Supporting Sustainable Maintenance of Substations under Cyber-Threats: An Evaluation Method of Cybersecurity Risk for Power CPS
Abstract
:1. Introduction
2. Cyber-Security Analysis of the SAS in a Power CPS
2.1. Procedure and Tools of Cyberattacks
2.2. Paths of Cyberattacks on an SAS
2.3. Security Countermeasures of the SAS
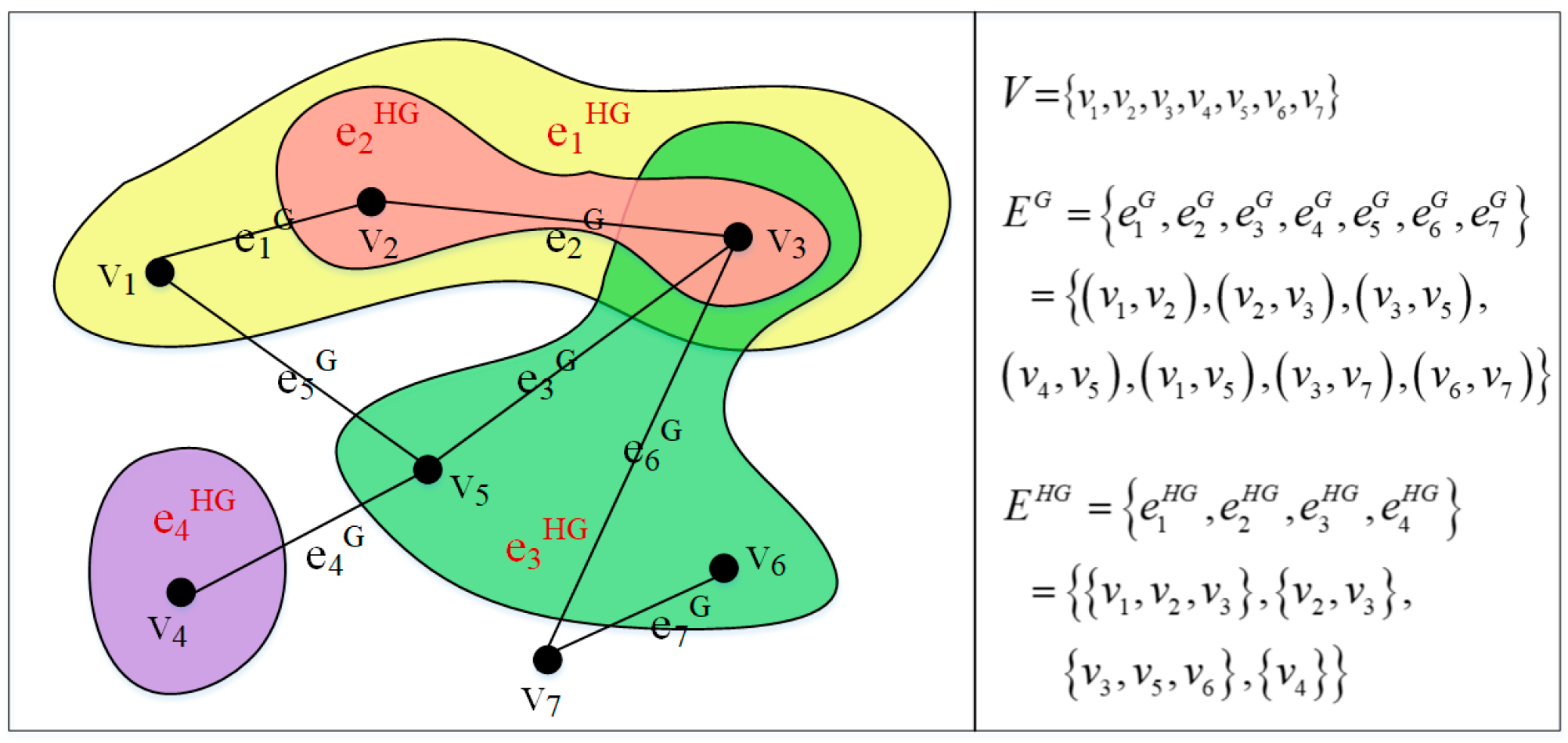
3. Modified Hypergraph Model of the SAS in a Power CPS
3.1. Introduction to SAS Structure
3.2. Definitions of Modified Hypergraph
3.2.1. Basic Definition
3.2.2. Matrix Expressions
3.3. Modified Hypergraph Model of the SAS
4. Evaluation Framework for the Risk of a Power CPS
4.1. Substructure Model
4.2. Superstructure Model
4.2.1. Model of Time Delay Accumulation
| Algorithm 1. Modeling and calculating time delay accumulation under jamming attacks. |
| Note: The equation of the data flow network is . |
| Input: The actual communication network topology, the parameters of devices in the communication network, the types of data injected, the priority queuing in the SAS, the targets of jamming attacks, jamming attack technology, and the modified hyper-graph model of the SAS. |
| Output: The time delay of data flows mapped to the modified hyper-graph model. |
| Initialization: The number of information sources , the types of information sources, the initial state of data paths in communication network , and the matrix expressions of the modified hypergraph model of SAS k before jamming attacks and |
| Step 1: Construct the vector of injected information flow for ← 0 to do = 185;// if the information source is an intelligent electronic device (IED) && the type of message is GOOSE = 152;// else if the information source is MU && the type of message is SV = 524;// else if the information source is PC && the type of message is MMS = ∞;// else end for |
| Step 2: Construct the matrix of the communication network connection , where represents port. ;// if there is a connection between port and port , and they are in different devices ;// if there is a connection between port and port , and they are in the same device , ;// else |
| Step 3: Calculate the matrix of data flow path by the iterative method,
|
| Step 4: Construct the equivalent bandwidth matrix of the data stream between switch port and information source according to Equation (18). The element is calculated as follow:
