A Novel Block-based Watermarking Scheme Using the SVD Transform
Abstract
:1. Introduction
- the use of the angles formed by the singular vectors to embed the watermark while maintaining the property of orthonormality. To our knowledge, there are no watermarking schemes, based on singular vectors, that respect this property;
- an increased security of the watermarking process based on the SVD transform, due to the use of singular vectors for the watermark insertion rather than singular values. Indeed, many of the existing SVD-based algorithms embed the watermark into the singular values of the image, which implies a high robustness against common image processing operations and geometric attacks but, on the other hand, a complete vulnerability towards attacks based on singular value substitution, as explained for example in [15,16].
2. SVD Transform
3. Related Works
3.1 Overview of the SVD-based watermarking schemes
- watermarking algorithms which embed the watermark or its singular values into the singular values of the host image;
- watermarking algorithms which insert the watermark by modifying the right/left singular vectors of the host image;
- watermarking techniques based on modification of singular vectors and values; the watermark inserted in singular vectors is used as a control parameter to avoid the false positive problem;
- watermarking methods that combine all features of the SVD transform (singular vectors/values) with others transforms (DFT, DCT, DWT, Zernike Moments Transform, Haar Transform, Hadamard Transform).
3.2 Watermarking algorithms based on Singular Values
- False positive. As stated in [16, 31,32,33,34,35], these schemes are subject to the false positive problem, which is an erroneous detection of a watermark in a content which does not actually contain one [36]. However, a false positive may occur also when a specific watermark is detected from a content in which a different watermark was embedded, causing an ambiguous situation [32]. This fact does not allow one to solve the rightful ownership problem [37]. In general, SVD-based watermarking methods which embed the Singular Values of the watermark into the Singular Values of the host image are considered invertible schemes [31]. Thus, they are vulnerable to the false positive problem, which appears in the detection phase, during the watermark reconstruction. Recently, Mohammad et al. [31] proposed a scheme which modifies the Tan’s algorithm [23] in order to solve this problem. However, the algorithm cannot resist against common and geometric attacks even if the original image is used in the detection process.
- Quality of the watermarked image. In these schemes, modifying the largest SV may degrade the watermarked image, thus it is necessary to use an adequate strength factor in the embedding process, which attenuates the energy of the watermark and thus lowers the resistance against attacks.
- Payload. To increase the payload of these schemes the host image is split into small blocks; this fact lowers the robustness against common attacks (e.g., JPEG compression and noise addition) since the stability of the SVs decreases when reducing the size of the blocks.
