A Systematic Review of Smart City Infrastructure Threat Modelling Methodologies: A Bayesian Focused Review
Abstract
:1. Introduction
- 1.
- To analyse current smart city modelling and simulation literature towards understanding the key issues and challenges faced where threat modelling can be used for a solution;
- 2.
- To critically review and evaluate the current research surrounding Bayesian-based smart city infrastructure alongside unique alternative modelling and simulation methodologies to provide the best possible solution performing cyber-security analysis within the smart city environment.
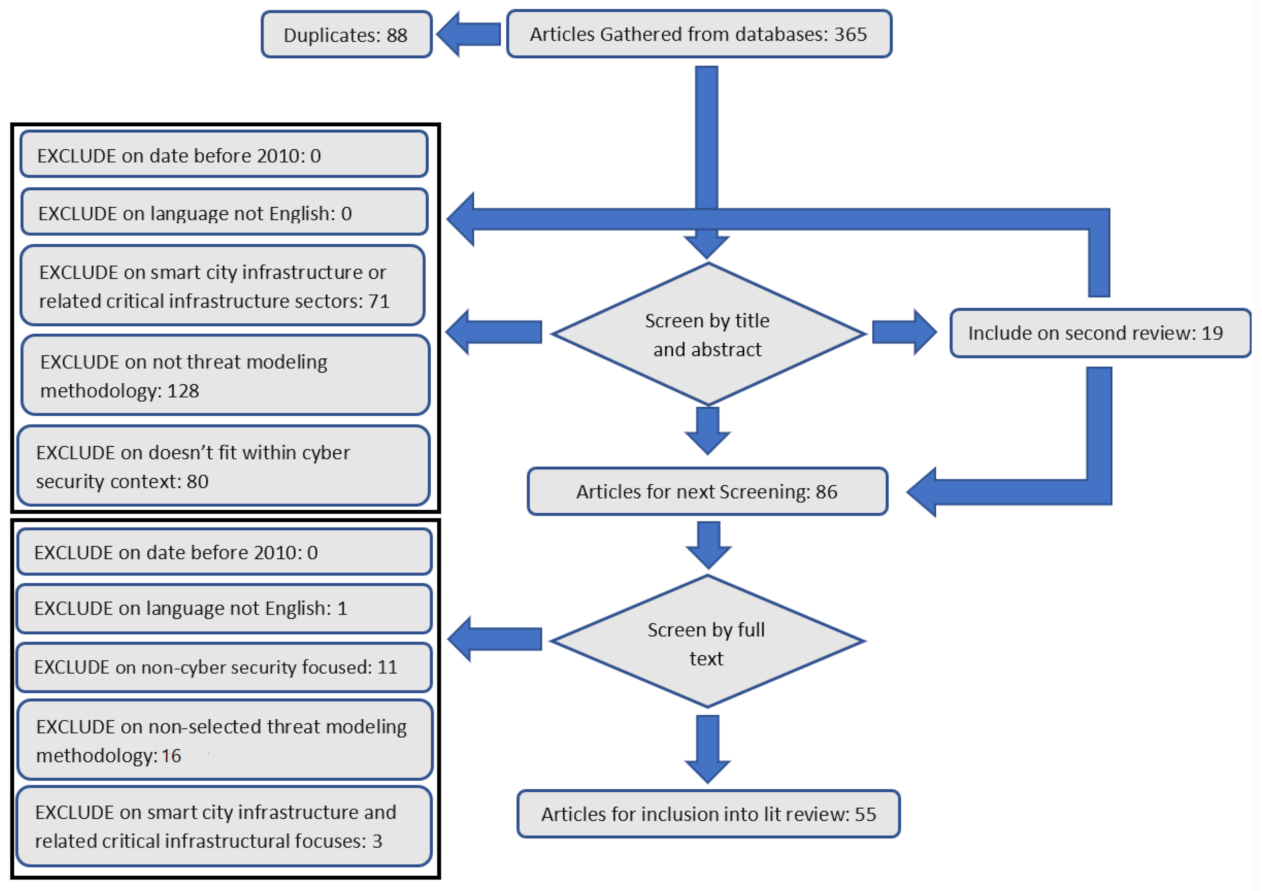
2. Systematic Review Research Methodology
- (Challenges OR issues) AND city infrastructure;
- Threat modelling AND Bayesian networks;
- Bayesian networks AND (city infrastructure AND (critical national infrastructure/critical infrastructure) OR (smart city infrastructure).
- Review of metrics, aspects, and technology implementations;
- Systematic/normal literature review of smart or critical national infrastructure;
- Bayesian network threat modelling methodology towards smart city or critical national infrastructure;
- Alternative threat modelling methodology towards smart city or critical national infrastructure.
- Exclude on date: the study report was published after 2010.
- Exclude on language: there is no English version or translations available.
- Exclude on smart city infrastructure or related critical infrastructure sectors: the article does not fit within the project’s scope regarding smart city infrastructure or any of the closely linked critical sectors that comprise it.
- Exclude on not threat modelling methodology: the paper does not discuss or propose a threat modelling methodology applied towards smart city infrastructure or related critical national infrastructures.
- Exclude on does not fit within cyber security context: the articles do not contain cyber-security focus within their analysis of smart city infrastructure or related critical national infrastructures.
- Include the second review: the paper will be coded for a second review after all other literature has been reviewed, then a decision to include or exclude shall be made.
- Include on title and abstract: include on the title and abstract, which will go through the next level of reviewing for full-text review.
- Exclude on date: the study report was published after 2010.
- Exclude on language: there is no English version or translations available.
- Exclude on non-cyber security-focused: the article does not focus enough within the cyber-security context regarding smart city infrastructure and related critical national infrastructures.