|
| Step 5: Calculate the equivalent velocity matrix :
|
| Step 6: Calculate the delay matrix of different data paths, . |
| Step 7: Map the actual communication paths to sets of edges in the modified hyper-graph model of the SAS, assigning the maximum summed weight of each edge set to the accumulated time delay of data flow from the original LN to its destination. |
4.2.2. Model of Data Error Propagation
| Algorithm 2. Constructing the similarity adjacency matrix of hyper-edges . |
| Input: The modified hyper-graph model of SAS, the attributes of the target and the hyper-edge name it belongs to |
| Output: |
| Initialize: The number of hyper-edges = 0, hyper-incidence matrix . |
| Step 1: Define a function IsHyperTrangle() to judge whether three logical nodes and two hyper-edges can form a hyper-triangle. If yes, return 1, otherwise return 0 #define int IsHyperTrangle(HE1,HE2,LN1,LN2,LN3, ) { ; ; ; // Initialization ; // = 1 indicates LN1 and LN2 belong to hyper-edge HE1 ;// ; for ← 0 to do ; end for ;// indicates LN3 and LN1 belong to a hyper-edge, where is a signum function return ; } |
| Step 2: Construct the similarity adjacency matrix of hyper-edges . for ← 0 to do for ← 0 to & do ; // The set of total LNs in hyperedge i and j. ; // The set of common LNs in hyperedge i and j. ; // The number of total LNs in hyperedge i and j. ; // The number of common LNs in hyperedge i and j. for ← 0 to do for ← 0 to & do for ← 0 to & & do = IsHyperTrangle (i, j, m, n, l,); = IsHyperTrangle (i, j, n, l, m,); = IsHyperTrangle (i, j, l, m, n,); = IsHyperTrangle (i, j, m, l, n,); = IsHyperTrangle (i, j, l, n, m,); = IsHyperTrangle (i, j, n, m, l,); ; end for end for end for ; // is the combination of 3 in . end for end for |
4.2.3. Model of Cybersecurity Risk Evaluation
4.3. Calculation Flow
5. Case Study and Discussions
5.1. Analysis of Cybersecurity Events
5.1.1. Cybersecurity Event 1
5.1.2. Cybersecurity Event 2
5.2. Comparative Analysis of Cybersecurity Risks
5.2.1. Comparative Analysis of Risks with Different Target LNs
5.2.2. Comparative Analysis of Risks with Different Data Attack Technologies
5.2.3. Comparative Analysis of Risks with Different Target SASs
5.3. Comparisons with other Methods and Discussion
