1. Introduction
The nodes of the Mobile Ad-hoc Network (MANET) are the group of self-organized mobile nodes that are deployed randomly without predefined models. These mobile nodes follow adhoc modelling for data communication in the absence of a router or any centralized devices. MANETs are widely applied for observing terrestrial abnormalities such as earthquakes, forest disasters and other natural disasters. Generally, MANETs are deployed with a vast amount of adhoc nodes to cover a wide range of geographical areas to detect notable natural objects. In this case, the Internet of Things (IoT) is considered a decentralized MANET environment. IoT base is required to take MANET observations into the internet domain, or any processing node (cloud system) deployed outside the local network domain. In the same manner, WSN is a type of network that contains resource-limited sensor nodes with a homogeneous type of internal components. In this work, WSN has mostly energy-limited sensor nodes than MANET nodes. In addition, sensor nodes deployed under the WSN environment need a gateway node to reach the outer network. The combination of MANET and WSN under an IoT environment creates heterogeneous network characteristics. Under this environment, energy optimization and routing protocol optimization are challenging tasks. This work takes this challenging research problem to be solved.
The MANET topology changes dynamically between multiple nodes, Jamali et al. [
1] and Devi et al. [
2]. The routing protocols are providing a route from source to destination. At the same time, various types of routing attacks in the network are reducing the performance of the network and minimizing the rate of transferred packets from sender to receiver, Kumar Debnath et al. [
3]. This kind of problem can be solved using the trust route method. Initially, available routes are identified using the route discovery process. Finally, the best and trusted route is selected from the available routes with the support of optimization techniques. WSN nodes are spatially dispersed and linked to the wireless medium, Hu, Z et al. [
4]. The sensors collect data from the physical environment and transmit the data to a centralised location, Khokhlachova et al. [
5]. The nodes of the IoT environment can collect, control and monitor environmental data such as weather, forecast, object detection, gas leakage, etc. In an IoT environment, the collected information is stored and processed in the cloud system.
The MANET carries more data than the WSN, but the WSN consists of more sensors than the MANET, Ray, S et al. [
6] and Jayalakshmi et al. [
7]. The number of WSN sensor nodes is static and sensor nodes consume less energy than a MANET node. In contrast, node mobility is higher in MANET than in WSN. The MANET provides better power utilization and increases network lifetime through various energy-saving routing algorithms. The MANET is a special network, it utilizes less amount of energy with good scalability. In a MANET, the energy-saving mode increases the lifetime of each node’s energy level and controls energy utilization by the appropriate selection of the energy-saving algorithm.
The MANET connects the nodes to the Internet through the gateway node. The gateway node acts as a connector to connect the MANET node to the Internet. The source MANET node is connected directly to the gateway node, or connected to the gateway node with the support of the adjacent node. The gateway node connects the different networks by MANET routing protocol and DNS server.
In this paper, the destination node gathers all of the sensor nodes’ details, like protocol address, position and mobility rate (meters/second) in MANET. Here, IoT communication is established by WSN, MANET and the Internet. Consequently, this kind of network is represented as a heterogeneous network. The source sensor nodes detect the physical information and transfer the data to destinations through a multi-hop fashion. The clustering method is used to form the MANET. The cluster node reduces power wastage while transmitting and receiving the data. Finally, the data is forwarded to the gateway node to reach the internet server point. The gateway node is connected to a cloud network and the cloud system collects the data and stores the details.
The following conditions are considered in the research:
Cluster Network: More than one sensor node is connected as a cluster in the MANET. Each cluster is connected through a selected cluster head.
Routing Protocol: MANET considers an optimized routing protocol to determine the shortest route between sensors to the gateway node.
Internet and IoT: Data collected from various nodes are stored in the internet cloud server.
The IoT is a recent technology widely applied in this electronic world. Generally, the open wireless medium has poor security and utilizes more energy to sense the data and transmit the data to the nearest gateway. The recent works developed for wireless data communication use secure internet protocol functions and transport layer functions. In this network, neighbouring sensor nodes are formed into a small group by one MANET node is called a cluster network. In the cluster, MANET nodes act as cluster heads (CH) to forward the information between sensors. This cluster formation is reducing the bandwidth utilization rate and increasing the sensor node’s lifespan. In addition, MANET is creating a trusted route and shortest route between sensors in the Internet Cloud.
