Securing Smart Grids: A Triplet Loss Function Siamese Network-Based Approach for Detecting Electricity Theft in Power Utilities
Abstract
1. Introduction
2. Methodology
2.1. Data Collection and Pre-Preprocessing
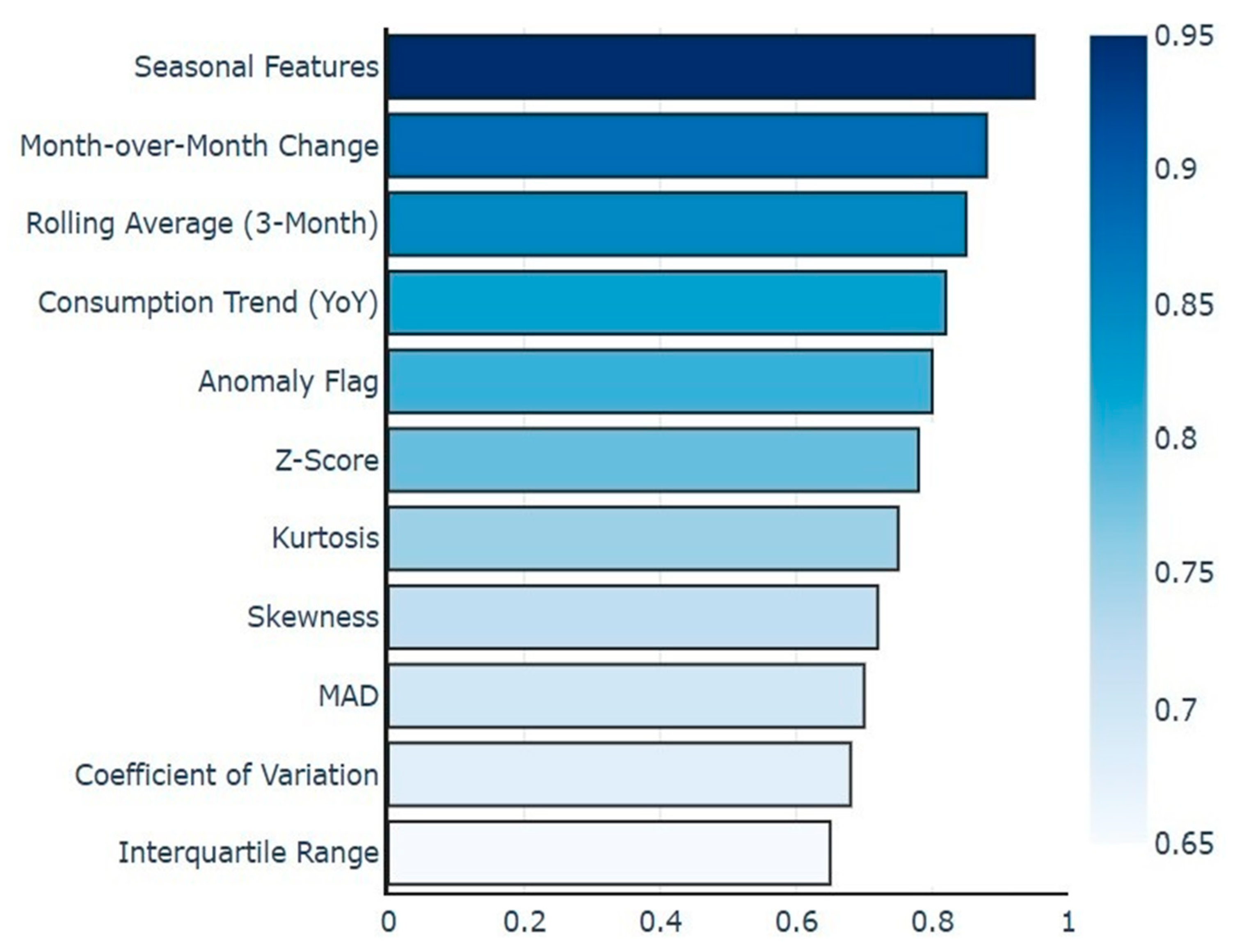
2.2. Feature Extraction
- i.
- Seasonal Features
- ii.
- Month-over-Month Change
- iii.
- Rolling Average (3-Month Average)
- iv.
- Consumption Trend (Year-over-Year or Slope)
- v.
- Anomaly Flag
- vi.
- Z-Score Comparison
- vii.
- Kurtosis Comparison
- viii.
- Skewness Comparison
- ix.
- MAD (Mean Absolute Deviation) Comparison
- x.
- Coefficient of Variation Comparison
- xi.
