1. Introduction
It is undeniable that supply chains and all involved stakeholders are called to face serious challenges that bring disorder to effective operations. Nowadays, the issue of counterfeiting seems to constitute one of the most critical and emerging challenges for the sustainability of a supply chain since its impact can be destructive both for human health and for a company’s economic viability. In fact, the complexity, and the high number of stakeholders along the supply chain render it more vulnerable in cases of falsifying actions. Counterfeiting can have multiple applications, but a counterfeited product is generally considered a product deliberately and fraudulently produced and/or mislabeled concerning its identity and/or source to make it appear genuine. Illegal products can be detected in every step of the supply chain, and unfortunately, this phenomenon occurs in several industry sectors. Tampered goods can usually occur in the foods and spirits industry, while also quite frequently, spurious drugs have been uncovered in the health sector. These two fields seem to be highly prone to such pathogenies, while the fields of clothing, electronics, automotive, logistics, and luxury goods have also started to be targeted.
The implications of an imitated product can vary from simple symptoms to serious health issues-even to death in extreme situations. Except for the health harm, the financial cost for the industry and the whole economy, in the end, is in no way negligible. The unfair competition, usually cultivated by illegal actions, may negatively influence the brand name and lead to the customer’s loss of trust.
Approaching the issue of counterfeiting quantitatively, the volume of international trade in counterfeit products for 2016 amounted to 509 billion US dollars, or 3.3% of the total trade market, an increase of 0.8% compared to 2013, according to the latest study conducted jointly by the European Intellectual Property Office and the Organization for Economic Cooperation and Development [
1]. From the European Union’s point of view, illicit trade accounted for 6.8% of imports from non-EU countries in the same year, with China being the number one producer of counterfeit goods [
2]. Hong Kong and the United Arab Emirates complete the top three positions. In the European Union, it is estimated that around 790,000 jobs are lost annually due to counterfeiting, while lost public revenue (non-payment of income tax, VAT, and excise duties) is estimated at 14.3 billion euros [
3].
In order to overcome the issue of counterfeiting, an effective supply chain traceability system is necessary. A traceability system includes mechanisms for identifying, linking, recording, storing, verifying, and accessing information. The system consists of rules, procedures, and documentation and may require potential logistics and human resources. If a product is found to be faulty, the traceability system gives all of the information essential to conduct a successful recall of the problematic product or batch. Thus, it serves as a solution for ensuring the security and sustainability of businesses, their rapid reaction in times of crisis, their protection from malicious activities, and the overall improvement of operations via the discovery of root causes. Global and country regulations and standards regarding traceability and its implementation must be followed to implement such systems successfully. The Global Traceability Standard (GTS), through the nonprofit GS1, helps more than 100 countries effectively implement traceability systems. The ISO 22005: 2007 is another food and beverage traceability standard based on the general principles of system implementation and design. The adoption of specific standards helps improve a company’s internal processes and achieve safe and sustainable supply chains.
Research on traceability approaches for combating supply chain counterfeiting is relatively new as only during the last five years has it started to gain significant popularity. When reviewing the relevant research attempts, it becomes clear that a substantial number of solutions that differ based on the field of application have already been proposed. These solutions incorporate various techniques, methods, and technologies that could reduce or even eliminate supply chain counterfeiting. However, a coherent and effective classification and an interpretation of those solutions have yet to be performed. As a result, traceability research remains disordered as it is difficult to gain valuable guidelines for effectively solving the problem of counterfeiting. Today, an ever-growing interest is observed in research and operational projects aiming to overcome supply chain counterfeiting. This fact sets a strong need for structured works that can direct projects concerning what has been achieved by the researchers and the scientific community.
This paper aims to investigate the issue of counterfeiting in different industry sectors that directly affect consumers’ health and underline current trends and research directions through a systematic literature review. Furthermore, it aims to classify the detected traceability approaches and analyze the technological advancements that can be integrated into traceability systems for safe and sustainable supply chain operations. Therefore, this paper aims to create a detailed framework that can be used both by researchers and practitioners to detect the appropriate traceability approaches to combat product supply chain counterfeiting. This is why the paper not only creates a classification framework but also thoroughly discusses the literature review’s findings as per supply chain sector and traceability approaches.
The contribution of this paper is that it extends the analysis and classification down to the lowest levels of traceability approaches for combating supply chain counterfeiting. Therefore, a valuable framework is created to be used as a guideline for both researchers and practitioners in supply chains that aim for more safe and sustainable operations.
2. Materials and Methods
The first step in preparing a systematic literature review is to have a precise and transparent protocol for its implementation. This research aimed to investigate the research attempts related to the thematic axes of supply chain counterfeiting and traceability approaches. For a successful and comprehensive literature review, it is essential to define from the outset the databases that will be used to extract academic articles and research. As it is necessary to ensure immediate and easy access during the preparation of the study, the Elsevier Scopus database was selected. Scopus is a database that hosts more than 23,000 scientific titles and 5000 publishers. It contains approximately 1,400,000,000 citations, while the published entries are more than 73,000,000 scientific articles. Therefore, it becomes clear that Scopus was selected as it is one of the most popular and complete bibliographic databases.
Table 1 presents the research protocol that was followed in order to conduct the systematic literature review. This protocol sets the foundations for performing the research and was carefully constructed in order to achieve a valuable outcome as a result of the systematic literature review.
