An Effective Secured Dynamic Network-Aware Multi-Objective Cuckoo Search Optimization for Live VM Migration in Sustainable Data Centers
Abstract
1. Introduction
- During LVMM, we present a novel dynamic multi-objective Cuckoo Search method to select the optimal secured network path.
- An innovative search strategy based on dynamic cuckoo Levy flights and a Gaussian distribution is proposed.
- To establish the optimal secured path, the combined risk score factor is evaluated.
- The proposed NDCS outperforms the state-of-the-art techniques in terms of performance metrics such as total migration time, makespan time, energy consumption, resource usage, and ensuring risk scores.
2. Related Works
2.1. Path Selection in Cloud Computing
2.2. Usage of Cuckoo Search in the Cloud-Computing Area
3. Classical Cuckoo Search Optimization Algorithm
- A single cuckoo egg is laid at a time and dumped into a randomly selected nest.
- Cuckoos lay their eggs in many nests per generation. The next generation will inherit the best nest with a satisfactory solution.
- Each generation has a constant number of host nests, and alien eggs are discovered according to host bird probability (). The nest owner will either build a new nest or throw the cuckoo egg away once the egg is found.
4. System Model
4.1. Resource Availability
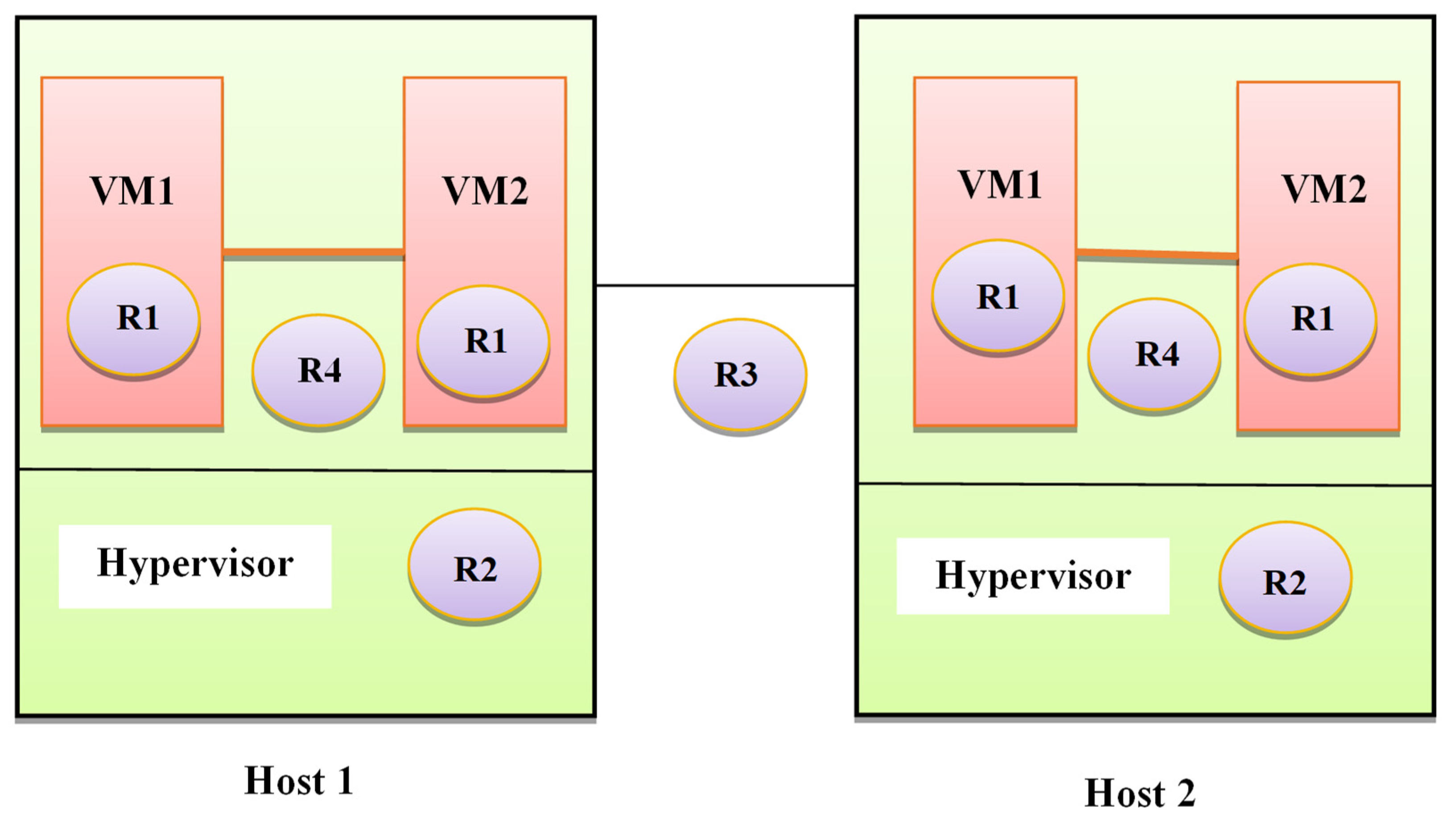
4.2. Communication Topology
4.3. Security
4.3.1. VM Risks (R1)
4.3.2. Hypervisor Risks (R2)
4.3.3. Network Risks (R3)
4.3.4. Co-Residence Risks (R4)
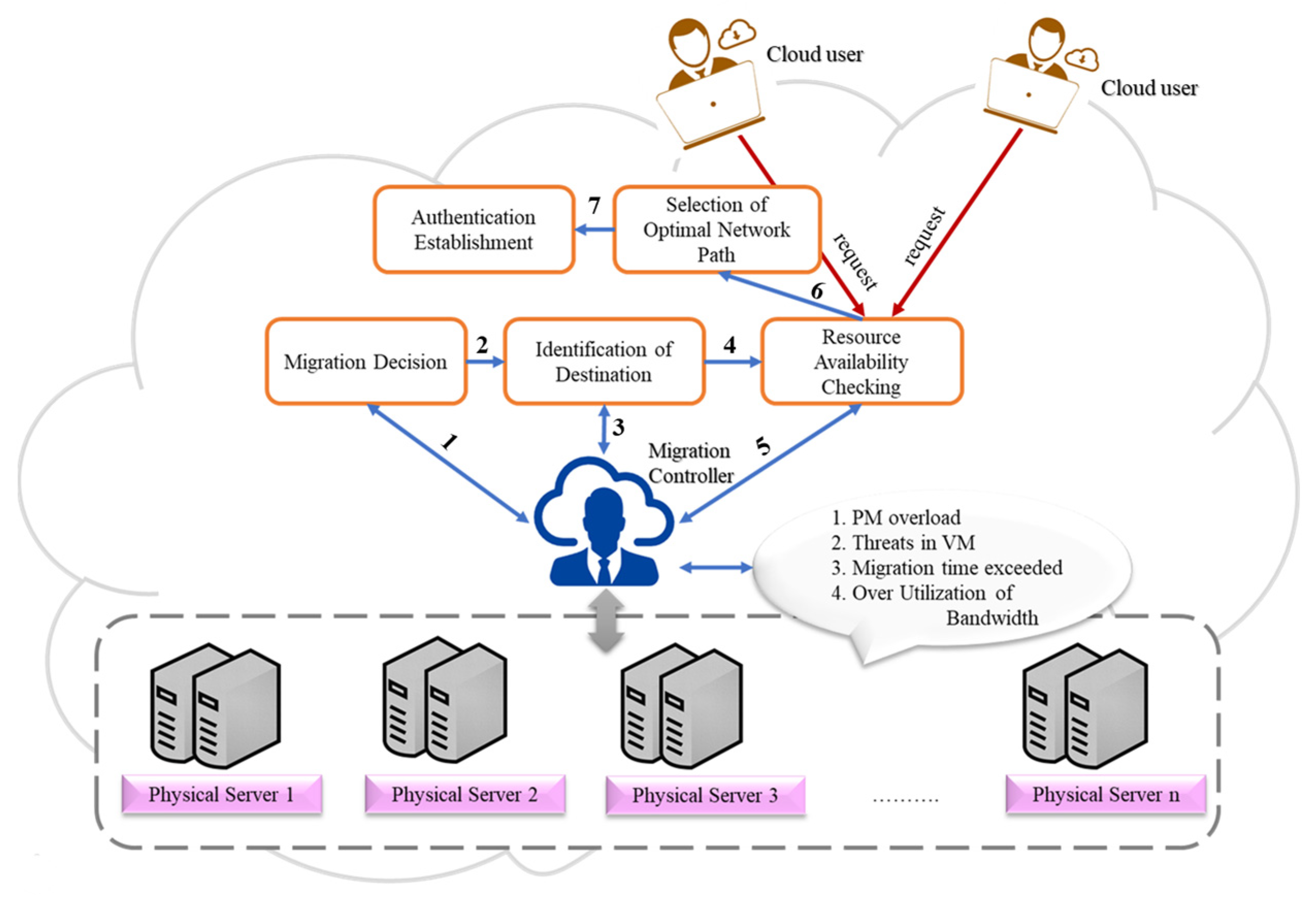
5. Proposed Network-Aware Dynamic Path Selection
5.1. Overview of the Architecture of the Proposed Model
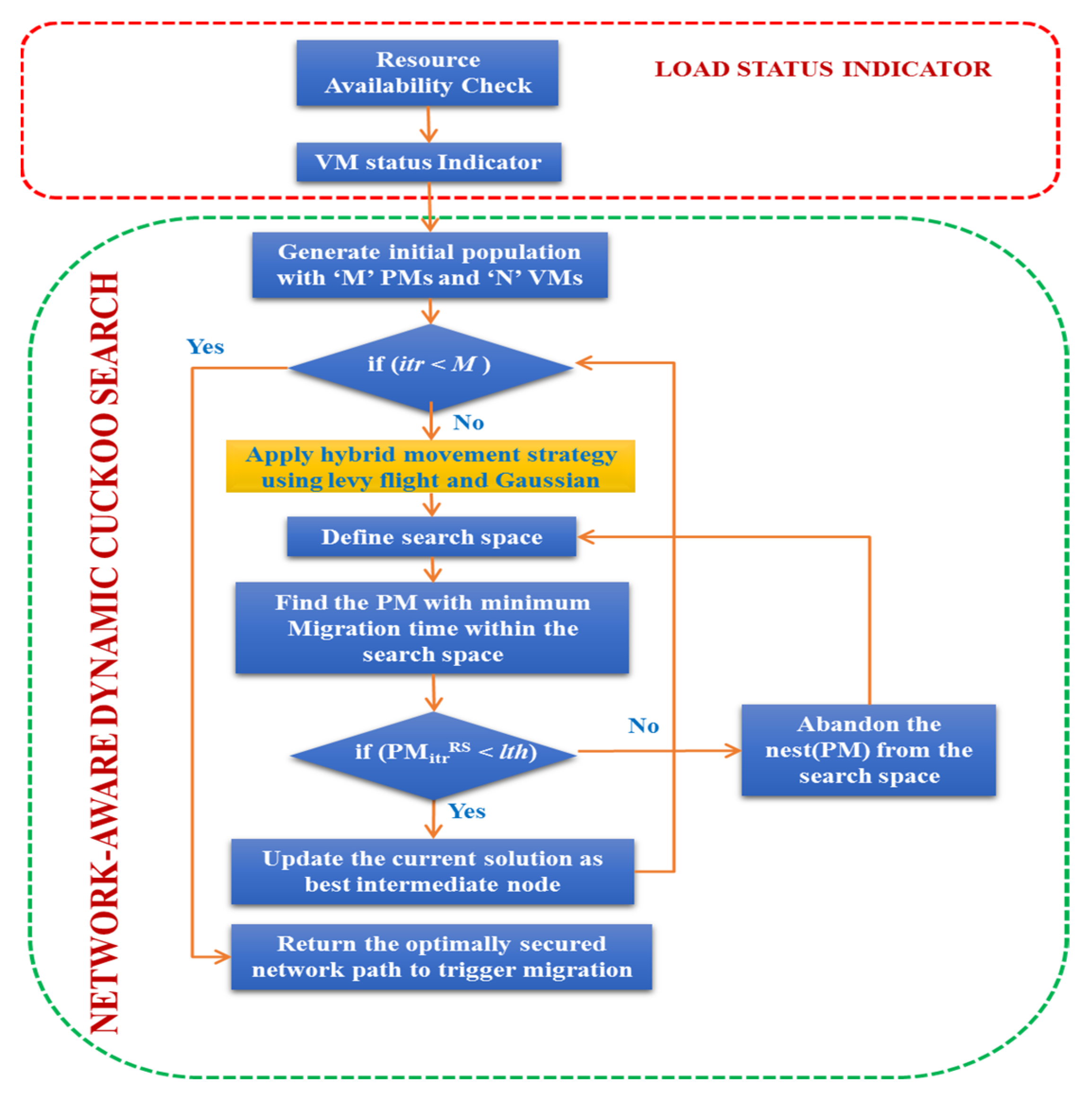
5.2. Network-Aware Dynamic Cuckoo Search Algorithm
| Pseudocode 1: Network-aware Dynamic Cuckoo Search algorithm |
| Input: |
| IntN, DS, LF, GRW, RS, LTH //Intermediate Node, Destination PM, Levy Flights, Gaussian random number generation, Risk Score, Lower Threshold |
| IntN, DS, LF, GRW, RS, LTH //Intermediate Node, Destination PM, Levy Flights, Gaussian random number generation, Risk Score, Lower Threshold |
