Efficient IoT-Based Formal Model for Vehicle-Life Interaction in VANETs Using VDM-SL
Abstract
:1. Introduction
1.1. VANETs with IoT
1.2. Comparison between Fog-Based RSU and Traditional RSU
1.3. Formal Methods
1.4. Contribution
- I.
- We adopt a fog-based protocol and specify this protocol in a formal method approach, which provides emergency services with the arrival of an emergency vehicle at accident locations.
- II.
- We also adopt a unicast routing protocol to send a message from one vehicle to another, which is focused on V2V communication.
- III.
- The network of V2V communication will be represented using graph theory.
- IV.
- Unified Modeling Language (UML) is utilized to model and capture different components of a system.
- V.
- The formal language VDM-SL is utilized to provide the specification of the system, and a VDM-SL toolbox is used to check the validation of the proposed model.
2. Related Work
2.1. IoT and VANETs
2.2. Message Dissemination and Authentication Scheme
2.3. Emergency Vehicle’s Route Clearance
2.4. Routing-Based Scheme for Accident Prevention and Avoidance
2.5. Related Work of Unicast Protocols
2.6. Literature Review of Formal Methods
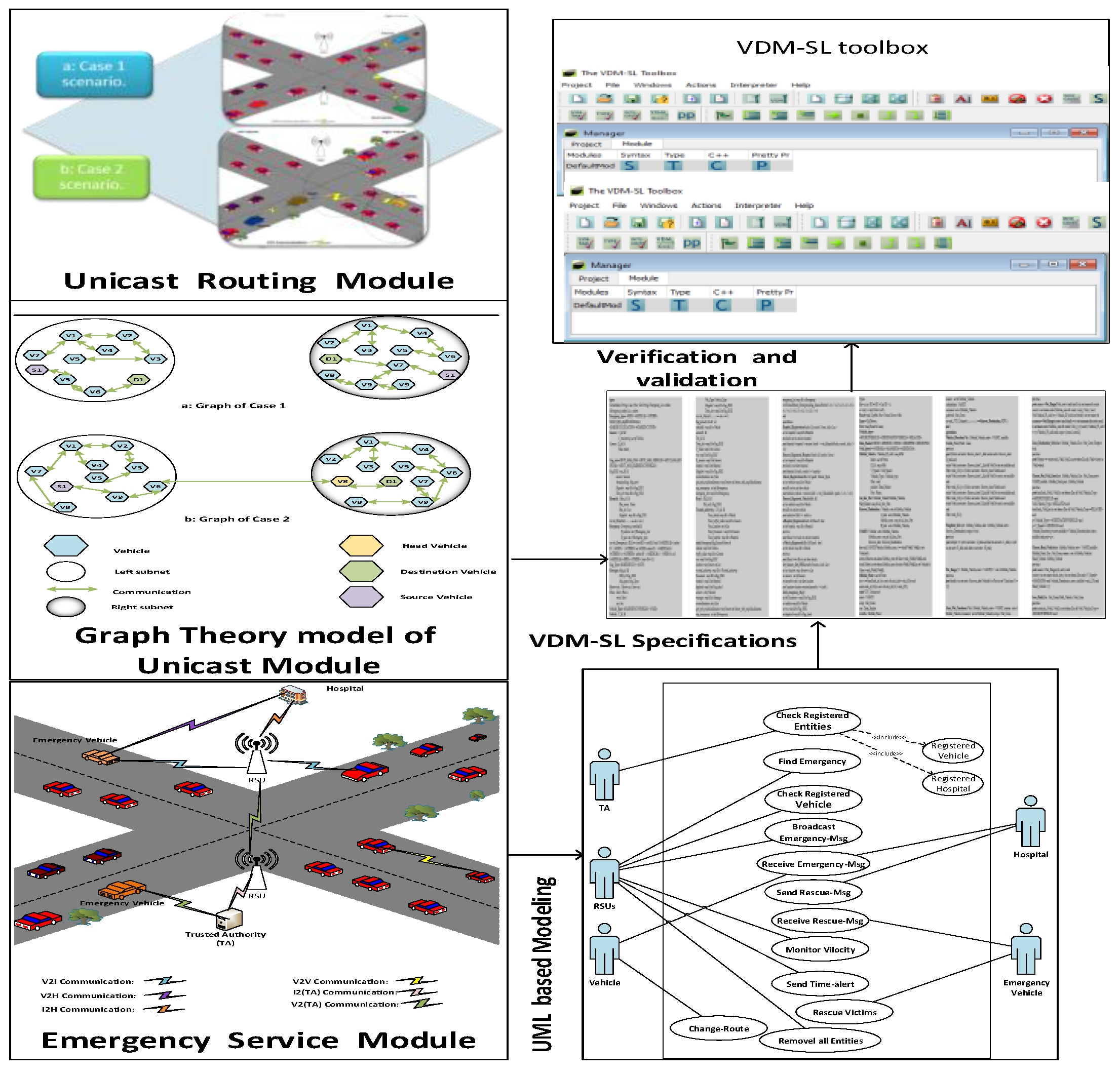
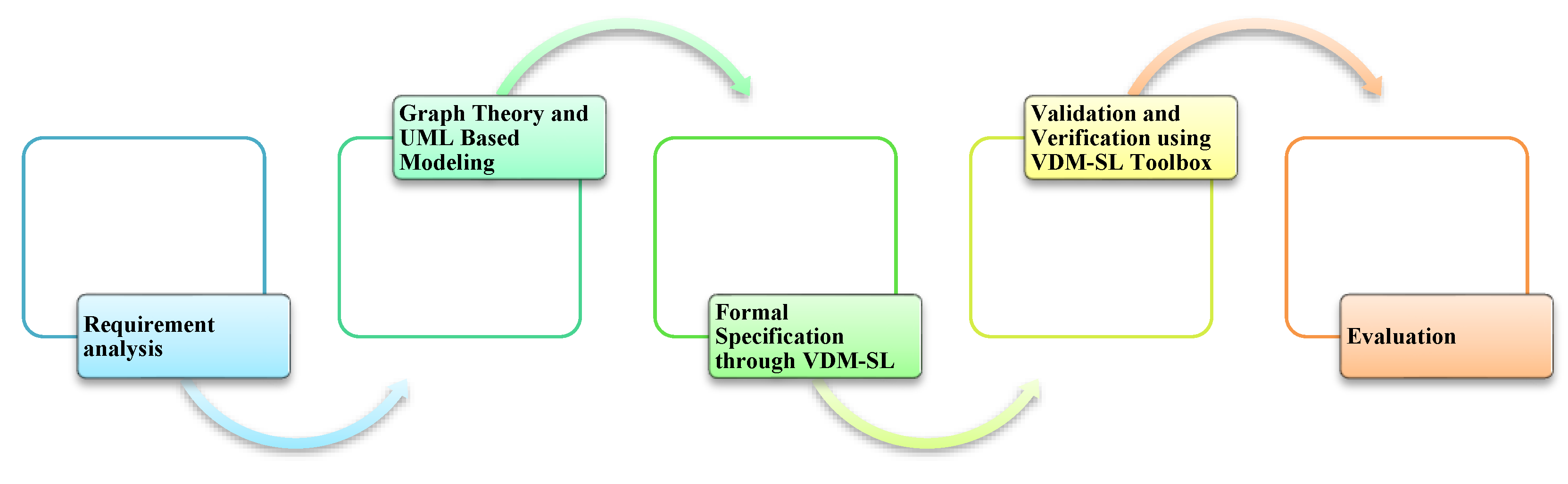
3. Methodology
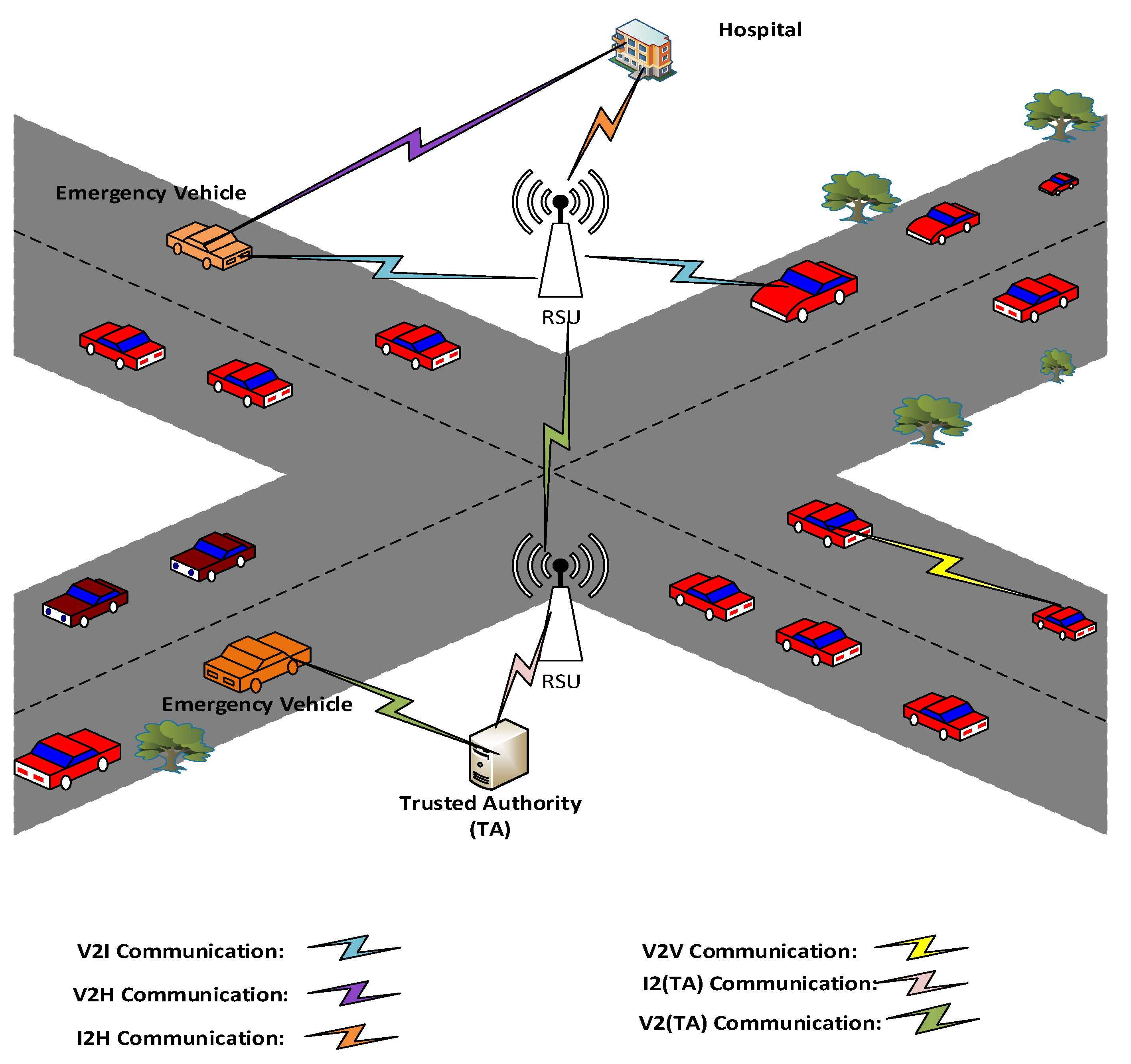
3.1. Architecture of the System
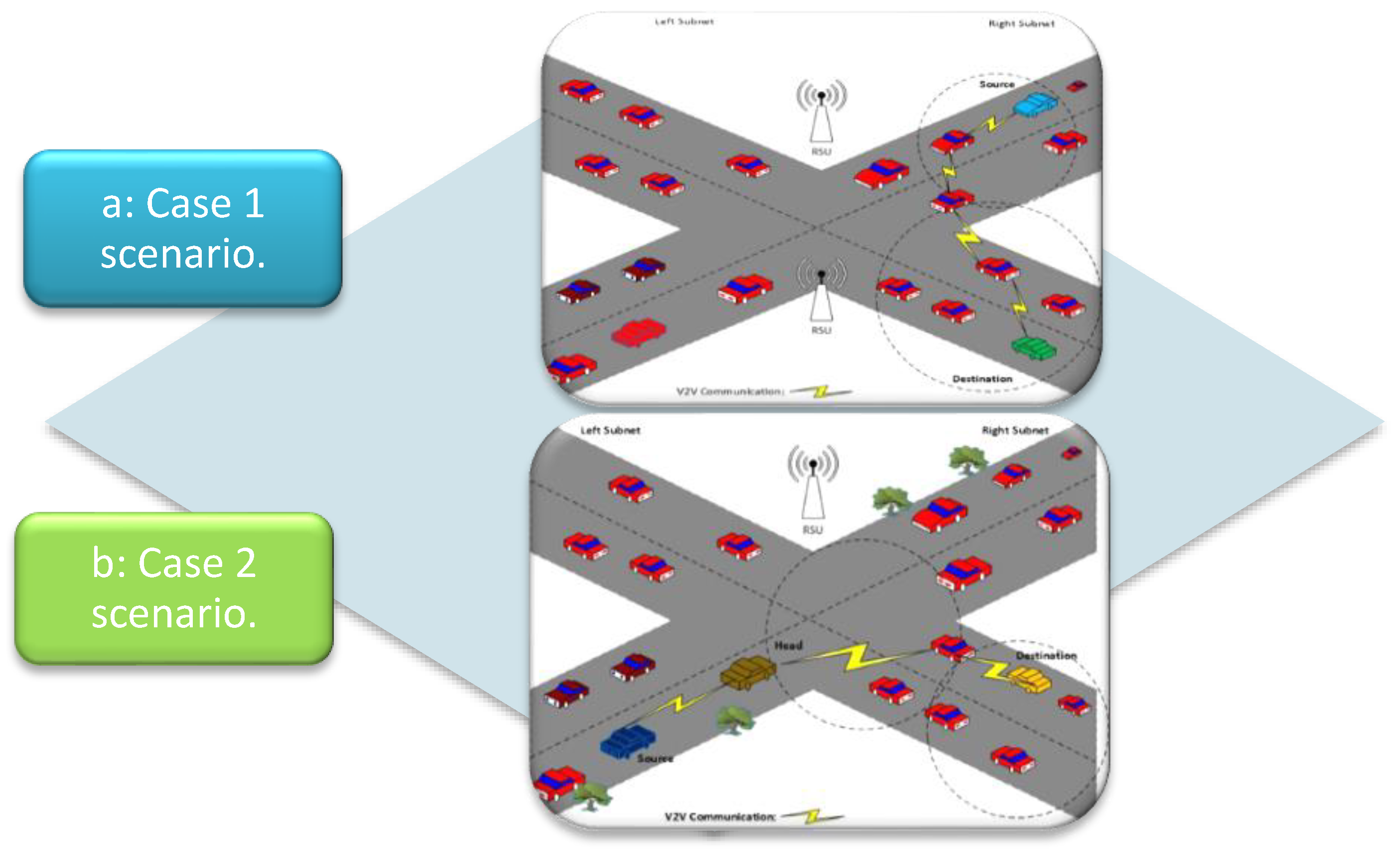
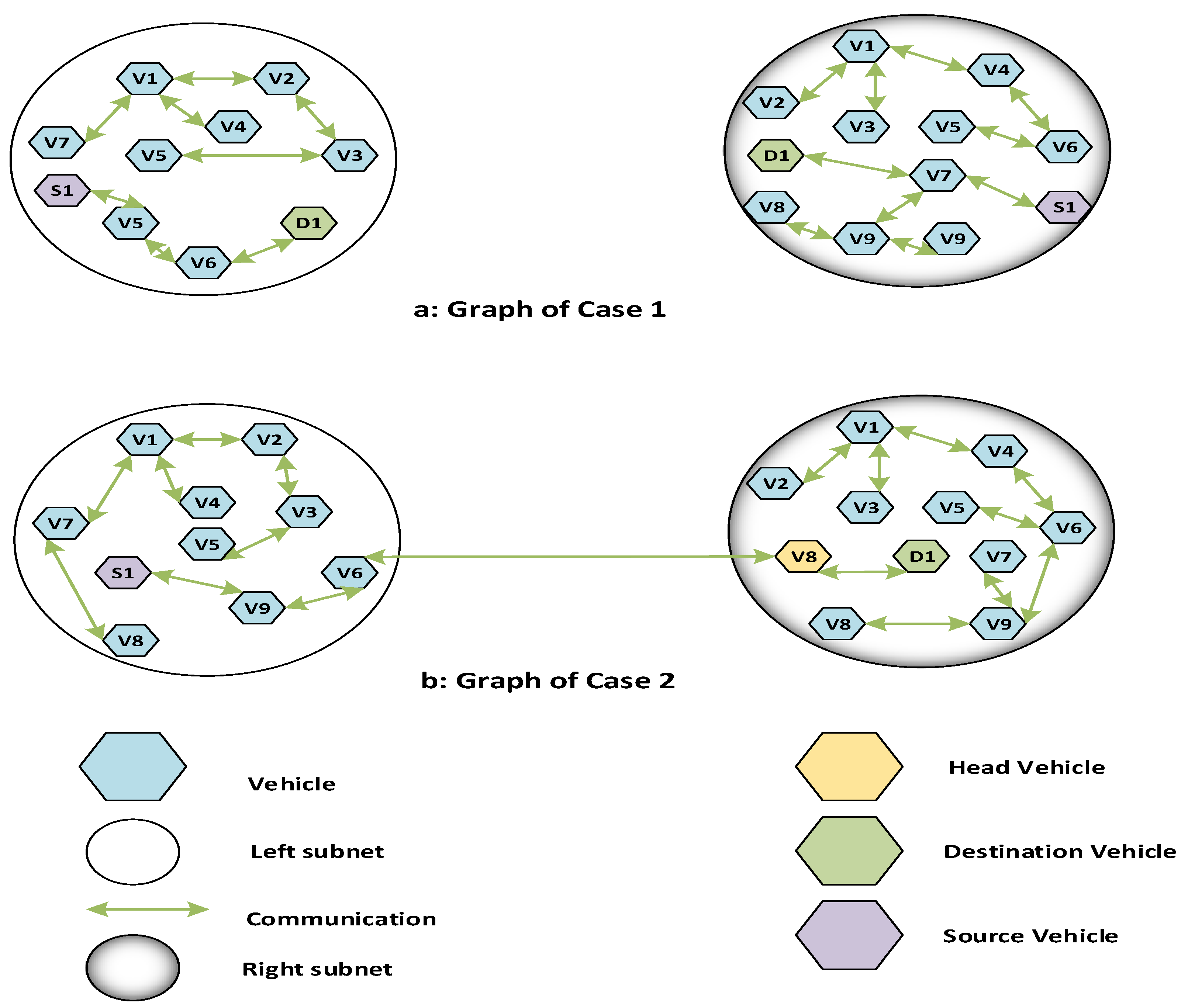
3.2. Unicast Routing Module for V2V Communication
| Algorithm 1: V2V Communication using Unicast Algorithm |
| 1. Procedure Unicast 2. Input: V2V Comm (Communication) 3. if Veh1 Comm Veh2 then 4. Str ← Veh1 & Dest ← Veh2 5. Vehicle-Direction (KDT, Str, VB, Middle) & Vehicle-Direction (KDT, Dest, VL, Middle) 6. Neighbour-Search (Str, Dest, L_S, R_S) 7. if Neighbour-Search (Str, Dest, L_S, R_S) == TRUE 8. 2H- Zone-Creationn (Str, Subnet) 9. Scope-Destination-Srch(Dest, Scope) 10. if Scope-Destination-Srch (Dest, Scope) == TRUE 11. Save-Path (Dest, Str, Scope) 12. Acknowledged(Path) 13. EXIT 14. else if Scope-Destination-Srch (Dest, Scope) == FALSE 15. Choose-Peri-Veh (Scope) 16. Loop from step 8 to step 9 17. if Neighbour-Search (Str, Dest, L_S, R_S) == FALSE 18. Choose-Head (Str, Middle) 19. Move hv to Middle 20. if Str in set L_S 21. 2H_Zone-Creation (hv, R_S) 22. if Scope-Destination-Srch (Dest, Scope) == TRUE 23. Save-Path (Dest, Str, Scope) 24. Acknowledged(Path) 25. EXIT 26. else if Scope-Destination-Srch (Dest, Scope) == FALSE 27. Choose-Peri-Veh(Scope) 28. Loop from step 21 to step 26 29. else if Str in set R_S 30. 2H_Zone_Creation (hv, L_S) 31. if Scope-Destination-Srch (Dest, Scope) == TRUE 32. Save-Path (Dest, Str, Scope) 33. Acknowledged(Path) 34. EXIT 35. else if Scope-Destination-Srch (Dest, Scope) == FALSE 36. Choose_Peri_Veh(Scope) 37. Loop from step 31 to step 35 |
Graph Theory Model of Unicast Module in V2V Communication
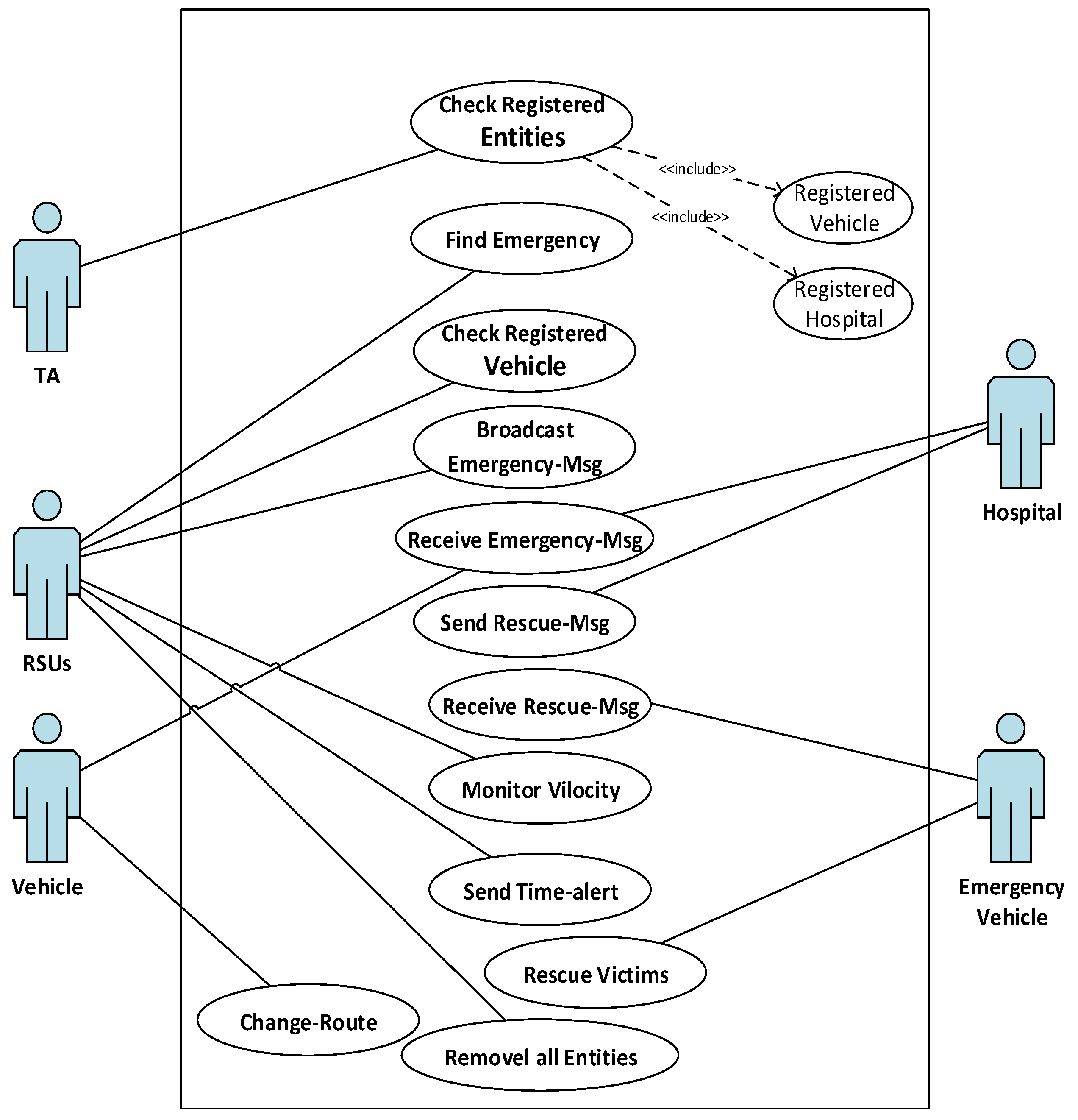
3.3. Emergency Service Module
| Algorithm 2: Broadcast Emergency Message Algorithm |
| 1. Procedure System Communication (Fog-RSU, Vehicle, Hospital); 2. Input: Emer(Emergency); 3. if Message = TRUE then 4. The Fog-RSU checks a V-id; 5. if a V-id registered then 6. if Msg-type = Emer then 7. Broadcast Emer_Msg to Vehicles & Fog-RSUs; 8. RSU sends Emer_Msg to Hospital; 9. if Hospital = registered then 10. RSU sends Emer_Msg to the Hospital; 11. Hospital checked Msg-type & V-id; 12. Hospital covey Rescue-Msg to Emer_Vehicle; 13. if Emer_Msg = Emer_Vehicle then 14. Emer_Vehicle extract Rescue_Msg; 15. RSU monitors velocity & wait for some period; 16. if RSU send Time-alert, after some Time_period then 17. Emer_Msg Broadcast to Emer_Vehicle when it is in the range of RSU; 18. else 19. Do Nothing; 20. end 21. else 22. Emer_Msg Broadcast to other vehicle to change their route; 23. end 24. else 25. Rescue_Msg extracts by Emer_Vehicle; 26. Monitors velocity by RSU also wait for some Time-period; 27. end 28. else 29. Emer-Msg Broadcast to other vehicle to change their route; 30. Victims Rescue by Emer_Vehicle; 31. if Rescue_Msg = TRUE then 32. RSU Remove all entries; 33. Rescue_Msg send to previous RSU and Vehicles; 34. else 35. Send to Trusted-Authority 36. end 37. end 38. else 39. Send to Trusted-Authority 40. if V_id is registered then 41. Send verify msg to RSU; 42. else 43. Contact to Trusted-Authority; 44. end 45. end 46. else 47. Do Nothing; 48. end |