The research protocol shows that the widely approved and reliable Scopus database was selected for performing the literature review. Once the database was chosen, the keywords that form the basis for the search were then selected. In order to achieve targeted research both quantitatively and qualitatively, the appropriate keywords were selected and then combined using Boolean algebra. The selection of keywords included a learning and testing process of various combinations before the final selection in order to find the most appropriate combination. In this way, a number of irrelevant results were avoided, and the resulting publications were quantitatively controlled. This particular way of writing the keywords focuses on documents that address supply chain counterfeiting based on traceability approaches. Additionally, the only restriction set for the literature review is that the abstracts and main text of all included papers are written in the English language so that they can be easily accessible for analysis.
As far as the time range related to the subject of documents is concerned, no restriction was set since most of the papers that were finally accepted were published within the last five years. Of course, through studying less recent relevant publications, conclusions were drawn concerning the evolution of traceability methods with the advancement of technology. Having selected the database and defined the topic, the search field, and the search criteria, the search results presented 215 posts in total as of 15 March 2022. Subsequently, after sorting the documents in Microsoft Excel based on the date of publication, their abstracts were studied in order to evaluate their relevance and reliability for the scope of the research. Despite the restrictions and criteria set from the beginning, due to the large volume of the results, it was expected that some publications would be excluded as they did not cover the requirements.
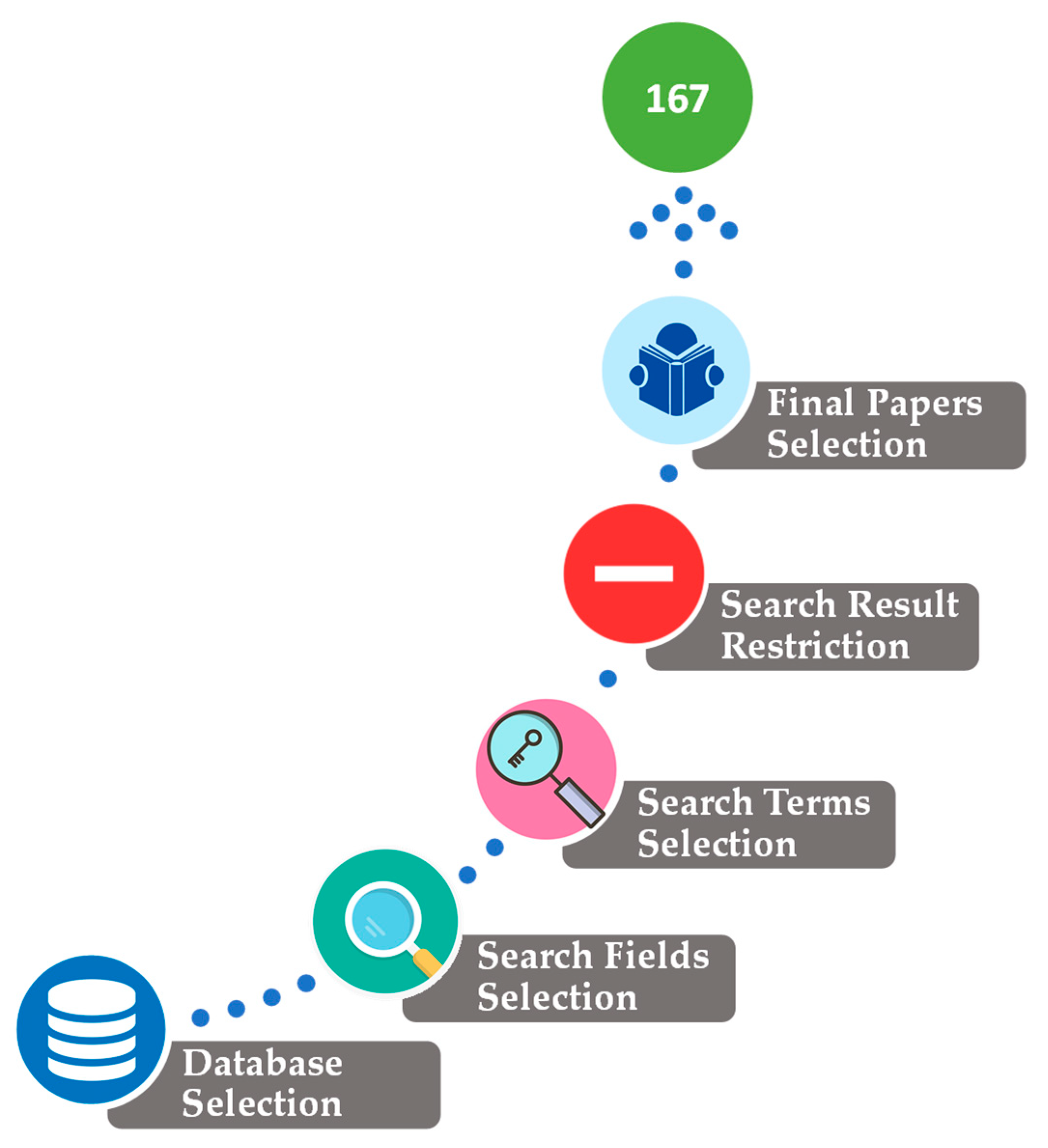
In particular, a few articles were found that, although having a short summary in English, were written in other languages. However, the majority of the rejected publications were publications that had little, or no relevance to the scope of the research, which is why it was decided by the authors that these papers need to be excluded from the final list of the selected-for-review papers. Additionally, there were also a few cases where articles were rejected because the main text was absent or in seldom cases (e.g., conference reports) did not correspond to one publication but included a huge list of documents. Eventually, 48 papers were disqualified after this first evaluation process, and the accepted papers were 167 in total.
