A Trust-Based Model for the Adoption of Smart City Technologies in Australian Regional Cities
Abstract
1. Introduction
2. Literature Review
2.1. Role of Trust in Technology Adoption
2.2. Technology Adoption Models
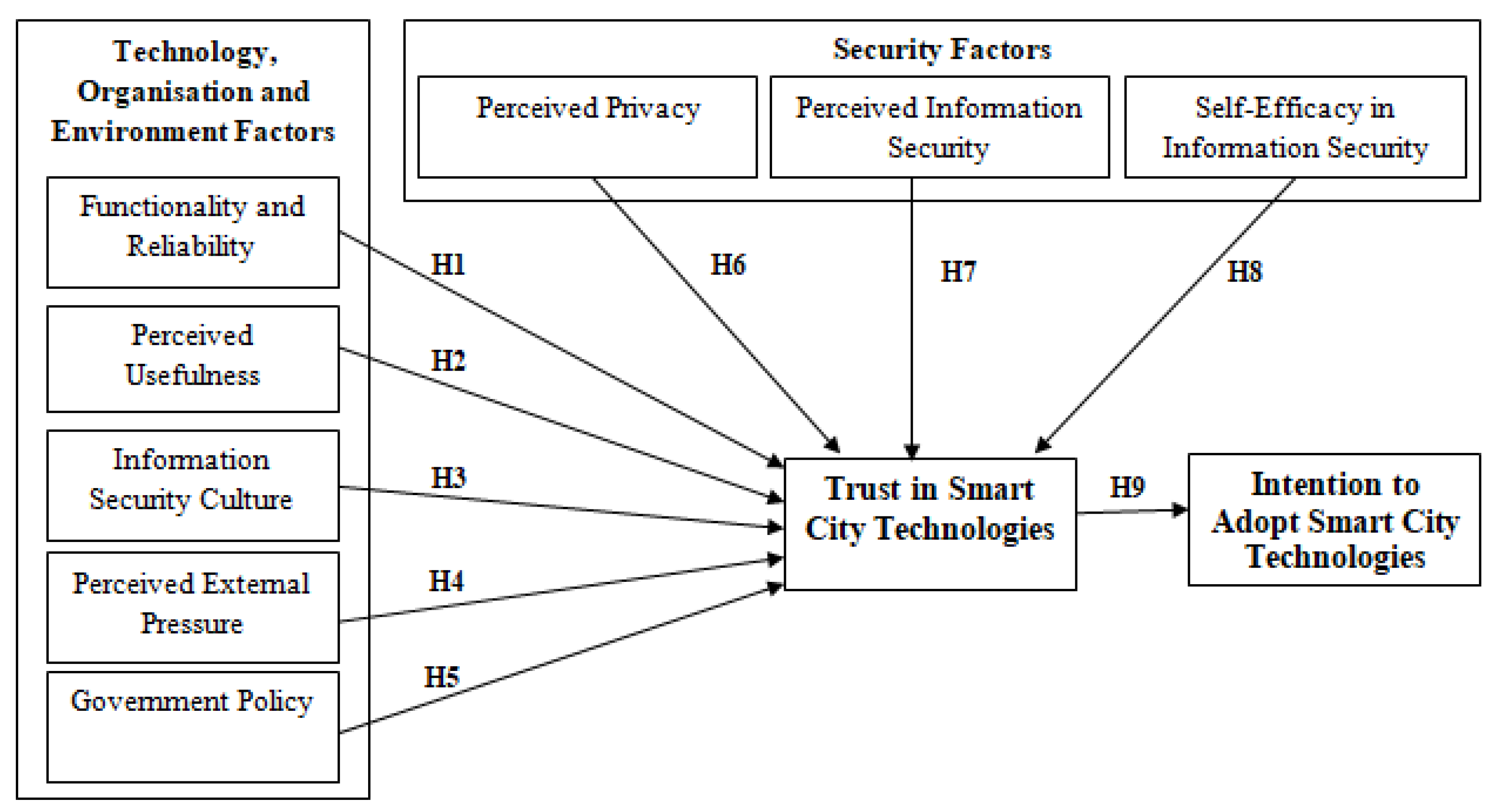
3. A Trust-Based Model
3.1. Technology-Related Factors
3.1.1. Functionality and Reliability
3.1.2. Perceived Usefulness
3.2. Organization Related Factors
Information Security Culture
3.3. Environment Related Factors
3.3.1. Pressure from External Partners
3.3.2. Government Policy
3.4. Security-Related Factors
3.4.1. Perceived Privacy
3.4.2. Perceived Information Security
3.4.3. Self-Efficacy in Information Security
3.5. Trust in Smart City Technologies
4. Research Design
Questionnaire Development
5. Data Analysis
5.1. Sample Demographics
5.2. Structural Equation Modeling
5.3. Instrument Validation
5.4. Structural Model Assessment
Assessment of R2, Q2 and f2
5.5. Hypotheses Evaluation
6. Results and Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Conflicts of Interest
References
- Braun, T.; Fung, B.C.; Iqbal, F.; Shah, B. Security and privacy challenges in smart cities. Sustain. Cities Soc. 2018, 39, 499–507. [Google Scholar] [CrossRef]
- Dewi, M.A.; Hidayanto, A.N.; Purwandari, B.; Kosandi, M.; Budi, N.A. Smart city readiness model based on technology-organization-environment (toe) framework and its effect on adoption decision. In Proceedings of the Pacific Asia Conference Information System, Yokohama, Japan, 26–30 June 2018. [Google Scholar]
- AlKalbani, A.; Deng, H.; Kam, B. Organisational security culture and information security compliance for E-government development: The moderating effect of social pressure. In Proceedings of the Pacific Asia Conference on Information Systems, Singapore, 5–9 July 2015. [Google Scholar]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An integrative model of organizational trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Gefen, D.; Karahanna, E.; Straub, D.W. Trust and TAM in online shopping: An integrated model. MIS Q. 2003, 27, 51–90. [Google Scholar] [CrossRef]
- Belanche, D.; Casaló, L.V.; Flavián, C. Integrating trust and personal values into the technology acceptance model: The case of E-government services adoption. Cuad. Econ. Dir. Empresa 2012, 15, 192–204. [Google Scholar] [CrossRef]
- Van Zoonen, L. Privacy concerns in smart cities. Govern. Inf. Q. 2016, 33, 472–480. [Google Scholar] [CrossRef]
- Australian Government. “Smart Cities and Suburbs”, Department of Infrastructure. 2020. Available online: https://www.infrastructure.gov.au/cities/Sustainable-Development-Goal-11.aspx (accessed on 11 November 2020).
- Wibowo, S.; Mubarak, S. Exploring stakeholders perceived risk and trust towards their intention to adopt cloud computing: A theoretical framework. In Proceedings of the Twenty-Third Pacific Asia Conference on Information Systems, Dubai, United Arab Emirates, 22–24 June 2020. [Google Scholar]
- Dahlberg, T.; Mallat, N.; Öörni, A. Trust enhanced technology acceptance model consumer acceptance of mobile payment solutions: Tentative evidence. Stockh. Mobil. Roundtable 2003, 22, 1–19. [Google Scholar]
- Yeh, H. The Effects of successful ICT-based smart city services: From citizens’ perspectives. Govern. Inf. Q. 2017, 34, 556–565. [Google Scholar] [CrossRef]
- Kramer, R.M. The sinister attribution error: Paranoid cognition and collective distrust in organizations. Motiv. Emot. 1994, 18, 199–230. [Google Scholar] [CrossRef]