| Output: |
| Selection of optimally secured network path. |
| 1. Begin: |
| 2. Initializing a population of ‘M’ number of Physical servers, hitr (itr ≤ M); |
| 3. While (itr < M) or (IntN = = DS) |
| 4. Revise cuckoo hitr by LF or GRW via Equation (3); |
| 5. SearchSpace= function Ret_SearchSpace(hitr); |
| 6. MinMT_PM = minMigTimePM(SearchSpace) |
| 7. Evaluate fitness (). |
| 8. if new one is better than old |
| 9. IntN = MinMT_PMitrRS. |
| 10. Add IntN in the network path. |
| 11. else: |
| 12. Abandon the PM from the search space and goto step 5 |
| 13. End while |
| 14. Return the optimally secured Network path. |
| 15. End; |
| fitness (MinMT_PMitrRS) |
| 1. Begin: |
| 2. If MinMT_PMitrRS < LTH: |
| 3. IntN = MinMT_PMitrRS. |
| 4. Return IntN |
| 5. End; |
5.3. Stages of the Network-Aware Dynamic Cuckoo Search Algorithm
5.3.1. Cuckoo Egg Representation
5.3.2. Self-Adaptive Model Parameter
5.4. Hybrid Movement Strategy of Cuckoo
5.5. Fitness Evaluation
5.6. NDCS Termination Criteria and Evaluation Function
6. Experimental Evaluation
6.1. Workload Dataset Description
6.2. Simulation Setup and Experimental Results
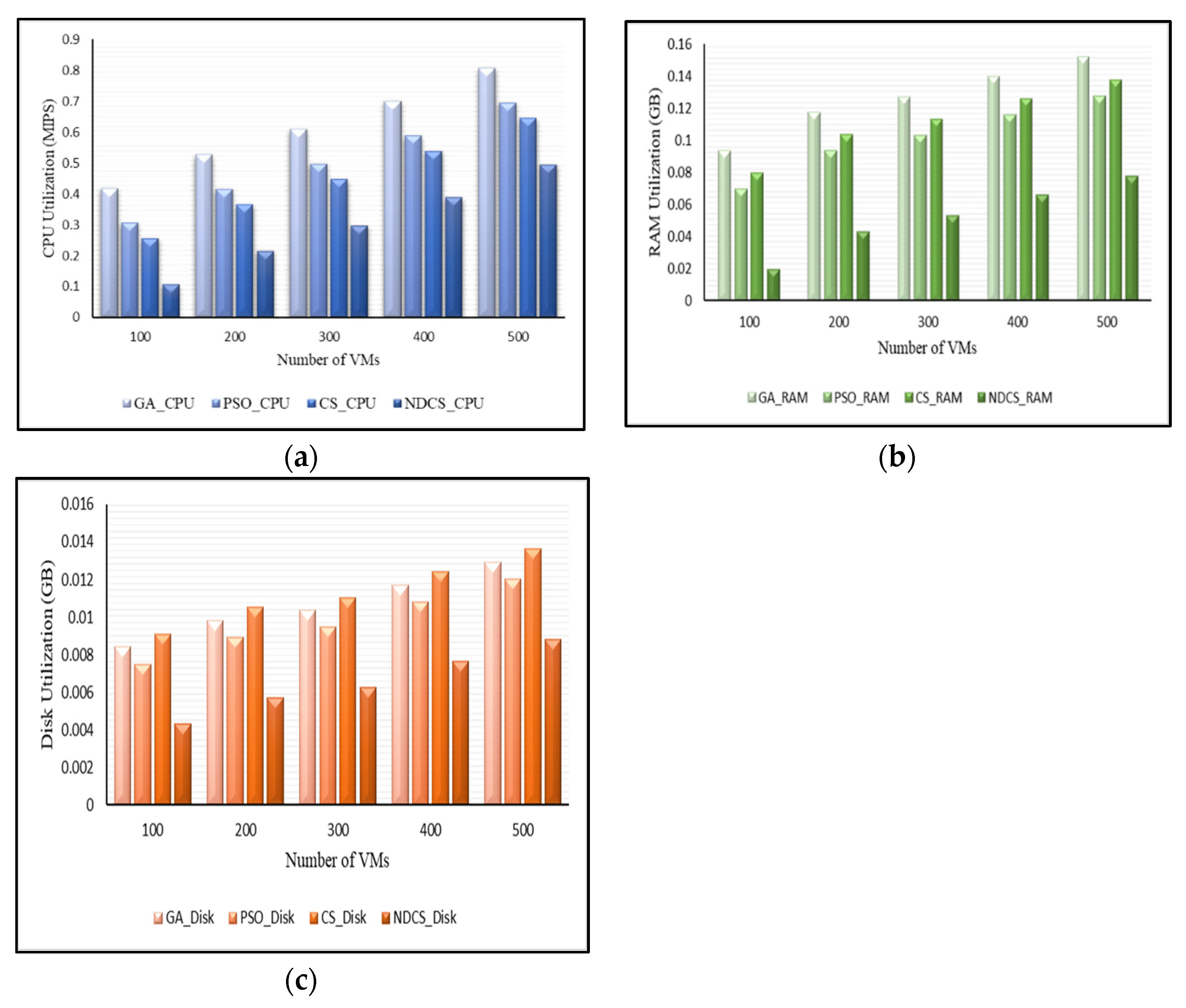
6.2.1. Resource Utilization
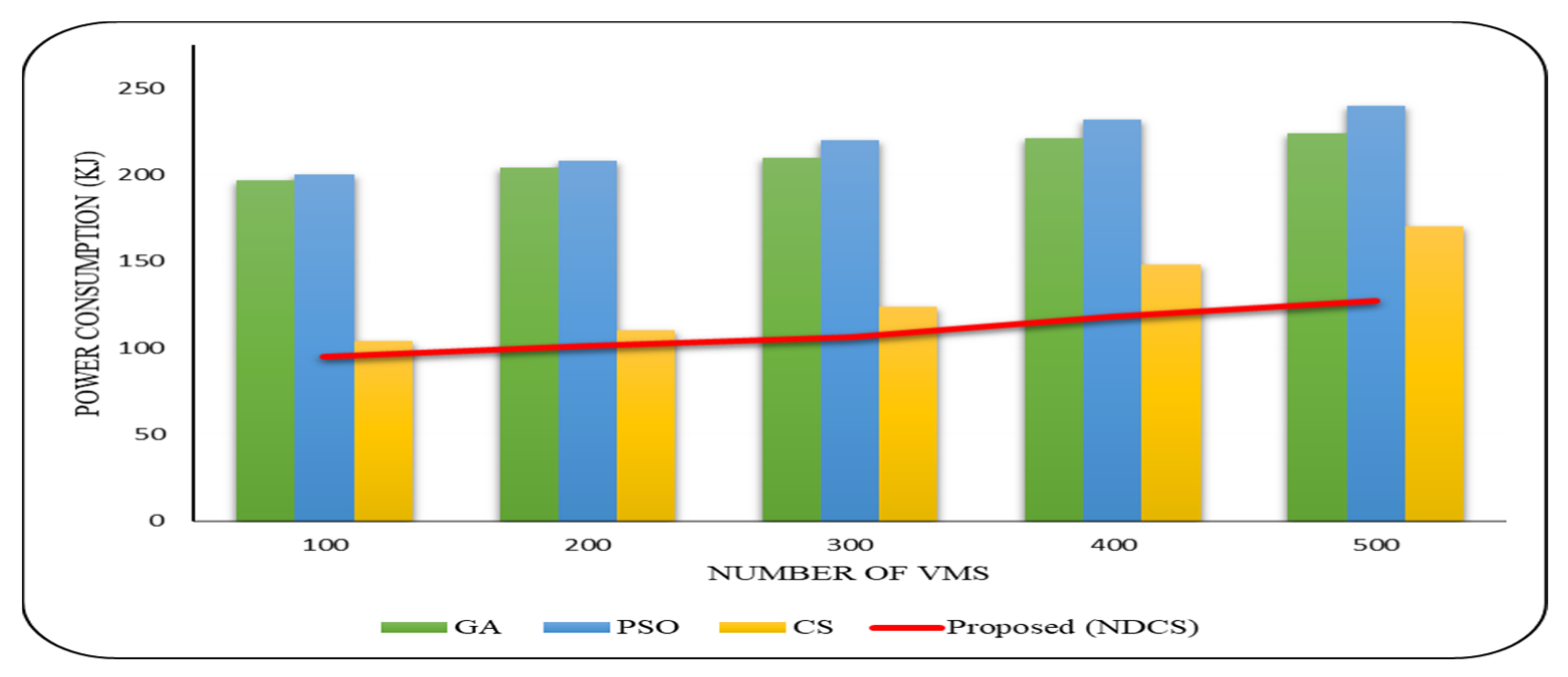
6.2.2. Energy consumption
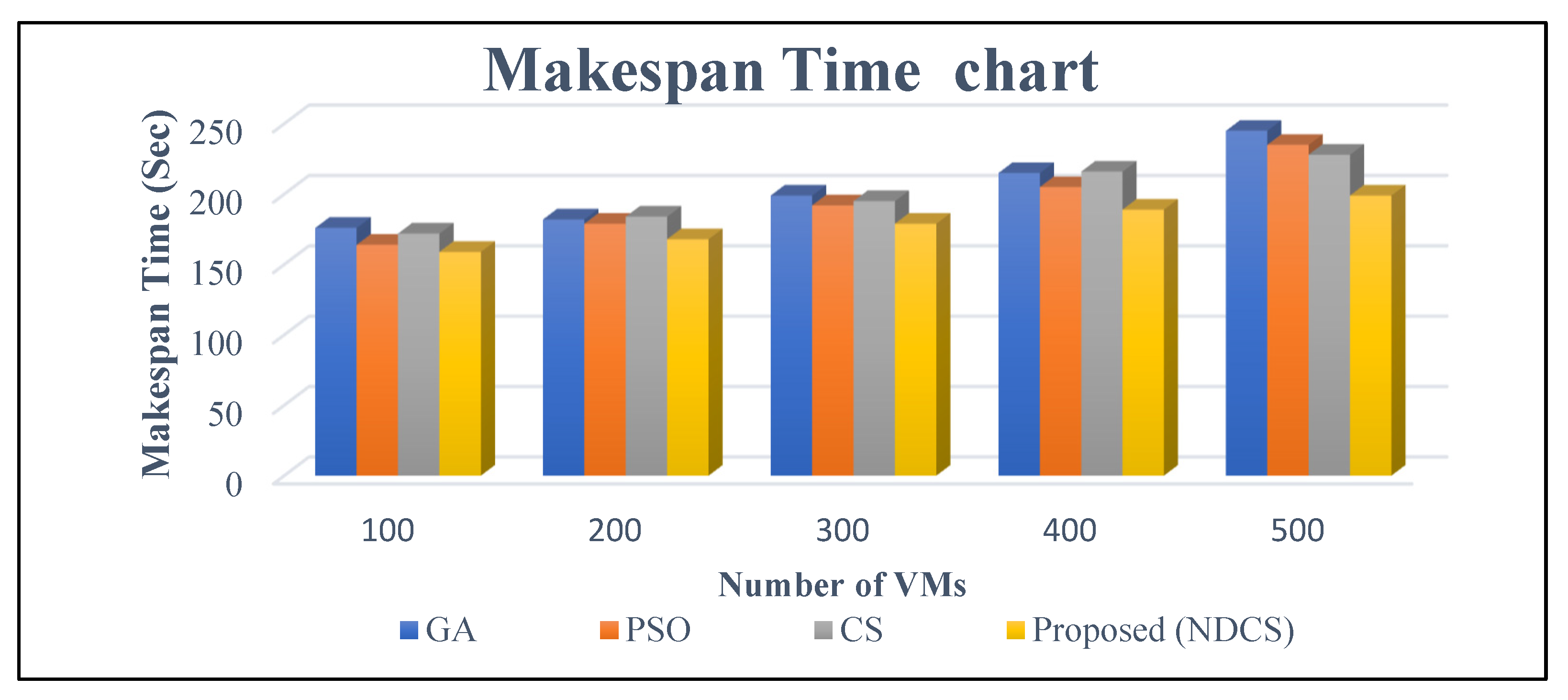
6.2.3. Makespan
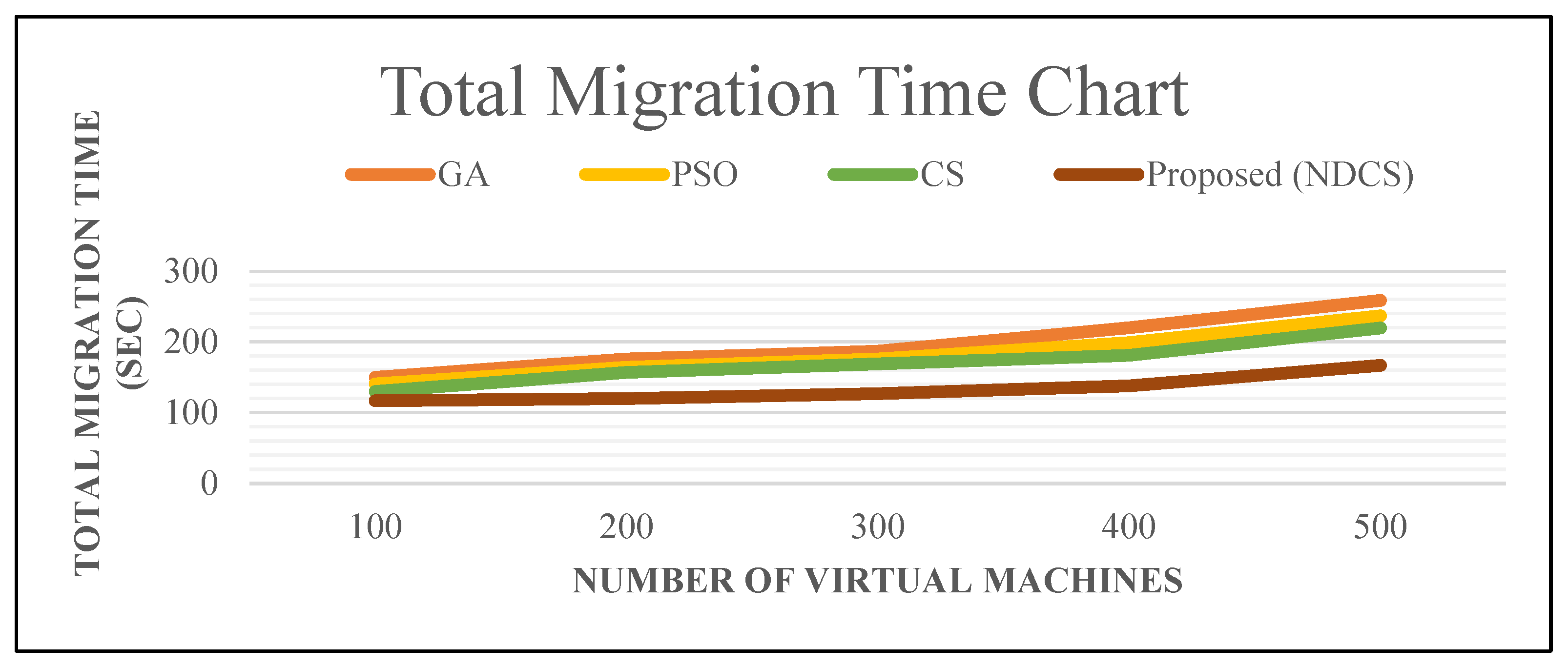
6.2.4. Total Migration Time
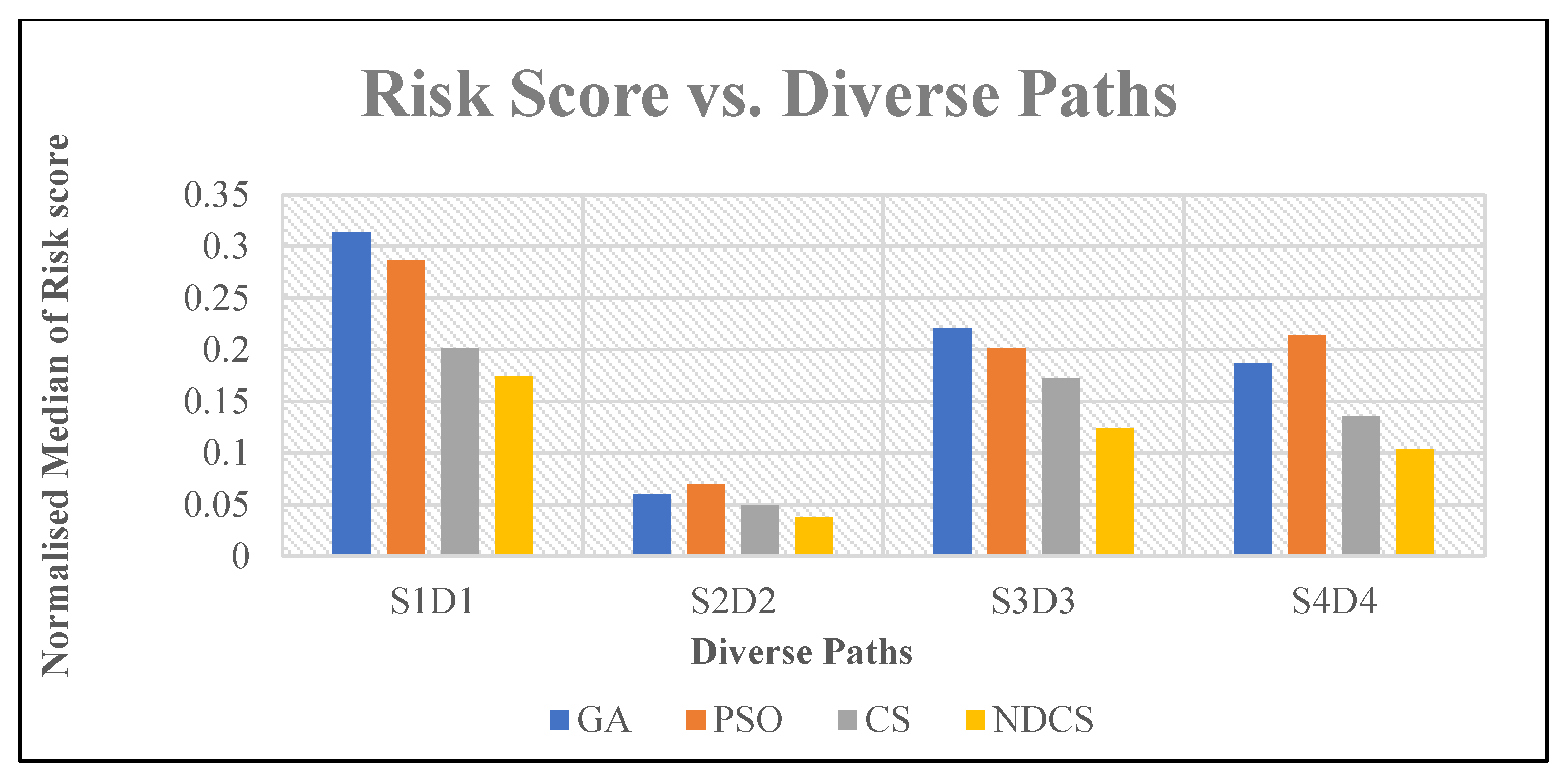
6.2.5. Security
6.3. Performance analysis of CS and Variants
6.4. Performance Analysis of the Migration Metrics
6.4.1. Resource Utilization
6.4.2. Energy Consumption
6.4.3. Makespan
6.4.4. Total Migration Time
6.4.5. Security Analysis
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Al-Wesabi, F.N.; Obayya, M.; Hamza, M.A.; Alzahrani, J.S.; Gupta, D.; Kumar, S. Energy Aware Resource Optimization Using Unified Metaheuristic Optimization Algorithm Allocation for Cloud Computing Environment. Sustain. Comput. Inform. Syst. 2022, 35, 100686. [Google Scholar] [CrossRef]
