Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions
Abstract
:1. Introduction
1.1. Motivation of Study
1.2. Research Problems and Contribution
- We provide adequate knowledge about the underlying MIoT ecosystem and highlight its architecture, the key layers that the architecture itself is made out of, and the devices and technologies used in each layer.
- We provide a discussion about the security and privacy requirements of the MIoT and highlight the latest trends to provide a better understanding of what is happening now.
- We classify security and privacy attacks in terms of the MIoT layered architecture and suggest countermeasures and solutions to prevent these attacks in terms of the layered architecture.
- We provide a brief comparison of the existing literature, highlighting its key contributions and limitations to justify our work.
- In terms of the security and privacy of the MIoT, we highlight key challenges based on the layered architecture and also provide future directions as well.
1.3. Outline of Study
2. The Architecture of MIoT
- Perception layer.
- Network layer.
- Application layer.
2.1. Classification of Devices Based on the Architecture
2.1.1. Devices Employed in the Perception Layer
- Patient monitoring devices.
- Remote wellness and chronic disease monitoring devices.
- Real-time location service (RTL) devices.
- Facility monitoring devices.
2.1.2. Devices Employed in the Network Layer
- Wired/Wireless media: It is evident that MIoT devices often use wired or wireless networks to connect to the end-user or the gateway [5,14]. In addition, MIoT devices can be connected to Wireless Sensor Networks (WSNs), which use a traditional Wi-Fi network or low-powered wireless personal area network (6LoWPAN). On the other hand, most devices that use wired connections are stationary (e.g., medical imaging devices) [26].
- Radio communication media: Some low-powered MIoT mobile devices use radio communication media such as Bluetooth, RFID, Bluetooth Low Energy (BLE), NFC, and all sorts of cellular communication networks to connect with each node and with end-users and the gateways. Many of the wearable medical IoT devices use BLE for short-range communication. Cellular networks (e.g., 2G, 3G, 4G, 5G) are used for long-range communication [14,25].
2.1.3. Devices Employed in the Application Layer
3. Security and Privacy Requirement of MIoT
- Access control: There should be an underlying access control mechanism for authenticated users [17].
- Privacy of patient information: Medical data can be apportioned into two categories, general records and sensitive data [17]. Sensitive data can also be called patient privacy information and includes details about infectious diseases, sexual orientation, mental status, drug addiction, and identity information. Because of the criticality and the sensitivity of this data, we need to ensure that these sensitive data are not exposed to unauthorized users or that unauthorized users do not have the capacity to understand the meaning of the data, even if the data are captured and intercepted [9,28,32,45].
- The MIoT is an emerging technological paradigm where adequate research has not been conducted regarding security, where device manufacturers themselves rush to provide MIoT solutions without security in mind.
- The fact that highly confidential and sensitive data are always being transmitted across the MIoT ecosystem makes it a sound target for attackers.
- In order to control, monitor, and operate, MIoT solutions encompass different applications. There is huge concern about the implementation risks in this application layer, such as breaches of access control and session hijacking as well as the general security functionalities of the applications.
- A large fraction of computational resources are consumed by certain security computations such as the execution of encryption algorithms. Due to the limited computing capacities (e.g., limited computing power and memory), many of these MIoT devices lack integrated encryption mechanisms, as execution cannot be completed in those resource-constrained environments. This lack of strong encryption mechanisms across devices makes devices susceptible to malicious attacks.
- The amount of financial profit that can be gained by exploiting the devices and data make these data a sound target for attackers by way of blackmailing someone, releasing the exploited data to the public, or selling it on the dark web [11].
- Personally identifiable information (PII) and personal health information (PHI), which can be contained within MIoT data, would make the entire MIoT ecosystem a sound target that could be exploited for profit [4].
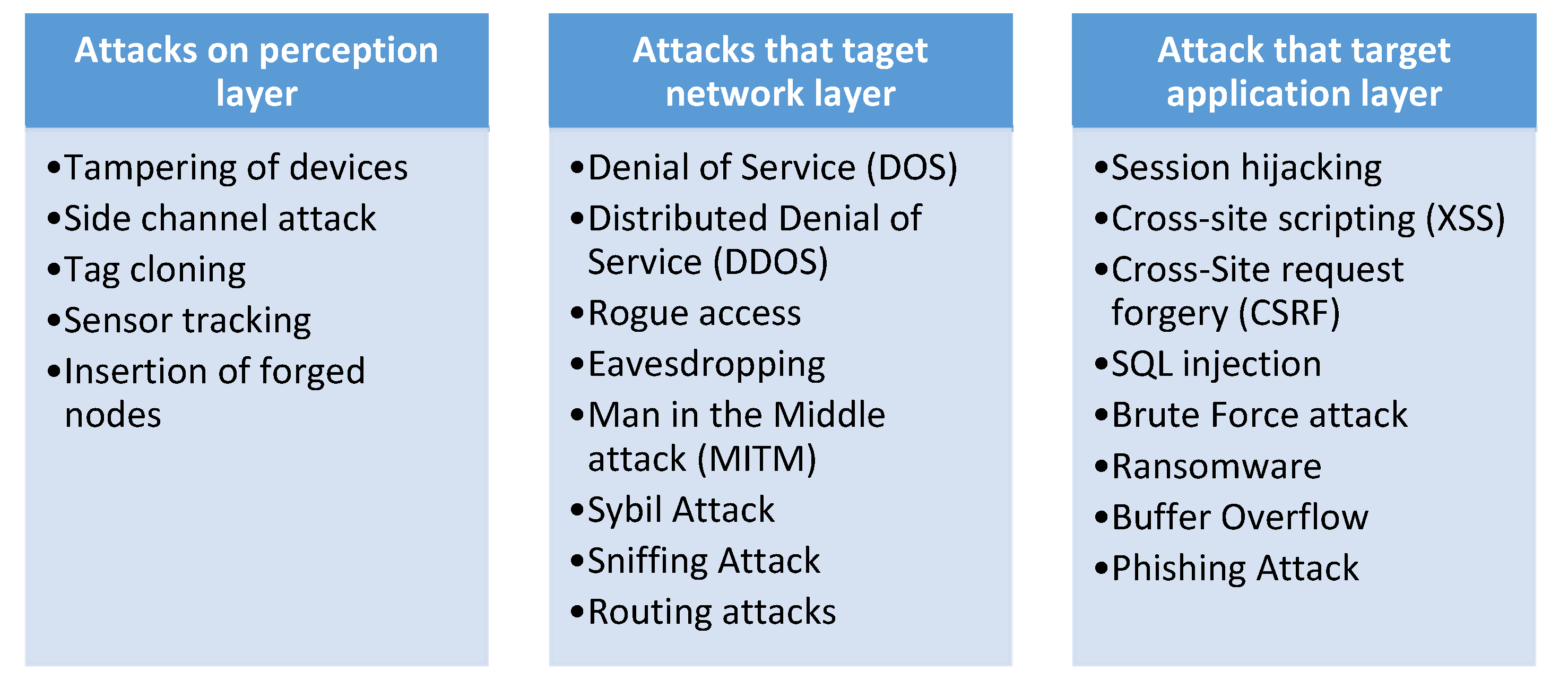
4. Attack Classification Based on the Architecture
4.1. Attacks on Perception Layer
- Tampering of devices
- Side channel attack
- Tag cloning
- Sensor tracking
- Insertion of forged nodes
4.2. Attacks on Network Layer
- Denial of Service (DOS)
- Rogue access
- Eavesdropping
- Man in the Middle attack (MITM)
- Replay attack
- Sybil attack
- Sniffing attack
- Routing attacks
4.3. Attacks on Application Layer
- Session hijacking
- Cross-Site Scripting (XSS)
- Cross-Site Request Forgery (CSRF)
- SQL injection
- Brute force attack
- Ransomware
- Buffer Overflow
- Phishing attack
5. Related Work and Contributions
6. Countermeasures and Solutions
- Access control
- Data encryption
- Data auditing
- IoT healthcare policies
- Data search
- Data minimization
- Data anonymization
- Inventory devices
- Network segmentation
- Follow the best practices
- Wider awareness
- Continuous monitoring and reporting
7. Challenges and Future Directions
- Insecure network
- Limitation of resources
- Heterogeneous devices
- Zero-day vulnerabilities and security patches
- High Mobility
- Dynamic network topology
- Trust management
- Social Engineering
Future Directions
- In recent times, the emergence of AI has made a huge turning point in the IoT healthcare market and is helping to the growth of the MIoT market. Hence, it is evident that the significant use of AI-powered solutions will assist in real-time security monitoring [77,85]. Nevertheless, it is noted that MIoT security solutions rely on 03 aspects to successfully mitigate risks, such as the discovery of risks, network monitoring, and incident management, where AI would be an integral part of these solutions to provide an in-depth overview of threats and incidents and to provide the ability to respond to attacks in a timely manner while performing real-time monitoring.