- Exclude on non-selected threat modelling methodology: the methodology does not fit within Bayesian-based techniques or selected comparative methods.
- Exclude on smart city infrastructure and related critical infrastructural focuses: the article does not fit within the context of smart city infrastructure or other related critical infrastructure analysis.
- Include on the second review: the paper will be coded for a second review after all other literature has been reviewed, then a decision to include or exclude shall be made.
- Include on the full study: include into the full systematic literature review, where it will be used within the research articles synthesis.
2.1. Previous Systematic Literature Reviews
2.2. Review Limitations
3. Background and Concepts
3.1. Critical National Infrastructure
3.2. Smart City Infrastructure
3.3. Critical Infrastructure Interdependency
3.4. Threat Modelling Cyber-Physical Systems
3.5. Bayesian Networks
4. Systematic Literature Review
4.1. Issues and Challenges within Smart City Infrastructure
4.2. Smart City Threat Modelling Methodologies
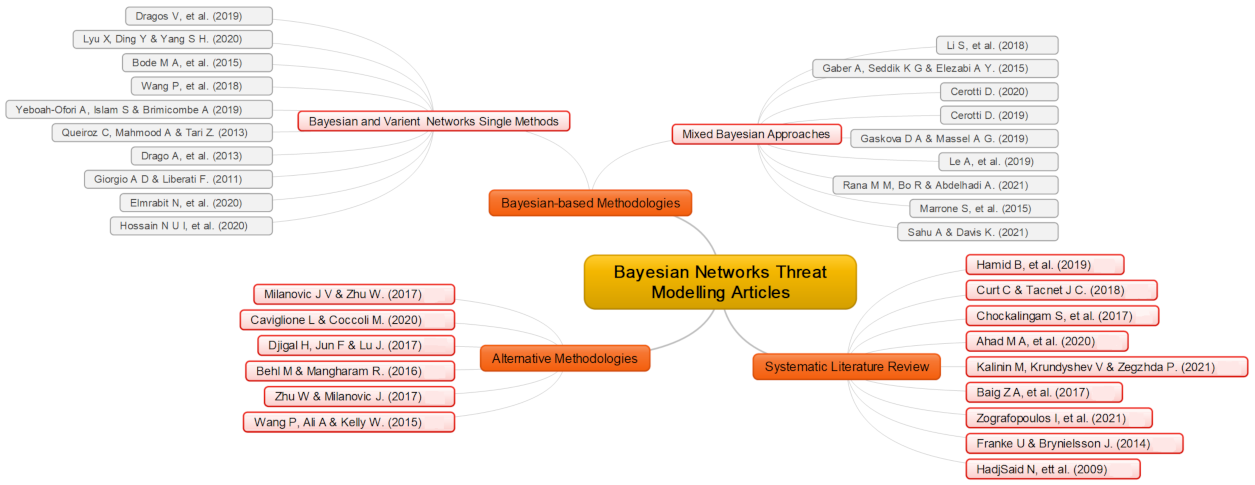
4.2.1. Bayesian Network Methodologies
4.2.2. Adjusting Typical Threat Modelling Methods
4.2.3. Dynamic Bayesian Networks
4.2.4. Mixed Bayesian Methodologies
4.2.5. Proposed Non-Bayesian Methodological Comparison
5. Findings: Comparative Analysis of Different Methodologies
- 1.
- To analyse current smart city modelling and simulation literature towards understanding the key issues and challenges faced where threat modelling can be used for a solution.
- 2.
- To critically review and evaluate the current research surrounding smart city infrastructure Bayesian-based alongside unique alternative modelling and simulation methodologies to provide the best possible solution performing cyber-security analysis within the smart city environment.
5.1. Objective One Findings
- Security focus towards CPSs as integration increases attack surface: SCI is constructed with the introduction of Industry 4.0 technologies, which constitute the introduction of CPSs and with the issues that come with having all devices be able to network.
- Understanding of the complex interconnected nature regarding SCI: this is further complicated from the previous issues regarding cyber-physical elements, which can make the system excessively complex with the objective relationships local, national, and global levels across different interdependency layers.
- Identification of associated CPS system metrics within the smart city context: many different systems have an array of both internal and external components that affect how interlinked systems are effective, which furthermore are varied in their influences and valuations.
5.2. Objective Two Findings
5.2.1. Modelling Process and Structure
5.2.2. Modelling Metrics
- Reactive Restoration—resilience, recovery, and redundancy of associated CPS, which is important because of the nature regarding CNI for them to either return to full functionality and mitigate adverse events to maintain functionality.
- Physical Proactive Countermeasures—physical evaluation and monitoring of physical-domain of systems. These are physical elements and processes usually seen with typical CNI systems.
- Cyber Proactive Countermeasures—analysis and review of the network, local and external-based devices, where it can be seen within supervisory control and data acquisition (SCADA) or transformed previous physical-only systems [58].
- Threat Characteristics—dictate the different characteristics regarding that specific type of cyber threat, which can be used to provide a taxonomy of identified threats.