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Lee, I.; Liu, S.; Stankovic, J. Cyber-Physical Systems: The next computing revolution. In Proceedings of the Design Automation Conference IEEE, Anaheim, CA, USA, 13–18 June 2010; pp. 731–736. [Google Scholar]
- Mo, Y.; Kim, T.H.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyber-physical security of a smart grid infrastructure. Proc. IEEE 2011, 100, 195–209. [Google Scholar]
- Xin, S.; Guo, Q.; Sun, H.; Zhang, B.; Wang, J.; Chen, C. Cyber-physical modeling and cyber-contingency assessment of hierarchical control systems. IEEE Trans. Smart Grid 2017, 6, 2375–2385. [Google Scholar] [CrossRef]
- Mo, H.; Sansavini, G. Dynamic defense resource allocation for minimizing unsupplied demand in cyber-physical systems against uncertain attacks. IEEE Trans. Reliab. 2017, 66, 1253–1265. [Google Scholar] [CrossRef]
- Wurm, J.; Jin, Y.; Liu, Y.; Hu, S.; Heffner, K.; Rahman, F.; Tehranipoor, M. Introduction to cyber-physical system security: A cross-layer perspective. IEEE Trans. Multi-Scale Comput. Syst. 2017, 3, 215–227. [Google Scholar] [CrossRef]
- Ye, X.M.; Wen, F.S.; Shang, J.C.; He, Y. Propagation mechanism of cyber physical security risks in power systems. Power Syst. Technol. 2015, 39, 3072–3079. [Google Scholar]
- Tang, Y.; Han, X.; Wu, Y.; Ju, Y.; Zhou, X.; Ni, M. Electric power system vulnerability assessment considering the influence of communication system. Proc. CSEE 2015, 35, 6066–6074. [Google Scholar]
- Teixeira, A.; Sou, K.C.; Sandberg, H.; Johansson, K.H. Secure control systems a quantitative risk management approach. IEEE Control Syst. 2015, 35, 24–45. [Google Scholar]
- Understanding Denial-of-Service Attacks. Available online: https://www.uscert.gov/ncas/tips/ST04-015 (accessed on 14 February 2018).
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electronic power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Teixeira, A.; Shames, I.; Sandberg, H.; Johansson, K.H. A secure control framework for resource-limited adversaries. Automatica 2015, 51, 135–148. [Google Scholar] [CrossRef] [Green Version]
- IEC Standard for Power Systems Management and Associated Information Exchange—Data and Communications Security, Part 1 Communication Network and System Security—Introduction to Security Issues; IEC TS 62351-1; IEC: Geneva, Switzerland, 2007.