- Security. Most of the proposed schemes [23, 29, technique 1 in 31, 38] cannot be considered secure because they do not use any secret information in the watermarking process. To increase security and also to avoid the false positive problem, these algorithms must use secrets for choosing the embedding blocks [27, 28] or preprocess the watermark and the original image before embedding [24,25,26].
3.3 Watermarking algorithms based on singular vectors
3.4 Watermarking algorithms based on Singular values and vectors
3.5 Combined watermarking algorithms
4. Proposed Watermarking Scheme
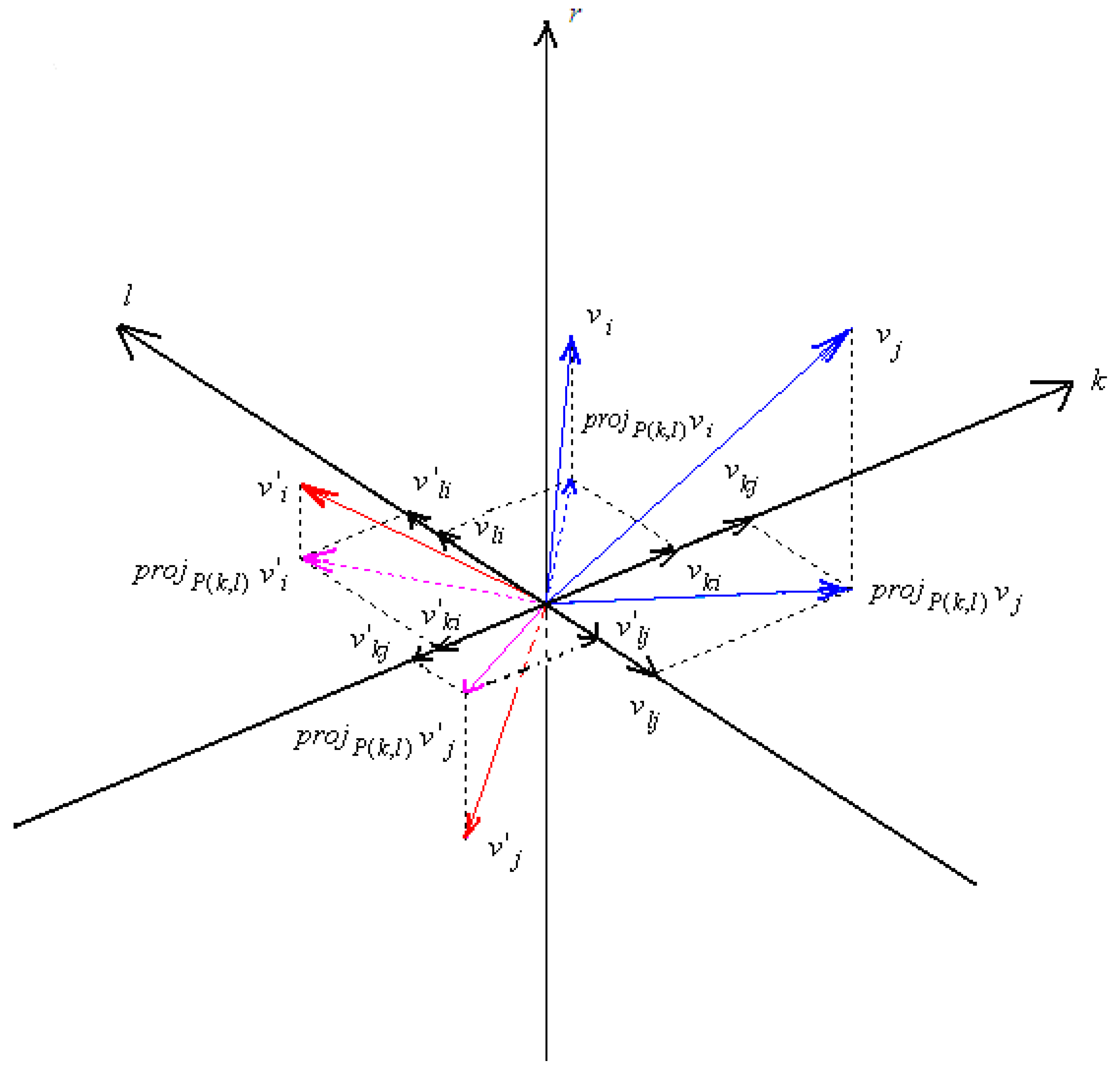
4.1 Watermark embedding
- 1)
- Split the host image Io of size N ×N into n2 non-overlapping blocks, Bb, of size M × M, where M = N/n and .
- 2)
- Generate the watermark W, i.e., a pseudo-random Gaussian sequence of size n2, by means of the secret key K.
- 3)
- 4)
- From the secret key K, extract the indices i and j that choose the vi and vj vectors belonging to the matrix Vb. From K, also extract the indices k and l which define the components on vi and vj, used to compute the secret plane P(k, l). For simplicity, we refer to such components as x = vki, y = vli, z = vkj and w = vlj.
- 5)
- Compute the angle θb, derived by the projection of vector vi with the positive axis k, i.e., defined by the components x and y, using the four quadrant arctangent function (see Appendix A):θb is then inserted in the feature set F.The scaling factor δ is used to obtain a feature angle that is not close to the point of discontinuity in –π and π. In this way, all angles are “compressed” around the origin, so the modification made by the watermark insertion should not allow the angle to bypass the discontinuity point. This can be obtained by carefully choosing the scaling factor and the watermark strength, taking also into account that the angle obtained after the watermark insertion should, in theory, span all the range [-π..π]. Nonetheless, it is possible (in a few cases, if the multiplicative constants are not carefully chosen) that for large values of the feature angle and of the watermark, the discontinuity will be traversed.
- 6)
- Compute the angle αb, by adding the angle extracted from the watermark sequence Wb to the angle θb:where β is the strength factor of the embedded watermark.
- 7)
- Determine the rotation angle φb, which is needed to rotate the vi and vj vectors in the plane P(vi,vj) so that . To obtain this result, we apply the following relation (for its derivation see Appendix B):
- 8)
- Construct the unitary transformation matrix Gb which rotates clockwise a single pair of right singular vectors, i.e., vi and vj, in the plane P(vi, vj), by an angle φb:
- 9)
- Apply the transformation matrix to Vb:where V’b is the modified matrix of the right singular vectors.
- 10)
- Reconstruct the modified watermarked image block using V’b:
4.2 Watermark detection
- 1)
- Apply the first three steps of the embedding on the possible watermarked and attacked image, Iwa, by means of the secret key K.