- Since most medical IoT devices do not have enough computational power and memory on the devices themselves, for further data processing and storage, powerful and highly scalable computing and large storage infrastructure are needed [17,86,87,88,89]. As a result of that, due to high scalability and rapid elasticity, many healthcare organizations prefer to store their data and deploy their application servers in a stable cloud environment. As such, focus will be moved towards securing cloud environments where processing and storage happen at the same time in the same place [5,94,95].
- Security standards and regulations will be tighter to make sure that there are fewer gaps in the healthcare organizational security [96].
- The healthcare organizations will invest more and more in improving the organization’s information security strategy in order to maintain their organizational image and to prevent any adverse security incidents beforehand [96].
- Traditional network routers provide some sorts of security capabilities such as firewall, password protection, and blocking unnecessary services, whereas modern network routers will continue to become more secure and smarter, which is a better way to provide added network security at the network entry points [96,97,98,99].
- Biometric identity management is highly valued in healthcare settings, and its use is increasing. Along with multi-factor authentication, this is presently being investigated by more advanced healthcare organizations and pharmaceutical firms in order to improve their organizational security. Biometric applications in healthcare organizations is expected to expand in the next three to five years, and this would mostly be used as a method to add an extra security layer, govern identity management and access, and provide a more seamless clinical experience to all stakeholders [96,97,98,99].
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Plachkinova, M.; Vo, A.; Alluhaidan, A. Emerging Trends in Smart Home Security, Privacy and Digital Forensics. 2016. Available online: https://aisel.aisnet.org/amcis2016/ITProj/Presentations/23/ (accessed on 20 July 2021).
- Apthorpe, N.; Reisman, D.; Feamster, N. A smart home is no castle: Privacy vulnerabilities of encrypted IoT traffic. Available online: http://datworkshop.org/papers/dat16-final37.pdf (accessed on 20 July 2021).
- Jacobsson, A.; Boldt, M.; Carlsson, B. A risk analysis of a smart home automation system. Future Gener. Comput. Syst. 2016, 56, 719–733. [Google Scholar] [CrossRef] [Green Version]
- Thilakarathne, N.N.; Kagita, M.K.; Gadekallu, D.T.R. The Role of the Internet of Things in Health Care: A Systematic and Comprehensive Study. Int. J. Eng. Manag. Res. 2020, 10, 145–159. [Google Scholar] [CrossRef]
- Thilakarathne, N.N. Security and Privacy Issues in IoT Environment. Int. J. Eng. Manag. Res. 2020, 10, 26–29. [Google Scholar] [CrossRef] [Green Version]
- Alsubaei, F.; Abuhussein, A.; Shiva, S. Security and privacy in the internet of medical things: Taxonomy and risk assessment. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks Workshops (LCN Workshops), Singapore, 9–12 October 2017; pp. 112–120. [Google Scholar] [CrossRef]
- Darwish, S.; Nouretdinov, I.; Wolthusen, S.D. Towards composable threat assessment for medical IoT (MIoT). Procedia Comput. Sci. 2017, 113, 627–632. [Google Scholar] [CrossRef] [Green Version]
- Elhoseny, M.; Ramírez-González, G.; Abu-Elnasr, O.M.; Shawkat, S.A.; Arunkumar, N.; Farouk, A. Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 2018, 6, 20596–20608. [Google Scholar] [CrossRef]
- Tarouco, L.M.R.; Bertholdo, L.M.; Granville, L.Z.; Arbiza, L.M.R.; Carbone, F.; Marotta, M.; De Santanna, J.J.C. Internet of Things in healthcare: Interoperatibility and security issues. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, USA; 2012; pp. 6121–6125. [Google Scholar] [CrossRef]
- Hossain, M.; Islam, S.R.; Ali, F.; Kwak, K.S.; Hasan, R. An internet of things-based health prescription assistant and its security system design. Future Gener. Comput. Syst. 2018, 82, 422–439. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Samuel, O.W.; Wu, W.; Sangaiah, A.K.; Li, G. A joint resource-aware and medical data security framework for wearable healthcare systems. Future Gener. Comput. Syst. 2019, 95, 382–391. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shandilya, V.; Shiva, S. IoMT-SAF: Internet of medical things security assessment framework. Internet Things 2019, 8, 100123. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q.; Ray, S.; Jin, Y. Internet-of-Things security and vulnerabilities: Taxonomy, challenges, and practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- El-hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A survey of internet of things (IoT) Authentication schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [Green Version]
- Asplund, M.; Nadjm-Tehrani, S. Attitudes and perceptions of IoT security in critical societal services. IEEE Access 2016, 4, 2130–2138. [Google Scholar] [CrossRef]
- Kumar, J.S.; Patel, D.R. A survey on internet of things: Security and privacy issues. Int. J. Comput. Appl. 2014, 9, 20–26. [Google Scholar]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and privacy in the medical internet of things: A review. Secur. Commun. Netw. 2018, 2018, doi. [Google Scholar] [CrossRef]
- Kang, J.; Adibi, S. A review of security protocols in mHealth wireless body area networks (WBAN). In Proceedings of the Future Network Systems and Security: First International Conference, FNSS, Paris, France, 11–13 June 2015; Doss, R., Piramuthu, S., Zhou, W., Eds.; Springer: Cham, Switzerland, 2015; pp. 61–83. [Google Scholar]
- AlMotiri, S.H.; Khan, M.A.; Alghamdi, M.A. Mobile health (m-health) system in the context of IoT. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 39–42. [Google Scholar] [CrossRef]
- Azzawi, M.A.; Hassan, R.; Bakar, K.A. A review on Internet of Things (IoT) in healthcare. Int. J. Appl. Eng. Res. 2016, 11, 10216–10221. [Google Scholar]
