Assessing the Vulnerability of Logistics Service Supply Chain Based on Complex Network
Abstract
1. Introduction
2. Literature Review
2.1. Service Supply Chain
2.2. Complex Network
3. Research Methods and Indicators Construction
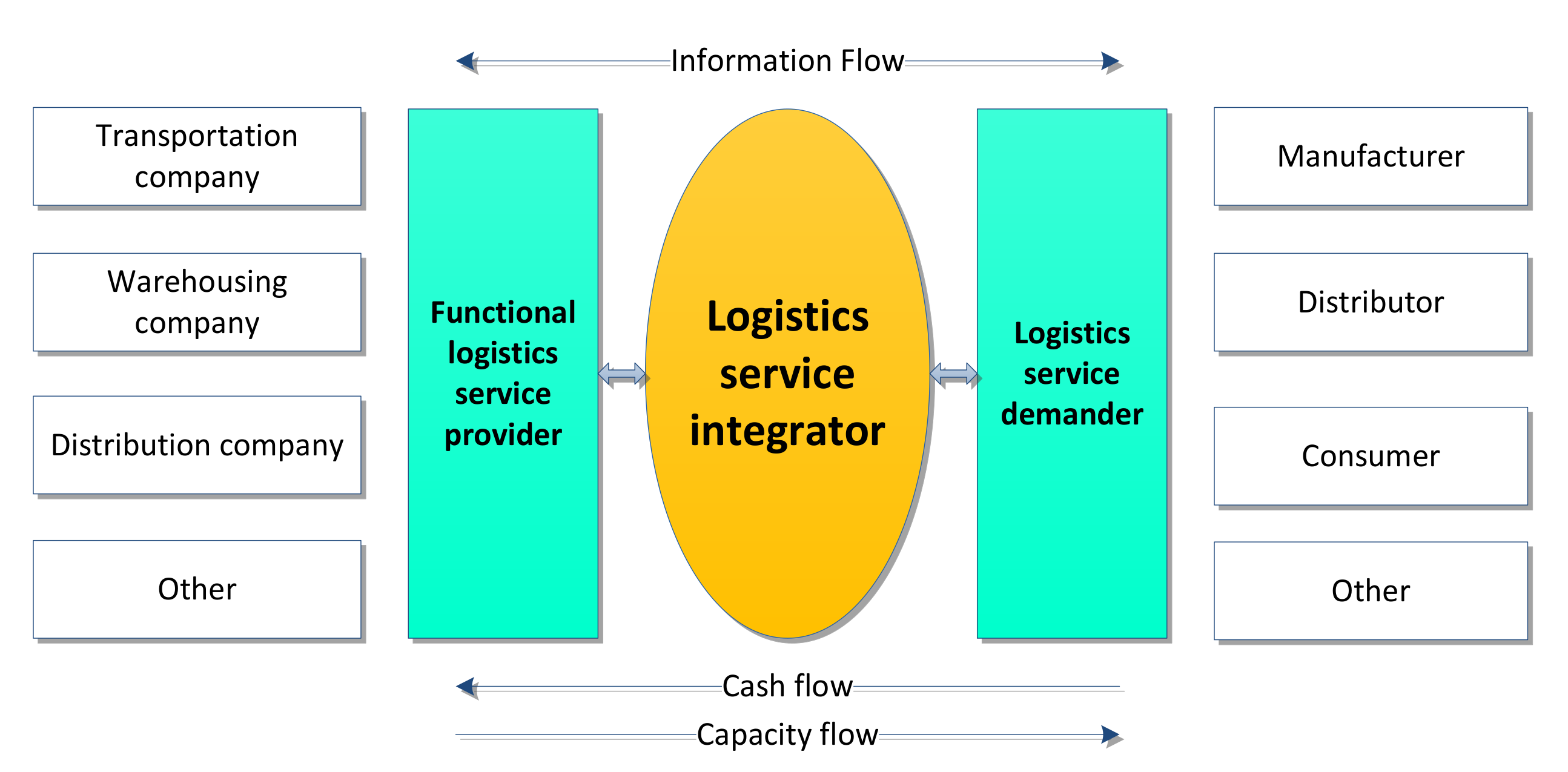
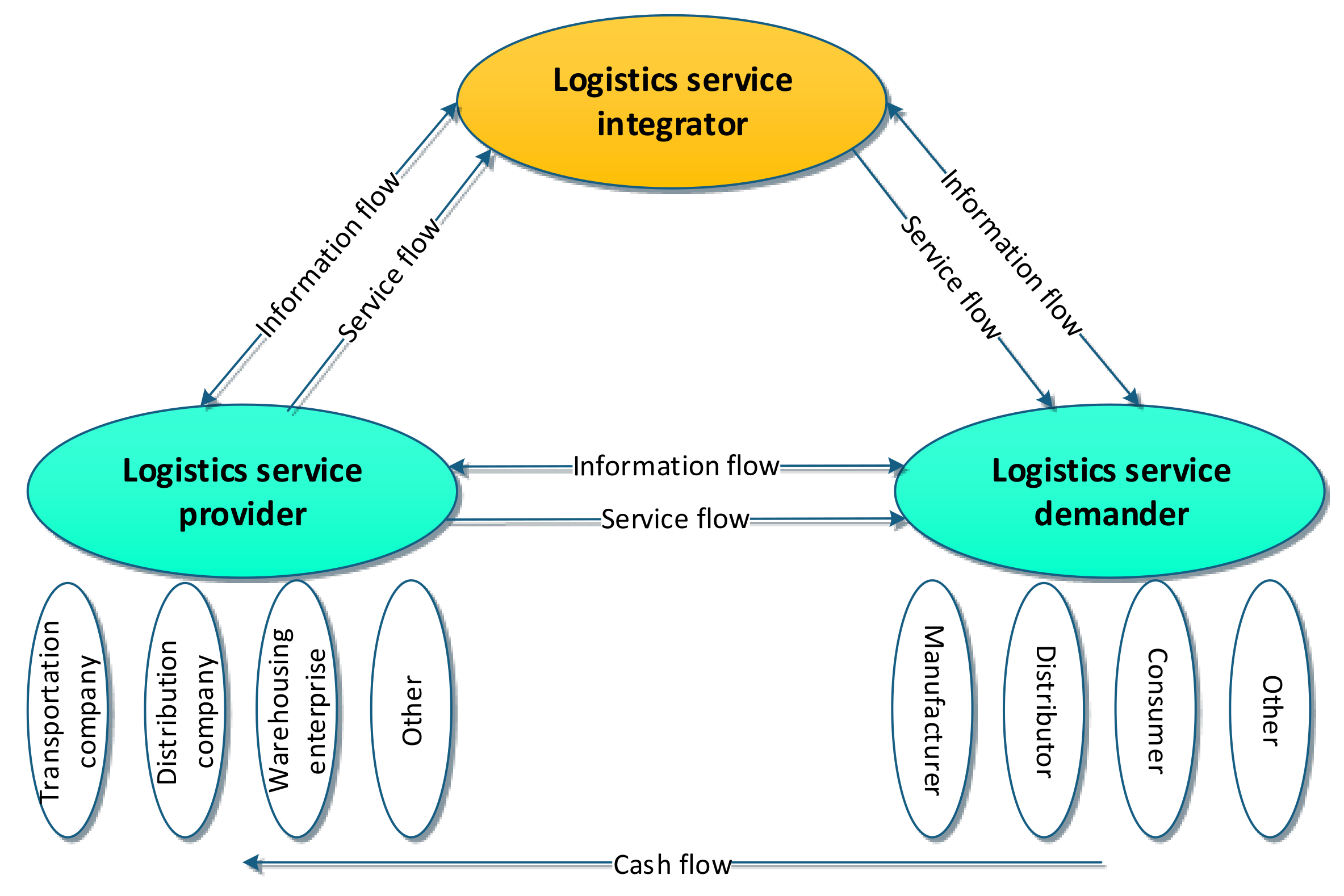
3.1. LSSC Structure Description
3.2. Explanation of the New LSSC Structure
3.3. LSSC Evolution Process
3.4. LSSC Network Model Construction
