Review of Cyberattack Implementation, Detection, and Mitigation Methods in Cyber-Physical Systems
Abstract
1. Introduction
2. Cyber-Physical Systems: Characteristics and Requirements
2.1. Safety
2.2. Availability
2.3. Integrity
2.4. Security
2.5. Timeliness
2.6. Confidentiality
2.7. Authentication and Authorization
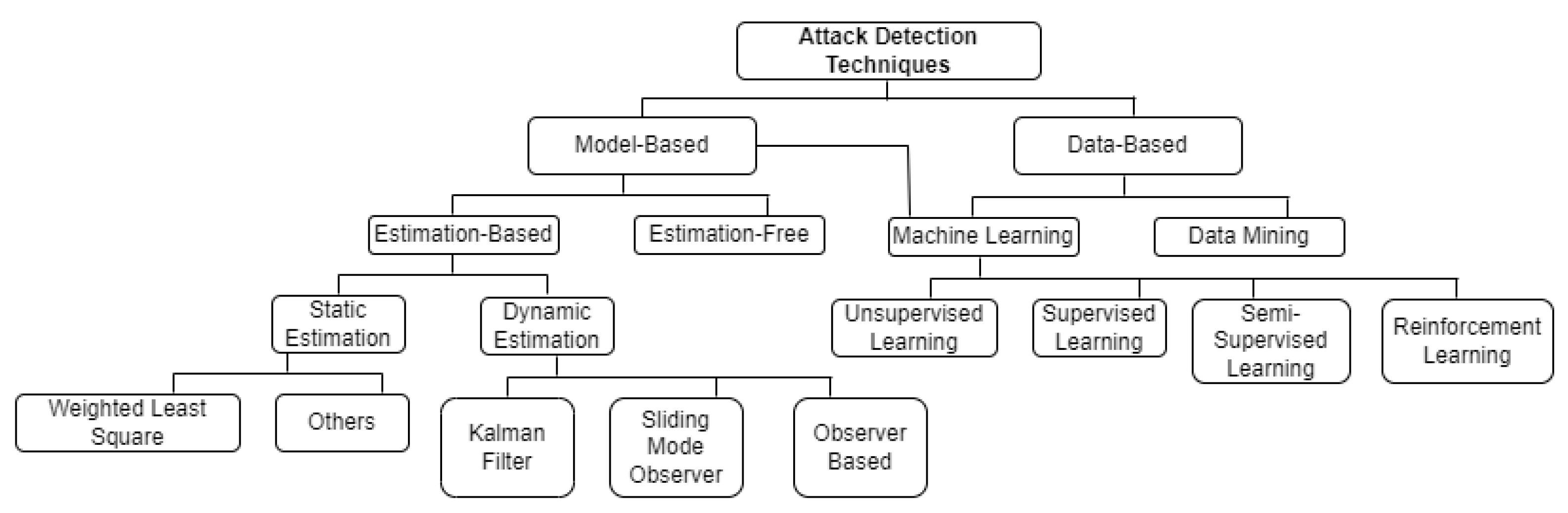
3. Cyber-Attack Detection and Mitigation Methods
3.1. Model-Based Methods
3.1.1. Kalman Filter (KF)-Based Methods
- Compromised actuator;
- Compromised physical system;
- Compromised sensor;
- Compromised actuator and physical system;
- Compromised actuator and sensor;
- Compromised physical system and sensor;
- Compromised actuator, physical system, and sensor.
3.1.2. Sliding Mode Observer Methods
3.1.3. Unknown Input Observer Methods
- ;
- () is a detectable pair, where .
3.1.4. Model-Based Machine Learning Methods
3.1.5. Advantages and Disadvantages of Model-Based Methods
3.2. Data-Driven Methods
- Data mining methods.
- Machine learning methods.
- Other methods outside of 1 and 2.
3.2.1. Data Mining Methods
3.2.2. Data-Based Machine Learning Methods
Unsupervised Learning Method
Supervised Learning Methods
Semi-Supervised Learning Method
Reinforcement Learning Methods
3.2.3. Advantages and Disadvantages of Data-Driven Methods
Advantages
- It has a more powerful ability to select informative samples.
- Although its training is slower, its prediction is faster.
- Its dependence on prior assumptions and human experiences is low.
- It is more efficient to run computationally and simple to implement.
- It depends on the I/O data and does not depend on the prior knowledge of the system in question.
- Updating the model with changing conditions over time is straightforward.
Disadvantages
- Designing a good data-driven network architecture is a huge task.
- Its statistical and physical meaning may not be very clear.
- It usually requires considerable amounts of sample data for training.
- The availability of sufficiently large empirical and historical data determines the confidence level of its predictions.
- In some instances, such as the case of a new component or system, obtaining historical data may be difficult. Some cases may require a long time and expensive tests to generate the required data.