- Yeh, K.H. A secure IoT-based healthcare system with body sensor networks. IEEE Access 2016, 4, 10288–10299. [Google Scholar] [CrossRef]
- Silva, C.A.; Aquino, G.S.; Melo, S.R.; Egídio, D.J. A fog computing-based architecture for medical records management. Wirel. Commun. Mob. Comput. 2019, 2019, 1968960. [Google Scholar] [CrossRef]
- David, S.; Sagayam, K.M.; Elngar, A.A. Parasitic overview on different key management schemes for protection of Patients Health Records. J. Cybersecur. Inf. Manag. 2021, 6, 96–100. [Google Scholar]
- Kodali, R.K.; Swamy, G.; Lakshmi, B. An implementation of IoT for healthcare. In Proceedings of the 2015 IEEE Recent Advances in Intelligent Computational Systems (RAICS), Kerala, India, 10–12 December 2015; pp. 411–416. [Google Scholar] [CrossRef]
- Rajput, D.S.; Gour, R. An IoT framework for healthcare monitoring systems. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 451. [Google Scholar]
- Maher, O.; Sitnikova, E. A Trustworthy Learning Technique for Securing Industrial Internet of Things Systems. J. Intell. Syst. Internet Things 2021, 5, 33–48. [Google Scholar]
- Dimitrov, D.V. Blockchain applications for healthcare data management. Healthc. Inform. Res. 2019, 25, 51–56. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. BSN-Care: A secure IoT-based modern healthcare system using body sensor network. IEEE Sens. J. 2015, 16, 1368–1376. [Google Scholar] [CrossRef]
- Milovanovic, D.; Bojkovic, Z. Cloud-based IoT healthcare applications: Requirements and recommendations. Int. J. Internet Things Web Serv. 2017, 2, 60–65. [Google Scholar]
- Mahmud, R.; Koch, F.L.; Buyya, R. Cloud-Fog Interoperability in IoT-Enabled Healthcare Solutions. Available online: https://dl.acm.org/doi/10.1145/3154273.3154347 (accessed on 20 July 2021).
- Sebestyen, G.; Hangan, A.; Oniga, S.; Gál, Z. eHealth solutions in the context of Internet of Things. In Proceedings of the 2014 IEEE International Conference on Automation, Quality and Testing, Robotics, Cluj-Napoca, Romania, 22–24 May 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N. Fog computing for Healthcare 4.0 environment: Opportunities and challenges. Comput. Electr. Eng. 2018, 72, 1–13. [Google Scholar] [CrossRef]
- Bui, N.; Zorzi, M. Health Care Applications: A Solution Based on the Internet of Things. Available online: https://dl.acm.org/doi/10.1145/2093698.2093829 (accessed on 20 July 2021).
- Hassanalieragh, M.; Page, A.; Soyata, T.; Sharma, G.; Aktas, M.; Mateos, G.; Andreescu, S. Health monitoring and management using Internet-of-Things (IoT) sensing with cloud-based processing: Opportunities and challenges. In Proceedings of the 2015 IEEE International Conference on Services Computing, New York City, NY, USA, 27 June–2 July 2015; pp. 285–292. [Google Scholar] [CrossRef] [Green Version]
- Joyia, G.J.; Liaqat, R.M.; Farooq, A.; Rehman, S. Internet of Medical Things (IOMT): Applications, benefits and future challenges in healthcare domain. J. Commun. 2017, 12, 240–247. [Google Scholar] [CrossRef] [Green Version]
- Elsharkawy, M.; Al Masri, A.N. A Novel Image Encryption with Deep Learning Model for Secure Content based Image Retrieval. J. Cybersecur. Inf. Manag. 2019, 0, 54–64. [Google Scholar]
- Zhao, W.; Wang, C.; Nakahira, Y. Medical Application on Internet of Things. In Proceedings of the IET International Conference on Communication Technology and Application (ICCTA 2011), Beijing, China, 14–16 October 2011. [Google Scholar]
- Dimitrov, D.V. Medical internet of things and big data in healthcare. Healthc. Inform. Res. 2016, 22, 156–163. [Google Scholar] [CrossRef]
- Hu, F.; Xie, D.; Shen, S. On the application of the internet of things in the field of medical and health care. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 2053–2058. [Google Scholar] [CrossRef]
- Gómez, J.; Oviedo, B.; Zhuma, E. Patient monitoring system based on internet of things. Procedia Comput. Sci. 2016, 83, 90–97. [Google Scholar] [CrossRef] [Green Version]
- Sangpetch, O.; Sangpetch, A. Security context framework for distributed healthcare iot platform. In Proceedings of the Internet of Things Technologies for HealthCare, Västerås, Sweden, 18–19 October 2016; Springer: Cham, Switzerland, 2016; pp. 71–76. [Google Scholar]
- Dohr, A.; Modre-Opsrian, R.; Drobics, M.; Hayn, D.; Schreier, G. The internet of things for ambient assisted living. In Proceedings of the 2010 Seventh International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 12–14 April 2010; pp. 804–809. [Google Scholar] [CrossRef]
- Rghioui, A.; L’aarje, A.; Elouaai, F.; Bouhorma, M. The internet of things for healthcare monitoring: Security review and proposed solution. In Proceedings of the 2014 Third IEEE International Colloquium in Information Science and Technology (CIST), Tetouan, Morocco, 20–22 October 2014; pp. 384–389. [Google Scholar] [CrossRef]
- Laplante, P.A.; Laplante, N. The internet of things in healthcare: Potential applications and challenges. It Prof. 2016, 18, 2–4. [Google Scholar] [CrossRef]
- Li, C.; Hu, X.; Zhang, L. The IoT-based heart disease monitoring system for pervasive healthcare service. Procedia Comput. Sci. 2017, 112, 2328–2334. [Google Scholar] [CrossRef]
- Dridi, A.; Sassi, S.; Faiz, S. Towards a semantic medical internet of things. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia,, 30 October-3 November 2017; pp. 1421–1428. [Google Scholar] [CrossRef]
- Clark, S.S.; Ransford, B.; Rahmati, A.; Guineau, S.; Sorber, J.; Xu, W.; Fu, K. Wattsupdoc: Power Side Channels to Nonintrusively Discover Untargeted Malware on Embedded Medical Devices. Available online: https://www.semanticscholar.org/paper/WattsUpDoc%3A-Power-Side-Channels-to-Nonintrusively-Clark-Ransford/6c455f1daf739827c2e9af41c8f60cf93aaac84b (accessed on 20 July 2021).
- Yasser, I.; Khalil, A.T.; Mohamed, M.A.; Khalifa, F. A New Chaos-based Approach for Robust Image Encryption. J. Cybersecur. Inf. Manag. 2021, 7, 51–64. [Google Scholar]
- Jack, B. Wikipedia. 2020. Available online: http://en.wikipedia.org/wiki/Barnaby_Jack (accessed on 28 October 2020).
