Efficient Neighbour Feedback Based Trusted Multi Authenticated Node Routing Model for Secure Data Transmission
Abstract
1. Introduction
2. Routing Protocol Types
3. Literature Survey
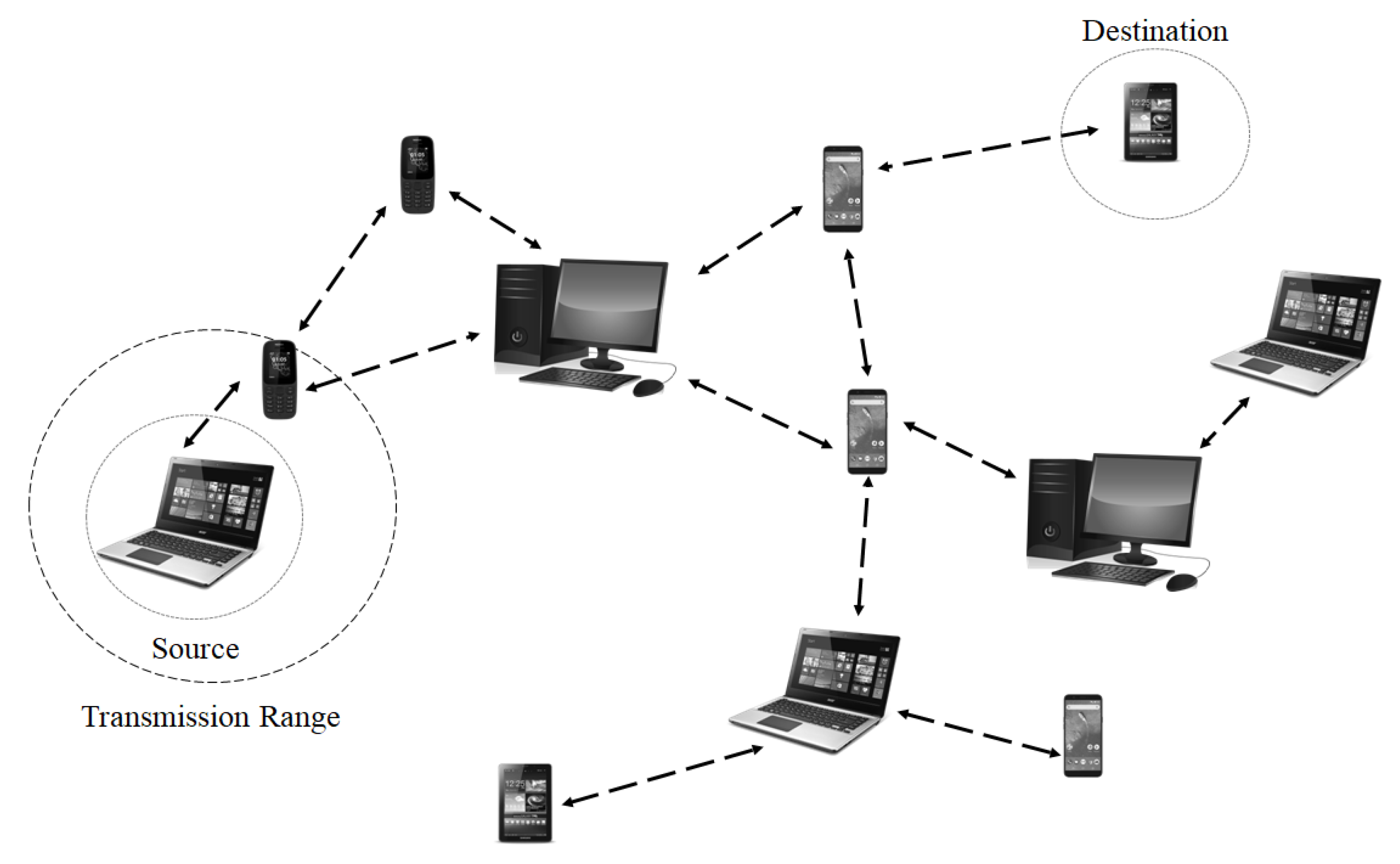
4. Proposed Model

5. Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, T.; Xu, X.; Zhou, L.; Jiang, X.; Loo, J. Cache Space Efficient Caching Scheme for Content-Centric Mobile Ad Hoc Networks. IEEE Syst. J. 2019, 13, 530–541. [Google Scholar] [CrossRef]
- Guha, A.; Samanta, D.; Banerjee, A.; Agarwal, D. A deep learning model for Information Loss Prevention from multi-page digital documents. IEEE Access 2021, 9, 80451–80465. [Google Scholar] [CrossRef]
- Hurley-Smith, D.; Wetherall, J.; Adekunle, A. SUPERMAN: Security Using Pre-Existing Routing for Mobile Ad hoc Networks. IEEE Trans. Mob. Comput. 2017, 16, 2927–2940. [Google Scholar] [CrossRef]
- Afzal, M.K.; Rehmani, M.H.; Zikria, Y.B.; Ni, Q. Data-Driven Intelligence in Wireless Networks: Issues, Challenges, and Solution. Trans. Emerg. Telecommun. Technol. 2019, 30, e3722. [Google Scholar] [CrossRef]
- Zhang, D.G.; Zhao, P.Z.; Cui, Y.y.; Chen, L.; Zhang, T.; Wu, H. A New Method of Mobile Ad Hoc Network Routing Based on Greed Forwarding Improvement Strategy. IEEE Access 2019, 7, 158514–158524. [Google Scholar] [CrossRef]
- Xu, H.; Zhao, Y.; Zhang, L.; Wang, J. A Bio-Inspired Gateway Selection Scheme for Hybrid Mobile Ad Hoc Networks. IEEE Access 2019, 7, 61997–62010. [Google Scholar] [CrossRef]
- Dbouk, T.; Mourad, A.; Otrok, H.; Tout, H.; Talhi, C. A Novel Ad-Hoc Mobile Edge Cloud Offering Security Services Through Intelligent Resource-Aware Offloading. IEEE Trans. Netw. Serv. Manag. 2019, 16, 1665–1680. [Google Scholar] [CrossRef]
- Biswal, A.K.; Singh, D.; Pattanayak, B.K.; Samanta, D.; Yang, M.H. IoT-Based Smart Alert System for Drowsy Driver Detection. Wirel. Commun. Mob. Comput. 2021, 2021, 6627217. [Google Scholar] [CrossRef]
- Bhardwaj, A.; El-Ocla, H. Multipath Routing Protocol Using Genetic Algorithm in Mobile Ad Hoc Networks. IEEE Access 2020, 8, 177534–177548. [Google Scholar] [CrossRef]
- Paranthaman, V.V.; Kirsal, Y.; Mapp, G.; Shah, P.; Nguyen, H.X. Exploiting Resource Contention in Highly Mobile Environments and Its Application to Vehicular Ad-Hoc Networks. IEEE Trans. Veh. Technol. 2019, 68, 3805–3819. [Google Scholar] [CrossRef]
- Gomathy, V.; Padhy, N.; Samanta, D.; Sivaram, M.; Jain, V.; Amiri, I.S. Malicious node detection using heterogeneous cluster based secure routing protocol (HCBS) in wireless adhoc sensor networks. J. Ambient Intell. Humaniz. Comput. 2020, 11, 4995–5001. [Google Scholar] [CrossRef]
- Zhang, Y.; Shi, Y.; Shen, F.; Yan, F.; Shen, L. Price-Based Joint Offloading and Resource Allocation for Ad Hoc Mobile Cloud. IEEE Access 2019, 7, 62769–62784. [Google Scholar] [CrossRef]