- Baig, Z.A.; Szewczyk, P.; Valli, C.; Rabadia, P.; Hannay, P.; Chernyshev, M.; Johnstone, M.; Kerai, P.; Ibrahim, A.; Sansurooah, K. Future challenges for smart cities: Cyber-security and digital forensics. Digit. Investig. 2017, 22, 3–13. [Google Scholar] [CrossRef]
- Koller, M. Risk as a determinant of trust. Basic Appl. Soc. Psych. 1988, 9, 265–276. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and privacy in smart city applications: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Lin, Z.; Dong, L. Clarifying trust in social internet of things. IEEE Trans. Knowl. Data Eng. 2018, 30, 234–248. [Google Scholar] [CrossRef]
- Davis, F.D. Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Q. 1989, 13, 319–340. [Google Scholar] [CrossRef]
- Tornatzky, L.G.; Fleischer, M. The Process of Technological Innovation; Lexington Books: Lexington, MA, USA, 1990. [Google Scholar]
- Gangwar, H.; Date, H.; Ramaswamy, R. Understanding determinants of cloud computing adoption using an integrated TAM-TOE model. J. Enterp. Inf. Manag. 2015, 28, 107–130. [Google Scholar] [CrossRef]
- Alhogail, A. Improving IoT technology adoption through improving consumer trust. Technologies 2018, 6, 64. [Google Scholar] [CrossRef]
- Saif Almuraqab, N.; Jasimuddin, S. Factors that influence end-users’ adoption of smart government services in the UAE: A conceptual framework. Electron. J. Inf. Syst. Eval. 2017, 20, 11–23. [Google Scholar]
- Ratten, V. Behavioral intentions to adopt technological innovations: The role of trust, innovation and performance. Int. J. Enterp. Inf. Syst. 2014, 10, 1–12. [Google Scholar] [CrossRef][Green Version]
- Lippert, S.K.; Swiercz, P.M. Human resource information systems (HRIS) and technology trust. J. Inf. Sci. 2005, 31, 340–353. [Google Scholar] [CrossRef]
- Li, C.; Dai, Z.; Liu, X.; Sun, W. Evaluation system: Evaluation of smart city shareable framework and its applications in china. Sustainability 2020, 12, 2957. [Google Scholar] [CrossRef]
- Goldfinch, S.; Gauld, R.; Herbison, P. The participation divide? political participation, trust in government, and E-government in Australia and New Zealand. Aust. J. Publ. Admin. 2009, 68, 333–350. [Google Scholar] [CrossRef]
- Rhee, H.S.; Kim, C.; Ryu, Y.U. Self-efficacy in information security: Its influence on end users’ information security practice behavior. Comput. Secur. 2009, 28, 816–826. [Google Scholar] [CrossRef]
- Teo, T.S.; Ranganathan, C.; Dhaliwal, J. Key dimensions of inhibitors for the deployment commerce. IEEE Trans. Eng. Manag. 2006, 53, 395–411. [Google Scholar] [CrossRef]
- Von Solms, B. Information security—The third wave? Comput. Secur. 2000, 19, 615–620. [Google Scholar]
- Bulgurcu, B.; Cavusoglu, H.; Benbasat, I. Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Q. 2010, 34, 523–548. [Google Scholar] [CrossRef]
- Wu, Y.C.; Sun, R.; Wu, Y.J. Smart city development in Taiwan: From the perspective of the information security policy. Sustainability 2020, 12, 2916. [Google Scholar] [CrossRef]
- Grandhi, L.S.; Grandhi, S.; Wibowo, S. A security-UTAUT framework for evaluating key security determinants in smart city adoption by the Australian city councils. In Proceedings of the 21st ACIS International Winter Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, Ho Chi Minh City, Vietnam, 28–30 January 2021; pp. 17–22. [Google Scholar]