- Zadrozny, B. The Good Hacker: Barnaby Jack Dies. The Daily Beast 2013. Available online: https://www.thedailybeast.com/the-good-hacker-barnaby-jack-dies (accessed on 28 October 2020).
- 87% of Healthcare Organizations Will Adopt Internet of Things Technology by 2019. HIPAA J. 2017. Available online: https://www.hipaajournal.com/87pc-healthcare-organizations-adopt-internet-of-things-technology-2019-8712/ (accessed on 28 October 2020).
- Learn More Cybersecurity Insights by Neil Weinberg, NW Securing IoT in Healthcare is Critical. CSO Online 2018. Available online: https://www.csoonline.com/article/3270948/data-breach/securing-iot-in-healthcare-is-critical.html (accessed on 28 October 2020).
- Ryckaert, V. Hackers Held Patient Data Ransom, so Indiana Hospital System Paid $50,000. USA Today 2018. Available online: https://www.usatoday.com/story/tech/nation-now/2018/01/17/hackers-held-patient-data-ransom-so-indiana-hospitalsystem-paid-50-000/1042266001/ (accessed on 28 October 2020).
- Hollywood Hospital Pays $17,000 in Bitcoin to Hackers; FBI Investigating. Los Angeles Times 2016. Available online: http://www.latimes.com/business/technology/la-me-ln-hollywood-hospital-bitcoin-20160217-story.html (accessed on 28 October 2020).
- Armerding, T. Medical Devices at Risk: 5 Capabilities That Invite Danger. CSO Online 2017. Available online: https://www.csoonline.com/article/3202081/security/medical-devices-at-risk-5-capabilities-that-invite-danger.html (accessed on 28 October 2020).
- Securing the Internet of Healthcare Things. Available online: https://www.blackberry.com/us/en/forms/campaigns/ecp/healthcare (accessed on 28 October 2020).
- Greenberg A How the Internet of Things Got Hacked. Wired. Available online: https://www.wired.com/2015/12/2015-the-year-the-internet-of-things-got-hacked/ (accessed on 28 October 2020).
- Center for Devices Radiological Health Cybersecurity. U.S. Food and Drug Administration. Available online: https://www.fda.gov/medicaldevices/digitalhealth/ucm373213.htm (accessed on 28 October 2020).
- Medical & IoT Device Security for Healthcare. Armis 2020. Available online: https://www.armis.com/resources/iot-security-white-papers/medical-iot-device-security-for-healthcare/ (accessed on 28 October 2020).
- Islam, S.R.; Kwak, D.; Kabir, M.H.; Hossain, M.; Kwak, K.S. The internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Zeadally, S.; Siddiqui, F.; Baig, Z.; Ibrahim, A. Smart healthcare: Challenges and potential solutions using internet of things (IoT) and big data analytics. PSU Res. Rev. 2019, 4, 149–168. [Google Scholar] [CrossRef] [Green Version]
- IoT Security Forecasts and Trends: IoT, Security and Data Protection. 2020. Available online: https://www.i-scoop.eu/internet-of-things-guide/iot-security-forecasts/ (accessed on 28 October 2020).
- Nasiri, S.; Sadoughi, F.; Tadayon, M.H.; Dehnad, A. Security Requirements of Internet of Things-Based Healthcare System: A Survey Study. 2019. Available online: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7004290/ (accessed on 28 October 2020).
- Electropages Medical IoT and Security. In: Latest Electronics News on Components and Electrical Engineering. Available online: https://www.electropages.com/blog/2020/08/medical-iot-and-security (accessed on 28 October 2020).
- Elngar, A.; KRIT, S. Performance Analysis of Machine Learning based Botnet Detection and Classification Models for Information Security. J. Cybersecur. Inf. Manag. 2019, 0, 44–53. [Google Scholar]
- Binance Academy. Sybil Attacks Explained. In: Binance Academy. 2020. Available online: https://academy.binance.com/en/articles/sybil-attacks-explained (accessed on 28 October 2020).
- Buffer Overflow Attack with Example. GeeksforGeeks 2017. Available online: https://www.geeksforgeeks.org/buffer-overflow-attack-with-example/ (accessed on 28 October 2020).
- OWASP Secure Medical Device Deployment Standard. Available online: https://owasp.org/www-project-secure-medical-device-deployment-standard/migrated_content (accessed on 28 October 2020).
- OWASP Internet of Things. Available online: https://owasp.org/www-project-internet-of-things/ (accessed on 28 October 2020).
- Eken, C.; Eken, H. Security Threats and Recommendation in IoT Healthcare. Available online: https://ep.liu.se/ecp/article.asp?issue=142&article=054&volume=0# (accessed on 20 July 2021).
- Gloss, K. Healthcare IoT Security Risks and What to Do about Them. IoT Agenda 2020. Available online: https://internetofthingsagenda.techtarget.com/feature/Healthcare-IoT-security-issues-Risks-and-what-to-do-about-them (accessed on 28 October 2020).
- Thilakarathne, N.N.; Kagita, M.K.; Gadekallu, T.R.; Maddikunta, P.K.R. The Adoption of ICT Powered Healthcare Technologies towards Managing Global Pandemics. arXiv 2020, arXiv:2009.05716, preprint. [Google Scholar]
- Kagita, M.K.; Thilakarathne, N.; Gadekallu, T.R.; Maddikunta, P.K.R. A Review on Security and Privacy of Internet of Medical Things. arXiv 2020, preprint. arXiv:2009.05394. [Google Scholar]
- Kagita, M.K.; Thilakarathne, N.; Rajput, D.S.; Lanka, D.S. A Detail Study of Security and Privacy issues of Internet of Things. arXiv 2020, arXiv:2009.06341, preprint. [Google Scholar]
- BioRender. BioRender App. Available online: https://app.biorender.com/ (accessed on 28 October 2020).
- Navod, T. Review on the Use of ICT Driven Solutions Towards Managing Global Pandemics. J. ICT Res. Appl. 2021, 14, 207. [Google Scholar] [CrossRef]
- Fortune Business Insights. IoT Security Market: Employment of Connected Medical Devices in Healthcare to Boost Market Amid COVID-19. GlobeNewswire News Room. Available online: https://www.globenewswire.com/news-release/2021/04/22/2214917/0/en/IoT-Security-Market-Employment-of-Connected-Medical-Devices-in-Healthcare-to-Boost-Market-Amid-COVID-19.html (accessed on 22 April 2021).
- Healthcare IoT Security Market Applications, Share: Size Analysis 2027. Healthcare IoT Security Market Applications, Share|Size Analysis 2027. Available online: https://www.marketresearchfuture.com/reports/healthcare-iot-security-market-946 (accessed on 22 April 2021).
- Reports and Data. IoT in Healthcare Market. IoT in Healthcare Market Size, Trends & Growth, Industry Statistics. 2020. Available online: https://www.reportsanddata.com/;https://www.reportsanddata.com/report-detail/iot-in-healthcare-market (accessed on 22 April 2021).
- Kalra, R. Explore 3 IoT Trends in Healthcare for 2021. IoT Agenda. Available online: https://internetofthingsagenda.techtarget.com/feature/Explore-3-IoT-trends-in-healthcare (accessed on 28 December 2020).