- Najm, M.; Tamarapalli, V. Towards Cost-Aware VM Migration to Maximize the Profit in Federated Clouds. Futur. Gener. Comput. Syst. 2022, 134, 53–65. [Google Scholar] [CrossRef]
- Elshabka, M.A.; Hassan, H.A.; Sheta, W.M.; Harb, H.M. Security-Aware Dynamic VM Consolidation. Egypt. Inform. J. 2021, 22, 277–284. [Google Scholar] [CrossRef]
- Balamurugan, E.; Mehbodniya, A.; Kariri, E.; Yadav, K.; Kumar, A.; Anul Haq, M. Network Optimization Using Defender System in Cloud Computing Security Based Intrusion Detection System Withgame Theory Deep Neural Network (IDSGT-DNN). Pattern Recognit. Lett. 2022, 156, 142–151. [Google Scholar] [CrossRef]
- Cao, G. Topology-Aware Multi-Objective Virtual Machine Dynamic Consolidation for Cloud Datacenter. Sustain. Comput. Inform. Syst. 2019, 21, 179–188. [Google Scholar] [CrossRef]
- Farzai, S.; Shirvani, M.H.; Rabbani, M. Multi-Objective Communication-Aware Optimization for Virtual Machine Placement in Cloud Datacenters. Sustain. Comput. Inform. Syst. 2020, 28, 100374. [Google Scholar] [CrossRef]
- Ch, S.; Ramesh, T. Energy Efficient VM Scheduling and Routing in Multi-Tenant Cloud Data Center. Sustain. Comput. Inform. Syst. 2019, 22, 139–151. [Google Scholar] [CrossRef]
- Singh, P.; Prakash, V.; Bathla, G.; Singh, R.K. QoS Aware Task Consolidation Approach for Maintaining SLA Violations in Cloud Computing. Comput. Electr. Eng. 2022, 99, 107789. [Google Scholar] [CrossRef]
- Ai, N.; Wu, B.; Li, B.; Zhao, Z. 5G Heterogeneous Network Selection and Resource Allocation Optimization Based on Cuckoo Search Algorithm. Comput. Commun. 2021, 168, 170–177. [Google Scholar] [CrossRef]
- Mareli, M.; Twala, B. An Adaptive Cuckoo Search Algorithm for Optimisation. Appl. Comput. Inform. 2018, 14, 107–115. [Google Scholar] [CrossRef]
- Qin, X.; Xia, B.; Ding, T.; Zhao, L. An Improved Cuckoo Search Localization Algorithm for UWB Sensor Networks. Wirel. Netw. 2021, 27, 527–535. [Google Scholar] [CrossRef]
- Alboaneen, D.; Tianfield, H.; Zhang, Y.; Pranggono, B. A Metaheuristic Method for Joint Task Scheduling and Virtual Machine Placement in Cloud Data Centers. Futur. Gener. Comput. Syst. 2021, 115, 201–212. [Google Scholar] [CrossRef]
