Valuable Business Knowledge Asset Discovery by Processing Unstructured Data
Abstract
:1. Introduction
- Every company has logs to be used as an entry to the process mining tools, which is not true, bearing in mind that from the 333.34 million companies existing around the world, 332.99 million are Small and Medium Enterprises (Source: Eurostat; ILO; OECD; Statista; World Bank), with few resources to invest on process mining tools.
- For companies that already have logs, the identification of data that will lead to intangible asset identification among existing logs is a critical, albeit difficult, task for the business.
- A systemic approach, based on the existing relationship between employee and stakeholder knowledge of the organizational business goals, which can, throughout the execution of the methodological process, operate within complex real-world environments where process mining software tools are used to more accurately represent the underlying activities in each of the respective processes.
- An agile business intelligence and natural language processing approach, based on the performed data processing, which can, throughout the process, operate on and manage lots of datasets from heterogeneous sources and with different formats.
2. State of the Art
- -
- Reference [10] gathers the most recent works around BI, capable of handling all data types. Existing works promote the rapid adaptation of the organization’s BI systems to the changes required by the business, thus, promoting system flexibility, but it does not map data with the strategic and business objectives of the company.
- -
- Reference [11] presents an extensive literature review on process mining, highlighting that process mining is a new kind of Business Analytics and has emerged as a powerful family of Process Science techniques for analyzing and improving business. Existing works fail to address unstructured data or define business-critical information and knowledge assets. It is stated that “The current scientific literature does not present an up-to-date research agenda specifying the directions the application of PM can take in Business Management”.
- -
- Reference [12] introduces a practical guide on how to implement an agile BI project, again improving the flexibility demanded by BI systems. However, it does not mention which data types can be processed, nor does it provide any steps to define business-critical information and knowledge assets.
- Compatibility with most IT tools: the criterion applied for this variable to be rated as “Yes” was for the software tool to be compatible with at least six or more tools known on the market or in the corporate environment.
- Definition of strategic and business objectives required: this variable is based on the fact that process mining does not require the company to define its strategic and business objectives to implement the project.
- Level of detail of organizational processes (Low, Medium, High): this variable is assessed according to three levels: 1. Low (L), when company organizational processes have not been digitalized or formalized, 2. Medium (M), when some company organizational processes have been digitalized, although others may or may not be formalized and 3. High (H), when most company organizational processes have been digitalized and all have been formalized.