- 2)
- Construct the feature set F’ with angles computed using the same procedure presented in step 5 of the embedding process. The angle θ’b is determined using vectors v’i and v’j and their relative components x’ = v’ki, y’ = v’li, z’ = v’kj and w’ = v’lj, according to the following relation:
- 3)
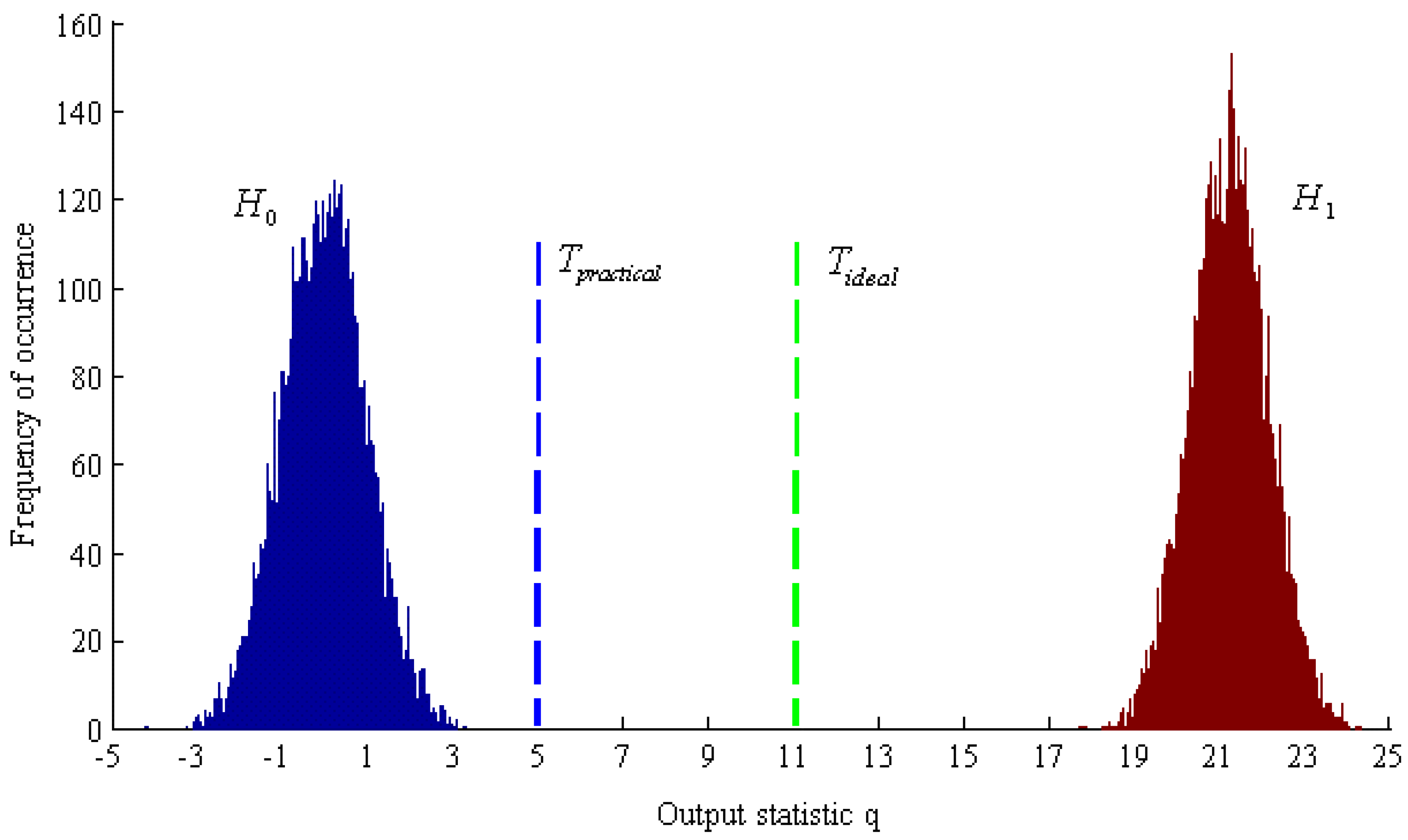
- To detect the watermark in the extracted feature set F’ we construct the following hypothesis test [53]:where F and F’ are, respectively, the initial and the extracted feature sets, W is the watermark sequence and Z is the noise signal. Under the null hypothesis H0 the original image is unmarked, whereas under the alternative hypothesis H1 the watermark sequence W is embedded into the original image.
- 4)
- Compute the test statistic q with the following relation:where MeanY and VarY are, respectively, the sample mean and the Root Mean Square Error (RMSE) of , whilst L=n2 is the size of the feature set F’. According to [53], since the watermark strength factor β is a constant value, then it is possible to use , that is the sequence generated from the seed contained in the key. Intuitively, the value q measures the correlation between the watermark sequence and the extracted feature set.
- 5)
- The value of q computed above is compared with the acceptance threshold T which is calculated, under the hypothesis H1 and for large L, with the relation:where is the mean of the distribution of the output statistic q under the hypothesis H1.As proposed by Zeng et al. [53], in the above relation we disregard the noise factor Z; then, if , we consider that the watermark sequence W is present in the feature set F’.
5. Considerations on the Proposed Scheme
- Imperceptibility: A perfectly imperceptible bit sample of the watermark is present if the watermarked media and the original cannot be distinguished.
- Undetectability: The digital content due to the carried watermark information is not detectable if it is consistent with the original data. Non-detectability cannot be directly linked to non-perceptibility that is based on the concepts of human perceptions. Non-detectability is related to the data source and its components. It describes the consistency with the original data.
- The seed used to generate the watermark sequence W, i.e., the Gaussian distribution with zero mean and unitary variance.
- The singular vectors chosen in the watermarking process and their components from which we construct the feature set. For each block of the cover image, the secret key K produces the right singular vectors and the specific pair of their components. Note that more than one couple of vectors can be chosen to embed the watermark, with the purpose to improve the overall robustness of the watermarking process.
6. Experimental Results
- to generate a sufficiently long sequence of features which allows to maintain the statistical properties required by the insertion/detection method;
- to have a high speed of computation of the SVD;
- to maintain a good visual quality of the watermarked image.