- Mohiuddin, I.; Almogren, A. Workload Aware VM Consolidation Method in Edge/Cloud Computing for IoT Applications. J. Parallel Distrib. Comput. 2019, 123, 204–214. [Google Scholar] [CrossRef]
- Pradhan, A.; Bisoy, S.K. A Novel Load Balancing Technique for Cloud Computing Platform Based on PSO. J. King Saud Univ. Comput. Inf. Sci. 2020, 34, 3988–3995. [Google Scholar] [CrossRef]
- Rekha, P.M.; Dakshayini, M. Efficient Task Allocation Approach Using Genetic Algorithm for Cloud Environment. Clust. Comput. 2019, 22, 1241–1251. [Google Scholar] [CrossRef]
- Mamun, S.A.; Ganguly, A.; Markopoulos, P.P.; Kwon, M.; Kwasinski, A. NASCon: Network-Aware Server Consolidation for Server-Centric Wireless Datacenters. Sustain. Comput. Inform. Syst. 2021, 29, 100452. [Google Scholar] [CrossRef]
- Lin, L.; Wei, D.S.L.; Ma, R.; Li, J.; Guan, H. Online Traffic-Aware Linked VM Placement in Cloud Data Centers. Sci. China Inf. Sci. 2020, 63, 172101. [Google Scholar] [CrossRef]
- Kanniga Devi, R.; Murugaboopathi, G.; Muthukannan, M. Load Monitoring and System-Traffic-Aware Live VM Migration-Based Load Balancing in Cloud Data Center Using Graph Theoretic Solutions. Clust. Comput. 2018, 21, 1623–1638. [Google Scholar] [CrossRef]
- Kandoussi, E.M.; El Mir, I.; Hanini, M.; Haqiq, A. Modeling Virtual Machine Migration as a Security Mechanism by Using Continuous-Time Markov Chain Model. In Proceedings of the 2019 4th World Conference on Complex Systems (WCCS), Ouarzazate, Morocco, 22–25 April 2019; pp. 1–6. [Google Scholar]
- Saxena, D.; Gupta, I.; Kumar, J.; Singh, A.K.; Wen, X. A Secure and Multiobjective Virtual Machine Placement Framework for Cloud Data Center. IEEE Syst. J. 2021, 16, 3163–3174. [Google Scholar] [CrossRef]
- Verma, G. Secure VM Migration in Cloud: Multi-Criteria Perspective with Improved Optimization Model. Wirel. Pers. Commun. 2022, 124, 75–102. [Google Scholar] [CrossRef]