- Sivakumar, P.; Nagaraju, R.; Samanta, D.; Sivaram, M.; Hindia, M.N.; Amiri, I.S. A novel free space communication system using nonlinear InGaAsP microsystem resonators for enabling power-control toward smart cities. Wirel. Netw. 2020, 26, 2317–2328. [Google Scholar] [CrossRef]
- Khamparia, A.; Singh, P.K.; Rani, P.; Samanta, D.; Khanna, A.; Bhushan, B. An internet of health things-driven deep learning framework for detection and classification of skin cancer using transfer learning. Trans. Emerg. Telecommun. Technol. 2020, 32, e3963. [Google Scholar] [CrossRef]
- Althar, R.R.; Samanta, D. The realist approach for evaluation of computational intelligence in software engineering. Innov. Syst. Softw. Eng. 2021, 17, 17–27. [Google Scholar] [CrossRef]
- Jevtic, N.J.; Malnar, M.Z. Novel ETX-Based Metrics for Overhead Reduction in Dynamic Ad Hoc Networks. IEEE Access 2019, 7, 116490–116504. [Google Scholar] [CrossRef]
- Liu, J.; Xu, Y.; Li, Z. Resource Allocation for Performance Enhancement in Mobile Ad Hoc Networks. IEEE Access 2019, 7, 73790–73803. [Google Scholar] [CrossRef]
- Guha, A.; Samanta, D. Hybrid Approach to Document Anomaly Detection: An Application to Facilitate RPA in Title Insurance. Int. J. Autom. Comput. 2021, 18, 55–72. [Google Scholar] [CrossRef]
- El-Hadidi, M.G.; Azer, M.A. Traffic Analysis for Real Time Applications and its Effect on QoS in MANETs. In Proceedings of the 2021 International Mobile, Intelligent, and Ubiquitous Computing Conference (MIUCC), Cairo, Egypt, 26–27 May 2021; pp. 155–160. [Google Scholar] [CrossRef]
- Anand, A.; Aggarwal, H.; Rani, R. Partially distributed dynamic model for secure and reliable routing in mobile ad hoc networks. J. Commun. Netw. 2016, 18, 938–947. [Google Scholar] [CrossRef]
- Venkanna, U.; Agarwal, J.K.; Velusamy, R.L. A Cooperative Routing for MANET Based on Distributed Trust and Energy Management. Wirel. Pers. Commun. 2015, 81, 961–979. [Google Scholar] [CrossRef]
- Malathi, M.; Jayashri, S. Modified Bi-directional Routing with Best Afford Path (MBRBAP) for Routing Optimization in MANET. Wirel. Pers. Commun. 2016, 90, 861–873. [Google Scholar] [CrossRef]
- Biswas, J.; Kayal, P.; Samanta, D. Reducing Approximation Error with Rapid Convergence Rate for Non-Negative Matrix Factorization (NMF). Math. Stat. 2021, 9, 285–289. [Google Scholar] [CrossRef]
- Samanta, D.; Alahmadi, A.H.; Karthikeyan, M.P.; Khan, M.Z.; Banerjee, A.; Dalapati, G.K.; Ramakrishna, S. Cipher Block Chaining Support Vector Machine for Secured Decentralized Cloud Enabled Intelligent IoT Architecture. IEEE Access 2021, 9, 98013–98025. [Google Scholar] [CrossRef]