- Liu, N.; Zhang, J.; Zhang, H.; Liu, W. Vulnerability assessment for communication network of Substation Automation Systems to cyber attack. Power Syst. Conf. Expo. 2009, 20, 1–7. [Google Scholar]
- Guo, Y.; Duan, R.; Cao, J.; Li, S. Power Grid Vulnerability Identifying Based on Complex Network Theory. Int. Conf. Instrum. 2013, 7, 474–477. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ji, X.; Wang, B.; Liu, D.; Dong, Z.; Chen, G.; Zhu, Z.; Zhu, X.; Wang, X. Will electrical cyber–physical interdependent networks undergo first-order transition under random attacks? Phys. A Stat. Mech. Appl. 2016, 460, 235–245. [Google Scholar] [CrossRef]
- Xin, S.; Guo, Q.; Sun, H.; Chen, C.; Wang, J.; Zhang, B. Information-energy flow computation and cyber-physical sensitivity analysis for power systems. IEEE J. Emerg. Sel. Top. Circuits Syst. 2017, 7, 329–341. [Google Scholar] [CrossRef]
- Fan, Y.; Li, J.; Zhang, D. A method for identifying critical elements of a cyber-physical system under data attack. IEEE Access 2018, 6, 16972–16984. [Google Scholar] [CrossRef]
- Jiang, X.; Yang, J.; Jin, G.; Wei, W. RED-FT: A scalable random early detection scheme with flow trust against dos attacks. IEEE Commun. Lett. 2013, 17, 1032–1035. [Google Scholar] [CrossRef]
- Zhao, J.; Mili, L.; Wang, M. A generalized false data injection attacks against power system nonlinear state estimator and countermeasures. IEEE Trans. Power Syst. 2018, 33, 4868–4877. [Google Scholar] [CrossRef]
- Vellaithurai, C.; Srivastava, A.; Zonouz, S.; Berthier, R. CPIndex: Cyber-physical vulnerability assessment for power-grid infrastructures. IEEE Trans. Smart Grid 2015, 6, 566–575. [Google Scholar] [CrossRef]
- Wu, W.; Kang, R.; Li, Z. Risk assessment method for cybersecurity of cyber-physical systems based on inter-dependency of vulnerabilities. In Proceedings of the IEEE International Conference on Industrial Engineering & Engineering Management, Singapore, 6–9 December 2015; pp. 1618–1622. [Google Scholar]
- Axelsson, S. The base-rate fallacy and its implications for the difficulty of intrusion detection. ACM Trans. Inf. Syst. Secur. 1999, 4, 186–205. [Google Scholar]
- Chen, Y.; Hong, J.; Liu, C.C. Modeling of intrusion and defense for assessment of cyber security at power substations. IEEE Trans. Smart Grid 2016, 9, 2541–2552. [Google Scholar] [CrossRef]
- Winterfeld, S.; Andress, J. The Basics of Cyber Warfare: Understanding the Fundamentals of Cyber Warfare in Theory and Practice; Syngress Publishing: Rockland, MA, USA, 2012; pp. 51–66. [Google Scholar]
- IEC Standard for Power Systems Management and Associated Information Exchange. Data and Communications Security, Part 8 Role-Based Access Control; IEC TS 62351-8; IEC: Geneva, Switzerland, 2011.
- IEC Standard for Communication Network and Systems in Substations, Part 1 Introduction and Overview; IEC 61850-1; IEC: Geneva, Switzerland, 2003.
- IEC Standard for Power Systems Management and Associated Information Exchange—Data and Communications Security, Part 6 Security for IEC 61850; IEC TS 62351-6; IEC: Geneva, Switzerland, 2007.
- IEC Standard for Communication Networks and Systems for Power Utility Automation, Part 8-1: Specific Communication Service Mapping (SCSM)—Mappings to MMS (ISO 9506-1 and ISO 9506-2) and to ISO/IEC 8802-3; IEC 61850-8-1; IEC: Geneva, Switzerland, 2011.
- IEC Standard for Power Systems Management and Associated Information Exchange—Data and Communications Security, Part 4 Profiles Including MMS and Derivatives; IEC TS 62351-4; IEC: Geneva, Switzerland, 2018.