UML Based Model of Emergency Service Module
4. Formal Methods and Formal Specifications
4.1. Unicast Routing Module’s Specifications for V2V Communication
| types Bit = a inv BT == BT = 0 or BT = 1; a = int; b = int; Point = a*b; Road= real; Up=Bit; Pos = Point; Down = Bit; Lane = Up*Down; Ad_hoc_Net = Mobile_Vehicle*Mobile_Vehicle; Rdd= map Road to Lane; Net_Conn = seq of Ad_hoc_Net; Vehicle_type= <SOURCEVEHICLE>|<DESTINATIONVEHICLE>|<RELAYED>; Data_Packet= <SENT>|<RESEND>|<SEND>|<DROPPED>|<RECEIVED>; Veh_Speed = <NORMAL>|<MAXIMUM>|<MINIMUM>; MobileVehicle :: Vehicle_IP_Add : seq of Bit limit : set of Point R_Id : seq of Bit V_Speed : Veh_Speed Vehicle_Type : Vehicle_type Dist : real packet : Data_Packet Pos : Point; |
| KnownDestination :: Vehicle : set of Mobile_Vehicle L_link : set of Mobile_Vehicle Mobile_conn : seq of Ad_hoc_Net R_link : set of Mobile_Vehicle; |
| VANET:: Vehicle : set of Mobile_Vehicle Mobile_conn : seq of Ad_hoc_Net Known_dest : Known_Destination inv mk_VANET(Vehicle, Mobile_conn,-) == forall Va, Vb in set Vehicle & exists Mnet in set elems Mobile_conn & Mnet = mk_( Va, Vb) and forall Mnet in set elems Mobile_conn & exists Va, Vb in set Vehicle & Mnet = mk_( Va, Vb); Middle_Point = set of Point inv x == forall mk_(a, b) in set x & mk_(a,b) = mk_(0,b) and exists mk_(a1,b1) in set x & mk_(a1,b1) = mk_(0,0); |
| state V2V_Unicast of netw : VANET scop : Net_Conn res : Data_Packet middle : Middle_Point nearer : set of MobileVehicle subnetbase : VANET nonearer: set of MobileVehicle pathveh : Net_Conn inv mk_V2V_Unicast(-,-,-,-,-,-,-,-) == KnownDestinationV2V () end |
| operations VehicleDirection(Veh : MobileVehicle, netw : VANET, middle : Middle_Point) Path : Lane pre true post (Veh in set netw. KnownDestination. L_link union netw. KnownDestination. R_link and exists Veh in set netw. KnownDestination. L_link & Veh.Pos in set middle and Path = mk_(1,0)) or (Veh in set netw. KnownDestination.Vehicle and exists Veh in set netw. KnownDestination. L_link & Veh.Pos not in set middle and Path = mk_(0,1)) or (Veh in set netw. KnownDestination.Vehicle and exists Veh in set netw. KnownDestination. R_link & Veh.Pos in set middle and Path = mk_(1,0)) or (Veh in set netw. KnownDestination.Vehicle and exists Veh in set netw. KnownDestination. R_link & Veh.Pos not in set middle and Path = mk_(0,1)); |
| NeighborSrch (str : MobileVehicle, dest : MobileVehicle, netw : KnownDestination) output : bool pre true post output <=> (str in set netw. L_link and dest in set netw. L_link) or (str in set netw. R_link and dest in set netw. R_link); |
| NetRange (V : MobileVehicle, netw : VANET) Y : set of MobileVehicle pre true post forall y in set netw. KnownDestination.Vehicle & y.Pos in set V.limit and Y = {y}; |
| ZoneNetCreationn(Veh : MobileVehicle, netw : VANET, nearer : set of MobileVehicle, nonearer : set of Mobile_Vehicle) scope : Net_Conn pre true post nearer = NetRange(Veh, netw) and forall y in set nearer & exists conn1 in set elem netw.Mobile_conn & conn1 = mk_( Veh, y) and Veh.Vehicle_IP_Add <> y.Vehicle_IP_Add and forall y in set nearer & nonearer = NetRange(y,netw) and forall yv in set nonearer & exists conn2 in set elems netw.Mobile_conn & conn2 = mk_(y,yv) and y.Vehicle_IP_Add <> yv.Vehicle_IP_Add and scope = [conn1, conn2]; |
| ZoneDestinationSrch(dest : MobileVehicle, Zon : Net_Conn) Output: bool pre true post Output <=> exists mk_(Veh1,Veh2) in set elems Zon & (Veh1= dest) or (Veh2=dest); |
| ChoosePeriVehZone(dest : MobileVehicle, Zon : Net_Conn,netw : VANET,middle : Middle_Point) peri : MobileVehicle pre true post forall mk_(Veh1, Veh2) in set elems Zon & Veh1.Vehicle_Type =<SOURCEVEHICLE> and Veh2.Vehicle_Type = <RELAYED> and forall mk_(Veh2,pv) in set elems Zon & Veh2.Vehicle_Type =<RELAYED> and pv.Vehicle_Type <> <DESTINATIONVEHICLE> and pv.V_Speed = <MINIMUM> and VehicleDirection( pv,netw,middle) = VehicleDirection(dest, netw, middle) and peri = pv; |
| ChooseHeadVehicle(srt : MobileVehicle, netw : VANET,middle : Middle_Point, Zon : Net_Conn, nearer : set of MobileVehicle) Head_Vehicle : MobileVehicle pre true post nearer = NetRange(srt, netw) and (exists y in set nearer & mk_(srt,y) in set elems Zon and y.V_Speed= <MAXIMUM> and VehicleDirection(y, netw, middle) = mk_(1,0) and Head_Vehicle = y); |