Figure 1 briefly describes the aforementioned methodological steps for selecting the appropriate papers for review. These steps included the selection of the bibliographic database, the definition of the search fields, the definition of the search terms, the restriction of search results, and the final selection of the 167 papers based on reading their titles and abstracts. These are the papers that will be analyzed, and all findings and discussions are based on them. The full list of papers that resulted from the Scopus query is provided in the
Supplementary Materials of this paper.
3. Literature Review Data Analysis
As already mentioned, the initial results that appeared after the search in the Scopus database were 215 papers, of which 167 were considered acceptable and relevant to the research topic. A quantitative analysis was performed for these papers based on the following criteria:
Year of publication
Type of publication
Source Title
Figure 2 presents the number of publications per year. It can be noticed that most of the publications were published recently, mainly in 2020 and 2021, and that during the last five years, the research has gained significant popularity. This trend shows the growing market need for robust traceability approaches to combat counterfeiting and perform safe and sustainable supply chain activities. The relatively high number of publications for 2021 confirms this trend and sets high expectations for future research efforts. For 2022, only three relevant papers were found as it was still the first months of the year, an early period for most papers to be published. These papers were not presented in
Figure 2 as they would affect the trendline. After all, articles commonly appear in Scopus with a short time delay after their publication date. In recent years, more and more studies have been conducted that address the issue of counterfeiting and, at the same time, emphasize the need to ensure traceability and achieve safe and sustainable product supply chains.
Based on the type of publication (
Figure 3), it was found that both scientific journal articles and conference papers dominate the results. This is reasonable since most publications in the Scopus database are of one of these two types. It should also be noted that supply chain counterfeiting and technological advancements for achieving safe and sustainable supply chains are research topics that have been gaining increasing interest over the last few years. Therefore, the number of scientific articles and conference papers is expected to rocket in the following years.
Based on the source of the publication (
Figure 4), it is observed that research is relatively shared since no scientific journal dominates. As shown in
Figure 4, where the most popular source titles are presented, the most popular journal contains only 5 out of the 167 papers. It becomes clear, once again, that this research concerns various scientific groups and research fields and is still at its early stages. In any case, observing the most popular source titles, it becomes clear that they are either food or technology-related journals.
This is further proven by performing a quartiles-based analysis according to the source-title occurrence, as seen in
Figure 5. More specifically, 88.15% of source titles only occur once. Therefore, the Q0 (min), Q1, Q2 (Median), Q3, are all equal to 1. Q4 (max) is equal to 5 as the Food Control journal is the one that occurs the most times, while IQR is equal to 0 as Q1 = Q3 and the range R = 4. This is why, as seen in
Figure 5, all occurrences that are greater than 1 are outliers.
4. Development of the Classification Framework
As already discussed, the 167 papers were placed in Microsoft Excel in order to sort and filter them effectively to perform the quantitative analysis. Microsoft excel also enabled the identification of the different categories in which the papers will be classified. After analyzing the papers, two main classification groups were created:
Industry Sector
Traceability Approach
More specifically, concerning the industry sector, as presented in
Figure 5, the following eight sectors were identified:
Based on the industry sector that each publication deals with (
Figure 6), the majority of them are related to the food and spirits sector, with 74 out of 167, or almost half of the papers (44.3%) belonging to this sector. This was rather predictable as the food supply chain has the most challenges related to product counterfeiting, containing both health and financial risks. This sets effective traceability as a necessity in this sector in order to achieve safe and sustainable operations. After all, in the sector of foods and spirits, counterfeiting is directly linked to the alteration of matter and therefore endangers public health, so the need to combat it becomes even more significant. Many publications also concern the healthcare sector as it was detected that drugs, vaccines, and other medical treatments have gained considerable popularity for counterfeiting activities during the last few years. In addition, there are a considerable number of papers that are not related to a specific sector, but present general traceability approaches in an effort to provide traceability models that are universally applicable and effective. In the last places are the electronics, logistics, clothing, automotive, and luxury goods sectors, where counterfeiting activities have recently started to be observed but are expected to be further targeted in the next few years.
Additionally, concerning the traceability approaches, being the main focus of the present study, it was identified that a variety of techniques or mechanisms are used to combat supply chain counterfeiting. Based on the analysis of the 167 papers, the following three major categories, as well as their subcategories (
Figure 6), were identified:
Marking Techniques: Overt and Covert Technologies
IT Solutions: IoT, Blockchain, Machine Learning
Laboratory Techniques: Genetic and Chemical Methods
Based on the traceability approaches that each publication deals with (
Figure 7), most of them are related to the IT Solutions category, with 145 out of 217, or about two-thirds of the papers (66.8%) belonging to this category. It should be noted that the total number of traceability approaches in the papers greatly exceeds the total number of papers, as in many cases, multiple approaches were presented in a single paper. The most popular IT solution was found to be blockchain technology. It should be noted that all papers that present such an approach are from the last five years, showing once again the rocketing of the research interest in the previous few years. Older papers mainly present marking and laboratory techniques.