| Threshold T | Probability of False positive error Pf [Pf (q ≥ T)] |
|---|---|
| 3 | 3×10-4 |
| 4 | 1.23×10-7 |
| 5 | 2.54×10-12 |
| 1.36×10-20 |
| Attack | Factor | Average of the output statistic q | |
|---|---|---|---|
| Sampling | Down | 0.7 | 10.14 |
| 0.8 | 14.56 | ||
| Up | 1.3 | 20.16 | |
| 1.75 | 18.78 | ||
| JPEG Compression | QF = 90 | 15.75 | |
| QF = 80 | 11.17 | ||
| QF = 70 | 7.94 | ||
| QF = 60 | 5.83 | ||
| Additive White Gaussian Noise | 1% | 17.69 | |
| 2% | 12.87 | ||
| 3% | 10.59 | ||
| Salt & Pepper Noise | Density = 0.001 | 12.81 | |
| Density = 0.003 | 9.55 | ||
| Density = 0.005 | 7.11 | ||
| Row-Column Copying | 5-11 | 18.63 | |
| 35-78 | 19.08 | ||
| 67-437 | 18.03 | ||
| 3-16, 43-72 | 17.88 | ||
| 139-126, 123-211 | 18.21 | ||
| 333-164, 431-142 | 17.50 | ||
| 14-26, 169-99, 119-192 | 17.27 | ||
| 139-126, 123-211,43-72 | 16.80 | ||
| 5-11, 35-78, 67-437 | 17.01 | ||
| Row Column Blanking | 5-11 | 19.65 | |
| 35-78 | 20.07 | ||
| 67-437 | 20.54 | ||
| 3-16, 43-72 | 19.12 | ||
| 139-126, 123-211 | 20.81 | ||
| 333-164, 431-142 | 19.75 | ||
| 14-26, 169-99, 119-192 | 17.64 | ||
| 139-126, 123-211,43-72 | 17.27 | ||
| 5-9, 11-67, 437-500 | 17.60 | ||
| Gamma Correction | γ = 0.6 | 10.31 | |
| γ = 0.8 | 13.76 | ||
| γ = 1.1 | 14.04 | ||
| γ = 1.2 | 12.05 | ||
| γ = 1.5 | 10.58 | ||
| Cropping | 10% | 17.12 | |
| 20% | 15.26 | ||
| 25% | 14.41 | ||
| 30% | 10.34 | ||
- increasing the strength factor β;
- decreasing the multiplicative factor δ;
- increasing the size of the blocks of the original images used in the embedding process.
- 1-column copying (e.g., we copied the 5th column to the 11th column or the 35th column to the 78th column or the 67th column to the 437th column);
- 2-columns copying (e.g., we copied the 3rd column to the 16th column and the 43rd column to the 72nd column, etc.);
- 3-columns copying (e.g., we copied the 14th column to the 26th column and the 169th column to the 99th column and the 119th column to the 192nd column, etc.).
- 1-row 1-column blanking (e.g., we deleted the 5th row and the 11th column, etc.);
- 2-rows 2-columns blanking (e.g., we deleted the 3rd and 43rd rows and the 16th and 72nd columns, etc.);
- 3-rows 3-columns blanking (e.g., we deleted the 14th, 169th and 119th rows and the 26th, 99th and 192nd columns, etc.).

- the scheme proposed by Patra et al. [40] due to the lack of information regarding the quality of the watermarked image (i.e., PSNR) and the test performed to demonstrate the robustness of the scheme;
- the watermarking schemes based on singular values (SVs) since they are subject to the security and false positive problems, described in section 3. A discussion on the security of the watermarking schemes based on SVs is presented in Appendix C.
- the size of the test images equal to ;
- a binary image of size as watermark;
- the segmentation block size equal to ;
- the threshold th set to 0.012;
- Quality of the watermarked image. Our scheme produces a perceptually good watermarked image (PSNR 38 dB) since it modifies the middle singular vectors in each block (i.e., the 6th and 7th right singular vectors). Differently from the Chung’s scheme, which embeds the watermark into the first singular vector in each block, our method discards the first two couples of vectors to maintain the image quality as high as possible.
- Robustness against attacks. From Table 3, it can be observed that the Chung’s method performs well against cropping and row and column blanking/copying. Instead, when other attacks are applied, the detection ratio considerably decreases as the scheme fails to extract the watermark from all attacked images. Moreover, the Chung’s scheme has worse performance compared to ours when JPEG compression and noise addition are applied and doesn’t resist to down-sampling and gamma correction attacks. In our opinion this behavior is due to the way the watermark is embedded into the cover image, i.e., the orthogonality property of the singular vectors is not maintained in the embedding process. On the contrary, preserving such a property allows our scheme to detect the watermark from all attacked images, except when JPEG compression with quality factor 60 is applied (but still having a detection ratio equal to 94%).