| SavePath(Zon : Net_Conn) Path_Vehicle : Net_Conn pre true post exists mk_(Veh1, Veh2) in set elems Zon & Veh1.Vehicle_Type = <SOURCEVEHICLE> and Veh2.Vehicle_Type = <RELAYED> and exists mk_(Veh3, Veh4) in set elems Zon & Veh3.Vehicle_Type =<RELAYED> and Veh4.Vehicle_Type = <DESTINATIONVEHICLE> and forall mk_(Veh2, Veh3) in set elems Zon & Veh2.Vehicle_Type =<RELAYED> and Veh3.Vehicle_Type =<RELAYED> and Path_Vehicle = [mk_(Veh1,Veh2),mk_( Veh2, Veh3),mk_(Veh3, Veh4)]; |
| Acknowledged(pv : Net_Conn) Veh_Msg : Data_Packet pre true post exists mk_(Veh1,Veh2) in set elems pv & Veh1.Vehicle_Type =<SOURCEVEHICLE> and Veh2.Vehicle_Type = <RELAYED> and exists mk_(Veh3,Veh4) in set elems pv & Veh3.Vehicle_Type=<RELAYED> and Veh4.Vehicle_Type = <DESTINATIONVEHICLE> and forall mk_(Veh2, Veh3) in set elems pv & Veh2.Vehicle_Type =<RELAYED> and Veh3.Vehicle_Type =<RELAYED> and (pv = [mk_(Veh1, Veh2),mk_(Veh2,Veh3),mk_(Veh3, Veh4)] and Veh_Msg = <RECEIVED> or pv <> [mk_(Veh1,Veh2),mk_(Veh2,Veh3),mk_(Veh3,Veh4 )] and Veh_Msg = <RESEND> ); |
| KnownDestinationV2V() output : bool ext wr res : Data_Packet rd netw : VANET wr pathveh : Net_Conn wr nonearer : set of MobileVehicle rd middle : Middle_Point wr nearer : set of MobileVehicle wr scop : Net_Conn pre true post exists Veh in set netw.Vehicle & Veh.Vehicle_Type =<SOURCEVEHICLE> and exists Veh1 in set netw.Vehicle & Veh1.Vehicle_Type =<DESTINATIONVEHICLE> and (NeighborSrch( Veh, Veh1, netw. KnownDestination) = true and nearer = NetRange (Veh, netw) and forall vn in set nearer & nonearer = NetRange(vn,netw) and scop = ZoneNetCreationn (Veh, netw, nearer, nonearer) and (ZoneDestinationSrch (Veh1, scop) = true and pathveh = SavePath(scop) and res = Acknowledged (pathveh)) or (ZoneDestinationSrch (Veh1, scop) = false and exists pv in set netw.Vehicle & pv = ChoosePeriVehZone (Veh1, scop, netw, middle) and nearer = NetRange(pv,netw) and forall vn in set nearer & nonearer = NetRange(vn, netw) and forall vn in set nearer & nonearer = NetRange(vn, netw) and scop = ZoneNetCreationn (pv,netw,nearer,nonearer) and ZoneDestinationSrch (pv, scop) = true and pathveh = SavePath(scop) and res = Acknowledged(pathveh) or res = <DROPPED>) and output = true) or (NeighborSrch(Veh, Veh1,netw. KnownDestination) = false and exists hv in set netw.Vehicle & hv = ChooseHeadVehicle(Veh1,netw,middle, scop, nearer) and scop = ZoneNetCreationn(hv, netw,nearer,nonearer) and ((ZoneDestinationSrch(Veh1,scop) = true and pathveh = SavePath(scop) and res = Acknowledged (pathveh) or (exists pv in set netw.Vehicle & pv = ChoosePeriVehZone (Veh1, scop, netw, middle) and nearer = Net_Range(pv,netw) and (forall vn in set nearer & nonearer = NetRange (vn, netw)) and scop = ZoneNetCreationn(pv,netw,nearer,nonearer) and (ZoneDestinationSrch(pv,scop) = true and pathveh = SavePath(scop) and res = Acknowledged(pathveh) or res = <DROPPED> andoutput = true))))); |
4.2. Emergency Service Module’s Specifications
| types Name=token; String = seq of char; Id= String; Loc = token; Emergency_Loc = token; isAny_Emergency =token; Emergency_type= <FIRE>|<MEDICAL>|<OTHER>; Sensor_info_anyMiscellaneous= <EMEGENCYLOCATION>|<EMEGENCYTYPE>; Hospital :: Hos_id : Id Hos_name : Name Hos_loc : Loc Msgalert : map Id to FogBasedRSU inv mk_Hospital(i, -, -, - )== len i <= 8; |
| Emergency:: Emergency_recorded:Id E_location: set of Emergency_Loc E_type: set of Emergency_type inv mk_Emergency(-,Le,Lt)== (card(Le) = card(Lt)) and (({<MEDICAL>} subset Lt \ {<FIRE>} \ {<OTHER>} or {<FIRE>} subset Lt \ {<MEDICAL>}\ {<OTHER>} or {<OTHER>} subset Lt \ {<MEDICAL>} \ {<FIRE>}) and {<MEDICAL>,<FIRE>, <OTHER> } inter Lt <> {}); |
| Sensor :: S_Id: Id S_monitoring: set of Vehicle; Msg_sent=<SENT_MSG_RSU>|<SENT_MSG_VEHICLE>|<SENT_MSG_HOSPITAL>| <SENT_MSG_EMERGENCYVEHICLE>; FogBasedRSU:: rsu_Id: Id sensors: Sensors broadcastMsg: Msg_sent Msgalert : map Id to FogBasedRSU Time_alrt: map Id to FogBasedRSU; Message:: RSU_id: FogBasedRSU Msg_type: Emergency; Hours= nat; Mint= nat; Sec= nat; Time:: hours: Hours mint: Mint sec: Sec; |
| Vehicle_Type= <EMERGENCYVEHICLE>|<VEHICLE>; Vehicle :: T_Id: Id Veh_Type: Vehicle_Type Msgalert : map Id to FogBasedRSU Time_alrt: map Id to FogBasedRSU inv mk_Vehicle( i, -, -, -)== len i <= 8; |
