Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization
Abstract
:1. Introduction
- A method for data clustering based on the MFO is presented;
- The quality of the solutions provided by the suggested technique is compared to three well-known algorithms to determine which is superior;
- A total of five statistical tests have been conducted using different grid sizes to evaluate the proposed approach’s statistical quality;
- The use of k-means density and the MRCQ approach for data compression has been employed to improve the CH selection process;
- Experimental and statistical graphs demonstrate the effectiveness of the suggested technique.
2. Background and Motivation
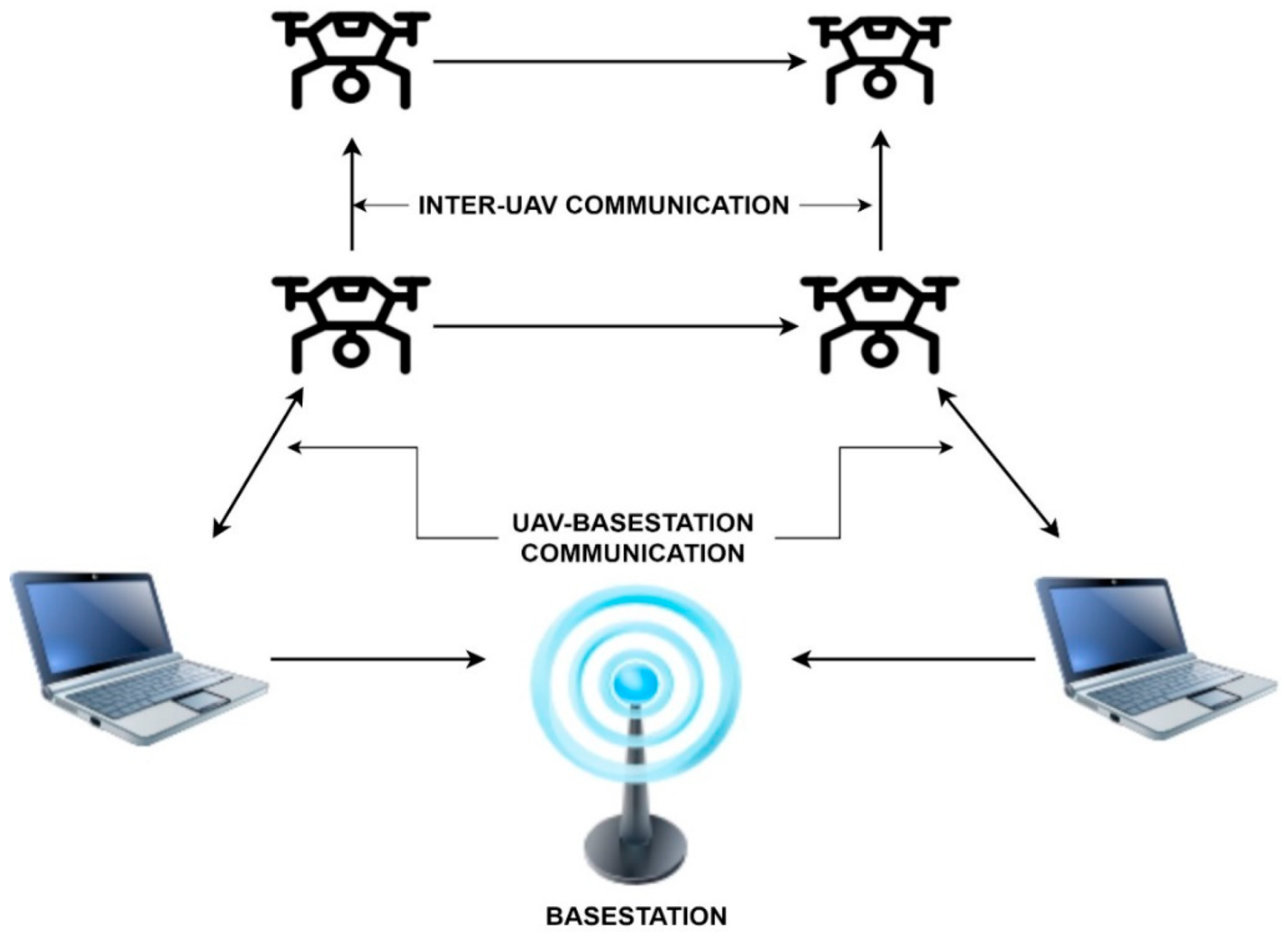
2.1. FANETS
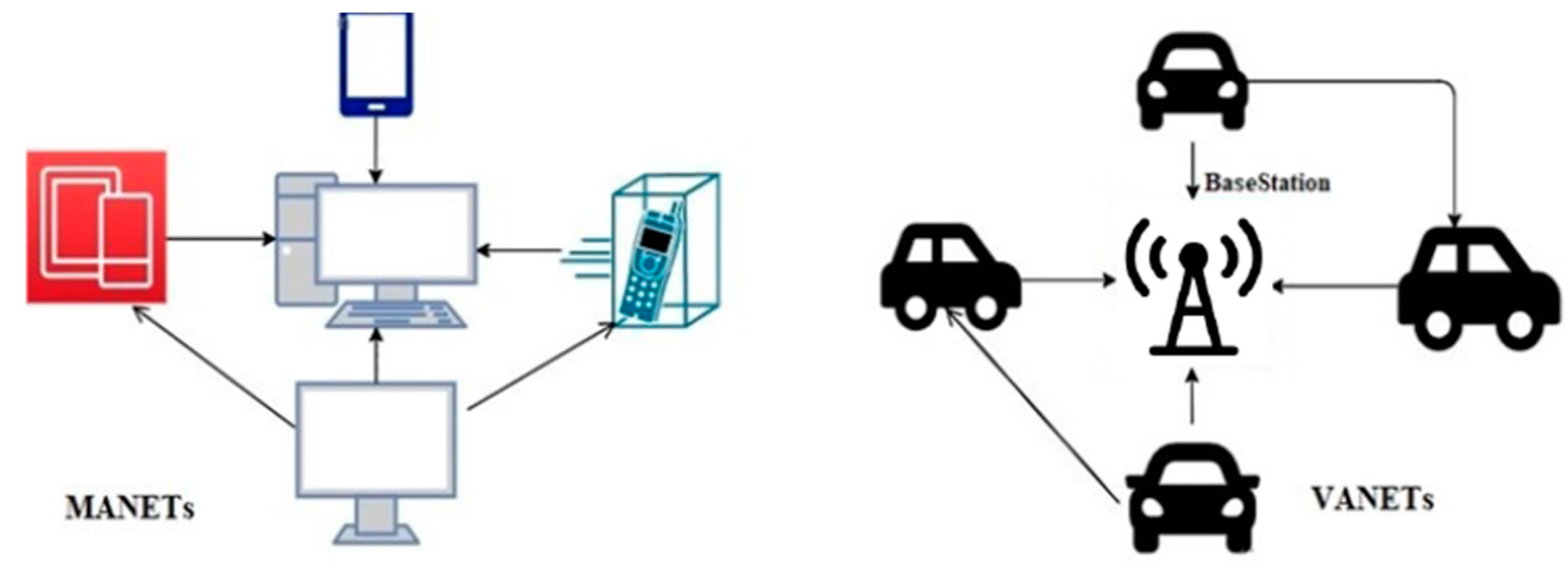
2.2. What Links Make FANETs, Different from MANETs, and VANETs?
- There are now many ad hoc networks striving to connect. For example, Wireless sensor networks make extensive use of these technologies for gathering and transmitting data about the surrounding environment [24]. Peer-to-peer and broadcast traffic must be allowed simultaneously for FANET to work effectively.
- The Distances between FANET and FANETS nodes are much longer than the distances between the two networks [12,13,24]. Unmanned aerial vehicles (UAVs) need a more extended communication range than either MANETs or VANETs if they are to be linked together. Consequently, radio links, hardware circuits, and physical layer behaviour are all impacted.
- Multi-UAV systems may contain various types of sensors, each of which may need a separate data transmission strategy [19].