- O’Halloran, J.; 5G, IoT Technology to Transform Health and Social Care. ComputerWeekly.com. Available online: https://www.computerweekly.com/news/252492039/5G-IoT-technology-to-transform-health-and-social-care?ga=2.4808240.284146281.1623082131-1475437348.1621161510;https://blog.eccouncil.org/3-key-cyber-trends-that-the-healthcare-industry-should-avoid-to-combat-cyberattacks/ (accessed on 13 November 2020).
- Certified Ethical Hacker: InfoSec Cyber Security Certification: EC-Council. EC. Available online: https://www.eccouncil.org/ (accessed on 22 April 2021).
- Radware. Security Challenges for Healthcare Providers Radware Blog. Available online: https://blog.radware.com/security/2020/08/security-challenges-for-healthcare-providers/ (accessed on 10 August 2020).
- Infosecurity Magazine—Information Security & IT Security. Available online: https://www.infosecurity-magazine.com/ (accessed on 22 April 2021).
- Mahendran, R.K.; Velusamy, P. A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things. Comput. Commun. 2020, 153, 545–552. [Google Scholar] [CrossRef]
- Mahendran, R.K.; Velusamy, P.; Pandian, P. An efficient priority-based convolutional auto-encoder approach for electrocardiogram signal compression in Internet of Things based healthcare system. Trans. Emerg. Telecommun. Technol. 2021, 32, e4115. [Google Scholar]
- Srivastava, G.; Crichigno, J.; Dhar, S. A light and secure healthcare blockchain for iot medical devices. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Shen, M.; Deng, Y.; Zhu, L.; Du, X.; Guizani, N. Privacy-preserving image retrieval for medical IoT systems: A blockchain-based approach. IEEE Netw. 2019, 33, 27–33. [Google Scholar] [CrossRef]
- Thilakarathne, N.N.; Kagita, M.K.; Priyashan, W.M. Green Internet of Things: The Next Generation Energy Efficient Internet of Things. Available online: https://arxiv.org/ftp/arxiv/papers/2012/2012.01325.pdf (accessed on 10 August 2021).
- Mustafa, M.M.; Parthasarathy, V.; Kumar, M.R.; Hemalatha, S. An Efficient DTDM H-MAC Protocol with Self-Calibrating Algorithm in BSN for Sporting Application. (2016). Available online: https://moam.info/an-efficient-dtdm-h-mac-protocol-with-self-_59c575931723ddde92385716.html (accessed on 10 August 2021).
- Kumar, P.; Chouhan, L. A privacy and session key based authentication scheme for medical IoT networks. Comput. Commun. 2021, 166, 154–164. [Google Scholar] [CrossRef]
- Karunarathne, S.M.; Saxena, N.; Khan, M.K. Security and Privacy in IoT Smart Healthcare. IEEE Internet Comput. 2021, 25, 37–48. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Towards design and implementation of security and privacy framework for internet of medical things (iomt) by leveraging blockchain and ipfs technology. J. Supercomput. 2021, 77, 1–40. [Google Scholar] [CrossRef]
- Bhandari, K.S.; Ra, I.H.; Cho, G. Multi-topology based QoS-differentiation in RPL for internet of things applications. IEEE Access 2020, 8, 96686–96705. [Google Scholar] [CrossRef]
- Bhandari, K.S.; Seo, C.; Cho, G.H. Towards Sensor-Cloud Based Efficient Smart Healthcare Monitoring Framework using Machine Learning. 2020. Available online: https://manuscriptlink-society-file.s3-ap-northeast-1.amazonaws.com/kism/conference/sma2020/presentation/SMA-2020_paper_129.pdf (accessed on 10 August 2021).
- Sadek, I.; Rehman, S.U.; Codjo, J.; Abdulrazak, B. Privacy and Security of IoT Based Healthcare Systems: Concerns, Solutions, and Recommendations. Available online: https://link.springer.com/chapter/10.1007/978-3-030-32785-9_1 (accessed on 10 August 2021).
- Yaacoub, J.P.A.; Noura, M.; Noura, H.N.; Salman, O.; Yaacoub, E.; Couturier, R.; Chehab, A. Securing internet of medical things systems: Limitations, issues and recommendations. Future Gener. Comput. Syst. 2020, 105, 581–606. [Google Scholar] [CrossRef]
- Tawalbeh, L.A.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and security: Challenges and solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Research, G.D.T. Cybersecurity in Medical: Cybersecurity Trends. Medical Device Network, Retrieved 30 September 2021. Available online: https://www.medicaldevice-network.com/comment/cybersecurity-in-medical-cybersecurity-trends/ (accessed on 22 April 2021).
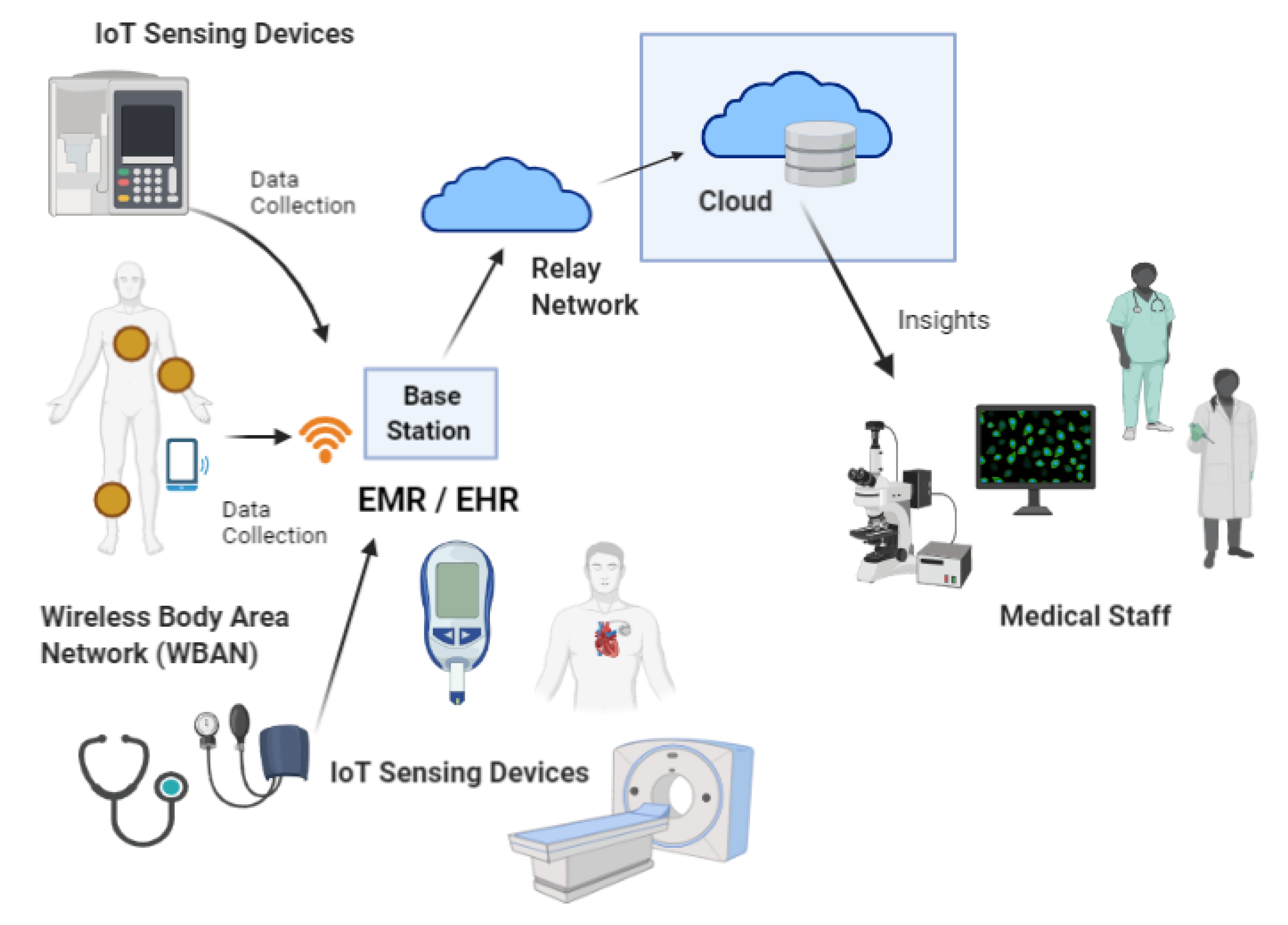

| Network Layer | Application Layer |
|---|---|
| For network layer addressing IPv4/IPv6 protocols are used. For routing RPL, CARP, and CORPL protocols are used. The rest of the protocols used in network layer includes TCP, UDP, 6LoWPAN, IEEE 802.15.4 (e.g.: ZigBee) IEEE 802.15.1 (Bluetooth) LPWAN (e.g.: LoRaWAN) RFID, NFC, IEEE 802.11 (Wi-Fi). | MQTT, CoAP, DSS, AMQP, HTTP, HTTPS, TLS |
| Device Category | Examples |
|---|---|
| Clinical monitors | Heart rate monitors, ventilators, pulse oximetry monitors, electrocardiogram monitors, capnography monitors, depth of consciousness monitors |
| Medical devices | Ventilators, medical imaging devices (e.g., X-rays, computerized tomography (CT) scanners, and magnetic resonance imaging (MRI)), infusion pumps, incubators, smart medical devices, telemetry devices, smart stethoscopes |
| Virtual care devices | Remote ICU telemetry |
| Devices in smart patient rooms | Fall detection monitors, smart beds, personal hygiene monitors |
| Device Category | Examples |
| Wearables | Wristbands, bio-energy patches, smart watches |
| Implantable devices | Pacemakers, defibrillators, neurostimulators, respiratory rate sensors, muscle activity sensors, swallowable camera capsules, embedded cardiac devices |
| Remote clinical monitors | Pulse oximeter monitors, ECG monitors, glucometers, fall detection monitors |
| Device Category | Examples |
|---|---|
| Devices for tracking employees | For tracking nursing staff, ancillary staff, physicians |
| Devices for tracking patients | Infant abduction, wandering systems, rehabilitation systems |
| Devices for tracking visitors | Way finding and digital signage |
| Devices for tracking assets | For wheelchairs, infusion pumps, smart cabinets, medication carts |
| Device Category | Examples |
|---|---|
| Devices used for environmental controls | Lighting (Daylight sensors), room control, humidity monitoring, water quality monitoring, HVAC |
| Devices used for building management | Elevators, power monitoring and power distribution |
| Devices used for security monitoring | Door locks and entry systems, fire alarms, video surveillance systems |
| Reference and Year | Tittle | IoT in General | MIoT Specific | Scope | Contributions and Critique |
|---|---|---|---|---|---|