- Knowledge of business and IT systems required: the criterion applied for this variable to be rated as “Yes” was based on the professional effort required by a company to implement a process mining project.
- Known and proven methodologies used: this variable is based on the fact that the process mining definition and structure do not use any known or proven methodology in the IT and business environment since it is based exclusively on tool deployment and use in order to later analyze the automatically generated process models.
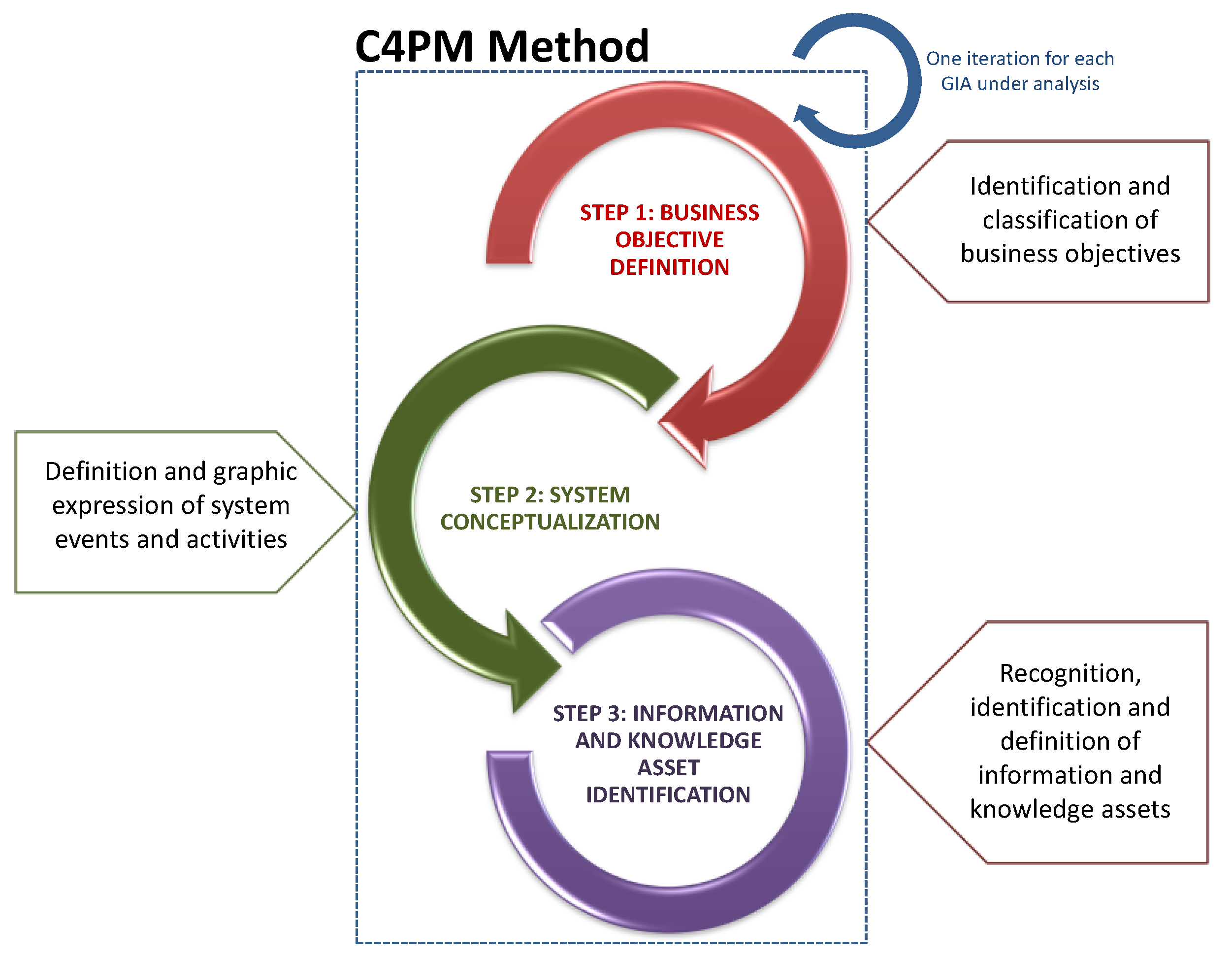
3. Materials and Methods
- Main requirement: create an agile, systemic and iterative approach using natural language processing techniques to discover behavioral patterns in the analyzed data. These steps should be applied in a balanced way according to the business objectives and should not be limited to a specific project; that is, experts in software and IT solution development and IT and security managers should be able follow these steps to adopt this method in their projects as a building block to implement any type of action on the identified information and knowledge assets.
- Find answers to the next four key questions:
- o
- Question 1: What is the flow of non-physical assets within the organizational processes?
- o
- Question 2: How can we discover the use to which these assets are put?
- o
- Question 3: How locatable are these assets?
- o
- Question 4: Which assets can be used to improve company sustainability?
- GIA 1. Production model/model of service execution: operational vision of production (goods and services) and related knowledge application and transfer practices.
- GIA 2. Commercial or customer model: company’s commercial plan, including client management directives.
- GIA 3. Supply and diversification of services model/model of innovation: approach and process for any business development initiative related to the delivery of goods or services and their modification. It also includes management initiatives and policies for business improvement.
- GIA 4. Model of international geographic expansion: international business expansion guidance, procedures, policies and schemes.
- GIA 5. Models of human resources/professional development/principles and values: policies for the supervision, organization and administration of the company workforce, including professional improvement and modernization and moral and ethical (professional and personal) basics for the business.
- GIA 6. Remuneration and property model: salary distribution policy, financial incentives and company ownership.
- GIA 7. Model of brand development: business vision and rules for marketing campaigns and improvements in public impact.
- GIA 8. Model of institutional relations and high-level networking/stakeholders: business regulations for professional alliances and industry and social involvement.
- GIA 9. Model of organization and processes: procedures and rules for the satisfactory operation of any business processes.