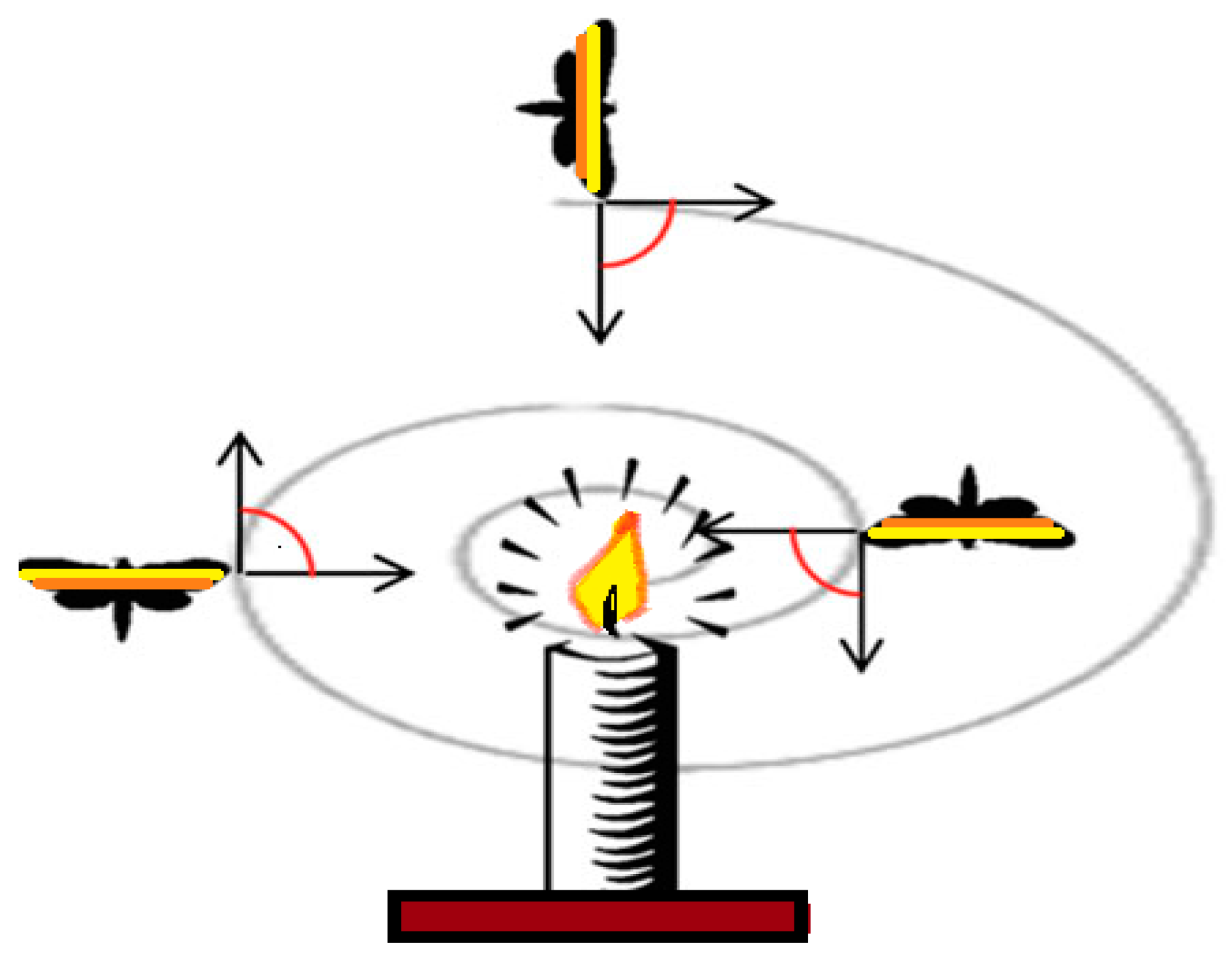
2.3. What’s the Roles of Bioinspired Algorithms in FANETs?
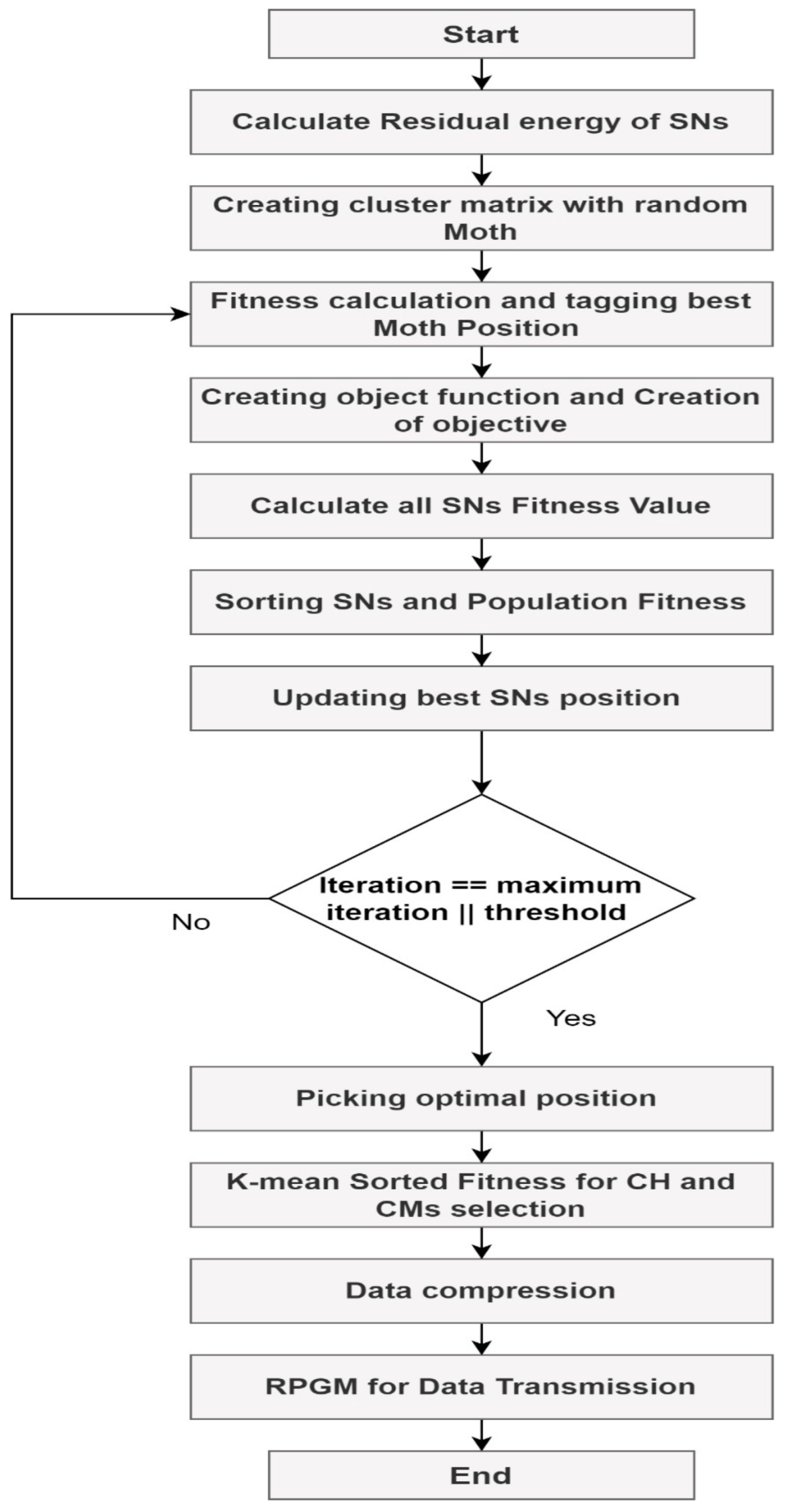
3. Proposed Methodology
3.1. Network Building and Nodes Positioning
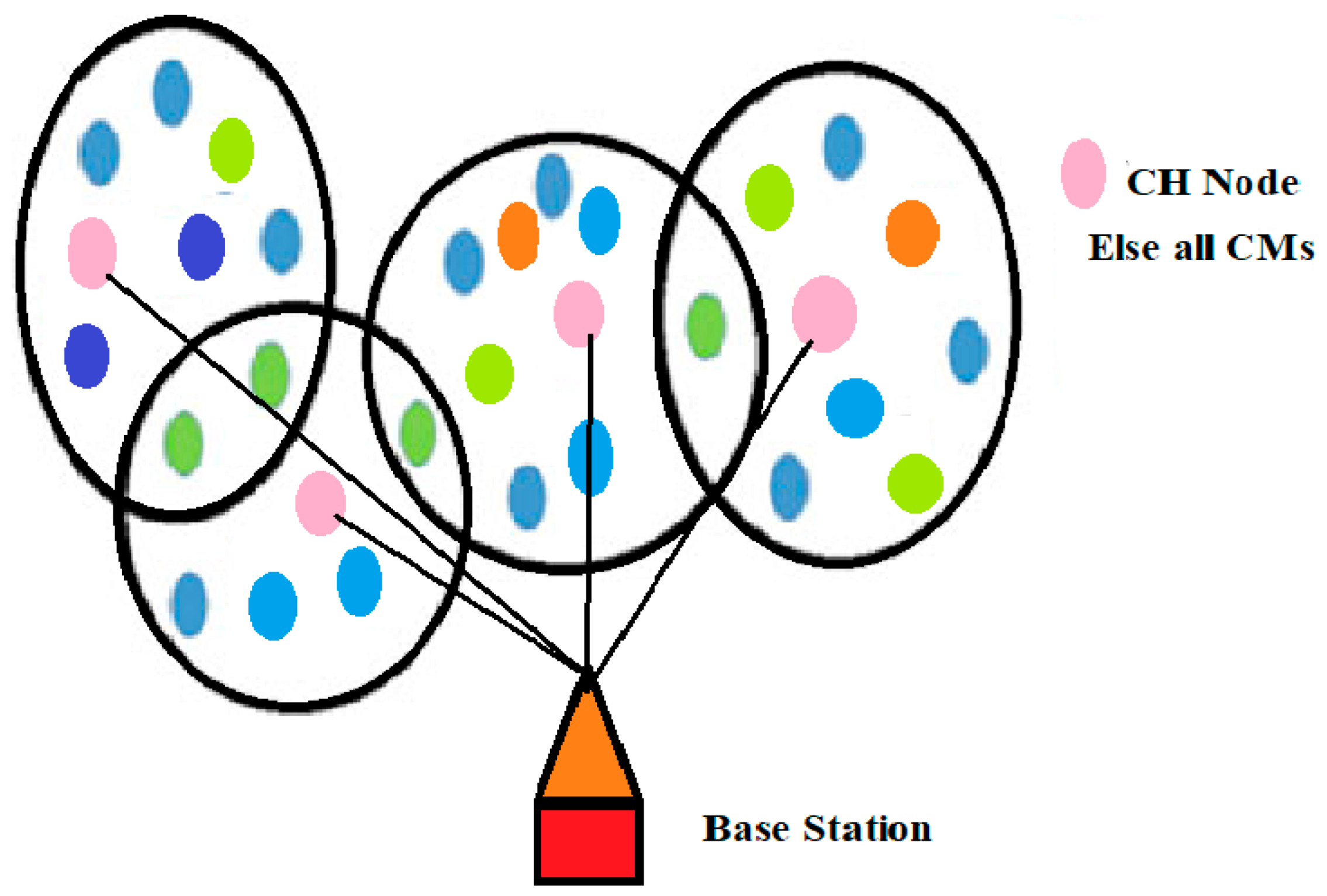
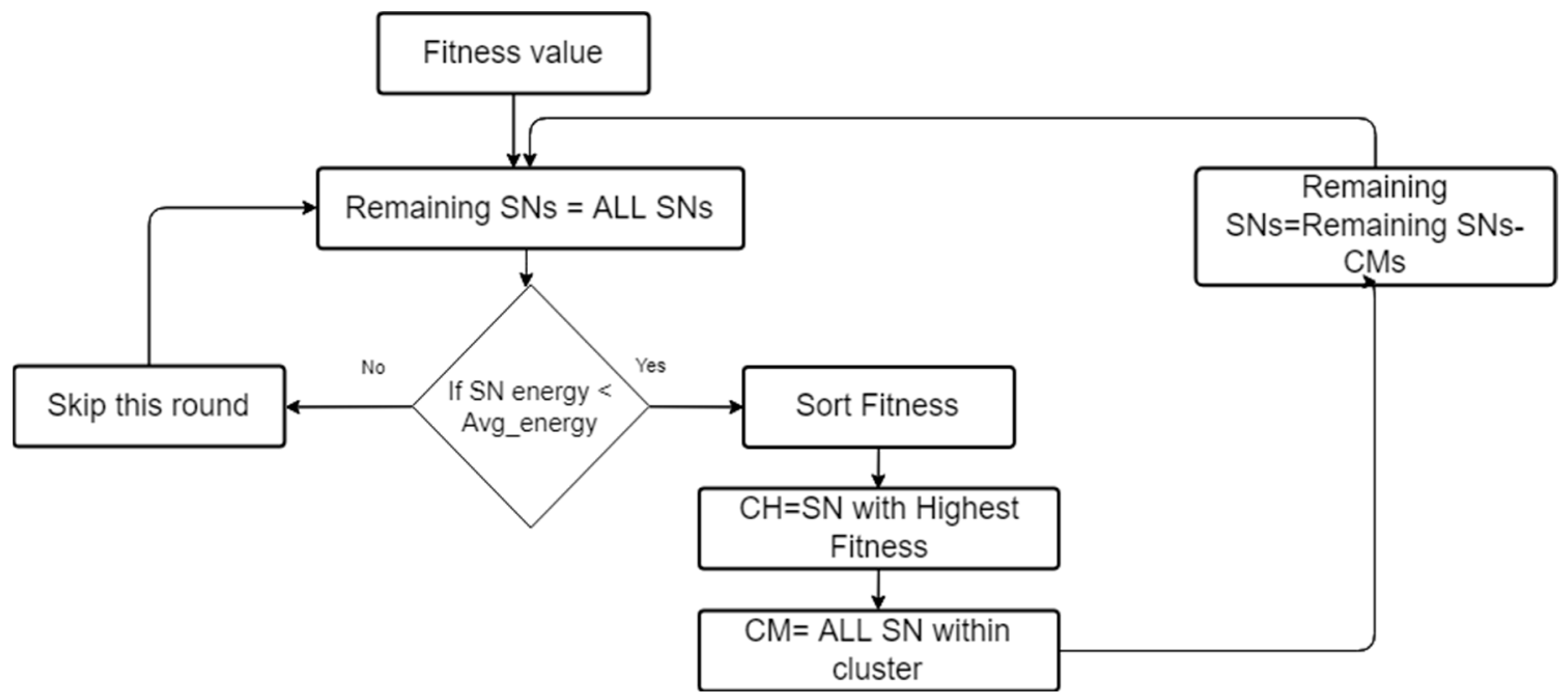
3.2. Cluster Formulation and CH selection with K-Means Sorted Fitness
3.3. Data Compression and Network Commination
- Data compressionOur proposed protocol is used for captured data, primarily images and videos. So, to reduce the data transmission energy, we need to use a compression algorithm. Our proposed protocol uses MRCQ (multi-resolution compression and query) image-based compression approach [26]. Sensor nodes are organized in a hierarchy to establish multiresolution summaries of sensed data in the network [11]. Lower-resolution summaries are transmitted to the sink, whereas high-resolution outlines remain in the network and can be accessed for further analysis [32]. As a result, MRCQ has lower implementation costs and may be used with low-cost sensor systems [33,34].