| FogCloud:: RsuId : Id vehicleId : map Id to Vehicle sensorId : Id TA_id: Id Time_alrt: map Id to FogBasedRSU Video_Trafic: map Id to Camera rsu: map Id to FogBasedRSU R_sensors: map Id to Sensors hospital : map Id to Hospital Msgalert : map Id to FogBasedRSU currentlocation: set of Loc get_info_anyMiscellaneous: map Sensors to Sensor_info_anyMiscellaneous any_emergency : set of isEmergency emergency_list: map Id to Emergency; Road :: Rd_Id: Id Rd_rsu1: FogBasedRSU; |
| TrustedAuthority :: TA_id: Id View_vehicle: map Id to Vehicle View_traffic_video: map Id to Camera View_location: set of Loc View_Rsusensor : map Id to Sensors View_hospital : map Id to Hospital; |
| state EmergencyMsg_RescueVictim of vehicle: map Id to Vehicle traffic_video: map Id to Camera rsu: map Id to FogBasedRSU location: map Sensors to Loc trusted_authority: map Id to TrustedAuthority Rsusensor : map Id to FogBasedRSU hospital : map Id to Hospital fogcloud: map Id to FogCloud sensors : set of Sensor currentlocation: set of Loc get_info_anyMiscellaneous: map Sensors to Sensor_info_anyMiscellaneous any_emergency : set of isAny_Emergency emergency_list: map Id to Emergency init EM==EM=mk_EmergencyMsg_RescueVictim({|->}, {|->},{|->},{|->},{|->},{|->}, {|->}, {|->},{}, {}, {|->},{}, {|->}) end |
| operations HospitalRegistration(hosIn: Id, namIn: Name, locIn: Loc ) ext wr hospital : map Id to Hospital pre hosIn not in set dom hospital post hospital = hospital ~ munion{ hosIn |-> mk_Hospital(hosIn, namIn, locIn, {|->})}; |
| RemovedRegisteredHospital (hosIn: Id, namIn: Name) ext wr hospital : map Id to Hospital pre hosIn in set dom hospital post hospital ={ hosIn, namIn }<-: hospital~; |
| VehicleRegistration(inputId: Id, typeIn: Vehicle_Type) ext wr vehicle: map Id to Vehicle pre inputId not in set dom vehicle post vehicle = vehicle ~ munion{ inputId |-> mk_Vehicle(inputId, typeIn, {|->},{|->})}; |
| RemoveRegisteredVehicle(inputId: Id) ext wr vehicle: map Id to Vehicle pre inputId in set dom vehicle post vehicle ={ inputId }<-: vehicle ~; |
| isHospitalRegistered(hosIn: Id) Result : bool ext rd hospital : map Id to Hospital pre true post Result <=> hosIn in set dom hospital; |
| isVehicleRegistered(idIn: Id) Result : bool ext rd vehicle: map Id to Vehicle pre true post Result <=> idIn in set dom vehicle; |
| getNoOfRegisteredEmer_Vehicle() Result: nat ext rd vehicle: map Id to Vehicle pre true post Result = card {ev | ev in set rng vehicle & ev.Veh_Type =<EMERGENCYVEHICLE>}; |
| getNoOfRegisteredVehicle() Result: nat ext rd vehicle: map Id to Vehicle pre true post Result = card {tv | tv in set rng vehicle & tv.Veh_Type =<VEHICLE>}; |
| SetSensorsOnRSU(inputS:Sensors, locIn: Loc) ext wr location: map Sensors to Loc wr sensors : set of Sensor pre inputS not in set dom location post location= location munion{ inputS |-> locIn }; |
| EmergencyAlertMsg() ext wr vehicle: map Id to Vehicle rd Rsusensor : map Id to FogBasedRSU wr rsu: map Id to FogBasedRSU wr hospital : map Id to Hospital wr fogcloud: map Id to FogCloud pre true post exists msg in set dom fogcloud & fogcloud (msg).Msgalert = Rsusensor and vehicle (msg).Msgalert = Rsusensor and rsu (msg).Msgalert = Rsusensor; |
| SendTrafficData() ext rd traffic_video: map Id to Camera wr fogcloud: map Id to FogCloud pre true post exists vd in set dom fogcloud & fogcloud (vd). Video_Trafic = traffic_video; |
| TimeAlert() ext wr vehicle: map Id to Vehicle rd Rsusensor : map Id to FogBasedRSU wr rsu: map Id to FogBasedRSU wr fogcloud: map Id to FogCloud pre true post exists tm in set dom fogcloud & fogcloud (tm). Time_alrt = Rsusensor and vehicle (tm). Time_alrt = Rsusensor and rsu (tm). Time_alrt = Rsusensor; |
| GetInfoForRescueVictim(sensorIn: Sensors, getInfo: Sensor_info_anyMiscellaneous) ext wr get_info_anyMiscellaneous: map Sensors to Sensor_info_anyMiscellaneous wr fogcloud: map Id to FogCloud pre (getInfo not in set rng get_info_anyMiscellaneous)and(sensorIn in set dom location) post get_info_anyMiscellaneous = get_info_anyMiscellaneous munion{ getInfo |-> sensorIn }; |
| getEmergency(inputId: Id) ext rd emergency_list: map Id to Emergency pre true post emergency_list = { inputId }<: emergency_list; |
