7S Model for Technology Protection of Organizations
Abstract
:1. Introduction
2. Related Research
2.1. Cases of Technology Leakages
2.2. Technology Protection Models
S Model for Technology Protection
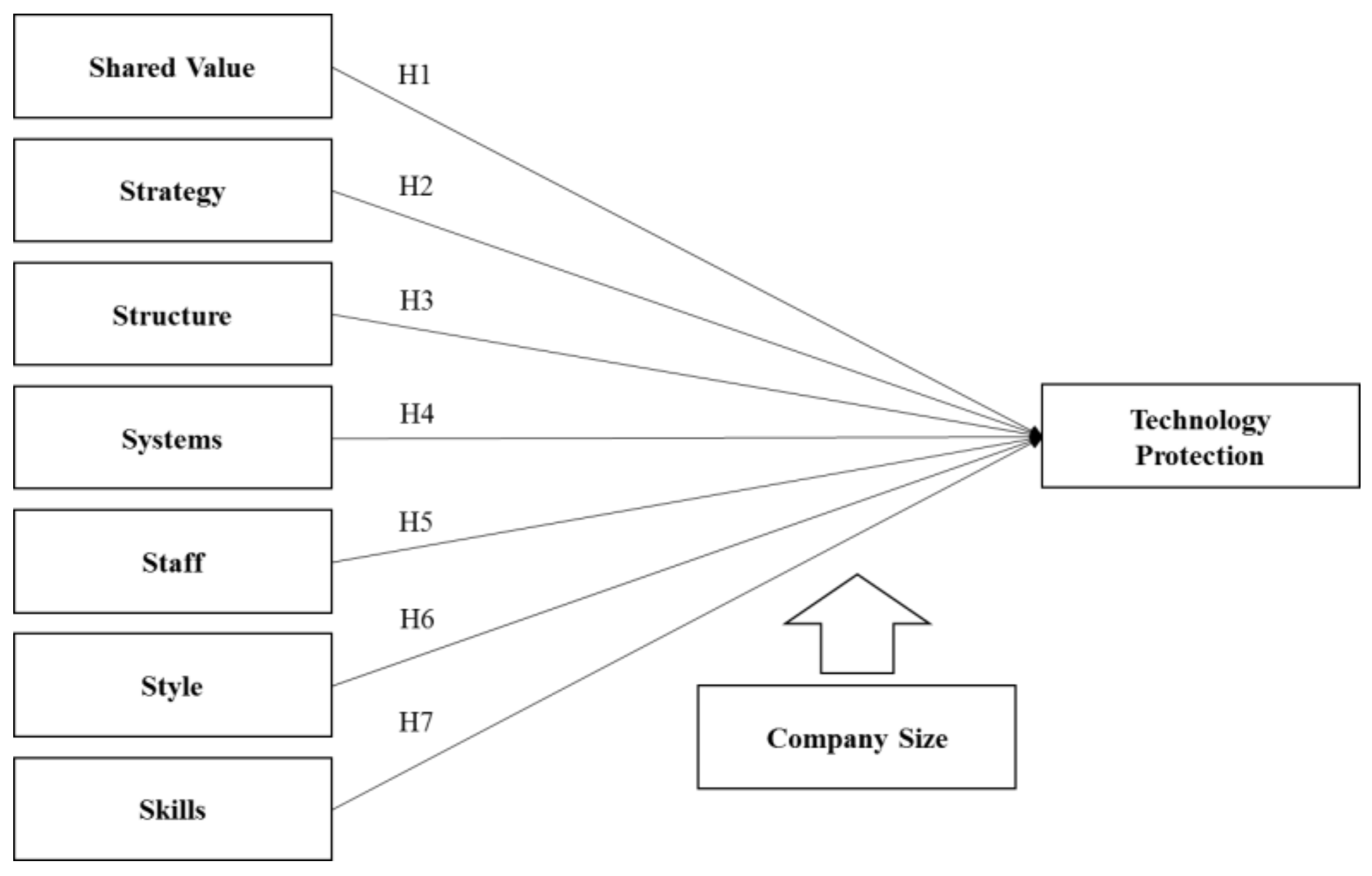
3. Research Model and Hypothesis Development
4. Method and Data
5. Results
5.1. Verification of the Measurement Model
5.2. Hypotheses Testing and Relative Importance
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Park, S.; Kim, Y.; Park, G.; Na, O.; Chang, H. Research on digital forensic readiness design in a cloud computing-based smart work environment. Sustainability 2018, 10, 1203. [Google Scholar] [CrossRef] [Green Version]
- Ferry, J. Top Five Cases of Huawei IP Theft and Patent Infringement. Available online: https://www.prosperousamerica.org/top_five_cases_of_huawei_ip_theft_and_patent_infringement (accessed on 21 June 2021).
