The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth
Abstract
:1. Introduction
2. Information Leakage Incidents and Evaluation of Security Level
2.1. Information Leakage Incidents
2.2. Evaluation of Security Level
3. Development of a Security Evaluation Model for Information Leakage Protection
4. Validation of the Security Evaluation Model for Information Leakage Protection
4.1. Statistical Validation of the Security Evaluation Model for Information Protection
4.2. Proposal of an Objective Measurement for the Electronic Security System
4.3. The Results of Feasibility Test in Objective Measurement for the Electronic Security System
5. Results and Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Appendix A
| ID | Controls | [18] | [19] | [20] | [21] | [22] | [23] | [24] | [25] | [26] | [27] | [28] | [29] | [30] | [31] | [32] | [33] | [34] | [35] | [36] | [37] | [38] | [39] | [40] |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| A | Regulatory requirements of the industry | ● | ● | ● | ● | |||||||||||||||||||
| B | Degree of participation of management in security education | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||||||||||
| C | Degree of support for security organization by management | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||
| D | Practical security activities for security personnel | ● | ● | |||||||||||||||||||||
| E | (Considering security of the general staff) Degree of discomfort (security acceptability) | ● | ● | |||||||||||||||||||||
| F | Allocation of work to security personnel (installation of security department) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||||||||||
| G | General employee security management (security pledge and security training) | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||||||||
| H | Amount of investment in technology protection (security manpower + security education + security consulting + introduction and operation of the security system) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||||||||||
| I | Research asset security management (e.g., researcher security pledge and research content security management) | ● | ● | ● | ● | |||||||||||||||||||
| J | Joint (trust) research security management (e.g., consignor of the security contract and security activity check) | ● | ● | ● | ● | |||||||||||||||||||
| K | Identification and evaluation of the importance of the research results | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||||||||||||
| L | Research results (performance management) | ● | ● | ● | ||||||||||||||||||||
| M | Improvement of the research environment for researchers (e.g., regularization of researchers and operation of compensation for job incentives) | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||||||||
| N | Security zone (equipment) setup and management | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||||
| O | Security system introduction and utilization (access control + intrusion alarm + image detection) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||||||||||
| P | Security level of personal computer | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ||||
| Q | Server security (e.g., user authentication, management of (shared folder) access rights, and updating versions) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||||