3.5. LSSC Vulnerability Measurement Indicators and Attack Strategies
4. Results Analysis and Discussion
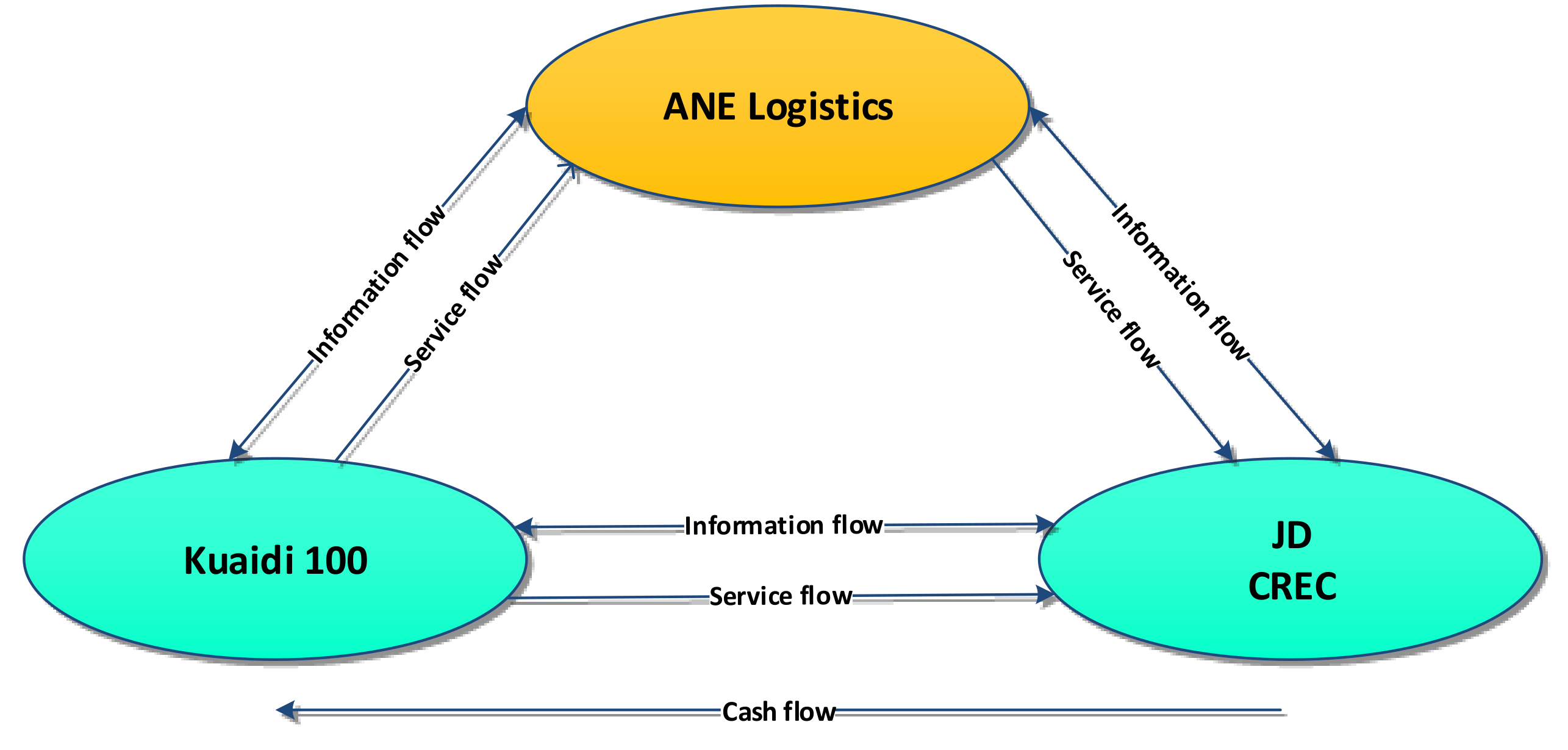
4.1. Case Description
- (1)
- Each integrator enters the network and randomly establishes connections with eight customers.
- (2)
- Each logistics service provider enters the network and randomly establishes connections with two logistics service integrators and six customers.