As a result of the classification of the papers based on the literature review, a framework was developed by the authors highlighting all identified traceability approaches for combating supply chain counterfeiting. The framework is presented in
Figure 8 and is analyzed in detail in
Section 5 where the traceability approaches are analyzed.
After thoroughly analyzing the two classification groups of the framework, the industry sectors and the traceability approaches, a pivot table (
Table 2) was created in order to present the correlation between the sectors and the approaches. A graphical illustration of the interconnections of sectors and approaches is presented in
Figure 9. From the industry sector point of view, it was observed that the food and health sectors are, by far, the most popular research sectors, while blockchain and IoT are the most popular traceability approaches. Regarding correlations between data, it can be observed that IT Solutions dominate the automotive, luxury, and logistics sectors as traceability approaches. Clothing, electronics, and general sectors contain IT Solutions and marking techniques. Finally, the most popular sectors, food, and health include research efforts with all discovered traceability approaches.
From the traceability approach point of view, it can be observed that IoT solutions and marking techniques have a universal field of application, in contrast to laboratory techniques that can only be applied in only a few of the industry sectors. The laboratory techniques are primarily found in the food sector, with a few appearances in the health and electronics sectors. Marking techniques have a wider field of application as they can be found in all sectors except automotive, logistics, and luxury. Finally, IT solutions have a universal field of application.
5. Analysis of the Framework’s Traceability Approaches
This section presents a detailed analysis of the traceability approaches that were identified during the literature review. More specifically,
Section 5.1 analyses the identified marking techniques based on their two major subcategories, the overt and covert technologies. Overt technologies have been applied for many years and to a certain extent can continue to be applied for product traceability, however, as technology progresses, these methods have become easier to copy. The technological advancements have led to the creation of more advanced covert technologies, that require special equipment and are much harder to be copied. In any case, marking techniques are more and more often combined with other traceability approaches in order to provide an effective traceability system.
Section 5.2 analyses the most popular traceability approach category, IT solutions. This category includes the blockchain, IoT, and machine learning technologies, that especially during the last five years, have skyrocketed in popularity. These technologies also seem to be where future research efforts will focus in order to create appropriate traceability systems for all industry sectors and effectively eliminate counterfeiting. Finally,
Section 5.3 presents laboratory techniques, that while having a narrower field of application, are proven to be a very effective aid against product counterfeiting in specific supply chains. This is because they contain genetic and chemical methods that can detect alterations and falsifications of products. As technology progresses, these techniques have also evolved and are increasingly being combined with other traceability approaches in order to combat specific product counterfeiting attempts such as food, beverages, vaccines, and drugs.
5.1. Marking Techniques
Marking techniques were identified to cover two major subcategories, overt and covert technologies.
5.1.1. Overt Technologies
These technologies include techniques visible to the naked eye on a product’s packaging and do not require extravagant actions to evaluate. The auditor must have some basic knowledge or undergo brief training in order to be able to identify whether the object in question is imitated or not. These are mainly prominent characteristics, which change depending on the angle from which we see them. Typical examples are barcodes, QR codes, holograms, variable inks, and watermarks.
The most popular overt technology for marking products is one- or two-dimensional barcodes. There are several types of barcodes, but the most widely used ones are QR codes and 2D Datamatrices. QR codes alone do not offer protection against product counterfeiting. They can, however, be combined with other authentication technologies to provide automated authentication via a smart device. Obviously, appropriate readers are needed. The barcode scanner, for example, emits a beam of light, the reflection of which in the lines or in the code register allows the recognition of their amplitude and brightness. In this way, the symbol is converted into information, and the product is identified. The resulting code then acts as a search key in the database of the connected information system, from which the rest of the product information can be retrieved.
Holograms, another overt technology, are three-dimensional images or coatings of two-dimensional images created by a photographic technique in which light diffused by an object is recorded and presented in a three-dimensional way, confirming the product’s authenticity. Holograms are printed either on the product label without interfering with the production process or even directly on the packaging after proper control of the used material. There are several types of holograms depending on the technique that is reproduced, with one of the best-known ones for anti-counterfeiting being the dot-matrix hologram. This is made up of small pins, acting as a diffraction grid, resulting in a concentrated three-dimensional feel. In addition, drawing illustrations or engravings, which are often confused with holograms, are achieved with special laser printers, while the most detailed advanced micro-images are achieved with the help of an electron beam generator [
4]. Of course, the more complex the pattern followed, the higher the security of the product, which, however, makes it difficult to control without specialized tools and increases costs [
5].
In terms of inks to mark or identify the product, sophisticated iridescent inks are used, which can be differentiated under a specific light and visual view by tilting or rotating the point where they are printed. The most common color pairs are red-green, silver-gold, and green-blue. In addition, thermochromic inks are now available, which change color when exposed to temperature deviations, with this change sometimes being reversible and sometimes not. Many such inks at high temperatures become transparent and reveal the background color on which they are deposited. Of course, it is not only the temperature that matters but factors such as the color, the concentration, and the thickness of the paint influence when the color change will occur. Finally, penetrating inks and reaction inks have also been developed to combat counterfeiting. The former penetrates deep into the fibers of the label, leaving their mark, so they are not easy to remove. The latter, in an attempt to overcome counterfeiting, reacts with the substance that will try to discolor them, whether it is a chemical or a water-based substance, resulting in staining on the spot.