| R | Database security (e.g., user authentication, version updating, security system introduction, and operation (access control + encryption)) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||
| S | Computer network security (e.g., user authentication, management of access rights, and security system introduction and operation (network access control (NAC)) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||||||
| T | Supply chain security (service security) guidelines and implementation | ● | ● | ● | ● | ● | ● | ● | ||||||||||||||||
| U | Guidance and implementation of production process security (prevention of work interruption and information leakage) | ● | ● | ● | ● | |||||||||||||||||||
| V | Degree of internal security audit activity | ● | ● | ● | ● | |||||||||||||||||||
| W | Efforts to improve the security system through analysis of cases of excellent external security | ● | ● | |||||||||||||||||||||
| X | Acquisition of objectified security certification by a third party (e.g., ISO 27001 certification and Korea-Information Security Management System (KISMS) certification) | ● | ||||||||||||||||||||||
| Y | System failure response activities (e.g., business continuity planning, system redundancy, and backup) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● | |||||||||||
| Z | Measures to cope with technology leakage incidents (e.g., incident response plan, measures to prevent recurrence of accidents, and analysis of the causes of an accident) | ● | ● | ● | ● | ● | ● | ● | ● | ● | ● |
| Controls | Sub-Controls | Result | |
|---|---|---|---|
| Personal Computer | Operating system (OS) | Check on user password setting (Encryption set-up + change period) | ○ |
| Check on complexity of user authentication method (Electronic signature + biometric) | ○ | ||
| Check on updated version of Operating System (OS) (Check on updated security patch) | ○ | ||
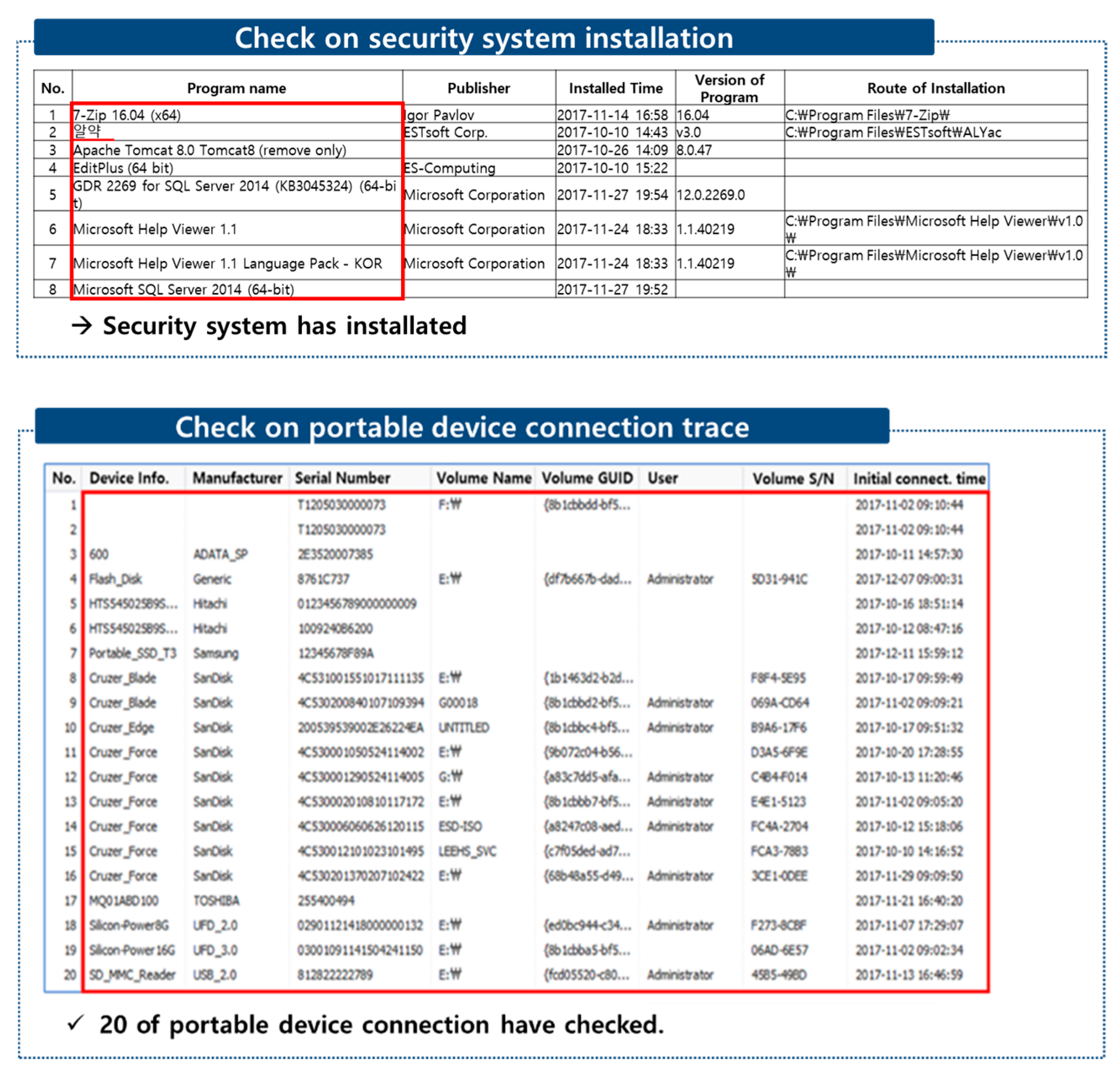
| Check on security system installation | ○ | ||
| Check on security system uninstallation trace | ○ | ||
| E-mail (P2P messenger) only use own e-mail program | Check on usage trace of mail on business (Sent offsite) | Ⅹ | |
| Check on updated version of application program | Ⅹ | ||
| Check on security system installation | - | ||
| Check on security system user authentication (Delete·Change on account + password change period) | - | ||
| Check on security system uninstallation trace | |||
| Portable storage device | Check on portable device connection trace | Ⅹ | |
| Check on fixed storage device (hard disk driver, compact disk) | ○ | ||
| Check on updated version of application program (Driver) | - | ||
| Check on security system installation | ○ | ||
| Check on security system uninstallation trace | ○ | ||
References
- Wong, W.P.; Tan, H.C.; Tan, K.H.; Tseng, M.L. Human factors in information leakage: Mitigation strategies for information sharing integrity. Ind. Manag. Data Syst. 2019, 119, 1242–1267. [Google Scholar] [CrossRef]
- Crowd Research Partners. Insider Threat 2018 Report; Haystax: Kansas, MO, USA, 2018. [Google Scholar]
- Gontar, A.A.; Lomakin, N.I.; Gorbacheva, A.S.; Chekrygina, T.A.; Tokareva, E.V. Methods of data intellectual analysis in assessment of economic security level. In Ubiquitous Computing and the Internet of Things: Prerequisites for the Development of ICT; Springer: Cham, Switzerland, 2019; pp. 455–464. [Google Scholar]
