A Systematic Review of Traffic Incident Detection Algorithms
Abstract
1. Introduction
1.1. Research Background
1.2. Objectives
- Understand the application of AID systems to curb the negative impacts of incidents and increase safety on the roads;
- Investigate the advantages, challenges and concerns of the existing AID systems and identify solutions to improve them;
- Investigate the feasibility of applying new emerging technologies such as connected vehicles, Artificial Intelligence (AI) and Machine Learning (ML) in developing AID systems.
1.3. Organization of the Paper
- The first section provides the background and the objectives of the study;
- The second section discusses the methodology adopted in this study to evaluate existing AID systems;
- The third section summarizes the previous studies related to incident detection systems and evaluates their strengths and drawbacks;
- The fourth section provides the conclusions and the critical findings of the paper;
- The fifth section presents the recommendations of the paper and proposes some directions for future research.
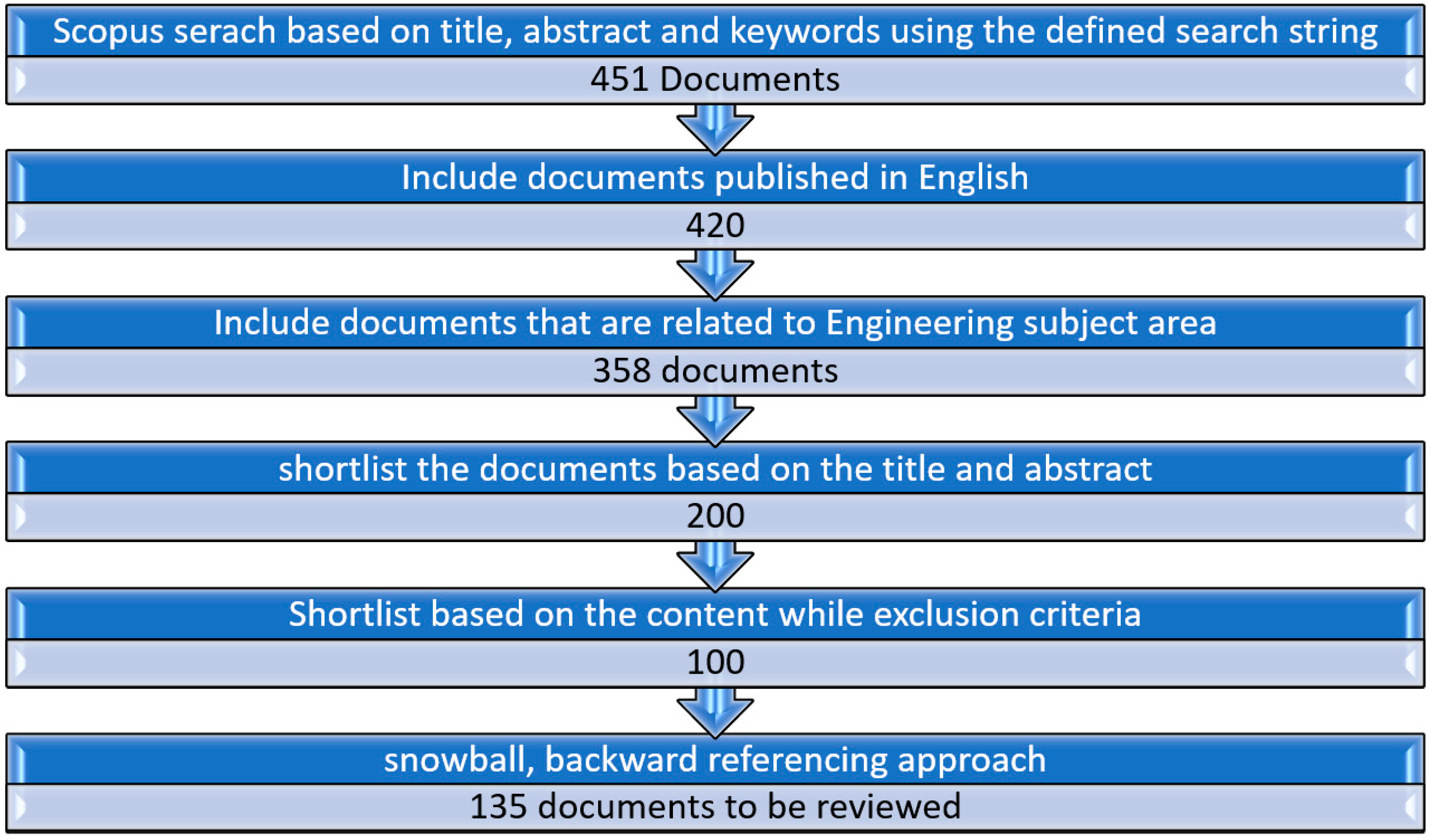
2. Research Methodology
“automatic” AND “traffic” AND “incident” AND “detection”.
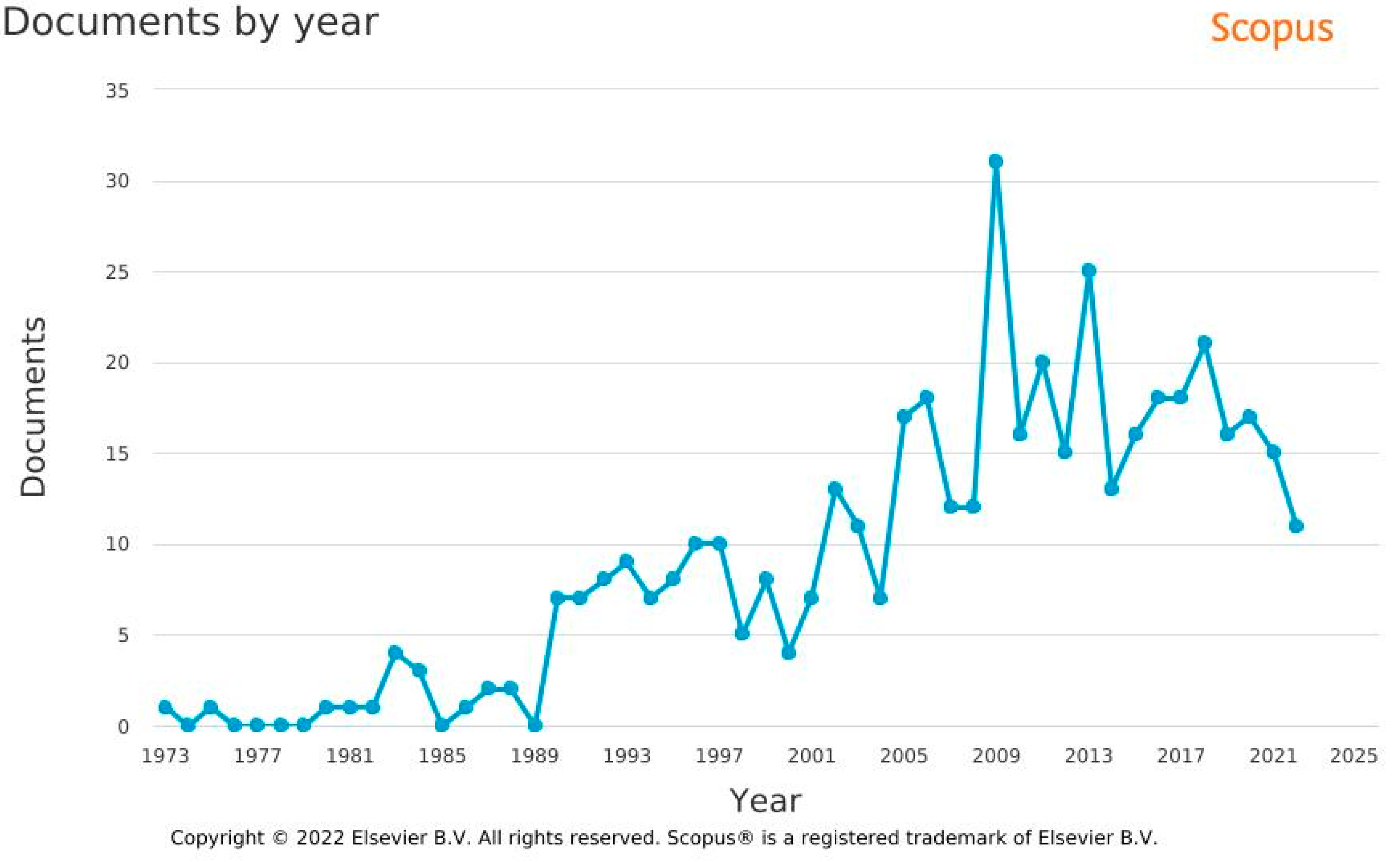
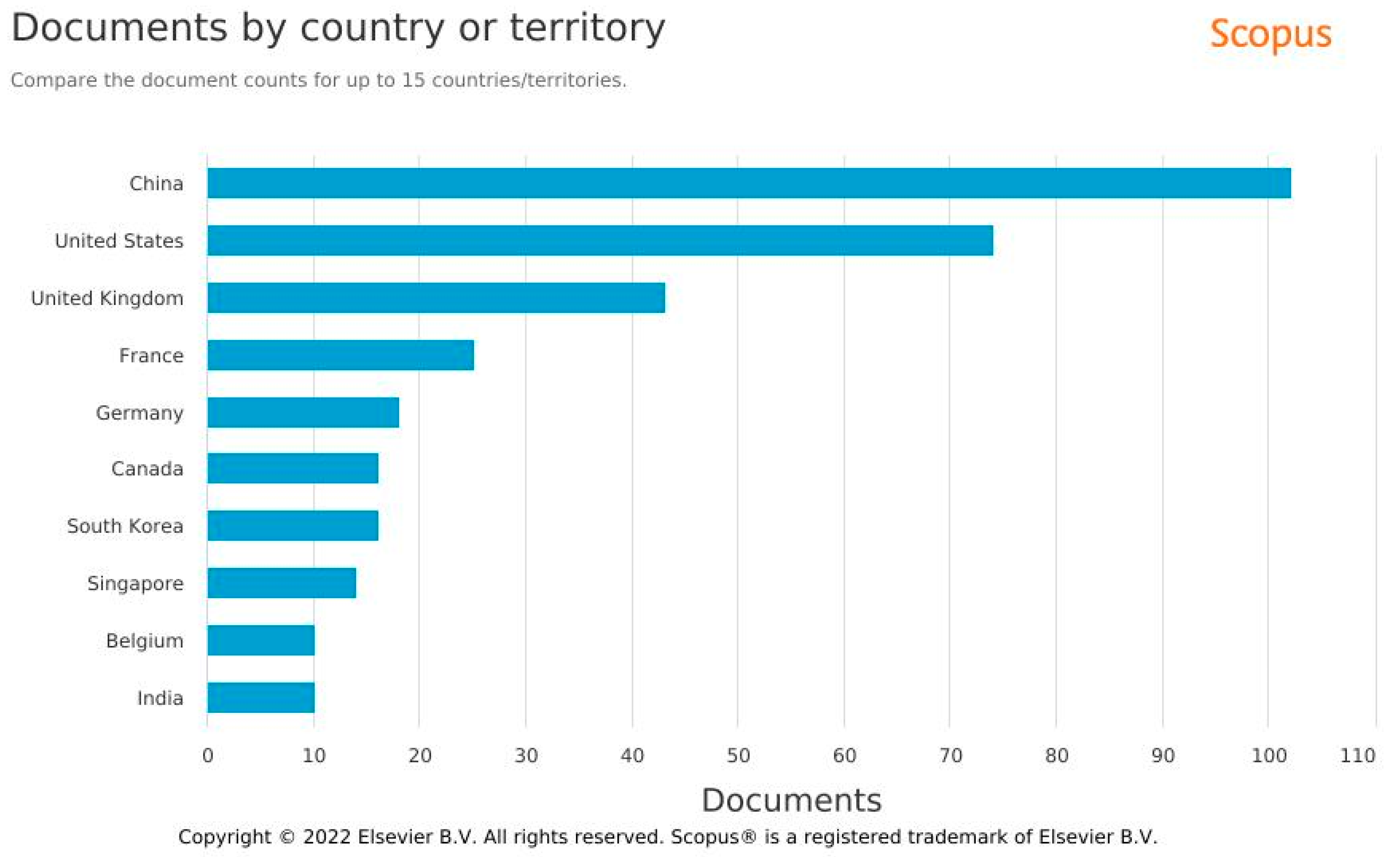
2.1. Descriptive Analysis and Initial Data Statistics
3. Literature Review
3.1. Comparative (Pattern Recognition) Algorithms
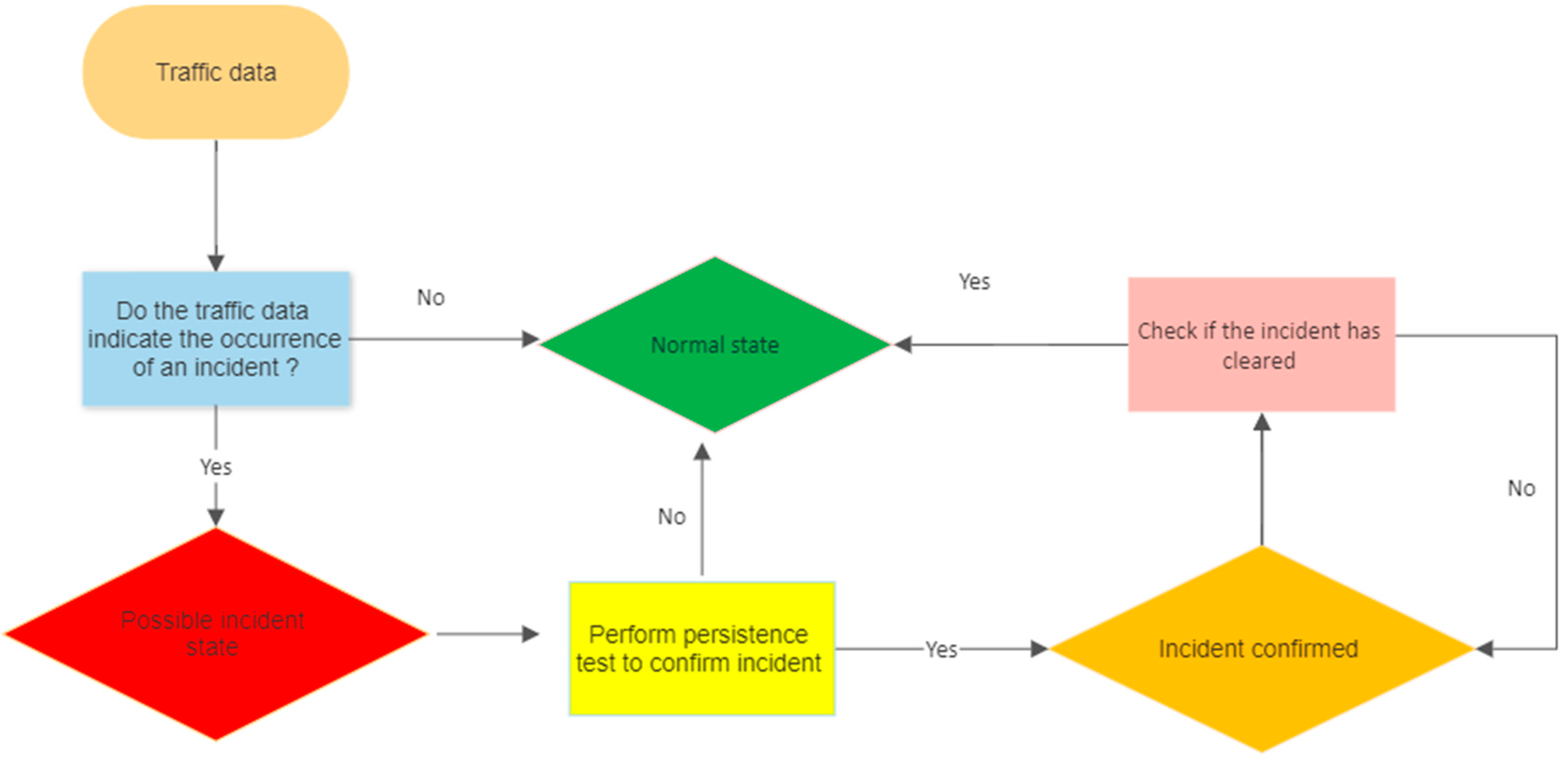
3.2. Statistical Algorithms
3.3. Artificial Intelligence Algorithms
3.3.1. Artificial Neural Network Algorithms
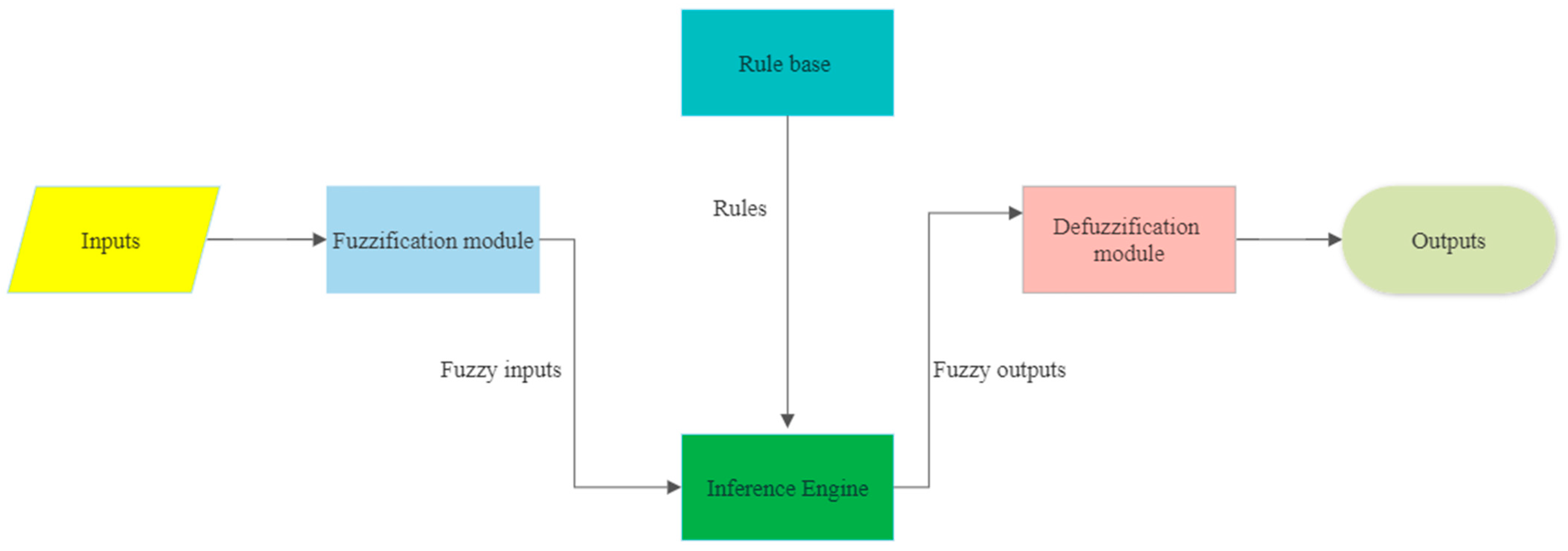
3.3.2. Fuzzy Logic Algorithms
3.3.3. Support Vector Machine Algorithms
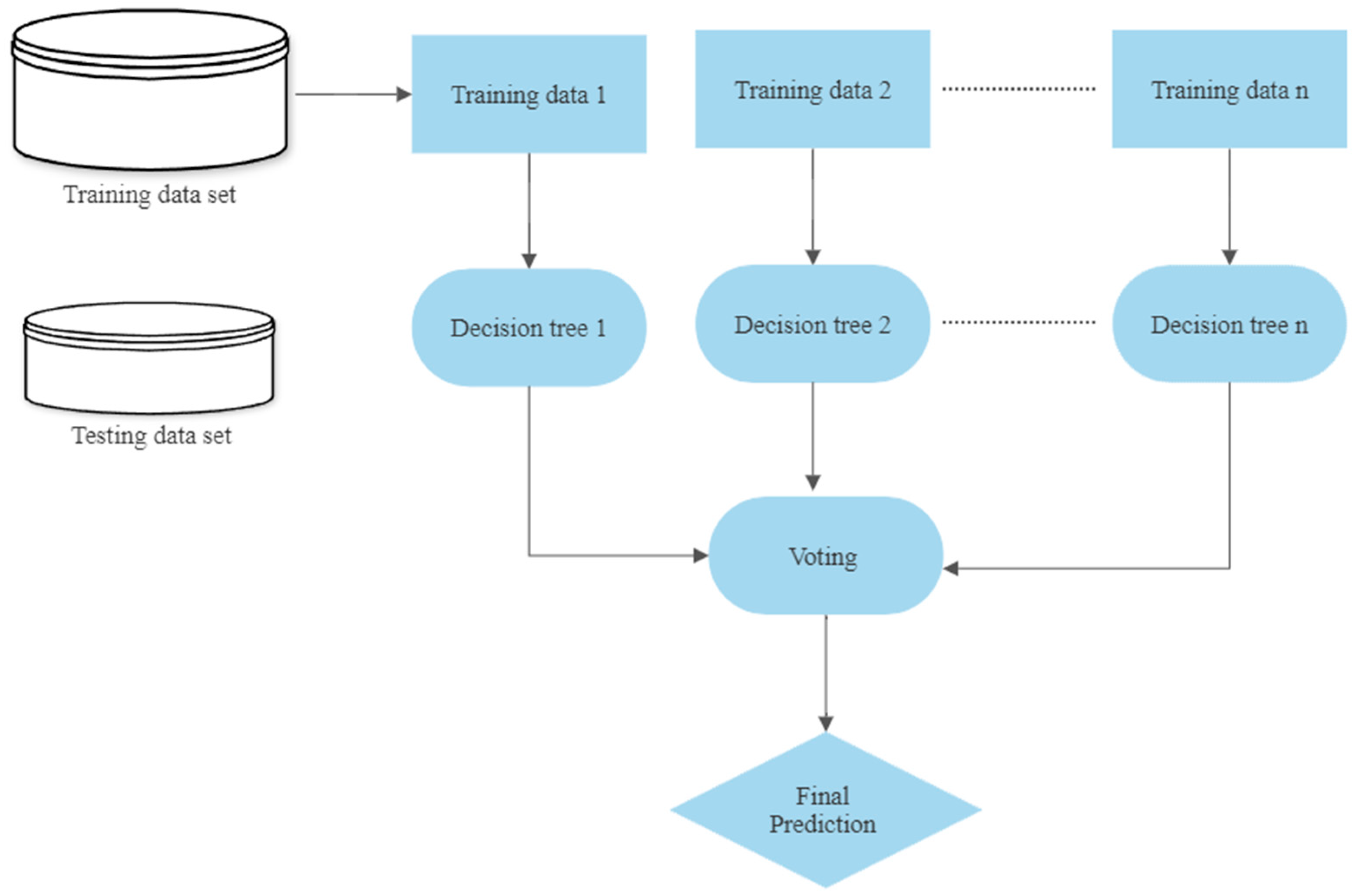
3.3.4. Ensemble Learning Algorithms
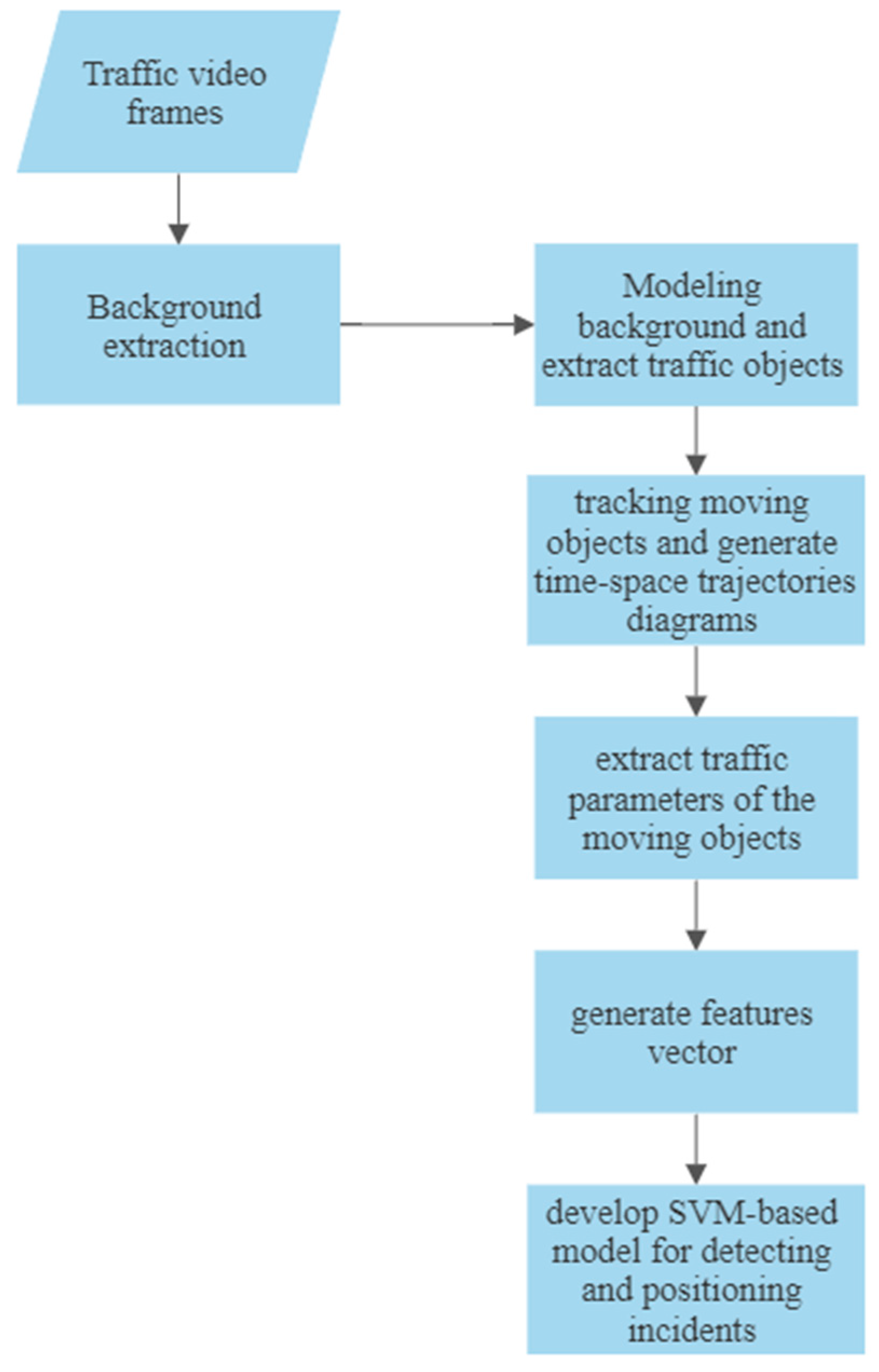
3.4. Video–Image Processing Algorithms
4. Conclusions
- It illustrates the importance of an incident detection system’s role in traffic management and in increasing safety on the roadways;
- It presents an extensive review of the development of incident detection systems from the beginning of the 1970s until now;
- It investigates the advantages of the existing AID systems and highlights their drawbacks and limitations and the gaps that exist in the literature, which are useful for future development.
5. Recommendations and Research Direction
5.1. Recommendations
- Some of the AID systems depend on one traffic variable (such as the California algorithm) to detect the occurrence of the incidents. This might result in a high FAR and a low DR. Hence, AID systems should consider multiple traffic variables such as occupancy, flow and speed simultaneously to enhance the detection performance of the model;