3.3. The Role of Machine Learning Methods in Cyber Assaults
3.3.1. Analysis of Raw Data
3.3.2. Management of Alerts
3.3.3. Detection of Assaults
3.3.4. Assessment of Risk Exposure
3.3.5. Threat Intelligence
4. Industrial Review
5. Current Challenges and Future Directions
5.1. Complexity of CPS Models
5.2. Advanced Measurement and Data Collection Techniques
5.3. Detection of Advanced and Stealthy Attacks
5.4. Standardization of Security Measures for a CPS
5.5. Testing of Detection and Mitigation Methods
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AKF | Adaptive Kalman Filter |
| ANN | Artificial Neural Network |
| ASMO | Adaptive Sliding Mode Observer |
| CKF | Contrained Kalman Filter |
| CNN | Convolutional Neural Networks |
| CPS | Cyber-Physical System |
| DER | Distributed Energy Resource |
| DoS | Denial of Service |
| DSMO | Distributed Sliding Mode Observer |
| DT | Decision Tree |
| EKF | Extended Kalman Filter |
| ELM | Extreme Learning Machine |
| FDIA | False Data Injection Attack |
| IoT | Internet of Things |
| KF | Kalman Filter |
| ML | Machine Learning |
| SCADA | Supervisory Control And Data Acquisition |
| SMO | Sliding Mode Observer |
| SVM | Support Vector Machine |
| UIO | Unknown Input Observer |
| UKF | Unscented Kalman Filter |
References
- Fan, H.; Ni, M.; Zhao, L.; Li, M. Review of cyber physical system and cyber attack modeling. In Proceedings of the 2020 12th IEEE PES Asia-Pacific Power and Energy Engineering Conference (APPEEC), Nanjing, China, 20–23 September 2020; pp. 1–5. [Google Scholar]
- Liu, Y.; Peng, Y.; Wang, B.; Yao, S.; Liu, Z. Review on cyber-physical systems. IEEE/CAA J. Autom. Sin. 2017, 4, 27–40. [Google Scholar] [CrossRef]
- Lozano, C.V.; Vijayan, K.K. Literature review on cyber physical systems design. Procedia Manuf. 2020, 45, 295–300. [Google Scholar] [CrossRef]
- Ten, C.W.; Manimaran, G.; Liu, C.C. Cybersecurity for critical infrastructures: Attack and defense modeling. IEEE Trans. Syst. Man Cybern.-Part A Syst. Hum. 2010, 40, 853–865. [Google Scholar] [CrossRef]
- Franze, G.; Fortino, G.; Cao, X.; Sarne, G.M.L.; Song, Z. Resilient control in large-scale networked cyber-physical systems: Guest editorial. IEEE/CAA J. Autom. Sin. 2020, 7, 1201–1203. [Google Scholar] [CrossRef]
- Zhang, Y.; Qiu, M.; Tsai, C.W.; Hassan, M.M.; Alamri, A. Health-CPS: Healthcare cyber-physical system assisted by cloud and big data. IEEE Syst. J. 2015, 11, 88–95. [Google Scholar] [CrossRef]
- Muthuppalaniappan, M.; Stevenson, K. Healthcare cyber-attacks and the COVID-19 pandemic: An urgent threat to global health. Int. J. Qual. Health Care 2021, 33, mzaa117. [Google Scholar] [CrossRef]
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Cyber security in control of grid-tied power electronic converters—Challenges and vulnerabilities. IEEE J. Emerg. Sel. Top. Power Electron. 2019, 9, 5326–5340. [Google Scholar] [CrossRef]
- Liagkou, V.; Kavvadas, V.; Chronopoulos, S.K.C.; Tafiadis, D.; Christofilakis, V.; Peppas, K.P. Attack Detection for Healthcare Monitoring Systems Using Mechanical Learning in Virtual Private Networks over Optical Transport Layer Architecture. Computation 2019, 7, 24. [Google Scholar] [CrossRef]
- Duo, W.; Zhou, M.; Abusorrah, A. A survey of cyber attacks on cyber physical systems: Recent advances and challenges. IEEE/CAA J. Autom. Sin. 2022, 9, 784–800. [Google Scholar] [CrossRef]
- Hallaji, E.; Razavi-Far, R.; Saif, M. Detection of malicious SCADA communications via multi-subspace feature selection. In Proceedings of the 2020 International Joint Conference on Neural Networks (IJCNN), Glasgow, UK, 19–24 July 2020; pp. 1–8. [Google Scholar]
- Van Long, D.; Fillatre, L.; Nikiforov, I. Sequential monitoring of SCADA systems against cyber/physical attacks. IFAC-PapersOnLine 2015, 48, 746–753. [Google Scholar]
- Bernieri, G.; Miciolino, E.E.; Pascucci, F.; Setola, R. Monitoring system reaction in cyber-physical testbed under cyber-attacks. Comput. Electr. Eng. 2017, 59, 86–98. [Google Scholar] [CrossRef]
- Yang, L.; Cao, X.; Li, J. A new cyber security risk evaluation method for oil and gas SCADA based on factor state space. Chaos Solitons Fractals 2016, 89, 203–209. [Google Scholar] [CrossRef]
- Liu, S.; Wei, G.; Song, Y.; Liu, Y. Extended Kalman filtering for stochastic nonlinear systems with randomly occurring cyber attacks. Neurocomputing 2016, 207, 708–716. [Google Scholar] [CrossRef]
- He, H.; Yan, J. Cyber-physical attacks and defences in the smart grid: A survey. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 13–27. [Google Scholar] [CrossRef]
- Alguliyev, R.; Imamverdiyev, Y.; Sukhostat, L. Cyber-physical systems and their security issues. Comput. Ind. 2018, 100, 212–223. [Google Scholar] [CrossRef]
- Aluko, A.O.; Carpanen, R.P.; Dorrell, D.G.; Ojo, E.E. Real-Time Cyber Attack Detection Scheme for Standalone Microgrids. IEEE Internet Things J. 2022, 9, 21481–21492. [Google Scholar] [CrossRef]
- Aluko, A.; Musumpuka, R.; Dorrell, D. Cyberattack-Resilient Secondary Frequency Control Scheme for Stand-Alone Microgrids. IEEE Trans. Ind. Electron. 2022, 70, 1622–1634. [Google Scholar] [CrossRef]
- Al-Mhiqani, M.N.; Ahmad, R.; Yassin, W.; Hassan, A.; Abidin, Z.Z.; Ali, N.S.; Abdulkareem, K.H. Cyber-security incidents: A review cases in cyber-physical systems. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 499–508. [Google Scholar]
- Cardenas, A.; Amin, S.; Sinopoli, B.; Giani, A.; Perrig, A.; Sastry, S. Challenges for securing cyber physical systems. In Workshop on Future Directions in Cyber-Physical Systems Security; Citeseer: San Francisco, CA, USA, 2009; Volume 5. [Google Scholar]
- Zeller, M. Common questions and answers addressing the aurora vulnerability. In Proceedings of the DistribuTECH Conference, Tulsa, Okla, 2 February 2011. [Google Scholar]
- Case, D.U. Analysis of the cyber attack on the Ukrainian power grid. Electr. Inf. Shar. Anal. Cent. (E-ISAC) 2016, 388, 1–29. [Google Scholar]
- Loukas, G. Cyber-Physical Attacks: A Growing Invisible Threat; Butterworth-Heinemann: Oxford, UK, 2015. [Google Scholar]