- Ferry, J. Top Ten Cases of Chinese IP Theft. Available online: https://www.prosperousamerica.org/top_ten_cases_of_chinese_ip_theft (accessed on 21 June 2021).
- Parker, H. Knowledge acquisition and leakage in inter-firm relationships involving new technology-based firms. Manag. Decis. 2012, 50, 1618–1633. [Google Scholar] [CrossRef]
- Chang, H.-B. The design of information security management system for SMEs industry technique leakage prevention. J. Korea Multimed. Soc. 2010, 13, 111–121. [Google Scholar]
- Kim, J.; Lee, C.; Chang, H. The Development of a Security Evaluation Model Focused on Information Leakage Protection for Sustainable Growth. Sustainability 2020, 12, 10639. [Google Scholar] [CrossRef]
- Waterman, R.H.; Peters, T.J. In Search of Excellence: Lessons from America’s Best-Run Companies; Harper & Row: New York, NY, USA, 1982. [Google Scholar]
- Chen, J.-X.; Liu, W. Research on operational risk management framework for commercial banks in Internet world-based on McKinsey 7S model. In Proceedings of the 2010 International Conference on Internet Technology and Applications, Wuhan, China, 20–22 August 2010; pp. 1–6. [Google Scholar]
- Gechkova, T.; Kaleeva, T. The mckinsey 7s model in the airport system protection. Knowl. Int. J. 2020, 42, 843–848. [Google Scholar]
- Peteraf, M.A.; Bergen, M.E. Scanning dynamic competitive landscapes: A market-based and resource-based framework. Strateg. Manag. J. 2003, 24, 1027–1041. [Google Scholar] [CrossRef]
- Miyazaki, K. Building Competences in the Firm: Lessons from Japanese and European Optoelectronics; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Eisenhardt, K.M. Making fast strategic decisions in high-velocity environments. Acad. Manag. J. 1989, 32, 543–576. [Google Scholar]
- Korean National Police Agency. Available online: https://www.police.go.kr/index.do (accessed on 21 June 2021).
- Stone, D.L.; Deadrick, D.L.; Lukaszewski, K.M.; Johnson, R. The influence of technology on the future of human resource management. Hum. Resour. Manag. Rev. 2015, 25, 216–231. [Google Scholar] [CrossRef]
- Korean Intellectual Property Office. Manual for Trade Secret Management; Korean Intellectual Property Office: Daejeon, Korea, 2011.
- Ministry of Trade Industry and Energy. Industrial Technology Protection Guidelines; Ministry of Trade Industry and Energy: Sejong, Korea, 2021.
- Ministry of SMEs and Startups. Technology Protection Guidelines for Small and Medium-Sized Enterprises; Ministry of SMEs and Startups: Daejeon, Korea, 2018.
- Swanson, M. Security Self-Assessment Guide for Information Technology Systems; Booz-Allen and Hamilton Inc.: Mclean, VA, USA, 2001. [Google Scholar]
- Office of the Government Chief Information Officer. Practice Guide for Security Risk Assessment & Audit [ISPG-SM01]; Office of the Government Chief Information Officer: Wan Chai, Hong Kong, 2017.
- Australian Cyber Security Centre. Australian Government Information Security Manual; Australian Cyber Security Centre: Kingston, Australia, 2021.
- International Organization for Standardization. Available online: https://www.iso.org (accessed on 21 June 2021).