5.2.3. Testing Methodologies and Validation Methods
5.2.4. Model Complexity
5.2.5. Modelling Interdependencies
5.2.6. Applicable Bayesian-Based Smart City Environments
5.3. Overview of the Systematic Literature Review
5.3.1. Towards an Effective Solution
5.3.2. Smart City Environment Overview
6. Conclusions
7. Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| BN | Bayesian networks |
| DBN | Dynamic Bayesian networks |
| DAG | Directed acyclic graph |
| CNI | Critical national infrastructure |
| CII | Critical infrastructure interdependency |
| CLGD | conditional linear Gaussian distributions |
| SLR | Systematic literature review |
| SCI | Smart city infrastructure |
| CF | Cascading failures |
| CPS | Cyber-physical system |
| IoT | Internet of things |
| URREF | Uncertainty representation and reasoning evaluation framework |
| CPT | Conditional probability table |
| ToE | Target of evaluation |
| SCADA | supervisory control and data acquisition |
| MaS | Modelling and simulation |
| AT | Attack graph |
| NPF | Neyman-Pearson forms |
| DCM | Dynamic cognitive maps |
| FAIR LEF | Factor analysis of information risk loss event frequency |
| RBNE | Refined Bayesian Nash equilibrium |
| OFTGT | Optimal filter theory graph theory |
| PN | Petri net |
| HMM | Hidden Markov model |
| MBSL | Machine-based structured learning |
| ICTS | Information communication technology system |
| TLBN | Two-layered Bayesian network |
| ICMDD | Identification and classification model-driven design |
| ZKPECDLP | Zero-knowledge protocol using elliptic curve discrete logarithm problem |
| RTBM | Regression tree-based model |
| TTMM | Typical threat modelling methodology |
| WCNT | Weighted complex network theory |
References
- Simon, T. Critical Infrastructure and the Internet of Things. Pap. Ser. No 2017, 46, 1–20. [Google Scholar]
- Zografopoulos, I.; Ospina, J.; Liu, X.; Konstantinou, C. Cyber-Physical Energy Systems Security: Threat Modeling, Risk Assessment, Resources, Metrics, and Case Studies. IEEE Access 2021, 9, 29775–29818. [Google Scholar] [CrossRef]
- Selin, J. Evaluation of Threat Modeling Methodologies: A Case Study. Master’s Thesis, JAMK University of Applied Science, School of Technology Information and Communication Technology, Degree-Granting University, Chicago, IL, USA, 2019. [Google Scholar]
- Queiroz, C.; Mahmood, A.; Tari, Z. A Probabilistic Model to Predict the Survivability of SCADA Systems. IEEE Trans. Ind. Informatics 2013, 9, 1975–1985. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhu, C.; Tang, L.; Zhang, W.; Wang, P. Cyber Security Inference Based on a Two-Level Bayesian Network Framework. In Proceedings of the 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Miyazaki, Japan, 7–10 October 2018; pp. 3932–3937. [Google Scholar] [CrossRef]
- Le, A.; Chen, Y.; Chai, K.K.; Vasenev, A.; Montoya, L. Incorporating FAIR into Bayesian Network for Numerical Assessment of Loss Event Frequencies of Smart Grid Cyber Threats. Mob. Netw. Appl. 2019, 24, 1713–1721. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Zhang, J.; Zhu, P.; Tan, Q.; Yin, W. Quantitative cyber-physical security analysis methodology for industrial control systems based on incomplete information Bayesian game. Comput. Secur. 2021, 102, 102138. [Google Scholar] [CrossRef]
- Chockalingam, S.; Pieters, W.; Teixeira, A.; van Gelder, P. Bayesian network models in cyber security: A systematic review. Lect. Notes Comput. Sci. 2017, 10674, 105–122. [Google Scholar] [CrossRef] [Green Version]
- Hossain, N.U.I.; Nagahi, M.; Jaradat, R.; Shah, C.; Buchanan, R.; Hamilton, M. Modeling and assessing cyber resilience of smart grid using Bayesian network-based approach: A system of systems problem. J. Comput. Des. Eng. 2020, 7, 352–366. [Google Scholar] [CrossRef]
- Franke, U.; Brynielsson, J. Cyber situational awareness - A systematic review of the literature. Comput. Secur. 2014, 46, 18–31. [Google Scholar] [CrossRef]
- Hamid, B.; Jhanjhi, N.; Humayun, M.; Khan, A.; Alsayat, A. Cyber Security Issues and Challenges for Smart Cities: A survey. In Proceedings of the 2019 13th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics (MACS), Karachi, Pakistan, 14–15 December 2019. [Google Scholar] [CrossRef]
- Colding, J.; Barthel, S. An urban ecology critique on the “Smart City” model. J. Clean. Prod. 2017, 164, 95–101. [Google Scholar] [CrossRef]
- Dragos, V.; Ziegler, J.; De Villiers, J.P.; De Waal, A.; Jousselme, A.L.; Blasch, E. Entropy-Based Metrics for URREF Criteria to Assess Uncertainty in Bayesian Networks for Cyber Threat Detection. In Proceedings of the 2019 22th International Conference on Information Fusion (FUSION), Ottawa, ON, Canada, 2–5 July 2019. [Google Scholar]
- Ahad, M.A.; Paiva, S.; Tripathi, G.; Feroz, N. Enabling technologies and sustainable smart cities. Sustain. Cities Soc. 2020, 61, 102301. [Google Scholar] [CrossRef]
- Infrastructure Interdependencies and Resilience. In Chile Earthquake of 2010; American Society of Civil Engineers: Reston, VA, USA, 2013; Volume 37, pp. 365–386. [CrossRef]
- Chourabi, H.; Nam, T.; Walker, S.; Gil-Garcia, J.R.; Mellouli, S.; Nahon, K.; Pardo, T.A.; Scholl, H.J. Understanding smart cities: An integrative framework. In Proceedings of the 2012 45th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012; pp. 2289–2297. [Google Scholar] [CrossRef]
- Djigal, H.; Jun, F.; Lu, J. Secure Framework for Future Smart City. In Proceedings of the 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud), New York, NY, USA, 26–28 June 2017; pp. 76–83. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Technical Report 2.3; Keele University: Keele, UK, 2007. [Google Scholar]
- Wohlin, C.; Runeson, P.; Höst, M.; Ohlsson, M.C.; Regnell, B.; Wesslén, A. Experimentation in Software Engineering; Springer: Berlin/Heidelberg, Germany, 2012; p. 259. [Google Scholar] [CrossRef]
- Social Science Research Unit. EPPI-Reviewer. 2021. Available online: https://eppi.ioe.ac.uk/cms/Default.aspx?tabid=2914 (accessed on 14 November 2021).