- Durgadevi, P.; Srinivasan, S. Resource Allocation in Cloud Computing Using SFLA and Cuckoo Search Hybridization. Int. J. Parallel Program. 2020, 48, 549–565. [Google Scholar] [CrossRef]
- Salami, H.O.; Bala, A.; Sait, S.M.; Ismail, I. An Energy-Efficient Cuckoo Search Algorithm for Virtual Machine Placement in Cloud Computing Data Centers. J. Supercomput. 2021, 77, 13330–13357. [Google Scholar] [CrossRef]
- Madni, S.H.H.; Latiff, M.S.A.; Ali, J.; Abdulhamid, S.M. Multi-Objective-Oriented Cuckoo Search Optimization-Based Resource Scheduling Algorithm for Clouds. Arab. J. Sci. Eng. 2019, 44, 3585–3602. [Google Scholar] [CrossRef]
- Shehab, M.; Khader, A.T.; Al-Betar, M.A. A Survey on Applications and Variants of the Cuckoo Search Algorithm. Appl. Soft Comput. 2017, 61, 1041–1059. [Google Scholar] [CrossRef]
- Mohanty, P.K. An Intelligent Navigational Strategy for Mobile Robots in Uncertain Environments Using Smart Cuckoo Search Algorithm. J. Ambient Intell. Humaniz. Comput. 2020, 11, 6387–6402. [Google Scholar] [CrossRef]
- Pankaj, B.S.; Naidu, M.N.; Vasan, A.; Varma, M.R.R. Self-Adaptive Cuckoo Search Algorithm for Optimal Design of Water Distribution Systems. Water Resour. Manag. 2020, 34, 3129–3146. [Google Scholar] [CrossRef]
- Roeva, O.; Zoteva, D.; Atanassova, V.; Atanassov, K.; Castillo, O. Cuckoo Search and Firefly Algorithms in Terms of Generalized Net Theory. Soft Comput. 2020, 24, 4877–4898. [Google Scholar] [CrossRef]
- SS, V.C.; HS, A. Nature Inspired Meta Heuristic Algorithms for Optimization Problems. Computing 2022, 104, 251–269. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Nguyen, T.T. An Improved Cuckoo Search Algorithm for the Problem of Electric Distribution Network Reconfiguration. Appl. Soft Comput. 2019, 84, 105720. [Google Scholar] [CrossRef]
- Khan, M.S.A.; Santhosh, R. Hybrid Optimization Algorithm for VM Migration in Cloud Computing. Comput. Electr. Eng. 2022, 102, 108152. [Google Scholar] [CrossRef]
- Liu, L.; Liu, X.; Wang, N.; Zou, P. Modified Cuckoo Search Algorithm with Variational Parameters and Logistic Map. Algorithms 2018, 11, 30. [Google Scholar] [CrossRef]