- Security and Privacy Controls for Federal Information Systems and Organizations; NIST Special Publication 800-53 Revision 4; Joint Task Force Transformation Intiative; National Institute of Standards and Technology: Boulder, CO, USA, 2014.
- Liggett, R.L. The Effects of Information Security on Business Continuity: Case Study. Ph.D. Thesis, University of Phoenix, Phoenix, AZ, USA, 2020. [Google Scholar]
- Council of the European Union. General Data Protection Regulation; Council of the European Union: Brussels, Belgium, 2016.
- Na, O.; Park, L.W.; Yu, H.; Kim, Y.; Chang, H. The rating model of corporate information for economic security activities. Secur. J. 2019, 32, 435–456. [Google Scholar] [CrossRef] [Green Version]
- Yassin, W.M.; Ahmad, R.; Mohammad, N.A.N. An Insider Threat Factors and Features Categorization for Manufacturing Execution System. In Advances in Electronics Engineering; Springer: Singapore, 2020; pp. 329–337. [Google Scholar]
- Azaria, A.; Richardson, A.; Kraus, S.; Subrahmanian, V.S. Behavioral analysis of insider threat: A survey and bootstrapped prediction in imbalanced data. IEEE Trans. Comput. Soc. Syst. 2014, 1, 135–155. [Google Scholar] [CrossRef]
- Suman, R.; Far, B.; Mohammed, E.A.; Nair, A.; Janbakhsh, S. Visualization of Server Log Data for Detecting Abnormal Behaviour. In Proceedings of the 2018 IEEE International Conference on Information Reuse and Integration (IRI), Salt Lake City, UT, USA, 7–9 July 2018; pp. 244–247. [Google Scholar]
- Parrot, A.; Bechhofer, L. Acquaintance Rape: The hidden Crime (No. 157); Wiley: New York, NY, USA, 1991. [Google Scholar]
- EKRAN. Insider Threat Statistics for 2020: Facts and Figures; EKRAN: Newport Beach, CA, USA, 2019. [Google Scholar]
- Moon, S.J. A Study on Security Level Assessment Methodology Development for Internal Information Leakiness Control: Centering on National & Public Agency. Master’s Thesis, Department of Business Administration Graduate School of Business Administration, Chosun University, Gwangju, Korea, 2008. [Google Scholar]
- Drtil, J. Impact of information security incidents—Theory and reality. J. Syst. Integr. 2013, 4, 44–52. [Google Scholar]
- Bland, J.M.; Altman, D.G. Statistics notes: Cronbach’s alpha. BMJ 1997, 314, 572. [Google Scholar] [CrossRef] [Green Version]
- Corbett, R.J.T.; Laptook, A.R.; Nunnally, R.L.; Hassan, A.; Jackson, J. Intracellular pH, lactate, and energy metabolism in neonatal brain during partial ischemia measured in vivo by 31P and 1H nuclear magnetic resonance spectroscopy. J. Neurochem. 1988, 51, 1501–1509. [Google Scholar] [CrossRef]
- Kim, J.S.; Eun, C.; Jeong, I.Y. Automatic user analysis using artifact of Windows environment. In Proceedings of the Symposium of the Korean Institute of communications and Information Sciences, Jeju Island, Korea, 21–23 June 2017; pp. 1437–1438. [Google Scholar]
- Han, D.-S. Proposal of information security management system specialized in industrial security. Korea Ind. Saf. Res. 2016, 6, 143–172. [Google Scholar]
- Ministry of Trade, Industry and Energy; Korea Industrial Technology Protection Association. Industrial Technology Protection Guidelines and Manuals; Ministry of Trade, Industry and Energy: Seoul, Korea, 2017.