| [4], 2020 | The Role of the Internet of Things in Health Care: A Systematic and Comprehensive Study | ✓ | A general systematic review that highlights security and privacy challenges. | The researchers discussed recent security and privacy challenges, pointing out the vulnerabilities that are present, but they did not put much effort towards discussing security and privacy requirements, countermeasures, and solutions. | |
| [6], 2017 | Security and privacy in the internet of medical things: taxonomy and risk assessment | ✓ | Taxonomy of security and privacy issues pertaining to MIoT is discussed. | A quantitative approach to identifying and assessing risks in MIoT is highlighted. Even though the researchers highlighted security and privacy issues, how to mitigate them was not discussed in detail in the study. | |
| [7], 2017 | Towards composable threat assessment for medical IoT (MIoT) | ✓ | A general analysis of MIoT threat assessment is discussed. | A framework for identifying, assessing, and evaluating threats in the MIoT environment is highlighted, whereas the study did not provide adequate knowledge about the security and privacy of MIoT. | |
| [8], 2018 | Secure medical data transmission model for IoT-based healthcare systems | ✓ | Proposed a hybrid security model for securing the content in medical images. | A security model based on the steganography technique with a hybrid encryption scheme is introduced towards protecting the security and data integrity of patient diagnosis data that are transmitted across MIoT networks. | |
| [9], 2012 | Internet of Things in healthcare: Interoperatibility and security issues | ✓ | A general discussion with regard to the security issues, benefits, and solutions in MIoT is provided. | Security challenges pertaining to the IoT in telemonitoring are highlighted. Even though the researchers provided a discussion in terms of the security of telemonitoring, this study did not provide adequate knowledge related to security attacks pertaining to MIoT-based telemonitoring solutions. | |
| [10], 2018 | An internet of things-based health prescription assistant and its security system design | ✓ | A theoretical framework for an MIoT health prescription assistant is proposed. | A security system for a health prescription assistance system is designed, implemented, and validated; this study only provides knowledge about the security aspects of MIoT-based telemedicine and not about the entire MIoT environment. | |
| [11], 2019 | A joint resource-aware and medical data security framework for wearable healthcare systems | ✓ | A security framework for resource-constrained wearable health monitoring systems is introduced. | A biometric-based security framework for a wearable health monitoring systems is introduced, and a performance comparison of the proposed model is also conducted. Even though the researchers conducted an experimental evaluation to test their framework, they failed to discuss security and privacy repercussions in terms of wearable MIoT, which is becoming a booming trend as of now. | |
| [12], 2019 | IoMT-SAF: Internet of medical things security assessment framework | ✓ | A web-based MIoT security assessment framework is developed. | The researchers developed a web-based framework that recommends security features in MIoT and assesses protection and deterrence based on ontology. Nevertheless, even though the featured web solution ranks the security solutions in terms of security and privacy, the study does not provide comprehensive knowledge about MIoT security and privacy. | |
| [13], 2018 | Internet-of-Things security and vulnerabilities: Taxonomy, challenges, and practice | ✓ | A summary of overall IoT security attacks is depicted. | The authors provide a taxonomy and classification based on IoT security attacks based on application domains, including healthcare, where they also highlight security and privacy requirements. Even though this provides a comprehensive overview of security and privacy attacks, countermeasures for the attacks are not featured in this study. | |
| [17], 2018 | Security and privacy in the medical internet of things: a review | ✓ | A review on security and privacy requirements and solutions with regard to the MIoT is provided. | Security and privacy requirements, open challenges, and anticipated future directions in terms of the security and privacy of MIoT are discussed, where this provides adequate knowledge about the underlying ecosystem, leading to security vulnerabilities. | |
| [18], 2015 | A review of security protocols in mHealth wireless body area networks (WBAN) | ✓ | Threats pertaining to the medical networks are discussed. | The latest trends and future directions are discussed as they pertain to medical networks, where the researchers were able to provide adequate knowledge about security requirements and mechanisms pertaining to medical networks. However, this features the security of MIoT networks only. | |
| [21], 2016 | A secure IoT-based healthcare system with body sensor networks | ✓ | A secure MIoT system is proposed in this study. | A secure MIoT system with a body sensor network is proposed and implemented using the Raspberry PI platform. | |
| [28], 2015 | BSN-Care: A secure IoT-based modern healthcare system using body sensor network | ✓ | Security concerns and requirements in the field of body sensor network-based healthcare systems are discussed. | The researchers proposed a secure MIoT healthcare system using a body sensor network (BSN) called BSN-Care. | |
| [35], 2017 | Internet of Medical Things (IOMT): applications, benefits and future challenges in healthcare domain | ✓ | Applications and challenges of MIoT are discussed, highlighting the security concerns. | A comprehensive review is presented in terms of MIoT applications and challenges to the domain, where the researchers do not put much emphasis on security as a key challenge. | |
| [36], 2017 | Internet of things for smart healthcare: Technologies, challenges, and opportunities | ✓ | A survey is conducted that highlights the state of the art related to the MIoT. | Security, privacy, wearability, and low-power operations related to MIoT are discussed, but the researchers do not provide that much focus on security and piracy as a key challenge. | |
| [41], 2016 | Security context framework for distributed healthcare IoT platform | ✓ | Context aware security framework is introduced for MIoT | The researchers introduce a security framework that can be used to secure data transmission across distributed MIoT platforms, whereas this does not feature any security and privacy attacks. | |
| [43], 2014 | The internet of things for healthcare monitoring: security review and proposed solution | ✓ | Security problems related to MIoT monitoring system are presented. | Proposed a security model for MIoT monitoring systems based on symmetric cryptography and network node authentication mechanisms, and authors provide decent knowledge in terms of security arracks and countermeasures. | |