- Liu, C.; Wang, J.; Zhou, L.; Rezaeipanah, A. Solving the Multi-Objective Problem of IoT Service Placement in Fog Computing Using Cuckoo Search Algorithm. Neural Process. Lett. 2022, 54, 1823–1854. [Google Scholar] [CrossRef]
- Venkata Subramanian, N.; Shankar Sriram, V.S. Load-Aware VM Migration Using Hypergraph Based CDB-LSTM. Intell. Autom. Soft Comput. 2023, 35, 3279–3294. [Google Scholar] [CrossRef]
- Yang, X.S.; Deb, S. Multiobjective Cuckoo Search for Design Optimization. Comput. Oper. Res. 2013, 40, 1616–1624. [Google Scholar] [CrossRef]
- Samal, T.K.; Patra, S.C.; Kabat, M.R. An Adaptive Cuckoo Search Based Algorithm for Placement of Relay Nodes in Wireless Body Area Networks. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 1845–1856. [Google Scholar] [CrossRef]
- Reda, M.; Onsy, A.; Elhosseini, M.A.; Haikal, A.Y.; Badawy, M. A Discrete Variant of Cuckoo Search Algorithm to Solve the Travelling Salesman Problem and Path Planning for Autonomous Trolley inside Warehouse. Knowl. Based Syst. 2022, 252, 109290. [Google Scholar] [CrossRef]
- Karuppusamy, L.; Daniya, T.; Kanagarathinam, K. Hybrid Cuckoo Search Algorithm with Iterative Local Search for Optimized Task Scheduling on Cloud Computing Environment. J. Comput. Theor. Nanosci. 2019, 16, 2065–2071. [Google Scholar] [CrossRef]
- Han, J.; Zang, W.; Chen, S.; Yu, M. Reducing Security Risks of Clouds through Virtual Machine Placement. In Proceedings of the IFIP Annual Conference on Data and Applications Security and Privacy, Philadelphia, PA, USA, 19–21 July 2017; pp. 275–292. [Google Scholar]
- Reiss, C.; Wilkes, J.; Hellerstein, J.L. {Google} Cluster-Usage Traces: Format + Schema; Google: Mountain View, CA, USA, 2011. [Google Scholar]
- Barbierato, E.; Gribaudo, M.; Iacono, M.; Jakóbik, A. Exploiting CloudSim in a Multiformalism Modeling Approach for Cloud Based Systems. Simul. Model. Pract. Theory 2019, 93, 133–147. [Google Scholar] [CrossRef]

| Author Name | Technique Used | Data Set Used | Performance Metrics | Disadvantages |
|---|---|---|---|---|