- Interquartile Range Comparison
2.3. Feature Selection for Siamese Network Optimization
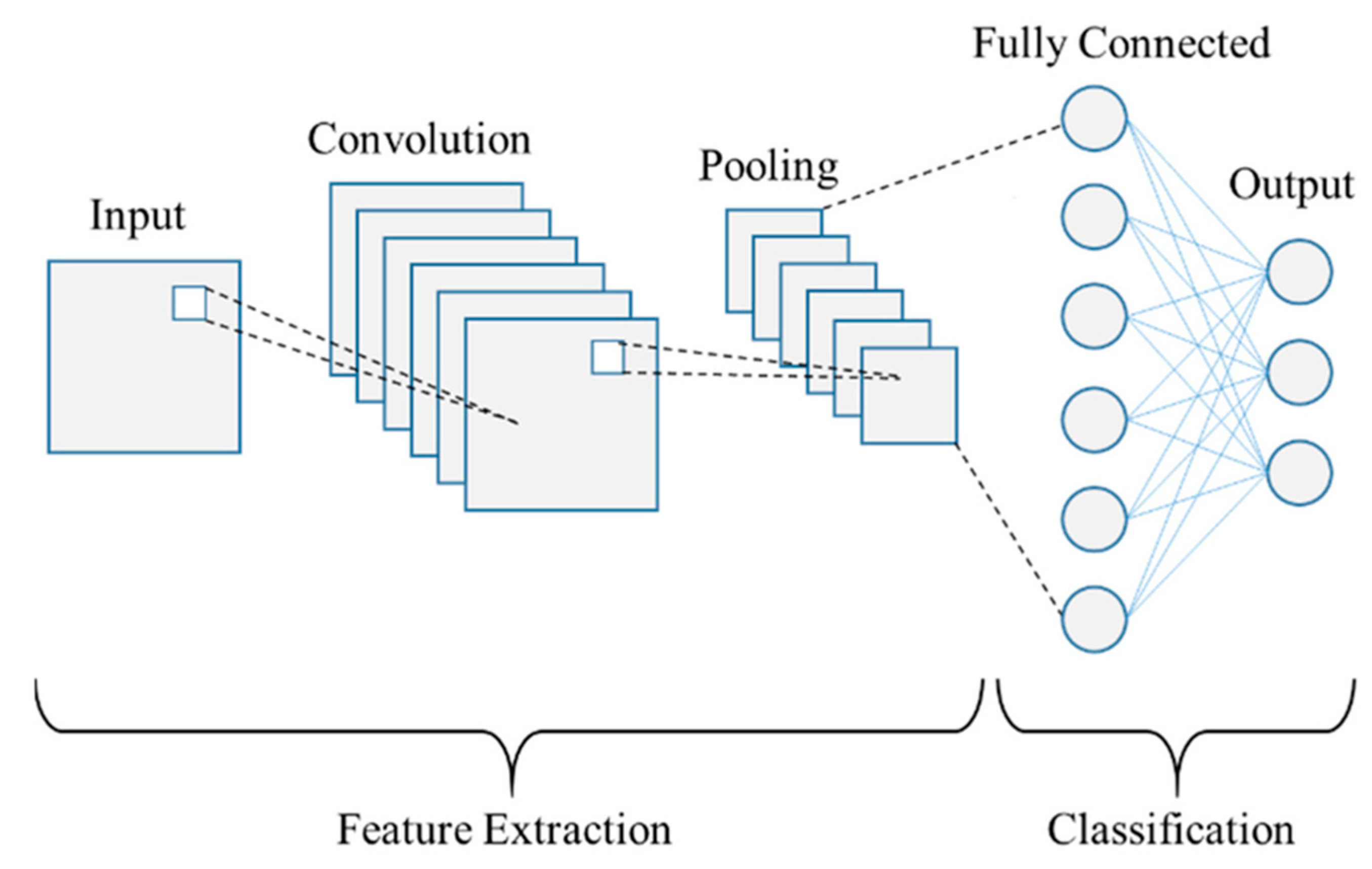
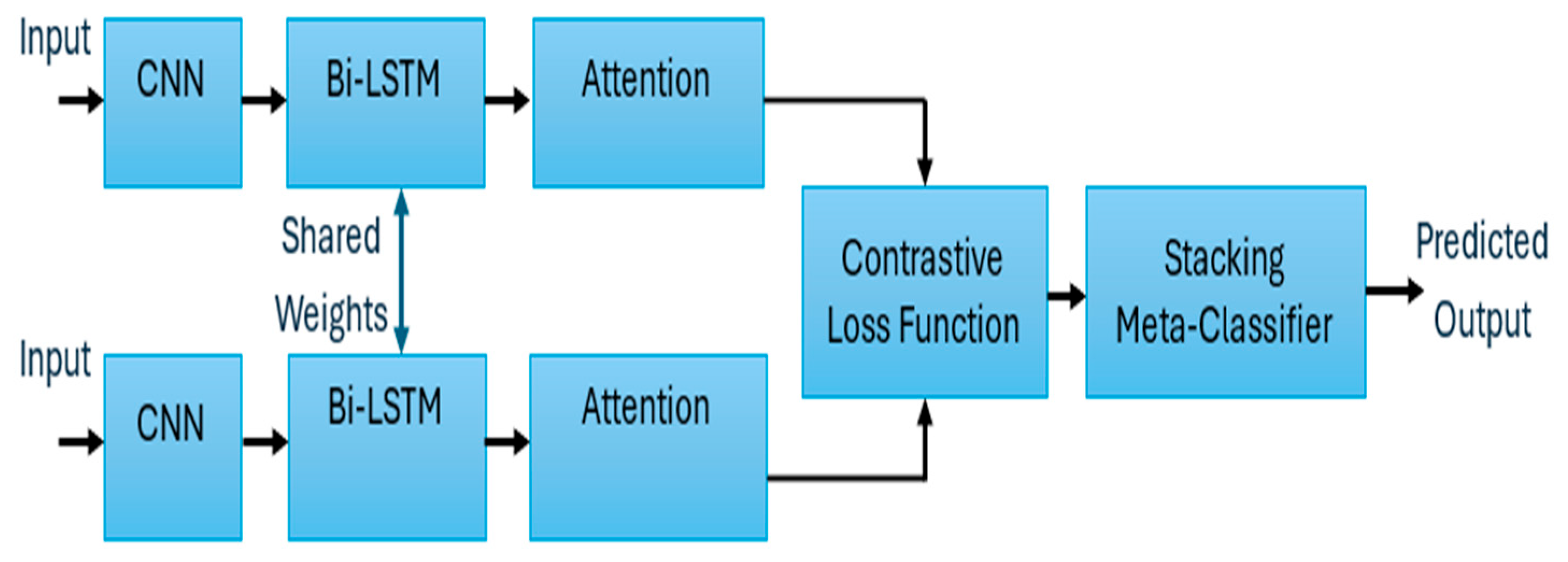
3. Siamese Networks with Triplet Loss for Classification
3.1. Basic Architecture of Siamese Network
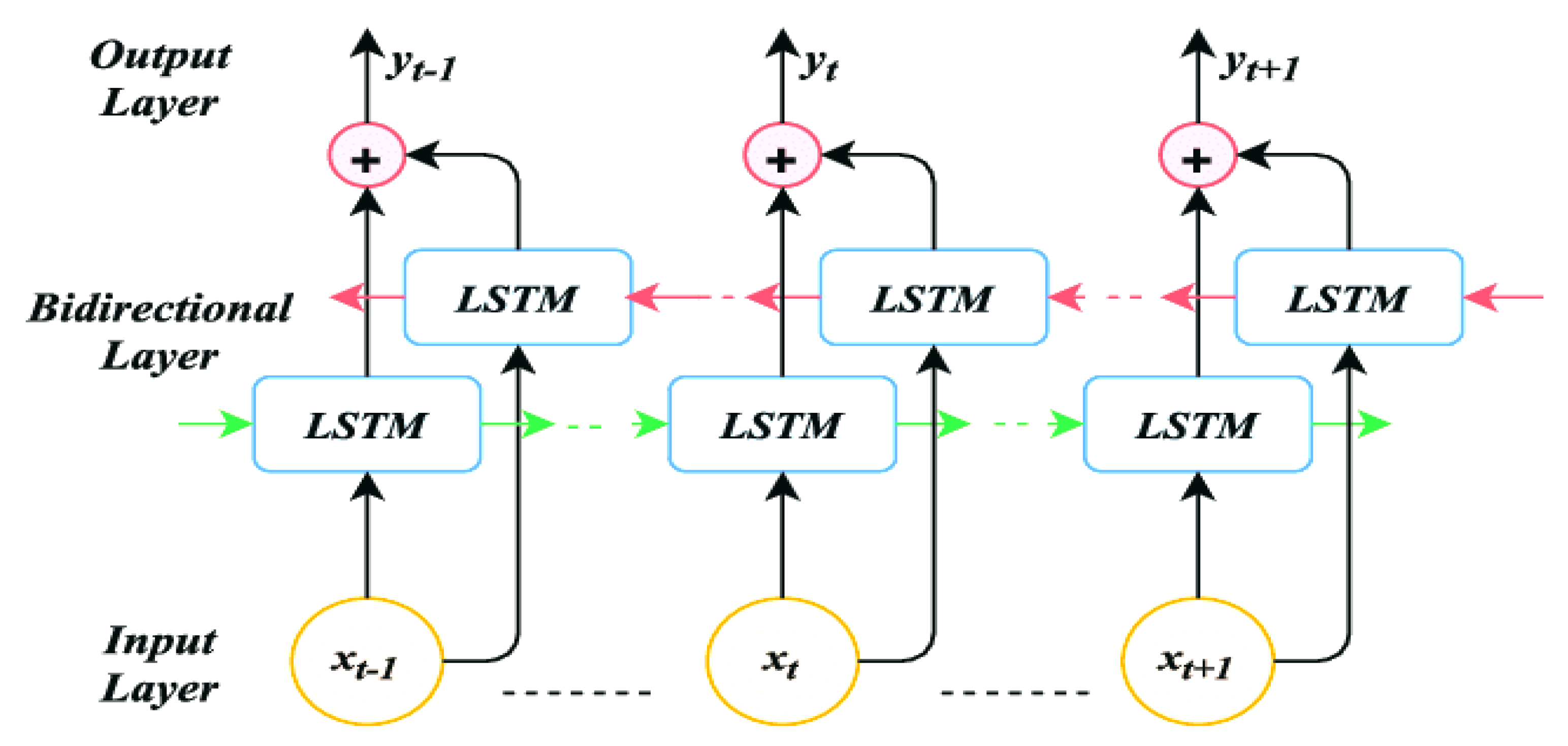
3.2. Fundamentals of Bidirectional Long Short-Term Memory Networks
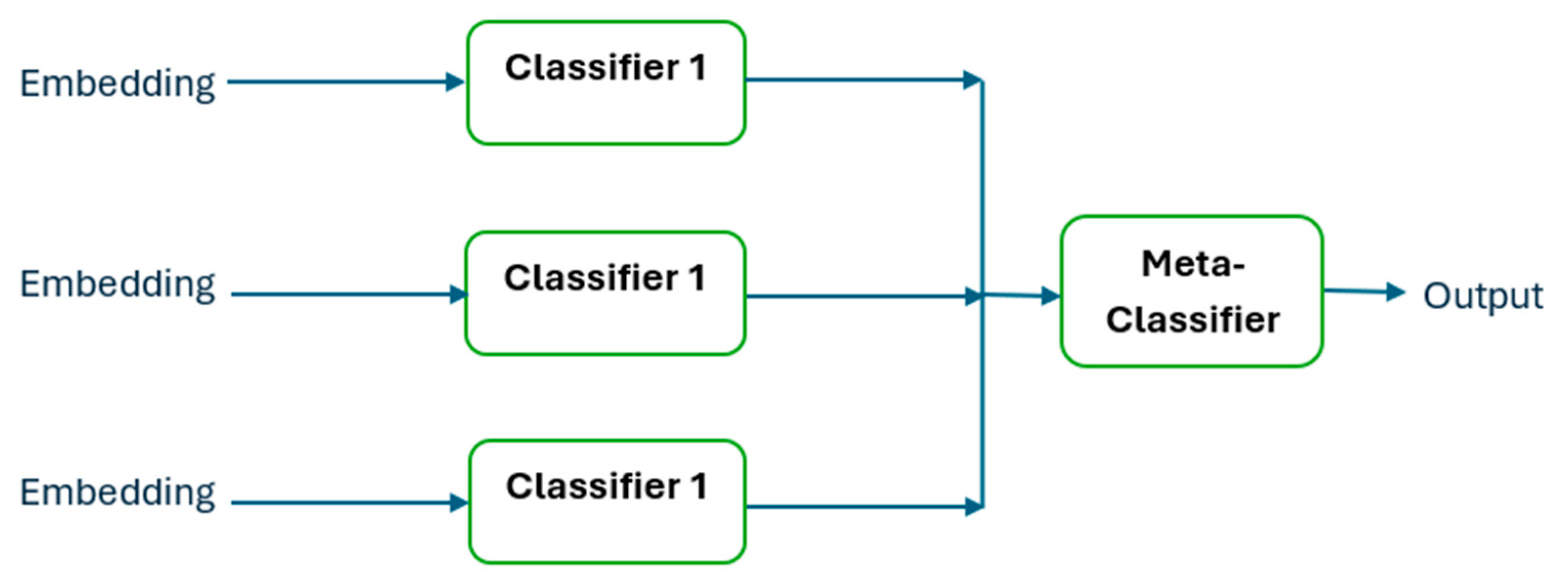
3.3. Stacking Meta-Classifier as a Decision Maker
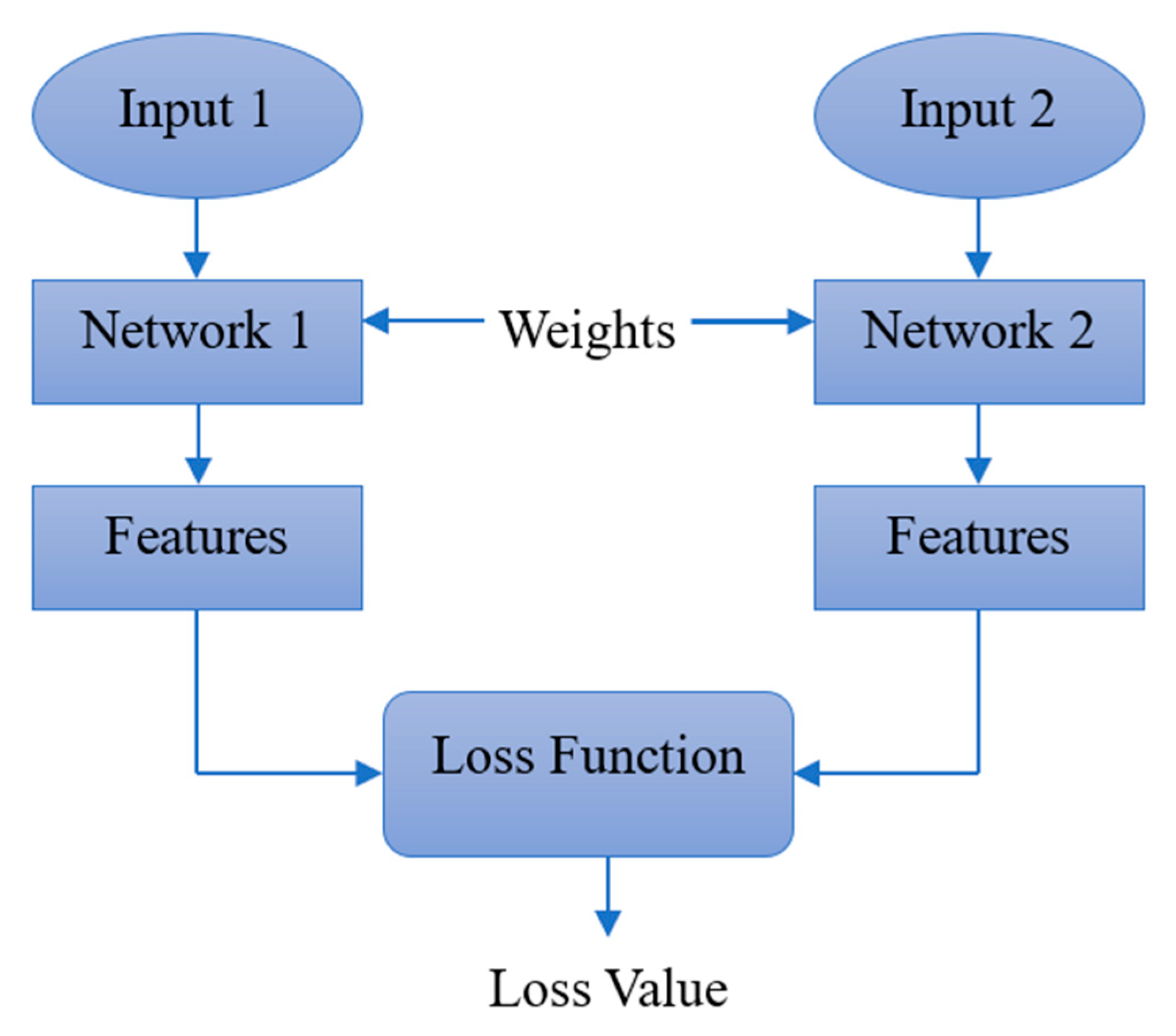
3.4. Mathematical Model for Siamese Network and Loss Function
4. Evaluation Metrics
- i.
- Accuracy
- ii.
- Precision
- iii.
- Sensitivity
- iv.
- False Positive Rate
- v.
- Area Under Curve (AUC)
- vi.
- F1 Score
5. Results and Discussion
5.1. Statistical Evaluation of Model Performance
5.2. Computational Efficiency and Deployment Analysis
5.3. Limitations and Future Work
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kessides, I.N. Chaos in power: Pakistan’s electricity crisis. Energy Policy 2013, 55, 271–285. [Google Scholar] [CrossRef]
- Wang, Z.; Hou, H.; Wei, R.; Li, Z. A Distributed Market-Aided Restoration Approach of Multi-Energy Distribution Systems Considering Comprehensive Uncertainties from Typhoon Disaster. IEEE Trans. Smart Grid 2025, 16, 3743–3757. [Google Scholar] [CrossRef]
- Saeed, M.S.; Mustafa, M.W.; Sheikh, U.U.; Jumani, T.A.; Mirjat, N.H. Ensemble bagged tree based classification for reducing non-technical losses in multan electric power company of Pakistan. Electronics 2019, 8, 860. [Google Scholar] [CrossRef]