- Curt, C.; Tacnet, J.M. Resilience of Critical Infrastructures: Review and Analysis of Current Approaches. Risk Anal. 2018, 38, 2441–2458. [Google Scholar] [CrossRef] [PubMed]
- Kalinin, M.; Krundyshev, V.; Zegzhda, P. Cybersecurity risk assessment in smart city infrastructures. Machines 2021, 9, 78. [Google Scholar] [CrossRef]
- Hadjsaid, N.; Tranchita, C.; Rozel, B.; Viziteu, M.G.; Caire, R. Modeling cyber and physical interdependencies—Application in ICT and power grids. In Proceedings of the 2009 IEEE/PES Power Systems Conference and Exposition, Seattle, WA, USA, 15–18 March 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, P.; Ali, A.; Kelly, W. Data security and threat modeling for smart city infrastructure. In Proceedings of the 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), Shanghai, China, 5–7 August 2015. [Google Scholar] [CrossRef]
- Di Giorgio, A.; Liberati, F. Interdependency modeling and analysis of critical infrastructures based on Dynamic Bayesian Networks. In Proceedings of the 2011 19th Mediterranean Conference on Control & Automation (MED), Corfu, Greece, 20–23 June 2011; pp. 791–797. [Google Scholar] [CrossRef]
- Lyu, X.; Ding, Y.; Yang, S.H. Bayesian Network Based C2P Risk Assessment for Cyber-Physical Systems. IEEE Access 2020, 8, 88506–88517. [Google Scholar] [CrossRef]
- Drago, A.; Marrone, S.; Mazzocca, N.; Tedesco, A.; Vittorini, V. Model-driven estimation of distributed vulnerability in complex railway networks. In Proceedings of the 2013 IEEE 10th International Conference on Ubiquitous Intelligence and Computing and 2013 IEEE 10th International Conference on Autonomic and Trusted Computing, Vietri sul Mare, Italy, 18–21 December 2013; pp. 380–387. [Google Scholar] [CrossRef]
- Baig, Z.A.; Szewczyk, P.; Valli, C.; Rabadia, P.; Hannay, P.; Chernyshev, M.; Johnstone, M.; Kerai, P.; Ibrahim, A.; Sansurooah, K.; et al. Future challenges for smart cities: Cyber-security and digital forensics. Digit. Investig. 2017, 22, 3–13. [Google Scholar] [CrossRef]
- Caviglione, L.; Coccoli, M. A holistic model for security of learning applications in smart cities. J. E-Learn. Knowl. Soc. 2020, 16, 1–10. [Google Scholar] [CrossRef]
- Wang, W.; Yang, S.; Hu, F.; Stanley, H.E.; He, S.; Shi, M. An approach for cascading effects within critical infrastructure systems. Phys. A Stat. Mech. Its Appl. 2018, 510, 164–177. [Google Scholar] [CrossRef]
- Elmrabit, N.; Yang, S.H.; Yang, L.; Zhou, H. Insider Threat Risk Prediction based on Bayesian Network. Comput. Secur. 2020, 96, 101908. [Google Scholar] [CrossRef]
- Yeboah-Ofori, A.; Islam, S.; Brimicombe, A. Detecting cyber supply chain attacks on cyber physical systems using bayesian belief network. In Proceedings of the 2019 International Conference on Cyber Security and Internet of Things (ICSIoT), Accra, Ghana, 29–31 May 2019; pp. 37–42. [Google Scholar] [CrossRef]
- Bode, M.A.; Oluwadare, S.A.; Alese, B.K.; Thompson, A.F.B. Risk analysis in cyber situation awareness using Bayesian approach. In Proceedings of the 2015 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), London, UK, 8–9 June 2015. [Google Scholar] [CrossRef]
- Cerotti, D.; Codetta-Raiteri, D.; Egidi, L.; Franceschinis, G.; Portinale, L.; Dondossola, G.; Terruggia, R. Analysis and Detection of Cyber Attack Processes targeting Smart Grids. In Proceedings of the 2019 IEEE PES Innovative Smart Grid Technologies Europe (ISGT-Europe), Bucharest, Romania, 29 September–2 October 2019. [Google Scholar] [CrossRef]
- Cerotti, D.; Codetta-Raiteri, D.; Dondossola, G.; Egidi, L.; Franceschinis, G.; Portinale, L.; Terruggia, R. Evidence-based analysis of cyber attacks to security monitored distributed energy resources. Appl. Sci. 2020, 10, 4725. [Google Scholar] [CrossRef]
- Gaskova, D.; Massel, A. Semantic modeling of cyber threats in the energy sector using Dynamic Cognitive Maps and Bayesian Belief Network. Adv. Intell. Syst. Res. 2019, 166, 326–329. [Google Scholar] [CrossRef]
- Drago, A.; Marrone, S.; Mazzocca, N.; Nardone, R.; Tedesco, A.; Vittorini, V. A model-driven approach for vulnerability evaluation of modern physical protection systems. Softw. Syst. Model. 2019, 18, 523–556. [Google Scholar] [CrossRef]
- Marrone, S.; Rodríguez, R.J.; Nardone, R.; Flammini, F.; Vittorini, V. On synergies of cyber and physical security modelling in vulnerability assessment of railway systems. Comput. Electr. Eng. 2015, 47, 275–285. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Zhao, S.; Yuan, Y.; Sun, Q.; Zhang, K. Dynamic Security Risk Evaluation via Hybrid Bayesian Risk Graph in Cyber-Physical Social Systems. IEEE Trans. Comput. Soc. Syst. 2018, 5, 1133–1141. [Google Scholar] [CrossRef] [Green Version]
- Behl, M.; Mangharam, R. Interactive analytics for smart cities infrastructures. In Proceedings of the 2016 1st International Workshop on Science of Smart City Operations and Platforms Engineering (SCOPE) in partnership with Global City Teams Challenge (GCTC) (SCOPE-GCTC), Vienna, Austria, 11 April 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Zhu, W.; Milanovic, J.V. Interdepedency modeling of cyber-physical systems using a weighted complex network approach. In Proceedings of the 2017 IEEE Manchester PowerTech, Manchester, UK, 18–22 June 2017. [Google Scholar] [CrossRef] [Green Version]