- Cao, X.; Wei, C.; Li, J.; Yang, L.; Zhang, D.; Tang, G. The geological disasters defense expert system of the massive pipeline network SCADA system based on FNN. In Proceedings of the Web Technologies and Applications: APWeb 2012 International Workshops: SenDe, IDP, IEKB, MBC, Kunming, China, 11–13 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 19–26. [Google Scholar]
- Bradbury, D. The World’s Dumbest Hackers. Infosecurity 2011, 8, 16–19. [Google Scholar] [CrossRef]
- Kennedy, D.; Simon, R. Pentesting over Power lines. Defcon 2011, 2011. [Google Scholar] [CrossRef]
- Gopstein, A.; Gopstein, A.; Nguyen, C.; Byrnett, D.S.; Worthington, K.; Villarreal, C. Framework and Roadmap for Smart Grid Interoperability Standards Regional Roundtables Summary Report; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [Google Scholar]
- Stouffer, K.; Falco, J.; Kent, K. Guide to supervisory control and data acquisition (SCADA) and industrial control systems security. NIST Spec. Publ. 2006, 800, 82. [Google Scholar]
- Cardenas, A.A.; Amin, S.; Sastry, S. Secure control: Towards survivable cyber-physical systems. In Proceedings of the 2008 28th International Conference on Distributed Computing Systems Workshops, Beijing, China, 17–20 June 2008; pp. 495–500. [Google Scholar]
- Rezaee, H.; Abdollahi, F. Secure consensus control of multiagent cyber-physical systems with uncertain nonlinear models. IEEE Syst. J. 2019, 14, 3539–3546. [Google Scholar] [CrossRef]
- Gawand, H.L.; Bhattacharjee, A.; Roy, K. Securing a cyber physical system in nuclear power plants using least square approximation and computational geometric approach. Nucl. Eng. Technol. 2017, 49, 484–494. [Google Scholar] [CrossRef]
- Lyu, X.; Ding, Y.; Yang, S. Safety and security risk assessment in cyberphysical systems. IET Cyber-Phys. Syst. Theory Appl. 2019, 4, 221–232. [Google Scholar] [CrossRef]
- Catelani, M.; Ciani, L.; Luongo, V. Safety analysis in oil & gas industry in compliance with standards IEC61508 and IEC61511: Methods and applications. In Proceedings of the 2013 IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Minneapolis, MN, USA, 6–9 May 2013; pp. 686–690. [Google Scholar]
- Cheminod, M.; Durante, L.; Valenzano, A. Review of security issues in industrial networks. IEEE Trans. Ind. Inf. 2013, 9, 277–293. [Google Scholar] [CrossRef]
- Zhu, B.; Joseph, A.; Sastry, S. A taxonomy of cyber attacks on SCADA systems. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 1922 October 2011; pp. 380–388. [Google Scholar]
- Aluko, A.O.; Dorrell, D.G.; Ojo, E.E. Observer-Based Detection and Mitigation Scheme for Isolated Microgrid Under False Data Injection Attack. In Proceedings of the 2021 IEEE Southern Power Electronics Conference (SPEC), Kigali, Rwanda, 6–9 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Widergren, S.; Levinson, A.; Mater, J.; Drummond, R. Smart grid interoperability maturity model. In Proceedings of the IEEE PES General Meeting, Minneapolis, MN, USA, 25–29 July 2010; pp. 1–6. [Google Scholar]
- Guerrero, J.M.; Vasquez, J.C.; Matas, J.; De Vicuña, L.G.; Castilla, M. Hierarchical control of droop-controlled AC and DC microgrids—A general approach toward standardization. IEEE Trans. Ind. Electron. 2010, 58, 158–172. [Google Scholar] [CrossRef]
- Creery, A.; Byres, E. Industrial cybersecurity for power system and SCADA networks. In Proceedings of the Record of Conference Papers Industry Applications Society 52nd Annual Petroleum and Chemical Industry Conference, Denver, CO, USA, 12–14 September 2005; pp. 303–309. [Google Scholar]
- Dumont, D. Cyber security concerns of Supervisory Control and Data Acquisition (SCADA) systems. In Proceedings of the 2010 IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 8–10 November 2010; pp. 473–475. [Google Scholar]
- Silberschatz, A.; Galvin, P.B.; Gagne, G. Operating System Principles; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef]
- Kordestani, M.; Saif, M. Observer-based attack detection and mitigation for cyberphysical systems: A review. IEEE Syst. Man Cybern. Mag. 2021, 7, 35–60. [Google Scholar] [CrossRef]
- Filter, K.; Dmitry, Z.; Anastasiia, Y. Predicting cyber attacks on industrial systems using the Kalman filter. In Proceedings of the World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 30–31 July 2019; pp. 317–321. [Google Scholar]
- Ayyarao, S.L.; Tummala, V.; Inapakurthi, R.K. A Two-stage Kalman Filter for Cyber-attack Detection in Automatic Generation Control System. J. Mod. Power Syst. Clean Energy 2022, 10, 50–59. [Google Scholar]
- Jiang, Y.; Yang, Y.; Tan, S.C.; Hui, S.Y. Distributed sliding mode observer-based secondary control for DC microgrids under cyber-attacks. IEEE J. Emerg. Sel. Top. Circuits Syst. 2020, 11, 144–154. [Google Scholar] [CrossRef]
- Zhang, N.; Qi, W.; Pang, G.; Cheng, J.; Shi, K. Observer-based sliding mode control for fuzzy stochastic switching systems with deception attacks. Appl. Math. Comput. 2022, 427, 127153. [Google Scholar] [CrossRef]
- Luo, X.; Wang, X.; Pan, X.; Guan, X. Detection and isolation of false data injection attack for smart grids via unknown input observers. IET Gener. Transm. Distrib. 2019, 13, 1277–1286. [Google Scholar] [CrossRef]
- Alhelou, H.H.; Esmail, M.; Golshan, H.; Hatziargyriou, N.D. A Decentralized Functional Observer Based Optimal LFC Considering Unknown Inputs, Uncertainties, and Cyber-Attacks. IEEE Trans. Power Syst. 2019, 34, 4408–4417. [Google Scholar] [CrossRef]
- Qu, Z.; Bo, X.; Yu, T.; Liu, Y.; Dong, Y.; Kan, Z.; Wang, L.; Li, Y. Active and passive hybrid detection method for power CPS false data injection attacks with improved AKF and GRU-CNN. IET Renew. Power Gener. 2022, 16, 1490–1508. [Google Scholar] [CrossRef]
- Padhan, S.; Turuk, A.K. Design of False Data Injection Attacks in Cyber-Physical Systems. Inf. Sci. 2022, 608, 825–843. [Google Scholar] [CrossRef]
- Guan, Y.; Ge, X. Distributed attack detection and secure estimation of networked cyber-physical systems against false data injection attacks and jamming attacks. IEEE Trans. Signal Inf. Process. Netw. 2017, 4, 48–59. [Google Scholar] [CrossRef]