Generally, clusters are created in MANET to easily organise the topology. In this manner, recent techniques use various energy-efficient clustering approaches for improving the performance of routing protocol. On the scope, clustering algorithms such as Low Energy Adaptive Clustered Hierarchy (LEACH) is a well-known algorithm for choosing the cluster heads based on optimal energy constraints. LEACH is a cluster formation protocol in a tree-based (hierarchical) network environment. Notably, the clusters of mobile nodes or sensor nodes are formed under the base station (centralized control centre). Clusters of nodes under each base station provide hierarchical network architecture. The IoT environment of cluster nodes can communicate with other cluster nodes through a centralized base station (control unit). In this case, cluster heads (nodes with the highest residual energy) can reach the base station for communicating the data [
8].
In the same manner, real-time challenges and flat architectures in making MANET clusters are significantly noted by various research works. Unlike hierarchical IoT structures, flat network clusters can be formed for the distributed scenario. Particularly, flat networks deploy multiple gateway nodes for collecting the field node’s data through cluster heads. The chosen gateway nodes are deployed in each cluster. In this method, cluster heads and other cluster nodes that are nearer to gateway nodes of neighbour clusters can communicate with each other. This kind of mechanism reduces energy overhead happens in each cluster head. Thus, the effective formation of clusters creates a crucial impact on energy-efficient data communication in IoT environments (hierarchical and flat networks) [
9].
In this article, the MANET-ESO performance in the IoT environment is experimented with using the modules such as clustering principles, MANET-based on-demand routing process, IoT data collection process and trusted route establishment policies.
The simulation environment is created by MANET mobile nodes and Wireless sensor nodes with Internet (cloud network). The Sensor nodes are divided into small clusters and grouped by Mobile Ad-hoc nodes. Upon the validation of energy levels, nodes are assigned as CH to control sensor nodes. The routes are discovered from the sensor source to the gateway node with the help of the MANET cluster and on-demand routing protocol. The best route is evaluated by the total energy of the route, time is taken from source to destination and minimum hop count. In this method, IoT communication is stabilized over a long period of time using node energy level. In this case, the trust validation algorithm improves the packet delivery ratio, throughput, and reduces the routing overhead of the selected route among clusters.
The rest of this paper follows as:
Section 2 expresses the literature review of problem formulation.
Section 3 offers suggestions for network topology measurement tools.
Section 4 describes the suggested approach for heterogeneity network utilising MANET-ESO in IoT Algorithm. The simulation and algorithm results are discussed with various parameters in
Section 5.
Section 6 is concluding the article with future work.
2. Literature Survey
To enhance the performance of MANET and IoT environments, the authors suggest a new routing protocol. The existing techniques are compared in this section. The Dynamic Critical Node Identification (DCNI) method was suggested by the authors Jayalakshmi et al. [
7] and Hou, Y.T. et al. [
10], who also identified the MANET-IoT network critical nodes. In this section, the currently used methods are contrasted. The DCNI approach controls the dynamically changing topology to identify fusion nodes in one topology. The outcome of DCNI supports the identification of the crucial nodes and results with enhanced quality and time complexity. However, only simple DOS attacks were used to evaluate the DCNI technique, Alam et al. [
11]. The author Niu Z et al. [
12] and Narayandas et al. [
13] discusses the operation of MANET systems in IoT. This is a basic MANET with an IoT technique that already exists. This technology uses programmers to run the MANET, where some systems have more end devices.
The Dynamic Range Clustering (DRC) method with a learning-based routing scheme implements the load balancing strategies that are optimising the performance of MANETs, Aroulanandam V et al. [
14] (LR). The management of network data and energy is improved by this strategy. The cluster has increased network stability with distinctive neighbours for learning-based routing and enabled non-congested data transformation at various network traffic rates. Because of the dynamic topology, the LR method’s delay time is getting longer.
A new multi-objective scheme in a heterogeneous network is introduced as a multi-characteristics model by Amiri et al. [
15]. This scheme achieves better throughput, energy usage, packet delivery ratio, fewer dead nodes throughout more rounds, and increased network lifetime. Using various network metrics, the cluster creates the network path and transfers the data from the source node to the neighbour node. However, large routing networks have little fault tolerance and significant delay times in this case.