- Tajer, A.; Kar, S.; Poor, H.V.; Cui, S. Distributed joint cyber attack detection and state recovery in smart grids. In Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011; pp. 202–207. [Google Scholar] [CrossRef]
- Ahmadi-Assalemi, G.; Al-Khateeb, H.; Epiphaniou, G.; Maple, C. Cyber Resilience and Incident Response in Smart Cities: A Systematic Literature Review. Smart Cities 2020, 3, 894–927. [Google Scholar] [CrossRef]
- House of Lords; House of Commons. Joint Committee on the National Security Strategy Cyber Security Skills and the UK’s Critical National Infrastructure: Government Response to the Committee’s Second Report of Session 2017–2019 Second Special Report of Session; House of Lords: London, UK, 2018; p. 64. [Google Scholar]
- Luiijf, H.A.; Besseling, K.; Spoelstra, M.; De Graaf, P. Ten national cyber security strategies: A comparison. Lect. Notes Comput. Sci. 2013, 6983, 1–17. [Google Scholar] [CrossRef]
- UK Trade & Investment. Smart Cities Pitchbook. In Technology is Great, Britian & Northern Ireland; Old Admiralty Building: London, UK, 2016; p. 49. [Google Scholar]
- Knapp, E. Industrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, Scada, and Other Industrial Control Systems; Syngress: Waltham, MA, USA, 2011; pp. 1–341. [Google Scholar] [CrossRef]
- Rinaldi, S.M.; Peerenboom, J.P.; Kelly, T.K. Identifying, understanding, and analyzing critical infrastructure interdependencies. IEEE Control Syst. Mag. 2001, 21, 11–25. [Google Scholar] [CrossRef]
- Rinaldi, S.M. Modeling and simulating critical infrastructures and their interdependencies. In Proceedings of the 37th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 5–8 January 2004; Volume 37, pp. 873–880. [Google Scholar] [CrossRef]
- Alcaraz, C. Critical infrastructure protection: Requirements and challenges for the 21st century. Int. J. Crit. Infrastruct. Prot. 2017, 8, 53–66. [Google Scholar] [CrossRef]
- Khan, R.; McLaughlin, K.; Laverty, D.; Sezer, S. STRIDE-based threat modeling for cyber-physical systems. In Proceedings of the 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Turin, Italy, 26–29 September 2017; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Dudenhoeffer, D.D.; Permann, M.R.; Manic, M. CIMS: A framework for infrastructure interdependency modeling and analysis. In Proceedings of the 2006 Winter Simulation Conference, Monterey, CA, USA, 3–6 December 2006; pp. 478–485. [Google Scholar] [CrossRef] [Green Version]
- St. John-Green, M.; Watson, T. Safety and Security of the Smart City—When our infrastructure goes online. In Proceedings of the 9th IET International Conference on System Safety and Cyber Security (2014), Manchester, UK, 15–16 October 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Burmester, M.; Magkos, E.; Chrissikopoulos, V. Modeling security in cyber-physical systems. Int. J. Crit. Infrastruct. Prot. 2012, 5, 118–126. [Google Scholar] [CrossRef]
- Gaber, A.; Seddik, K.G.; Elezabi, A.Y. Joint estimation-detection of cyber attacks in smart grids: Bayesian and non-Bayesian formulations. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; pp. 2245–2250. [Google Scholar] [CrossRef]
- Rana, M.M.; Bo, R.; Abdelhadi, A. Distributed Grid State Estimation under Cyber Attacks Using Optimal Filter and Bayesian Approach. IEEE Syst. J. 2021, 15, 1970–1978. [Google Scholar] [CrossRef]
- Sahu, A.; Davis, K. Structural Learning Techniques for Bayesian Attack Graphs in Cyber Physical Power Systems. In Proceedings of the 2021 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 2–5 February 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Graja, I.; Kallel, S.; Guermouche, N.; Cheikhrouhou, S.; Hadj Kacem, A. A comprehensive survey on modeling of cyber-physical systems. Concurr. Comput. Pract. Exp. 2020, 32, e4850. [Google Scholar] [CrossRef]
- Smith, M.; Paté-Cornell, E. Cyber Risk Analysis for a Smart Grid: How Smart Is Smart Enough? A Multi-Armed Bandit Approach. In A Systems Approach to Cyber Security; IOS Press: Amsterdam, The Netherlands, 2017; pp. 37–56. [Google Scholar]
- Milanović, J.V.; Zhu, W. Modeling of interconnected critical infrastructure systems using complex network theory. IEEE Trans. Smart Grid 2017, 9, 4637–4648. [Google Scholar] [CrossRef]
- Boyes, H.; Isbell, R.; Watson, T. Critical Infrastructure in the Future City Developing Secure and Resilient Cyber–Physical Systems. In Proceedings of the 9th International Conference, CRITIS 2014, Limassol, Cyprus, 13–15 October 2014; pp. 13–15. [Google Scholar]
| IEEE Xplore | 204 |
| Web of Science | 179 |
| UoG Library Discovery | 70 |
| Total | 453 |
| Authors | Main Method | Secondary Method (s) |
|---|---|---|
| Queiroz C, Mahmood A Tari Z (2013) [4] | Bayesian networks | N/A |
| Cerotti D, et al. (2019) [34] | Bayesian networks | Attack graph |
| Cerroti D, et al. (2020) [35] | Dynamic Bayesian networks | Attack graph |
| Giorgio A D Liberati F. (2011) [25] | Dynamic Bayesian networks | N/A |