The watermarks, which can be commonly found on the banknotes, can well be classified as methods of ensuring authenticity. They are printed on paper and produced by applying pressure to the substrate in the form of a pattern or text. This causes compression and thinning of the paper only in the areas where pressure is applied. Thus, more light can pass through the thin parts of the paper, so the watermarked image is displayed without the need to incorporate other materials.
Unfortunately, overt techniques are now easier to copy as technology progresses, especially when used individually. Of course, overt technologies can be combined with covert technologies, which will be presented in
Section 5.1.2, to work in combination and act as a deterrent against possible falsification.
5.1.2. Covert Technologies
These are technologies that are either encrypted or placed in invisible parts of the product. They require appropriate high-tech tools to identify them. Therefore, whoever wants to use them, must know how to handle them. Obviously, the nature of these technologies makes them more effective against counterfeiting, while there are a plethora of such technologies that are growing more and more over time.
A classic method of ensuring authenticity and protection against counterfeiting is the use of inks. Covert technologies include a special category, inks that are sensitive to either infrared or ultraviolet radiation. These inks are entirely invisible to the “naked eye,” and to be detected, they require the use of a special infrared scanner. They are applied to all kinds of material, and they are mainly used in order to hide the code of a product. The latter may be visible, but they change color or disappear when exposed to ultraviolet radiation. However, they are classified as covert technologies for dealing with counterfeiting as they require a special light source that emits electromagnetic radiation in the ultraviolet spectrum. These inks are placed in encoded microcapsules on the surface of the package, which can be detected by electron microscopy. Such inks are hard to find and of course, more costly, so they are harder to reproduce [
6].
Another method that is used regularly is encrypted images and, even more often, small, encrypted texts on the labels of bottles. These encrypted parts, which are in the background of the label, are decoded with the help of special lenses or laboratory equipment. This technology is found either in labels or documents of transport and certifications of goods. Due to their encrypted nature, specialized equipment is required in order to decode them [
7].
5.2. IT Solutions
It was identified that most traceability approaches are based on information technology solutions and play a leading role in the effort to guarantee counterfeit-free and sustainable supply chain activities. They can be either overt or covert and are mainly linked to a database to transfer encrypted information [
8]. IT solutions for traceability include blockchain, internet of things (IoT), and machine learning solutions.
5.2.1. IoT
The IoT enables various devices to connect to the internet and share helpful information, using wireless sensors, through servers to perform specific processes in the external environment, such as measuring temperature or humidity or even detecting the movement of a product. Through the IoT it is possible to deliver the correct information to the right people at the right time. Various sensors are constantly receiving data that can be used to make decisions. The “things” that are connected to the internet are expected to exceed 50 billion in the near future, and they should be designed so that they can be integrated and work together so that the needs of the future can be met. The IoT architecture is basically the backbone of any application, and so it should be designed based on needs such as scalability, availability, functionality, and maintenance. It is, therefore, clear that security is a very important factor at all levels of IoT.
The use of RFID (Radio Frequency Identification) technology, which is considered to be the evolution of barcodes, is a popular IoT enabler. RFID uses radio frequency technologies to identify objects, animals, or people remotely. This is achieved through electronic labels that have as their essential property to give a unique identity to everything connected and transmitted through radio frequency channels. This unique ID, along with any other data that can be stored on the device, can be retrieved by RFID readers. RFID readers can be connected to the internet, allowing real-time data monitoring [
9,
10,
11].
NFC (Near Field Communication) technology, another popular IoT enabler, is a set of communication protocols for secure wireless communication between electronic devices smaller than 10 cm from each other. NFC is based on contactless cards and RFID technologies. However, unlike these technologies, an NFC system can send and receive queries and act as a tag, meaning it can operate both actively and passively. They can be configured either to communicate under specific conditions or in the same way as contactless cards do. Unlike RFID system readers, which can read large numbers at a time, NFC readers can only communicate with one tag at a time. They are used in a wide variety of materials and products and are usually placed on the labels or in the product itself after relative processing. An NFC tag can be easily accessed and read from a smartphone and costs a few tens of cents of a euro, slightly higher than passive RFID tags, as it offers more features [
12,
13,
14].
5.2.2. Blockchain
Blockchain technology is based on the concept of a sorted and growing list of transactions. Records (blocks) are encrypted and interconnected [
15]. Each block contains an encrypted hash code of the previous block (hash), transaction timestamps, and data. The transaction file is maintained on various computers that are connected to a peer-to-peer (p2p) network. Thus, Blockchain technology allows distributed and unchanged data to exist in a secure and encrypted manner while ensuring that transactions can never be modified. Essentially, blockchain is a decentralized data structure in which transaction groups are stored on a distributed network. Network participants have access to all historical data and transactions, including block creation time. Each block consists of specific information, a list of transactions made in a certain period of time, a stamp of the time of its creation, and a digital reference (hash) to the previous block.
Consensus algorithms are used to verify the validity almost in real-time. This is done in conjunction with the encrypted report, the hash that exists, and the algorithm that validates it. In public blockchains, this process is called mining which involves a form of reward for someone who verifies or validates a block. If someone tries to change or violate the transaction information recorded in a block, the hash for that block will change and will no longer show the hash of the previous, verified block [
16].
The key elements that characterize the blockchain architecture and have set it high on the list of preferable traceability solutions are the following [
17]:
Unchanged: blockchain is a permanent transaction file. If a block is added to the node, it is impossible to modify it.
Decentralized: it is stored in a file that is accessible to interested parties and copied from any network node.