| Attack | Factor | Detection Ratio | |||
| Proposed | Chung et al. | ||||
| Sampling | Down | 0.7 | 100% | 0% | |
| 0.8 | 100% | 0% | |||
| Up | 1.3 | 100% | 100% | ||
| 1.75 | 100% | 33% | |||
| JPEG Compression | QF = 90 | 100% | 100% | ||
| QF = 80 | 100% | 86% | |||
| QF = 70 | 100% | 31% | |||
| QF = 60 | 94% | 11% | |||
| Additive White Gaussian Noise | 1% | 100% | 93% | ||
| 2% | 100% | 21% | |||
| 3% | 100% | 5% | |||
| Salt & Pepper Noise | D = 0.001 | 100% | 100% | ||
| D = 0.003 | 100% | 55% | |||
| D = 0.005 | 100% | 33% | |||
| Row-Column Copying | 5-11 | 100% | 97% | ||
| 35-78 | 100% | 97% | |||
| 67-437 | 100% | 96% | |||
| 3-16, 43-72 | 100% | 91% | |||
| 139-126, 123-211 | 100% | 91% | |||
| 333-164, 431-142 | 100% | 92% | |||
| 14-26, 169-99, 119-192 | 100% | 90% | |||
| 139-126, 123-211,43-72 | 100% | 90% | |||
| 5-11, 35-78, 67-437 | 100% | 92% | |||
| Row Column Blanking | 5-11 | 100% | 95% | ||
| 35-78 | 100% | 95% | |||
| 67-437 | 100% | 95% | |||
| 3-16, 43-72 | 100% | 93% | |||
| 139-126, 123-211 | 100% | 92% | |||
| 333-164, 431-142 | 100% | 93% | |||
| 14-26, 169-99, 119-192 | 100% | 90% | |||
| 139-126, 123-211,43-72 | 100% | 94% | |||
| 5-9, 11-67, 437-500 | 100% | 94% | |||
| Gamma Correction | γ = 0.6 | 100% | 0% | ||
| γ = 0.8 | 100% | 0% | |||
| γ = 1.1 | 100% | 0% | |||
| γ = 1.2 | 100% | 0% | |||
| γ = 1.5 | 100% | 0% | |||
| Cropping | 10% | 100% | 100% | ||
| 20% | 100% | 92% | |||
| 25% | 100% | 55% | |||
| 30% | 100% | 50% | |||
- Security. The security property of our watermarking scheme is granted by the capability to choose one or more couples of vectors among a set of many possible candidates. In addition, a further improvement to security is assured by selecting any pair of components of the chosen singular vectors. Instead, we can not say that the algorithm proposed by Chung is secure because it always embeds the watermark by modifying the same components (2nd and 3rd) of the first singular vector.
- Type of the watermark. In our scheme, the watermark is a pseudo-random Gaussian sequence whereas in Chung’s scheme it can be a significant watermark (i.e., binary or a gray-scale image). In general, it is better to use a significant mark in the watermarking process because of the possibility, in the detection step, to visually compare the original watermark with the inserted one [31].
7. Conclusions
Acknowledgements
Appendix A
Appendix B
- l-th component: vli cos φ – vlj sin φ
- k-th component: vki cos φ – vkj sin φ
Appendix C
- when both images A and B are watermarked by different owners, the watermark in A may be completely substituted by the one in B, therefore changing the ownership of the image;
- when only image A is marked, the substitution of its SVs with those of an unmarked image B causes the watermark removal from A, and by consequence, a failure in proving the rightful ownership of A.


References
- Seitz, J.; Jahnke, T. Digital Watermarking: An introduction. In Digital Watermarking for Digital Media; Information Science Publishing: Hershey, Pennsylvania, USA, 2005; pp. 19–20. [Google Scholar]
- Johnson, N.F.; Katezenbeisser, S.C. A Survey of Steganographic Techniques. In Information Techniques for Steganography and Digital Watermarking; Katzenbeisser, S.C., Petitcolas, F.A.P., Eds.; Artech House: Northwood, Massachusetts, USA, 1999; pp. 43–75. [Google Scholar]
- Schyndel, R.G.; Tirkel, A.Z.; Osborne, C.F. A digital watermark. In Proceedings of IEEE International Conference on Image Processing (ICIP’94), Austin Texas, USA, November 13-16, 1994; 2, pp. 86–90.
- Langelaar, G.; Setyawan, I.; Lagendijk, R.L. Watermarking Digital Image and Video Data. In IEEE Signal Processing Magazine; Piscataway: New Jersey, USA, September 2000; Volume 17, pp. 20–46. [Google Scholar]
- Wollan, H. Digital Watermarking in Still Images. Proceedings of the Computer Science Discipline Seminar Conference (CSCI 3901), University of Minnesota, Morris, Spring 2000; Available on http://cda.morris.umn.edu/~lopezdr/seminar/spring2000/wollan.pdf.
- Podilchuk, C.; Zeng, W. Image-adaptive watermarking using visual models. IEEE J. Sel. Are. Comm. 1998, 16, 525–539. [Google Scholar] [CrossRef]
- Cox, I.; Kilian, J.; Leighton, F. T.; Shamoon, T. Secure spread spectrum watermarking for multimedia. In IEEE Transaction on Image Processing; Piscataway, New Jersey, USA, December 1997, Volume 6, pp. 1673–1687.