- Devi, V.S.; Hegde, N.P. Multipath Security Aware Routing Protocol for MANET Based on Trust Enhanced Cluster Mechanism for Lossless Multimedia Data Transfer. Wirel. Pers. Commun. Int. J. 2018, 100, 923–940. [Google Scholar] [CrossRef]
- Hammamouche, A.; Omar, M.; Djebari, N.; Tari, A. Lightweight reputation-based approach against simple and cooperative black-hole attacks for MANET. J. Inf. Secur. Appl. 2018, 43, 12–20. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, R.; Samanta, D.; Paul, M.; Kumar, V. A combining approach using DFT and FIR filter to enhance impulse response. In Proceedings of the 2017 International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 18–19 July 2017; pp. 134–137. [Google Scholar] [CrossRef]
- Samanta, D.; Galety, M.G.; Shivamurthaiah, M.; Kariyappala, S. A Hybridization Approach based Semantic Approach to the Software Engineering. TEST Eng. Manag. 2020, 83, 5441–5447. [Google Scholar]
- Subramaniyan, S.; Johnson, W.; Subramaniyan, K. A distributed framework for detecting selfish nodes in MANET using Record- and Trust-Based Detection (RTBD) technique. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 205. [Google Scholar] [CrossRef]
- Mekala, M.S.; Patan, R.; Islam, S.H.; Samanta, D.; Mallah, G.A.; Chaudhry, S.A. DAWM: Cost-Aware Asset Claim Analysis Approach on Big Data Analytic Computation Model for Cloud Data Centre. Secur. Commun. Netw. 2021, 2021, 6688162. [Google Scholar] [CrossRef]
- Dhanush, V.; Mahendra, A.R.; Kumudavalli, M.V.; Samanta, D. Application of deep learning technique for automatic data exchange with air-gapped systems and its security concerns. In Proceedings of the 2017 International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 18–19 July 2017; pp. 324–328. [Google Scholar] [CrossRef]
- Gurunath, R.; Agarwal, M.; Nandi, A.; Samanta, D. An Overview: Security Issue in IoT Network. In Proceedings of the 2018 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC)I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 30–31 August 2018; pp. 104–107. [Google Scholar] [CrossRef]
- Maheswari, M.; Geetha, S.; Kumar, S.S.; Karuppiah, M.; Samanta, D.; Park, Y. PEVRM: Probabilistic Evolution Based Version Recommendation Model for Mobile Applications. IEEE Access 2021, 9, 20819–20827. [Google Scholar] [CrossRef]
- Musaddiq, A.; Zikria, Y.B.; Ali, R.; Rasool, I.U.; Kim, S.W. Congestion control routing using optimal channel assignment mechanism in wireless mesh network. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 355–360. [Google Scholar] [CrossRef]
- Zikria, Y.B.; Nosheen, S.; Kim, S.W. Quality of service analysis for multimedia traffic using DSR, AODV and TORA over Wi-Media ultra wide band. In Proceedings of the 2015 12th International Bhurban Conference on Applied Sciences and Technology (IBCAST), Islamabad, Pakistan, 13–17 January 2015; pp. 539–546. [Google Scholar] [CrossRef]