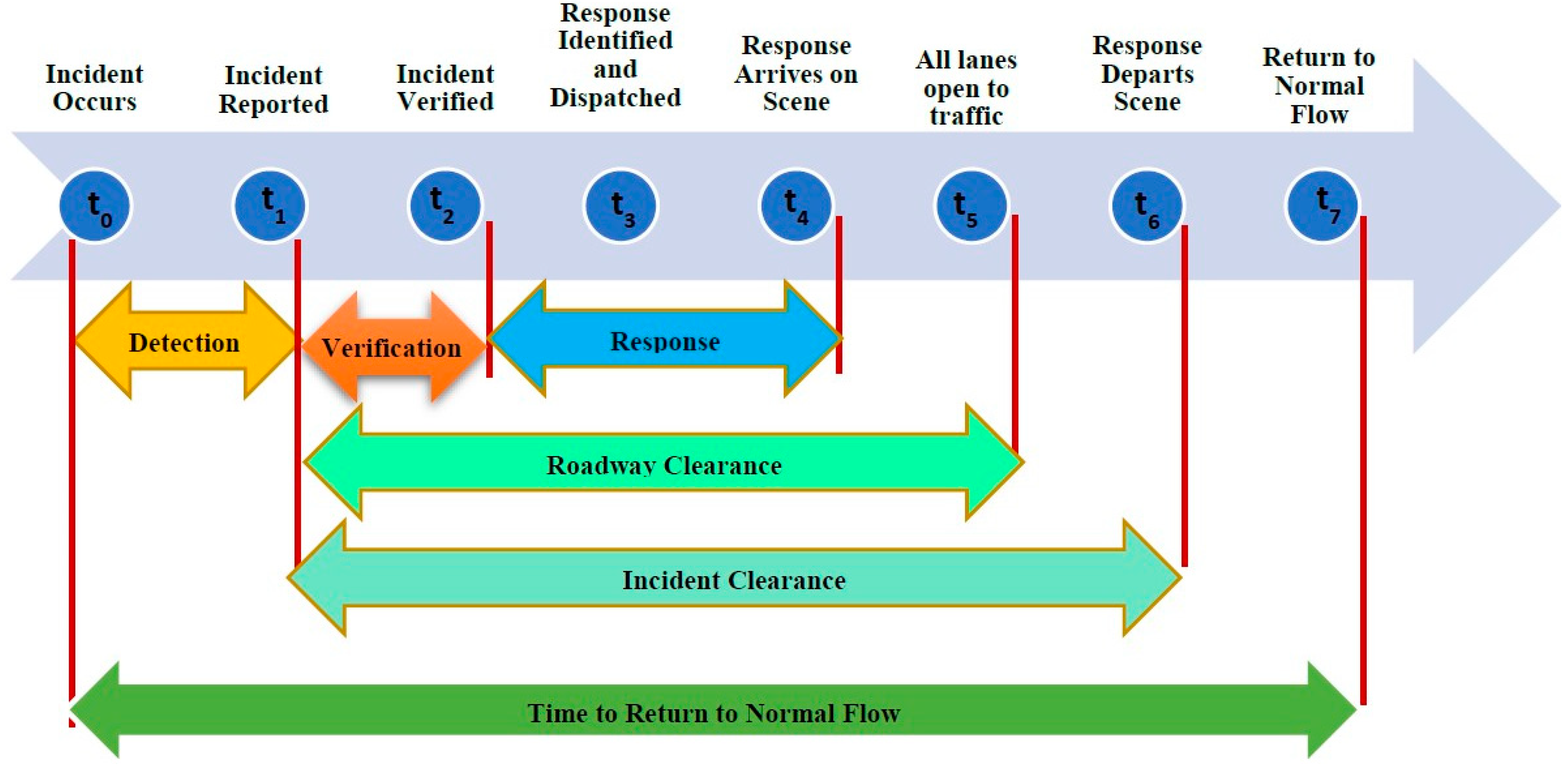
- The literature review identified some factors that can have a substantial impact on the performance of the model. An example of these factors is the spacing between the detectors, as mentioned before in Section 2.1, which has a major impact on the detection ability of the system. Alternatively, the coverage range of CCTV or other sensors can also impact the detection ability of the system. In addition, the traffic conditions are a key factor. During high traffic flow periods, any incident, even a minor incident, can be detected because its impact will intensify and will be easily detected. However, at low traffic volumes, the detection of the incidents is difficult because their impacts may not be significant. Another crucial factor is the severity of the incident. The severity of the incident affects its detectability. Moreover, weather conditions are a crucial factor that not only affects the performance of AID algorithms but can also be a major cause of incidents and traffic disruption [136,137]. Further, the road conditions and the geometry of the road can cause false alarms and undermine the performance of the AID system, as mentioned in Section 3.1.
- (1)
- Based on the gaps that are identified from the literature review, there is a need for a comprehensive and generic AID system that considers all possible factors that can impact the detection of incidents;
- (2)
- According to the National Highway Transportation Safety Administration (NHTSA), more than 90% of traffic incidents are due to human error such as speeding, texting, drunk drivers and distracted drivers [138,139,140]. Thus, implementing AID systems is not enough to reduce the number of incidents. There is a need for strict driving and traffic laws that suppress violators and careless drivers and hence enhance road safety. In addition, utilizing new emerging technologies such as connected and autonomous vehicles can reduce these errors and the number of traffic incidents [141].
- (3)
- The study focused on the role of AID systems in mitigating the problem of traffic incidents. Yet there are some other factors that have a vital role in roadway safety such as road conditions and vehicle maintenance [142]. Thus, proper maintenance of the road infrastructure and vehicles is essential. Moreover, intelligent transportation systems (ITS) are a crucial component that can improve safety and improve traffic performance on roadway networks [77].
- (4)
- The study illustrates the importance of utilizing AI and ML models in incident detection based on their superior performance in terms of DR, FAR and MTTD. Additionally, these are used in almost every aspect of the transportation sector due to their promising future of providing safer, more efficient and sustainable transportation [143]. Thus, the applications of AI and ML in transportation should be the focus of future research to evaluate their benefits and the challenges facing them.