| Elmrabit N, et al. (2020) [31] | Bayesian networks | N/A |
| Gaber A, Seddik G K, and Elezabi A Y. (2015) [55] | Bayesian methodology | Neyman–Pearson forms |
| Gaskova D A Massel A G. (2019) [36] | Bayesian network | Dynamic cognitive maps |
| Hossain N U I, et al. (2020) [9] | Bayesian networks | N/A |
| Le A, et al. (2019) [6] | Bayesian networks | Factor Analysis of Information Risk Loss Event Frequency (FAIR LEF) |
| Liu X, et al. (2021) [7] | Bayesian attack-defence game model | Refined Bayesian Nash equilibrium |
| Bode M A, et al. (2015) [33] | Bayesian networks | N/A |
| Rana M M, Bo R Abdelhadi. (2020) [56] | Bayesian networks | Optimal filter theory Graph theory |
| Marrone S, et al. (2015) [38] | Bayesian networks | Petri nets |
| Li S, et al. (2018) [39] | Hybrid Bayesian risk graph (HBRG) | Hidden Markov model |
| Sahu A Davis K. (2021) [57] | Bayesian attack graphs | Machine-based structured learning |
| Drago V, et al. (2019) [13] | Bayesian networks | N/A |
| Lyu X, Ding Y Yang S H. (2020) [26] | Bayesian networks | N/A |
| Wang P, et al. (2018) [30] | Bayesian networks | Attack graphs |
| Drago A, et al. (2013) [27] | Two-layered Bayesian networks | N/A |
| Yeboah-Ofori A, et al. (2019) [32] | Bayesian belief network | N/A |
| M Smith M Pate-Cornell (2017) [59] | Bayesian-adaptive multi-armed bandits | N/A |
| J Milanovic W Zhu (2017) [60] | Complex network theory | N/A |
| Caviglione L Coccoli M (2020) [29] | Identification and classification Model-driven design | N/A |
| Djigal H, Jun F Lu J. (2017) [17] | Zero-Knowledge Protocol using Elliptic Curve Discrete Logarithm Problem | N/A |
| Zografopoulos I, Ospina J, Konstantinou C. (2020) [2] | Typical holistic risk assessment framework | N/A |
| Behl M Mangharam R. (2016) [40] | Regression trees-based models | N/A |
| Wang P, Ali A Kelly W. (2015) [24] | Typical threat modelling methodology | N/A |
| Zhu W Milanovic J V. (2017) [41] | Weighted complex network theory | N/A |
| Reactive Restoration | Physical Proactive Countermeasures |
|
Survivability, Information diversity score, Service state, Interdependencies, Heterogeneity, Stability, Recoverability, Resilience, Redundancy. | Monitoring, Atomic events, Boundary values, Constraints, Intentions, Impact, System performance, Scalability, Physical layer, Field control layer, Learner space, Data space, Infrastructure space, Security policy, Predictive value, Electrical distance, Risk. |
| Cyber Proactive Countermeasures | Threat Characteristics |
|
Network traffic, Communication-layer, Monitoring, Offline diagnosis (smoothing), Reporting, Propagation level, Service layers, Bad data, Detector decision, Hypothesis, Cost value (non-financial), Concepts, types, Boundary values, Sensitivity analysis, factors, sub-factors, Vulnerability, Control strength, Constraints, Intentions, Impact, System performance, vulnerability, Alerts, Scalability, Data dependency, Time complexity, Accuracy, Precision, Interpretation, Simplicity, Expressiveness, Definiteness of state, Evidence impact, Process monitoring layer, Enterprise management layer, Services, Learner space, Data space, Infrastructure space, Loc/Glob-Storage, Data processing, Security policy, Resources, Leaf support, Predictive value, Confidence, Threat intelligence, Vulnerable-Weighted, Risk, Link direction. | Attack capabilities, Prediction, Probability, Severity, Loss event frequency, Attack techniques, Threat capabilities, End goal, Attack mission, Type, Attack sequence, General, Specific, Impairment, Action, Weight adjustment, CVSS. — Insider Threat Exclusive — Technical factors, Organisational factors, Human factors, Risk, User profiles, Keywords, Behaviour, Influences. |
| Authors | Validation Method | Secondary Method (s) |
|---|---|---|
| Queiroz C, Mahmood A Tari Z (2013) [4] | Simulation | N/A |
| Cerotti D, et al. (2019) [34] | Case study | N/A |
| Cerroti D, et al. (2020) [35] | Case study | Expert opinion |
| Giorgio A D Liberati F. (2011) [25] | Case study | N/A |
| Elmrabit N, et al. (2020) [31] | Case study | Expert opinion |
| Gaber A, Seddik G K, and Elezabi A Y. (2015) [55] | Case study | N/A |
| Gaskova D A Massel A G. (2019) [36] | Example demonstration | N/A |
| Hossain N U I, et al. (2020) [9] | Case study | Expert opinion |
| Le A, et al. (2019) [6] | Experiment | Expert opinion |
| Liu X, et al. (2021) [7] | Case study | N/A |
| Bode M A, et al. (2015) [33] | Experiment | N/A |
| Rana M M, Bo R Abdelhadi. (2020) [56] | Simulation | N/A |
| Marrone S, et al. (2015) [38] | Case study | N/A |
| Li S, et al. (2018) [39] | Experiment | N/A |
| Sahu A Davis K. (2021) [57] | Experiment | N/A |
| Drago V, et al. (2019) [37] | Case study | Expert models |
| Lyu X, Ding Y Yang S H. (2020) [26] | Case study | Expert opinions |
| Wang P, et al. (2018) [30] | Experiment | N/A |
| Drago A, et al. (2013) [27] | Experiment | N/A |
| Yeboah-Ofori A, et al. (2019) [32] | Case study | N/A |
| M Smith & M Pate-Cornell (2017) [59] | Case study | N/A |
| J Milanovic & W Zhu (2017) [60] | Case study | N/A |
| Caviglione L & Coccoli M (2020) [29] | Toy example | N/A |