Transparent: each party can access and control transactions. This creates the concept of origin and tracking the product’s entire supply chain.
Consent-based: each block in the blockchain is independently verified by consent models that provide rules for validating a block. Oftentimes, public networks need a lot of resources to achieve this.
Blockchain technology has been adopted in recent years in traceability systems in a wide range of industries. However, complete traceability systems are not readily available as the technology is not yet fully understood by industries, and many companies are in the testing phase of its utilization, and the detailed features of such systems remain to be discovered [
18,
19,
20,
21,
22]. There are several types of blockchain networks, with Ethereum and Hyperledger being more prominent for traceability applications [
23], with the main difference being that the former tends to force developers to build their applications around generalized protocols. At the same time, the latter promotes personal rules based on the respective business. Today, blockchain technology is proposed to be adapted to existing traceability systems and to take advantage of existing innovations such as RFID tags, QR codes, and NFCs [
24]. Ethereum applications seem to have great potential as traceability enablers, as shown by [
25], who present the use of smart contracts, i.e., automated programs that complete a transaction autonomously, while also analyzing the combination of blockchain with machine learning and deep learning algorithms that are discussed in
Section 5.2.3.
Blockchain technology, when applied to a supply chain, is distinguished by significant advantages, as pointed out by [
26], which arise either directly or indirectly through value-added services in the supply chain. The first includes:
The decentralized character that improves the resilience of IoT applications by avoiding a single point of failure for data storage
The integrity of the process as it is a peer-to-peer network where all nodes are equal, and new blocks are multiplied, validated, and accepted between nodes. Larger chain data cannot be modified without being detected and discarded by other nodes
The network consent as data between nodes are maintained continuously by consent algorithms
The private network with certified users since permissioned networks (private rights) are preferred to reduce the possibility of attack by a strong public node
The ability to support some information chains
The latter include:
The production planning due to the waiting of the demand and therefore the better coordination of the activities
The optimization of the stock if there is knowledge of what is in the warehouse so better organization of orders
The early warning due to the immediate detection of the defective batch and therefore reliability to the customer
Of course, it has some drawbacks that need to be normalized in the future. The most remarkable of these are [
27]:
The scalability restrictions as they are not tested databases for a plethora of data
The data size limitations as unnecessary information can affect system efficiency
The possible incompatibility between blockchain networks as a few standards exist
The privacy issues as the data entered in the database can be quite sensitive
The high energy and operating costs
The unclear legal frameworks
5.2.3. Machine Learning
Machine learning functions via examining a large number of samples, including both genuine and counterfeit products, and manages (learns) to distinguish what separates them. The most widely used machine learning technology is augmented intelligence (AI). The technology is currently being used in manufacturing to detect faults and in cellphones to improve functioning and recognize sceneries, but it can also be used similarly to detect counterfeit goods. In contrast to the human eye, machine learning can review hundreds of instances of produced items and analyze billions of data points to identify issues. Machine learning algorithms such as the ant colony optimization algorithm (ACO) [
28] and the Convolutional Neural Networks (CNN) [
29] have already been successfully applied in research for counterfeit prevention. Optical Character Recognition (OCR) is another technique based on machine learning that has been applied by [
24] for the digital transformation of the wine supply chain in order to prevent counterfeit wine commerce. Videogrammetry, a machine learning process for creating 3D models using videos, has also been proposed as an approach by [
30] in order to achieve food supply chain traceability.
5.3. Laboratory Techniques
These technologies are based primarily on laboratory analysis and include chemical and genetic methods while aiming to ensure the product’s authenticity based on its characteristics. Genetic methods that have been studied as traceability approaches for counterfeit prevention include:
DNA Barcodes: encoded DNA molecules that carry unique genetic information and are implanted on labels or packaging while being invisible to the naked observer [
31].
Restriction Fragment Length Polymorphism (RFLP) markers: detected polymorphisms that result from DNA sequence variations [
32].
Polymerase Chain Reaction (PCR) Analysis: a laboratory technique used to amplify DNA sequences [
33].
Single Nucleotide Polymorphisms (SNP): common genetic type variations that can act as biological markers in order to detect and compare genetic variations [
34].
Accordingly, chemical methods include:
Chemometry: specific chemical properties are placed in small quantities on the label material during the production process to ensure the origin and quality of the good. These properties are recorded in a database to validate the authenticity of the product while reading them requires special laboratory equipment, strict protocols, and some time for the final analysis [
35,
36,
37].
Spectrometry: concerns measuring interactions between light and products, including reactions and measurements of radiation intensity and wavelength in order to determine counterfeit products [
38].
Photochemical Analysis: used for plant-based counterfeits, this method extracts, screens, and identifies active substances found in plants [
39].
Chromatography: a process for dissolving a mixture into its constituents that can aid the detection of illegal or counterfeit substances [
40].
6. Discussion
In this section, the most important findings of the literature review are discussed, focusing both on the challenges and the mechanisms for combating supply chain counterfeiting. Additionally, the evolution of traceability approaches is presented according to the literature review findings.