- Guo, X.; Yin, Y.; Dong, C.; Yang, G.; Zhou, G. On the class imbalance problem. In Proceedings of the 2008 Fourth International Conference on Natural Computation, Jinan, China, 18–20 October 2008. [Google Scholar] [CrossRef]
- Hussain, S.; Mustafa, M.W.; Jumani, T.A.; Baloch, S.K.; Saeed, M.S. A novel unsupervised feature-based approach for electricity theft detection using robust PCA and outlier removal clustering algorithm. Int. Trans. Electr. Energy Syst. 2020, 30, e12572. [Google Scholar] [CrossRef]
- Liao, W.; Yang, D.; Ge, L.; Jia, Y.; Yang, Z. Electricity theft detection in integrated energy systems considering multi-energy loads. Int. J. Electr. Power Energy Syst. 2025, 164, 110428. [Google Scholar] [CrossRef]
- Tiwari, R.S.; Sharma, J.P.; Gupta, O.H.; Ahmed Abdullah Sufyan, M. Extension of pole differential current based relaying for bipolar LCC HVDC lines. Sci. Rep. 2025, 15, 16142. [Google Scholar] [CrossRef] [PubMed]
- Tursunboev, J.; Palakonda, V.; Kang, J.M. Multi-Objective Evolutionary Hybrid Deep Learning for energy theft detection. Appl. Energy 2024, 363, 122847. [Google Scholar] [CrossRef]
- Messinis, G.M.; Hatziargyriou, N.D. Review of non-technical loss detection methods. Electr. Power Syst. Res. 2018, 158, 250–266. [Google Scholar] [CrossRef]
- Jokar, P.; Arianpoo, N.; Leung, V.C.M. Electricity theft detection in AMI using customers’ consumption patterns. IEEE Trans. Smart Grid 2016, 7, 216–226. [Google Scholar] [CrossRef]