- Tu, W.; Dong, J.; Zhai, D. Optimal ϵ-stealthy attack in cyber-physical systems. J. Frankl. Inst. 2021, 358, 151–171. [Google Scholar] [CrossRef]
- Zhang, T.Y.; Ye, D. False data injection attacks with complete stealthiness in cyber–physical systems: A self-generated approach. Automatica 2020, 120, 109117. [Google Scholar] [CrossRef]
- Ding, D.; Han, Q.L.; Ge, X.; Wang, J. Secure state estimation and control of cyber-physical systems: A survey. IEEE Trans. Syst. Man Cybern. Syst. 2020, 51, 176–190. [Google Scholar] [CrossRef]
- Kwon, C.; Liu, W.; Hwang, I. Security analysis for cyber-physical systems against stealthy deception attacks. In Proceedings of the 2013 American control conference, Washington, DC, USA, 17–19 June 2013; pp. 3344–3349. [Google Scholar]
- Ye, D.; Zhang, T.Y. Summation detector for false data-injection attack in cyber-physical systems. IEEE Trans. Cybern. 2019, 50, 2338–2345. [Google Scholar] [CrossRef]
- Mo, Y.; Sinopoli, B. On the performance degradation of cyber-physical systems under stealthy integrity attacks. IEEE Trans. Autom. Control 2015, 61, 2618–2624. [Google Scholar] [CrossRef]
- Zhang, D.; Wang, Q.G.; Feng, G.; Shi, Y.; Vasilakos, A.V. A survey on attack detection, estimation and control of industrial cyber–physical systems. ISA Trans. 2021, 116, 1–16. [Google Scholar] [CrossRef]
- Manandhar, K.; Cao, X.; Hu, F.; Liu, Y. Detection of faults and attacks including false data injection attack in smart grid using Kalman filter. IEEE Trans. Control Netw. Syst. 2014, 1, 370–379. [Google Scholar] [CrossRef]
- Perruquetti, W.; Barbot, J.P. Sliding Mode Control in Engineering; Marcel Dekker: New York, NY, USA, 2002; Volume 11. [Google Scholar]
- Singh, K.; Padhy, P.K. Modified PSO based PID Sliding Mode Control using Improved Reaching Law for Nonlinear systems. arXiv 2022, arXiv:2209.09170. [Google Scholar]
- Spurgeon, S.K. Sliding mode observers: A survey. Int. J. Syst. Sci. 2008, 39, 751–764. [Google Scholar] [CrossRef]
- Nguyen, M.H.; Dao, H.V.; Ahn, K.K. Extended sliding mode observer-based high-accuracy motion control for uncertain electro-hydraulic systems. Int. J. Robust Nonlinear Control 2023, 33, 1351–1370. [Google Scholar] [CrossRef]
- Wang, H.; Shao, Y.; Zhou, S.; Zhang, C.; Xiu, N. Support Vector Machine Classifier via L_{0/1} Soft-Margin Loss. arXiv 2019, arXiv:1912.07418. [Google Scholar]
- Li, J.; Yang, D.; Su, Q. Reliable control strategy based on sliding mode observer against FDI attacks in smart grid. Asian J. Control 2022, 25, 910–920. [Google Scholar] [CrossRef]
- Adeli, M.; Hajatipour, M.; Yazdanpanah, M.J.; Hashemi-Dezaki, H.; Shafieirad, M. Optimized cyber-attack detection method of power systems using sliding mode observer. Electr. Power Syst. Res. 2022, 205, 107745. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Dörfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- An, Q.; Sun, L.; Sun, L.; Jahns, T. Low-cost diagnostic method for open-switch faults in inverters. Electron. Lett. 2010, 46, 1021–1022. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Y. A Diagnosis Method of Inverter Anomalies under DoS Attack Based on Interval Sliding Mode Observer. In Proceedings of the 2022 IEEE 5th International Conference on Industrial Cyber-Physical Systems (ICPS), Coventry, UK, 24–26 May 2022; pp. 1–6. [Google Scholar]
- Alhelou, H.H.; Golshan, M.E.H.; Hatziargyriou, N.D. Deterministic dynamic state estimation-based optimal lfc for interconnected power systems using unknown input observer. IEEE Trans. Smart Grid 2019, 11, 1582–1592. [Google Scholar] [CrossRef]
- Zhao, S.; Yu, J.; Wang, Z.; Gao, D. Unknown input observer based distributed fault detection for nonlinear multi-agent systems with probabilistic time delay. J. Frankl. Inst. 2023, 360, 1058–1076. [Google Scholar] [CrossRef]
- Chaouche, A.; Zemouche, A.; Ramdani, M.; Chaib Draa, K.; Delattre, C. Unknown input estimation algorithms for a class of LPV/nonlinear systems with application to wastewater treatment process. Proc. Inst. Mech. Eng. Part J. Syst. Control Eng. 2022, 236, 1372–1385. [Google Scholar] [CrossRef]
- Aluko, A.O.; Carpanen, R.P.; Dorrell, D.G.; Ojo, E.E. Robust state estimation method for adaptive load frequency control of interconnected power system in a restructured environment. IEEE Syst. J. 2020, 15, 5046–5056. [Google Scholar] [CrossRef]
- Zhu, F.; Fu, Y.; Dinh, T.N. Asymptotic convergence unknown input observer design via interval observer. Automatica 2023, 147, 110744. [Google Scholar] [CrossRef]
- Pan, C.; Peng, Z.; Liu, L.; D, W. Data-driven distributed formation control of under-actuated unmanned surface vehicles with collision avoidance via model-based deep reinforcement learning. Ocean Eng. 2023, 267, 113166. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.; Hyun, S.; Koo, I. Mitigating the impacts of covert cyber-attack in smart grids via reconstruction of measurement data utilizing deep denoising autoencoders. Energies 2019, 12, 3091. [Google Scholar] [CrossRef]
- Cohen, M.H.; Serlin, Z.; Leahy, K.; Belta, C. Temporal logic guided safe model-based reinforcement learning: A hybrid systems approach. Nonlinear Anal. Hybrid Syst. 2023, 47, 101295. [Google Scholar] [CrossRef]
- Guo, J.; Li, L.; Wang, J.; Li, K. Cyber-Physical System-Based Path Tracking Control of Autonomous Vehicles under Cyber-Attacks. IEEE Trans. Ind. Inform. 2022, 19, 6624–6635. [Google Scholar] [CrossRef]
- Ahmed, C.M.; Ochoa, M.; Zhou, J.; Mathur, A.P.; Qadeer, R.; Murguia, C.; Ruths, J. Noiseprint: Attack detection using sensor and process noise fingerprint in cyber physical systems. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security, Incheon, Republic of Korea, 4–8 June 2018; pp. 483–497. [Google Scholar]
- Syrmakesis, A.D.; Alhelou, H.H.; Hatziargyriou, N.D. Novel SMO-Based Detection and Isolation of False Data Injection Attacks against Frequency Control Systems. IEEE Trans. Power Syst. 2023. [Google Scholar] [CrossRef]
- Wu, C.; Dong, B.; Han, S.; Yao, W. An Optimal Sliding Mode Controller Against False Data Injection Attacks. In Proceedings of the 2022 IEEE 11th Data Driven Control and Learning Systems Conference (DDCLS), Chengdu, China, 3–5 August 2022; pp. 102–107. [Google Scholar]