4.2. Result Analysis
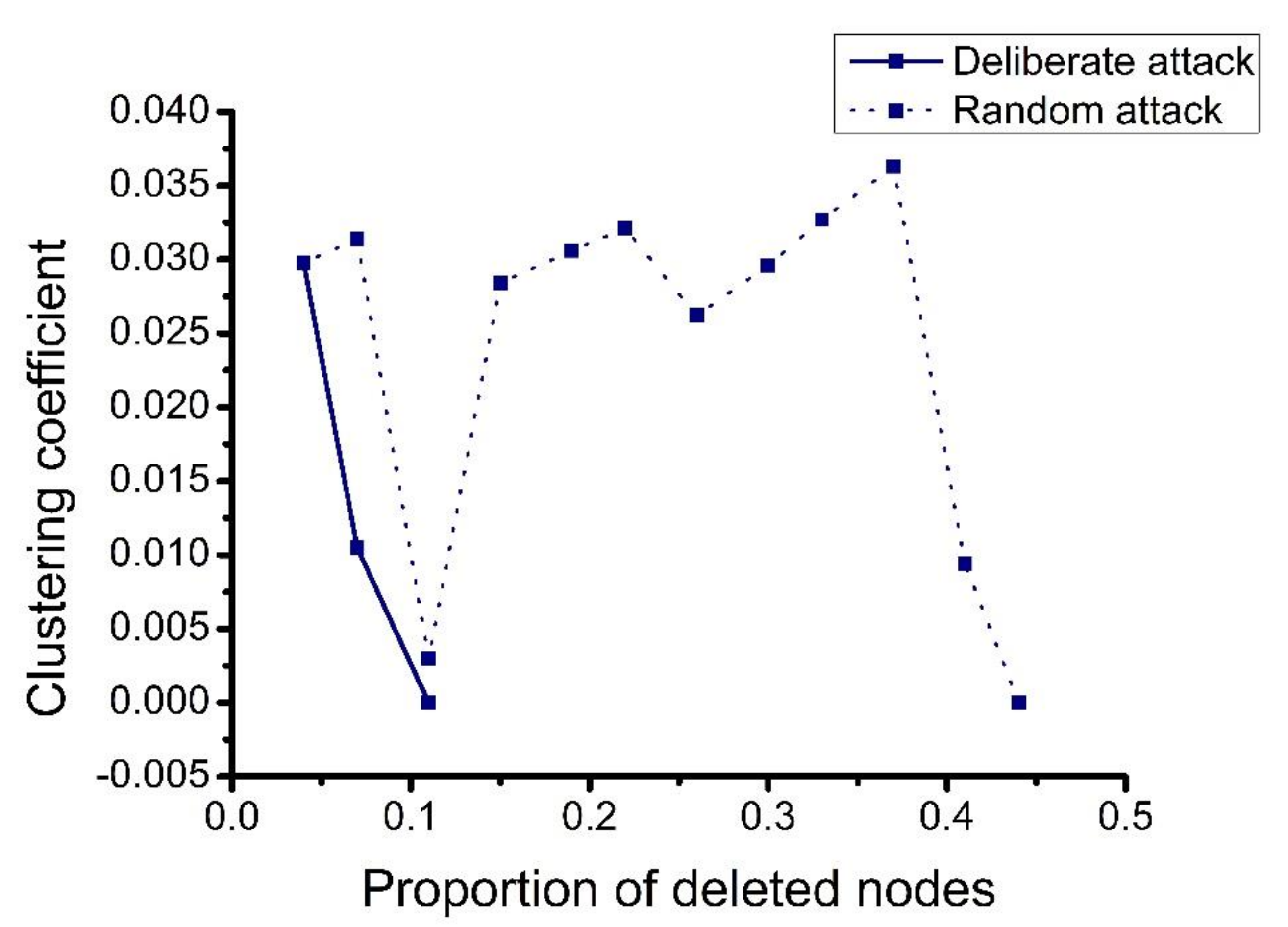
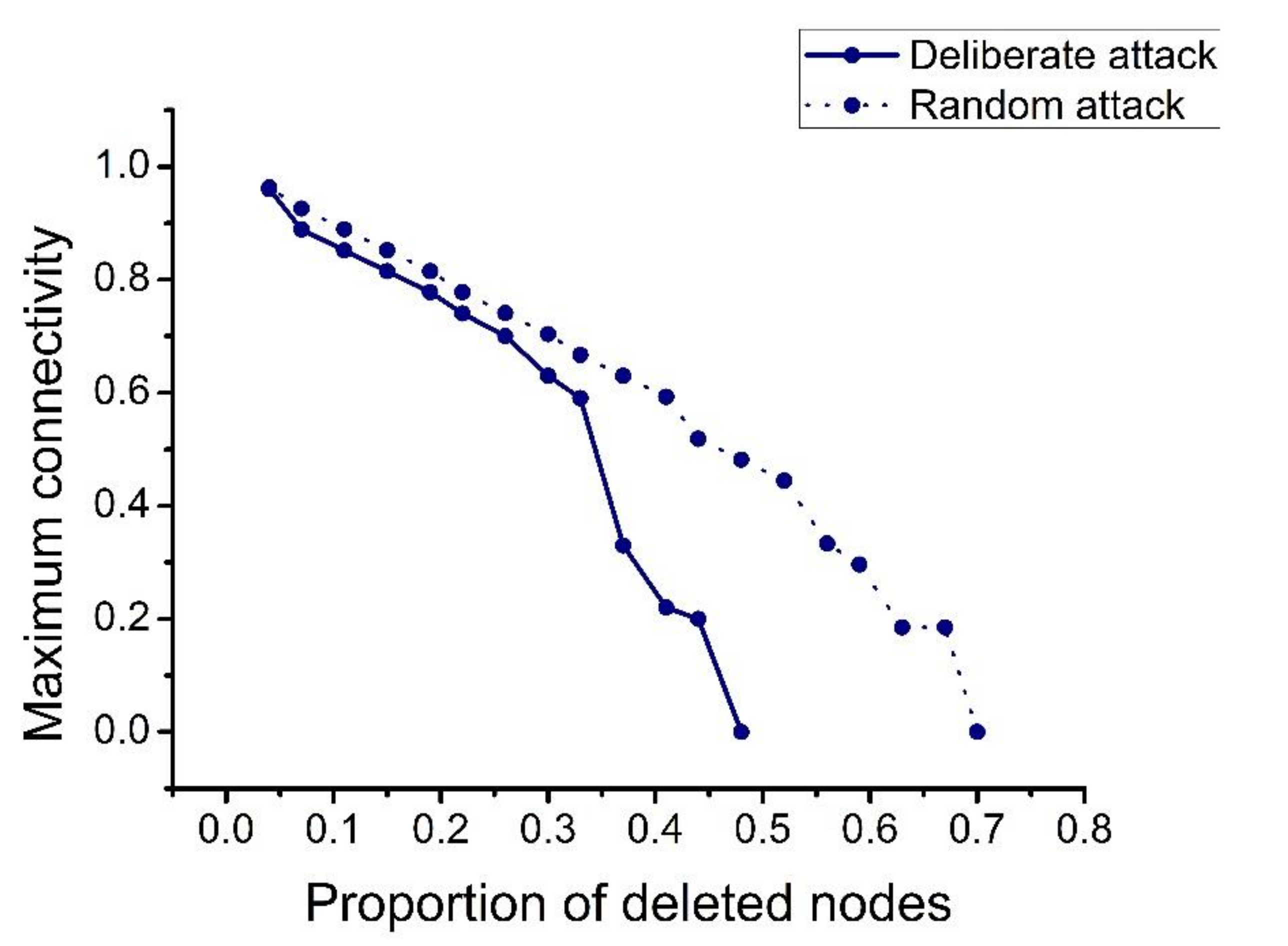
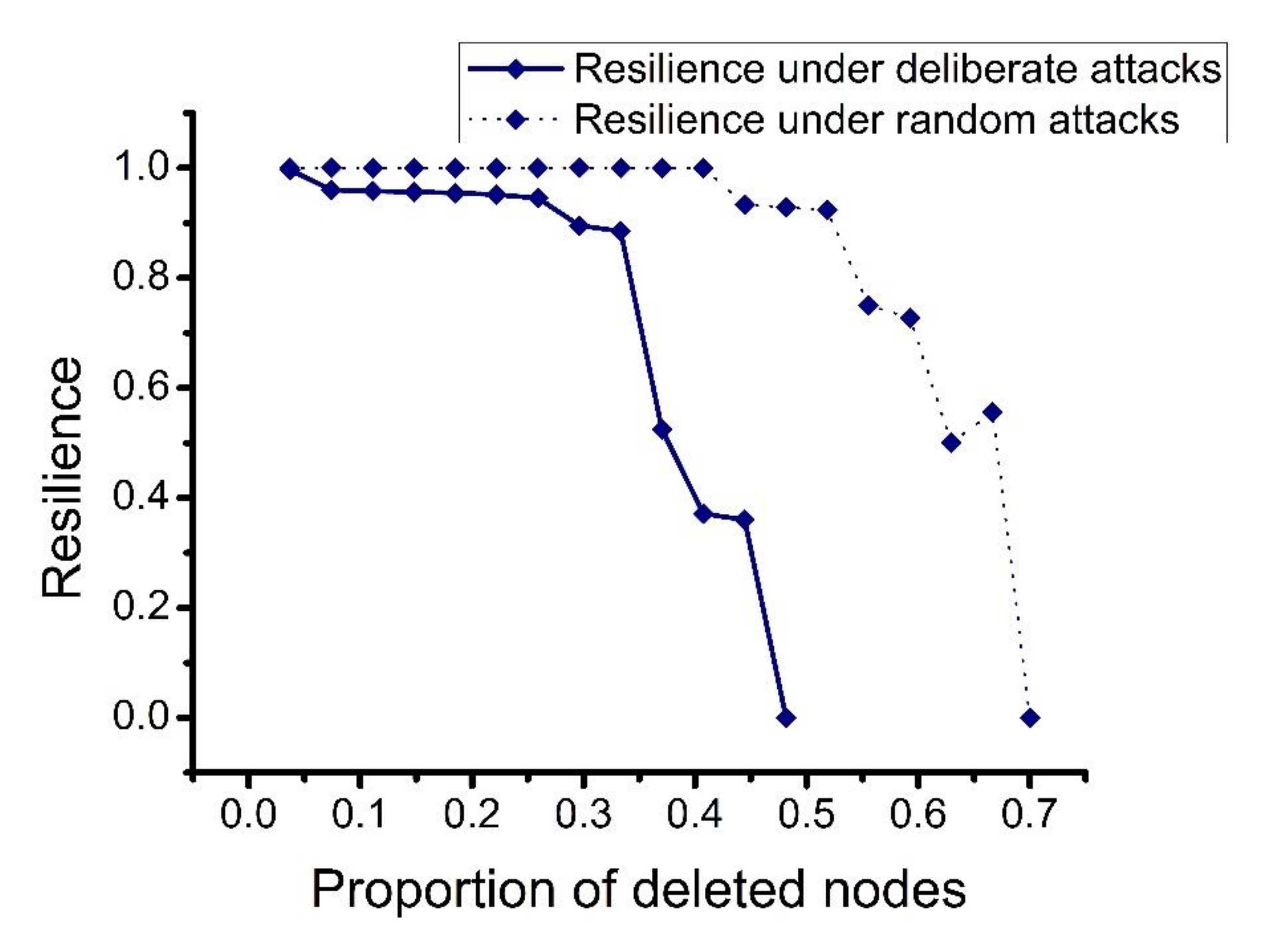
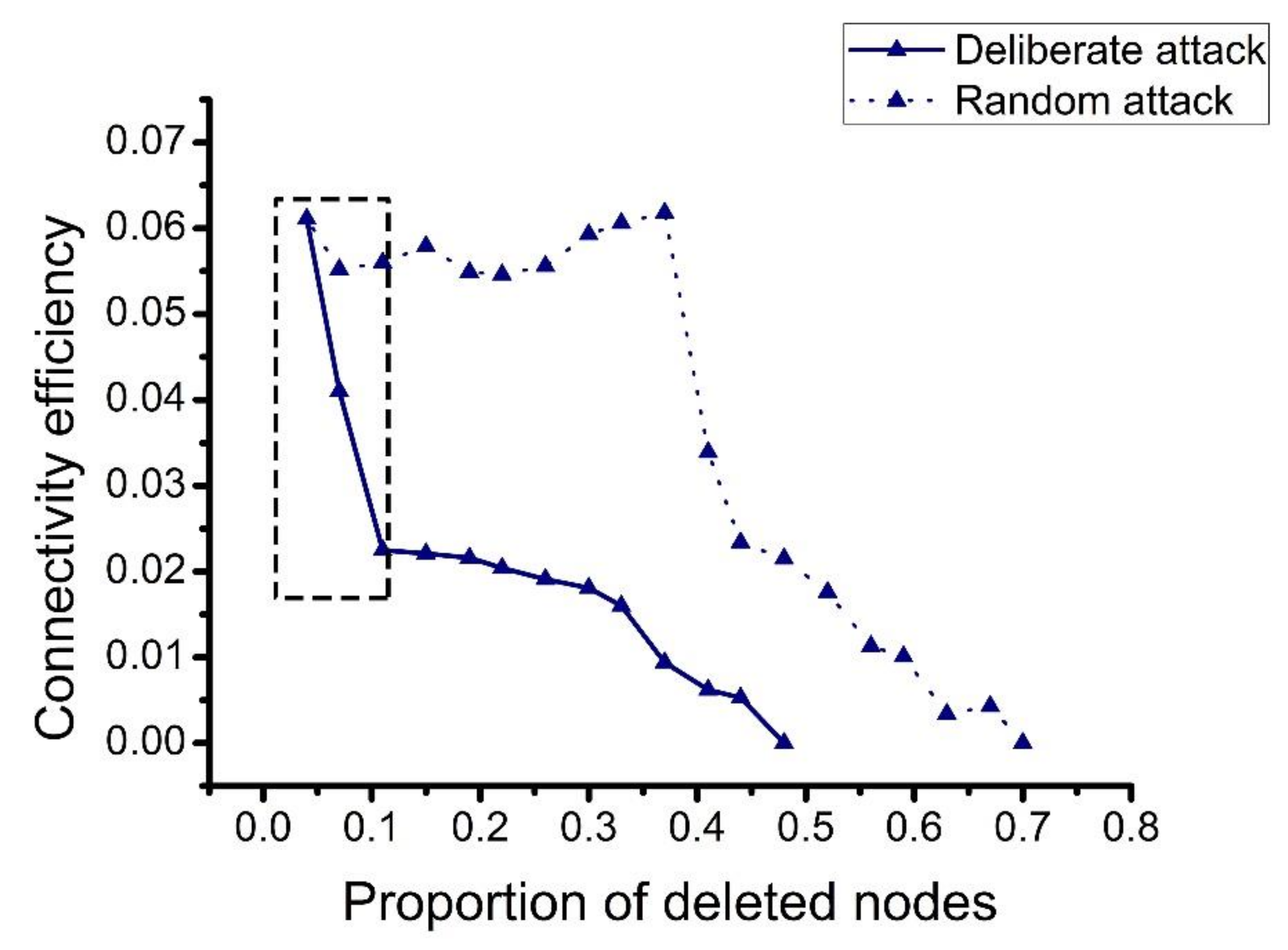
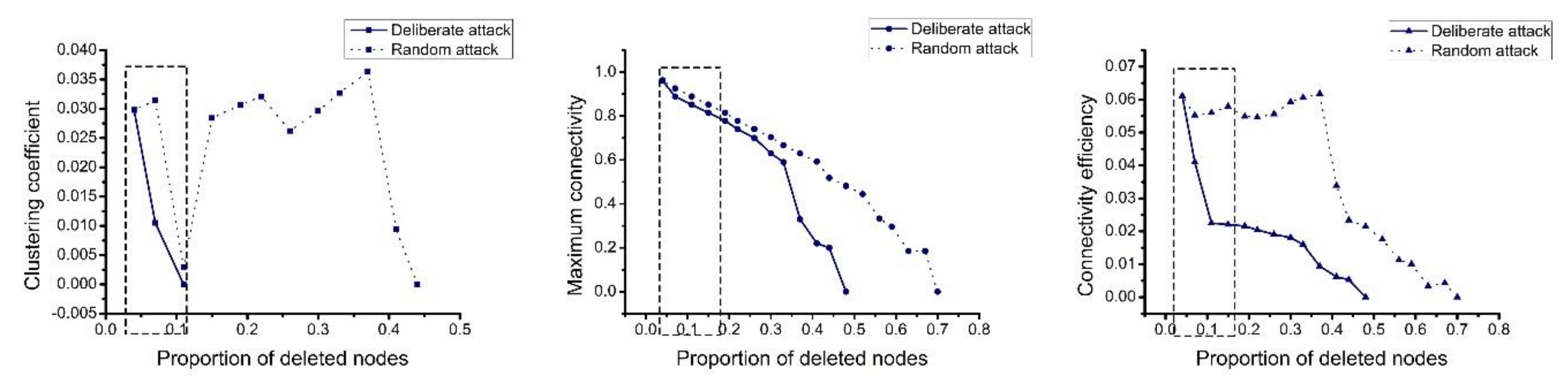
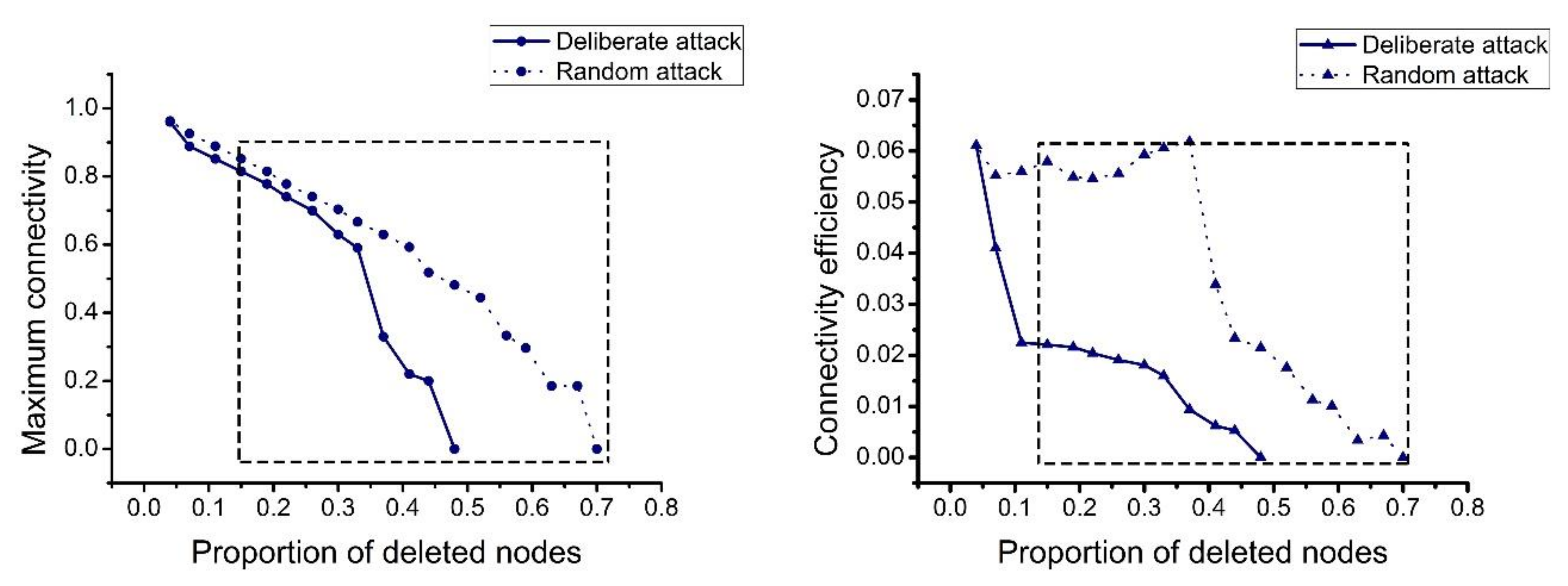
4.2.1. Single Chart Analysis
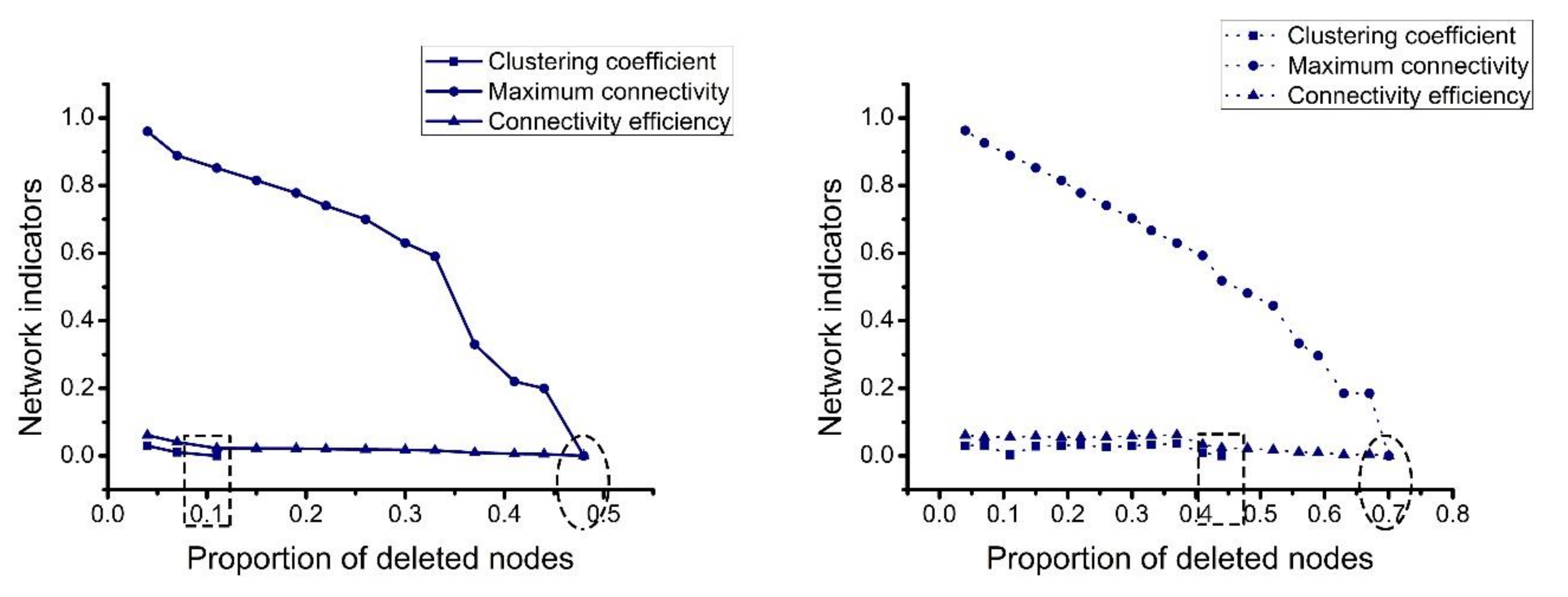
4.2.2. Comprehensive Analysis
5. Conclusions and Policy Recommendations
- (1)
- Protecting important nodes and preventing deliberate attacks. In our analysis, the damage caused by deliberate attacks was found to be far greater than the damage caused by random attacks. Therefore, it is necessary