- Chang, Y.; Wong, S.F.; Libaque-Saenz, C.F.; Lee, H. The role of privacy policy on consumers’ perceived privacy. Gov. Inf. Q. 2018, 35, 445–449. [Google Scholar] [CrossRef]
- Chellappa, R.K.; Pavlou, P.A. Perceived information security, financial liability and consumer trust in electronic commerce transactions. Logist. Inf. Manag. 2002, 15, 358–368. [Google Scholar] [CrossRef]
- Sarabdeen, J.; Rodrigues, G.; Balasubramanian, S. E-government users’ privacy and security concerns and availability of laws in Dubai. Int. Rev. Law Comput. Technol. 2014, 28, 261–276. [Google Scholar] [CrossRef]
- Nikitas, A.; Michalakopoulou, K.; Njoya, E.T.; Karampatzakis, D. Artificial intelligence, transport and the smart city: Definitions and dimensions of a new mobility Era. Sustainability 2020, 12, 2789. [Google Scholar] [CrossRef]
- Tolbert, C.J.; Mossberger, K. The effects of E-government on trust and confidence in government. Pub. Admin. Rev. 2006, 66, 354–369. [Google Scholar] [CrossRef]
- Alharbi, N.; Papadaki, M.; Dowland, P. The impact of security and its antecedents in behaviour intention of using E-government services. Behav. Inf. Technol. 2017, 36, 620–636. [Google Scholar] [CrossRef]
- Neupane, C.; Wibowo, S.; Grandhi, S.; Hossain, R. A Trust based smart city adoption model for the Australian regional cities: A conceptual framework. In Proceedings of the ACIS, Perth, Australia, 9–11 December 2019. [Google Scholar]
- Hair, J.F.; Sarstedt, M.; Hopkins, L.; Kuppelwieser, V.G. Partial least squares structural equation modeling (PLS-SEM). Eur. Bus. Rev. 2014, 26, 106–121. [Google Scholar] [CrossRef]
- Lew, Y.K.; Sinkovics, R.R. Crossing borders and industry sectors: Behavioral governance in strategic alliances and product innovation for competitive advantage. Long Range Plan. 2012, 46, 13–38. [Google Scholar] [CrossRef]
- Lewis, B.R.; Templeton, G.F.; Byrd, T.A. A methodology for construct development in MIS research. Eur. J. Inf. Syst. 2005, 14, 388–400. [Google Scholar] [CrossRef]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Henseler, J.; Ringle, C.M.; Sarstedt, M. A new criterion for assessing discriminant validity in variance-based structural equation modeling. J. Acad. Mark. Sci. 2015, 43, 115–135. [Google Scholar] [CrossRef]
- Chin, W.W. The partial least squares approach to structural equation modeling. Mod. Methods Bus. Res. 1998, 29, 295–336. [Google Scholar]
- Peng, D.X.; Lai, F. Using partial least squares in operations management research: A practical guideline and summary of past research. J. Oper. Manag. 2012, 30, 467–480. [Google Scholar] [CrossRef]
- Schmidheiny, K. Clustering in the linear model. Short Guides Microeconometrics-Univ. Basel 2012, 1, 7–11. [Google Scholar]
- Knack, S.; Zak, P.K. Building trust: Public policy, interpersonal trust, and economic development. Supreme Court. Econ. Rev. 2003, 10, 91–107. [Google Scholar] [CrossRef]

| Research Context | Strengths | Limitations | |
|---|---|---|---|
| Role of security and trust in technology adoption | Presented several issues relating to trust and security in smart cities. | Lack of discussion on specific issues | Braun et al. [1] |
| Influence of technology trust towards implementation of HR information system | Framework details determinants of technology trust using technology, organization and user dimensions. | Lack of discussion on environment and security dimensions and their influence on trust | Lippert and Swiercz [23] |