- Wang, X.; Luo, X.; Zhang, M.; Jiang, Z.; Guan, X. Detection and isolation of false data injection attacks in smart grid via unknown input interval observer. IEEE Internet Things J. 2020, 7, 3214–3229. [Google Scholar] [CrossRef]
- Long, H.; Wu, Z.; Fang, C.; Gu, W.; Wei, X.; Zhan, H. Cyber-attack detection strategy based on distribution system state estimation. J. Mod. Power Syst. Clean Energy 2020, 8, 669–678. [Google Scholar] [CrossRef]
- Ye, L.; Zhu, F.; Zhang, J. Sensor attack detection and isolation based on sliding mode observer for cyber-physical systems. Int. J. Adapt. Control Signal Process. 2020, 34, 469–483. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Trans. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Naha, A.; Teixeira, A.; Ahlen, A.; Dey, S. Quickest detection of deception attacks in networked control systems with physical watermarking. arXiv 2021, arXiv:2101.01466. [Google Scholar]
- Saura, J.R.; Palacios-Marqués, D.; Ribeiro-Soriano, D. Using data mining techniques to explore security issues in smart living environments in Twitter. Comput. Commun. 2021, 179, 285–295. [Google Scholar] [CrossRef]
- Tomasevic, N.; Gvozdenovic, N.; Vranes, S. An overview and comparison of supervised data mining techniques for student exam performance prediction. Comput. Educ. 2020, 143, 103676. [Google Scholar] [CrossRef]
- Salo, F.; Injadat, M.; Nassif, A.B.; Shami, A.; Essex, A. Data mining techniques in intrusion detection systems: A systematic literature review. IEEE Access 2018, 6, 56046–56058. [Google Scholar] [CrossRef]
- Mughal, M.J.H. Data mining: Web data mining techniques, tools and algorithms: An overview. Int. J. Adv. Comput. Sci. Appl. 2018, 9. [Google Scholar] [CrossRef]
- Manjarres, A.V.; Sandoval, L.G.M.; Suárez, M.S. Data mining techniques applied in educational environments: Literature review. Digit. Educ. Rev. 2018, 33, 235–266. [Google Scholar] [CrossRef]
- Amin, M.S.; Chiam, Y.K.; Varathan, K.D. Identification of significant features and data mining techniques in predicting heart disease. Telemat. Inform. 2019, 36, 82–93. [Google Scholar] [CrossRef]
- Ishaq, A.; Sadiq, S.; Umer, M.; Ullah, S.; Mirjalili, S.; Rupapara, V.; Nappi, M. Improving the prediction of heart failure patients’ survival using SMOTE and effective data mining techniques. IEEE Access 2021, 9, 39707–39716. [Google Scholar] [CrossRef]
- Viloria, A.; Acuña, G.C.; Franco, D.J.A.; Hernández-Palma, H.; Fuentes, J.P.; Rambal, E.P. Integration of data mining techniques to PostgreSQL database manager system. Procedia Comput. Sci. 2019, 155, 575–580. [Google Scholar] [CrossRef]
- Mengash, H.A. Using data mining techniques to predict student performance to support decision making in university admission systems. IEEE Access 2020, 8, 55462–55470. [Google Scholar] [CrossRef]
- Moudoud, H.; Mlika, Z.; Khoukhi, L.; Cherkaoui, S. Detection and Prediction of FDI Attacks in IoT Systems via Hidden Markov Model. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2978–2990. [Google Scholar] [CrossRef]
- Nguyen, D.; Vadaine, R.; Hajduch, G.; Garello, R.; Fablet, R. GeoTrackNet–A Maritime Anomaly Detector Using Probabilistic Neural Network Representation of AIS Tracks and A Contrario Detection. IEEE Trans. Intell. Transp. Syst. 2021, 23, 5655–5667. [Google Scholar] [CrossRef]
- Zhao, H.; Liu, J.; Chen, H.; Chen, J.; Li, Y.; Xu, J.; Deng, W. Intelligent diagnosis using continuous wavelet transform and gauss convolutional deep belief network. IEEE Trans. Reliab. 2022, 72, 692–702. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Unsupervised machine learning-based detection of covert data integrity assault in smart grid networks utilizing isolation forest. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2765–2777. [Google Scholar] [CrossRef]
- Bergh, D.v.d.; Clyde, M.A.; Gupta, A.R.; de Jong, T.; Gronau, Q.F.; Marsman, M.; Ly, A.; Wagenmakers, E.J. A tutorial on Bayesian multi-model linear regression with BAS and JASP. Behav. Res. Methods 2021, 53, 2351–2371. [Google Scholar] [CrossRef] [PubMed]
- Amrutha, B.; Meghana, I.; Tejas, R.; Pilare, H.V.; Annapurna, D. An Efficient Automated Intrusion Detection System Using Hybrid Decision Tree. In Inventive Systems and Control; Springer: Berlin/Heidelberg, Germany, 2022; pp. 703–716. [Google Scholar]
- Chen, Y.; Zheng, W.; Li, W.; Huang, Y. Large group activity security risk assessment and risk early warning based on random forest algorithm. Pattern Recognit. Lett. 2021, 144, 1–5. [Google Scholar] [CrossRef]
- Dong, Y.; Ma, X.; Fu, T. Electrical load forecasting: A deep learning approach based on K-nearest neighbors. Appl. Soft Comput. 2021, 99, 106900. [Google Scholar] [CrossRef]
- Yan, J.; Tang, B.; He, H. Detection of false data attacks in smart grid with supervised learning. In Proceedings of the 2016 International Joint Conference on Neural Networks (IJCNN), Vancouver, BC, Canada, 24–29 July 2016; pp. 1395–1402. [Google Scholar]
- Pu, W. Shuffle GAN with autoencoder: A deep learning approach to separate moving and stationary targets in SAR imagery. IEEE Trans. Neural Netw. Learn. Syst. 2021, 33, 4770–4784. [Google Scholar] [CrossRef]
- Manoharan, J.S. Study of variants of Extreme Learning Machine (ELM) brands and its performance measure on classification algorithm. J. Soft Comput. Paradig. (JSCP) 2021, 3, 83–95. [Google Scholar]
- Onaolapo, A.K.; Carpanen, R.P.; Dorrell, D.G.; Ojo, E.E. A Comparative Assessment of Conventional and Artificial Neural Networks Methods for Electricity Outage Forecasting. Energies 2022, 15, 511. [Google Scholar] [CrossRef]
- Onaolapo, A.K.; Carpanen, R.P.; Dorrell, D.G.; Ojo, E.E. Event-Driven Power Outage Prediction using Collaborative Neural Networks. IEEE Trans. Ind. Inform. 2022, 19, 3079–3087. [Google Scholar] [CrossRef]
- Onaolapo, A.; Carpanen, R.P.; Dorrell, D.; Ojo, E. Forecasting Electricity Outage in KwaZulu-Natal, South Africa using Trend Projection and Artificial Neural Networks Techniques. In Proceedings of the 2021 IEEE PES/IAS PowerAfrica, Virtual, 23–27 August 2021; pp. 1–5. [Google Scholar]
