparty computation: Theory, practice and applications. Inf. Sci. 2019, 476, 357–372. [Google Scholar] [CrossRef]
- Thoma, C.; Cui, T.; Franchetti, F. Secure multiparty computation based privacy preserving smart metering system. In Proceedings of the 2012 North American Power Symposium (NAPS), Champaign, IL, USA, 9–11 September 2012; pp. 1–6. [Google Scholar]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. An MPC-based protocol for secure and privacy-preserving smart metering. In Proceedings of the 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Torino, Italy, 26–29 September 2017; pp. 1–6. [Google Scholar]
- Ben-Or, M.; Goldwasser, S.; Wigderson, A. Completeness theorems for non-cryptographic fault-tolerant distributed computation. In Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; ACM: New York, NY, USA, 2019; pp. 351–371. [Google Scholar]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. A secure and privacy-preserving protocol for smart metering operational data collection. IEEE Trans. Smart Grid 2019, 10, 6481–6490. [Google Scholar] [CrossRef] [Green Version]
- Tonyali, S.; Akkaya, K.; Saputro, N.; Uluagac, A.S.; Nojoumian, M. Privacy-preserving protocols for secure and reliable data aggregation in IoT-enabled smart metering systems. Future Gener. Comput. Syst. 2018, 78, 547–557. [Google Scholar] [CrossRef]
- Ács, G.; Castelluccia, C. I have a dream!(differentially private smart metering). In Proceedings of the International Workshop on Information Hiding; Springer: Cham, Switzerland, 2011; pp. 118–132. [Google Scholar]
- Liu, H.; Chen, J.; Lin, L.; Ye, A.; Huang, C. An efficient and privacy-preserving data aggregation scheme supporting arbitrary statistical functions in IoT. China Commun. 2022, 19, 91–104. [Google Scholar] [CrossRef]
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF formulas on ciphertexts. In Proceedings of the Theory of Cryptography Conference; Springer: Cham, Switzerland, 2005; pp. 325–341. [Google Scholar]
- Abdallah, A.; Shen, X.S. A lightweight lattice-based homomorphic privacy-preserving data aggregation scheme for Smart Grid. IEEE Trans. Smart Grid 2016, 9, 396–405. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. EDAT: Efficient data aggregation without TTP for privacy-assured smart metering. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Li, F.; Luo, B.; Liu, P. Secure information aggregation for Smart Grids using homomorphic encryption. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar]
- Cho, S.; Li, H.; Choi, B.J. PALDA: Efficient privacy-preserving authentication for lossless data aggregation in Smart Grids. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 914–919. [Google Scholar]
- Bakondi, B.G.; Peter, A.; Everts, M.; Hartel, P.; Jonker, W. Publicly verifiable private aggregation of time-series data. In Proceedings of the 2015 10th International Conference on Availability, Reliability and Security, Toulouse, France, 24–28 August 2015; pp. 50–59. [Google Scholar]
- Li, S.; Xue, K.; Yang, Q.; Hong, P. PPMA: Privacy-preserving multisubset data aggregation in Smart Grid. IEEE Trans. Ind. Informatics 2017, 14, 462–471. [Google Scholar] [CrossRef]
- Chen, L.; Lu, R.; Cao, Z.; AlHarbi, K.; Lin, X. MuDA: Multifunctional data aggregation in privacy-preserving smart grid communications. Peer-to-Peer Netw. Appl. 2015, 8, 777–792. [Google Scholar] [CrossRef]
- Borges, F.; Demirel, D.; Böck, L.; Buchmann, J.; Mühlhäuser, M. A privacy-enhancing protocol that provides in-network data aggregation and verifiable smart meter billing. In Proceedings of the 2014 IEEE Symposium on Computers and Communications (ISCC), Madeira, Portugal, 23–26 June 2014; pp. 1–6. [Google Scholar]
- Keoh, S.L.; Tang, Z. Towards secure end-to-end data aggregation in AMI through delayed-integrity-verification. In Proceedings of the 2014 10th International Conference on Information Assurance and Security, Okinawa, Japan, 28–30 November 2014; pp. 6–11. [Google Scholar]

| Technique Used | Attack Model | System Model | Strength | Weakness |
|---|---|---|---|---|
| Diluted geometric distribution, quad tree, key management centre (KMC) [15] | Malware, data pollution attacks | SM, CC, GW | Privacy, DP, FT, low compu. and comm. cost | Less effective, inefficient, and unreliable |