- Hong, S.W.; Park, J.-P. Effective Management of Personal Information & Information Security Management System (ISMS-P) Authentication systems. J. Korea Acad. Ind. Coop. Soc. 2020, 21, 634–640. [Google Scholar]
- Johansson, E.; Johnson, P. Assessment of enterprise information security-an architecture theory diagram definition. In Proceedings of the Conference on Systems Engineering Research, Hoboken, NJ, USA, 24 March 2005. [Google Scholar]
- Bae, J.-M.; Kim, S.; Chang, H. A study on design direction of industry-centric security level evaluation model through analysis of security management system. J. Soc. E Bus. Stud. 2016, 20, 177–191. [Google Scholar] [CrossRef]
- Eminağaoğlu, M.; Uçar, E.; Eren, Ş. The positive outcomes of information security awareness training in companies–A case study. Inf. Secur. Tech. Rep. 2009, 14, 223–229. [Google Scholar] [CrossRef]
- Hunker, J.; Probst, C.W. Insiders and Insider Threats-An Overview of Definitions and Mitigation Techniques. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2011, 2, 4–27. [Google Scholar]
- Wong, W.P.; Tan, H.C.; Tan, K.H.; Tseng, M.-L. Human factors in information leakage: Mitigation strategies for information sharing integrity. Ind. Manag. Data Syst. 2019, 119, 1242–1267. [Google Scholar] [CrossRef]
- Lim, H.-c.L.; Kwon, Y.-h.; Park, S.-h.; Han, H.-j. Development of a Diagnosis Tool to Measure Enterprise Security Culture Using 7S Model and Competing Value Model. Korean Manag. Consult. Rev. 2017, 17, 183–192. [Google Scholar]
- Von Solms, B. Information security—The fourth wave. Comput. Secur. 2006, 25, 165–168. [Google Scholar] [CrossRef]
- Sullivant, J. Building a Corporate Culture of Security: Strategies for Strengthening Organizational Resiliency; Butterworth-Heinemann: Oxford, UK, 2016. [Google Scholar]
- Bacal, R. Organizational conflict-the good, the bad, and the ugly. J. Qual. Particip. 2004, 27, 21–22. [Google Scholar]
- Naipinit, T.; Kojchavivong, S.; Kowittayakorn, V.; Sakolnakorn, T.P.N. McKinsey 7S model for supply chain management of local SMEs construction business in upper northeast region of Thailand. Asian Soc. Sci. 2014, 10, 35–41. [Google Scholar] [CrossRef]
- AlHogail, A.; Mirza, A. Information security culture: A definition and a literature review. In Proceedings of the 2014 World Congress on Computer Applications and Information Systems (WCCAIS), Hammamet, Tunisia, 17–19 January 2014; pp. 1–7. [Google Scholar]
- Singh, A. A study of role of McKinsey’s 7S framework in achieving organizational excellence. Organ. Dev. J. 2013, 31, 39–51. [Google Scholar]
- Ravanfar, M.M. Analyzing Organizational Structure based on 7s model of McKinsey. Glob. J. Manag. Bus. Res. 2015, 15, 6–12. [Google Scholar] [CrossRef]
- Anderson, E.E.; Choobineh, J. Enterprise information security strategies. Comput. Secur. 2008, 27, 22–29. [Google Scholar] [CrossRef]
- Modenov, A.; Vlasov, M. Organizational structure and economic security of an enterprise. Rev. Espac. 2018, 39, 22. [Google Scholar]
- Antoni, C.H.; Baeten, X.; Perkins, S.J.; Shaw, J.D.; Vartiainen, M. Reward management: Linking employee motivation and organizational performance. J. Pers. Psychol. 2017, 16, 57–60. [Google Scholar] [CrossRef]
- Furnell, S.; Clarke, N. Organizational security culture: Embedding security awareness, education, and training. In Proceedings of the IFIP TC11 WG, Moscow, Russia, 18–20 May 2005; pp. 67–74. [Google Scholar]
- Odetunde, O.J. Influence of transformational and transactional leaderships, and leaders’ sex on organisational conflict management behaviour. Gend. Behav. 2013, 11, 5323–5335. [Google Scholar]
- Centre for the Protection of National Infrastructure. Managing Security Risks throughout COVID-19; Centre for the Protection of National Infrastructure: London, UK, 2021.
- Pradhan, M.K.; Oh, J.; Lee, H. Understanding travelers’ behavior for sustainable smart tourism: A technology readiness perspective. Sustainability 2018, 10, 4259. [Google Scholar] [CrossRef] [Green Version]
- Henseler, J.; Ringle, C.M.; Sinkovics, R.R. The use of partial least squares path modeling in international marketing. In New Challenges to International Marketing; Emerald Group Publishing Limited: Bingley, UK, 2009. [Google Scholar]
- Binsawad, M.H. Corporate Social Responsibility in Higher Education: A PLS-SEM Neural Network Approach. IEEE Access 2020, 8, 29125–29131. [Google Scholar] [CrossRef]
- Abdi, H. Factor rotations in factor analyses. In Encyclopedia for Research Methods for the Social Sciences; Sage: Thousand Oaks, CA, USA, 2003; pp. 792–795. [Google Scholar]