- Onaolapo, A.K.; Carpanen, R.P.; Dorrell, D.G.; Ojo, E.E. Transmission line fault classification and location using multi-layer perceptron artificial neural network. In Proceedings of the IECON 2020 the 46th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 18–21 October 2020; pp. 5182–5187. [Google Scholar]
- Onaolapo, A.; Pillay-Carpanen, R.; Dorrell, D.; Ojo, E. A Comparative Evaluation of Conventional and Computational Intelligence Techniques for Forecasting Electricity Outage. In Proceedings of the 2021 Southern African Universities Power Engineering Conference/Robotics and Mechatronics/Pattern Recognition Association of South Africa (SAUPEC/RobMech/PRASA), Potchefstroom, South Africa, 27–29 January 2021; pp. 1–6. [Google Scholar]
- Sarvamangala, D.; Kulkarni, R.V. Convolutional neural networks in medical image understanding: A survey. Evol. Intell. 2022, 15, 1–22. [Google Scholar] [CrossRef]
- Srinidhi, C.L.; Ciga, O.; Martel, A.L. Deep neural network models for computational histopathology: A survey. Med Image Anal. 2021, 67, 101813. [Google Scholar] [CrossRef]
- Qi, R.; Rasband, C.; Zheng, Z.; Longoria, R. Detecting Cyber Attacks in Smart Grids Using Semi-Supervised Anomaly Detection and Deep Representation Learning. Information 2021, 12, 328. [Google Scholar] [CrossRef]
- Le, D.C.; Zincir-Heywood, N.; Heywood, M. Training regime influences to semi-supervised learning for insider threat detection. In Proceedings of the IEEE Symposium on Security and Privacy Workshops, San Francisco, CA, USA, 27–27 May 2021; pp. 1–14. [Google Scholar]
- Parizad, A.; Hatziadoniu, C. A Laboratory Set-Up for Cyber Attacks Simulation Using Protocol Analyzer and RTU Hardware Applying Semi-Supervised Detection Algorithm. In Proceedings of the IEEE Texas Power and Energy Conference, College Station, TX, USA, 2–5 February 2021; pp. 1–6. [Google Scholar]
- Gronauer, S.; Diepold, K. Multi-agent deep reinforcement learning: A survey. Artif. Intell. Rev. 2022, 55, 895–943. [Google Scholar] [CrossRef]
- Liu, P.; Wang, L.; Ranjan, R.; He, G.; Zhao, L. A Survey on Active Deep Learning: From Model Driven to Data Driven. ACM Comput. Surv. (CSUR) 2022, 54, 1–34. [Google Scholar] [CrossRef]
- Sutharssan, T.; Stoyanov, S.; Bailey, C.; Yin, C. Prognostic and health management for engineering systems: A review of the data-driven approach and algorithms. J. Eng. 2015, 2015, 215–222. [Google Scholar] [CrossRef]
- Zhang, Y.; Wu, J.; Li, N.; Li, S.; Li, K. Data-driven water supply systems modelling. In Proceedings of the 2013 9th Asian Control Conference (ASCC), Istanbul, Turkey, 23–26 June 2013; pp. 1–6. [Google Scholar]
- De Cauwer, C.; Verbeke, W.; Coosemans, T.; Faid, S.; Van Mierlo, J. A data-driven method for energy consumption prediction and energy-efficient routing of electric vehicles in real-world conditions. Energies 2017, 10, 608. [Google Scholar] [CrossRef]
- Alhelou, H.H.; Cuffe, P. A Dynamic-State-Estimator-Based Tolerance Control Method Against Cyberattack and Erroneous Measured Data for Power Systems. IEEE Trans. Ind. Inform. 2021, 18, 4990–4999. [Google Scholar] [CrossRef]
- Driss, M.; Almomani, I.; Ahmad, J. A federated learning framework for cyberattack detection in vehicular sensor networks. Complex Intell. Syst. 2022, 8, 4221–4235. [Google Scholar] [CrossRef]
- Stănculescu, M.; Deleanu, S.; Andrei, P.C.; Andrei, H. A case study of an industrial power plant under cyberattack: Simulation and analysis. Energies 2021, 14, 2568. [Google Scholar] [CrossRef]
- Kaddoura, S.; Haraty, R.A.; Al Kontar, K.; Alfandi, O. A parallelized database damage assessment approach after cyberattack for healthcare systems. Future Internet 2021, 13, 90. [Google Scholar] [CrossRef]
- Ghafur, S.; Kristensen, S.; Honeyford, K.; Martin, G.; Darzi, A.; Aylin, P. A retrospective impact analysis of the WannaCry cyberattack on the NHS. NPJ Digit. Med. 2019, 2, 1–7. [Google Scholar] [CrossRef]
- Huma, Z.E.; Latif, S.; Ahmad, J.; Idrees, Z.; Ibrar, A.; Zou, Z.; Alqahtani, F.; Baothman, F. A hybrid deep random neural network for cyberattack detection in the industrial internet of things. IEEE Access 2021, 9, 55595–55605. [Google Scholar] [CrossRef]
- Kong, P.Y. A Survey of Cyberattack Countermeasures for Unmanned Aerial Vehicles. IEEE Access 2021, 9, 148244–148263. [Google Scholar] [CrossRef]
- Zhou, C.; Hu, B.; Shi, Y.; Tian, Y.C.; Li, X.; Zhao, Y. A unified architectural approach for cyberattack-resilient industrial control systems. Proc. IEEE 2020, 109, 517–541. [Google Scholar] [CrossRef]
- Narasimhan, S.; El-Farra, N.H.; Ellis, M.J. Active multiplicative cyberattack detection utilizing controller switching for process systems. J. Process Control 2022, 116, 64–79. [Google Scholar] [CrossRef]
- Sabeel, U.; Heydari, S.S.; Elgazzar, K.; El-Khatib, K. Building an intrusion detection system to detect atypical cyberattack flows. IEEE Access 2021, 9, 94352–94370. [Google Scholar] [CrossRef]
- Yen, T.; Oprea, A.; Onarlioglu, K.; Leetham, T.; Robertson, W.; Juels, A.; Kirda, E. Beehive: Large-scale log analysis for detecting suspicious activity in enterprise networks. In Proceedings of the CAnnual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 199–208. [Google Scholar]
- Du, M.; Li, F.; Zheng, G.; Srikumar, V. Deeplog: Anomaly detection and diagnosis from system logs through deep learning. In Proceedings of the Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; pp. 1285–1298. [Google Scholar]
- Apruzzese, G.; Marchetti, M.; Colajanni, M.; Zoccoli, G.G.; Guido, A. Identifying Malicious Hosts Involved in Periodic Communications. In Proceedings of the IEEE International Symposium on Network Computing Applications, Cambridge, MA, USA, 30 October–1 November 2017; pp. 1–8. [Google Scholar]
- Yagemann, C.; Pruett, M.; Chung, S.P.; Bittick, K.; Saltaformaggio, B.; Lee, W. ARCUS: Symbolic Root Cause Analysis of Exploits in Production Systems. In Proceedings of the Usenix Secur. Symp., virtual, 11–13 August 2021; pp. 1–19. Available online: https://www.usenix.org/conference/usenixsecurity21/presentation/yagemann (accessed on 10 May 2023).