- GIA 10. Model of organizational strategy, mission and vision: high-level company strategies and directions and business philosophy, organizational and behavioral guidelines and relation with stakeholders and market institutions.
- GIA 11. Model of organizational knowledge management: company mechanisms, tools and models that enable the elicitation, gathering, recovery, use, evolution and valuation of company know-how.
- High: detailed description, formally established by the company, of its strategic objectives, organizational processes and mechanisms and qualitative and quantitative business objective performance indicators.
- Medium: less-detailed description of the strategic objectives and organizational processes that the company has formally established.
- Low: a generic description of the strategic objectives and organizational processes have not yet been formally established by the company.
4. Case Study Results
4.1. Valuable Assets Discovered for Accounting Department
4.1.1. Structural Knowledge Type (16 Identified Knowledge Assets)
- Order request procedure: The company can provide a clear definition of this asset to the respective area to improve the management of customer order requests. This asset can also be adapted and/or improved within the company’s organizational processes.
- Stock list: With this asset, the company will be able to analyze the available lists and define a template that facilitates stock management for its employees.
- Register of shares: With this asset, the company will be able to keep control of all the shares it acquires, helping it to make decisions on its investments.
- Procedure for share purchases: The company can provide a clear definition of this asset to the respective area to improve the management of share purchases. This asset can also be adapted and/or improved within the company’s organizational processes.
- List of services: With this asset, the company will be able to monitor the services offered and promote their internal and external dissemination, whereby it will be able to consider/improve new services.
- Cash flow reports: With this asset, the company will be able to adapt/improve the cash flow reporting templates, providing the respective area with better financial control, which contributes to making better strategic decisions.
- List of rates: The company will be able to provide a clear definition of this asset to the respective areas to control the tariffs applied to the services. Likewise, this asset can be analyzed to define a single format that improves the time taken to define the tariffs applied to the services.
- List of orders: With this asset, the company will be able to analyze the available lists and define a template that makes it easier for its employees to attend to orders, improving response times to customers.
- Sales reports: With this asset, the company will be able to adapt/improve the sales report templates, providing the respective area with a better financial control of sales and, thus, helping to make better, more timely decisions.
- Expenditure reports: With this asset, the company will be able to adapt/improve the expense report templates, providing the respective area with better financial control of expenses, thus, contributing to better strategic decision making.
- Payment reports: With this asset, the company will be able to adapt/improve payment report templates, providing the respective area with better financial control of payments, thus, contributing to better strategic decision making.
- Risk reports: With this asset, the company will be able to analyze and adapt/improve the available reports by defining a template, which facilitates better risk control over investments.
- Database maintenance procedure: The company can provide a clear definition of this asset to the respective area to improve the management of the databases. This asset can also be adapted and/or improved within the company’s organizational processes.
- Procedure for the operation of IT systems: The company can provide a clear definition of this asset to the corresponding area to improve the management of the databases. This asset can also be adapted and/or improved within the company’s organizational processes.
- Continuity planning procedures: The company can provide a clear definition of this asset to the respective area to ensure the integrity and continuity of the systems. This asset may also be adapted and/or enhanced within the organizational processes of the company.
- Information retrieval processes: The company can provide a clear definition of this asset to the respective area to ensure contingency plans for the recovery of system information. Likewise, this asset may be adapted and/or improved within the company’s organizational processes.
4.1.2. Human Knowledge Type (Four Identified Knowledge Assets)
- Security standards compliance criteria documents (ISO): With this asset, the company will be able to analyze how the process is carried out for improvement purposes and to establish formats to help the respective area understand, update and identify the company’s shortcomings in terms of maintaining ISO standards.
- Information systems audit reports: The company will be able to analyze this asset to improve the security, availability and integrity of its information systems. In addition, it will be able to adapt/create a template to improve decision making in the respective area.
- Minutes of meeting agreements: The company will be able to analyze this asset to improve decision making, keeping the focus on meeting agreements. In this way, the company will be able to make meetings more and more productive.
- Project initiation minutes: The company will be able to analyze this asset to improve decision making on projects in order to produce the desired deliverables within the established timeframe.