- Chang, H.-B. Design of information security management system for prevention of industrial technology leakage in small and medium business. J. Korea Multimed. Soc. 2010, 13, 111–121. [Google Scholar]
- Bae, S.; Kim, J.H. A study on the development of security level evaluation model for national R & D project research. J. Korea Comput. Assoc. 2013, 16, 73–80. [Google Scholar]
- Choi, M.-G.; Lee, D.H.; Hwang, W.J. Design of security protocol for collaborative workflow management system. J. Korea Acad. Ind. Coop. Soc. 2008, 9, 1271–1278. [Google Scholar]
- Korea Federation of SMEs. 2016 SME Technical Statistics Survey Report; Korea Federation of SMEs: Seoul, Korea, 2016. [Google Scholar]
- Korea Federation of SMEs; Large and Small Enterprises Cooperation Foundation. 2016 Survey of Technical Protection Level of SMEs; Korea Federation of SMEs: Seoul, Korea, 2017. [Google Scholar]
- Mbowe, J.E.; Zlotnikova, I.; Msanjila, S.S.; Oreku, G.S. A conceptual framework for threat assessment based on organization’s information security policy. J. Inform. Secur. 2013, 5, 166–177. [Google Scholar] [CrossRef] [Green Version]
- Shamala, P.; Ahmad, R.; Yusoff, M. A conceptual framework of info structure for information security risk assessment (ISRA). J. Inf. Secur. Appl. 2013, 18, 45–52. [Google Scholar] [CrossRef] [Green Version]
- Laura, S. Cyber Security Assessment Tool. Nuclear Plant. J. 2016, 34, 43–45. [Google Scholar]
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar] [CrossRef] [Green Version]
- Kim, I.-H.; Lee, K.H. Evaluation model of contractor security management using DEA model. J. Korea Inst. Inf. Secur. 2017, 27, 687–704. [Google Scholar]
- Noh, S.Y.; Lim, J.I. A study on corporate security management system. J. Korea Inst. Inf. Secur. 2017, 27, 617–636. [Google Scholar]
- Lee, H.M.; Lim, J.I. A study on the development of measuring model for information security level of enterprises. J. Korea Inst. Inf. Secur. 2008, 18, 161–170. [Google Scholar]
- Park, S.H.; Kim, S.R.; Park, G.W.; Kim, S.J.; Byun, S.H.; Lim, H.S.; Lee, S.W. Information security level diagnostic tool development model proposal: At the introduction stage of information security products and services. In Proceedings of the Korea Information Science Society, Jeju Island, Korea, 18–20 June 2017; pp. 1119–1121. [Google Scholar]
- Shin, J.-I. Development of information system maturity model evaluation tool. J. Korea Multimed. Soc. 2010, 13, 520–523. [Google Scholar]
- Oh, E. Improvement of the authentication model to improve the efficiency of information security management in financial institutions. J. Korea Inst. Inf. Secur. 2016, 26, 541–550. [Google Scholar]
- Park, G.; Yeom, H.Y. A Study on the improvement of information protection level of electronic financial infrastructure: Through the analysis of information security management level. J. Korea Inst. Inf. Secur. 2016, 26, 1605–1618. [Google Scholar]
- Kotenko, I.; Chechulin, A. Fast network attack modeling and security evaluation based on attack graphs. J. Cyber Secur. 2014, 3, 27–46. [Google Scholar] [CrossRef] [Green Version]
- Stouffer, K.; Falco, J.; Scarfone, K. Special Publication 800-82 Revision 1, Guide to Industrial Control. Systems (ICS) Security; National Institute of Standards and Technology: Gaithersberg, MD, USA, 2015.