To avoid the pitfall of becoming stuck in local optima, the author devised the Energy Efficient Cluster Head Selection Using Improved Sparrow Search Algorithm (EECHS–ISSA–DE), Kathiroli et al. [
16] method. Based on residual energy, this algorithm chooses CH. Although the CH is not distributed evenly, stability is good. This algorithm’s results for handling vast amounts of data take less time, and the crossover and CH selection procedures are enhanced. Nonetheless, the breadth and connectivity of this approach are crucial. In WSN, the Butterfly and Ant approach is suggested by Maheswari et al. [
17]. In WSN, route generation and the best CH selection are challenging tasks. The path is chosen based on the nodes’ energy, their distance from one another and the base station and the node’s degree. This methodology’s simulation results are taken into account for the local base station and global network.
To choose the best energy-saving nodes, the author Rajpoot et al. [
18] proposed a modified Bellman-Ford algorithm. This algorithm was tested in both static and dynamic networks. This scheme found that the static network provided accuracy between 34 and 48 percent and the dynamic network provided energy savings between 35 and 42 percent. However, we found that the amount of energy saved depends on the network’s size. In addition, routing protocols play a major role in energy-saving plans. In comparison, Adhoc On-Demand Routing Protocol (AODV) and Energy Quantized (EQ-AODV) routing protocols, the Energy Efficient AODV (EE-AODV) in Mobile Ad-hoc network has increased the energy level of the nodes. Since the ties in this protocol are less stable, the scientists intend to use a genetic algorithm to strengthen the links in their subsequent work.
Li Y et al. [
19] proposed a novel EED algorithmic approach. The authors used two parameters such as hop count and residual node energy to estimate an optimal load distribution-based routing mechanism. This work expected the outcomes like optimal energy usage, maximum packet delivery ratio and maximum network lifetime. However, this method implemented a load-balancing routing mechanism to the MANET without considering IoT.
In the description of Er-rouidi M et al. [
20], MANET and IoT networks with energy optimization rules are suggested to increase network efficiency. Additionally, the improved cluster method for a heterogeneous network uses the sensor node energy level to determine the route. Due to insufficient load balancing, the tiny size of a node in the network consumes more battery power than the huge size of the network.
Similarly, Vu Q.K. et al. [
21] found energy efficiency and safe weight of the cluster approach when MANET and WSN are combined. In this work, all routes’ costs are represented by the cluster-weighted values from the sources to the receiver. In MANET, the dynamic genetic algorithm is utilised to determine the dynamic topology based on the many node characteristics of power, position, availability, and latency, Bruzgiene R et al. [
22] Chatterjee B et al. [
23]. This approach is one of the path-finding optimization techniques. However, in a large-scale network, the network’s accuracy is lower. The aforementioned existing algorithm has improved network performance using a variety of techniques such as residual energy calculation and clustering procedures. It has also optimized packet loss, hop count, distance, increased throughput, and packet delivery ratio. It has also formed a heterogeneous network with low cost and high performance. However, in this approach, every author focuses on a distinct characteristic and omitting any one of the crucial ones has decreased the service’s quality.
The existing works are formed by heterogeneous networks with different algorithms, like cluster creation and genetic algorithms, to improve the performance of the network. However, the existing work has not fulfilled the expectations. Some clustering algorithms do not distribute clusters evenly, consequently, CH energy is drained soon. The genetic algorithm saves the network energy but has less fault tolerance and a high time delay.
In this proposed work, the energy utilisation of network nodes is improved using clustering, S. Sugumaran et al. [
24] and a trust route selection method. The nodes in the network are divided into small segments using cluster techniques. The cluster nodes are formed by mobile ad-hoc nodes and sensors. The sensors are linked to neighbouring mobile ad-hoc nodes. The node with more sensors is elected as CH. Otherwise, the mobile ad-hoc node is acting as an adjacent node between the sensor (source) and destination. The CH is re-elected by the residual energy of the node. The route discovery process Kanthe A.M et al. [
25] is selecting the different routes from source to destination. However, the best and trusted route is evaluated by the total energy utilisation of the nodes, and the distance between the source and destination, S. Sugumaran et al. [
26]. This type of route selection provides a better result in terms of saving the total energy of the route, Lorincz et al. [
27] under both malicious (DoS) and non-malicious conditions.
3. The Measurement Tools of Network Topology
The clustering techniques manage the large size of the network effect and control traffic and improve the energy level of each node. Faulty nodes can be easily identified in a cluster and automatically replaced by a suitable algorithm. In the cluster network, Venkatasubramanian et al. [
28], the graphical method G (N, E) is represented. Here, N is the number of nodes in the cluster, and E is the total energy utilized to transmit the packet from node i to j and i,j ∈ N. CH energy is evaluated by the residual energy of the node E
Ri. The residual energy E
Ri is calculated from the total energy of the node to the utilized energy of the node and distance d
ij is equal to the velocity of sending the packet to the time required to send all the packets from i to j. The Energy required to transmit one packet E
p and a Total number of packets P
n.