5.2. Research Direction
- All the factors mentioned in Section 5.1 should be considered when developing AID systems;
- Future studies should focus on the usability of some of the emerging technologies in developing AID systems, for instance, utilizing autonomous vehicles in the FCD approach;
- Future studies should conduct a more in-depth analysis of the application of AI and ML models in the transportation sector, the feasibility of using these models in detecting and even predicting the occurrence of traffic incidents and the potential issues and challenges that may arise from using these models.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kamran, S.; Haas, O. A Multilevel Traffic Incidents Detection Approach: Identifying Traffic Patterns and Vehicle Behaviours Using Real-Time GPS Data. In Proceedings of the 2007 IEEE Intelligent Vehicles Symposium, Istanbul, Turkey, 13–15 June 2007; pp. 912–917. [Google Scholar] [CrossRef]
- Srinivasan, D.; Jin, X.; Cheu, R.L. Evaluation of Adaptive Neural Network Models for Freeway Incident Detection. IEEE Trans. Intell. Transp. Syst. 2004, 5, 1–11. [Google Scholar] [CrossRef]
- Srinivasan, D.; Jin, X.; Cheu, R.L. Adaptive Neural Network Models for Automatic Incident Detection on Freeways. Neurocomputing 2005, 64, 473–496. [Google Scholar] [CrossRef]
- Saini, M. Survey On Vision Based On-Road Vehicle Detection. Int. J. u- e-Serv. Sci. Technol. 2014, 7, 139–146. [Google Scholar] [CrossRef][Green Version]
- Farradyne, P.B. Traffic Incident Management. In Encyclopedia of Transportation: Social Science and Policy; SAGE Publications, Inc.: Thousand Oaks, CA, USA, 2014. [Google Scholar] [CrossRef]
- Knoop, V.L.; Hoogendoorn, S.P.; van Zuylen, H.J. Capacity Reduction at Incidents: Empirical Data Collected from a Helicopter. Transp. Res. Rec. 2008, 2071, 19–25. [Google Scholar] [CrossRef]
- Yang, H.; Wang, Z.; Xie, K. Impact of Connected Vehicles on Mitigating Secondary Crash Risk. Int. J. Transp. Sci. Technol. 2017, 6, 196–207. [Google Scholar] [CrossRef]
- Khattak, A.J.; Fan, Y.; Teague, C. Economie Impact of Traffic Incidents on Businesses. Transp. Res. Rec. 2008, 2067, 93–100. [Google Scholar] [CrossRef]
- Jan, K.A. Economic Impact of Traffic Incidents on North Carolina’s Interstate Facilities. Transp. Res. Rec. 2008, 92, 99. [Google Scholar]
- World Health Organization. Road Traffic Injuries. Available online: https://www.who.int/news-room/fact-sheets/detail/road-traffic-injuries (accessed on 21 December 2021).