- US Department of Energy; Applied Communication Sciences; DTE Energy; Electric Power Research Institute; University of Illinois at Urbana-Champaign. Tools & Methods for Hardening Communication Security of Energy Delivery Systems: Final Report; Applied Communication Sciences; US Department of Energy: Basking Ridge, NJ, USA, 2014.
- Galloway, B.; Hancke, G.P. Introduction to industrial control networks. IEEE Commun. Surv. Tutor. 2013, 15, 860–880. [Google Scholar] [CrossRef] [Green Version]
- Soh, W.Y.; Kim, W.K.; Kim, S.S. Development of security level evaluation tool (ISSPET) based on information protection system. J. Korea Acad. Ind. Coop. Soc. 2009, 10, 1911–1919. [Google Scholar]





| Attacks from Outside | Attacks from Inside | |
|---|---|---|
| Recognizing the occurrence of a security incident | Easy (Network access log or system firewall) | Difficult (Difficulty identifying insider information leakage) |
| Security incident occurrences | More (Security incident from unspecified individuals) | Fewer (Security incident from insider, a specific person) |
| The scale of the security incident | Small (Access to system but hard to find and information leaked) | Large (Loss of market share, possibility of declining stock price, and/or eventual bankruptcy) |
| Recovery time | Short (Confirmation of the access point) | Long (Difficult to find leakage range) |
| ID | Controls | Degree of Validity |
|---|---|---|
| A | Regulatory requirements of the industry | 4.69 |
| B | Degree of participation of management in security education | 4.23 |
| C | Degree of support for security organization by management | 4.25 |
| D | Practical security activities for security personnel | 4.31 |
| E | (Considering security of the general staff) Degree of discomfort (security acceptability) | 4.13 |
| F | Allocation of work to security personnel (installation of security department) | 4.54 |
| G | General employee security management (security pledge and security training) | 4.48 |
| H | Amount of investment in technology protection (security manpower + security education + security consulting + introduction and operation of the security system) | 4.49 |
| I | Research asset security management (e.g., researcher security pledge and research content security management) | 4.52 |
| J | Joint (trust) research security management (e.g., consignor of the security contract and security activity check) | 4.41 |
| K | Identification and evaluation of the importance of the research results | 4.32 |
| L | Research results (performance management) | 4.41 |
| M | Improvement of the research environment for researchers (e.g., regularization of researchers and operation of compensation for job incentives) | 4.45 |
| N | Security zone (equipment) setup and management | 4.45 |
| O | Security system introduction and utilization (access control + intrusion alarm + image detection) | 4.41 |
| P | Security level of personal computer | 4.61 |
| Q | Server security (e.g., user authentication, management of (shared folder) access rights and updating versions) | 4.62 |
| R | Database security (e.g., user authentication, version updating, security system introduction, and operation (access control + encryption)) | 4.63 |
| S | Computer network security (e.g., user authentication, management of access rights, and security system introduction and operation (network access control (NAC)) | 4.58 |
| T | Supply chain security (service security) guidelines and implementation | 4.32 |
| U | Guidance and implementation of production process security (prevention of work interruption and information leakage) | 4.23 |
| V | Degree of internal security audit activity | 4.24 |
| W | Efforts to improve the security system through analysis of cases of excellent external security | 4.10 |
| X | Acquisition of objectified security certification by a third party (e.g., ISO 27001 certification, Korea-Information Security Management System (KISMS) certification) | 4.13 |