- Jindal, A.; Dua, A.; Kaur, K.; Singh, M.; Kumar, N.; Mishra, S. Decision Tree and SVM-Based Data Analytics for Theft Detection in Smart Grid. IEEE Trans. Ind. Inform. 2016, 12, 1005–1016. [Google Scholar] [CrossRef]
- Nawaz, A.; Ali, T.; Mustafa, G.; Rehman, S.U.; Rashid, M.R. A novel technique for detecting electricity theft in secure smart grids using CNN and XG-boost. Intell. Syst. Appl. 2023, 17, 200168. [Google Scholar] [CrossRef]
- Zheng, Z.; Yang, Y.; Niu, X.; Dai, H.-N.; Zhou, Y. Wide and Deep Convolutional Neural Networks for Electricity-Theft Detection to Secure Smart Grids. IEEE Trans. Ind. Inform. 2018, 14, 1606–1615. [Google Scholar] [CrossRef]
- Salman Saeed, M.; Mustafa, M.W.; Sheikh, U.U.; Jumani, T.A.; Khan, I.; Atawneh, S.; Hamadneh, N.N. An Efficient Boosted C5.0 Decision-Tree-Based Classification Approach for Detecting Non-Technical Losses in Power Utilities. Energies 2020, 13, 3242. [Google Scholar] [CrossRef]
- Saeed, M.S.; Mustafa, M.W.; Sheikh, U.U.; Khidrani, A.; Mohd, M.N.H. Theft Detection in Power Utilities Using Ensemble of Chaid Decision Tree Algorithm. Sci. Proc. Ser. 2020, 2, 161–165. [Google Scholar] [CrossRef]
- Nabil, M.; Ismail, M.; Mohmoud, M.; Shahin, M.; Qaraqe, K.; Serpedin, E. Deep Recurrent Electricity Theft Detection in AMI Networks with Random Tuning of Hyper-parameters. arXiv 2018, arXiv:1809.01774v1. [Google Scholar] [CrossRef]
- Glauner, P.; Boechat, A.; Dolberg, L.; State, R.; Bettinger, F.; Rangoni, Y.; Duarte, D. Large-scale detection of non-technical losses in imbalanced data sets. In Proceedings of the 2016 IEEE Power and Energy Society Innovative Smart Grid Technologies Conference, ISGT 