- Tantillo, M.J.; Roberts, E.; Mangar, U. Roles of Transportation Management Centers in Incident Management on Managed Lanes; FHWA Report no: FHWA-HOP-14-022; Vanasse Hangen Brustlin, Inc. (VHB): Tysons, VA, USA, 2014. [Google Scholar]
- Jin, X.; Zhang, Z.; Gan, A. Traffic Management Centers: Challenges, Best Practices, and Future Plans; National Center for Transportation Systems Productivity and Management (US): Atlanta, GA, USA, 2014. [Google Scholar]
- Cook, A.R.; Cleveland, D.E. Detection of Freeway Capacity-Reducing Incidents By Traffic-Stream Measurements. Transp. Res. Rec. 1970, 495, 1–11. [Google Scholar]
- Dudek, C.L.; Messer, C.J.; Nuckles, N.B. Incident Detection on Urban Freeways. Transp. Res. Rec. 1974, 495, 12–24. [Google Scholar]
- Payne, H. Freeway Incident Detection Based upon Pattern Classification. In Proceedings of the 1975 IEEE Conference on Decision and Control Including the 14th Symposium on Adaptive Processes, Houston, TX, USA, 10–12 December 1975; pp. 688–692. [Google Scholar] [CrossRef]
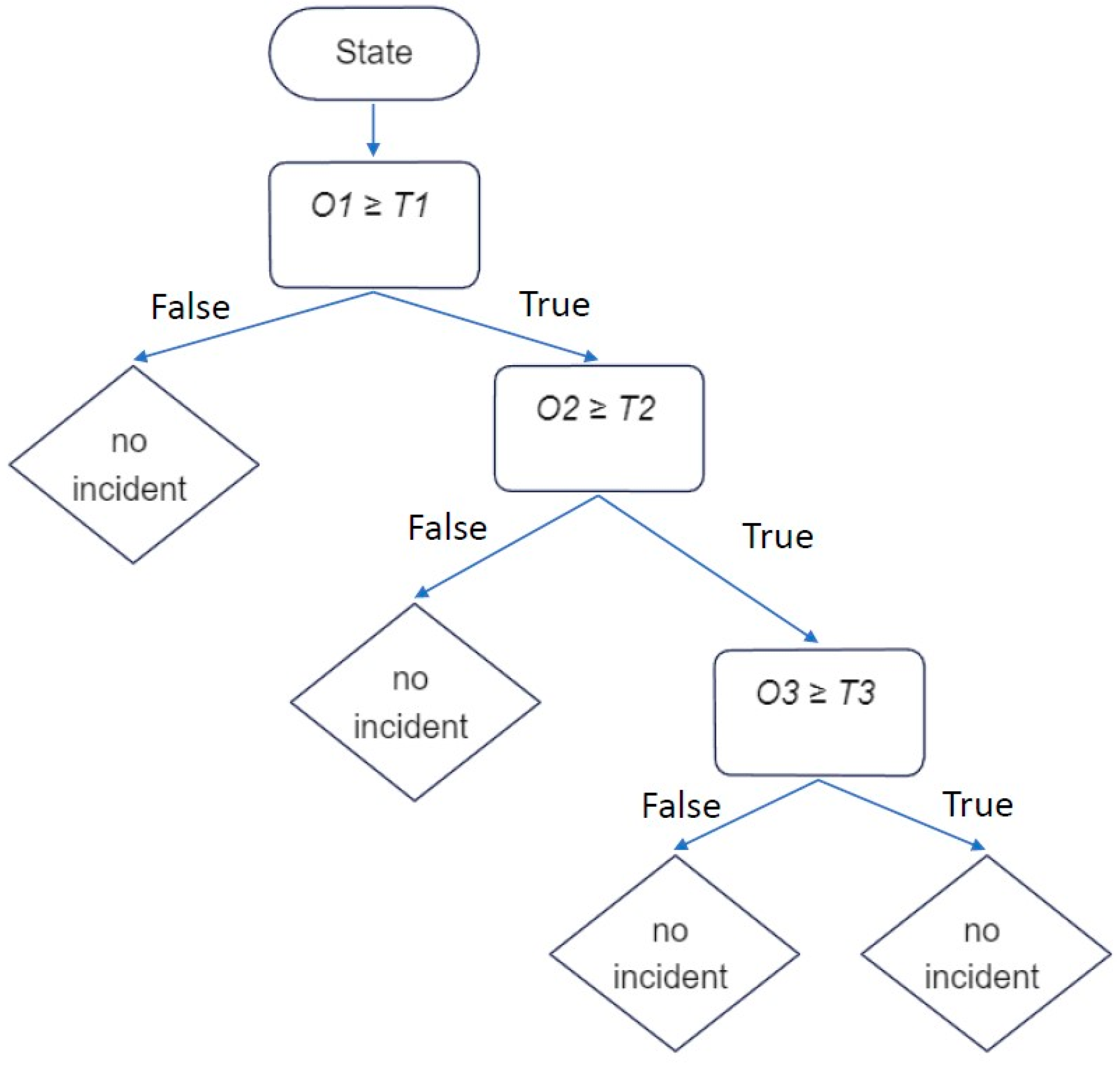
- Payne, H.J.; Tignor, S. Freeway Incident-Detection Algorithms Based on Decision Trees With States. In Proceedings of the 57th Annual Meeting of the Transportation Research Board, Washington, DC, USA, 16–20 January 1978. [Google Scholar]
- Dudek, C.L.; Weaver, G.D.; Ritch, G.P.; Messer, C.J. Detecting Freeway Incidents under Low-Volume Conditions; Texas A&M University: College Station, TX, USA, 1975. [Google Scholar]
- Levin, M.; Krause, G.M. Incident Detection: A Bayesian Approach. Transp. Res. Rec. 1978, 682, 52–58. [Google Scholar]
- Ki, Y.-K.; Kim, J.-H.; Kim, T.-K.; Heo, N.-W.; Choi, J.-W.; Jeong, J.-H. Method for Automatic Detection of Traffic Incidents Using Neural Networks and Traffic Data. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 184–188. [Google Scholar] [CrossRef]
- Elefteriadou, L. An Introduction to Traffic Flow Theory, 17th ed.; Springer optimization and its applications; Springer: New York, NY, USA, 2014; Volume 84, Available online: https://aus.on.worldcat.org/oclc/863640178 (accessed on 15 December 2021). [CrossRef]
- Motamed, M. Developing a Real-Time Freeway Incident Detection Model Using Machine Learning Techniques. Ph.D. Thesis, University of Texas at Austin, Austin, TX, USA, 2016. [Google Scholar] [CrossRef]
- Motamed, M.; Machemehl, R. Real Time Freeway Incident Detection; Center for Transportation Research University of Texas at Austin: Austin, TX, USA, 2014; Volume 7. [Google Scholar]
- Xie, T.; Shang, Q.; Yu, Y. Automated Traffic Incident Detection: Coping With Imbalanced and Small Datasets. IEEE Access 2022, 10, 35521–35540. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. An Improved Automatic Traffic Incident Detection Technique Using a Vehicle to Infrastructure Communication. J. Adv. Transp. 2020, 2020, 1–14. [Google Scholar] [CrossRef]
- Li, R.; Pereira, F.C.; Ben-Akiva, M.E. Overview of Traffic Incident Duration Analysis and Prediction. Eur. Transp. Res. Rev. 2018, 10, 22. [Google Scholar] [CrossRef]
- Chimba, D.; Kutela, B.; Ogletree, G.; Horne, F.; Tugwell, M. Impact of Abandoned and Disabled Vehicles on Freeway Incident Duration. J. Transp. Eng. 2014, 140, 4013013. [Google Scholar] [CrossRef]
- Valenti, G.; Lelli, M.; Cucina, D. A Comparative Study of Models for the Incident Duration Prediction. Eur. Transp. Res. Rev. 2010, 2, 103–111. [Google Scholar] [CrossRef]
- National Academies of Sciences, Engineering, and Medicine. Highway Capacity Manual 7th Edition: A Guide for Multimodal Mobility Analysis; National Academies Press: Washington, DC, USA, 2022. [Google Scholar] [CrossRef]
- Shah, V.; Hatcher, G.; Greer, E.; Fraser, J.; Franz, M.; Sadabadi, K. Guidelines for Quantifying Benefits of Traffic Incident Management Strategies; National Academies Press: Washington, DC, USA, 2022. [Google Scholar] [CrossRef]
- Haule, H.J.; Sando, T.; Lentz, R.; Chuan, C.H.; Alluri, P. Evaluating the Impact and Clearance Duration of Freeway Incidents. Int. J. Transp. Sci. Technol. 2019, 8, 13–24. [Google Scholar] [CrossRef]
- Parkany, E.; Xie, C. A Complete Review of Incident Detection Algorithms & Their Deployment: What Works and What Doesn’t; Report No: NETCR37; The New England Transportation Consortium: Mansfield Center, CT, USA, 2005. [Google Scholar]
- Calderoni, L.; Maio, D.; Rovis, S. Deploying a Network of Smart Cameras for Traffic Monitoring on a “City Kernel”. Expert Syst. Appl. 2014, 41, 502–507. [Google Scholar] [CrossRef]
- Cheng, H.Y.; Gau, V.; Huang, C.W.; Hwang, J.N. Advanced Formation and Delivery of Traffic Information in Intelligent Transportation Systems. Expert Syst. Appl. 2012, 39, 8356–8368. [Google Scholar] [CrossRef]
- Wen, W. An Intelligent Traffic Management Expert System with RFID Technology. Expert Syst. Appl. 2010, 37, 3024–3035. [Google Scholar] [CrossRef]
- Dogru, N.; Subasi, A. Traffic Accident Detection Using Random Forest Classifier. In Proceedings of the 2018 15th Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 25–26 February 2018; pp. 40–45. [Google Scholar] [CrossRef]
- Chen, S.; Wang, W.; van Zuylen, H. Construct Support Vector Machine Ensemble to Detect Traffic Incident. Expert Syst. Appl. 2009, 36, 10976–10986. [Google Scholar] [CrossRef]
- Cheu, R.L.; Ritchie, S.G. Automated Detection of Lane-Blocking Freeway Incidents Using Artificial Neural Networks. Transp. Res. Part C 1995, 3, 371–388. [Google Scholar] [CrossRef]
- Imani, H.N. The Use of Real-Time Connected Vehicles and HERE Data in Developing an Automated Freeway Incident Detection Algorithm. Master’s Thesis, University of North Florida, Jacksonville, FL, USA, 2019. Available online: https://digitalcommons.unf.edu/etd/929 (accessed on 12 April 2022).