| Role of trust in adopting mobile payment solutions | Introduced trust factor in original TAM model to develop trust enhanced TAM model. | Unable to establish the validity and reliability of the proposed model | Dahlberg et al. [10] |
| Role of trust, innovation and performance in technology adoption | Compared two (USA and China) different cultural contexts to understand the behavioral attitude towards technological innovations. | Self-reported data were collected that may mean there is a respondent bias | Ratten [22] |
| Determinants of acceptance of ICT-based smart city services and their effect on the quality of life | Presented a user acceptance model for the adoption of ICT-based smart city services using the diffusion of innovation theory. Trust is found to have a significant influence on user acceptance of smart city services. | Control variables (gender, education and age can have different influences on different smart city service domains) | Yeh [11] |
| IoT adoption by improving consumer trust | Considered security-related factors as determinants of trust towards IoT adoption. | Environmental and organisational domains are not considered as determinants of trust | AlHogail [20] |
| Dimension | Factors | Indicators |
|---|---|---|
| Technology | Perceived Usefulness | Will not create harassment [38] Services are convenient [38] Services give greater control [17] |
| Functionality and Reliability | Technical capacity to ensure data will not be intercepted by hackers [37] Sufficient technical capacity to ensure data cannot be modified by a third party [37] | |
| Organisation | Information Security Culture | Familiarity with the information security policies of the organization [34] Individual’s role for escalating information security incidents [29] Awareness of the information security responsibilities [3] |
| Environment | Perceived External Pressure | Smart city services are an effective way to interact with the government [30] The use of smart services will improve the efficiency of obtaining services [26] |
| Government Policy | Aware of the potential damage to the information system by hacker threats [26] The use of smart services will improve the efficiency of obtaining services [26] | |
| Security | Perceived Privacy | There will be no loss of data from an agency behaving opportunistically in smart city services [30] Feel safe when I send personal information [22] Feel confident about privacy with regards to the smart city services [34] |
| Perceived Information Security | Smart services provided are reliable [34] Concern for the privacy of its users [34] The transaction is secure while using the smart services [37] Information I provide to the council will not be manipulated [37] | |
| Self-Efficacy in Information Security | Confidence in handling virus-infected files [26] Confidence in understanding terms relating to information security [26] Confidence in learning the method to protect information and information system [26] Confidence in managing files in computer [26] Confidence in setting the Web browser to different security levels [26] Confidence in using different programs to protect my information and information system [26] Confidence in updating security patches to the operating system [26] Confidence in following the ‘user guide’ when help is needed to protect my information [26] | |