- Ruanaidh, J.J.K.; Dowling, W.J.; Boland, F.M. Phase watermarking of digital images. In Proceedings of the 1996 International Conference on Image Processing, Lausanne, Switzerland, September 1996; 3, pp. 239–242.
- Dugad, R.; Ratakonda, K.; Ahuja, N. A new wavelet-based scheme for watermarking images. In International Conference on Image Processing Proceedings (ICIP 98), Chicago, USA, October 4-7, 1998; 2, pp. 419–423.
- Wolfgang, R. B.; Podilchuk, C. I.; Delp, E. J. Perceptual watermarks for digital images and video. In Proceedings of the IEEE, Bellingham, USA, July 1999; 87, pp. 1108–1126.
- Bartolini, F.; Barni, M.; Cappellini, V.; Piva, A. Mask building for perceptually hiding frequency embedded watermarks. In Proceedings of the International Conference on Image Processing (ICIP 98), Chicago, Illinois, USA, 1998; 1, pp. 450–454.
- Lin, E.T.; Delp, E.J. A Review of Fragile Image Watermarks. In Proceedings of ACM Multimedia & Security Workshop, Orlando, USA, October 1999; pp. 25–29.
- Kutter, M.; Hartung, F. Introduction to watermarking techniques. In Information Hiding Techniques for Steganography and Digital Watermarking; Katzenbeisser, Stefan, Petitcolas, F.A.P., Eds.; Artech House: Nordwood, Massachusetts, USA, 2000; pp. 97–120. [Google Scholar]
- Craver, S.; Memon, D. N.; Yeo, B.-L.; Minerva, M. M. Can invisible watermarks resolve rightful ownerships? In Proceedings of SPIE, Bellingham, USA, 1997; 3022, pp. 310–321.
- Wu, H.-C.; Yeh, C.-P.; Tsai, C.-S. A Semi-fragile Watermarking Scheme Based on SVD and VQ Techniques. In Workshop on Applied Cryptography and Information Security (ACIS 2006), LNCS 3982; Springer Berlin/Heidelberg: Germany, 2006; pp. 406–415. [Google Scholar]
- Ling, H.-C.; Phan, C.-W.; Heng, S.-H. Attacks on SVD-Based Watermarking Schemes. In Proceedings of ISI 2008 Workshop, Taipei, Taiwan, LNCS 5075, Springer Berlin/Heidelberg, Germany, June 2008; pp. 83–91.
- Yang, J.-F.; Lu, C.-L. Combined Techniques of Singular Value Decomposition and Vector Quantization for Image Coding. In IEEE Transaction on Image Processing; Piscataway, New Jersey, USA, August 1995, Volume 4, pp. 1141–1146.
- Andrews, H.C.; Patterson, C.L. Singular Value Decomposition (SVD) Image Coding. In IEEE Transactions on Communications; Piscataway, New Jersey, USA, April 1976, pp. 425–432.
- Shnayderman, A.; Gusev, A.; Eskicioglu, A. A Multidimensional Image Quality Measure Using Singular Value Decomposition. In Proceedings of the SPIE Image Quality and System Performance Conference, San Jose, California, USA, January 19-20, 2004; 5294, pp. 82–92.
- Gorodetski, V.I.; Popyack, L.J.; Samoilov, V. SVD-Based Approach to Transparent Embedding Data into Digital Images. In Proceedings of International Workshop on Mathematical Methods, Models and Architectures for Computer Network Security (MMM-ACNS01), St. Petersburg, Russia, 2001; pp. 263–274.
- Calagna, M.; Guo, H.; Mancini, L.V.; Jajodia, S. Robust Watermarking System based on SVD Compression. In Proceedings of the 2006 ACM Symposium on Applied Computing, Dijon, France, April 23 -27, 2006; pp. 1341–1347.
- Liu, J.; Niu, X.; Kong, W. Image watermarking scheme based on singular value decomposition. In International Conference on Intelligent Information Hiding and Multimedia, Pasadena, California, USA, December 2006; 2006; pp. 457–460. [Google Scholar]
- Liu, R.; Tan, T. A new SVD based Image Watermarking method. In IEEE Transactions on Multimedia, Piscataway, New Jersey, USA, March 2002; 4, pp. 121–128.
- Ganic, E.; Zubair, N.; Eskicioglu, A. M. An Optimal Watermarking Scheme Based on Singular Value Decomposition. In Proceedings of the IASTED International Conference on Communication, Network, and Information Security (CNIS 2003), Uniondale, New York, USA, December 10-12, 2003; pp. 85–90.
- Chandra, D. Digital image watermarking using singular value decomposition. In Proceedings of the IEEE 45th Midwest Symposium on Circuits and Systems, Oklahoma State University, USA, August 4-7, 2002; 3, pp. 264–267.
- Shieh, J.-M.; Lou, D.-C.; Chang, M.-C. A semi-blind digital watermarking scheme based on singular value decomposition. In Computer Standards & Interfaces; Elsevier, April 2006; Volume 28, pp. 428–440. [Google Scholar]
- Chang, C.-C.; Hu, Y.-S.; Lin, C.-C. A Digital watermarking scheme based on singular value decomposition. In Proceedings of the International Symposium on Combinatory, Algorithms, Probabilistic and Experimental Methodologies Hangzhou, China, LNCS 4614, Springer Berlin/Heidelberg, Germany, September 2007; pp. 82–93.