| ViewCloudDataByTA(taId : Id) ext rd fogcloud: map Id to FogCloud wr trusted_authority: map Id to TrustedAuthority pre exists x in set dom fogcloud & fogcloud(x). TA_id = taId post exists x in set dom trusted_authority & trusted_authority (x). View_vehicle = fogcloud (x). vehicleId and trusted_authority (x). View_traffic_video = fogcloud (x).T_Video and trusted_authority (x). View_location = fogcloud (x).currentlocation and trusted_authority (x). View_Rsusensor = fogcloud (x) . R_sensors and trusted_authority (x). View_hospital = fogcloud (x) .hospital; |
| BroadcastEmergencyMsg(msg : Id) Registed: bool ext wr message : map Id to Message wr vehicle: map Id to Vehicle wr rsu: map Id to FogBasedRSU rd trusted_authority: map Id to TrustedAuthority rd Rsusensor : map Id to FogBasedRSU rd hospital : map Id to Hospital rd fogcloud: map Id to FogCloud pre exists ms in set dom message & message (ms). Msg_id = msg post if Registed =true and exists m in set rng message & m. Msg_type = <EMERGENCY> then exists r in set rng rsu & r.broadcastMsg= <SENT_MSG_RSU> and exists r in set rng rsu & r.broadcastMsg= <SENT_MSG_HOSPITAL> and exists r in set rng rsu & r.broadcastMsg= <SENT_MSG_VEHICLE> and exists r in set rng rsu & r.broadcastMsg= <SENT_MSG_EMERGENCYVEHICLE> else Registed = false and if Registed =true and exists msg in set dom fogcloud & fogcloud (msg).Msgalert = Rsusensor then hospital (msg).Msgalert = Rsusensor and vehicle (msg).Msgalert = Rsusensor and rsu (msg).Msgalert = Rsusensor else Registed = false; |
5. Model Analysis by VDM-SL Toolbox
6. Conclusions
7. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Jiang, Y.; Shi, M.; Shen, X.; Lin, C. BAT: A robust signature scheme for vehicular networks using binary authentication tree. IEEE Trans. Wirel. Commun. 2008, 8, 1974–1983. [Google Scholar] [CrossRef] [Green Version]
- Sumanth, G.; Prabodh, C. A Survey on Security in VANETS and Applications. Int. Res. J. Eng. Technol. 2016, 3, 431–436. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Sotres, P.; Santana, J.R.; Sánchez, L.; Lanza, J.; Muñoz, L. Practical lessons from the deployment and management of a smart city internet-of-things infrastructure: The smartsantander testbed case. IEEE Access 2017, 5, 14309–14322. [Google Scholar] [CrossRef]
- Hatim, S.M.; Elias, S.J.; Awang, N.; Darus, M.Y. VANETS and Internet of Things (IoT): A discussion. Indones. J. Electr. Eng. Comput. Sci. 2018, 12, 218–224. [Google Scholar] [CrossRef]
- Kumar, S.; Singh, J. Internet of Vehicles over Vanets: Smart and Secure Communication using IoT. Scalable Comput. Pract. Exp. 2020, 21, 425–440. [Google Scholar] [CrossRef]
- Benslimane, A. Optimized dissemination of alarm messages in vehicular ad-hoc networks (VANET). In Proceedings of the IEEE International Conference on High Speed Networks and Multimedia Communications, Toulouse, France, 30 June–2 July 2004; Springer: Berlin, Germany, 2004; pp. 655–666. [Google Scholar]
- Doukha, Z.; Moussaoui, S. Dissemination of an emergency message in a vehicular ad hoc network. In Proceedings of the 2011 International Conference on Communications, Computing and Control Applications (CCCA), Hammamet, Tunisia, 3–5 March 2011; IEEE: Manhattan, NY, USA, 2011; pp. 1–6. [Google Scholar]
- Ullah, A.; Yaqoob, S.; Imran, M.; Ning, H. Emergency message dissemination schemes based on congestion avoidance in VANET and vehicular FoG computing. IEEE Access 2018, 7, 1570–1585. [Google Scholar] [CrossRef]
- Wing, J.M. A specifier’s introduction to formal methods. Computer 1990, 23, 8–22. [Google Scholar] [CrossRef]
- Presti, S.L.; Butler, M.; Leuschel, M.; Booth, C. A trust analysis methodology for pervasive computing systems. In Trusting Agents for Trusting Electronic Societies; Springer: Berlin/Heidelberg, Germany, 2004; pp. 129–143. [Google Scholar]
- Nguyen, V.; Khanh, T.T.; Oo, T.Z.; Tran, N.H.; Huh, E.-N.; Hong, C.S. A cooperative and reliable RSU-assisted IEEE 802.11 p-based multi-channel MAC protocol for VANETs. IEEE Access 2019, 7, 107576–107590. [Google Scholar] [CrossRef]
- Bello-Salau, H.; Onumanyi, A.J.; Abu-Mahfouz, A.M.; Adejo, A.O.; Mu’Azu, M.B. New discrete cuckoo search optimization algorithms for effective route discovery in IoT-based vehicular ad-hoc networks. IEEE Access 2020, 8, 145469–145488. [Google Scholar] [CrossRef]