4.2. Valuable Assets Discovered for Investment Relations Department
4.2.1. Structural Knowledge Type (Six Identified Knowledge Assets)
- Border protocols: The company will be able to provide a clear definition of this asset to the respective area for adaptation and/or improvement within the company’s organizational processes.
- Energy trading procedure: The company can provide a clear definition of this asset to the respective area to improve energy service commercialization. This asset can also be adapted and/or improved within the company’s organizational processes.
- List of customers: With this asset, the company will be able to analyze the available lists and define a template that will enable its employees to improve customer service and promote customer loyalty.
- Market reports on employee management in the energy sector: With this asset, the company will be able to adapt/improve the templates of market reports, helping the respective area to carry out better talent management in energy services.
- On-boarding and employee monitoring procedures: The company will be able to provide a clear definition of this asset to the respective area to improve talent management in the organization. Likewise, this asset can be adapted and/or improved within the company’s organizational processes.
- List of gas company employees: With this asset, the company will be able to analyze the available rosters and define a template that will help the organization to understand the existing talent in the gas sector.
4.2.2. Human Knowledge Type (13 Identified Knowledge Assets)
- Pulp extraction process for paper production: The company will be able to provide a clear definition of this asset to the respective area to improve the pulp extraction process and facilitate paper manufacturing.
- Forest exploitation reports: With this asset, the company will be able to adapt/improve the templates of forest exploitation reports, providing the respective area with better control over this activity, thus, contributing to better strategic decision making.
- Gas standards guidelines: With this asset, the company will be able to analyze how standards are evolving in the gas sector to enable the respective area to understand, update and identify gaps in the company’s ability to maintain these standards.
- Product delivery procedure in the energy sector: The company can provide a clear definition of this asset to the respective area to improve the delivery of energy service products to its customers. This asset can also be adapted and/or improved within the company’s organizational processes.
- Minutes of meeting agreements: The company will be able to analyze this asset to improve decision making, keeping the focus on meeting agreements. In this way, the company will be able to make meetings more and more productive.
- Project initiation minutes: The company will be able to analyze this asset to improve decision making on projects and output the desired deliverables within the established timeframe.
- Time scheduling documents for the operation of gas systems: With this asset, the company will be able to analyze how this process is carried out for improvement purposes and establish formats to help the respective area to understand, update and schedule gas system operation that guarantees service availability for customers.
- California Power System Operation Scheduling Documents: With this asset, the company will be able to analyze how this process is carried out for improvement purposes and establish formats to help the respective area to understand, update and schedule energy system operation in a state (California) that guarantees service availability for customers.
- Gas system operating procedure: The company will be able to provide a clear definition of this asset to the respective area to improve the gas system operation process.
- Research work in the energy, oil and gas industry: With this asset, the company will be able to analyze scientific advances in the energy, oil and gas industry to improve its production processes and the strategy to be applied in each sector.
- List of sports teams: With this asset, the company will be able to analyze the available rosters and define a template that will enable the respective area to better manage talent for sporting activities.
- Sports practice guide: With this asset, the company will be able to analyze how employee sports activities are carried out and improve their management.
- Championship results reports: With this asset, the company will be able to analyze the development of sporting activities in order to make better strategic decisions about the organization’s talent.
4.2.3. Relational Knowledge Type (Seven Identified Knowledge Assets)
- Agreements with other companies (Dynergy): The company will be able to analyze this asset to improve strategic decision making on agreements with other organizations.
- Investor agreements: The company will be able to analyze this asset to improve strategic decision making on agreements with various investors.
- Customer contracts in the gas sector: With this asset, the company will be able to analyze how contracts with customers in the gas sector are drawn up in order to improve their format and ensure compliance.
- Partner agreements: The company will be able to analyze this asset to improve strategic decision making on the services provided, based on the agreements established with various partners.
- Contracts with customers and suppliers: With this asset, the company will be able to analyze how contracts with customers and service providers are drawn up in order to improve their format and ensure compliance.
- Court reports: With this asset, the company will be able to analyze and report the cases settled by a court to the respective area in order to establish the necessary corrective measures that lead to better strategic decision making.
- List of partners: With this asset, the company will be able to analyze the available lists and define a template to help the respective area better manage activities with the organization’s partners.