- Chang, C.-C.; Lin, C.-C.; Hu, Y.-S. An SVD oriented watermark embedding scheme with high qualities for the restored images. In International Journal of Innovative Computing, Information and Control (IJICIC); Toroku, Kumamoto, Japan, June 2007, Volume 3, pp. 609–620.
- Mohan, B.C.; Srinivaskumar, S.; Chatterji, B.N. A Robust Digital Image Watermarking Scheme using Singular Value Decomposition (SVD), Dither Quantization and Edge Detection. ICGST-GVIP J. 2008, 8, 17–23. [Google Scholar]
- Rezazadeh, S.; Yazdi, M. A Nonoblivious Image Watermarking System Based on Singular Value Decomposition and Texture Segmentation. In Proceedings of the World Academy of Science, Engineering and Technology, Budapest, Hungary, May 26-28, 2006; 13, pp. 255–259.
- Mohammad, A.A.; Alhaj, A.; Shaltaf, S. An improved SVD-based watermarking scheme for protecting rightful ownership. In Signal Processing; Elsevier North-Holland: Amsterdam, The Netherlands, September 2008; Volume 88, pp. 2158–2180. [Google Scholar]
- Ting, G.C.-W. Ambiguity Attacks on the Ganic-Eskicioglu Robust DWT-SVD Image Watermarking Scheme. In Proceedings of Information Security and Cryptology (ICISC 2005), Seoul, Korea, LNCS 3935, Springer Berlin/Heidelberg, Germany, 2006; pp. 378–389.
- Wu, Y. On the Security of an SVD-Based Ownership Watermarking. In IEEE Transactions On Multimedia; Piscataway, New Jersey, USA, August 2005, Volume 7, pp. 624–627.
- Zhang, X.-P.; Li, K. Comments on An SVD-Based watermarking scheme for protecting rightful Ownership. IEEE Trans. Multimed. 2005, 7, 593–594. [Google Scholar] [CrossRef]
- Yavuz, E.; Telatar, Z. SVD Adapted DCT Domain DC Sub-band Image Watermarking Against Watermark Ambiguity. In Proceedings of International Workshop on Multimedia Content Representation, Classification and Security (IW-MRCS2006). LNCS 4105, Istanbul, Turkey, 2006; pp. 66–73.
- Cox, I.J.; Miller, M.L.; Bloom, J.A. Digital Watermarking; Morgan Kaufmann Publishers Inc.: San Francisco, USA, 2001. [Google Scholar]
- Craver, S.; Memon, D.N.; Yeo, B.-L.; Yeung, M.M. Resolving rightful ownerships with invisible watermarking techniques: Limitations, attacks, and implications. In IEEE Journal on Selected Areas in Communications, California, USA, May 1998; 16, pp. 573–586.
- Ghazy, R.; El-Fishawy, N.; Hadhoud, M.; Dessouky, M.; El-Samie, F. An efficient block-by block SVD-based image watermarking scheme. In Proceedings of the 24th National Radio Science Conference, Cairo, Egypt, March 2007; pp. 1–9.
- Chang, C.-C.; Tsai, P.; Lin, C.-C. SVD-based Digital Image Watermarking scheme. In Pattern Recognition Letters; Elsevier, 2005; Volume 26, pp. 1577–1586. [Google Scholar]
- Patra, J.C.; Soh, W.; Ang, E.L.; Meher, P.K. An Improved SVD-Based Watermarking Technique for Image and Document Authentication. In Circuits and Systems (APCCAS 2006), IEEE Asia Pacific, Singapore, December 4-7, 2006; 2006; pp. 1984–1987. [Google Scholar]
- Mohan, B.C.; Kumar, S. A Robust Digital Image Watermarking Scheme using Singular Value Decomposition. J. Multimed. 2008, 3, 7–15. [Google Scholar] [CrossRef]
- Chung, K.-L.; Yang, W.-N.; Huang, Y.-H.; Wu, S.-T.; Hsu, Y.-C. On SVD-based watermarking algorithm. Appl. Math. Comput. 2007, 8, 54–57. [Google Scholar] [CrossRef]
- Sverdlov, A.; Dexter, S.; Eskicioglu, A. M. Robust DCT-SVD domain image watermarking for copyright protection: embedding data in all frequencies. In Proceedings of 13th European Signal Processing Conference (EUSIPCO2005), Antalya, Turkey, September 2005; pp. 4–8.
- Tsai, C.-F.; Yang, W.-Y. Real-Time Color Image Watermarking Based on D-SVD Scheme. In Advances in Image and Video Technology, LNCS 4872, Springer Berlin/Heidelberg, Germany, December 2007; pp. 289–297.
- Liu, F.; Liu, Y. watermarking Algorithm for Digital Image based on DCT and SVD. In IEEE Congress on Image and Signal Processing, Sanya, Hainan, China, May 27-30, 2008; 1, pp. 380–383.