- Chin, W.W.; Johnson, N.; Schwarz, A. A fast form approach to measuring technology acceptance and other constructs. MIS Q. 2008, 32, 687–703. [Google Scholar] [CrossRef]
- Chong, A.Y.-L.; Liu, M.J.; Luo, J.; Keng-Boon, O. Predicting RFID adoption in healthcare supply chain from the perspectives of users. Int. J. Prod. Econ. 2015, 159, 66–75. [Google Scholar] [CrossRef]
- Foo, P.-Y.; Lee, V.-H.; Tan, G.W.-H.; Ooi, K.-B. A gateway to realising sustainability performance via green supply chain management practices: A PLS–ANN approach. Expert Syst. Appl. 2018, 107, 1–14. [Google Scholar] [CrossRef]
- Zabukovšek, S.S.; Kalinic, Z.; Bobek, S.; Tominc, P. SEM–ANN based research of factors’ impact on extended use of ERP systems. Cent. Eur. J. Oper. Res. 2019, 27, 703–735. [Google Scholar] [CrossRef]
- Beckett, J.C. Evaluating the Need for IT Security in the Small Medium Enterprise Sectors; Texas A&M University: College Station, TX, USA, 2017. [Google Scholar]
- Karlsson, M.; Denk, T.; Åström, J. Perceptions of organizational culture and value conflicts in information security management. Inf. Comput. Secur. 2018, 26, 213–229. [Google Scholar] [CrossRef]
- Herath, T.; Rao, H.R. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 2009, 47, 154–165. [Google Scholar] [CrossRef]
- Solomon, J.; Solomon, A.; Park, C.Y. The evolving role of institutional investors in South Korean corporate governance: Some empirical evidence. Corp. Gov. Int. Rev. 2002, 10, 211–224. [Google Scholar] [CrossRef]

| Year | Case Name | Source of Leak | Detailed Description |
|---|---|---|---|
| 2010 | Leakage of confidential information related to Boeing’s Space Shuttle program and the Delta IV rocket | Former employee | A former Rockwell and Boeing engineer sent trade secrets comprising information related to the Space Shuttle program and the Delta IV rocket to China via Chinese spies |
| 2011 | Leakage of stealth missile exhaust designs and military-technical data | Current employee | Noshir Gowadia, an engineer with the Northrop Grumman Corporation, leaked stealth missile exhaust designs and military-technical data to assist China with its cruise missile system |
| 2015 | Leakage of technology related to the insulation of cryogenic and liquefied natural gas (LNG) systems | Former employee | A former researcher from the shipbuilding industry renamed 15 files containing key technical data as “research preparation” and emailed to a Germany-based chemical company from a personal account, before moving to the company |
| 2016 | Leakage of designs related to Hyundai Heavy Industries’ engine power plant | Supplier’s Employee | An employee of Hyundai Heavy Industries’ supplier stored designs instead of destroying them after testing parts belonging to the engine power plant. Subsequently, the supplier copied, produced, and sold the fuel injection system to distributors and other parties. |
| 2017 | Leakage of designs related to membrane tanks for LNG storage | Former employee | A former team leader of a research institute had stolen the designs of membrane tanks developed by the institute. After resigning from the institute, this ex-employee joined a new company and used the stolen designs to construct a new factory and build mold manufacturing facilities for membrane tanks |
| 2017 | Leakage of technology related to Waymo’s LiDAR | Former employee | Anthony Levandowski illegally obtained R&D information while employed at Waymo, an R&D company specializing in autonomous driving technology. After resigning, he joined a new company, Otto, and used the technology. |
| 2018 | Leakage of technology related to Samsung Display’s edge display | Supplier’s Employee | TOPTEC, a manufacturer of Samsung Display, was exclusively supplying products to Samsung and was also under the confidentiality agreement. However, TOPTEC leaked the technology behind the products to a Chinese company in exchange for financial gain |
| 2019 | Leakage of wet etching techniques for displays | Former employee | Upon resignation, a former developer of a South Korean SME transferred the entire technology-related source code of its company to a USB. A Chinese company that subsequently hired the developer used this leaked information. |
| 2019 | Leakage of BASF’s confidential information related to semiconductors | Former and current employees | The former and current employees of BASF leaked manufacturing-related technologies to China |
| 2020 | Leakage of key technology related to autonomous vehicles | Current employee | A professor at the Korea Advanced Institute of Science and Technology (KAIST) signed a research service contract with the Chongqing University of Technology in China without notifying KAIST. Subsequently, the professor leaked KAIST’s research data on the light detection and ranging technology of the autonomous vehicles to the researchers of the Chinese university |