| [44], 2016 | The internet of things in healthcare: Potential applications and challenges | ✓ | A review is provided in terms of MIoT applications. | Challenges are discussed in terms of the security and privacy MIoT applications as they pertain to MIoT solutions. | |
| [47], 2013 | Wattsupdoc: Power side channels to nonintrusively discover untargeted malware on embedded medical devices | ✓ | A research experiment is conducted with regard to MIoT platforms. | Proposed an add-on monitoring system for detecting malware that targets MIoT devices. | |
| [60], 2015 | The internet of things for health care: a comprehensive survey | ✓ | A survey is provided in terms of architecture, threat model, security requirements, and challenges. | Security and privacy issues, the latest trends pertaining to the MIoT ecosystem, are highlighted; this study provides a comprehensive survey about pervasive MIoT ecosystems. On the other hand, this study does not place much focus on security and privacy as key challenges. | |
| [63], 2019 | Security Requirements of Internet of Things-Based Healthcare System: a Survey | ✓ | In order to identify the security requirements pertaining to MIoT, a survey isconducted. | Features and concepts associated with security requirements for MIoT are highlighted, but this study only features security and privacy requirements. | |
| [70], 2018 | Security Threats and Recommendation in IoT Healthcare | ✓ | Provides a review of various MIoT systems. | Security and privacy issues pertaining to MIoT systems and threats are discussed in terms of the layered architecture, and the researchers do not place much emphasis on challenges and future directions in terms of security and privacy. | |
| [85], 2020 | A secure fuzzy extractor based biometric key authentication scheme for body sensor network in Internet of Medical Things | ✓ | Biometric authentication schema for MIoT body sensor network is introduced | Secure fuzzy extractor combined with fuzzy vault is introduced to protect sensitive patient data using encryption techniques. | |
| [91], 2021 | A privacy and session key based authentication scheme for medical IoT networks | ✓ | Network security schema for MIoT is introduced. | Secure addressing and mutual authentication protocol (SAMA) scheme is proposed and validated using formal and informal methods. | |
| [92], 202. | Security and Privacy in IoT Smart Healthcare | ✓ | The current state of security and privacy of MIoT is analyzed. | The researchers provide a detailed discussion about challenges and security frameworks in terms of MIoT, and they also highlight security solutions in the study. | |
| [93], 2021 | Towards design and implementation of security and privacy framework for internet of medical things (iomt) by leveraging blockchain and ipfs technology | ✓ | Smart-contract-enabled blockchain network is introduced | To protect the security and privacy of patient data, a blockchain-based methodology is proposed where the data can be stored on blockchain ledgers, towards enhancing data integrity and user privacy. |
| Reference and Year | Security and Privacy Requirements Are Discussed | Security and Privacy Attack Types Are Discussed | Countermeasures and Solutions for Attacks Are Discussed | Challenges Are Discussed in Terms of Security and Privacy | Recent Trends in Terms of Security and Privacy Are Highlighted | Future Directions Are Discussed in Terms of Security and Privacy |
|---|---|---|---|---|---|---|
| Thilakarathne, N. N., Kagita, M. K., and Gadekallu, D. T. R. (2020) | X | X | X | ✓ | ✓ | X |
| Alsubaei, F., Abuhussein, A., and Shiva, S. (2017) | ✓ | X | X | X | X | X |
| Darwish, S., Nouretdinov, I., and Wolthusen, S. D. (2017) | ✓ | X | X | ✓ | X | X |
| Tarouco et al. (2012) | ✓ | X | X | ✓ | X | X |
| Chenet al. (2018) | ✓ | ✓ | X | X | X | X |
| Sun et al. (2018) | ✓ | ✓ | ✓ | X | X | ✓ |
| Joyia et al. (2017) | X | X | X | ✓ | X | X |
| Baker, S. B., Xiang, W., and Atkinson, I. (2017). | X | ✓ | X | ✓ | X | X |
| Rghioui et al. (2014) | ✓ | ✓ | ✓ | X | X | X |
| Laplante, P. A., and Laplante, N. (2016) | X | ✓ | ✓ | ✓ | X | X |
| Islam et al. (2015) | X | ✓ | ✓ | ✓ | X | X |
| Nasiri S, Sadoughi F, Tadayon MH, and Dehnad A (2019) | ✓ | X | X | ✓ | X | X |
| Karunarathne et al. (2021). | ✓ | X | X | ✓ | X | X |
| Our review | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| MIoT Attack Type | Related Layer | Access Control | Data Encryption | Data Auditing | IoT Healthcare Policies | Data Search | Data Minimization | Data Anonymization | Inventory Devices | Network Segmentation | Follow the Best Practices | Wider Awareness | Continuous Monitoring and Reporting | Justification/Other Measures That Can Take |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Tampering of devices | Perception | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | As the tampering of devices deals with physical MIoT components, having access control mechanisms, anti-tampering mechanisms, implementing organization-wide healthcare policies and regularly monitoring the devices, and following up the best security practices can be taken as countermeasures. | ||||||
| Side channel attack | Perception | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | As side-channel attacks are reliant on the relationship between information leaked through a side-channel and secret data, two types of countermeasures can be taken: eliminating or reducing the release of such information and eliminating the relationship between the leaked information and the secret data using some kind of data scrambling method. | |||||
| Tag cloning | Perception | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Following a successful side-channel attack, a tag cloning attack can be performed, which can be mainly mitigated through the implementation of data encryption methods. | |||
| Sensor tracking | Perception | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | In order to avoid sensor tracking attacks, data that are mainly transmitted across MIoT networks can be encrypted, and access control mechanisms can be implemented. On the other hand, data search, anonymization, and minimization techniques can also be used. | ||
| Insertion of forged nodes | Perception | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | In order to avoid these types of attacks physical access control mechanisms, regularly monitoring devices can be conducted apart from adhering to healthcare policies and by following up with the best practices. | ||||||