- Berge, C. Graphs and Hypergraphs; Elsevier: New York, NY, USA, 1973; pp. 389–391. [Google Scholar]
- Wang, Z.T.; Wang, Z.P. Elementary study of supernetworks. Chin. J. Manag. 2008, 5, 1–8. [Google Scholar]
- Estrada, E. Subgraph centrality and clustering in complex hyper-networks. Phys. A Stat. Mech. Appl. 2006, 364, 581–594. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Cai, Z.; Li, X.; He, R. Analytical modeling of traffic flow in the substation communication network. IEEE Trans. Power Deliv. 2015, 30, 2119–2127. [Google Scholar] [CrossRef]
- Ruiwen, H.E.; Dong, W.; Yanxu, Z.; Zexiang, C.; Xiaowang, H.E.; Yuhui, C. Modeling and static calculation method of the information flow on smart grid. Proc. CSEE 2016, 36, 1527–1535. [Google Scholar]
- Boudec, J.-Y.L.; Thiran, P. Network Calculus: A theory of Deterministic Queuing Systems for the Internet in Ser. Number 2050 in Lecture Notes in Computer Science; Springer: Berlin, Germany, 2001; pp. 7–20, 122–125. [Google Scholar]
- Cruz, R.L. A calculus for network delay. I. Network elements in isolation. IEEE Trans. Inf. Theory 1991, 37, 114–131. [Google Scholar] [CrossRef]
- Lv, L.; Zhou, T. Link Prediction; Higher Education Press: Beijing, China, 2013; pp. 156–213. [Google Scholar]
- Gou, J.; Liu, J.Y.; Liu, Y.B.; Xu, L.; Zhang, L.; Lei, C. Energy entropy measure based risk identification of power system cascading failures. Power Syst. Technol. 2013, 37, 2754–2761. [Google Scholar]
- Zimmerman, R.D.; Murillo-Sánchez, C.E.; Thomas, R.J.; Anderson, C.L. Free, Open-Source Electric Power System Simulation and Optimization Tools for MATLAB and Octave. Download MATPOWER. Available online: http://www.pserc.cornell.edu/matpower/#download (accessed on 16 March 2017).
- Li, Q.; Sun, H.; Sheng, T.; Zhang, B.; Wu, W.; Guo, Q. Injection attack analysis of transformer false data in substation state estimation. Autom. Electr. Power Syst. 2016, 40, 79–86. [Google Scholar]
- Lü, L.; Chen, D.; Ren, X.L.; Zhang, Q.M.; Zhang, Y.C.; Zhou, T. Vital nodes identification in complex networks. Phys. Rep. 2016, 650, 1–63. [Google Scholar] [CrossRef] [Green Version]
- Guo, C.; Yu, B.; Guo, J.; Wen, B.J.; Zhang, J.J. Security Risk Assessment of the IEC61850-based Substation Automation System. Proc. CSEE 2014, 34, 685–694. [Google Scholar]











| Stage No. | Stage Name | Common Tools |
|---|---|---|
| 1 | Reconnaissance | Websites Search engines Google Hacking WHOIS search/DNS queries Metadata Maltego |
| 2 | Scanning | Nmap Nessus OpenVAS |
| 3 | Accessing and escalating privilege | Password decoding/deciphering tool Metasploit CANVAS |
| 4 | Exfiltrating data | Physical exfiltrating Encryption and steganography Covert channels over general protocols Out of band (OOB) methods |
| 5 | Assaulting | Tampering of software or OS settings Attacking hardware Changing settings |
| 6 | Sustaining access | Adding authorized accounts Backdoor program Adding monitor service |
| 7 | Concealing traces | Hiding physical location Modifying logs Modifying files |
| Attack Action | Type | Potential Target | Target Position in Figure 3 | Target Mapped to Logical Structure |
|---|---|---|---|---|
| Accessing | Inside the SAS | Cyber network of SAS | A1 | ALL the LNs |
| Devices in bay level | A2 | LNs in bay level | ||
| User interface | A3 | IHMI | ||
| Outside the SAS | Wide-area network | A4 | N/A | |
| Control center network | A5 | N/A | ||
| Adjacent SAS | A6 | N/A | ||
| Corporation office network | A7 | N/A | ||
| Assaulting | Device in cyber network | Firewall | C1–C5 | All the LNs |