The data packet travels from one sensor node to another sensor node and is significantly observed in the network. Particularly, the data throughput of the network is evaluated from the amount of data transferred between the source and destination within a second.
The time, S. Sugumaran et al. [
29] is considered depending on the state of the node. At some point, the node acts as inactive, sleeping and idle. The total time is regarded as,
In active mode, nodes start to transfer and receive the packet with less delay. But few nodes enter sleep mode because of a less level of energy and other nodes act in idle mode. It takes a bit more time to complete the packet transmission and receive, S. Sugumaran et al. [
29]. The active time is evaluated by the total bandwidth of the sender-to-receiver channel and the total number of nodes within a network
Distance is very important in the routing algorithm; the shorter distance brings the data to the destination in less time. In this work, the distance is calculated as the sum of the distance between the adjacent node from i to j, and the total transfer and receive time of the packet. The bandwidth, S M, B et al. [
30] is the capability of the route to take the data
The total residual energy, S M, B et al. [
30] of the network is taken into account by the energy of the cluster network and the remaining energy of the MANET route.
where r is the route between the sender and destination, and E
CH is CH residual energy. The MANET discovered the route’s residual energy determined by the sum of the energy level between the adjacent links. The energy level of each link is calculated from the residual energy of the packet sent and received. The hop count of the source sensor node to the destination node is evaluated on all the discovered routes in MANET. The hop count is evaluated between the adjacent sequential nodes from the sensor to the destination. Sequential count details are collected from the route discovery process. Different types of routing algorithms provide more than one number of routes to reach the gateway node discovered by any one of the routing algorithms. However, the trusted route (R
t) offers long life, less time delay, reduced packet loss and improved performance of the system, Poluboyina et al. [
31]. In this work, MANET optimized energy-saving route algorithm for IoT is evaluated using residual energy level of the node and distance D
ij, hop count.
4. Proposed Work of MANET-ESO in IoT
The MANET is using the proposed MANET-ESO in an IoT environment, and it increases the rate of trust and successive communication between sensor nodes. The IoT is consisting of WSN techniques with internet service. The mutual internet world of the electronics domain is growing with intelligent network applications. The IoT sensors are successively gathering physical incidents to digital data in different time intervals. Nevertheless, IoT data transmission delay and power utilization are increased due to the uncertainty of sensor nodes. However, the proposed model increases throughput and minimizes energy factors. This MANET Algorithm has improved network performance through trust and the best route optimization method. In