2016, Minneapolis, MN, USA, 6–9 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Xia, X.; Xiao, Y.; Liang, W.; Cui, J. Detection Methods in Smart Meters for Electricity Thefts: A Survey. Proc. IEEE 2022, 110, 273–319. [Google Scholar] [CrossRef]
- Reddy, M.S.; Lakshmi, A.A.; Reddy, G.S.; Madhavi, B.K.; Panigrahi, B.S.; Mohan, V. Signature Forgery Detection using Siamese-Convolutional Neural Network. In Proceedings of the 2024 1st International Conference on Cognitive, Green and Ubiquitous Computing (IC-CGU), Bhubaneswar, India, 1–2 March 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Gupta, R.; Kashyap, I.; Jindal, V. SBiLM: Siamese Bi-LSTM model for handling imbalance in fake review detection. Procedia Comput. Sci. 2024, 235, 1157–1166. [Google Scholar] [CrossRef]
- Tapia, J.E.; Schulz, D.; Busch, C. Single-morphing attack detection using few-shot learning and triplet-loss. Neurocomputing 2025, 636, 130033. [Google Scholar] [CrossRef]
- Ullah, K.; Ahsan, M.; Hasanat, S.M.; Haris, M.; Yousaf, H.; Raza, S.F.; Tandon, R.; Abid, S.; Ullah, Z. Short-Term Load Forecasting: A Comprehensive Review and Simulation Study with CNN-LSTM Hybrids Approach. IEEE Access 2024, 12, 111858–111881. [Google Scholar] [CrossRef]
- Dao, F.; Zeng, Y.; Qian, J. Fault diagnosis of hydro-turbine via the incorporation of bayesian algorithm optimized CNN-LSTM neural network. Energy 2024, 290, 130326. [Google Scholar] [CrossRef]
- Sherkatghanad, Z.; Ghazanfari, A.; Makarenkov, V. A self-attention-based CNN-Bi-LSTM model for accurate state-of-charge estimation of lithium-ion batteries. J. Energy Storage 2024, 88, 111524. [Google Scholar] [CrossRef]