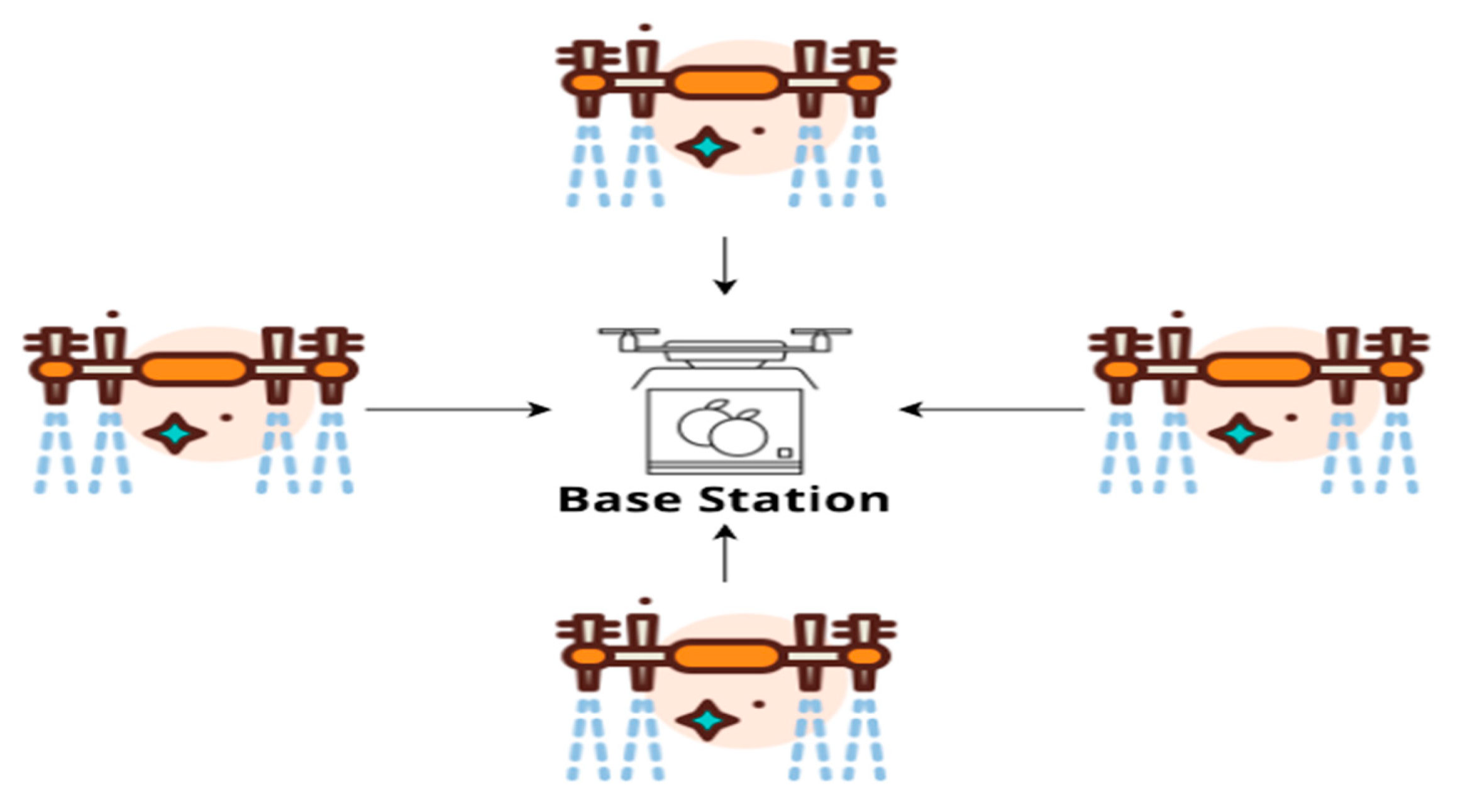
- Node Movement and Network CommunicationsCommunication and data transfer between nodes begin when clustering is complete. Whether a node inside a cluster [35], a node across the cluster, or the base station is the intended destination for the data, the CH is responsible for getting it there [36,37]. EECP-MFO adheres to the RPGM [38] reference point group mobility model. There is a point of reference for all nodes in RPGM that they all will follow. EECP-MFO considers a reference point for the CHs, and all CMs adjust their positions under how their respective CHs move.
4. Experimental Results and Analysis
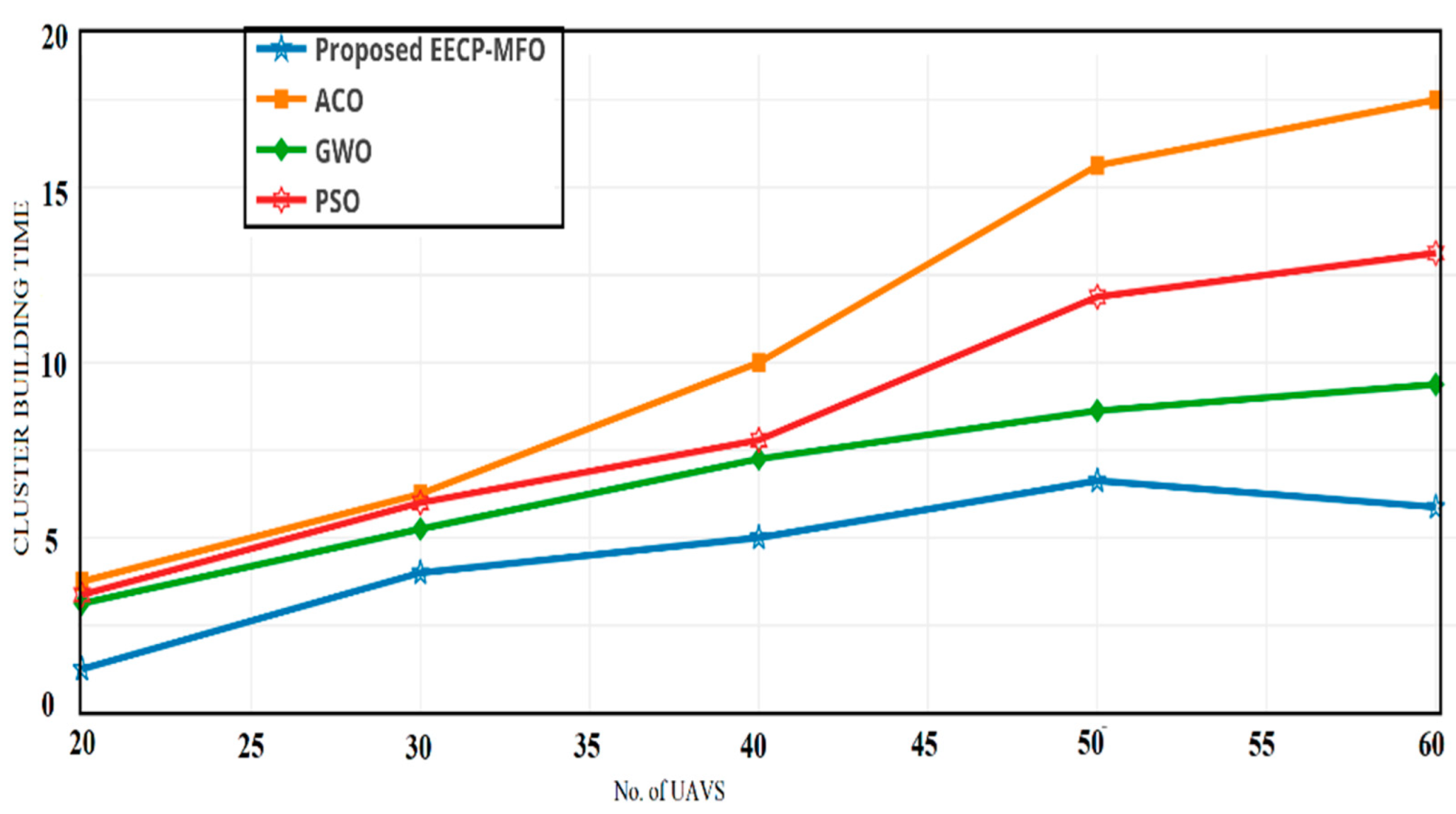
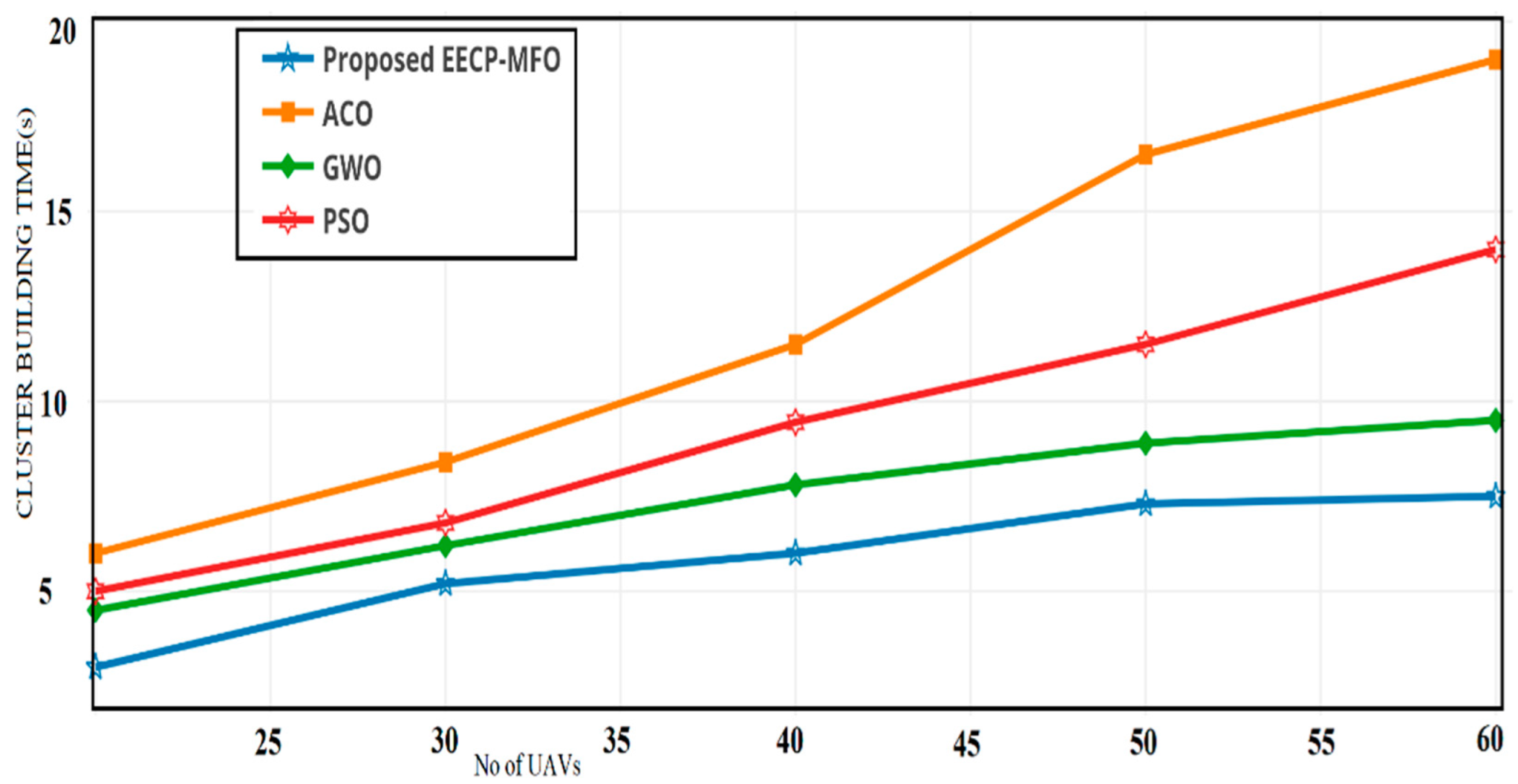
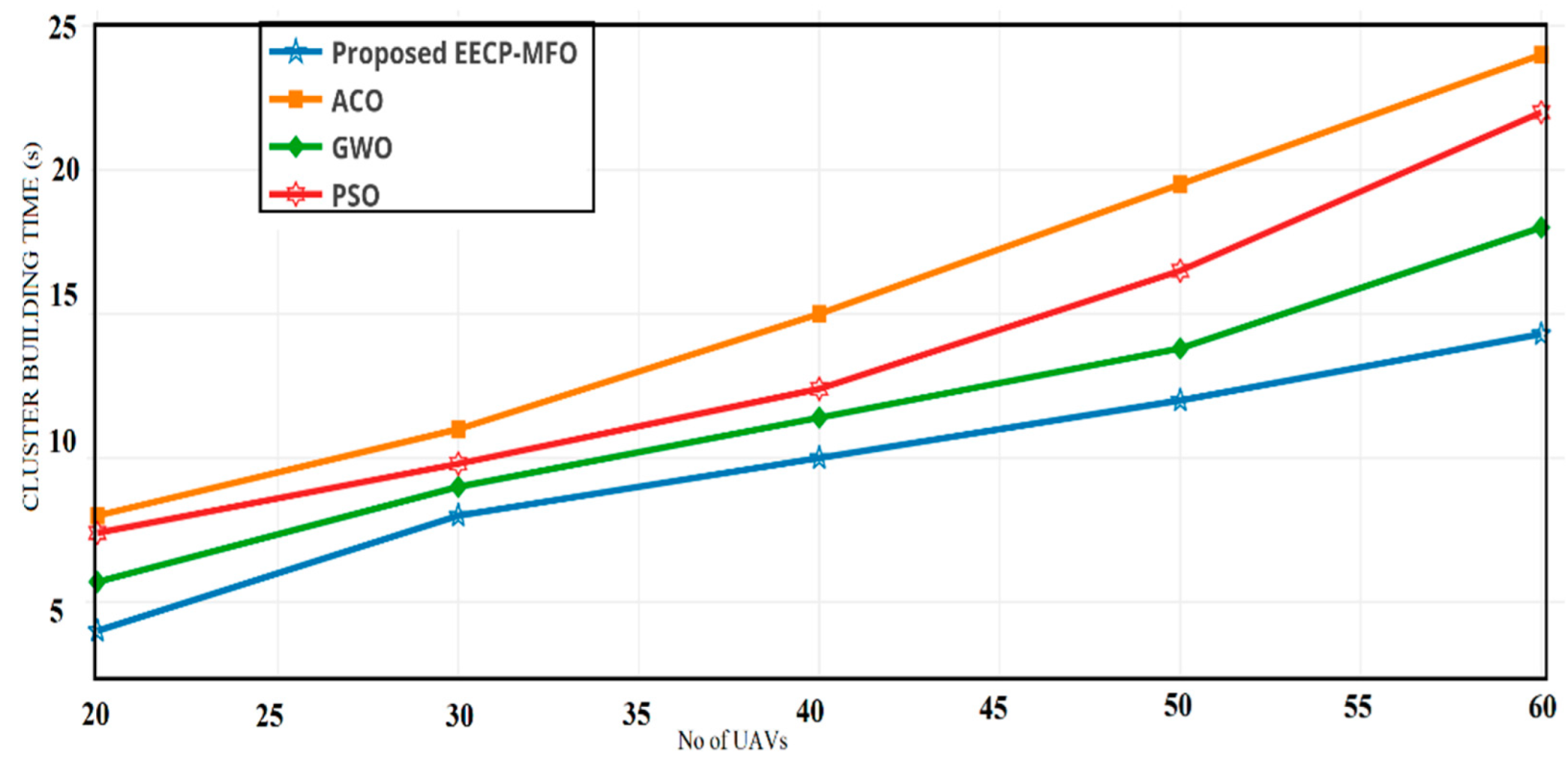
4.1. Cluster Building Time
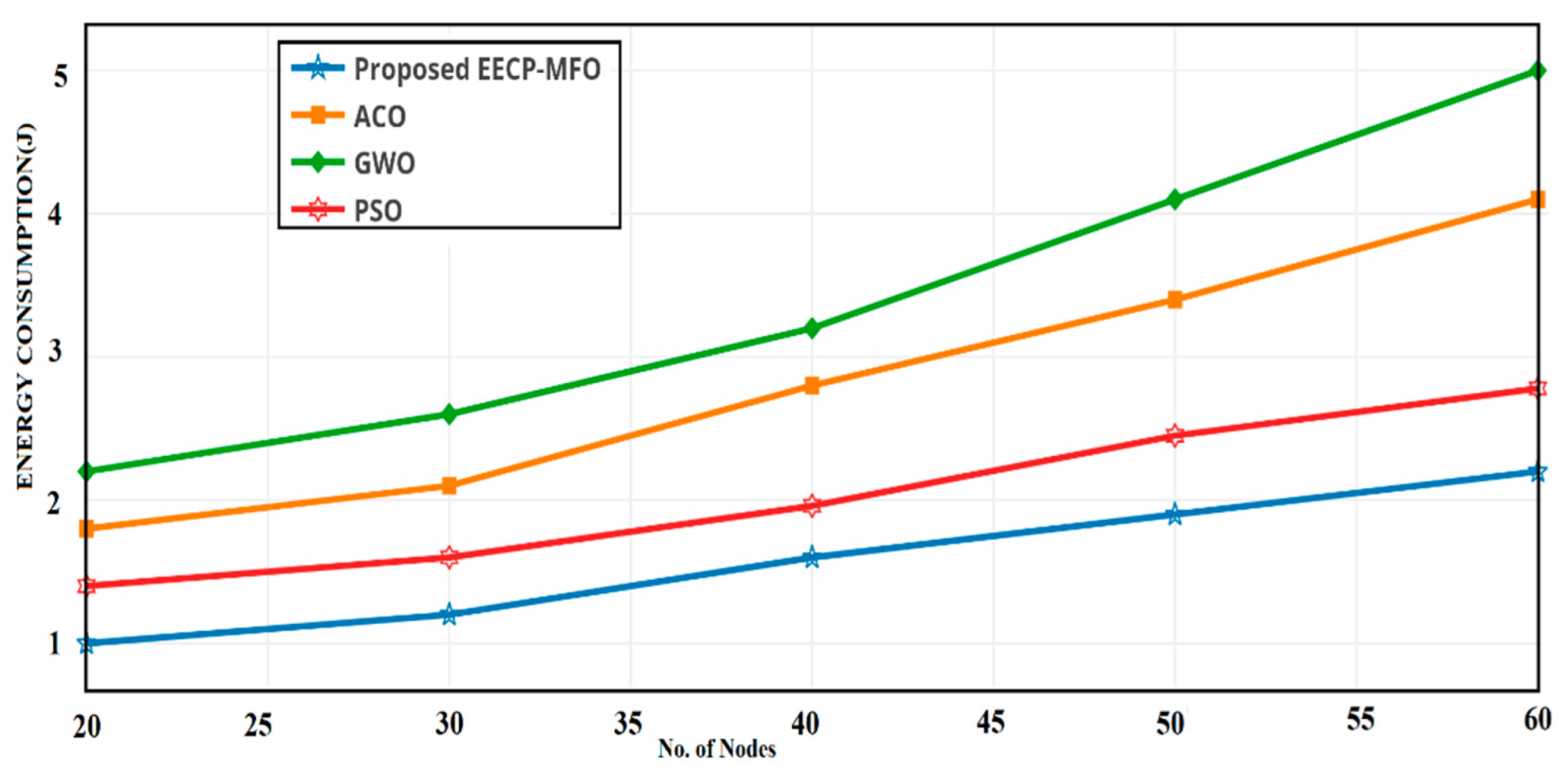
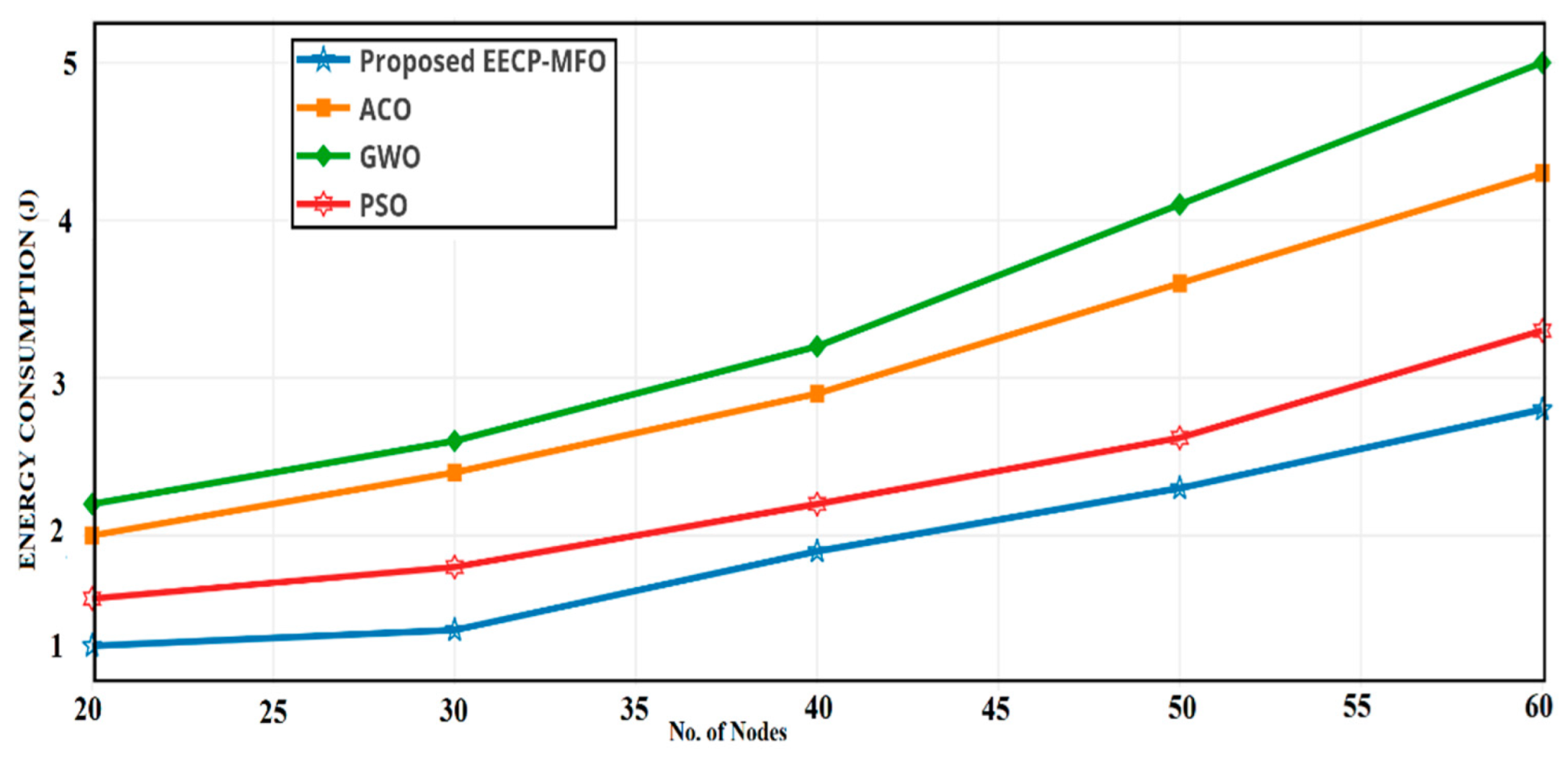
4.2. Energy Consumption
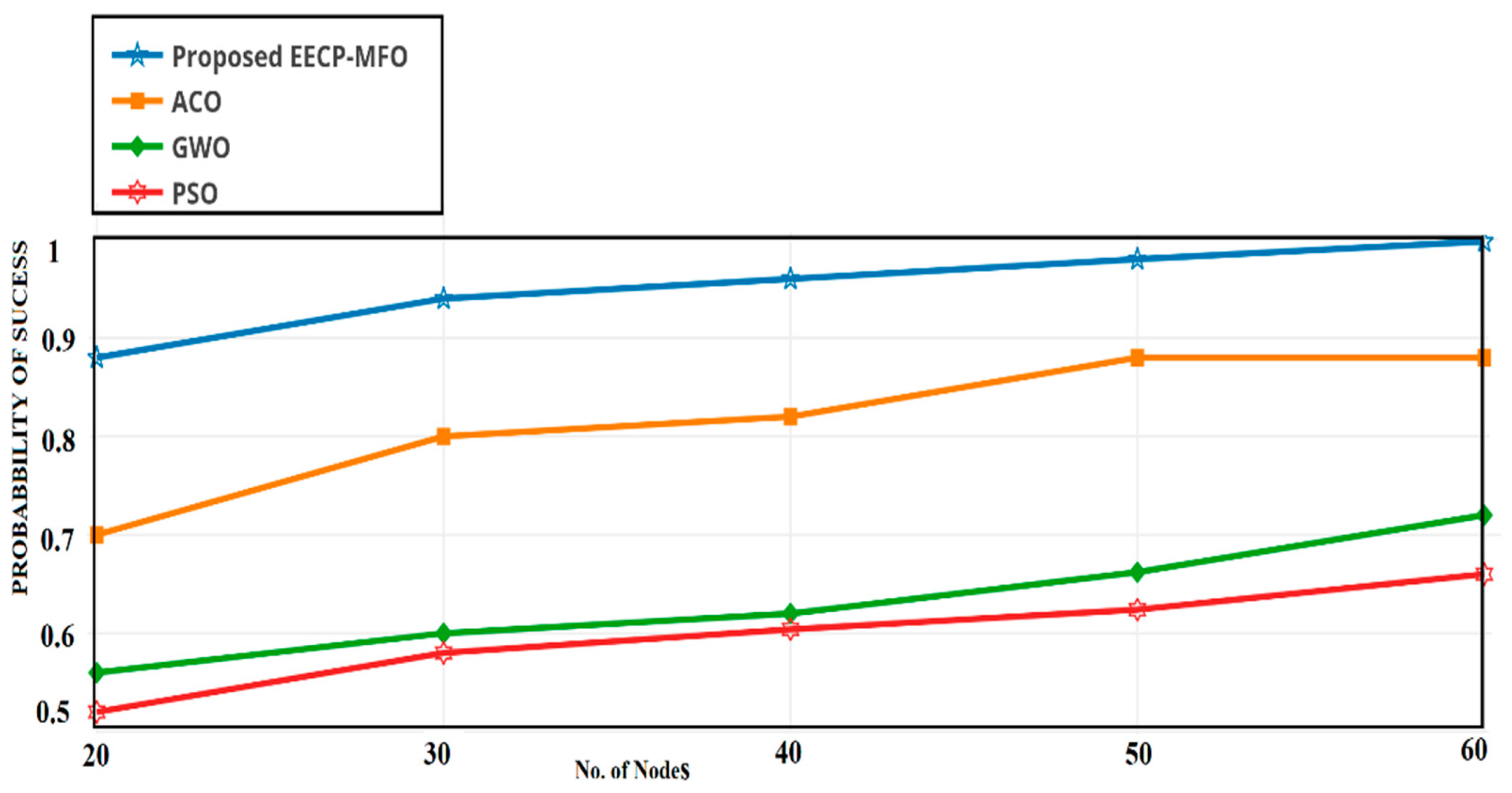
4.3. Probability of Success
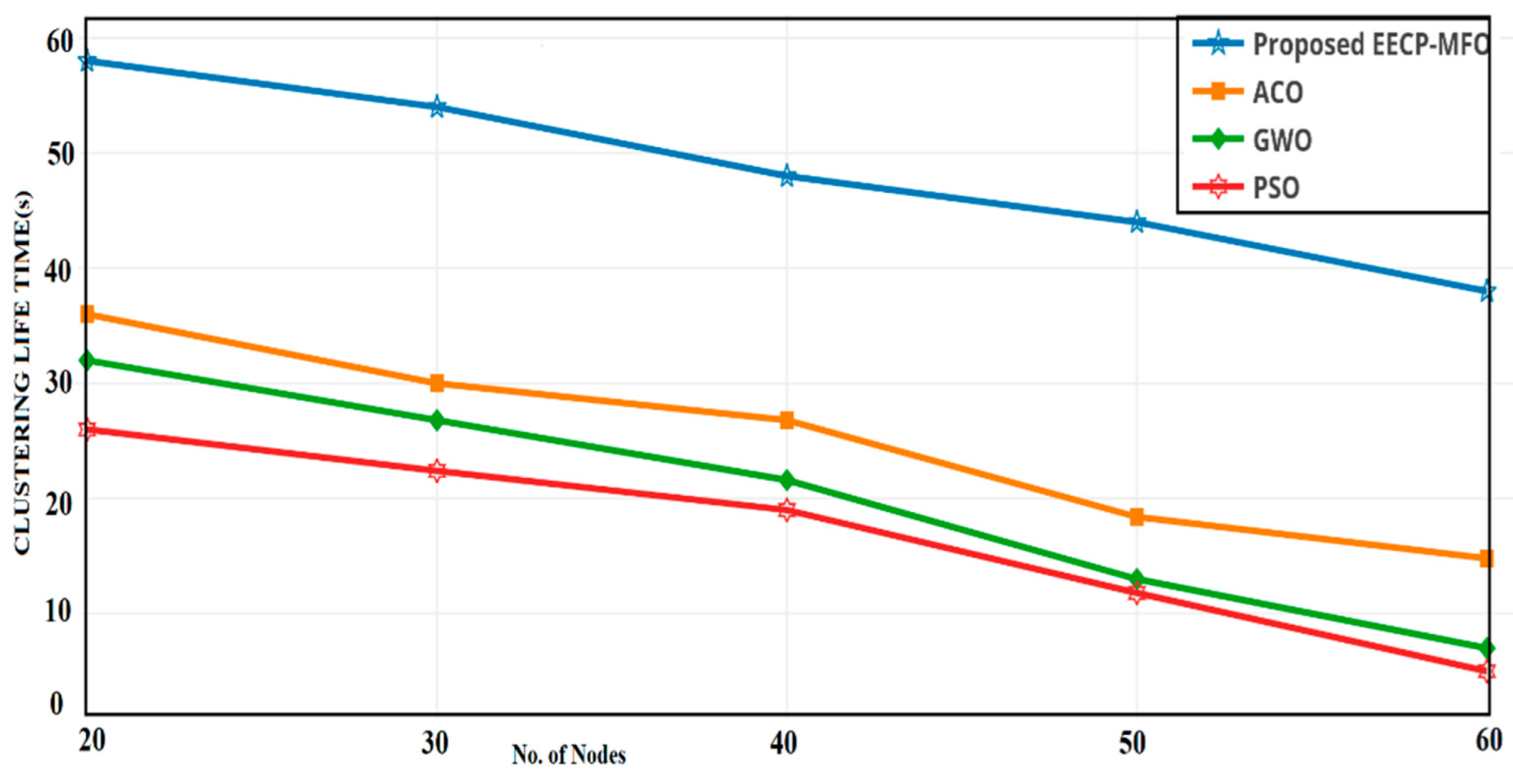
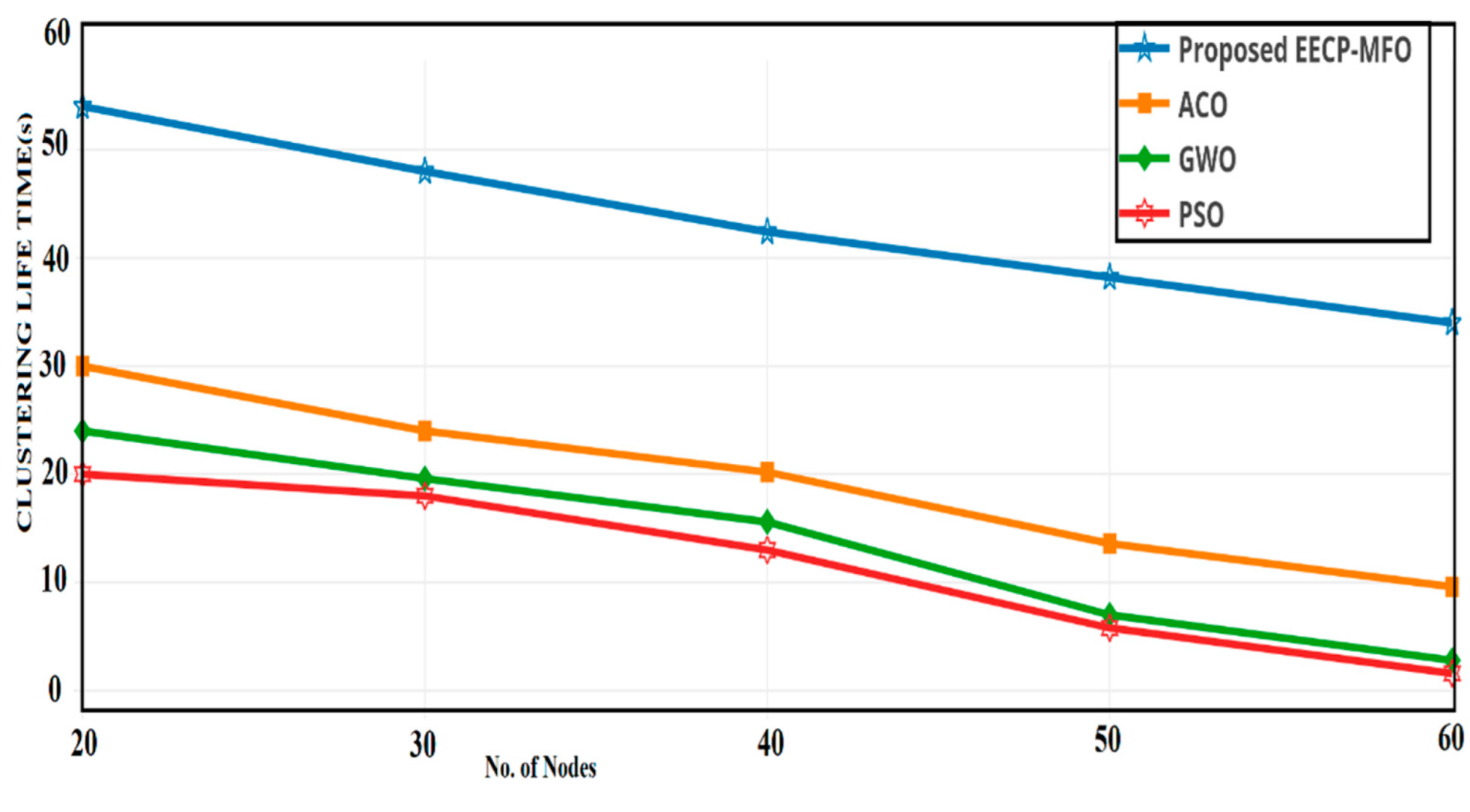
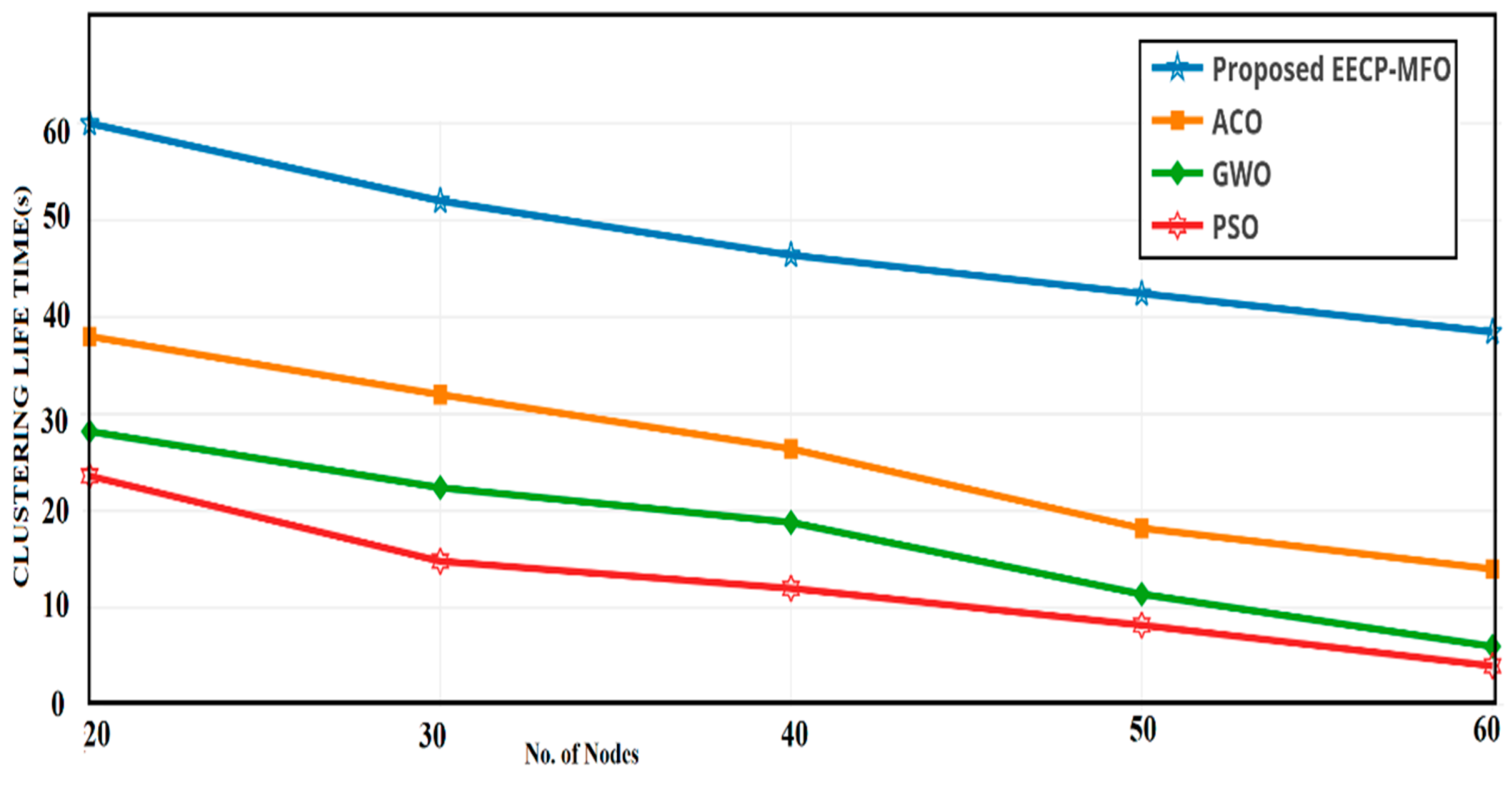
4.4. Cluster Lifetime
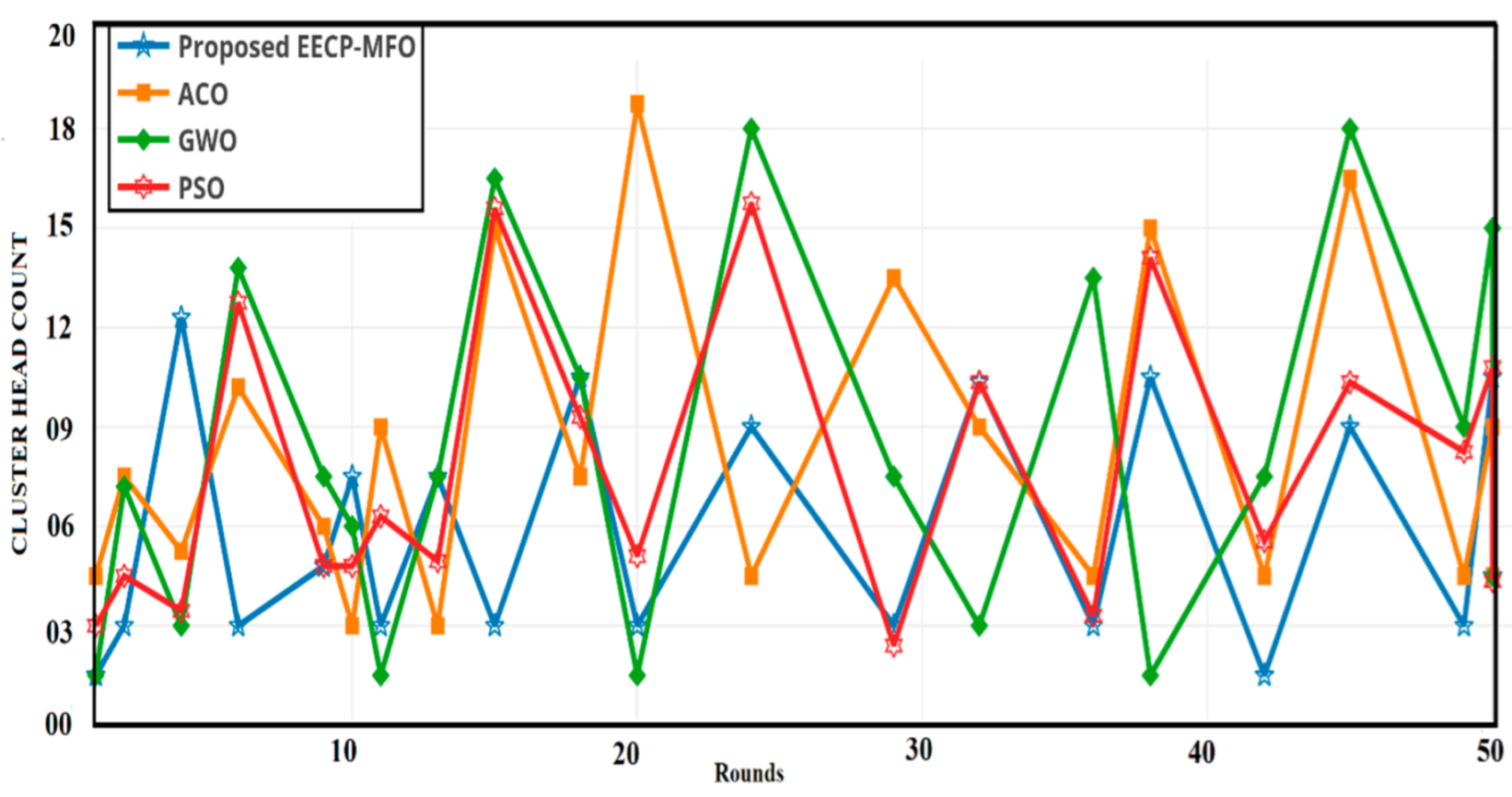
4.5. Consistency of Cluster Heads
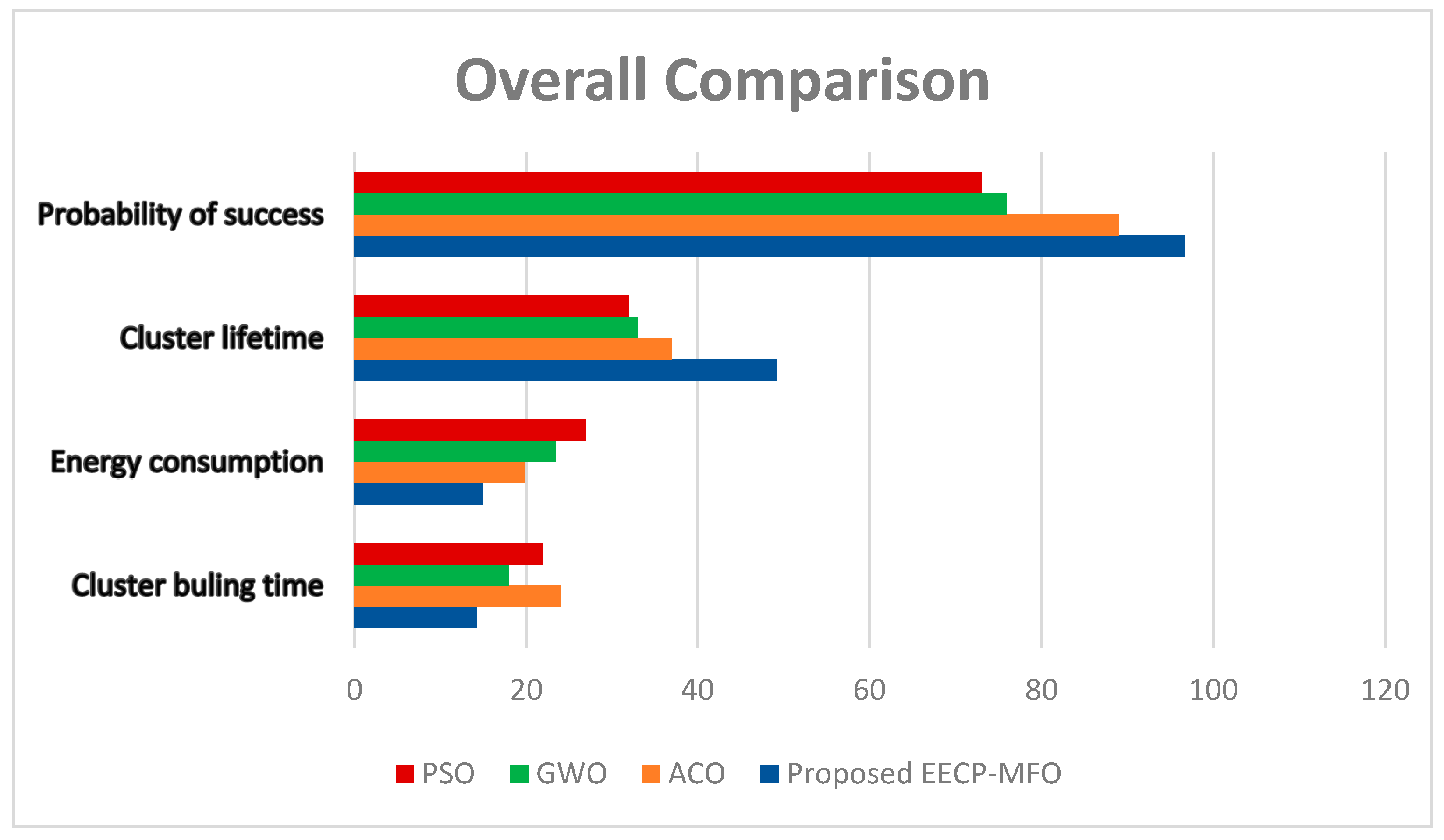
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Tariq, R.; Iqbal, Z.; Aadil, F. IMOC: Optimization technique for drone-assisted VANET (DAV) based on moth flame optimization. Wirel. Commun. Mob. Comput. 2020, 1–29. [Google Scholar] [CrossRef]
- Aadil, F.; Raza, A.; Khan, M.F.; Maqsood, M.; Mehmood, I.; Rho, S. Energy aware cluster-based routing in flying ad-hoc networks. Sensors 2018, 18, 1413. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-efficient clustering scheme for flying ad-hoc networks using an optimized LEACH protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Han, X.; Quan, L.; Xiong, X.; Almeter, M.; Xiang, J.; Lan, Y. A novel data clustering algorithm based on modified gravitational search algorithm. Eng. Appl. Artif. Intell. 2017, 61, 1–7. [Google Scholar] [CrossRef]
- Bhatia, S.; Alam, S.; Shuaib, M.; Alhameed, M.H.; Jeribi, F.; Alsuwailem, R.I. Retinal Vessel Extraction via Assisted Multi-Channel Feature Map and U-Net. Front. Public Health 2022, 10, 355. [Google Scholar] [CrossRef] [PubMed]