5. Discussion: Theoretical and Practical Implications
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Andriole, S. The Hard Truth About Soft Digital Transformation. IT Prof. 2020, 22, 13–16. [Google Scholar] [CrossRef]
- U.N. Digital Economy Report 2019. In Value Creation and Capture: Implications for Developing Countries; United Nations: New York, NY, USA, 2019; ISBN1 9210042166. ISBN2 9789210042161.
- Andrew, J.H. The next phase of business sustainability. In Stanford Social Innovation Review; Stanford University: Stanford, CA, USA, 2018; Volume 16, pp. 34–39. [Google Scholar] [CrossRef]
- Xu, X.L.; Li, J.; Wu, D.; Zhang, X. The intellectual capital efficiency and corporate sustainable growth nexus: Comparison from agriculture, tourism and renewable energy sector. Environ. Dev. Sustain. 2021, 23, 16038–16056. [Google Scholar] [CrossRef]
- van Zelst, S.J.; Buijs, J.C.A.M.; Vázquez-Barreiros, B.; Lama, M.; Mucientes, M. Repairing Alignments of Process Models. Bus. Inf. Syst. Eng. 2019, 62, 289–304. [Google Scholar] [CrossRef] [Green Version]
- Sanchez-Segura, M.-I.; Ruiz-Robles, A.; Medina-Dominguez, F.; Dugarte-Peña, G.-L. Strategic characterization of process assets based on asset quality and business impact. Ind. Manag. Data Syst. 2017, 117, 1720–1737. [Google Scholar] [CrossRef]
- Burton, B.; Scheibenreif, D.; Barnes, H.; Smith, M.; Buytendijk, F.; Bradley, A. Digital Business Gives Rise to the New Economics of Connections. Gartner 2015, 1–11, Retrieved 2020. Available online: https://www.gartner.com/smarterwithgartner/the-economics-of-connections (accessed on 5 October 2022).
- Schiuma, G. The managerial foundations of knowledge assets dynamics. Knowl. Manag. Res. Pract. 2009, 7, 290–299. [Google Scholar] [CrossRef]
- Otero, E.; Schwarz, M. Review of the literature on the techniques and methods for measuring Intellectual Capital. Rev. Científica De La UCSA 2018, 5, 41–60. Available online: http://ucsa.edu.py/yeah/wp-content/uploads/2018/05/7_AR2_Otero-E_Revisión-de-la-literatura-de-las-técnicas-y-métodos-de-medición_41-60.pdf (accessed on 4 October 2022). [CrossRef] [Green Version]
- Tabrizi, B.; Lam, E.; Girard, K.; Irvin, V. Digital Transformation is Not About Technology. Harv. Bus. Rev. 2019, 2–7. Available online: https://hbr.org/2019/03/digital-transformation-is-not-about-technology (accessed on 4 October 2022).
- Fakir, M.; Baslam, M.; El Ayachi, R. Business Intelligence: 6th International Conference, CBI 2021Beni Mellal, Morocco, May 27–29, 2021, Proceedings; Springer International Publishing: Berlin/Heidelberg, Germany, 2021. [Google Scholar] [CrossRef]
- Zerbino, P.; Stefanini, A.; Aloini, D. Process Science in Action: A Literature Review on Process Mining in Business Management. Technol. Forecast. Soc. Chang. 2021, 172, 121021. [Google Scholar] [CrossRef]
- Williams, M.; Ariyachandra, T.; Frolick, M. Business Intelligence- Success Through Agile Implementation. J. Manag. Eng. Integr. 2017, 10, 14–21. Available online: https://www.journalmei.com/_files/ugd/f76c8e_e5ea95afc7e9468cb279f9b89a825fb1.pdf (accessed on 4 October 2022).
- Janssenswillen, G.; Depaire, B. Towards Confirmatory Process Discovery: Making Assertions About the Underlying System. Bus. Inf. Syst. Eng. 2018, 61, 713–728. [Google Scholar] [CrossRef]
- Viner, D.; Stierle, M.; Matzner, M. A Process Mining Software Comparison. In Proceedings of the Conference: 2nd International Conference on Process Mining (ICPM), Padova, Italy, 4–9 October 2020; pp. 19–222. Available online: https://www.researchgate.net/publication/344657667_A_Process_Mining_Software_Comparison (accessed on 4 October 2022).