| Trust | Councils and other relevant authorities can be trusted to carry out online transactions faithfully [38] Legal and technological structures adequately protect from problems on the internet [38] Smart city services would provide a valuable service for residents in our city council [38] The responsible of taking full responsibility for any type of insecurity [38] | |
| Intention to Adopt | Confidence in the technology used in smart city’s services [38] Not concerned that the information submitted online could be misused [37] Believe that smart city services are safe to interact with for financial purposes [15] |
| Functionality and reliability | Perceived privacy | ||
| T_FR_1 | Technical capacity to ensure data will not be intercepted by hackers | S_PP_1 | There will be no loss of data from an agency behaving opportunistically |
| T_FR_2 | Sufficient technical capacity to ensure data cannot be modified by a third party | S_PP_2 | Feel safe when I send personal information to councils |
| Perceived Usefulness | S_PP_3 | Feel confident about privacy with regards to the smart city services | |
| T_PU_1 | Will not create harassment | Self-Efficacy in Information Security | |
| T_PU_2 | Services are convenient | S_SEIS_1 | Confidence in handling virus-infected files |
| T_PU_3 | Services give greater control | ||
| Information Security Culture | S_SEIS_2 | Confidence in understanding terms relating to information security | |
| O_ISC_1 | Familiarity with the information security policies of the organisation | S_SEIS_3 | Confidence in learning the method to protect information and information system |
| O_ISC_2 | Individual’s role for escalating information security incidents | S_SEIS_4 | Confidence in managing files in a computer |
| O_ISC_3 | Awareness of the information security responsibilities | S_SEIS_5 | Confidence in setting the Web browser to different security levels |
| Pressure from External Partners | S_SEIS_6 | Confidence in using different programs to protect my information | |
| E_PEP_1 | An effective way to interact with government | S_SEIS_7 | Confidence in updating security patches to the operating system |
| E_PEP_1 | will improve the efficiency of obtaining services | S_SEIS_8 | Confidence in following the ‘user guide’ when help is needed to protect information |
| Government Policy | Trust | ||
| E_GP_1 | Aware of the potential damage to the information system by hacker threats | TRU_1 | Smart city services would provide a valuable service for residents |
| E_GP_2 | The use of smart services will improve the efficiency of obtaining services | TRU_1 | Councils can be trusted to carry out online transactions faithfully |
| Perceived Information Security | TRU_1 | Legal and technological structures protect from problems on internet | |
| S_PS_1 | Smart services provided are reliable | TRU_1 | The responsible firm providing services will take full responsibility for insecurity |
| S_PS_2 | Council shows concern for the privacy of users | Intention to Adopt | |
| S_PS_3 | The transaction is secure while using the smart services | INTENT_1 | Confidence in the technology used in smart city’s services |
| S_PS_4 | Information I provide to council will not be manipulated | INTENT_1 | Not concerned that the information submitted online could be misused |
| INTENT_1 | Believe that smart city services are safe to interact with for financial purposes | ||
| Dimension | Factors | AVE | CR | α |
|---|---|---|---|---|
| Technology | Perceived usefulness (T_PU) | 0.584 | 0.808 | 0.64 |
| Functionality and reliability (T_FR) | 0.804 | 0.891 | 0.76 | |