- Tavazoei, M.S.; Haeri, M. Comparison of different one-dimensional maps as chaotic search pattern in chaos optimization algorithms. Appl. Math. Comput. 2007, 187, 1076–1085. [Google Scholar] [CrossRef]
- Alazab, M.; Lakshmanna, K.; Reddy, T.; Pham, Q.V.; Maddikunta, P.K.R. Multi-objective cluster head selection using fitness averaged rider optimization algorithm for IoT networks in smart cities. Sustain. Energy Technol. Assess. 2021, 43, 100973. [Google Scholar] [CrossRef]
- Shi, N.; Luo, X. A novel cluster-based location-aided routing protocol for UAV fleet networks. Int. J. Digit. Content Technol. Appl. 2012, 6, 376. [Google Scholar]
- Esmin, A.A.A.; Coelho, R.A.; Matwin, S. A review on particle swarm optimization algorithm and its variants to clustering high-dimensional data. Artif. Intell. Rev. 2015, 44, 23–45. [Google Scholar] [CrossRef]
- Yang, D.; Li, G.; Cheng, G. On the efficiency of chaos optimization algorithms for global optimization. Chaos Solitons Fractals 2007, 34, 1366–1375. [Google Scholar] [CrossRef]
- Zang, C.; Zang, S. Mobility prediction clustering algorithm for UAV networking. In 2011 IEEE Globecom Workshops (GC Wkshps); IEEE: Piscataway, NJ, USA, 2011; pp. 1158–1161. [Google Scholar]
- Bhushan, B.; Sahoo, G. Recent Advances in Attacks, Technical Challenges, Vulnerabilities and Their Countermeasures in Wireless Sensor Networks. Wirel. Pers. Commun. 2018, 98, 2037–2077. [Google Scholar] [CrossRef]
- Haque, A.K.M.B.; Bhushan, B.; Dhiman, G. Conceptualizing smart city applications: Requirements, architecture, security issues, and emerging trends. Expert Syst. 2021. [Google Scholar] [CrossRef]
- Mirjalili, S. Dragonfly algorithm: A new meta-heuristic optimization technique for solving single-objective, discrete, and multi-objective problems. Neural Comput. Appl. 2016, 27, 1053–1073. [Google Scholar] [CrossRef]
- Haider, B.; Henna, S.; Gul, A.; Aadil, F. A survey on mobility management techniques in VANETs. In 2016 IEEE International Conference on Computer and Information Technology (CIT), Nadi, Fiji, 8–10 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 125–133. [Google Scholar]