| Alboaneen, D. et al., (2021) [12] | Joint task scheduling and VM placement (JTSVMP) | NASA Ames iPSC/860 | Makespan, degree of imbalance, execution cost, Wilcoxon test | Failed to focus on Security and reliability |
| Mohiuddin, I, et al., (2019) [13] | Workload Aware Virtual Machine Consolidation Method | Random data | Power consumption, Number of active servers, Number of migrations | Test carried out through random data possibility of issues with real dataset |
| Arabinda Pradhan. et al., (2020) [14] | Modified PSO. | Random data | Makespan, resource utilization | Author left out to concentrate on throughput, number of migrations |
| SA Mamun, et al., (2021) [16] | Network-Aware Server Consolidation (NASCon) | Random data | Throughput, power consumption, consolidation cost | Security not focused, tested on random data |
| Lin, L., et al., (2020) [17] | Online traffic aware VM placement | Random data | SlotToPm, saving ratio | Security has not been focused. |
| Saxena, D., et al., (2021) [20] | WOGA | Amazon EC2 | Security threats, inter-communication cost, power consumption, and execution time | Virtual machines are not mapped to different server clusters. |
| Garima Verma (2022) [21] | Dual Conditional Moth Flame Algorithm (DC-MFA) | Synthetic Data | Migration cost, total cost, energy consumption, response time, and security analysis | Tested on synthetic data. |
| Madni, S.H.H., et al., (2021) [24] | Multi-objective Cuckoo Search Optimization (MOCSO) algorithm | HPC2N, NASA Ames iPCS/860, SDSC | Makespan, utilization rate, resource scheduling cost. | Failed to focus on security and reliability |
| Durgadevi, P., et al., (2020) [22] | Shuffled Frog Leaping Algorithm (SFLA) and Cuckoo Search (CS) | Yardstick | Execution time, throughput, turnaround time, waiting time | Tested with limited dataset and not focused on security. |
| Salami, H.O., et al., (2021) [23] | Cuckoo Search (CS) | A. Scholl and R. Klein, Synthetic Data | Execution time, power consumption, fitness cost | Test with random dataset, failed to focus on security |