| Djigal H, Jun F Lu J. (2017) [17] | Simulation cases | N/A |
| Zografopoulos I, Ospina J, and Konstantinou C. (2021) [2] | Case study | N/A |
| Behl M Mangharam R. (2016) [40] | Case study | N/A |
| Wang P, Ali A Kelly W. (2015) [24] | Experiment | N/A |
| Zhu W Milanovic J V. (2017) [41] | Experiment | N/A |
| Author | Methodology Application | Main Method | Sec. Method (s) | Threat Actor Type | Test Data Method | Validation | Key Metrics |
|---|---|---|---|---|---|---|---|
| Queiroz C, Mahmood A, and Tari Z. (2013) [4] | Predicting probabilistic survivability model for SCADA systems. | Bayesian networks | N/A | SCADA-focused cyber-attacks | Simulation | <<< | Information diversity score, survivability, service states, network traffic. |
| Cerotti D, et al. (2019) [34] | Framework to analyze and detect the smart grid infrastructure (also industrial control systems) | Bayesian networks | Attack graph | Predictive and diagnostic analysis | Case study | <<< | Attack capabilities, dependencies, communication. |
| Cerotti D, et al. (2020) [35] | Understanding cyber-security for distributed energy plants for both casual and temporal time. | Dynamic Bayesian networks | Attack graph | Predictive and diagnostic analysis of threat dependencies | Case study | Expert opinions | Monitoring, prediction, offline diagnosis, reporting messages. |
| Giorgio A D and Liberati F. (2011) [25] | Analyzing the different layers of critical infrastructure interdependency for modelling and simulation analysis. | Dynamic Bayesian networks | N/A | Analysis of critical infrastructure interdependencies | Case study | <<< | atomic events, propagation, services layers. |
| Elmrabit N, et al. (2020) [31] | Proactive insider risk predictive analysis framework for technical and non-technical threats. | Bayesian networks | N/A | Insider threat risk prediction | Case study | Expert opinions | Technical factors, organizational factors, human factors, risk level. |
| Gaber A, Seddik G K, and Elezabi A Y. (2015) [55] | Threat modelling methodology with joint estimation-detection for cyber-attacks towards the smart grid. | Bayesian methodology | Neyman-Pearson forms | Cyber-attacks in the smart grid | Case study | <<< | Bad data, detector decision, hypothesis, probability, cost value. |
| Gaskova D A and Massel A G. (2019) [36] | Relationship modelling methodology of cyber-threats towards the energy sector. | Bayesian network | Dynamic cognitive maps | Cyber-attacks in the smart grid | Example demonstration | <<< | Concepts, type, boundary values, pre-crisis/crisis. |
| Hossain N U I, et al. (2020) [9] | Modelling cyber-security within the smart grid system of systems for characteristics of resilience, vulnerability, and restoration. | Bayesian networks | N/A | Cyber-attacks in the smart grid | Case study | Expert opinion | Sensitivity analysis, resilience, factors and sub-factors, recoverability. |
| Le A, et al. (2019) [6] | Smart grid cyber-threat framework using analysis of information risk to identify cyber-security attacks. | Bayesian network | Factor Analysis of Information Risk Loss Event Frequency (FAIR LEF) | Cyber-attacks in the smart grid | Experiment | Expert opinion | Threat severity, vulnerability, event frequency, control strength. |
| Liu X, et al. (2021) [7] | Quantitative cyber-physical security analysis methodology for industrial control systems. | Bayesian attack-defense game model | Refined Bayesian Nash equilibrium | Cyber-attacks in the smart grid | Case study | <<< | Attack techniques, threat capabilities, end goal, |
| Bode M A, et al. (2015) [33] | Cyber situation awareness risk analysis through probability risk matrixes to identify key attack attributes. | Bayesian networks | N/A | Cyber situational awareness risk analysis | Experiment | <<< | Attack mission, constraints, capabilities, intentions, impact, types. |
| Rana M M, Bo R and Abdelhadi. (2020) [56] | Threat modelling methodology for distributed grid dynamic state estimation algorithm. | Bayesian networks | Optimal filter theory Graph theory | Cyber-attacks in the smart grid | Simulation | <<< | Resilience, false data, attack sequence |
| Marrone S, et al. (2015) [38] | Modelling methodology for both cyber and physical security vulnerability assessment railway system infrastructure. | Bayesian networks | Petri nets | Cyber and physical modelling of railway systems | Case study | <<< | System performance, vulnerability. |
| Li S, et al. (2018) [39] | Proposed dynamic security risk evaluation framework for cyber-physical systems to analyse attack activity patterns and risk propagations cross layer. | Hybrid Bayesian risk graph (HBRG) | Hidden Markov model | Cyber-attacks on cyber-physical social-based systems | Experiment | <<< | Attack types, user profiles, keywords, behaviour, influences. |
| Sahu A and Davis K. (2021) [57] | Attack graph machine learning techniques to understand cyber-physical power architecture evaluated score-based modelling and simulation. | Bayesian attack graphs | Machine-based structured learning | Cyber-attacks in the smart grid | Experiment | <<< | Alerts, scalability, data dependency, time complexity, accuracy. |