- De Cnudde, S.; Claes, J.; Poels, G. Improving the quality of the Heuristics Miner in ProM 6.2. Expert Syst. Appl. 2014, 41, 7678–7690. [Google Scholar] [CrossRef] [Green Version]
- Johannesson, P.; Perjons, E. An Introduction to Design Science; Springer International Publishing Switzerland: Stockholm, Sweden, 2014. [Google Scholar] [CrossRef]
- Sanchez-Segura, M.I.; Dugarte-Peña, G.; Amescua, A.; Medina-Dominguez, F. Exploring how the intangible side of an organization impacts its business model. Kybernetes 2020, 50, 2790–2822. [Google Scholar] [CrossRef]
- Chen, J. Enron (Company Profile). 2019. Available online: https://www.investopedia.com/terms/e/enron.asp (accessed on 4 October 2022).
- Cohen, W.W. Enron Email Dataset. 2015. Available online: http://www.cs.cmu.edu/~enron/ (accessed on 4 October 2022).
- Chabrak, N.; Daidj, N. Enron: Widespread myopia. Crit. Perspect. Account. 2007, 18, 539–557. [Google Scholar] [CrossRef]









| Tool Name (Manufacturer) | Supported Log File Extensions | Compatibility with Most IT Tools | Definition of Strategic and Business Objectives Required | Level of Detail of Organizational Processes (Low, Medium, High) | Knowledge of Business and IT Systems Required | Known and Proven Methodologies Used |
|---|---|---|---|---|---|---|
| ABBYY Timeline (ABBYY) | csv | No | No | M, H | Yes | No |
| ARIS Process Mining (Software AG) | csv, xls | Yes | No | M, H | Yes | No |
| BusinessOptix (BusinessOptix) | csv, xes, xml | Yes | No | M, H | Yes | No |
| Celonis Process Mining (Celonis SE) | csv, xlsx, xes | Yes | No | M, H | Yes | No |
| Disco (Fluxicon BV) | csv, txt, xls(x), mxml, xes | Yes (Via API) | No | M, H | Yes | No |
| EverFlow (EverFlow) | csv, xls, xml, xes, json | No | No | M, H | Yes | No |
| LANA Process Mining (Lana Labs GmbH) | csv | Yes | No | M, H | Yes | No |
| Logpickr Process Explorer 360 (Logpickr) | csv, txt | Yes (Vía API) | No | M, H | Yes | No |
| MEHRWERK ProcessMining (Mehrwerk GmbH) | csv, excel files, xml, dif, json | Yes | No | M, H | Yes | No |
| Minit (Minit j.s.a.) | csv, xes, mxml, xls(x) (m)(b), mdb, accdb | No | No | M, H | Yes | No |
| MyInvenio (myInvenio Srl.) | csv, xes | Yes | No | M, H | Yes | No |
| PAFnow (Process Analytics Factory GmbH) | csv, txt, excel formats | Yes | No | M, H | Yes | No |
| ProDiscovery (Puzzle Data Co., Ltd.) | csv, txt | No | No | M, H | Yes | No |
| QPR ProcessAnalyzer (QPR Software Plc) | csv, xes | Yes | No | M, H | Yes | No |
| Signavio Process Intelligence (Signavio GmbH) | csv, xes | Yes | No | M, H | Yes | No |
| UiPath Process Mining (UiPath Inc.) | csv, tsv, xls(x), txt, xes | No | No | M, H | Yes | No |
| Inputs | Level of Detail |
|---|---|
| Strategic objective: To increase the value of the company‘s shares | Low |
| Generic intangible asset model: GIA 1. Production model/model of service execution | Low |
| Employee | Most Frequently Used Words | Identified Assets |
|---|---|---|
| allen-p | buy, mail, information, message, phillip, downgraded, border, account, email, use, know, enron, request, new, need, see, password, strong, shares, sent, time, recipient, change, like, price, review, receive, original, subject, free, stock, coverage, first, initiated, company, type, date, corp, visit, read, back, allen, send, plan, questions, distribution, make, year, look, section, upgraded, cash, call, days, available, home, meeting, last, want, today |
|
| arnold-j | enron, company, said, new, credit, financial, trading, energy, billion, stock, week, shares, john, dynegy, business, jones, york, last, investors, year, message, dow, corp, mr, deal, news, houston, gas, sent, price, power, market, service, day, companies, street, rating, could, time, original, wall, million, rights, copyright, like, cash, fastow, transactions, know, email, reserved, monday, chief, reuters, friday, debt, markets, exchange, partnerships, offer |
|
