CoviBlock: A Secure Blockchain-Based Smart Healthcare Assisting System
Abstract
:1. Introduction
- We propose a blockchain-based decentralised distributed assisting system for preserving medical record privacy and security in pandemic mitigation operations.
- We introduce system-specific DDRAC and privacy-preserving mechanisms.
- We suggest a prototype security analysis to demonstrate system-level security versus scalability and usability.
- We introduce a blockchain-based certificate management mechanism to introduce system-level transparency in medical resources utilization.
2. Related Work
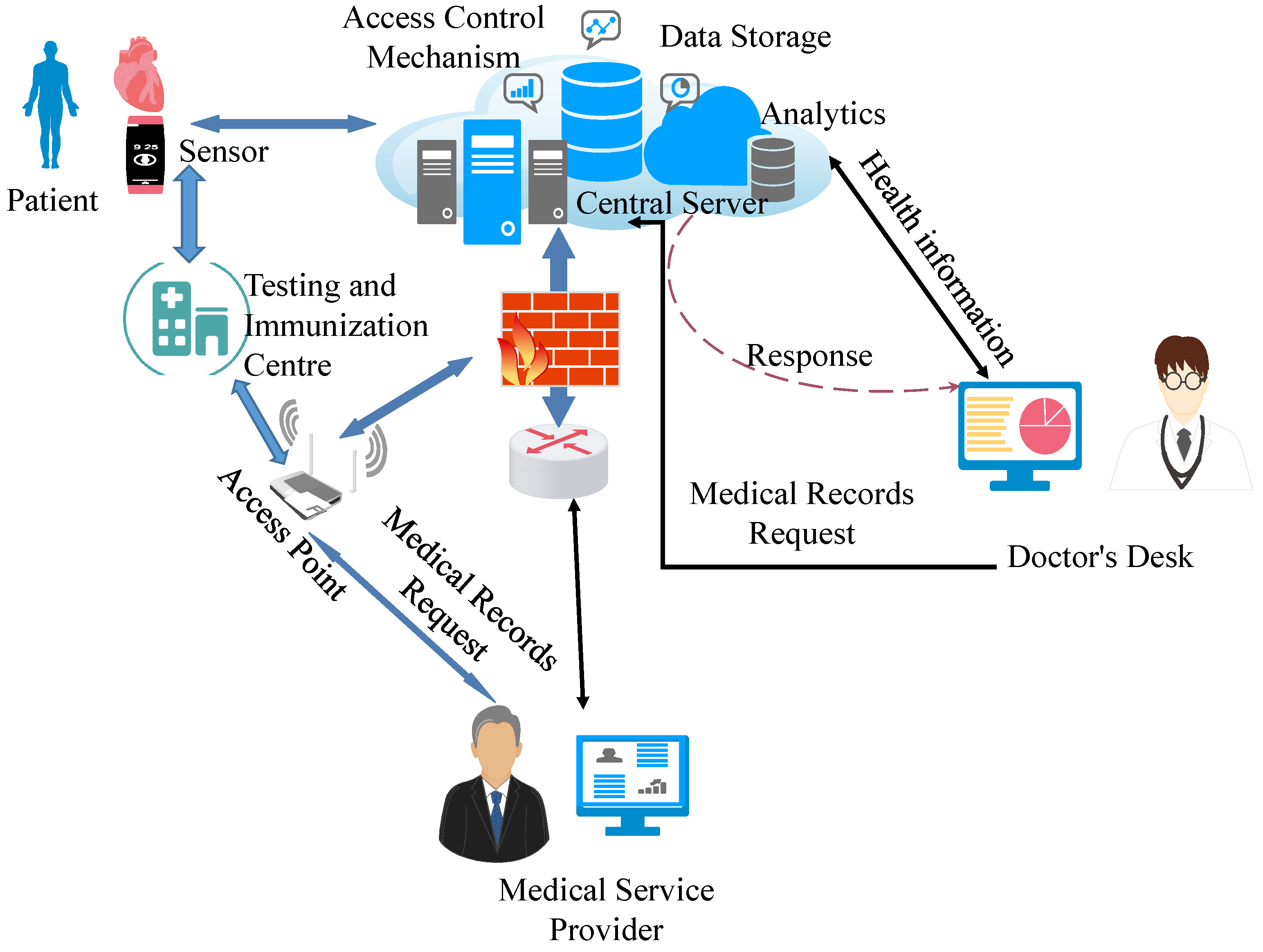
3. System Architecture and Identity Management
3.1. Three-Layered Identity and DDRAC
3.2. Group Formation and Leader Election
- i.
- Coverage rate is the ratio of the number of logical connections to the total number of nodes on the critical path. The device with the highest coverage rate is considered to be the new group leader. The availability of information can be ensured if a node has a greater number of connections.