to focus on preventing the occurrence of deliberate attacks. When a deliberate attack occurs, minimizing the damage is then necessary. Deliberate attacks mainly focus on the important nodes in the network. Therefore, the protection of important nodes must be strengthened by establishing a joint protection network for important nodes and preventing problems before they occur.
- (2)
- Strengthening the protection of logistics service integrators. Logistics service integrators have a strong impact on the decline of network indicators and network vulnerability. Once the logistics integrators are destroyed, the operational efficiency of the network greatly decreases. Therefore, strengthening the protection of logistics service integrators and the robustness of the logistics service integrator nodes are essential for maintaining the normal operation of the network.
- (3)
- Paying attention to the role of weak connections. Many connections in the network still exist after the integrator is destroyed because the network is not destroyed; these connections maintain the basic operation of the network. They are not important when the integrator is not destroyed and are considered weak connections. When the integrators’ nodes are destroyed, they become important nodes for maintaining the network. Therefore, it is necessary to pay attention to the role of the weak connections. It is important to keep in touch with some weakly connected companies, and companies should manage them as emergency companies to help them better respond to emergencies.
- (4)
- Preventing deliberate attacks and enhancing the flexibility of the logistics service supply chain. When a deliberate attack occurs, the resilience of the network decreases rapidly. Enterprises can improve network flexibility by designing early warning mechanisms, optimizing original plans, and responding to emergencies afterwards.