6.1. Counterfeiting Challenges in the Supply Chain
6.1.1. Food Sector
Undoubtedly, the issue of counterfeit products in a supply chain has taken on enormous proportions in recent years in many industries with significant implications. According to [
41], food supply chains become more vulnerable to counterfeiting due to their length and complexity. Therefore, the more stakeholders in the chain, the more information is entered and has to be circulated, resulting in the phenomenon of information asymmetry, in which there is an abnormal distribution of information to stakeholders, as reported by [
42]. Counterfeiting in the food industry, whether goods are fresh or canned, can take many forms and is associated with a variety of immoral acts. In general, according to [
43], it includes the distortion of the product, its substitution, or even dilution if it is a liquid product. Counterfeiting may also be achieved by fraudulent means and illegal processing methods that aim to remove the essential ingredients of food and replace them with additives in order to simulate a standard quality at a much lower cost but with serious health risks [
44].
Additionally, the falsification of the data in the certificates of supply, distribution, and sales as well as the falsification or incorrect placement of the labels are also considered counterfeit methods. False or altered information takes the place of the original and distorts the product’s authenticity, the production processes followed, and the nutritional value of the product. In addition, stolen goods that are smuggled into legal markets (smuggling), as well as the phenomenon of diversion of sales of products in gray markets, are parts of the problem of counterfeiting. Finally, counterfeiting may occur in the intellectual property rights of a good.
The effects of counterfeiting can be found in a wide range of areas. According to [
44], consumer confidence in food is shaken at the first level. Furthermore, unfair competition arises between companies, the company is often discredited, and the product’s brand name is irreparably injured. A food scandal affects not only the direct stakeholder, i.e., the company producing the goods but also the consequences can be extended to the cooperating companies that may undertake roles in the product’s supply chain. Such a severe problem can lead to long-term financial losses for a company but also for the entire economy of the country. Of course, as [
43] point out, consumer health is at stake as counterfeit foods can cause from a simple disease symptom to death. Additionally, the damage to the consumer’s health is likely to occur either immediately or in the long run. At the same time, the person also suffers moral damage, buying a product that does not cover the conditions of origin, raw material, and working conditions that were supposed to exist.
However, the need for a food traceability system arises as a result of addressing other challenges in the food supply chain. Therefore, there is a very strong need to maintain food safety as contamination at any stage of the supply chain lurks due to the nature of the good. This is verified by the ever-increasing number of food scandals [
45]. Additionally, without effective traceability, the raw material can deteriorate if, for some reason, the conditions (temperature, light conditions, humidity levels) in which they must be maintained are affected, and microorganisms may grow that will eventually trigger foodborne illnesses when consumed [
43]. In addition, the management of food waste, mainly at the retail stage but also after the raw material collection stage, reinforces the need for a targeted traceability system. It is necessary to structure it to cover all the activities of the supply chain in order to achieve a proper flow of material, to seek appropriate time management of the required activities at each step, and to use only the really required raw material. Additionally, only through an effective traceability system can a company ensure and prove that it follows sustainable practices.
6.1.2. Health Sector
The health sector is the second area that needs to be strengthened to combat corruption and counterfeiting. According to [
27], counterfeit drugs are the biggest problem in the pharmaceutical industry worldwide, with the World Health Organization estimating that their percentage reaches 10% in developing countries. Counterfeit and incorrectly labeled drugs, whose identity and source are either intentionally concealed or altered intentionally and fraudulently, are also considered counterfeit. These medicines may be generic or branded and contain false information such as false labels, insufficient and incorrect quantities of ingredients, and, most importantly, incorrect packages or even no packages.
Respectively, ref [
23] reports that about 50% of the drugs sold online are counterfeit while still stressing that the issue of counterfeit drugs depends on how strong the controls in the area are. Of course, counterfeiting in the pharmaceutical industry is intensifying due to its complexity but also the growing black markets that produce, distribute and sell counterfeit drugs. A component of the same pathogen is the placing on the market of lower quality or expired vaccines that internet transactions favor [
25]. According to [
27], the consequences of consuming unchecked drugs that do not meet the current standards are crucial for the health of consumers creating, from mild symptoms to death, with the death of children due to counterfeit drugs being the number one cause in developing countries. Naturally, the production and trade of counterfeit drugs harms legitimate companies operating in an unfair competitive environment and adversely affects all stakeholders in the drug chain, as a phenomenon causing billions of euros in damage to the global economy. It becomes clear that the health sector needs to be strongly protected from counterfeit activities in order to ensure secure and genuine medicine supply chain operations.
6.1.3. Other Sectors
Concern is also present in the electronics industry, where counterfeit goods are often found. More specifically, ref [
46] underlines the ever-increasing problem of counterfeit electronic systems due to the expansion of globalization. Microcircuits are recovered from used or discarded electronic waste and are classified as recycled microcircuits. As the critical life of a system’s critical infrastructure is much longer than the lifespan of electronic components, it is easy to obtain obsolete components, which are not produced by genuine component manufacturers but by unreliable suppliers that are often offshore. In addition, cloned electronic circuit components are more common. Ref [
47] emphasizes the negative impact that counterfeit electronic components have after the discovery of such in the US military as they have limited performance and reduced resistance to adverse environmental conditions while, in the worst-case scenario, can damage the reliability of sensitive systems.
To a much lesser extent, efforts have been made to apply traceability approaches against counterfeiting, focusing on the logistics, clothing, luxury goods, and automotive industries. Traceability approaches in these sectors are a relatively new research focus, and they still have much future potential to be further analyzed. In fact, it is estimated that the research attempts will significantly increase in the following few years [
48]. In any case, it should be noted that the small number of research papers on the automotive, logistics, luxury, clothing, and electronics sectors lead to interesting preliminary findings. These findings can be further researched and analyzed in order to achieve valuable conclusions.