- Kaur, M.; Malhotra, J.; Kaur, P.D. A VANET-IoT based Accident Detection and Management System for the Emergency Rescue Services in a Smart City. In Proceedings of the 2020 8th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 4–5 June 2020; IEEE: Manhattan, NY, USA, 2020; pp. 964–968. [Google Scholar]
- Zaheer, T.; Malik, A.W.; Rahman, A.U.; Zahir, A.; Fraz, M.M. A vehicular network–based intelligent transport system for smart cities. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719888845. [Google Scholar] [CrossRef]
- Ramakrishnan, B.; Selvi, M.; Nishanth, R.B.; Joe, M.M. An emergency message broadcasting technique using transmission power based clustering algorithm for vehicular ad hoc network. Wirel. Pers. Commun. 2017, 94, 3197–3216. [Google Scholar] [CrossRef]
- Nie, L.; Wang, H.; Gong, S.; Ning, Z.; Obaidat, M.S.; Hsiao, K.-F. Anomaly Detection Based on Spatio-Temporal and Sparse Features of Network Traffic in VANETs. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Manhattan, NY, USA, 2019; pp. 1–6. [Google Scholar]
- Zhong, T.; Xu, B.; Szczurek, P.; Wolfson, O. Trafficinfo: An algorithm for vanet dissemination of real-time traffic information. In Proceedings of the 5th World congress on Intelligent Transport Systems, London, UK, 2–4 July 2008. Citeseer. [Google Scholar]
- Wu, C.; Yoshinaga, T.; Ji, Y.; Zhang, Y. Computational intelligence inspired data delivery for vehicle-to-roadside communications. IEEE Trans. Veh. Technol. 2018, 67, 12038–12048. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Biswas, G. Design of authentication protocol for wireless sensor network-based smart vehicular system. Veh. Commun. 2017, 9, 64–71. [Google Scholar] [CrossRef]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Kang, J.; Lin, D.; Jiang, W.; Bertino, E. Highly efficient randomized authentication in VANETs. Pervasive Mob. Comput. 2018, 44, 31–44. [Google Scholar] [CrossRef]
- Alfadhli, S.A.; Lu, S.; Chen, K.; Sebai, M. Mfspv: A multi-factor secured and lightweight privacy-preserving authentication scheme for vanets. IEEE Access 2020, 8, 142858–142874. [Google Scholar] [CrossRef]
- Nellore, K.; Hancke, G.P. Traffic management for emergency vehicle priority based on visual sensing. Sensors 2016, 16, 1892. [Google Scholar] [CrossRef] [Green Version]
- Khaliq, K.A.; Qayyum, A.; Pannek, J. Prototype of automatic accident detection and management in vehicular environment using VANET and IoT. In Proceedings of the 2017 11th International Conference on Software, Knowledge, Information Management and Applications (SKIMA), Malabe, Sri Lanka, 6–8 December 2017; IEEE: Manhattan, NY, USA, 2017; pp. 1–7. [Google Scholar]
- Alazzawi, M.A.; Lu, H.; Yassin, A.A.; Chen, K. Efficient Conditional Anonymity with Message Integrity and Authentication in a Vehicular Ad-Hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Almalki, F.A.; Al-Dois, H.; Shvetsov, A.V.; Ansari, M.S.; Hawbani, A.; Gupta, S.K.; Lee, B. Multi-Drone Edge Intelligence and SAR Smart Wearable Devices for Emergency Communication. Wirel. Commun. Mob. Comput. 2021, 2021, 6710074. [Google Scholar] [CrossRef]
- Ramakrishnan, B.; Nishanth, R.B.; Joe, M.M.; Selvi, M. Cluster based emergency message broadcasting technique for vehicular ad hoc network. Wirel. Netw. 2017, 23, 233–248. [Google Scholar] [CrossRef]
- Gokulakrishnan, P.; Ganeshkumar, P. Road accident prevention with instant emergency warning message dissemination in vehicular ad-hoc network. PLoS ONE 2015, 10, e0143383. [Google Scholar]
- Truong, N.B.; Lee, G.M.; Ghamri-Doudane, Y. Software defined networking-based vehicular adhoc network with fog computing. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; IEEE: Manhattan, NY, USA, 2015; pp. 1202–1207. [Google Scholar]
- Jayaraj, V. Emergency vehicle signalling using VANETS. In Proceedings of the 2015 IEEE 17th International Conference on High Performance Computing and Communications, 2015 IEEE 7th International Symposium on Cyberspace Safety and Security, and 2015 IEEE 12th International Conference on Embedded Software and Systems, New York, NY, USA, 24–26 August 2015; IEEE: Manhattan, NY, USA, 2015; pp. 734–739. [Google Scholar]
- Senouci, O.; Aliouat, Z.; Harous, S. MCA-V2I: A Multi-hop Clustering Approach over Vehicle-to-Internet communication for improving VANETs performances. Future Gener. Comput. Syst. 2019, 96, 309–323. [Google Scholar] [CrossRef]