Author Contributions
Funding
Conflicts of Interest
References
- Dmitry, I.; Ajay, D.; Tsan-Ming, C. New flexibility drivers for manufacturing, supply chain and service operations. Int. J. Prod. Res. 2018, 56, 4067. [Google Scholar]
- Nilsson, F.R. A complexity perspective on logistics management Rethinking assumptions for the sustainability era. Int. J. Logist. Manag. 2019, 30, 681–698. [Google Scholar] [CrossRef]
- Asgari, N.; Nikbakhsh, E.; Hill, A.; Farahani, R.Z. Supply chain management 1982–2015: A review. Ima J. Manag. Math. 2016, 27, 353–379. [Google Scholar] [CrossRef]
- Cai, C. Contract Design of Logistics Service Supply Chain Considering Reliability. Ph.D. Thesis, Shenyang University of Technology, Shenyang, China, 2019. [Google Scholar]
- Liang, K. Research on TD Company’s Transportation Supplier Management under the Model of Logistics Service Supply Chain. Master’s Thesis, Shijiazhuang Tiedao University, Shijiazhuang, China, 2018. [Google Scholar]
- Muller, E.J. The Top Guns of Third-party Logistics. Distribution 1993, 92, 30–38. [Google Scholar]
- Tian, Y. Supplier Selection in Constructing Logistics Service Supply Chain. Syst. Eng. Theory Pract. 2003, 23, 49–53. [Google Scholar]
- Cui, A.; Liu, W. LSSC coordination based on competence division and cooperation. J. Shanghai Marit. Univ. 2008, 2, 43–47. [Google Scholar]
- Liu, W.; Bai, E.; Liu, L.; Wei, W. A Framework of Sustainable Service Supply Chain Management: A Literature Review and Research Agenda. Sustainability 2017, 9, 421. [Google Scholar] [CrossRef]
- Akkermans, H.; Vos, B. Amplification in service supply chains: An exploratory case study from the telecom industry. Prod. Oper. Manag. 2003, 12, 204–223. [Google Scholar] [CrossRef]
- Gunter, S.; Wilhelm, W.E. Strategic, Tactical and Operational Decisions in Multi- national Logistics Networks: A Review and Discussion of Modeling Issues. Int. J. Prod. Res. 2000, 38, 7. [Google Scholar]
- Yan, X.; Sun, L.; Wang, K. Research on Performance Evaluation and Characteristics in Logistics Service Supply Chain. China Mech. Eng. 2005, 11, 969–974. [Google Scholar]
- Choy, K.L.; Li, C.-L.; So, S.C.K.; Lau, H.; Kwok, S.K.; Leung, D.W.K. Managing uncertainty in logistics service supply chain. Int. J. Risk Assess. Manag. 2007, 7, 61–65. [Google Scholar] [CrossRef]
- Gao, Z.; Zhu, W.; Chen, S. Research on the Integration of Logistics Service Supply Chain. China Bus. Mark. 2017, 31, 46–54. [Google Scholar]
- Zhang, G.; Liu, W. Mechanism of Network Vulnerability of Logistics Service Supply Chain Based on Complex Network Theory. J. Bus. Econ. 2016, 12, 19–27. [Google Scholar]
- Demirkan, H.; Cheng, H.K. The risk and information sharing of application services supply chain. Eur. J. Oper. Res. 2008, 187, 765–784. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, J.; Li, C. Decisions of Supply Chain Considering Chain-to-Chain Competition and Service Negative Spillover Effect. Sustainability 2019, 11, 1612. [Google Scholar] [CrossRef]
- Daryanto, Y.; Wee, H.M.; Astanti, R.D. Three-echelon supply chain model considering carbon emission and item deterioration. Transp. Res. Part E Logist. Transp. Rev. 2019, 122, 368–383. [Google Scholar] [CrossRef]
- Novais, L.; Manuel Maqueira, J.; Ortiz-Bas, A. A systematic literature review of cloud computing use in supply chain integration. Comput. Ind. Eng. 2019, 129, 296–314. [Google Scholar] [CrossRef]
- Guerrero Campanur, A.; Olivares-Benitez, E.; Miranda, P.A.; Eleazar Perez-Loaiza, R.; Ablanedo-Rosas, J.H. Design of a Logistics Nonlinear System for a Complex, Multiechelon, Supply Chain Network with Uncertain Demands. Complexity 2018, 2018. [Google Scholar] [CrossRef]
- Zou, Y.; Donner, R.V.; Marwan, N.; Donges, J.F.; Kurths, J. Complex network approaches to nonlinear time series analysis. Phys. Rep. Rev. Sect. Phys. Lett. 2019, 787, 1–97. [Google Scholar] [CrossRef]
- Wang, H.; Wang, J.; Small, M.; Moore, J.M. Review mechanism promotes knowledge transmission in complex networks. Appl. Math. Comput. 2019, 340, 113–125. [Google Scholar] [CrossRef]
- Tsiotas, D.; Charakopoulos, A. Visibility in the topology of complex networks. Phys. A Stat. Mech. Appl. 2018, 505, 280–292. [Google Scholar] [CrossRef]
- Surana, A.; Kumara, S.; Greaves, M.; Raghavan, U.N. Supply-chain networks: A complex adaptive systems perspective. Int. J. Prod. Res. 2005, 43, 4235–4265. [Google Scholar] [CrossRef]
- ANE Logistics. Available online: http://www.ane56.com/ (accessed on 5 February 2020).
- Han, H. Research on ANE Logistics Service Supply Chain Risk Based on FMEA. Master’s Thesis, Ocean University of China, Qingdao, China, 2014. [Google Scholar]
- Kuaidi 100. Available online: https://www.kuaidi100.com/ (accessed on 5 February 2020).