- Aadil, F.; Rizwan, S.; Akram, A. Vehicular Ad Hoc Networks (VANETs), Past Present and Future: A Survey; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Arif, M.; Rahmani, K.I. Adaptive ARA (AARA) for MANETs. In 2012 Nirma University International Conference on Engineering (NUiCONE), Ahmedabad, India, 6–8 December 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 1–6. [Google Scholar]
- Sharma, R.; Kaushik, B.; Gondhi, N.K.; Tahir, M.; Rahmani, M.K.I. Quantum Particle Swarm Optimization Based Convolutional Neural Network for Handwritten Script Recognition. Comput. Mater. Contin. 2022, 71. [Google Scholar] [CrossRef]
- Ishtiaq, S.; Majeed, N.; Maqsood, M.; Javed, A. Improved scalable recommender system. Nucleus 2016, 53, 200–207. [Google Scholar]
- Aadil, F.; Bajwa, K.B.; Khan, S.; Chaudary, N.M.; Akram, A. CACONET: Ant colony optimization (ACO) based clustering algorithm for VANET. PLoS ONE 2016, 11, e0154080. [Google Scholar] [CrossRef] [Green Version]
- Aadil, F.; Khan, S.; Bajwa, K.B.; Khan, M.F.; Ali, A. Intelligent clustering in vehicular ad hoc networks. KSII Trans. Internet Inf. Syst. (TIIS) 2016, 10, 3512–3528. [Google Scholar]
- Aadil, F.; Ahsan, W.; Rehman, Z.U.; Shah, P.A.; Rho, S.; Mehmood, I. Clustering algorithm for internet of vehicles (IoV) based on dragonfly optimizer (CAVDO). J. Supercomput. 2018, 74, 4542–4567. [Google Scholar] [CrossRef]
- Aldabbagh, G.; Shah, P.A.; Hasbullah, H.B.; Aadil, F.; Awan, K.M.; Marwat, F. Fuzzy logic based enhanced AOMDV with link status classification for efficient multi-path routing in multi-hop wireless networks. J. Comput. Theor. Nanosci. 2017, 14, 620–630. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. E2SR2: An acknowledgement-based mobile sink routing protocol with rechargeable sensors for wireless sensor networks. Wirel. Netw. 2019, 25, 2697–2721. [Google Scholar] [CrossRef]
- Mirjalili, S.; Mirjalili, S.M.; Lewis, A. Grey wolf optimizer. Adv. Eng. Softw. 2014, 69, 46–61. [Google Scholar] [CrossRef] [Green Version]