| 2020 | Leakage of technology belonging to the Agency for Defense Development (ADD) | Former employee | More than 20 retired ADD researchers leaked a considerable amount of data on weapons-related technologies and information over the course of years |
| 2020 | Leakage of SoftBank’s confidential information | Former employee | A former employee used an office computer to access the company’s server and steal confidential manuals. Subsequently, the employee allowed a Russian trade diplomat to take pictures of the office computer screen containing confidential information and to encode the photo data |
| 2020 | Leakage of Samsung’s supplier SK Hynix’s semiconductor technology | Supplier’s Employee | The supplier company SK Hynix leaked core technologies to a competing Chinese semiconductor company |
| Classification | Evaluation Area | Evaluation Item | ||
|---|---|---|---|---|
| South Korea | The Manual for Trade Secret Management | Managerial Security | Trade Secret Policies Trade Secret Classification Trade Secret Management | |
| Personnel Security | Personnel Security Partners Management Planning of Security Education | |||
| Physical Security | Documentation Security Control Area Designation Computer Management | |||
| Industrial Technology Protection Guidelines | Managerial Security | NDA: NON-DISCLOSURE AGREEMENT Security Policies Incident Response | ||
| Personnel Security | Appointment of Professionals Professionals Classification Education and Training for Professionals | |||
| Physical Security | Protection Area Management Baggage Inspection | |||
| Technical Security | Protection Area Security Information Asset Management | |||
| Technology Protection Guidelines for Small and Medium-Sized Enterprises | Policies of Technology Protection | Appointment of Technical Protection Department Asset Management | ||
| Personnel Security | Personnel Management NDA: NON-DISCLOSURE AGREEMENT Employeesʼ Invention System | |||
| Facilities Management | Appointment of Protection Area Protection Facilities Area-specific Security Management | |||
| Information System Management | Periodically Backup Unnecessary System Uninstall Security Program Installation | |||
| Other Countries | U.S. (NIST) | Security self-assessment guide for information technology systems (SP800-26) | Management Controls | Risk Management Review of Security Controls Life Cycle Authorize Processing System Security Plan |
| Operational Controls | Personnel Security Physical Security Production, Input/Output Controls Technical Security | |||
| Technical Controls | Identification and Authentication Logical Access Controls Audit Trails | |||
| Hong Kong (OGCIO) | Practice guide for security risk assessment & audit (ISPG-SM01) | IT Security Policies | Security policy is well documented and easy to understand All rules stated in the security policy are implemented | |
| Human Resource Security | All staff are advised with acknowledgment of their IT security responsibilities All roles & responsibilities are clearly defined | |||
| Asset Management | Information is properly classified and its storage media is labeled and handled according to Security Regulations | |||
| Access Control | Each user is given with unique user identity User are informed about their privileges and access rights | |||
| Physical and Environmental Security | UPS are installed for necessary equipment Smoking, food, and drinks are not allowed inside the computer room | |||
| Technical Security | Network Management Firewall Management | |||
| Australian (ACSC) | Australian Government Information Security Manual | Security documentation | Development and management of documentation System-specific documentation | |
| Personnel Security | Cybersecurity awareness-raising and training Access to systems and their resources | |||
| Physical Security | Facilities and systems ICT equipment and media | |||
| Evaluation Area | Evaluation Item | |
|---|---|---|
| ISO/IEC 27001 | Managerial Security | Information security policies Operations security Organization of information security Human resource security Asset management Supplier relationships Information security incident management Information security aspects of business continuity management Compliance; with internal requirements, such as policies, and with external requirements, such as laws |
| Physical Security | Physical Security Environmental Security | |