| Y | System failure response activities (e.g., business continuity planning, system redundancy, and backup) | 4.42 |
| Z | Measures to cope with technology leakage incidents (e.g., incident response plan, measures to prevent recurrence of accidents, and analysis of the causes of an accident) | 4.45 |
| Controls | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | Factors | Cronbach’s | |
|---|---|---|---|---|---|---|---|---|---|---|---|
| K | 0.882 | 0.095 | −0.009 | −0.029 | 0.043 | −0.049 | 0.020 | 0.047 | Classification of developed technology | 0.892 | 0.912 |
| L | 0.872 | 0.033 | 0.007 | 0.024 | −0.015 | 0.223 | −0.032 | 0.147 | 0.890 | ||
| I | 0.810 | 0.300 | 0.158 | 0.063 | 0.069 | 0.169 | 0.071 | −0.043 | 0.893 | ||
| J | 0.799 | 0.131 | 0.019 | 0.144 | 0.008 | 0.311 | 0.022 | 0.136 | 0.880 | ||
| M | 0.794 | 0.125 | −0.073 | −0.091 | −0.097 | −0.043 | 0.084 | 0.224 | 0.906 | ||
| B | 0.204 | 0.908 | 0.130 | 0.077 | 0.146 | −0.016 | 0.034 | −0.036 | Security culture | 0.909 | 0.939 |
| C | 0.172 | 0.898 | 0.043 | 0.039 | 0.221 | 0.098 | −0.005 | 0.042 | 0.908 | ||
| E | 0.003 | 0.882 | 0.142 | 0.050 | −0.013 | 0.131 | −0.002 | 0.044 | 0.922 | ||
| D | 0.264 | 0.843 | 0.047 | 0.143 | 0.190 | 0.138 | 0.006 | 0.035 | 0.942 | ||
| Q | −0.050 | 0.087 | 0.918 | 0.190 | 0.026 | 0.003 | −0.021 | −0.018 | Electronic security system | 0.839 | 0.80 |
| R | 0.049 | 0.091 | 0.865 | 0.147 | −0.017 | 0.092 | 0.031 | −0.061 | 0.799 | ||
| P | 0.045 | 0.222 | 0.840 | 0.141 | 0.053 | −0.049 | −0.020 | −0.153 | 0.831 | ||
| S | 0.023 | −0.045 | 0.720 | −0.026 | 0.162 | 0.271 | 0.227 | 0.096 | 0.904 | ||
| W | −0.032 | 0.076 | 0.163 | 0.931 | 0.098 | 0.016 | 0.018 | −0.016 | Measuring and improving security level | 0.927 | 0.950 |
| X | 0.028 | 0.022 | 0.170 | 0.924 | 0.092 | 0.064 | 0.023 | 0.116 | 0.933 | ||
| V | 0.077 | 0.142 | 0.089 | 0.924 | −0.092 | 0.116 | 0.120 | 0.058 | 0.920 | ||
| F | 0.015 | 0.121 | 0.022 | −0.047 | 0.908 | 0.018 | 0.033 | 0.024 | Security organization and investment | 0.802 | 0.877 |
| G | 0.052 | 0.125 | 0.027 | 0.105 | 0.898 | 0.099 | −0.025 | 0.065 | 0.794 | ||
| H | −0.078 | 0.187 | 0.129 | 0.008 | 0.807 | 0.016 | −0.034 | 0.198 | 0.876 | ||
| T | 0.276 | 0.113 | 0.058 | 0.016 | 0.134 | 0.848 | 0.252 | 0.059 | Managerial security system | 0.930 | |
| U | 0.264 | 0.178 | 0.170 | 0.079 | 0.119 | 0.809 | 0.226 | 0.024 | |||
| A | −0.021 | 0.116 | 0.083 | 0.470 | −0.127 | 0.574 | −0.146 | −0.004 | - | - | |
| O | 0.064 | 0.022 | 0.025 | 0.053 | −0.017 | 0.073 | 0.950 | −0.020 | Physical security system | 0.917 | |
| N | 0.035 | −0.002 | 0.111 | 0.051 | −0.014 | 0.191 | 0.925 | 0.059 | |||
| Z | 0.211 | −0.005 | −0.065 | 0.060 | 0.133 | 0.005 | −0.002 | 0.939 | Incident response | 0.947 | |
| Y | 0.203 | 0.069 | −0.072 | 0.088 | 0.143 | 0.067 | 0.043 | 0.921 | |||
| Type | Hive File Path | |
|---|---|---|
| Operating System | Check on user password setting (Encryption set-up + change period) | |
| HKLM/SAM | ||
| Check on complexity of user authentication method (Electronic signature + biometric) | ||
| HKCU\SOFTWARE\Classes\LocalSettings\Software\Microsoft\Windows\Shell\MuiCache | ||
| Check on updated version of Operating System (Check on updated security patch) | ||
| HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Trace | ||
| Check on security system installation | ||
| HKCU\SOFTWARE\Classes\LocalSettings\Software\Microsoft\Windows\Shell\MuiCache | ||
| Check on security system uninstallation trace | ||
| HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall | ||
| Portable storage device | Check on portable device connection trace | |
| SYSTEM\ControlSet00x\Enum\USBSTOR | ||
| Check on fixed storage device (hard disk driver, compact disk) | ||
| SYSTEM\ControlSet00x\Enum\USBSTOR | ||
| Check on updated version of application program (Driver) | ||
| SYSTEM\ControlSet001\Enum\ROOT\XKmdfDriver\0000 | ||
| Check on security system installation | ||
| HKCU\SOFTWARE\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache | ||
| Check on security system uninstallation trace | ||
| HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall | ||
| Type | Controls | Requirement for Evaluation Model Focused on Insider Threats | |
|---|---|---|---|
| Security change management | Measuring and improving security level | Degree of internal security audit activity | Business continuity plan |
| Acquisition of objectified security certification by a third party (e.g., ISO 27001 certification and Korea-Information Security Management System certification) | |||
| Efforts to improve security system through analysis of cases of excellent external security | |||
| Incident response | System failure response activities (e.g., business continuity planning, system redundancy, and backup) | ||
| Measures to cope with technology leakage incidents (e.g., incident response plan, measures to prevent recurrence of accidents, and analysis the causes of an accident) | |||
| Security operation management | Physical security system | Security zone (equipment) setup and management | - |
| Security system introduction and utilization (access control + intrusion alarm + image detection) | |||
| Electronic security system | Security level of personal computer | Digital evidence (proposed objective measuring for the electronic technology security system) | |
| Server security (e.g., user authentication, management of (shared folder) access rights, updating versions) | |||
| Database security (e.g., user authentication, updating versions, security system introduction, and operation (access control + encryption)) | |||
| Computer network security (e.g., user authentication, management of access rights, security system introduction and operation, and network access control (NAC)) | |||
| Managerial security system | Supply chain security (service security) guidelines and implementation | - | |
| Guidance and implementation of production process security (prevention of work interruption and information leakage) | |||
| Classification of developed technology | Research asset security management (researcher security pledge and research content security management) | Information classification | |
| Joint (trust) research security management (e.g., consignor of the security contract and security activity check) | |||
| Identification and evaluation of the importance of research results | |||
| Research results (performance management) | |||
| Improvement of the research environment for researchers (e.g., regularization of researchers and operation of compensation for job incentives) | |||
| Security support environment | Security organization and investment | Allocation of work to security personnel (installation of security department) | - |
| General employee security management (security pledge and security training) | |||
| Amount of investment in technology protection (security manpower + security education + security consulting + introduction and operation of the security system) | |||
| Security culture | Internal/External security culture | Degree of participation of management education in security education | Security culture |
| Degree of support for security organization by management | |||
| Practical security activities for security personnel | |||
| (Considering security of the general staff) Degree of discomfort (security acceptability) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Lee, C.; Chang, H. The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth. Sustainability 2020, 12, 10639. https://doi.org/10.3390/su122410639
Kim J, Lee C, Chang H. The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth. Sustainability. 2020; 12(24):10639. https://doi.org/10.3390/su122410639
Chicago/Turabian StyleKim, Jawon, Chanwoo Lee, and Hangbae Chang. 2020. "The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth" Sustainability 12, no. 24: 10639. https://doi.org/10.3390/su122410639
APA StyleKim, J., Lee, C., & Chang, H. (2020). The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth. Sustainability, 12(24), 10639. https://doi.org/10.3390/su122410639