| arora-h | size, align, right, nbsp, new, left, enron, request, day, rates, year, message, call, free, see, continental, miles, time, report, week, date, email, specials, information, available, research, rate, harry, sent, power, make, analyst, houston, options, subject, review, price, offer, daily, november, businesses, market, mail, online, questions, purchase, investor, original, table, dynegy, page, monday, want, gas, name, financial, business, hr, need, data |
|
| causholli-m | top, align, gt, right, news, story, nov, valign, cn, enron, pulp, paper, section, message, detail, control, function, nbsp, digest, table, november, page, view, border, mail, information, contact, market, email, sent, original, press, mailto, edition, time, left, li, release, ou, october, dna, year, name, recipient, today, new, corp, use, service, products, like, cellpadding, online, finance, lumber, company, forest, intended, prices |
|
| corman-s | gas, day, october, sent, order, original, enron, know, need, call, information, related, message, shelley, pipelines, cash, security, market, report, new, imbalance, time, business, net, tw, email, questions, month, attached, area, mail, line, march, meeting, number, control, like, monday, issues, imbalances, interstate, quantities, pmto, standards, capacity, dell, european, july, gisb, contact, revised, following, comments, current, nexis, gary, contract, pipeline, send, kim |
|
| crandell-s | message, day, original, sent, time, enron, power, energy, know, sean, new, deal, product, pmto, real, ahead, call, october, wednesday, price, like, news, amto, meeting, thursday, friday, need, west, information, market, rto, monday, tuesday, questions, mw, change, california, said, deals, commission, week, mail, november, center, today, delivery, business, fran, see, parking, financial, group, portland, could, contract, ferc, bpa, steve, month, scheduling |
|
| cuilla-m | class, align, game, allowed, right, size, day, yards, face, last, points, helvetica, fantasy, height, src, week, new, year, miles, nbsp, rates, rank, passing, weeks, november, target, bgcolor, continental, sunday, vs, color, self, border, houston, specials, message, enron, hilton, gas, free, left, city, cera, martin, time, information, offers, available, use, book, table, middle, offer, car, updated, hotels, listed, energy, rushing, airport |
|
| dasovich-j | enron, said, company, power, energy, new, market, gas, state, business, year, size, mail, message, million, billion, jones, nbsp, table, face, corp, california, time, border, dow, sent, information, financial, jeff, last, stock, trading, october, original, could, verdana, service, helvetica, week, companies, news, cellpadding, credit, commission, electricity, call, mailto, houston, align, price, right, know, cellspacing, subject, use, september, years, center, shares, like |
|
| davis-d | enron, amp, new, mail, market, mitigation, dynegy, november, message, sent, information, company, power, day, mailto, original, fw, october, god, subject, commission, know, businesses, york, continue, make, time, see, work, size, amto, face, home, need, free, pray, employees, review, people, believe, financial, like, call, sec, year, every, including, proposed, today, measures, available, ferc, million, chocolate, bids, houston, help, questions, color, without |
|
| dean-c | type, database, final, trans, unknown, date, schedule, epmi, sc, hour, schedules, mkt, details, preferred, found, california, point, data, iso, tie, portland, variances, detected, price, scheduling, file, log, messages, table, term, process, ancillary, continuing, awarded, cannot, enron, perform, closed, operation, wheel, start, variance, energy, short, occurred, attempting, engine, total, user, time, transaction, disk, deal, progress, import, export, sp, long, trading, sale |
|
| delainey-d | contracts, december, message, david, enron, forward, issues, moving, employee, sent, original, call, unavailable, paid, meeting, notice, new, mailbox, brown, delainey, contract, friday, expense, report, time, following, know, bankruptcy, outlook, daniel, regarding, assets, expenses, terminate, pmto, need, retail, goods, contact, household, number, going, payment, think, status, amount, gas, yet, server, november, bill, worthy, agenda, received, luce, alan, scheduled, work, continue, today |