| Technical Security | Cryptography Operations security Communications security System acquisition, development, and maintenance | |
| ISMS-P | Managerial security system | Managerial security system Risk Management Managerial Security System development and maintenance |
| Protection Plan | Policies, Organizational and Asset management Human Resource Security Outsider Security Physical Security Access Control Cryptography System Development Security System Operations security Incident Response | |
| Personal Information Management System | Protection System for Personal Information | |
| Authors | Evaluation Area | Evaluation Item |
|---|---|---|
| Johansson and Johnson [23] | Scope | Technical, Organizational, Environmental |
| Purpose | Responsive, Detective, Preventive | |
| Time | Planning, Operating, Controlling | |
| Chang [5] | Investment Accounts for Technology Protection | Technology Protection Education and Training |
| Environment of Industrial Technology Protection | Managerial Security Human Resource Security | |
| Structure of Industrial Technology Protection | Physical Security Technical Security | |
| Bae, Kim, and Chang [24] | Environment of Industrial Technology Protection | Industrial Security Investment accounts Knowledge for Employees of Regulations about Industrial Technology Protection Related Business |
| Information Security Policies | Review of Policy and Management of Policy Document Effectiveness Assessment of Regulations about Industrial Technology Protection | |
| Organization of Information Security | Appointment of Chief Information Security Officer Information Security Committee | |
| Outsider Security | Execution Management of Outsider Security Security after Outsider Contract | |
| Industrial Asset management | Identification of Information Asset Intellectual Property Right Management | |
| Industrial Security Education and Training | Planning of Education Execution Assessment of Education Program | |
| Human Resource Security | Appointment of Main Person in Charge Foreign Employee Management and Outsourcing Employee and Visitor Management | |
| Physical Security | Appointment of Protection Area Protection Facilities Mobile Security | |
| System Development Security | Definition of Security Requirement Security Log | |
| Cryptography | Cryptography Policies | |
| Access Control | Establishment of Access Control Policy User Registration and Authorization | |
| Operation Management | Operational Procedure and Responsibilities Acquisition of Information System | |
| Incident Response to Industrial Technology Protection | Experience of leakage Number and cost of technology leakage | |
| Emergency Accident Management | Response Plan and System Digital Forensic | |
| IT Disaster Recovery | Establishment of IT Disaster Recovery System | |
| Difficulties and Policy Recommendations of Industrial Technology Protection | Application in Operation of Information Instrument Technology Leakage Risk Assessment Assessment of Management Level | |
| Kim, Lee, and Chang [6] | Security change management | Measuring and improving the security level |
| Incident response | ||
| Security operation management | Physical security system Electronic security system Managerial security system Classification of developed technology | |
| Security support environment | Security organization and investment | |
| Security culture | Internal/External security culture |
| Classification | Definition |
|---|---|
| Shared Values | The content on the importance of technology protection is integrated with a company’s shared goals and core values. |
| Strategy | An established technology protection strategy and sufficient budgetary allocation for the strategy |
| Structure | The way a company is organized to protect its technology |
| Systems | The activities and procedures necessary for technology protection |
| Staff | Members’ understanding of roles and responsibilities toward technology protection |
| Style | The management team’s perception of technology protection |
| Skills | The skills of employees in charge of technology protection and the competency of those skills |
| Element | Items | References | |
|---|---|---|---|
| Shared Values | SV1 | My company shares the importance and value of technology protection. | [29] |
| SV2 | My company includes the concept of technology protection in its management goals. | ||
| SV3 | My organization is aware of the necessity for technology protection. | ||
| SV4 | My company has an organizational culture that protects its technology. | ||
| Strategy | SG1 | My company has a technology protection strategy. | [7] |