- Apruzzese, G.; Laskov, P. The Role of Machine Learning in Cybersecurity. pp. 1–38. Available online: https://scholar.google.co.za/scholar?hl=en&as_sdt=0%2C5&q=The+Role+of+Machine+Learning+in+Cybersecurity+&btnG= (accessed on 29 May 2023).
- Su, Y.; Cheng, M.; Cho, Y.; Huang, H. False Alert Buster: An Adaptive Approach for NIDS False Alert Filtering. In Proceedings of the 2nd International Conference on Computing and Big Data, Taichung, Taiwan, 18–20 October 2019; pp. 58–62. [Google Scholar]
- Vidovic, K.; Tomicic, I.; Slovenec, K.; Mikus, M.; Braidic, I. Ranking Network Devices for Alarm Prioritisation: Intrusion Detection Case Study. In Proceedings of the IEEE SoftCOM, Split, Hvar, Croatia, 23–25 September 2021; pp. 1–5. [Google Scholar]
- Okutan, A.; Yang, S.J. ASSERT: Attack synthesis and separation with entropy redistribution towards predictive cyber defense. Cybersecurity 2021, 2, 1–18. [Google Scholar] [CrossRef]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Onaolapo, A.K.; Akindeji, K.T. Application of Artificial Neural Network for Fault Location in Distribution Network. In Proceedings of the Southern African Universities Power Engineering Conference, Bloemfontein, South Africa, 28-30 January 2019; pp. 299–304. [Google Scholar]
- Ghanem, M.C.; Chen, T.M. Reinforcement learning for intelligent penetration testing. In Proceedings of the IEEE World Conference on Smart Trends in Systems, Security and Sustainability, London, UK, 30–31 October 2018; pp. 185–192. [Google Scholar]
- Uwagbole, S.O.; Buchanan, W.J.; Fan, L. Applied machine learning predictive analytics to SQL injection attack detection and prevention. In Proceedings of the IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 1087–1090. [Google Scholar]
- Xu, T.; Goossen, G.; Cevahir, H.K.; Khodeir, S.; Jin, Y.; Li, F.; Shan, S.; Patel, S.; Freeman, D.; Pearce, P. Deep entity classification: Abusive account detection for online social networks. In Proceedings of the USENIX Security Symposium, Online, 11–13 August 2021; pp. 1–18. [Google Scholar]
- Biggio, B.; Roli, F. Wild patterns: Ten years after the rise of adversarial machine learning. Elsevier Pattern Recognit. 2018, 84, 317–331. [Google Scholar] [CrossRef]
- Sweet, C.; Moskal, S.; Yang, S.J. On the Variety and Veracity of Cyber Intrusion Alerts Synthesized by Generative Adversarial Networks. ACM Trans. Manag. Inf. Syst. 2020, 11, 1–21. [Google Scholar] [CrossRef]
- Nadeem, A.; Verwer, S.; Moskal, S.; Yang, S.J. Alert-driven Attack Graph Generation using S-PDFA. IEEE Trans. Dependable Secur. Comput. 2021, 19, 731–746. [Google Scholar] [CrossRef]
- Chua, Z.L.; Shen, S.; Saxena, P.; Liang, Z. Neural nets can learn function type signatures from binaries. In Proceedings of the USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 99–116. [Google Scholar]
- Kang, C.; Park, N.; Prakash, B.A.; Serra, E.; Subrahmanian, V.S. Ensemble models for data-driven prediction of malware infections. In Proceedings of the ACM International Conference on Web Search and Data Mining, San Francisco, CA, USA, 22–25 February 2016; pp. 583–592. [Google Scholar]
- Engströma, V.; Lagerströma, R. Two decades of cyberattack simulations: A systematic literature review. Comput. Secur. 2022, 116, 102681. [Google Scholar] [CrossRef]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M. A review of machine learning approaches to power system security and stability. IEEE Access 2020, 8, 113512–113531. [Google Scholar] [CrossRef]
- Setola, R.; Faramondi, L.; Salzano, E.; Cozzani, V. An overview of cyber attack to industrial control system. Chem. Eng. Trans. 2019, 77, 907–912. [Google Scholar]
- Al-Abassi, A.; Karimipour, H.; Dehghantanha, A.; Parizi, R.M. An ensemble deep learning-based cyber-attack detection in industrial control system. IEEE Access 2020, 8, 83965–83973. [Google Scholar] [CrossRef]
- Kayan, H.; Nunes, M.; Rana, O.; Burnap, P.; Perera, C. Cybersecurity of industrial cyber-physical systems: A review. ACM Comput. Surv. (CSUR) 2022, 54, 1–35. [Google Scholar] [CrossRef]
- Ani, U.P.D.; He, H.; Tiwari, A. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. J. Cyber Secur. Technol. 2017, 1, 32–74. [Google Scholar] [CrossRef]
- Zhang, F.; Coble, J.B. Robust localized cyber-attack detection for key equipment in nuclear power plants. Prog. Nucl. Energy 2020, 128, 103446. [Google Scholar] [CrossRef]
- Dhirani, L.L.; Armstrong, E.; Newe, T. Industrial IoT, cyber threats, and standards landscape: Evaluation and roadmap. Sensors 2021, 21, 3901. [Google Scholar] [CrossRef] [PubMed]
- Li, Y.; Liu, Q. A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments. Energy Rep. 2021, 7, 8176–8186. [Google Scholar] [CrossRef]
- Liu, G.X.; Shi, L.F.; Chen, S.; Wu, Z.G. Focusing matching localization method based on indoor magnetic map. IEEE Sens. J. 2020, 20, 10012–10020. [Google Scholar] [CrossRef]
- Onaolapo, A.K. Reliability Study under the Smart Grid Paradigm Using Computational Intelligent Techniques and Renewable Energy Sources. Ph.D. Thesis, University of KwaZulu-Natal, Durban, South Africa, 2022; pp. 1–181. [Google Scholar]
- Adefarati, T.; Sharma, G.; Onaolapo, A.K.; Njepu, A.; Akindeji, K.T.; Oladejo, S.O.; Obikoya, G.D.; Adeyanju, I. Optimal design and techno-economic analysis of a grid-connected photovoltaic and battery hybrid energy system. Int. J. Eng. Res. Afr. 2022, 60, 125–154. [Google Scholar] [CrossRef]