| Drago V, et al. (2019) [37] | Applying entropy metrics to assess uncertainty with the purpose of cyber threats detections. | Bayesian networks | N/A | Uncertainty analysis of cyber-attacks | Case study | Expert models | Accuracy, precision, interpretation, simplicity, expressiveness, definiteness of state, evidence impact. |
| Lyu X, Ding Y and Yang S H. (2020) [26] | Hierarchical identify cyber-to-physical risk assessment for cyber-physical systems to identify impacts on physical process safety. | Bayesian networks | N/A | Cyber-attacks at cyber-physical systems | Case study | Expert opinions | Physical, field control, process monitor, enterprise management. |
| Wang P, et al. (2018) [30] | Relationship framework for understanding cyber-security to classify and attacks into groups and specialized variety. | Bayesian networks | Attack graphs | Cyber attack inference | Experiment | <<< | General threat, specific threat, vulnerability, capabilities, |
| Drago A, et al. (2013) [27] | Model-driven distributed vulnerability methodology towards complex railway network cyber-physical systems. | Two-layered Bayesian networks | N/A | Cyber and physical | Experiment | <<< | Threat, service, system, attack, protection, impairment, action, object. |
| Yeboah-Ofori A, et al. (2019) [32] | Detecting supply chain attacks on cyber-physical systems through Bayesian belief networks. | Bayesian belief network | N/A | Cyber and physical | Case study | <<< | Malware propagation characteristics, attacker data, cybercrime type manipulation |
| M Smith and M Pate-Cornell (2017) [59] | Cyber risk analysis for the smart grid using multi-armed bandit approach | Bayesian-adaptive multi-armed bandits | N/A | Cyber and physical | Case study | <<< | Defensive value, optimal allocation, finance, Time remaining |
| J Milanovic W Zhu (2017) [60] | Modelling interconnected critical infrastructure using three dimensional complex network theory | Complex network theory | N/A | Cyber and physical | Case study | <<< | Adjacency matrix, node degree, path length and geodesics, betweenness centrality, efficiency. |
| Caviglione L and Coccoli M. (2020) [29] | Holistic model for cyber-security e-learning towards smart city infrastructure across three homogenous groups to classify threats and vulnerabilities. | Identification and classification Model-driven design | N/A | Cyber-security learning for smart cities. | Toy example | <<< | Learner space, data space, infrastructure space, attack type. |
| Djigal H, Jun F and Lu J. (2017) [17] | Secure framework called “SEFSCITY” for smart city infrastructure development governance surrounding key aspects. | Zero-Knowledge Protocol using Elliptic Curve Discrete Logarithm Problem | N/A | Threat modelling for smart cities | Simulation cases | <<< | Loc-storage, glob-storage, data processing, security policy. |
| Zografopoulos I, Ospina J, and Konstantinou C. (2021) [2] | Overview literature review for the cyber-physical security within the energy sector environment. | Typical holistic risk assessment framework | N/A | Cyber-attacks in the smart grid | Case study | <<< | Resources, frequency stability, time, packets |
| Behl M and Mangharam R. (2016) [40] | Reviewing different interactive analytic smart cities infrastructure for key metrics and evaluated systems. | Regression trees-based models | N/A | Threat modelling for smart cities | Case study | <<< | Leaf support, predicted value, confidence. |
| Wang P, Ali A, and Kelly W. (2015) [24] | Threat modelling methodologies for smart city infrastructure for data security and identification of threats. | Typical threat modelling methodology | N/A | Data security and threat modelling smart cities | Experiment | <<< | Threat value, threat weight, threat factor, weight adjustment, CVSS scores, threat intelligence. |
| Zhu W and Milanovic J V. (2017) [41] | Modelling of cyber-physical systems infrastructure interdependencies using weighted system and three-dimensioned approach. | Weighted complex network theory | N/A | Analysis of critical infrastructure interdependencies | Experiment | <<< | Distance, vulnerability-weighted, link direction, risk. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wright, M.; Chizari, H.; Viana, T. A Systematic Review of Smart City Infrastructure Threat Modelling Methodologies: A Bayesian Focused Review. Sustainability 2022, 14, 10368. https://doi.org/10.3390/su141610368
Wright M, Chizari H, Viana T. A Systematic Review of Smart City Infrastructure Threat Modelling Methodologies: A Bayesian Focused Review. Sustainability. 2022; 14(16):10368. https://doi.org/10.3390/su141610368
Chicago/Turabian StyleWright, Marc, Hassan Chizari, and Thiago Viana. 2022. "A Systematic Review of Smart City Infrastructure Threat Modelling Methodologies: A Bayesian Focused Review" Sustainability 14, no. 16: 10368. https://doi.org/10.3390/su141610368
APA StyleWright, M., Chizari, H., & Viana, T. (2022). A Systematic Review of Smart City Infrastructure Threat Modelling Methodologies: A Bayesian Focused Review. Sustainability, 14(16), 10368. https://doi.org/10.3390/su141610368