| SG2 | For my company, technology protection is a strategic priority. | ||
| SG3 | My company has a technology protection plan. | ||
| SG4 | My company invests a sufficient budget for protecting its technology. | ||
| Structure | SU1 | My company has a systematic organizational structure for protecting its technology. | [31] |
| SU2 | My company has a division in charge of its technology protection responsibilities. | ||
| SU3 | My company has a manager in charge of the technology protection responsibilities. | ||
| SU4 | My company operates and manages its technology protection responsibilities efficiently. | ||
| Systems | SM1 | My company has the relevant regulations to protect its technology. | [32] |
| SM2 | My company controls and monitors its technical data. | ||
| SM3 | My company uses confidentiality and non-compete agreements to protect its technology. | ||
| SM4 | My company uses rewards for employees who are excellent at protecting the company’s technology and punishments for those who violate regulations. | ||
| Staff | SF1 | The members of my company understand their roles and responsibilities toward protecting the company’s technology. | [33] |
| SF2 | The members of my company strictly adhere to the relevant regulations and directives to protect the company’s technology. | ||
| SF3 | The members of my company receive training related to technology protection. | ||
| SF4 | The members of my company respect the managers in charge of technology protection. | ||
| Style | SY1 | The management team at my company has a high level of interest in technology protection. | [34] |
| SY2 | The management team at my company recognizes that technology protection is important to business activities. | ||
| SY3 | The management team at my company actively supports the protection of the company’s technology. | ||
| SY4 | The management team at my company takes the issue of technology protection into account during decision-making processes. | ||
| Skills | SK1 | At my company, the division in charge of the company’s technology protection has expertise in technology protection. | [35] |
| SK2 | At my company, the members of personnel in charge of the company’s technology protection have professional certifications. | ||
| SK3 | At my company, the division or personnel in charge of the company’s technology protection receive the relevant professional training. | ||
| SK4 | My company has a response manual for the occurrence of technology leakages. | ||
| Technology Protection | TP1 | My company protects technology-related confidentiality well. | [6] |
| TP2 | My company is better at managing security than are other companies. | ||
| TP3 | My company has fewer technology leaks or security incidents compared to other companies. | ||
| TP4 | My company has never suffered major damage from technology leaks or security incidents. | ||
| Classification | Classification | N | % |
|---|---|---|---|
| Gender | Male | 310 | 71.3% |
| Female | 125 | 28.7% | |
| Age | 20 years | 120 | 27.6% |
| 30 years | 108 | 24.8% | |
| 40 years | 115 | 26.4% | |
| 50 years | 92 | 21.1% | |
| Degree | High School Graduates or Less | 27 | 6.2% |
| College Students | 12 | 2.8% | |
| College Graduates | 323 | 74.3% | |
| Graduate School Students | 6 | 1.4% | |
| Graduate School Graduates | 67 | 15.4% | |
| Company Size | Large Enterprise | 125 | 28.7% |
| Larger Medium-Sized Enterprise | 111 | 25.5% | |
| SME (Small and Medium-sized Enterprise) | 175 | 40.2% | |
| Research Institute | 7 | 1.6% | |
| Educational Institute | 8 | 1.8% | |
| Other Places | 9 | 2.1% | |
| Job Position | Intern (Contract Worker) | 6 | 1.4% |
| Staff | 112 | 25.7% | |
| Assistant Manager | 94 | 21.6% | |
| Manager | 91 | 20.9% | |
| Deputy General Manager | 51 | 11.7% | |
| General Manager | 54 | 12.4% | |
| Executives | 27 | 6.2% | |
| Technical Field | Manufacturing Industry (Weaving, Process Manufacturing, etc.) | 129 | 29.7% |
| Waterworks Industry | 9 | 2.1% | |
| Construction Industry | 21 | 4.8% | |
| Wholesale and Retail | 30 | 6.9% | |
| Information Service Industry | 28 | 6.4% | |
| Financial business and Industry | 20 | 4.6% | |
| science, or technical service industry | 108 | 24.8% | |
| Business supporting Service Industry | 21 | 4.8% | |
| Public Administration Service Industry | 31 | 7.1% | |
| Other Field | 38 | 8.7% | |
| Total (N) | 435 | ||
| Classification | Factor 1 | Factor 2 | Factor 3 | Factor 4 | Factor 5 | Factor 6 | Factor 7 | |
|---|---|---|---|---|---|---|---|---|
| Style (SY) | SY1 | 0.812 | 0.178 | 0.279 | 0.143 | 0.086 | 0.073 | 0.135 |