- Mahmudul Hasan, A.S.M.; Diepeveen, D.; Laga, H.; Jones, M.G.; Muzahid, A.; Sohel, F. Morphology-based weed type recognition using Siamese network. Eur. J. Agron. 2025, 163, 127439. [Google Scholar] [CrossRef]
- Liu, Z.; Huang, H.; Dong, H.; Xing, F. IoU-guided Siamese network with high-confidence template fusion for visual tracking. Neurocomputing 2025, 614, 128774. [Google Scholar] [CrossRef]
- Nagi, J.; Yap, K.S.; Tiong, S.K.; Ahmed, S.K.; Nagi, F. Improving SVM-based nontechnical loss detection in power utility using the fuzzy inference system. IEEE Trans. Power Deliv. 2011, 26, 1284–1285. [Google Scholar] [CrossRef]


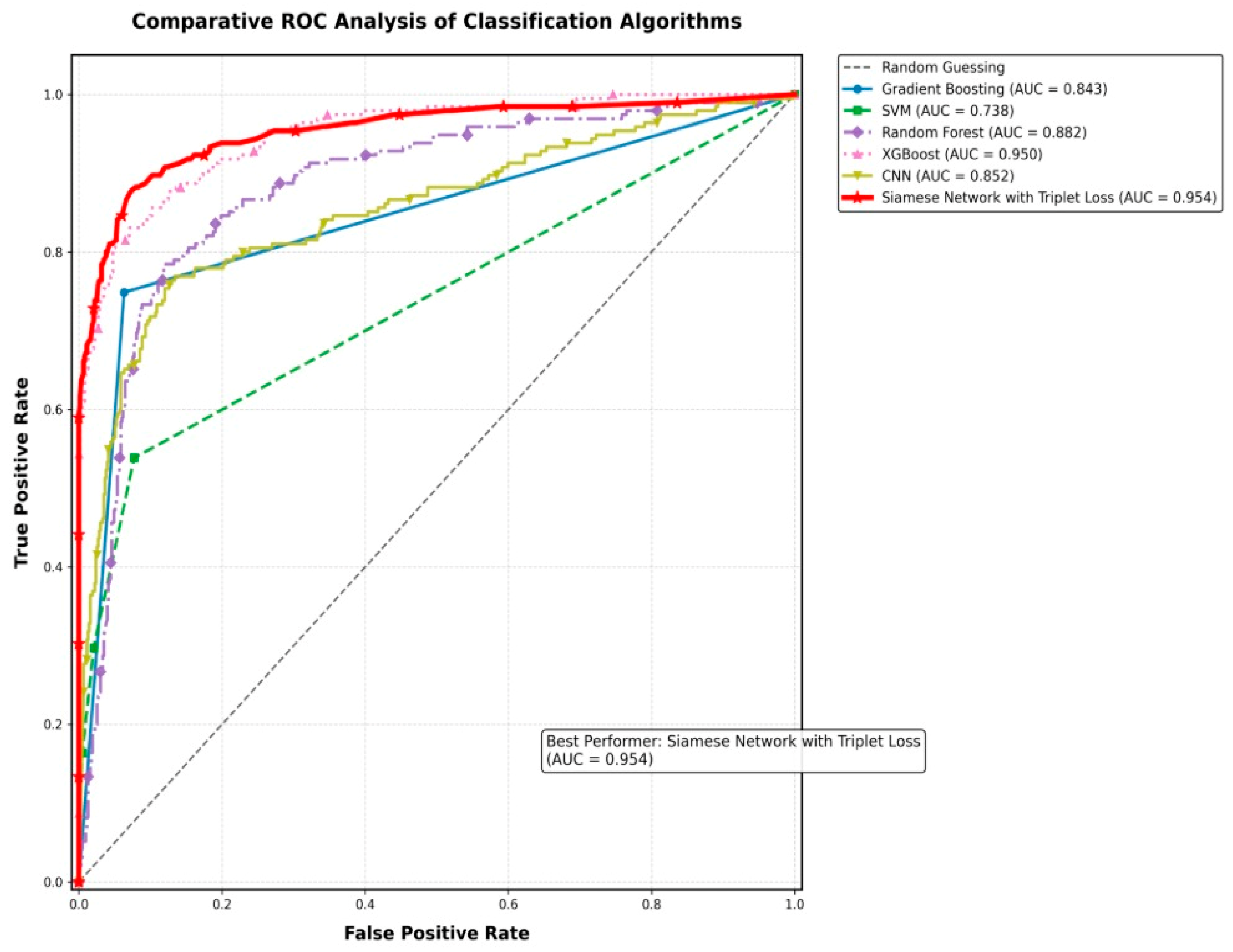

| Algorithm | Accuracy | Precision | TPR (Recall) | FPR | AUC | F1 Score |
|---|---|---|---|---|---|---|
| SVM | 0.85 ± 0.02 | 0.84 ± 0.03 | 0.83 ± 0.03 | 0.12 ± 0.02 | 0.89 ± 0.01 | 0.83 ± 0.02 |
| Random Forest | 0.88 ± 0.01 | 0.86 ± 0.02 | 0.85 ± 0.02 | 0.10 ± 0.01 | 0.88 ± 0.01 | 0.85 ± 0.02 |
| Gradient Boosting | 0.90 ± 0.01 | 0.88 ± 0.02 | 0.89 ± 0.02 | 0.08 ± 0.01 | 0.92 ± 0.01 | 0.88 ± 0.02 |
| XGBoost | 0.91 ± 0.01 | 0.89 ± 0.02 | 0.90 ± 0.02 | 0.07 ± 0.01 | 0.93 ± 0.01 | 0.89 ± 0.01 |
| CNN | 0.87 ± 0.02 | 0.86 ± 0.03 | 0.85 ± 0.03 | 0.11 ± 0.02 | 0.90 ± 0.01 | 0.85 ± 0.02 |
| Siamese Network (Proposed) | 0.954 ± 0.008 | 0.92 ± 0.01 | 0.94 ± 0.01 | 0.05 ± 0.008 | 0.96 ± 0.007 | 0.93 ± 0.009 |
| Model Variant | Accuracy | Precision | F1-Score | AUC |
|---|---|---|---|---|