- Wang, Y.-C.; Hsieh, Y.-Y.; Tseng, Y.-C. Multiresolution spatial and temporal coding in a wireless sensor network for long-term monitoring applications. IEEE Trans. Comput. 2009, 58, 827–838. [Google Scholar] [CrossRef]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Mashat, A.; Kumar, A.; Kumar, M. Self-Sovereign Identity Solution for Blockchain-Based Land Registry System: A Comparison. Mob. Inf. Syst. 2022, 2022, 8930472. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient communication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2000. [Google Scholar]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef] [Green Version]
- Rahmani, M.K.I.; Ansari, M.A. A color based fuzzy algorithm for CBIR. IET Conf. Publ. 2013. [Google Scholar] [CrossRef]
- Rahmani, M.K.I.; Pal, N.; Arora, K. Clustering of Image Data Using K-Means and Fuzzy K-Means. Int. J. Adv. Comput. Sci. Appl. 2014, 5. [Google Scholar] [CrossRef] [Green Version]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Koundal, D.; Mashat, A.; Belay, A. Identity Model for Blockchain-Based Land Registry System: A Comparison. Wirel. Commun. Mob. Comput. 2022, 2022, 5670714. [Google Scholar] [CrossRef]
- Naeem, A.; Javed, A.R.; Rizwan, M.; Abbas, S.; Lin, J.C.-W.; Gadekallu, T.R. DARE-SEP: A Hybrid Approach of Distance Aware Residual Energy-Efficient SEP for WSN. IEEE Trans. Green Commun. Netw. 2021, 5, 611–621. [Google Scholar] [CrossRef]
- Reddy, T.; Swarna Priya, R.M.; Parimala, M.; Chowdhary, L.C.; Hakak, S.; Khan, Z.W. A deep neural networks based model for uninterrupted marine environment monitoring. Comput. Commun. 2020, 157, 64–75. [Google Scholar]
- Guerrero-Sánchez, M.E.; Abaunza, H.; Castillo, P.; Lozano, R.; García-Beltrán, C.D. Quadrotor Energy-Based Control Laws: A Unit-Quaternion Approach. J. Intell. Robot. Syst. 2017, 88, 347–377. [Google Scholar] [CrossRef]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Agarwal, P.; Idrees, S.M. Land Registry Framework Based on Self-Sovereign Identity (SSI) for Environmental Sustainability. Sustainability 2022, 14, 5400. [Google Scholar] [CrossRef]
- Rahmani, M.K.I. A graphical approach for image retrieval based on five layered CNNs model. In 2021 5th International Joint Conference on Advances in Computational Intelligence (IJCACI 2021), Online, 23–24 October 2021; Jahangirnagar University: Dhaka, Bangladesh, 2021; p. 12. [Google Scholar]