| Remote access | C6 | N/A | ||
| Time synchronization | C7 | RSYN | ||
| Device in physical network | Devices in process level | C8,C9 | LNs in process level | |
| Server in control center | C10 | N/A | ||
| User interface in control center | C11 | N/A |
| Bay | Num. | Function | Detailed Structure |
|---|---|---|---|
| E01 | F1 | Measurement and metering |  |
| F2 | Distance protection |  | |
| F3 | Differential protection |  | |
| F4 | Interlocking |  | |
| E03 | F5 | Measurement and metering | The same as F1 |
| F6 | Distance protection | The same as F2 | |
| F7 | Differential protection | The same as F3 | |
| F8 | Interlocking | The same as F4 | |
| E02 | F9 | Distance protection | The same as F2 |
| F10 | Voltage regular |  | |
| D01 | F11 | Transformer differential protection |  |
| F12 | Overcurrent and over-voltage protection |  |
| Level Name | Logical Node | Full Name |
|---|---|---|
| Station level | IHMI | Human machine interface |
| IARC | Archiving | |
| ITMI | Telemonitoring interface | |
| ITCI | Telecontrol interface | |
| Bay/unit level | MMXU | Measurand unit/Op. |
| MMTR | Metering/acquisition and calculation | |
| PDIS | Line protection scheme | |
| PSCH | Line protection scheme | |
| PTRC | Protection trip conditioning | |
| PDIF | Differential protection | |
| RSYN | Synchrocheck | |
| CSWI | Switch controller | |
| CILO | Interlocking bay/station | |
| ATCC | Automatic tap changer control | |
| PTDF | Differential transformer protection | |
| PTOV | (Time) Overvoltage protection | |
| PIOC | Instantaneous overcurrent or rate of rise protection | |
| Process level | TVTR | Voltage transformer |
| TCTR | Current transformer | |
| XCBR | Circuit breaker | |
| RMXU | Differential measurements | |
| XSWI | Disconnector | |
| YLTC | Tap Changer |
| Ultimate Target | Level Name | Cybersecurity Event | ||
|---|---|---|---|---|
| IHMI | Station level | C11-A5-C4-A4-C2-A3 | 0.3932 | 0.2686 |
| PDIS | Bay level | A6-C5-C2-A1-A2 | 0.3703 | 0.2256 |
| XCBR | Process level | A3-A1-C9 | 0.2931 | 0.1232 |
| Ultimate Target | Intruder No. | Substation No. | Cybersecurity Event 1 | ||
|---|---|---|---|---|---|
| TCTR | Intruder 1 | S/S 5 | A3-A1-C8 | 0.2931 | 0.1232 |
| TVTR and TCTR | Intruder 2 | S/S 1 | C6-C1-A1-C8 | 0.3381 | 0.1758 |
| TVTR and TCTR | Intruder 5 | S/S 3 | A6-C5-C2-A1-C8 | 0.3703 | 0.2256 |
| TVTR and TCTR | Intruder 3 | S/S 9 | A7-C3-A4-C2-A1-C8 | 0.3932 | 0.2686 |
| Ultimate Target | Intruder No. | Level Name | Cybersecurity Event 2 | ||
|---|---|---|---|---|---|
| IHMI | Intruder 4 | Station | C11-A5-C4-A4-C2-A3 | 0.1966 | 0.1343 |
| MMXU | Intruder 5 | Bay | A6-C5-C2-A1-A2 | 0.1044 | 0.0636 |
| TVTR and TCTR | Intruder 3 | Process | A7-C3-A4-C2-A1-C8 | 0.3932 | 0.2686 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, Y.; Li, J.; Zhang, D.; Pi, J.; Song, J.; Zhao, G. Supporting Sustainable Maintenance of Substations under Cyber-Threats: An Evaluation Method of Cybersecurity Risk for Power CPS. Sustainability 2019, 11, 982. https://doi.org/10.3390/su11040982
Fan Y, Li J, Zhang D, Pi J, Song J, Zhao G. Supporting Sustainable Maintenance of Substations under Cyber-Threats: An Evaluation Method of Cybersecurity Risk for Power CPS. Sustainability. 2019; 11(4):982. https://doi.org/10.3390/su11040982
Chicago/Turabian StyleFan, Youping, Jingjiao Li, Dai Zhang, Jie Pi, Jiahan Song, and Guo Zhao. 2019. "Supporting Sustainable Maintenance of Substations under Cyber-Threats: An Evaluation Method of Cybersecurity Risk for Power CPS" Sustainability 11, no. 4: 982. https://doi.org/10.3390/su11040982