|
| derrick-j | page, enron, mail, message, information, sent, email, know, new, original, jim, state, epa, business, court, meeting, subject, law, june, power, time, corp, group, could, jr, mailto, company, federal, bna, committee, report, legal, review, year, week, board, think, need, gas, pmto, use, number, mark, agreement, intended, attached, work, national, today, contact, derrick, pay, energy, last, like, call, risk, office, management, project |
|
| donoho-l | tw, enron, message, sent, original, gas, capacity, november, report, market, information, october, new, time, know, pipeline, socal, dynegy, pmto, like, contract, attached, company, year, friday, rate, california, business, power, comments, need, use, review, available, tuesday, meeting, amto, questions, file, said, changes, project, transwestern, system, mmbtu, next, email, last, wednesday, week, order, pd, make, energy, service, volumes, watson, core, mail, houston, |
|
| donohoe-t | enron, scheduled, thru, gas, outages, energy, new, information, power, sat, contact, center, call, report, deal, pager, time, october, fri, original, impact, sun, london, ct, market, risk, services, data, natural, pt, available, email, impacted, company, system, help, houston, mail, server, questions, year, week, business, sent, londonoutage, message, november, employees, today, trading, industry, day, see, management, operations, north, free, know, support, cms |
|
| dorland-c | enron, message, energy, information, use, cera, report, mail, new, research, market, online, january, today, february, attachments, distribution, chris, email, contact, sent, associates, prohibited, access, cambridge, original, area, year, questions, password, company, day, intended, pira, strictly, contain, know, free, gas, list, simulation, companies, privileged, power, available, oil, executive, part, make, conference, follow, western, recipient, electronic, disclosure, changes, events, data, attachment, follows |
|
| ermis-f | updated, fantasy, week, free, game, agent, wr, sunday, rb, start, play, season, yards, injury, reports, gas, player, smith, expected, league, practice, day, new, back, starting, time, still, enron, year, te, team, energy, football, good, signed, available, scheduled, reserve, thru, company, weeks, exhibit, martin, last, green, monday, pts, listed, information, ankle, injured, passes, receiver, james, contact, sportsline, numbers, however, nfl, frank |
|
| ENRON | Type of Intellectual Capital | Number of Knowledge Assets Discovered |
|---|---|---|
| Accounting Department (20 valuable assets discovered) | Structural Capital | 16 |
| Human Capital | 4 | |
| Relational Capital | 0 | |
| Investment Relations Department (26 valuable assets discovered) | Structural Capital | 6 |
| Human Capital | 13 | |
| Relational Capital | 7 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sanchez-Segura, M.-I.; González-Cruz, R.; Medina-Dominguez, F.; Dugarte-Peña, G.-L. Valuable Business Knowledge Asset Discovery by Processing Unstructured Data. Sustainability 2022, 14, 12971. https://doi.org/10.3390/su142012971
Sanchez-Segura M-I, González-Cruz R, Medina-Dominguez F, Dugarte-Peña G-L. Valuable Business Knowledge Asset Discovery by Processing Unstructured Data. Sustainability. 2022; 14(20):12971. https://doi.org/10.3390/su142012971
Chicago/Turabian StyleSanchez-Segura, Maria-Isabel, Roxana González-Cruz, Fuensanta Medina-Dominguez, and German-Lenin Dugarte-Peña. 2022. "Valuable Business Knowledge Asset Discovery by Processing Unstructured Data" Sustainability 14, no. 20: 12971. https://doi.org/10.3390/su142012971
APA StyleSanchez-Segura, M.-I., González-Cruz, R., Medina-Dominguez, F., & Dugarte-Peña, G.-L. (2022). Valuable Business Knowledge Asset Discovery by Processing Unstructured Data. Sustainability, 14(20), 12971. https://doi.org/10.3390/su142012971