- Collins, J.F.; Hopkins, C.M.; Martin, J.A. Automatic Incident Detection: TRRL Algorithms HIOCC and PATREG; Transport and Road Research Laboratory: Crowthorne, UK, 1979. [Google Scholar]
- Masters, P.H.; Lam, J.K.; Wong, K. Incident Detection Algorithms for COMPASS—An Advanced Traffic Management System. In Proceedings of the Vehicle Navigation and Information Systems Conference, Troy, MI, USA, 20–23 October 1991; Volume 2, pp. 295–310. [Google Scholar] [CrossRef]
- Martin, P.T.; Perrin, J.; Hansen, B.; Kump, R.; Moore, D. Incident Detection Algorithm Evaluation; MPC-01-122; Utah Department of Transportation: Taylorsville, UT, USA, 2001. [Google Scholar]
- Liu, Q.; Chung, E.; Zhai, L. Fusing Moving Average Model and Stationary Wavelet Decomposition for Automatic Incident Detection: Case Study of Tokyo Expressway. J. Traffic Transp. Eng. 2014, 1, 404–414. [Google Scholar] [CrossRef]
- Bakioğlu, G.; Silgu, M.A.; Özcanan, S.; Gökaşar, I.; Büyük, M.; Çelikoğlu, H.B.; Osman, A. Incident Detection Algorithms: A Literature Review. In Proceedings of the 1st IRF Europe & Central Asia Regional Congress & Exhibition, Istanbul, Turkey, 15–18 September 2015. [Google Scholar]
- Lyall, B. Performance Evaluation of the Mc Master Incident Detection Algorithm. Ph.D. Thesis, McMaster University, Hamilton, ON, Canada, 1991. [Google Scholar]
- Cohen, S.; Ketselidou, Z. A Calibration Process for Automatic Incident Detection Algorithms. In Microcomputers in Transportation; ASCE: Reston, VA, USA, 1993; pp. 506–515. [Google Scholar]
- Guo, W.; Wang, Z.; Wang, W.; Bubb, H. Traffic Incident Automatic Detection Algorithms by Using Loop Detector in Urban Roads. Recent Patents Comput. Sci. 2015, 8, 41–48. [Google Scholar] [CrossRef]
- Athol, P. Interdependence of Certain Operational Characteristics within a Moving Traffic Stream. Highw. Res. Rec. 1965, 72, 58–87. [Google Scholar]
- Persaud, B.N.; Hall, F.L. Catastrophe Theory and Patterns in 30-Second Freeway Traffic Data—Implications for Incident Detection. Transp. Res. Part A Gen. 1989, 23, 103–113. [Google Scholar] [CrossRef]
- Stephanedes, Y.J.; Chassiakos, A.P. Application of Filtering Techniques for Incident Detection. J. Transp. Eng. 1993, 119, 13–26. [Google Scholar] [CrossRef]
- Margreiter, M.; Spangler, M.; Zeh, T.; Carstensen, C. Bluetooth-Measured Travel Times for Dynamic Re-Routing. In Proceedings of the Annual International Conference on ACE 2015 Singapore, Singapore, 13–14 April 2015. [Google Scholar] [CrossRef]
- Karatsoli, M.; Margreiter, M.; Spangler, M. Bluetooth-Based Travel Times for Automatic Incident Detection—A Systematic Description of the Characteristics for Traffic Management Purposes. Transp. Res. Procedia 2017, 24, 204–211. [Google Scholar] [CrossRef]
- Nikolaev, A.B.; Sapego, Y.S.; Ivakhnenko, A.M.; Mel’nikova, T.E.; Stroganov, V.Y. Analysis of the Incident Detection Technologies and Algorithms in Intelligent Transport Systems. Int. J. Appl. Eng. Res. 2017, 12, 4765–4774. [Google Scholar]
- Sun, Z.; Bebis, G.; Miller, R. On-Road Vehicle Detection: A Review. IEEE Trans. Pattern Anal. Mach. Intell. 2006, 28, 694–711. [Google Scholar] [CrossRef]
- Li, Y.; McDonald, M. Motorway Incident Detection Using Probe Vehicles. Proc. Inst. Civ. Eng. Transp. 2005, 158, 11–15. [Google Scholar] [CrossRef]
- Asakura, Y.; Kusakabe, T.; Nguyen, L.X.; Ushiki, T. Incident Detection Methods Using Probe Vehicles with On-Board GPS Equipment. Transp. Res. Part C Emerg. Technol. 2017, 81, 330–341. [Google Scholar] [CrossRef]
- Houbraken, M.; Logghe, S.; Schreuder, M.; Audenaert, P.; Colle, D.; Pickavet, M. Automated Incident Detection Using Real-Time Floating Car Data. J. Adv. Transp. 2017, 2017, 1–13. [Google Scholar] [CrossRef]
- Liang, Z.; Chen, H.; Song, Z.; Zhou, Y.; Zhang, B. Traffic Congestion Incident Detection and Dissipation Algorithm for Urban Intersection Based on FCD. In Proceedings of the 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 2578–2583. [Google Scholar] [CrossRef]
- Han, X.; Grubenmann, T.; Cheng, R.; Wong, S.C.; Li, X.; Sun, W. Traffic Incident Detection: A Trajectory-Based Approach. In Proceedings of the 2020 IEEE 36th International Conference on Data Engineering (ICDE), Dallas, TX, USA, 20–24 April 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1866–1869. [Google Scholar] [CrossRef]
- Asakura, Y.; Kusakabe, T.; Long, N.X.; Ushiki, T. Incident Detection Methods Using Probe Vehicles with On-Board GPS Equipment. Transp. Res. Procedia 2015, 6, 17–27. [Google Scholar] [CrossRef]
- Fogue, M.; Garrido, P.; Martinez, F.J.; Cano, J.; Calafate, C.T.; Manzoni, P. Automatic Accident Detection: Assistance Through Communication Technologies and Vehicles. IEEE Veh. Technol. Mag. 2012, 7, 90–100. [Google Scholar] [CrossRef]
- Fernandes, B.; Gomes, V.; Ferreira, J.; Oliveira, A. Mobile Application for Automatic Accident Detection and Multimodal Alert. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference (VTC Spring), Glasgow, UK, 11–14 May 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Bossom, R.; Brignolo, R.; Ernst, T.; Evensen, K.; Frötscher, A.; Höfs, W.; Jeftic, Z.; Jääskeläinen, J.; Kompfner, P.; Kosch, T.; et al. D31 European ITS Communication Architecture-Overall Framework–Proof of Concept Implementation; FP6-027377; BMW Group Research and Technology: München, Germany, 2009. [Google Scholar]
- Cesana, M.; Fratta, L.; Gerla, M.; Giordano, E.; Pau, G. C-VeT the UCLA Campus Vehicular Testbed: Integration of VANET and Mesh Networks. In Proceedings of the 2010 European Wireless Conference (EW), Lucca, Italy, 12–15 April 2010; pp. 689–695. [Google Scholar] [CrossRef]
- Welcome to OnStar. Available online: https://www.onstar.com/us/en/home/ (accessed on 15 April 2021).
- Grzeszczyk, R.; Merkisz, J.; Bogus, P.; Kaminski, T. Methods and Procedures for Testing the E-Call in-Vehicle Unit for the Purpose of Its Performance Assessment and Certification. In Proceedings of the 21st International Technical Conference on the Enhanced Safety of Vehicles (ESV), Stuttgart, Germany, 15–18 June 2009. [Google Scholar]
- Ahuja, L. Automatic Incident Detection (AID). Master’s Thesis, Iowa State University, Ames, IA, USA, 2018. [Google Scholar]
- Chakraborty, P.; Hegde, C.; Sharma, A. Data-Driven Parallelizable Traffic Incident Detection Using Spatio-Temporally Denoised Robust Thresholds. Transp. Res. Part C Emerg. Technol. 2019, 105, 81–99. [Google Scholar] [CrossRef]
- Chakraborty, P.; Sharma, A.; Knickerbocker, S.; Hess, J. Outlier Mining Based Traffic Incident Detection Using Big Data Analytics. In Proceedings of the 96th Annual Meeting Transportation Research Board, Washington, DC, USA, 8–12 January 2017. [Google Scholar]
- Federal Highway Administration. Traffic Congestion and Reliability: Trends and Advanced Strategies for Congestion Mitigation; FHWA-HOP-05-064; Federal Highway Administration: Washington, DC, USA, 2005. [Google Scholar]
- Ahmed, S.A.; Cook, A. Application of Time-Series Analysis Techniques to Freeway Incident DETECTION. Transp. Res. Rec. 1982, 841, 19–21. [Google Scholar]
- Cook, A.R.; Cleveland, D.E. The Detection of Freeway Capacity Reducing Incidents by Traffic Stream Measurements; HSRI Report No. TrS-1; The University of Michigan: Ann Arbor, MI, USA, 1970; Volume 138. [Google Scholar] [CrossRef]
- Deniz, O.; Celikoglu, H.B. Overview to Some Existing Incident Detection Algorithms: A Comparative Evaluation. Procedia Soc. Behav. Sci. 2011, 2, 153–168. [Google Scholar]
- Ahmed, S.A.; Cook, A.R. Time Series Models for Freeway Incident Detection. Transp. Eng. J. ASCE 1980, 106, 731–745. [Google Scholar] [CrossRef]
- Ahmed, M.S.; Cook, A.R. Analysis of Freeway Traffic Time-Series Data by Using Box-Jenkins Techniques. Transp. Res. Rec. 1997, 722, 1–9. [Google Scholar]
- Li, H.; Li, S.; Zhu, H.; Zhao, X.; Zhang, X. Automated Detection Algorithm for Traffic Incident in Urban Expressway Based on Lengthways Time Series. In Green Intelligent Transportation Systems; Springer: Singapore, 2019; Volume 503, pp. 625–633. [Google Scholar] [CrossRef]
- Niu, S.-F.; Jiang, G.-Y.; Li, H.-W.; Jiang, H. Automated Detection Algorithm for Traffic Incident in Urban Expressway Based on Lengthways Time Series of Traffic Parameters. Ha’erbin Gong Ye Da Xue Xue Bao 2011, 43, 144–148. [Google Scholar]
- Olugbade, S.; Ojo, S.; Imoize, A.L.; Isabona, J.; Alaba, M.O. A Review of Artificial Intelligence and Machine Learning for Incident Detectors in Road Transport Systems. Math. Comput. Appl. 2022, 27, 77. [Google Scholar] [CrossRef]
- Yuan, T.; Rocha Neto, W.; Rothenberg, C.E.; Obraczka, K.; Barakat, C.; Turletti, T. Machine Learning for Next-generation Intelligent Transportation Systems: A Survey. Trans. Emerg. Telecommun. Technol. 2022, 33, 1–35. [Google Scholar] [CrossRef]
- Šusteková, D.; Knutelská, M. How Is the Artificial Intelligence Used in Applications for Traffic Management. Mach. Technol. Mater. 2015, 9, 49–52. [Google Scholar]
- Olayode, O.I.; Tartibu, L.K.; Okwu, M.O. Application of Artificial Intelligence in Traffic Control System of Non-Autonomous Vehicles at Signalized Road Intersection. Procedia CIRP 2020, 91, 194–200. [Google Scholar] [CrossRef]
- Rusyaidi, M.; Ibrahim, Z. A Review: An Evaluation of Current Artificial Intelligent Methods in Traffic Flow Prediction. IOP Conf. Ser. Mater. Sci. Eng. 2020, 917, 012063. [Google Scholar] [CrossRef]
- Gamel, S.A.; Saleh, A.I.; Ali, H.A. Machine Learning-Based Traffic Management Techniques for Intelligent Transportation System: Review. Nile J. Commun. Comput. Sci. 2021, 1, 9–18. [Google Scholar]
- Nama, M.; Nath, A.; Bechra, N.; Bhatia, J.; Tanwar, S.; Chaturvedi, M.; Sadoun, B. Machine Learning-based Traffic Scheduling Techniques for Intelligent Transportation System: Opportunities and Challenges. Int. J. Commun. Syst. 2021, 34, e4814. [Google Scholar] [CrossRef]
- Sharma, S.; Harit, S.; Kaur, J. Traffic Accident Detection Using Machine Learning Algorithms. In Proceedings of Third International Conference on Sustainable Computing SUSCOM-2021; Springer: Jaipur, India, 2021; pp. 501–507. [Google Scholar] [CrossRef]
- Mani, D.; Amrith, P.; Umamaheswari, E.; Ajay, D.M.; Anitha, R.U. Smart Detection of Vehicle Accidents Using Object Identification Sensors with Artificial Intelligent Systems. Int. J. Recent Technol. Eng. 2019, 7, 375–379. [Google Scholar]
- Huang, T.; Wang, S.; Sharma, A. Highway Crash Detection and Risk Estimation Using Deep Learning. Accid. Anal. Prev. 2020, 135, 105392. [Google Scholar] [CrossRef]
- Jin, X.; Srinivasan, D.; Cheu, R.L. Classification of Freeway Traffic Patterns for Incident Detection Using Constructive Probabilistic Neural Networks. IEEE Trans. Neural Netw. 2001, 12, 1173–1187. [Google Scholar] [CrossRef]
- McCulloch, W.S.; Pitts, W.H. A Logical Calculus of the Ideas Immanent in Nervous Activity. Bull. Math. Biophys. 1943, 5, 115–133. [Google Scholar] [CrossRef]
- Hardesty, L. Explained: Neural Networks. MIT News|Massachusetts Institute of Technology. Available online: https://news.mit.edu/2017/explained-neural-networks-deep-learning-0414 (accessed on 27 December 2021).