| Denial of Service (DOS) | Network | ✓ | ✓ | ✓ | ✓ | ✓ | In order to prevent DOS attacks, network security can be strengthened by implementing next-generation firewalls, IPS, and IDS systems. Nevertheless, routers and firewalls can be configured to block malicious traffic, and unnecessary TCP/UDP services can be blocked to prevent DOS attacks. | |||||||
| Distributed Denial of Service (DDOS) | Network | ✓ | ✓ | ✓ | ✓ | ✓ | The same measures that are used to counter DOS attacks can be used as countermeasures for DDOS attacks. | |||||||
| Rogue access | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Apart from following up the best security practices and increasing user awareness, wireless intrusion prevention systems can be implemented to monitor the radio spectrum for unauthorized access points. | |||||
| Eavesdropping | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | To prevent eavesdropping attacks, medical data can be encrypted. On the other hand, by using a personal firewall, keeping antivirus software updated, and using a virtual private network, these attacks can be prevented. | |||||
| Man in the Middle attack (MITM) | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Encrypting the medical data that transmit across the network and sticking with the best security practices would help to prevent MITM attacks. | |||||
| Sybil Attack | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | These attacks can be prevented by implementing ace control mechanisms and by following up with the best security practices. | ||||||
| Sniffing Attack | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | These attacks can be prevented using implementing access control mechanisms and by following up the best security practices. | |||||
| Routing attacks | Network | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Routing attacks can be prevented using implementing network security mechanisms such as IDS. | |||||
| Session hijacking | Application | ✓ | ✓ | ✓ | In order to prevent session hijacking attacks, the network data can be encrypted, and other network security protection mechanisms such as SSL/TLS and HTTPS schema can be implemented to secure the communication media. | |||||||||
| Cross-site scripting (XSS) | Application | ✓ | ✓ | ✓ | ✓ | XSS attacks can be prevented by having adequate application access control mechanisms, validating user inputs, and encoding output data. | ||||||||
| Cross-Site request forgery (CSRF) | Application | ✓ | ✓ | ✓ | ✓ | ✓ | CSRF attacks can be prevented by having adequate network security mechanisms and by using anti-CSRF mechanisms. | |||||||
| SQL injection | Application | ✓ | ✓ | ✓ | ✓ | ✓ | These attacks can be prevented by implementing web application firewalls (WAF), IDS, and by having adequate application security controls, such as input validations. | |||||||
| Brute Force attack | Application | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Brute force attacks can be prevented by sticking with healthcare security policies, using adequate application security controls, and continuously monitoring logs through a SIEM. | |||||
| Ransomware | Application | ✓ | ✓ | ✓ | ✓ | These attacks can be mitigated by increasing user awareness and by sticking with the best security practices, such as having anti-virus and anti-spyware solutions and using the inbuilt ransomware protection features of operating systems. | ||||||||
| Buffer Overflow | Application | ✓ | ✓ | ✓ | ✓ | These attacks can be prevented by disabling unnecessary network services and by implementing firewalls and IPS systems. | ||||||||
| Phishing Attack | Application | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | In order to prevent phishing attacks, user awareness can be improved as the first defense, and antivirus and antispyware solutions can be installed on end-user machines to protect the organization’s resources. |
| Challenge | Impede to the Functionality of | Related Work | ||
|---|---|---|---|---|
| Perception Layer | Network Layer | Application Layer | ||
| Insecure network | ✓ | ✓ | Research studies [2,3,6,7,8,10,12,18,21,22,23,28,32,35,41,48] mostly focus on this insecure network challenges in the MIoT environment. In this regard, the authors contributed in the form of surveys/reviews and proposed solutions for network data transmission. | |
| Limitation of resources | ✓ | ✓ | ✓ | The research studies [4,5,6,7,9,32,35,47] mostly focus on this challenge, and most of the studies were surveys/reviews. |
| Heterogeneous devices | ✓ | These research studies [4,5,6,7,9,23,32,35] mostly focus on this challenging aspect, and most of them were surveys/reviews. | ||
| Zero-day vulnerabilities and security patches | ✓ | ✓ | These research studies [4,5,6,7,9,32,35] mostly focus on this challenging aspect, and most of them were surveys/reviews, and some of the studies proposed novel solutions. | |
| High Mobility | ✓ | These research studies [4,5,6,9,32,35] mostly focus on this challenging aspect, and most of them were surveys/reviews. | ||
| Dynamic network topology | ✓ | These research studies [4,5,6,7,9,32,35] mostly focus on this challenging aspect, and some of the studies have proposed solutions to this problem. | ||
| Trust management | ✓ | ✓ | These research studies [4,5,6,7,9,27,32,35,47,62] most focus on this challenging aspect, and some of the authors have proposed trust management solutions by incorporating encryption mechanism among these studies. | |
| Social Engineering | ✓ | Even though this was a rarely spoken subject, the research studies [4,5,6,7,9,32,35] provide some clues about this challenging aspect. | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elhoseny, M.; Thilakarathne, N.N.; Alghamdi, M.I.; Mahendran, R.K.; Gardezi, A.A.; Weerasinghe, H.; Welhenge, A. Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability 2021, 13, 11645. https://doi.org/10.3390/su132111645
Elhoseny M, Thilakarathne NN, Alghamdi MI, Mahendran RK, Gardezi AA, Weerasinghe H, Welhenge A. Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability. 2021; 13(21):11645. https://doi.org/10.3390/su132111645
Chicago/Turabian StyleElhoseny, Mohamed, Navod Neranjan Thilakarathne, Mohammed I. Alghamdi, Rakesh Kumar Mahendran, Akber Abid Gardezi, Hesiri Weerasinghe, and Anuradhi Welhenge. 2021. "Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions" Sustainability 13, no. 21: 11645. https://doi.org/10.3390/su132111645
APA StyleElhoseny, M., Thilakarathne, N. N., Alghamdi, M. I., Mahendran, R. K., Gardezi, A. A., Weerasinghe, H., & Welhenge, A. (2021). Security and Privacy Issues in Medical Internet of Things: Overview, Countermeasures, Challenges and Future Directions. Sustainability, 13(21), 11645. https://doi.org/10.3390/su132111645