| Parameter | Cuckoo Search | Binary Cuckoo Search | Dynamic Cuckoo Search |
|---|---|---|---|
| Input params | = probability of discovery n = size of population | = probability of discovery n = population sigmoid function | = probability of discovery as dynamic α = step size determined dynamically. |
| Output | Improved population | Improved population | Dynamically improved population |
| Step size | Commonly used step size = 0.01 | Commonly used step size = 0.01 | Dynamically determined step size and it will be greater than 0 |
| Range | , commonly , commonly n = 10 | , commonly , commonly n = 10 | Range will vary based on the number of generations. |
| Step length | In terms of step lengths, this process is governed by a power law distribution with a heavy tail. | There is a heavy tail power law distribution for the step length in this process. | As a function of the combination of the Levy and Gaussian distributions, the step length is calculated |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Venkata Subramanian, N.; Shankar Sriram, V.S. An Effective Secured Dynamic Network-Aware Multi-Objective Cuckoo Search Optimization for Live VM Migration in Sustainable Data Centers. Sustainability 2022, 14, 13670. https://doi.org/10.3390/su142013670
Venkata Subramanian N, Shankar Sriram VS. An Effective Secured Dynamic Network-Aware Multi-Objective Cuckoo Search Optimization for Live VM Migration in Sustainable Data Centers. Sustainability. 2022; 14(20):13670. https://doi.org/10.3390/su142013670
Chicago/Turabian StyleVenkata Subramanian, N., and V. S. Shankar Sriram. 2022. "An Effective Secured Dynamic Network-Aware Multi-Objective Cuckoo Search Optimization for Live VM Migration in Sustainable Data Centers" Sustainability 14, no. 20: 13670. https://doi.org/10.3390/su142013670
APA StyleVenkata Subramanian, N., & Shankar Sriram, V. S. (2022). An Effective Secured Dynamic Network-Aware Multi-Objective Cuckoo Search Optimization for Live VM Migration in Sustainable Data Centers. Sustainability, 14(20), 13670. https://doi.org/10.3390/su142013670