| Parameter | Value |
|---|---|
| Number of simulated Nodes | 20-40-60-80-100 nodes |
| Area size of topography (m) | 500 m × 500 m |
| Radio range | 150 m |
| Packet size | 1000 byte |
| Send rate of traffic | 4 packets/s |
| Traffic type | cbr |
| Number of traffic sources | 4 |
| Pause Time (s) at simulation | lOs |
| Simulation Time | 80 s |
| Simulated Routing Protocols | AODV |
| Network Nodes | Trust Factor Generation Time Levels | |
|---|---|---|
| NFbTMAN Model | NETAR Model | |
| 10 | 20 | 20 |
| 20 | 28 | 30 |
| 30 | 30 | 38 |
| 40 | 34 | 42 |
| 50 | 40 | 50 |
| 60 | 40 | 58 |
| 70 | 45 | 61 |
| 80 | 50 | 75 |
| 90 | 52 | 88 |
| Network Nodes | Route Identification Time Levels | |
|---|---|---|
| NFbTMAN Model | NETAR Model | |
| 10 | 8 | 32 |
| 20 | 14 | 38 |
| 30 | 18 | 42 |
| 40 | 22 | 48 |
| 50 | 28 | 53 |
| 60 | 32 | 57 |
| 70 | 40 | 60 |
| 80 | 43 | 65 |
| 90 | 50 | 75 |
| Network Nodes | Neighbour Feedback Assessment Time Level | |
|---|---|---|
| NFbTMAN Model | NETAR Model | |
| 10 | 20 | 50 |
| 20 | 25 | 60 |
| 30 | 30 | 70 |
| 40 | 38 | 75 |
| 50 | 40 | 79 |
| 60 | 45 | 80 |
| 70 | 50 | 85 |
| 80 | 58 | 90 |
| 90 | 60 | 95 |
| Network Nodes | Multi Authentication Time levels | |
|---|---|---|
| NFbTMAN Model | NETAR Model | |
| 10 | 18 | 45 |
| 20 | 22 | 60 |
| 30 | 25 | 62 |
| 40 | 30 | 65 |
| 50 | 35 | 70 |
| 60 | 38 | 75 |
| 70 | 40 | 82 |
| 80 | 40 | 95 |
| 90 | 42 | 98 |
| Network Nodes | Packet Delivery Rate | |
|---|---|---|
| NFbTMAN Model | NETAR Model | |
| 10 | 55 | 15 |
| 20 | 60 | 20 |
| 30 | 65 | 22 |
| 40 | 70 | 25 |
| 50 | 75 | 30 |
| 60 | 80 | 35 |
| 70 | 85 | 40 |
| 80 | 90 | 50 |
| 90 | 95 | 55 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bondada, P.; Samanta, D.; Chaudhry, S.A.; Zikria, Y.B.; Ishmanov, F. Efficient Neighbour Feedback Based Trusted Multi Authenticated Node Routing Model for Secure Data Transmission. Sustainability 2021, 13, 13296. https://doi.org/10.3390/su132313296
Bondada P, Samanta D, Chaudhry SA, Zikria YB, Ishmanov F. Efficient Neighbour Feedback Based Trusted Multi Authenticated Node Routing Model for Secure Data Transmission. Sustainability. 2021; 13(23):13296. https://doi.org/10.3390/su132313296
Chicago/Turabian StyleBondada, Praveen, Debabrata Samanta, Shehzad Ashraf Chaudhry, Yousaf Bin Zikria, and Farruh Ishmanov. 2021. "Efficient Neighbour Feedback Based Trusted Multi Authenticated Node Routing Model for Secure Data Transmission" Sustainability 13, no. 23: 13296. https://doi.org/10.3390/su132313296
APA StyleBondada, P., Samanta, D., Chaudhry, S. A., Zikria, Y. B., & Ishmanov, F. (2021). Efficient Neighbour Feedback Based Trusted Multi Authenticated Node Routing Model for Secure Data Transmission. Sustainability, 13(23), 13296. https://doi.org/10.3390/su132313296