- Qian, C.; Wang, S.; Liu, X.; Zhang, X. Low-Carbon Initiatives of Logistics Service Providers: The Perspective of Supply Chain Integration. Sustainability 2019, 11, 3233. [Google Scholar] [CrossRef]
- Zhang, G.; Liu, W. Vulnerability measurement research of complex network of logistics service supply chain. Comput. Eng. Appl. 2017, 53, 224–230. [Google Scholar]
- Adger, W.N. Vulnerability. Glob. Environ. Chang. 2006, 16, 268–281. [Google Scholar] [CrossRef]
- Chen, B.Y.; Lam, W.H.K.; Sumalee, A.; Li, Q.; Li, Z.-C. Vulnerability analysis for large-scale and congested road networks with demand uncertainty. Trans. Res. Part A Policy Pract. 2012, 46, 501–516. [Google Scholar] [CrossRef]
- Chen, X.; Li, J. Community detection in complex networks using edge-deleting with restrictions. Phys. A Stat. Mech. Appl. 2019, 519, 181–194. [Google Scholar] [CrossRef]
- Zhao, L.; W, X. Research Progress on Supply Chain Elasticity Management. J. Southeast Univ. 2019, 15, 21–27, 134. [Google Scholar]
- Liang, X. Research and Analysis on Simulation and Resilience of Container Logistics Center. Ph.D. Thesis, Wuhan University of Technology, Wuhan, China, 2018. [Google Scholar]
- Fan, P.; Xu, Y.; Cui, G. Research on Elasticity of Complex Network Model. Heilongjiang Sci. Technol. Inf. 2016, 33, 153. [Google Scholar]
- Ma, F.; Liu, F.; Yuen, K.F. Cascading Failures and Vulnerability Evolution in Bus-Metro Complex Bilayer Network under Rainstorm Weather Conditions. Int. J. Env. Res. Pub. He. 2019, 16, 1–30. [Google Scholar]
- Li, M. Invulnerability Reasearch of China High-Speed Railway Network based on Complex Network Theory. Master’s Thesis, Beijing Jiaotong University, Beijing, China, 2019. [Google Scholar]
- Ma, F.; Liang, Y.; Yuen, K.F.; Sun, Q.P. Assessing the vulnerability of urban rail transit network under heavy air pollution: A dynamic vehicle restriction perspective. Sustain. Cities Soc. 2020, 52, 1–13. [Google Scholar]





| No. | Out of Point | Entry Point | No. | Out of Point | Entry Point | No. | Out of Point | Entry Point |
|---|---|---|---|---|---|---|---|---|
| 1 | 17 | 5 | 31 | 20 | 4 | 61 | 24 | 13 |
| 2 | 17 | 15 | 32 | 20 | 10 | 62 | 24 | 6 |
| 3 | 17 | 13 | 33 | 21 | 19 | 63 | 24 | 15 |
| 4 | 17 | 6 | 34 | 21 | 18 | 64 | 24 | 5 |
| 5 | 17 | 8 | 35 | 21 | 10 | 65 | 24 | 7 |
| 6 | 17 | 11 | 36 | 21 | 15 | 66 | 25 | 18 |
| 7 | 17 | 1 | 37 | 21 | 12 | 67 | 25 | 17 |
| 8 | 17 | 2 | 38 | 21 | 11 | 68 | 25 | 15 |
| 9 | 18 | 15 | 39 | 21 | 13 | 69 | 25 | 13 |
| 10 | 18 | 6 | 40 | 21 | 14 | 70 | 25 | 5 |
| 11 | 18 | 13 | 41 | 22 | 18 | 71 | 25 | 11 |
| 12 | 18 | 6 | 42 | 22 | 19 | 72 | 25 | 8 |
| 13 | 18 | 8 | 43 | 22 | 12 | 73 | 25 | 12 |
| 14 | 18 | 5 | 44 | 22 | 8 | 74 | 26 | 17 |
| 15 | 18 | 12 | 45 | 22 | 2 | 75 | 26 | 19 |
| 16 | 18 | 10 | 46 | 22 | 3 | 76 | 26 | 5 |
| 17 | 19 | 7 | 47 | 22 | 10 | 77 | 26 | 10 |
| 18 | 19 | 14 | 48 | 22 | 16 | 78 | 26 | 12 |
| 19 | 19 | 3 | 49 | 23 | 19 | 79 | 26 | 7 |
| 20 | 19 | 16 | 50 | 23 | 18 | 80 | 26 | 13 |
| 21 | 19 | 5 | 51 | 23 | 4 | 81 | 26 | 2 |
| 22 | 19 | 13 | 52 | 23 | 12 | 82 | 27 | 19 |
| 23 | 19 | 8 | 53 | 23 | 6 | 83 | 27 | 17 |
| 24 | 19 | 11 | 54 | 23 | 8 | 84 | 27 | 3 |
| 25 | 20 | 19 | 55 | 23 | 13 | 85 | 27 | 14 |
| 26 | 20 | 18 | 56 | 23 | 7 | 86 | 27 | 4 |
| 27 | 20 | 3 | 57 | 23 | 15 | 87 | 27 | 5 |
| 28 | 20 | 15 | 58 | 24 | 18 | 88 | 27 | 1 |
| 29 | 20 | 5 | 59 | 24 | 19 | 89 | 27 | 6 |
| 30 | 20 | 11 | 60 | 24 | 10 | — | — | — |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ma, F.; Xue, H.; Yuen, K.F.; Sun, Q.; Zhao, S.; Zhang, Y.; Huang, K. Assessing the Vulnerability of Logistics Service Supply Chain Based on Complex Network. Sustainability 2020, 12, 1991. https://doi.org/10.3390/su12051991
Ma F, Xue H, Yuen KF, Sun Q, Zhao S, Zhang Y, Huang K. Assessing the Vulnerability of Logistics Service Supply Chain Based on Complex Network. Sustainability. 2020; 12(5):1991. https://doi.org/10.3390/su12051991
Chicago/Turabian StyleMa, Fei, Huifeng Xue, Kum Fai Yuen, Qipeng Sun, Shumei Zhao, Yanxia Zhang, and Kai Huang. 2020. "Assessing the Vulnerability of Logistics Service Supply Chain Based on Complex Network" Sustainability 12, no. 5: 1991. https://doi.org/10.3390/su12051991
APA StyleMa, F., Xue, H., Yuen, K. F., Sun, Q., Zhao, S., Zhang, Y., & Huang, K. (2020). Assessing the Vulnerability of Logistics Service Supply Chain Based on Complex Network. Sustainability, 12(5), 1991. https://doi.org/10.3390/su12051991