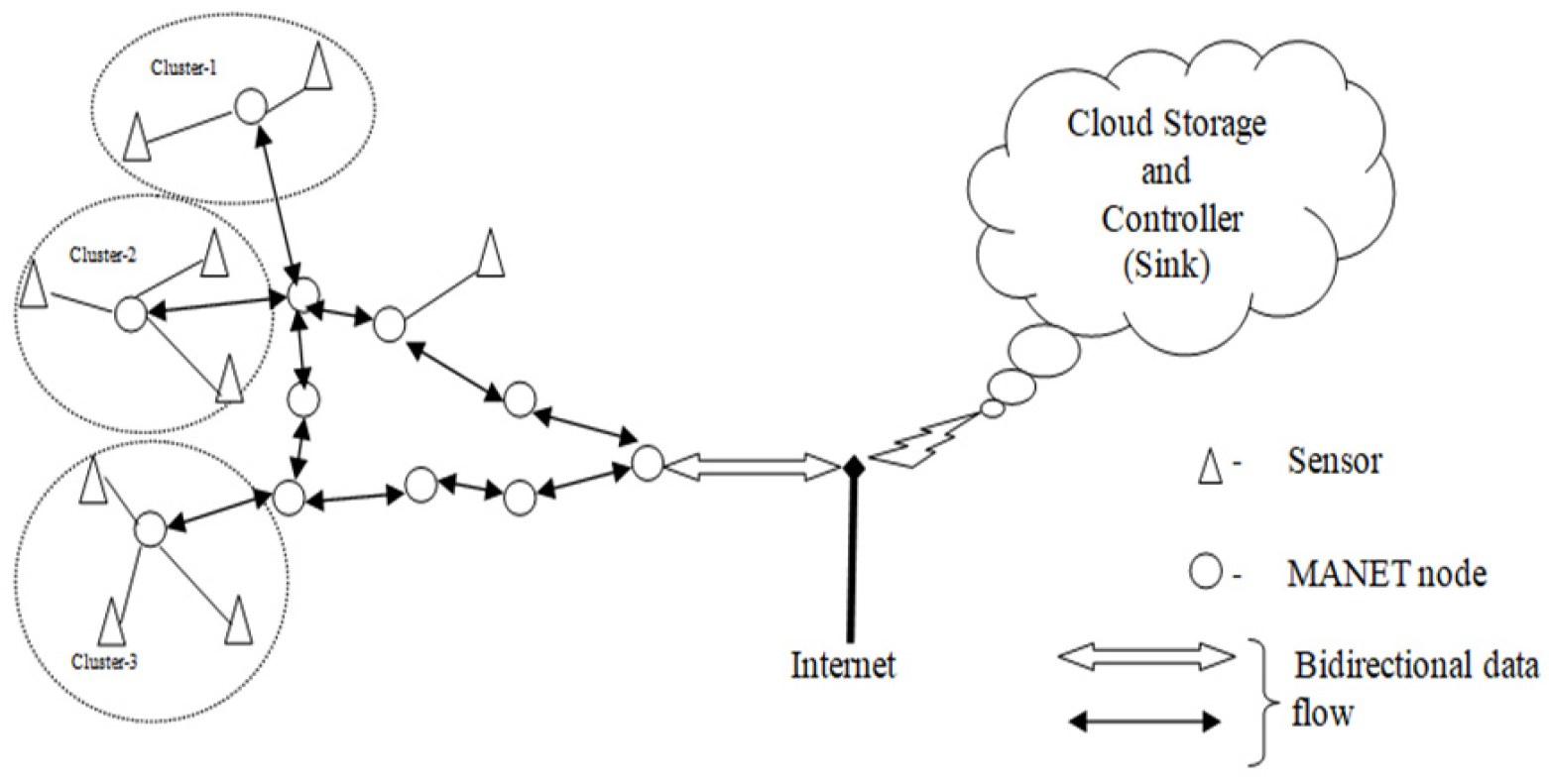
Figure 1, different sensor nodes are connected to the adjacent mobile nodes. Additionally, mobile nodes are forming the cluster using a high density of sensors in that network.
The CH controls, monitors and collects data from sensors. The CH is dynamically changing in the network in terms of the distance from the sensor to the mobile node and the energy level of the mobile node. In the MANET, the information is linked to the gateway node through the CH node, adjacent nodes and gateway nodes using the internet cloud network. The route created in MANET optimizes the energy and enables trusted route paths.
Table 1 shows the abbreviations used in the manuscript.
In this case, available routes and the best routes are created sequentially using the proposed model. In addition, the MANET transmits and stores data or receives commands using the Internet service. Consequently, a heterogeneous network is created to transfer or receive the data through the internet between MANET and the cloud systems (via gateways). The gateway nodes have created the link between the MANET and the cloud routing algorithm.
In this case, the overall performance of the network is higher than a simple IoT network with optimal performance metrics (throughput, energy, delay, packet delivery ratio and routing overhead) while using MANET-ESO (Algorithm 1).
| Algorithm 1: Algorithm for MANET-ESO in IoT |
Initialized: Simulation area considered with n—number of sensor nodes
CH—Cluster Head
m—number of mobile nodes
GW—Gate Way nodes
ECH—residual energy of CH
r = number of discovered routes
ET = Total residual energy of the node
Eth = Energy Threshold Level
Emin = Route total Energy threshold level
Dij = distance between sensor nodes
Hp = destination sequential count
If m is connected with more than one number of n, //cluster head selection
Then, m = CH
else,
m- act as an adjacent node in the network
End if
If m is connected to Internet service, // gateway node identification
Then, m = GW
else,
m–act as an adjacent node in the network
End if
if ECH>= Eth, // CH is reelected by Energy level of the node
Then, retained as a CH
else,
CH is re-elected
End if
ri=1 // discovered routes are being checked one by one
While ri ≤ r
Energy = ET
Distance = Dij
Hop Count = HP
If ET ≤ Emin then
If Dij ≤ Threshold-D, then
If Hp < Threshold–H, Then
ri = Trusted //All the conditions are satisfied then act as a
// trusted route
else
ri = ri++
Repeat the Trust condition
End while; |
5. Simulation and Result of MANET-ESO in IoT Techniques
The simulation of MANET-ESO using IoT Techniques has been simulated by ns-3 on Ubuntu 20 platform.