- Hong, X.; Gerla, M.; Pei, G.; Chiang, C.-C. A group mobility model for ad hoc wireless networks. In Proceedings of the 2nd ACM International Workshop on Modeling, Analysis and Simulation of Wireless and Mobile Systems, New York, NY, USA, 20 August 1999; pp. 53–60. [Google Scholar]
- Xiao, X.; Jin, L.; Yang, Y.; Yang, W.; Sun, J.; Chang, T. Building fast and compact convolutional neural networks for offline handwritten Chinese character recognition. Pattern Recognit. 2017, 72, 72–81. [Google Scholar] [CrossRef] [Green Version]
- Alam, S.; Shuaib, M.; Khan, Z.W.; Garg, S.; Kaddoum, G.; Hossain, S.M.; Zikria, B.Y. Blockchain-based Initiatives: Current state and challenges. Comput. Netw. 2021, 198, 108395. [Google Scholar] [CrossRef]
- Iwendi, C.; Jalil, Z.; Javed, A.R.; Reddy, T.; Kaluri, R.; Srivastava, G.; Jo, O. Keysplitwatermark: Zero watermarking algorithm for software protection against cyber-attacks. IEEE Access 2020, 8, 72650–72660. [Google Scholar] [CrossRef]
- Gadamsetty, S.; Ch, R.; Ch, A.; Iwendi, C.; Gadekallu, T.R. Hash-based deep learning approach for remote sensing satellite imagery detection. Water 2022, 14, 707. [Google Scholar] [CrossRef]


| Protocol | Year | Network Type | Cluster Method | Complexity | No of CH’s | No of Nodes in Cluster | Mobility | Energy Efficiency |
|---|---|---|---|---|---|---|---|---|
| LEACH | 2000 | Homogenous | Distributed | Low | Uncertain | Unforeseeable | Inactive | Yes |
| LEACH-C | 2002 | heterogenous | Centralized | Low | Certain | Unforeseeable | Inactive | Yes |
| CBLADSR | 2012 | Heterogenous | Distributed | High | Uncertain | Unforeseeable | Inactive | Yes |
| CACONET | 2016 | Homogenous/heterogenous | Centralized | High | Uncertain | Unforeseeable | Inactive | Yes |
| PSONET | 2011 | Homogenous/heterogenous | Centralized | Very high | Uncertain | Unforeseeable | Inactive | Yes |
| GWOCNET | 2014 | Homogenous/heterogenous | Centralized | Very high | Uncertain | Unforeseeable | Inactive | Yes |
| CAVDO | 2018 | Heterogenous | Distributed | Medium | Uncertain | Unforeseeable | Inactive | Yes |
| Protocol | Energy model | Location Awareness | Connectivity to Bs | Link Quality Based | Connection Awareness | Collison Avoidance | Position of Base Station | Deployment Mode |