- Ghazi, M.U.; Khattak, M.A.K.; Shabir, B.; Malik, A.W.; Ramzan, M.S. Emergency message dissemination in vehicular networks: A review. IEEE Access 2020, 8, 38606–38621. [Google Scholar] [CrossRef]
- Guerrero-Ibanez, J.A.; Zeadally, S.; Contreras-Castillo, J. Integration challenges of intelligent transportation systems with connected vehicle, cloud computing, and internet of things technologies. IEEE Wirel. Commun. 2015, 22, 122–128. [Google Scholar] [CrossRef]
- Iqbal, Z.; Saeed, T.; Zafar, N.A. Effective formal unicast routing for VANETs. In Proceedings of the 2017 Fifth International Conference on Aerospace Science & Engineering (ICASE), Islamabad, Pakistan, 14–16 November 2017; IEEE: Manhattan, NY, USA, 2017; pp. 1–6. [Google Scholar]
- Ding, Y.; Wang, C.; Xiao, L. A static-node assisted adaptive routing protocol in vehicular networks. In Proceedings of the Fourth ACM international workshop on Vehicular Ad Hoc Networks, Online, 10 September 2007; pp. 59–68. [Google Scholar]
- Ducourthial, B.; Khaled, Y.; Shawky, M. Conditional transmissions: Performance study of a new communication strategy in VANET. IEEE Trans. Veh. Technol. 2007, 56, 3348–3357. [Google Scholar] [CrossRef]
- Afzaal, H.; Saeed, T.; Iqbal, Z.; Zafar, N.A. VDM-SL-Based Model of Border Protection System using WSANs. In Proceedings of the in International Conference on Informatics and Computing (ICIC), Mataram, Indonesia, 28–29 October 2016; pp. 1–6. [Google Scholar]
- Zafar, N.A.; Khan, S.A.; Araki, K. Towards the safety properties of moving block railway interlocking syste. Int. J. Innov. Comput. Info Control. 2012, 8, 5677–5690. [Google Scholar]
- Tahir, H.M.; Nadeem, M.; Zafar, N.A. Specifying electronic health system with Vienna development method specification language. In Proceedings of the 2015 National Software Engineering Conference (NSEC), Rawalpindi, Pakistan, 17 December 2015; IEEE: Manhattan, NY, USA, 2015; pp. 61–66. [Google Scholar]
- Latif, S.; Afzaal, H.; Zafar, N.A. Intelligent traffic monitoring and guidance system for smart city. In Proceedings of the 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 3–4 March 2018; IEEE: Manhattan, NY, USA, 2018; pp. 1–6. [Google Scholar]
- Khan, S.A.; Zafar, N.A.; Ahmad, F. Extending promotion to operate controller based on trains operation. Int. J. Phys. Sci. 2011, 6, 7262–7270. [Google Scholar]
- Afzaal, H.; Zafar, N.A. Robot-based forest fire detection and extinguishing model. In Proceedings of the 2016 2nd International Conference on Robotics and Artificial Intelligence (ICRAI), Rawalpindi, Pakistan, 1–2 November 2016; IEEE: Manhattan, NY, USA, 2016. [Google Scholar]
- Saeed, T.; Iqbal, Z.; Afzaal, H.; Zafar, N.A. Formal modeling of traffic based flooding procedure of AODV for Mobile Ad hoc Networks. In Proceedings of the 2016 International conference on emerging technologies (ICET), Islamabad, Pakistan, 18–19 October 2016; IEEE: Manhattan, NY, USA, 2016; pp. 1–6. [Google Scholar]
- Jin, D.; Shi, F.; Song, J. A traffic flow theory based density adopted emergency message dissemination scheme for vehicular ad hoc networks. In Proceedings of the 2015 International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, 12–14 January 2015; IEEE: Manhattan, NY, USA, 2015; pp. 57–62. [Google Scholar]
- Feroz, B.; Mehmood, A.; Maryam, H.; Zeadally, S.; Maple, C.; Shah, M.A. Vehicle-Life Interaction in Fog-Enabled Smart Connected and Autonomous Vehicles. IEEE Access 2021, 9, 7402–7420. [Google Scholar] [CrossRef]
- Tehseen, A.; Zafar, N.A.; Ali, T.; Jameel, F.; Alkhammash, E.H. Formal Modeling of IoT and Drone-Based Forest Fire Detection and Counteraction System. Electronics 2022, 11, 128. [Google Scholar] [CrossRef]
- Zafar, N.A. Formal specification and analysis of take-off procedure using VDM-SL. Complex Adapt. Syst. Model. 2016, 4, 1–26. [Google Scholar] [CrossRef] [Green Version]
| Reference | Year | Tools/Approaches | Advantages of Methods | Description | Disadvantages and Limitations |
|---|---|---|---|---|---|
| [16] | 2017 | NS-2 | • Results can be quickly obtained and tested easily • Complex scenarios also tested easily | • Reduced accidents on highway and also reduced end-to-end delay | • No formal verification and validation • To model real system is complicated |