- Ganic, E.; Eskicioglu, A.M. Robust DWT-SVD Domain Image Watermarking: Embedding Data in All Frequencies. In Proceedings of the ACM Multimedia and Security workshop, Magdeburg, Germany, September 20-21, 2004; pp. 167–174.
- Lin, C.-H.; Liu, J.-C.; Han, P.-C. On the Security of the Full-Band Image Watermark for Copyright Protection. In IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, June 11-13, 2008; pp. 74–80.
- Li, H.; Wang, S.; Song, W.; Wen, Q. A Novel Watermarking Algorithm Based on SVD and Zernike Moments. In LNCS 3495, Springer Berlin/Heidelberg, Germany, 2005; pp. 448–453.
- Tang, X.; Yang, L.; Li, L.; Niu, Y. Study on a Multifunctional watermarking Algorithm. In In Proceedings of IEEE ICSP’2004, Istanbul, Turkey, 2004; 1, pp. 848–852.
- Sugiyama, M.; Goto, M.; Kovács, S.; Matsumoto, T.; Naoi, T. A cropping-robust watermarking method based on singular value decomposition and Haar transformation. Syst. Comp. Japan 2003, 34, 38–47. [Google Scholar] [CrossRef]
- Byun, S.-C.; Lee, S.-K.; Tewfik, A. H.; Ahn, B.-H. A SVD-Based Fragile Watermarking Scheme for Image Authentication. In Proceedings of First International Workshop (IWDW 2002), Seoul, Korea, LNCS 2613, Springer Berlin/Heidelberg, Germany, 2003; pp. 375–391.
- Sun, R.; Sun, H.; Yao, T. A SVD and quantization based semi-fragile watermarking technique for image authentication. In Proceedings of the 6th International Conference on Signal Processing (ICSP’02), Rochester, USA, 2002; 2, pp. 1592–1595.
- Zeng, W.; Liu, B. A statistical watermark detection technique without using original images for resolving rightful ownership of digital images. In IEEE Transactions on Image Processing, Piscataway, New Jersey, USA, November 1999; 8, pp. 1534–1548.
- Stathaki, T.; Dafas, P. Digital Image Watermarking Using Block-Based Karhunen-Loeve Transform. In Proceedings of the 3rd International Symposium (ISPA), Rome, Italy, September 18-20, 2003; 2, pp. 1072–1075.
- Anderson, E.; Bai, Z.; Bischof, C.; Blackford, S.; Demmel, J.; Dongarra, J.; Croz, D.J.; Greenbaum, A.; Hammarling, S.; Mckenney, A.; Sorensen, D. LAPACK User’s Guide, third edition; SIAM: Philadelphia, Philadelphia, USA, 1999. [Google Scholar]
- Bro, R.; Acar, E.; Kolda, T.G. Resolving the sign ambiguity in the singular value decomposition. J. Chemometr. 2008, 22, 135–140. [Google Scholar]
- Lu, C.-S. Multimedia Security: Steganography and Digital Watermarking Techniques for Protection of Intellectual Property; Idea Group Publishing (an imprint of Idea Group Inc.): Hershey, Pennsylvania, USA, 2005; Chapter 2. [Google Scholar]
- Li, L.-J.; Wang, G.; Li, F.-F. OPTIMOL: automatic Object Picture collecTion via Incremental MOdel Learning. In IEEE Computer Vision and Pattern Recognition (CVPR), Minneapolis, USA, 2007; pp. 1–8.
- Schaefer, G.; Stich, M. UCID - An Uncompressed Colour Image Database. In Proceedings of SPIE, Storage and Retrieval Methods and Applications for Multimedia, San Jose, USA, 2004; 5307, pp. 472–480.
- Schlauweg, M.; Pröfrock, D.; Zeibich, B.; Müller, E. Dual watermarking for protection of rightful ownership and secure image authentication. In Proceedings of the 4th ACM international workshop on Contents protection and security, Santa Barbara, California, USA, 2006; pp. 56–66.
- Wolfram Mathematica; Wolfram Research Inc. Web Resource: http://reference.wolfram.com/ mathematica/ref/ArcTan.html 2008.
© 2009 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Basso, A.; Bergadano, F.; Cavagnino, D.; Pomponiu, V.; Vernone, A. A Novel Block-based Watermarking Scheme Using the SVD Transform. Algorithms 2009, 2, 46-75. https://doi.org/10.3390/a2010046
Basso A, Bergadano F, Cavagnino D, Pomponiu V, Vernone A. A Novel Block-based Watermarking Scheme Using the SVD Transform. Algorithms. 2009; 2(1):46-75. https://doi.org/10.3390/a2010046
Chicago/Turabian StyleBasso, Alessandro, Francesco Bergadano, Davide Cavagnino, Victor Pomponiu, and Annamaria Vernone. 2009. "A Novel Block-based Watermarking Scheme Using the SVD Transform" Algorithms 2, no. 1: 46-75. https://doi.org/10.3390/a2010046
APA StyleBasso, A., Bergadano, F., Cavagnino, D., Pomponiu, V., & Vernone, A. (2009). A Novel Block-based Watermarking Scheme Using the SVD Transform. Algorithms, 2(1), 46-75. https://doi.org/10.3390/a2010046