| Needham–Schroeder authentication protocol [17] | Replay, DDoS, MITM attack | SM, TA, GW | Scalability, FT | Unreliable, high comm. overhead and compu. cost |
| BLS signature aggregation, batch verification, signature amortization [6] | Replay, DDoS attack | SM, TTP, CA, GW | FT, availability, low comm. and compu. cost. | Less effective, inefficient, and unreliable |
| Paillier homomorphic cryptosystem, distributed key-managing authority [38] | Aggregator obliviousness, malicious data consumer | SM, aggregator | Exchangeable statistical functions, group key management, DP, FT | Only group signature verification facility |
| Binary tree, block aggregation, geometric distribution [9] | Colluding, data pollution attack | SM, aggregator, TA | FT, no peer-to-peer comm., dynamic leaver/joiner | Extra communication if tree expanded |
| Pairwise private stream aggregation scheme [22] | Eavesdrop, privacy-divulging attack | KMC, SM, CCC | FT, privacy | Extra comm. overhead |
| Coding theory, spread spectrum communication over CDMA [18] | DP, MITM, inference attack | SM, TA, GW, CDMA, CCC | Low comm. and compu. cost, high performance | Extra storage, unreliable |
| Homomorphic encryption, geometric distribution [19] | Privacy divulging, data attack | CCC, TA, GW, SM, CH | FT, DP privacy, low compu. and comm. cost | Slow verification process, configuration and maintenance issues |
| Paillier-based homomorphic encryption [12] | DP, malware, privacy divulging, data alteration attack | CC, TA, GW, KMC, SMs | Decentralized, FT, DP | High storage, comm., and compu cost |
| Paillier homomorphic encryption [8] | Data mining, DDoS, replay attack | SM, GW, CCC | Privacy, FT, comp. efficiency, DP | Less efficient, high compu. cost |
| BGN, Diffie–Hellmann key exchange protocol [20] | Internal, external, and differential attack | CC, TA, GW, SM | Privacy, FT, DP, low error, less comp. cost | High storage cost, configuration and maintenance issue |
| SMPC, homomorphic encryption [24] | MITM, data mining and differential attack | One aggregator model | Privacy-preserving | No secure channel, high comp. and compu. cost |
| HE signature scheme, El Gamal cryptosystem [30] | Chosen message attacks | CCC, SMs, GW | Less comm. and comp. cost, privacy, FT | Less efficient, high storage cost, unreliable |
| Modular addition symmetric key, digital certificates [31] | Curious aggregator, chosen message and chosen ciphertext attack | SM, Aggregator | Scalability, FT, DP, high accuracy | High bandwidth, extra storage requirement |
| El Gamal homomorphic encryption, 0-knowledge range proof, PKI cert [32] | DDoS, n data mining attacks | CCC, n GW, n SM, n TA | Privacy, n DP, n FT, n range-based filtering | Comm. overhead, compu. cost |
| Ref. | PR1 | PR2 | PR3 | PR4 | PR5 | PR6 | PR7 |
|---|---|---|---|---|---|---|---|
| [15] | √ | √ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [16] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [17] | √ | √ | √ | ✗ | ✗ | ✗ | ✗ |
| [6] | √ | √ | √ | ✗ | ✗ | ✗ | ✗ |
| [38] | ✗ | ✗ | √ | ✗ | ✗ | ✗ | ✗ |
| [9] | ✗ | ✗ | √ | √ | ✗ | ✗ | ✗ |
| [22] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [7] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [19] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [12] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [8] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
| [20] | √ | √ | √ | ✗ | √ | √ | ✗ |
| [24] | √ | ✗ | √ | √ | ✗ | √ | √ |
| [30] | √ | √ | √ | ✗ | ✗ | ✗ | ✗ |
| [31] | ✗ | ✗ | ✗ | √ | ✗ | ✗ | ✗ |
| [34] | √ | √ | √ | √ | ✗ | ✗ | ✗ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, H.M.; Khan, A.; Khan, B.; Jeon, G. Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids: Techniques, Design Challenges, and Future Trends. Energies 2022, 15, 9350. https://doi.org/10.3390/en15249350
Khan HM, Khan A, Khan B, Jeon G. Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids: Techniques, Design Challenges, and Future Trends. Energies. 2022; 15(24):9350. https://doi.org/10.3390/en15249350
Chicago/Turabian StyleKhan, Hayat Mohammad, Abid Khan, Basheir Khan, and Gwanggil Jeon. 2022. "Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids: Techniques, Design Challenges, and Future Trends" Energies 15, no. 24: 9350. https://doi.org/10.3390/en15249350