| Organisation | Information security culture (O_ISC) | 0.688 | 0.868 | 0.77 |
| Environment | Government policy (E_GP) | 0.699 | 0.822 | 0.57 |
| Pressure from external partners (E_PEP) | 0.754 | 0.860 | 0.67 | |
| Security | Self-efficacy in information security (S_SEIS) | 0.535 | 0.898 | 0.87 |
| Perceived privacy (S_PP) | 0.522 | 0.758 | 0.54 | |
| Perceived security (S_PS) | 0.506 | 0.803 | 0.68 | |
| Trust | Trust (TRU) | 0.558 | 0.834 | 0.73 |
| Adoption Intention | Intention to adopt (INT) | 0.546 | 0.779 | 0.60 |
| E_GP | E_PEP | INTENT | O_ISC | S_PP | S_PS | S_SEIS | TRUST | T_FR | |
|---|---|---|---|---|---|---|---|---|---|
| E_PEP | 0.35 | ||||||||
| INTENT | 0.35 | 0.55 | |||||||
| O_ISC | 0.88 | 0.64 | 0.61 | ||||||
| S_PP | 0.48 | 0.49 | 0.9 | 0.43 | |||||
| S_PS | 0.47 | 0.53 | 0.74 | 0.65 | 0.75 | ||||
| S_SEIS | 0.73 | 0.51 | 0.52 | 0.78 | 0.51 | 0.67 | |||
| TRUST | 0.58 | 0.81 | 0.74 | 0.74 | 0.68 | 0.81 | 0.62 | ||
| T_FR | 0.40 | 0.52 | 0.77 | 0.61 | 0.83 | 0.74 | 0.56 | 0.62 | |
| T_PU | 0.31 | 0.89 | 0.84 | 0.53 | 0.68 | 0.54 | 0.38 | 0.80 | 0.65 |
| R2 | SSO | SSE | Q2 | SD | T-Statistics | p-Values | |
|---|---|---|---|---|---|---|---|
| INTENT | 0.279 | 675 | 580.41 | 0.14 | 0.056 | 4.989 | 0.00 |
| TRUST | 0.582 | 900 | 636.32 | 0.293 | 0.046 | 12.739 | 0.00 |
| Factors Influence | f2 Values | Sample Mean (M) | Std. Dev. |
|---|---|---|---|
| E_GP -> TRUST | 0.013 | 0.019 | 0.02 |
| E_PEP -> TRUST | 0.057 | 0.063 | 0.04 |
| O_ISC -> TRUST | 0.024 | 0.033 | 0.03 |
| S_PP -> TRUST | 0.018 | 0.025 | 0.02 |
| S_PS -> TRUST | 0.084 | 0.093 | 0.05 |
| S_SEIS -> TRUST | 0.004 | 0.011 | 0.01 |
| TRUST -> INTENT | 0.387 | 0.408 | 0.11 |
| T_FR -> TRUST | 0.00 | 0.007 | 0.01 |
| T_PU -> TRUST | 0.067 | 0.077 | 0.04 |
| Hypothesis | β | t-Value | p-Value | Remarks |
|---|---|---|---|---|
| H1: Functionality and reliability → Trust | −0.02 | 0.292 | 0.77 | Rejected |
| H2: Perceived usefulness → Trust | 0.224 | 3.65 | 0.000 | Supported |
| H3: Information security culture → Trust | 0.16 | 1.8 | 0.072 | Rejected |
| H4: Perceived external pressure → Trust | 0.20 | 2.99 | 0.003 | Supported |
| H5: Government policy → Trust | 0.093 | 1.5 | 0.134 | Rejected |
| H6: Perceived privacy → Trust | 0.117 | 1.8 | 0.07 | Rejected |
| H7: Perceived information security → Trust | 0.25 | 3.88 | 0.000 | Supported |
| H8: Self-efficacy in information security → Trust | 0.529 | 0.72 | 0.47 | Rejected |
| H9: Trust in smart city technologies → Adoption intention | 0.528 | 9.69 | 0.000 | Supported |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Neupane, C.; Wibowo, S.; Grandhi, S.; Deng, H. A Trust-Based Model for the Adoption of Smart City Technologies in Australian Regional Cities. Sustainability 2021, 13, 9316. https://doi.org/10.3390/su13169316
Neupane C, Wibowo S, Grandhi S, Deng H. A Trust-Based Model for the Adoption of Smart City Technologies in Australian Regional Cities. Sustainability. 2021; 13(16):9316. https://doi.org/10.3390/su13169316
Chicago/Turabian StyleNeupane, Chiranjivi, Santoso Wibowo, Srimannarayana Grandhi, and Hepu Deng. 2021. "A Trust-Based Model for the Adoption of Smart City Technologies in Australian Regional Cities" Sustainability 13, no. 16: 9316. https://doi.org/10.3390/su13169316
APA StyleNeupane, C., Wibowo, S., Grandhi, S., & Deng, H. (2021). A Trust-Based Model for the Adoption of Smart City Technologies in Australian Regional Cities. Sustainability, 13(16), 9316. https://doi.org/10.3390/su13169316