6.2. Evolution of Traceability Approaches
Initially, according to [
49], it was common for conventional traceability systems to operate separately from anti-counterfeiting systems, making them less accessible to consumers and more fragile. As reported by [
41], the first traceability systems were manual tracking systems with conservation of data on paper. Although they were very economical, they risked significant inaccuracies and it was virtually impossible to revoke a faulty batch on-time without being able to anticipate any impact related to the safety of the goods.
Next, research moved on to systems automation. The mechanical conventional traceability systems based their product coding along the supply chain on barcodes and RFID tags that are placed on their labels or packages and behind them there is a centralized database. As a result, information on each requested item is stored in isolation, and the information’s traceability becomes difficult. In addition, the process of retrieving information from tags was quite complicated, the cost of producing electronic tags was high, and they ended up being easily cloneable. As [
50] analyzes, in any case, and over time, visible and hidden technologies are constantly added, mainly to the final products (or their packaging), such as inks, holograms, micro-icons either carved or laser-marked, and many more innovations in order to give a safer and inviolable character to the product.
Of course, all these efforts complicate the work of the counterfeiters but cannot manage to guarantee that such practices are disabled. Moreover, despite the adoption of IoT innovations, such as temperature and location sensors, and advanced RFID tags with their own built-in capabilities that would no longer require the physical presence of humans to enter and send information, the centralized nature of the systems left them exposed to tampering and their reliability and transparency were constantly threatened.
Observing the traceability systems that are being developed, one can see the recent sweeping dominance of blockchain technology over time, especially from 2017 onwards. Until then, although it was a technology first released in 2008 to create a decentralized cryptography-based e-money trading system [
51], it was not used in traceability systems. The technology may still be in its infancy, but it is gaining traction and is set to monopolize interest in traceability systems in many industries for years to come.
It is considered that, nowadays, the technological advancements and the combination of various traceability approaches can lead to an effective traceability system that can ensure safe and sustainable supply chain operations. In fact, sustainable supply chains have become the center of various European Union initiatives such as Food 2030 and the Fork-to-Farm Strategy. Following the present research can aid the development of an effective and secure data-driven traceability system that meets societal needs in line with the goals of these initiatives. The system can ensure that products can be fully traceable, and their quality and authenticity will be guaranteed. The production and distribution of products can be monitored in order to ensure that the followed procedures are in line with safe and sustainable practices.
Finally, as it becomes clear, through a traceability system against product counterfeiting, supply chain operations can be significantly facilitated and lead to more effective product supply and recycling. The use of such a traceability system is fully harmonized with sustainable practices and can ensure that products are distributed only through legal supply chains with a solid awareness of consumer health protection. Additionally, the social impact can be significant as fraudulent activities are essentially eliminated, and local cultivators, producers, distributors, retailers, and communities are protected. Finally, financial sustainability can be enhanced as fair trade can be facilitated and promoted. This can enable the fostering of competitiveness in various supply chain sectors, and revenue and job losses due to counterfeiting can be preserved.
7. Conclusions
In today’s era, where counterfeiting activities cause serious supply chain challenges, effective traceability is the only way to confront this problem and achieve safe and sustainable supply chain operations. Traceability, aiming at tackling counterfeiting and the immediate recall of unwanted products, contributes decisively to the overall smooth operation of a business and strengthens its name and credibility in the market. It is a fact that many tools have been developed, both practical and informative, to deal with counterfeiting. Innovative technologies and laboratory techniques are increasingly being employed to prove and guarantee the authenticity and sustainability of products.
Today, the conventional solutions of the past are inferior in nature and are more vulnerable to counterfeiting. Technological advancements, such as blockchain and the IoT, and combinations of traceability approaches can provide reliable solutions in order to overcome the counterfeiting challenges. However, governments and supply chain stakeholders must intensify the controls and strengthen the fines for illegal activities in addition to the means used. The European Union has started to implement various such policies and initiatives in order to achieve safe and sustainable supply chains. This research can be used as a guideline both for supply chain stakeholders and policymakers to identify counterfeiting in the various supply chain sectors successfully. The provided classification framework and the thorough analysis of the supply chain sectors, and the traceability approaches set the basis for a holistic and effective strategy to combat supply chain counterfeiting.
In addition, industries have started to realize the need to shield themselves against counterfeiting by adopting advanced traceability solutions for both internal processes and the entire supply chain and harnessing the potential of technology to create a safer environment and become more competitive. Once again, this research can be used as a guideline for industries to achieve these goals. In fact, the more industries implement effective traceability approaches to combat counterfeiting, the more difficult it will be for such malpractices to affect supply chain operations. In this way, the economy will be shielded and a considerable percentage of the financial and job losses due to counterfeiting will be preserved.
Our future research will focus on the detailed analysis of all aspects of specific product supply chains as this can facilitate the more accurate and effective establishment of a traceability system. Furthermore, there is a need for further analysis of the sectors where research is still at the first stages in terms of discovering effective traceability approaches for combating product supply chain counterfeiting. Finally, exploiting the findings of the present research, our team will implement a traceability system that will combine cutting-edge technologies like blockchain, the internet of things, and marking techniques in order to combat counterfeiting in the wines and spirits sector effectively, which was found to be one of the most strongly impacted supply chain sectors.