- What Are Neural Networks? Available online: https://www.ibm.com/cloud/learn/neural-networks (accessed on 27 December 2021).
- Wang, L.; Zhao, J.; Mortier, R. Neural Network. In OCaml Scientific Computing; Springer: Cham, Switzerland, 2022; pp. 219–242. [Google Scholar] [CrossRef]
- Hopfield, J.J. Neural Networks and Physical Systems with Emergent Collective Computational Abilities. Proc. Natl. Acad. Sci. USA 1982, 79, 2554–2558. [Google Scholar] [CrossRef] [PubMed]
- Cheu, R.L.; Ritchie, S.G.; Recker, W.W.; Bavarian, B. Investigation of a Neural Network Model for Freeway Incident Detection; National Academies Press: Washington, DC, USA, 1991. [Google Scholar]
- Dia, H.; Rose, G. Development and Evaluation of Neural Network Freeway Incident Detection Models Using Field Data. Transp. Res. Part C Emerg. Technol. 1997, 5, 313–331. [Google Scholar] [CrossRef]
- Abdulhai, B.; Ritchie, S.G. Enhancing the Universality and Transferability of Freeway Incident Detection Using a Bayesian-Based Neural Network. Transp. Res. Part C Emerg. Technol. 1999, 7, 261–280. [Google Scholar] [CrossRef]
- Zyryanov, V.V. Incidents Detection on City Roads. IOP Conf. Ser. Mater. Sci. Eng. 2020, 913, 42065. [Google Scholar] [CrossRef]
- Gupta, G.; Singh, R.; Singh Patel, A.; Ojha, M. Accident Detection Using Time-Distributed Model in Videos. In Proceedings of the Fifth International Congress on Information and Communication Technology, London, UK, 20–21 February 2020; Yang, X.-S., Sherratt, S., Dey, N., Joshi, A., Eds.; Springer: Singapore, 2021; pp. 214–223. [Google Scholar]
- Hochreiter, S.; Schmidhuber, J. Long Short-Term Memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Jin, X.; Cheu, R.L.; Srinivasan, D. Development and Adaptation of Constructive Probabilistic Neural Network in Freeway Incident Detection. Transp. Res. Part C Emerg. Technol. 2002, 10, 121–147. [Google Scholar] [CrossRef]
- Lin, Y.; Li, L.; Jing, H.; Ran, B.; Sun, D. Automated Traffic Incident Detection with a Smaller Dataset Based on Generative Adversarial Networks. Accid. Anal. Prev. 2020, 144, 105628. [Google Scholar] [CrossRef]
- Li, L.; Lin, Y.; Du, B.; Yang, F.; Ran, B. Real-Time Traffic Incident Detection Based on a Hybrid Deep Learning Model. Transp. A 2022, 18, 78–98. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy Logic = Computing with Words. IEEE Trans. Fuzzy Syst. 1996, 4, 103–111. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy Algorithms. Inf. Control 1968, 12, 94–102. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy Sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy Sets and Systems. Int. J. Gen. Syst. 1990, 17, 129–138. [Google Scholar] [CrossRef]
- Mendel, J.M. Fuzzy Logic Systems for Engineering: A Tutorial. Proc. IEEE 1995, 83, 345–377. [Google Scholar] [CrossRef]
- Hüllermeier, E. Does Machine Learning Need Fuzzy Logic? Fuzzy Sets Syst. 2015, 281, 292–299. [Google Scholar] [CrossRef]
- Klir, G.J. Fuzzy Logic. IEEE Potentials 1995, 14, 10–15. [Google Scholar] [CrossRef]
- Albertos, P.; Sala, A.; Olivares, M. Fuzzy Logic Controllers. Methodology. Advantages and Drawbacks. In Proceedings of the Congreso Español Sobre Tecnologías y Lógica Fuzzy, Sevilla, Spain, 20–22 September 2000; pp. 1–11. [Google Scholar]
- Jantzen, J. Foundations of Fuzzy Control: A Practical Approach: Second Edition; Wiley Online Library: Chichester, UK, 2013. [Google Scholar] [CrossRef]
- Bai, Y.; Wang, D. Fundamentals of Fuzzy Logic Control—Fuzzy Sets, Fuzzy Rules and Defuzzifications. In Advanced Fuzzy Logic Technologies in Industrial Applications; Springer: London, UK, 2006. [Google Scholar] [CrossRef]
- Nedjah, N.; de Macedo Mourelle, L. Fuzzy Systems Engineering: Theory and Practice; Springer Science & Business Media: Berlin, Germany, 2005; Volume 181. [Google Scholar]
- Reshaping the World with Fuzzy Logic Reshaping the World with Fuzzy Logic. Available online: http://www.weareworldquant.com (accessed on 21 November 2021).
- Nguyen, D.-B.; Dow, C.-R.; Hwang, S.-F. An Efficient Traffic Congestion Monitoring System on Internet of Vehicles. Wirel. Commun. Mob. Comput. 2018, 2018, 1–17. [Google Scholar] [CrossRef]
- Mustafa, F.W.F. An Application of Fuzzy Logic in Urban Traffic Incident Detection. Master’s Thesis, United Arab Emirates University, Al Ain, United Arab Emirates, 2015. [Google Scholar]
- Rossi, R.; Gastaldi, M.; Gecchele, G.; Barbaro, V. Fuzzy Logic-Based Incident Detection System Using Loop Detectors Data. Transp. Res. Procedia 2015, 10, 266–275. [Google Scholar] [CrossRef]
- Ahmed, F.; Hawas, Y.E. A Fuzzy Logic Model for Real-Time Incident Detection in Urban Road Network. In Proceedings of the 5th International Conference on Agents and Artificial Intelligence, Barcelona, Spain, 15–18 February 2013; Volume 2, pp. 465–472. [Google Scholar] [CrossRef]
- Lee, S.; Krammes, R.A.; Yen, J. Fuzzy-Logic-Based Incident Detection for Signalized Diamond Interchanges. Transp. Res. Part C Emerg. Technol. 1998, 6, 359–377. [Google Scholar] [CrossRef]
- Cortes, C.; Vapnik, V. Support-Vector Networks. Mach. Learn. 1995, 20, 273–297. [Google Scholar] [CrossRef]
- Jeyakumar, V.; Li, G.; Suthaharan, S. Support Vector Machine Classifiers with Uncertain Knowledge Sets via Robust Optimization. Optimization 2014, 63, 1099–1116. [Google Scholar] [CrossRef]
- Bharath Kumar, M.; Basit, A.; Kiruba, M.B.; Giridharan, R.; Keerthana, S.M. Road Accident Detection Using Machine Learning. In Proceedings of the 2021 International Conference on System, Computation, Automation and Networking (ICSCAN), Puducherry, India, 30–31 July 2021; pp. 2–6. [Google Scholar] [CrossRef]
- Hsu, C.-W.; Chang, C.-C.; Lin, C.-J. A Practical Guide to Support Vector Classification; University of National Taiwan: Taipei, Taiwan, 2003. [Google Scholar]
- Yuan, F.; Cheu, R.L. Incident Detection Using Support Vector Machines. Transp. Res. Part C Emerg. Technol. 2003, 11, 309–328. [Google Scholar] [CrossRef]
- Ruppert, D. The Elements of Statistical Learning: Data Mining, Inference, and Prediction, 2nd ed.; Springer: New York, NY, USA, 2004; Volume 99. [Google Scholar] [CrossRef]
- Ho, T.K. Random Decision Forests. In Proceedings of the International Conference on Document Analysis and Recognition, ICDAR, Montreal, QC, Canada, 14–16 August 1995; Volume 1, pp. 278–282. [Google Scholar] [CrossRef]
- Sharda, R.; Voß, S.; Suthaharan, S. Machine Learning Models and Algorithms for Big Data Classification; Thinking with Examples for Effective Learning; Springer: New York, NY, USA, 2019; ISBN 978-1-4899-7641-3. [Google Scholar]
- Breiman, L. Random Forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Random Forest Algorithm. Available online: https://www.simplilearn.com/tutorials/machine-learning-tutorial/random-forest-algorithm?tag=randomforest (accessed on 8 May 2021).
- Iqbal, Z.; Khan, M.I.; Hussain, S.; Habib, A. An Efficient Traffic Incident Detection and Classification Framework by Leveraging the Efficacy of Model Stacking. Complexity 2021, 2021, 1–17. [Google Scholar] [CrossRef]
- Mahmassani, H.S.; Haas, C.; Zhou, S.; Peterman, J. Evaluation of Incident Detection Methodologies; FHWA/TX-00/1795-1; University of Texas at Austin: Austin, TX, USA, 1999. [Google Scholar]
- Bao, L.; Wang, Q.; Qu, W.; Mo, X. Research on Highway Traffic Event Detection Method Based on Image Processing. IOP Conf. Ser. Earth Environ. Sci. 2021, 791, 012193. [Google Scholar] [CrossRef]
- Mimbela, L.E.Y.; Klein, L.A. Summary Of Vehicle Detection And Surveillance Technologies Used in Intelligent Transportation Systems; Joint Program Office for Intelligent Transportation Systems; U.S. Department of Transportation: Washington, DC, USA, 2000. [Google Scholar]
- Ren, J.; Chen, Y.; Xin, L.; Shi, J.; Li, B.; Liu, Y. Detecting and Positioning of Traffic Incidents via Video-Based Analysis of Traffic States in a Road Segment. IET Intell. Transp. Syst. 2016, 10, 428–437. [Google Scholar] [CrossRef]
- Michalopoulos, P.G. Vehicle Detection Video Through Image Processing: The Autoscope System. IEEE Trans. Veh. Technol. 1991, 40, 21–29. [Google Scholar] [CrossRef]
- Michalopoulos, P.G.; Jacobson, R.D.; Anderson, C.A.; DeBruycker, T.B. Automatic Incident Detection through Video Image Processing. Traffic Eng. Control 1993, 34, 66–75. [Google Scholar]
- Hall, F.L.; Barrow, D. Effect of Weather on the Relationship between Flow and Occupancy on Freeways. Transp. Res. Rec. 1988, 1194, 55–63. [Google Scholar]
- Potash, C.B.; Brown, J.R. Fog Mitigation Update: Fog Mitigation Measures as Applied to Highway Bridge Structures. Transp. Res. Rec. 1988, 1172, 74–77. [Google Scholar]
- Evans, L. The Dominant Role of Driver Behavior in Traffic Safety. Am. J. Public Health 1996, 86, 784–786. [Google Scholar] [CrossRef] [PubMed]
- National Highway Transportation Safety Administration (NHTSA). 2016 Fatal Motor Vehicle Crashes: Overview; DOT HS 812 456; NHTSA’s National Center for Statistics and Analysis: Washington, DC, USA, 2017. [Google Scholar]
- Liu, W.; Li, H.; Zhang, H. Dangerous Driving Behavior Recognition Based on Hand Trajectory. Sustainability 2022, 14, 12355. [Google Scholar] [CrossRef]
- Elsahly, O.; Abdelfatah, A. Effects of Automated Vehicles on Freeway Traffic Performance. Wulfenia J. 2020, 27, 83–107. [Google Scholar]
- Bottlinger, J. How Poor Vehicle Maintenance Leads to Traffic Accidents. Available online: https://www.bottlingerlaw.com/blog/how-poor-vehicle-maintenance-leads-to-traffic-accidents/ (accessed on 22 October 2022).