| [28] | 2017 | NS-3 SUMO | • Contains an abundance of modules • Provide point-to-point wireless connection between a network | • Delivered the current condition of victims before arrival the victims in hospital with audio and video. • Under three evaluations parameters comparative analysis of the standards IEEE 802.11 | • The required quality of service QoS cannot achieved • Not calculate the accuracy of the model utilizing formal methods |
| [24] | 2016 | GPS module IDLE Arduino | • Broad range of libraries and low cost • Easily used not need to external expertise | • Hospital delivered an emergency vehicle at the accident area to provide medical services at shortest time | • Ignored traffic congestion at accident area. • No experimental result • No Formal verification and validation • Required too much efforts in scheduling |
| [29] | 2015 | NS-2 | • Results can be quickly obtained more ideas can be tested easily in shortest time | • In VANET cluster delivered the emergency alert message in shortest time. | • No Formal verification and validation • Bugs are unreliable and to model real system is complicated |
| [30] | 2015 | • Centralized management for network • provide security | • Create a framework for VANETS which is beneficial for both fog-computing and SDN | • Formal verification and validation is not provided • Significant amount of latency and lake in maintenance | |
| [31] | 2015 | SUMO NS-2 MOVE | • Not required costly equipments and easily tested in short time | • Reached emergency vehicle at shortest time • Delivered message from emergency vehicle to traffic signal | • No comparative performance result • Simulation based and not find the correctness of the system model Complicated structure, lightly maintained and not seen significant development |
| [32] | 2019 | NS-2, VanetMobiSim | • Support multiple protocols and many algorithms support in routing and queuing | • Multi-hop-clustering approach is proposed by using BFS algorithm • Improve the VANET’s performance Minimize the rate of message control | • Simulation based • Not calculate the accuracy of the model utilizing formal methods • Complicated structure and unreliable bugs |
| Composite Objects | Operations and Functions | Syntax Check | Type Check | Pretty Print |
|---|---|---|---|---|
| MobileVehicle | VehicleDirection | ✓ | ✓ | ✓ |
| NeighborSrch | ✓ | ✓ | ✓ | |
| NetRange | ✓ | ✓ | ✓ | |
| KnownDestination | ZoneNetCreation | ✓ | ✓ | ✓ |
| ZoneDestinationSrch | ✓ | ✓ | ✓ | |
| ChoosePeriVehZone | ✓ | ✓ | ✓ | |
| VANET | ChooseHeadVehicle | ✓ | ✓ | ✓ |
| Save Path | ✓ | ✓ | ✓ | |
| Time | Acknowledged | ✓ | ✓ | ✓ |
| KnownDestinationV2V | ✓ | ✓ | ✓ |
| Composite Objects | Operations and Functions | Syntax Check | Type Check | Pretty Print |
|---|---|---|---|---|
| Emergency | HospitalRegistration | ✓ | ✓ | ✓ |
| Hospital | RemovedRegisteredHospital | ✓ | ✓ | ✓ |
| Sensors | VehicleRegistration | ✓ | ✓ | ✓ |
| FogBasedRSU | RemovedRegisteredVehicle | ✓ | ✓ | ✓ |
| Message | isHospitalRegistered | ✓ | ✓ | ✓ |
| Time | isVehicle Registered | ✓ | ✓ | ✓ |
| Vehicle | getNoOfRegisteredEmerVehicle | ✓ | ✓ | ✓ |
| FogCloud | getNoOfRegisteredVehicle | ✓ | ✓ | ✓ |
| TrustedAuthority | SetSensorsOnRSU | ✓ | ✓ | ✓ |
| EmergencyAlertMsg | ✓ | ✓ | ✓ | |
| SendTrafficData | ✓ | ✓ | ✓ | |
| TimeAlert | ✓ | ✓ | ✓ | |
| GetInfoForRescueVictim | ✓ | ✓ | ✓ | |
| NewEmergencyDeduct | ✓ | ✓ | ✓ | |
| getEmergency | ✓ | ✓ | ✓ | |
| ViewCloudDataByTA | ✓ | ✓ | ✓ | |
| BroadcastEmergencyMsg | ✓ | ✓ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Iqbal, S.; Zafar, N.A.; Ali, T.; Alkhammash, E.H. Efficient IoT-Based Formal Model for Vehicle-Life Interaction in VANETs Using VDM-SL. Energies 2022, 15, 1013. https://doi.org/10.3390/en15031013
Iqbal S, Zafar NA, Ali T, Alkhammash EH. Efficient IoT-Based Formal Model for Vehicle-Life Interaction in VANETs Using VDM-SL. Energies. 2022; 15(3):1013. https://doi.org/10.3390/en15031013
Chicago/Turabian StyleIqbal, Sidra, Nazir Ahmad Zafar, Tariq Ali, and Eman H. Alkhammash. 2022. "Efficient IoT-Based Formal Model for Vehicle-Life Interaction in VANETs Using VDM-SL" Energies 15, no. 3: 1013. https://doi.org/10.3390/en15031013
APA StyleIqbal, S., Zafar, N. A., Ali, T., & Alkhammash, E. H. (2022). Efficient IoT-Based Formal Model for Vehicle-Life Interaction in VANETs Using VDM-SL. Energies, 15(3), 1013. https://doi.org/10.3390/en15031013