|---|---|---|---|---|---|---|---|---|
| LEACH | First order | No | Singe hop | Distance | No | No | Outside | Random |
| LEACH-C | First order | Yes | Singe hop | Distance | No | No | Outside | Random |
| CBLADSR | First order | No | Singe hop | Distance | Partially | No | Outside | Random and uniform |
| CACONET | First order | Yes | Singe hop | Distance | No | No | Outside | Random |
| PSONET | First order | Yes | Singe hop | Distance | No | No | Outside | Random |
| GWOCNET | First order | No | Singe hop | Distance | No | No | Outside | Random |
| CAVDO | First order | No | Singe hop | Distance | Partially | No | Outside | Random and non-uniform |
| Parameters | Values |
|---|---|
| Grid Size | 1000 × 1000 m2, 2000 × 2000 m2 and 3000 × 3000 m2 |
| Density of Connected Nodes | 20, 30, 40, 50, 60 |
| Minimum Distance Between Nodes | 5 m |
| Mobility Model | Reference Point Mobility Model |
| Simulation Runs | 10 |
| Simulation Time | 120 s |
| Position Exchange Interval | 2 s |
| Node Energy Level at Start Time | 80-Watt Hour |
| Transmission Range | Dynamic |
| Transmission Frequency | 2.45 GHz |
| Constant Bit Rate | 100 kbps |
| Receiver Sensitivity | −90 dBm |
| W1 +W2 + W3 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bharany, S.; Sharma, S.; Bhatia, S.; Rahmani, M.K.I.; Shuaib, M.; Lashari, S.A. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability 2022, 14, 6159. https://doi.org/10.3390/su14106159
Bharany S, Sharma S, Bhatia S, Rahmani MKI, Shuaib M, Lashari SA. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability. 2022; 14(10):6159. https://doi.org/10.3390/su14106159
Chicago/Turabian StyleBharany, Salil, Sandeep Sharma, Surbhi Bhatia, Mohammad Khalid Imam Rahmani, Mohammed Shuaib, and Saima Anwar Lashari. 2022. "Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization" Sustainability 14, no. 10: 6159. https://doi.org/10.3390/su14106159
APA StyleBharany, S., Sharma, S., Bhatia, S., Rahmani, M. K. I., Shuaib, M., & Lashari, S. A. (2022). Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability, 14(10), 6159. https://doi.org/10.3390/su14106159