- Lopez Conde, M.; Twinn, I. How Artificial Intelligence Is Making Transport Safer, Cleaner, More Reliable and Efficient in Emerging Markets; World Bank Group, International Finance Corporation: Washington, DC, USA, November 2019. [Google Scholar]
| Category | Contributions and Advantages | Limitations and Drawbacks | |
|---|---|---|---|
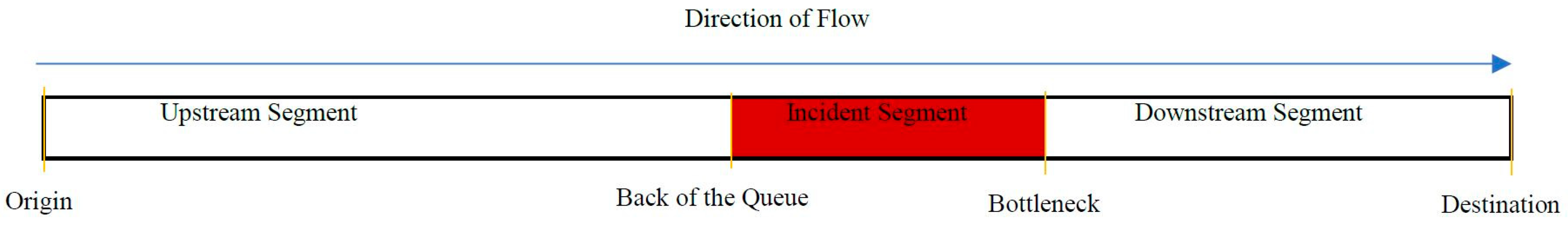
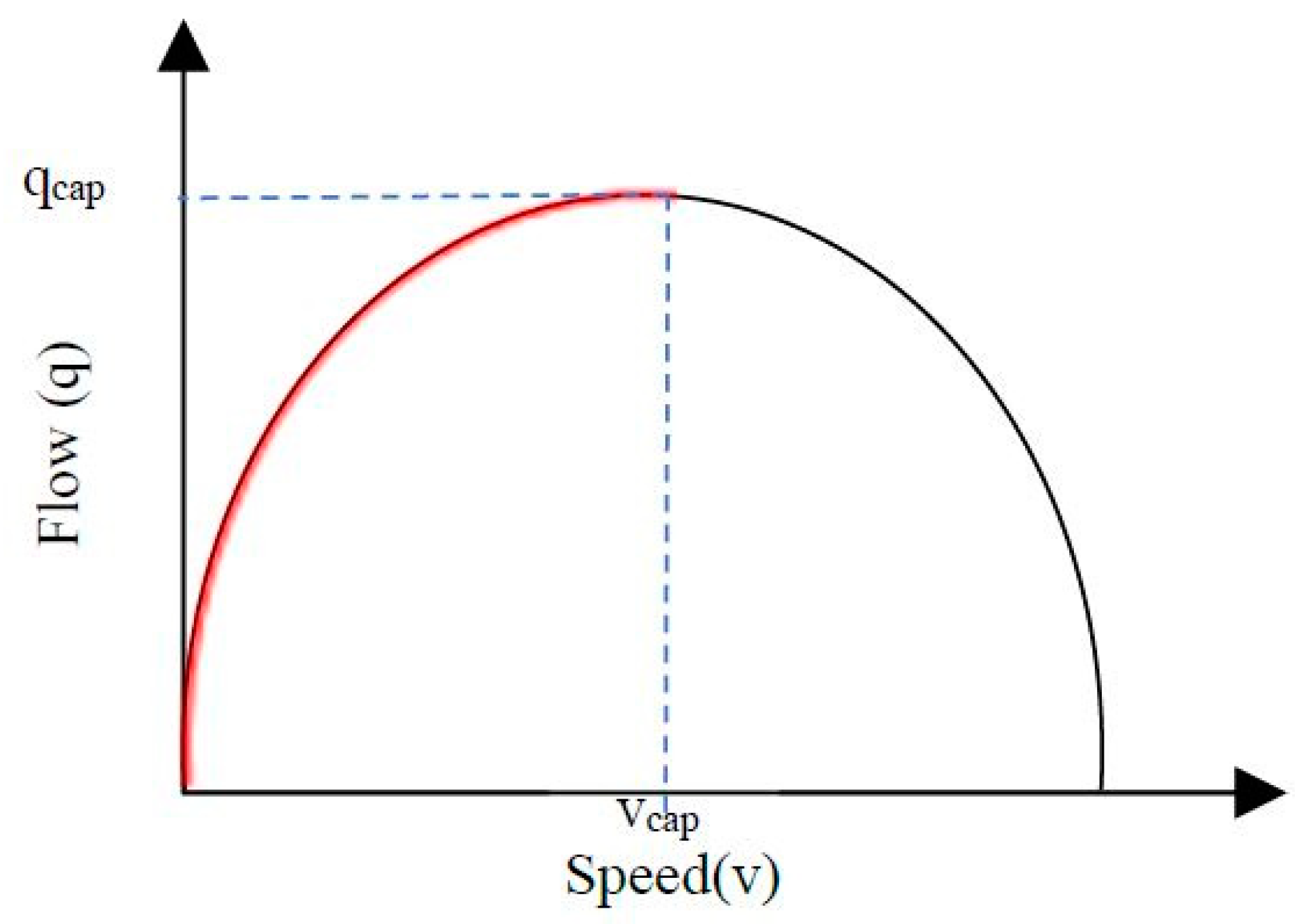
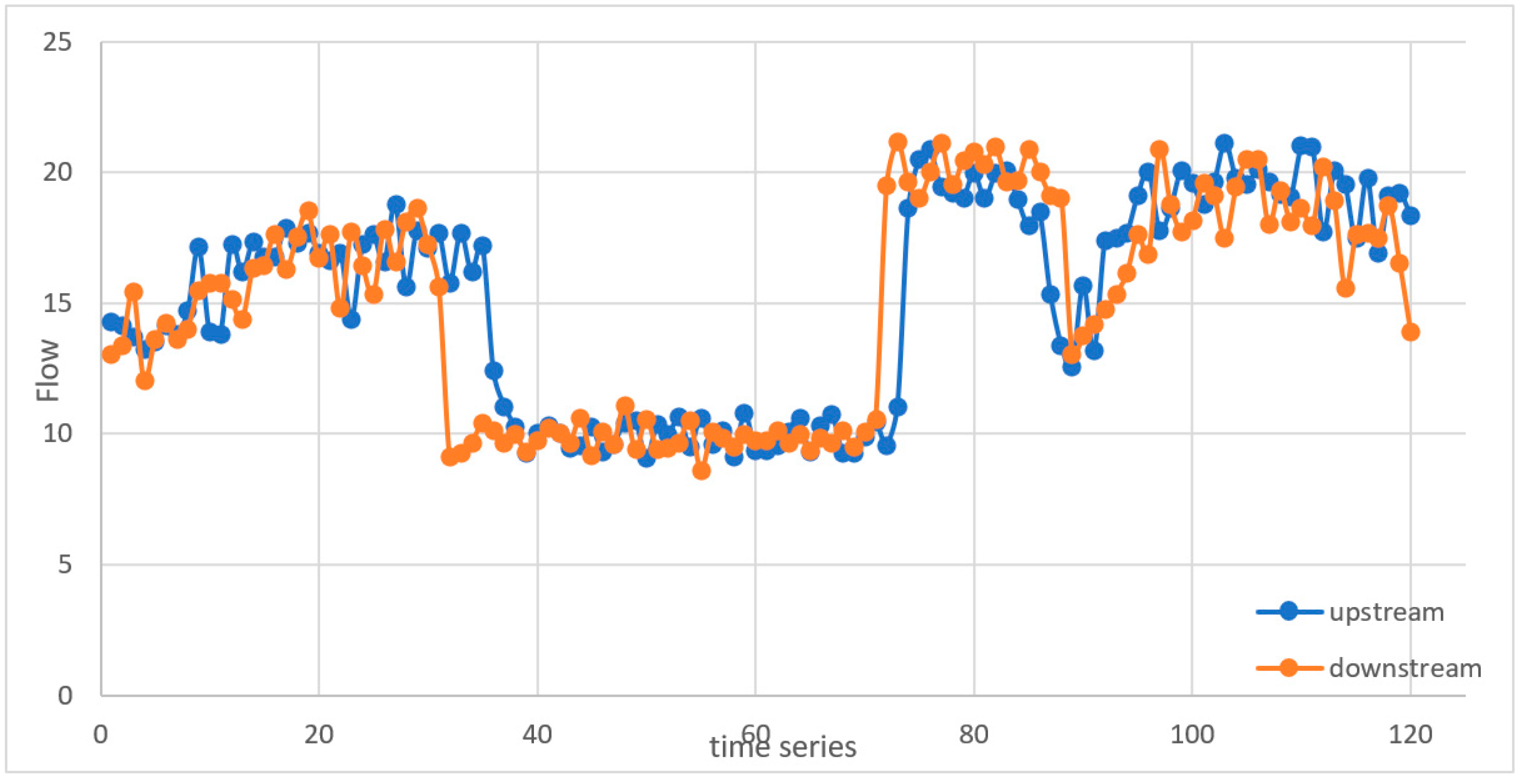
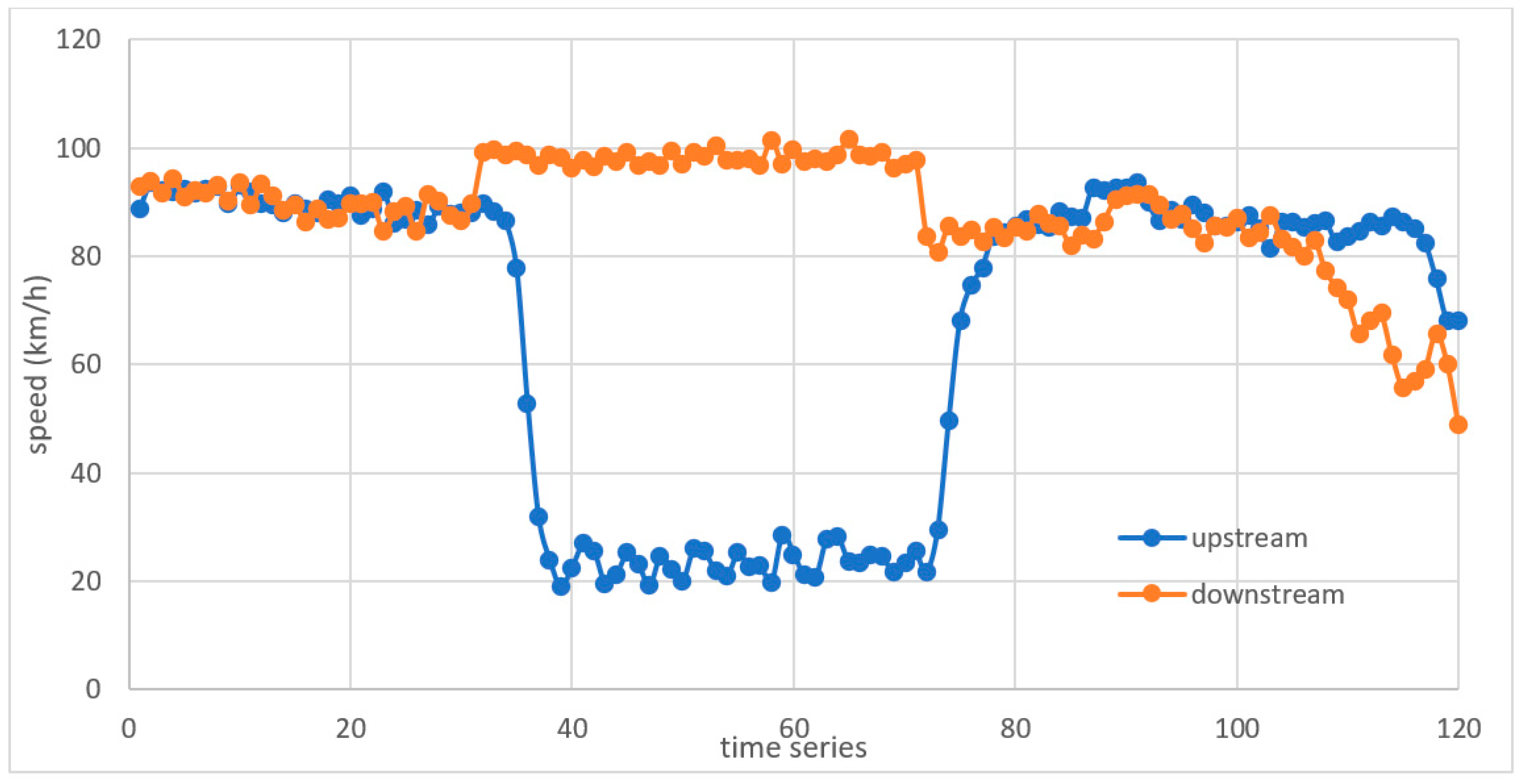
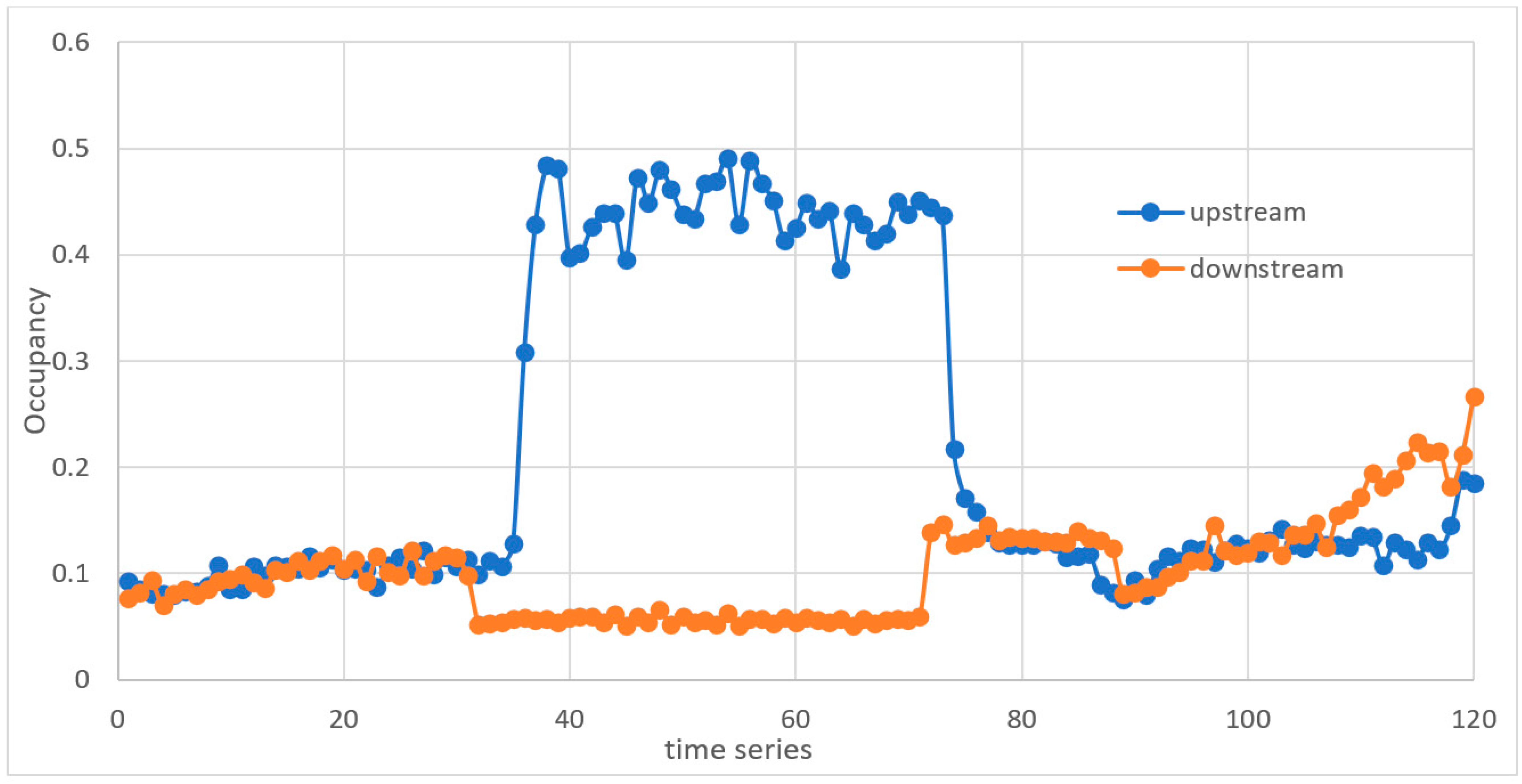
| Comparative algorithms | California algorithms | Look for discrepancies in traffic parameters between adjacent loop detectors to identify the presence of an incident [16,38,41,42,43,44,45,46]. It has good DR and a tolerable FAR. | It has a long MTTD that can reach about 4 min [44]. The performance of the algorithm is affected by any malfunction in any detector. Some factors can cause incident-like patterns and increase the number of false alarms. |
| McMaster algorithms | Overcome the weaknesses of the California algorithm series [47,48]. It uses the data from a single detector station instead of two adjacent stations and considers the relationship between speed, flow and occupancy. | It is sensitive to severe weather conditions such as rain or snow, which may result in an increase in the number of false alarms. | |
| Minnesota algorithm | Investigates the discontinuity in the average spatial occupancy difference between the two stations over six intervals. The algorithm uses short-term time averages to smooth up the random fluctuations in the data, filter the data, and remove the noise that triggers false alarms, which affects the detection capability of the algorithm [37,49]. | The detection time can be three minutes or more. It depends on the occupancy only to detect incidents, which can cause false alarms during low traffic conditions. | |
| Bluetooth based algorithms | Uses Bluetooth detectors instead of an inductive loop, which provides a reliable, cost-efficient and fast method for detecting traffic incidents or congestion [50,51]. | Some factors such as detectors spacing, operating conditions, duration and severity of the incident and the location of the incident relative to the detectors can impact the performance of the algorithm. | |
| GPS-based algorithms | Utilizes driver’s mobile phones or GPS trackers in the vehicles to establish spatio-temporal traces of the vehicles to detect traffic congestion and incidents [52,53]. | The range and the placement of the sensors can affect the efficiency of the sensors or may cause false alarms. | |
| FCD-based algorithms | Uses probe vehicles to collect real-time traffic data and detect the occurrence of incidents. Cost-effective method that can be used instead of fixed detectors [54,55,56,57,58,59]. | Penetration rate of the tracked vehicles on the road and data latency affect the performance of the algorithm. | |
| V2V- and V2I-based algorithms | Use V2V and V2I communications to monitor traffic and detect incidents and congestion [60,61,62,63,64,65]. | Impacted by the availability of the communications protocols among different entities (vehicles and infrastructure). | |
| Statistical Algorithms | SND algorithm | Evaluates the deviation of a variable from the means to identify potential incidents [14,31,39,41,66]. | Sensitive to the presence of outliers, which can cause the masking phenomenon. |
| IQD-based algorithm | Overcomes the masking phenomenon in the SND algorithm by using the median or the second quartile instead of the mean and Inter-Quartile score Q instead of the standard deviation to calculate IQD [67,68,69]. | It is prone to swamping phenomenon, which can increase FAR. | |