- Adefarati, T.; Obikoya, G.D.; Onaolapo, A.K.; Njepu, A. Design and analysis of a photovoltaic-battery-methanol-diesel power system. Int. Trans. Electr. Energy Syst. (ITEES) 2021, 31, e12800. [Google Scholar] [CrossRef]
- Onaolapo, A.K.; Ojo, E.E. Effects of Upside Risk on Microgrids’ Reliability Considering the COVID-19 Pandemic. In Proceedings of the Southern African Universities Power Engineering Conference (SAUPEC), Durban, South Africa, 25–27 January 2022; pp. 1–6. [Google Scholar]
- Onaolapo, A.K.; Sharma, G.; Sharma, S.; Adefarati, T. The Economic Feasibility and Cost Reduction of Grid-linked Solar PV Systems in South Africa. In Proceedings of the International Conference on Innovative Sustainable Computational Technologies (CISCT), Dehradun, India, 23–24 December 2022; pp. 1–5. [Google Scholar]
- Adefarati, T.; Obikoya, G.D.; Sharma, G.; Onaolapo, A.K.; Akindeji, K.T. Design and Feasibility Analysis of Grid-Connected Hybrid Renewable Energy System: Perspective of Commercial Buildings. Energy Syst. 2023, 1–60. [Google Scholar] [CrossRef]
| Reference | Method | System | Attack Type/Mode | Attacked Element | Detection Accuracy/Rate | Measures |
|---|---|---|---|---|---|---|
| [80] | EKF | Automotive Systems | DoS FDIA | Path Tracking: control of autonomous vehicles | High | Detection and isolation |
| [81] | KF | Industrial Control Systems (ICS) | Zero-Alarm | Sensor | 90 % | Detection |
| [82] | Sliding Mode Observer | Power Systems | FDIA | Load Frequency Control System | High | Detection and isolation |
| [83] | Optimal Sliding mode observer | Magneti-Tape-Drive Servo System | FDIA | Actuators | High | Detection |
| [84] | UI Interval Observer-Based | Smart Grid | FDIA | Smart Sensor | - | Detection and isolation |
| [49] | UI Observer-Based | DC Micro-Grid | FDIA | Phasor Measurement Unit (PMU) | - | Detection and isolation |
| [85] | Distribution System State Estimation (DSSE) | Power System | Generic | - | High ≈ 100% | Detection |
| [86] | Sliding Mode Observer | Generic Sub-System | FDIA | Sensor | - | Detection and mitigation |
| [87] | Weighted Least Square (WLS) | Smart Grid | FDIA | - | High | Detection |
| [88] | Watermarking | Control System | DoS | Sensor Attack | High | Detection |
| Reference | Method | System | Attack Type/Mode | Attack Parameter | Detection Accuracy/Rate | Measures |
|---|---|---|---|---|---|---|
| [124] | Dynamic-Estimator- Based Cyber-Attack Tolerant Control (CTC) | Power Systems | Generic (malware attacks, password attacks, phishing attacks, and SQL injection attacks) | - | Estimation error ; norm order , which is . | Detection and isolation |
| [125] | Federated Learning, (Gated Recurrent Units and Random Forest) | Vehicular Sensor Networks (VSN) | Intrusion | Car Hacking: Attack and Defense Challenge 2020 dataset. | 99.52% and 99.77% | Detection |
| [126] | Short Circuit Analysis | Industrial Power Plants | Short-Circuiting | Equipment (transformer, breaker, generator, etc.) security breach | High | Detection |
| [127] | Parallelized Database Approach | Healthcare Systems | Malicious transactions, damage | Damage assessment | High | Detection and isolation. |
| [128] | Retrospective Impact Analysis | National Health Service (NHS) | WannaCry attack, ransomware attack. | Missed appointments, deaths, and fiscal costs attributable to the ransomware | High | Detection |
| [129] | A Hybrid Deep Random Neural Network | Industrial Internet of Things (IIoT) | Generic | Two IIoT security-related datasets | 98% and 99% | Detection |
| [130] | Survey | Unmanned Aerial Vehicles (UAV) | Channel jamming, message interception, deletion, injection, spoofing, etc. | Cyberattack counter-measures | - | Prevention, detection, and mitigation |
| [131] | Unified Architectural Approach | Industrial Control Systems (ICSs) | Generic | Cyberattack resilience | High | - |
| [132] | Controller Switching | Process Control System (PCS) | Multiplying the data communicated over the link by a factor | Control system and attack-sensitive parameters | High | Detection |
| [133] | AI Engine, Two-Fold Feature Selection, and Hyper-Parameter Optimization | Network Traffic System | Intrusion | Binary attack, synthesized atypical attack flows | 90% | Detection |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mtukushe, N.; Onaolapo, A.K.; Aluko, A.; Dorrell, D.G. Review of Cyberattack Implementation, Detection, and Mitigation Methods in Cyber-Physical Systems. Energies 2023, 16, 5206. https://doi.org/10.3390/en16135206
Mtukushe N, Onaolapo AK, Aluko A, Dorrell DG. Review of Cyberattack Implementation, Detection, and Mitigation Methods in Cyber-Physical Systems. Energies. 2023; 16(13):5206. https://doi.org/10.3390/en16135206
Chicago/Turabian StyleMtukushe, Namhla, Adeniyi K. Onaolapo, Anuoluwapo Aluko, and David G. Dorrell. 2023. "Review of Cyberattack Implementation, Detection, and Mitigation Methods in Cyber-Physical Systems" Energies 16, no. 13: 5206. https://doi.org/10.3390/en16135206
APA StyleMtukushe, N., Onaolapo, A. K., Aluko, A., & Dorrell, D. G. (2023). Review of Cyberattack Implementation, Detection, and Mitigation Methods in Cyber-Physical Systems. Energies, 16(13), 5206. https://doi.org/10.3390/en16135206