The experimental configuration considers a MANET, cloud and wireless sensor network with the internet. Since the network has three separate network protocols and it is heterogeneous, the simulation area is estimated to be 1500 × 1500 m
2. All mobile nodes in the network are considered with the same memory size and random mobility model. A clustered network is made up of multiple sensors connected to CH. Therefore, CH in the MANET node is connected with more sensor nodes. All simulator parameters taken into consideration are shown in
Table 2.
This situation is accomplished with internet Gateway nodes. The Gateway node is considered the right side centre of the network area, sensor nodes are considered the left side of the network area and MANET nodes are placed between the sensor to Gateway node in different positions. Every node in the network is dynamically adjusted to a different angle and orientation. In a simulation environment, the traffic generation models, mobility models, topology management models and traffic scheduling models give a realistic network platform. As illustrated in
Table 2, a Poisson traffic model is configured under random packet generation mode. The packets generated in the traffic models are measured from 500 bits to 1500 bits in size based on the type of nodes in the IoT environment (mobile adhoc or sensor nodes). Generally, sensor nodes generate minimal-size packets compared to mobile adhoc nodes. Similarly, the mobility model has been configured with random waypoint procedures that allow mobile adhoc nodes to move independently at variable velocities (meters/seconds). In addition, the channel allocation models used in the 802.11 environments are working based on frequency-time allotment principles. The universal frequency band for IoT is configured in an ns-3 simulation environment as illustrated in
Table 2. The topology followed in this IoT environment is a hybrid model that is configured with a star topology and mesh topology. Star topology is configured in the ns-3 framework to manage higher-level internet cloud points with other geographical nodes. At the lower level, mobile adhoc nodes and sensor nodes are adopted with mesh topology as they are communicating directly for signal propagation. This simulation considers this dual-topology model as optimal for constructing the entire IoT infrastructure. Anyhow, the sensor nodes are mobile nodes are using random packet distribution schemes based on their initial energy and residual energy rates.
The implementation part of the ns-3 simulation testbed contains the modules of the proposed protocol, existing techniques (EECHS-ISSA DE and Butterfly and Ant) and network characteristics. In the simulated network environment (
Table 2), procedure 2 has been implemented among the nodes in the IoT platform. In a similar manner, EECHS-ISSA DE and Butterfly and Ant are implemented separately for evaluating the test cases. The protocols and traffic models used in the experiment are implemented as random Poisson event procedures, Adhoc On-Demand Routing Protocol (AODV), distributed LEACH protocol and energy models. On the basis of this experimental test bed, the performance metrics such as the number of active nodes, throughput rate, residual energy, packet delivery rate and average routing delay are calculated. The mentioned metrics are calculated for iteratively varying network parameters such as the number of nodes, test rounds and suspicious nodes. The prescribed ns-3 simulation model has been implemented using C++ modules (Initial network deployment). In addition, python codes are used for importing the library functions of routing protocols and traffic models.
5.1. Results and Analysis in Terms of Node Alive Node vs. Number of Rounds
When using IoT approaches, the node alive time of MANET-ESO is compared with existing algorithms such as EECHS-ISSA DE [
16] and Butterfly and Ant [
17] method.
Figure 2 illustrates the testing of the proposed methodology and the existing algorithm using 50 sensor nodes, 100 MANET nodes and one Gateway node in the ns-3 simulator. This shows the performance of the number alive node is better than the existing algorithm in a different number of rounds. The WSN constructed with MANET nodes using 10% of clusters was tested for 1800 rounds without dead nodes and produced better results. However, compared to other existing algorithms, the MANET-ESO protocol achieved high alive nodes up to 4500 rounds.
In the EECHS-ISSA DE method, all the nodes are connected via the clustering technique, and the cluster head selection process requires more energy to discover the route. Hence live nodes are limited after 1800 rounds.
In the Butterfly and Ant method, the link to the BS station is discovered by two different algorithms. Firstly, it forms clusters and discovered routes. Both are utilizing less energy compared with EECHS-ISSA DE methods. However, the performance is not better than the proposed work. In the proposed work, the energy utilization of the network is reduced by the clustering algorithm. The cluster head is controlling all nodes in the cluster. So apart from cluster head remaining node energy utilization is less and increasing the alive in the network.