| DES algorithm | Removes the noise and heterogeneity from the traffic data to clarify the true traffic patterns to help the system to detect incidents easily and reduce false alarms [30,70,71]. | It predicts the traffic variables under normal traffic conditions and assumes that the traffic will follow the predicted pattern over time. Additionally, it requires extensive computational efforts. | |
| Time Series Algorithms | Uses historical data of traffic variables to employ statistical short-term forecasting of normal traffic conditions. Significant deviations between the observed and predicted conditions indicate the existence of incidents [39,41,70,72,73,74,75,76]. | Time-consuming and require extensive computational efforts. Additionally, they assume the traffic follows a predictable pattern over time. | |
| Artificial Intelligence Algorithms | ANN algorithms | Uses machine learning to classify the provided traffic data as incident or non-incident situations [19,31,37,93,94,95,96,97,98,99,100,101]. | The accuracy of the algorithm depends on the performance of the model which needs optimization and tuning. There is no rule to determine the structure of the network, the appropriate structure is achieved through trial and error. |
| Fuzzy logic algorithms | Deal with the complex and stochastic nature of traffic variables. They provide the likelihood for an incident [52,114,115,116,117,118]. | The performance depends on the rules and membership functions that are set. They completely depend on human knowledge and expertise. It does not give a clear signal of incident or no incident. | |
| Support Vector Machine | Provides a computationally efficient nonlinear classifier that can be used in real-time incident detection [21,35,119,120,121,122,123]. | The accuracy of the model is highly dependent on the kernel function used. Nevertheless, selecting the appropriate kernel function is complex. SVM is suitable for large datasets because this will make the training process very time-consuming. | |
| Ensemble Learning Algorithms | Combine multiple machine learning models to build a powerful prediction model that has better predictive performance than any constituent machine learning model alone [25,35,66,129]. | The models should be selected carefully to improve the predictive performance of the model. The ensemble can be complex and less interpretable and can cost more time during creating and training. | |
| Video–image Processing Algorithms | Analyze videos of real-time traffic captured by surveillance cameras to detect traffic congestions and incidents [31,41,72,130,131,132,133,134,135]. | The lighting conditions, extreme weather conditions and coverage range of the camera that is used to capture traffic video have a major impact on the algorithm’s performance [41]. | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
ElSahly, O.; Abdelfatah, A. A Systematic Review of Traffic Incident Detection Algorithms. Sustainability 2022, 14, 14859. https://doi.org/10.3390/su142214859
ElSahly O, Abdelfatah A. A Systematic Review of Traffic Incident Detection Algorithms. Sustainability. 2022; 14(22):14859. https://doi.org/10.3390/su142214859
Chicago/Turabian StyleElSahly, Osama, and Akmal Abdelfatah. 2022. "A Systematic Review of Traffic Incident Detection Algorithms" Sustainability 14, no. 22: 14859. https://doi.org/10.3390/su142214859
APA StyleElSahly, O., & Abdelfatah, A. (2022). A Systematic Review of Traffic Incident Detection Algorithms. Sustainability, 14(22), 14859. https://doi.org/10.3390/su142214859