| SY2 | 0.810 | 0.158 | 0.185 | 0.199 | 0.111 | 0.162 | 0.115 | |
| SY4 | 0.692 | 0.111 | 0.196 | 0.158 | 0.355 | 0.116 | 0.270 | |
| SY3 | 0.646 | 0.266 | 0.245 | 0.193 | 0.322 | 0.176 | 0.095 | |
| Structure (SU) | SU3 | 0.158 | 0.810 | 0.161 | 0.133 | 0.218 | 0.174 | 0.196 |
| SU2 | 0.195 | 0.793 | 0.233 | 0.135 | 0.235 | 0.148 | 0.109 | |
| SU4 | 0.225 | 0.755 | 0.239 | 0.151 | 0.185 | 0.177 | 0.180 | |
| Strategy (SG) | SG2 | 0.371 | 0.201 | 0.748 | 0.217 | 0.144 | 0.018 | 0.083 |
| SG3 | 0.220 | 0.264 | 0.703 | 0.278 | 0.197 | 0.249 | 0.150 | |
| SG4 | 0.312 | 0.304 | 0.650 | 0.132 | 0.215 | 0.205 | 0.152 | |
| SG1 | 0.194 | 0.179 | 0.648 | 0.360 | 0.213 | 0.140 | 0.248 | |
| Shared Value (SV) | SV1 | 0.074 | 0.056 | 0.129 | 0.794 | 0.201 | 0.224 | 0.148 |
| SV2 | 0.241 | 0.168 | 0.308 | 0.749 | 0.052 | 0.070 | −0.015 | |
| SV3 | 0.300 | 0.204 | 0.213 | 0.671 | −0.010 | 0.096 | 0.329 | |
| Skills (SK) | SK4 | 0.171 | 0.190 | 0.172 | 0.173 | 0.782 | 0.120 | 0.217 |
| SK2 | 0.337 | 0.415 | 0.214 | 0.019 | 0.637 | 0.092 | −0.030 | |
| SK3 | 0.245 | 0.401 | 0.254 | 0.102 | 0.612 | 0.133 | 0.243 | |
| Systems (SM) | SM3 | 0.230 | 0.149 | 0.116 | 0.180 | 0.070 | 0.859 | 0.098 |
| SM1 | 0.088 | 0.466 | 0.212 | 0.159 | 0.197 | 0.598 | 0.283 | |
| SM2 | 0.104 | 0.406 | 0.259 | 0.215 | 0.232 | 0.542 | 0.403 | |
| Staff (SF) | SF1 | 0.254 | 0.289 | 0.189 | 0.195 | 0.197 | 0.223 | 0.712 |
| SF2 | 0.330 | 0.262 | 0.248 | 0.239 | 0.239 | 0.230 | 0.612 | |
| Variable | AVE | CR | C-alpha | SV | SG | SU | SM | SF | SY | SK | TP |
|---|---|---|---|---|---|---|---|---|---|---|---|
| SV | 0.71 | 0.88 | 0.79 | 0.84 | |||||||
| SG | 0.75 | 0.92 | 0.89 | 0.66 | 0.87 | ||||||
| SU | 0.83 | 0.94 | 0.90 | 0.47 | 0.65 | 0.91 | |||||
| SM | 0.76 | 0.91 | 0.85 | 0.55 | 0.63 | 0.69 | 0.87 | ||||
| SF | 0.85 | 0.92 | 0.83 | 0.59 | 0.66 | 0.64 | 0.70 | 0.92 | |||
| SY | 0.76 | 0.93 | 0.89 | 0.56 | 0.70 | 0.57 | 0.54 | 0.65 | 0.87 | ||
| SK | 0.74 | 0.90 | 0.83 | 0.44 | 0.65 | 0.70 | 0.60 | 0.64 | 0.65 | 0.86 | |
| TP | 0.71 | 0.88 | 0.80 | 0.61 | 0.60 | 0.51 | 0.51 | 0.61 | 0.52 | 0.50 | 0.84 |
| Inputs: SV, SG, SU, SM, SF, SY, SK Output: TP | ||||
|---|---|---|---|---|
| Neural Network | Training (90%) | Testing (10%) | ||
| SSE | RMSE | SSE | RMSE | |
| ANN1 | 3.613 | 0.096 | 0.245 | 0.079 |
| ANN2 | 3.529 | 0.095 | 0.323 | 0.086 |
| ANN3 | 3.344 | 0.094 | 0.498 | 0.094 |
| ANN4 | 3.431 | 0.093 | 0.304 | 0.093 |
| ANN5 | 3.390 | 0.094 | 0.385 | 0.085 |
| ANN6 | 3.649 | 0.097 | 0.324 | 0.085 |
| ANN7 | 3.545 | 0.095 | 0.352 | 0.089 |
| ANN8 | 3.525 | 0.096 | 0.281 | 0.076 |
| ANN9 | 3.690 | 0.097 | 0.210 | 0.070 |
| ANN10 | 3.630 | 0.096 | 0.334 | 0.095 |
| Mean | 0.095 | Mean | 0.085 | |
| Classification | All | Group A (LE, LME) | Group B (SME) | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Variable | ARI | NRI (%) | Ranking | ARI | NRI (%) | Ranking | ARI | NRI (%) | Ranking |
| SV | 0.337 | 100.0% | 1 | 0.297 | 100.0% | 1 | 0.137 | 55.5% | 4 |
| SG | 0.196 | 58.1% | 3 | 0.158 | 53.3% | 4 | 0.176 | 71.4% | 2 |
| SU | 0.113 | 33.5% | 4 | 0.049 | 16.6% | 6 | 0.164 | 66.5% | 3 |
| SM | 0.110 | 32.5% | 5 | 0.030 | 10.1% | 7 | 0.100 | 40.3% | 7 |
| SF | 0.281 | 83.3% | 2 | 0.227 | 76.3% | 2 | 0.247 | 100.0% | 1 |
| SY | 0.052 | 15.3% | 6 | 0.063 | 21.1% | 5 | 0.126 | 51.2% | 5 |
| SK | 0.047 | 14.0% | 7 | 0.175 | 59.0% | 3 | 0.113 | 45.6% | 6 |
| Path | Path Coefficient | Finding | PLS-SEM Ranking | Normalized Relative Importance (%) | ANN Ranking | Matched | |
|---|---|---|---|---|---|---|---|
| H1 | SV → TP | 0.308 | Positive | 1 | 100.0% | 1 | O |
| H2 | SG → TP | 0.147 | Positive | 3 | 58.1% | 3 | O |
| H3 | SU → TP | 0.066 | Negative | 4 | 33.5% | 4 | O |
| H4 | SM → TP | −0.034 | Negative | 6 | 32.5% | 5 | X |
| H5 | SF → TP | 0.270 | Positive | 2 | 83.3% | 2 | O |
| H6 | SY → TP | −0.001 | Negative | 7 | 15.3% | 6 | X |
| H7 | SK → TP | 0.074 | Negative | 5 | 14.0% | 7 | X |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, H.; Yoo, Y.; Lee, H. 7S Model for Technology Protection of Organizations. Sustainability 2021, 13, 7020. https://doi.org/10.3390/su13137020
Park H, Yoo Y, Lee H. 7S Model for Technology Protection of Organizations. Sustainability. 2021; 13(13):7020. https://doi.org/10.3390/su13137020
Chicago/Turabian StylePark, Hyunae, Youngcheon Yoo, and Hwansoo Lee. 2021. "7S Model for Technology Protection of Organizations" Sustainability 13, no. 13: 7020. https://doi.org/10.3390/su13137020
APA StylePark, H., Yoo, Y., & Lee, H. (2021). 7S Model for Technology Protection of Organizations. Sustainability, 13(13), 7020. https://doi.org/10.3390/su13137020