Figure 2 shows the proposed algorithm performance, as the alive node is an average of 67.7% higher than EECHS-ISSA DE and an average of 10.7% higher than the Butterfly and Ant Method.
5.2. Results and Analysis in Terms of Residual Energy vs. Number of Rounds
This section discusses the residual energy of the node after ‘n’ rounds. The results are contrasted with the existing methodology.
Figure 3 shows the results of residual energy vs. the number of rounds; the results of the proposed methods are compared to those of the EECHS-ISSA DE and Butterfly and Ant method. Both the cluster energy method and MANET trusted route algorithm compute and identify the best route to improve the residual energy of the route. The overall energy utilization is based on the number of adjacent nodes in the route. The performance of MANET-ESO in IoT is compared to other existing work and observed that EECHS-ISSA DE and Butterfly-Ant methods are wasting the energy level. The EECHS-ISSA DE reduces the energy level over the course of 1000 rounds. The energy balancing approach is being used in Butterfly and Ant method, which has maintained an energy level for up to 8200 rounds. Finally, when compared with the proposed method, the trusted route energy optimization method is choosing the best route based on the total energy utilization of the node, minimum distance and minimum hop count. So, the selected route is using less energy to complete the task and improved the performance of the network compared to other methods. The residual energy of nodes is increased by an average of 75% in this proposed algorithm compared to EECHS-ISSA DE and a 7.1% increase compared to Butterfly and Ant method.
5.3. Results and Analysis in Terms of Throughput vs. Number of Rounds
The throughput is calculated by the total time taken to transport all packets from the source to the destination. This algorithm identifies the shortest distance by total time duration to transfer packets and less hop count of the discovered routes. It is carrying more packets within a minimum time. So, it increases the throughput of the network compared to other existing work. In EECHS-ISSA DE and Butterfly and Ant methods, throughputs are reduced due to node energy loss. As a result, nodes become dead and the throughput of the network is minimized. However, compared with existing works, the proposed method has outperformed up to 6800 rounds in the network. The Proposed algorithm has a throughput average of 75% higher than EECHS-ISSA DE and an average of 12.2% higher than the Butterfly and Ant Method (
Figure 4).
5.4. Performance Evaluation of Packet Delivery Ratio (PDR) and Routing Overhead
This session compares the proposed work performance to EECHS-ISSA DE and Butterfly and Ant algorithms in terms of packet delivery ratio and routing overhead.
Figure 5 illustrates the evaluation of the packet delivery ratio with respect to 50, 100, and 150 nodes. Comparing this proposed method to existing ones, the packet delivery ratio is high. The clustering method and trust routing algorithm in the network reduced the packet transmission delay and transferred the packet to a short distance. As a result, all packets reach the destination node with minimum loss than other existing methods. Under 50 and 100 nodes scenarios, the packet delivery ratio of the proposed method is increased by approximately 8% compared to EECHS-ISSA DE and approximately 4% increase compared to the butterfly ant method. The PDR is increased by 8% to 9% for 50 nodes when compared to EECHS-ISSA DE and Butterfly and Ant Method.
Figure 6 shows the routing overhead of the proposed work in comparison to the existing algorithms.
The trusted routing method increases the route’s life span and decreases routing overhead compared to other existing algorithms. In the simulation scenarios compared with 50, 100 and 150 nodes, the output result is 71% better compared to EECHS-ISSA DE and 20% better compared to the Butterfly and Ant method.
In this
Figure 7, the packet delivery ratio of the MANET-ESO in the IoT algorithm is compared with the EECHS-ISSA DE, Butterfly and Ant algorithms with respect to the percentage of malicious nodes. The number of malicious nodes in the network increased by 10 and we observed that PDR improved.
Again, the number of malicious nodes is increased to 30% and 60% respectively. Now the proposed algorithm’s PDR ratio is reduced due to frequent route failures occurring from the source to the destination.
However, compared with the existing methods, the result of PDR is increased by 24% compared to EECHS-ISSA DE, and increased by 14% compared to the Butterfly and Ant method.
Figure 8 shows the performance of the proposed algorithm for routing overhead as the number of malicious nodes increase in the network. The routing overhead is increased due to frequent route failure in the network. Because of the increased malicious activity, the best route selection process requires more time to complete all packet transmission.