| Full Proposed Model | 0.954 ± 0.008 | 0.920 ± 0.016 | 0.930 ± 0.010 | 0.960 ± 0.012 |
| w/o Bi-LSTM | 0.925 ± 0.012 | 0.885 ± 0.020 | 0.895 ± 0.015 | 0.935 ± 0.015 |
| w/o Attention | 0.938 ± 0.010 | 0.905 ± 0.018 | 0.915 ± 0.013 | 0.948 ± 0.014 |
| w/o Meta-Classifier | 0.931 ± 0.011 | 0.892 ± 0.019 | 0.905 ± 0.014 | 0.941 ± 0.016 |
| CNN-Only Backbone | 0.910 ± 0.015 | 0.870 ± 0.022 | 0.880 ± 0.017 | 0.925 ± 0.018 |
| Algorithm | Accuracy | Precision | TPR | FPR | AUC | F1 Score |
|---|---|---|---|---|---|---|
| SVM | 0.850 ± 0.022 | 0.840 ± 0.025 | 0.830 ± 0.020 | 0.120 ± 0.015 | 0.890 ± 0.018 | 0.830 ± 0.015 |
| Random Forest | 0.880 ± 0.018 | 0.860 ± 0.020 | 0.850 ± 0.018 | 0.100 ± 0.012 | 0.880 ± 0.015 | 0.850 ± 0.012 |
| Gradient Boosting | 0.900 ± 0.016 | 0.880 ± 0.018 | 0.890 ± 0.016 | 0.080 ± 0.010 | 0.920 ± 0.014 | 0.880 ± 0.012 |
| XGBoost | 0.910 ± 0.015 | 0.890 ± 0.017 | 0.900 ± 0.015 | 0.070 ± 0.009 | 0.930 ± 0.013 | 0.890 ± 0.011 |
| CNN | 0.870 ± 0.019 | 0.860 ± 0.021 | 0.850 ± 0.019 | 0.110 ± 0.014 | 0.900 ± 0.016 | 0.850 ± 0.013 |
| Siamese Network (Proposed) | 0.954 ± 0.018 | 0.920 ± 0.016 | 0.940 ± 0.015 | 0.050 ± 0.008 | 0.960 ± 0.012 | 0.930 ± 0.010 |
| Comparison Model | Mean F1 Difference | t-Statistic | p-Value |
|---|---|---|---|
| SVM | −0.100 | −25.00 | <0.001 |
| Random Forest | −0.080 | −22.00 | <0.001 |
| Gradient Boosting | −0.050 | −18.00 | <0.001 |
| XGBoost | −0.040 | −15.00 | <0.001 |
| CNN | −0.080 | −20.00 | <0.001 |
| Model | Avg. Training Time (s) | Avg. Inference Time per Sample (ms) | Model Size (MB) |
|---|---|---|---|
| SVM | 12.5 ± 2.1 | 0.05 ± 0.01 | 1.2 |
| Random Forest | 8.3 ± 1.5 | 0.15 ± 0.03 | 3.8 |
| Gradient Boosting | 22.7 ± 3.8 | 0.08 ± 0.02 | 2.5 |
| XGBoost | 6.1 ± 1.2 | 0.04 ± 0.01 | 0.9 |
| CNN | 145.3 ± 15.6 | 1.25 ± 0.15 | 15.7 |
| Siamese Network (Ours) | 183.5 ± 18.9 | 1.42 ± 0.18 | 18.2 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmed, T.; Saeed, M.S.; Masud, M.I.; Ahmad Arfeen, Z.; Baloch, M.; Aman, M.; Shahzad, M. Securing Smart Grids: A Triplet Loss Function Siamese Network-Based Approach for Detecting Electricity Theft in Power Utilities. Energies 2025, 18, 4957. https://doi.org/10.3390/en18184957
Ahmed T, Saeed MS, Masud MI, Ahmad Arfeen Z, Baloch M, Aman M, Shahzad M. Securing Smart Grids: A Triplet Loss Function Siamese Network-Based Approach for Detecting Electricity Theft in Power Utilities. Energies. 2025; 18(18):4957. https://doi.org/10.3390/en18184957
Chicago/Turabian StyleAhmed, Touqeer, Muhammad Salman Saeed, Muhammad I. Masud, Zeeshan Ahmad Arfeen, Mazhar Baloch, Mohammed Aman, and Mohsin Shahzad. 2025. "Securing Smart Grids: A Triplet Loss Function Siamese Network-Based Approach for Detecting Electricity Theft in Power Utilities" Energies 18, no. 18: 4957. https://doi.org/10.3390/en18184957
APA StyleAhmed, T., Saeed, M. S., Masud, M. I., Ahmad Arfeen, Z., Baloch, M., Aman, M., & Shahzad, M. (2025). Securing Smart Grids: A Triplet Loss Function Siamese Network-Based Approach for Detecting Electricity Theft in Power Utilities. Energies, 18(18), 4957. https://doi.org/10.3390/en18184957