- ii.
- In the initial phase, the node with the greatest number of connections within the group is regarded as the interim leader. When the elected leader assumes control, the ledgers are transferred to the elected leader. In situations where only one node actively participates in the critical path and there is no competition for election, a temporary leader node is elected for the permanent position.
- iii.
- A device with a low offline rate has a lower priority than a device with a high critical path coverage rate. It assists in preventing service interruptions and enhances service availability.
- iv.
- In the event of a tie, a candidate’s election history is taken into account to prevent the election from being biassed. In order to prevent a monopoly in the election, the system imposes a minimum threshold on each leader.
- v.
- The election history is considered to identify valid nodes, thereby preventing the selection of a malicious device.

| Algorithm 1 Leader Election |
 |
4. 3T with CoviBlock
| Algorithm 2 Mitigation Assisting |
 |
4.1. Electronic Health Record (EHR)
4.2. Resource Management
| Algorithm 3 Resource Allocation |
 |
- i.
- Allocating ICU resources to patients in an emergency situation;
- ii.
- Allocating a dedicated group of service providers for continuous monitoring;
- iii.
- Patients’ digital records are generated automatically based on the services and resources used during their treatments;
- iv.
- Timely distribution of medical kits to front-line workers and other healthcare service providers.
4.3. Contact Tracing and Immunization
| Algorithm 4 Immunization |
 |
4.4. Digital Health Certificate Management
| Algorithm 5 Digital Health Certificate |
 |
5. Experimental Setup
6. Results and Analysis
6.1. Security Analysis
6.2. Privacy and Anonymity
6.2.1. Integrity and Version Control
6.2.2. Accountability and Authorization
6.3. DDoS and Availability
6.4. Cost and Response-Rate Analysis
6.5. Transparency
6.6. Scalability
6.7. Reliability
6.8. Limitations
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yu, L.J. Study on the impact and Countermeasures caused by International Public Health Emergency response measures–based on COVID-19. In Proceedings of the 2021 International Conference on Public Health and Data Science (ICPHDS), Chengdu, China, 9–11 July 2021; pp. 139–147. [Google Scholar] [CrossRef]
- Sahraoui, Y.; Korichi, A.; Kerrache, C.A.; Bilal, M.; Amadeo, M. Remote sensing to control respiratory viral diseases outbreaks using Internet of Vehicles. Trans. Emerg. Telecommun. Technol. 2022, 33, e4118. [Google Scholar] [CrossRef]
- Egala, B.S.; Priyanka, S.; Pradhan, A.K. SHPI: Smart Healthcare System for Patients in ICU using IoT. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. iBlock: An Intelligent Decentralised Blockchain-based Pandemic Detection and Assisting System. J. Signal Process. Syst. 2021, 94, 595–608. [Google Scholar] [CrossRef] [PubMed]
- Bilal, M.; Pack, S. Secure Distribution of Protected Content in Information-Centric Networking. IEEE Syst. J. 2020, 14, 1921–1932. [Google Scholar] [CrossRef] [Green Version]
- Christodoulou, K.; Christodoulou, P.; Zinonos, Z.; Carayannis, E.G.; Chatzichristofis, S.A. Health Information Exchange with Blockchain amid Covid-19-like Pandemics. In Proceedings of the 2020 16th International Conference on Distributed Computing in Sensor Systems (DCOSS), Marina del Rey, CA, USA, 15–17 June 2020; pp. 412–417. [Google Scholar] [CrossRef]
- Vangipuram, S.L.T.; Mohanty, S.P.; Kougianos, E. CoviChain: A Blockchain Based Framework for Nonrepudiable Contact Tracing in Healthcare Cyber-Physical Systems During Pandemic Outbreaks. SN Comput. Sci. 2021, 2, 346. [Google Scholar] [CrossRef] [PubMed]
- Magid, E.; Zakiev, A.; Tsoy, T.; Lavrenov, R.; Rizvanov, A. Automating pandemic mitigation. Adv. Robot. 2021, 35, 572–589. [Google Scholar] [CrossRef]
- Hussain, I.; Park, S.J. HealthSOS: Real-Time Health Monitoring System for Stroke Prognostics. IEEE Access 2020, 8, 213574–213586. [Google Scholar] [CrossRef]
- Hussain, I.; Park, S.J. Big-ECG: Cardiographic Predictive Cyber-Physical System for Stroke Management. IEEE Access 2021, 9, 123146–123164. [Google Scholar] [CrossRef]
- Bidkhori, Y.Y.H.; Rajgopal, J. Optimizing vaccine distribution networks in low and middle-income countries. Omega 2021, 99, 714–725. [Google Scholar]
- Faroug, A.; Demirci, M. Blockchain-Based Solutions for Effective and Secure Management of Electronic Health Records. In Proceedings of the 2021 International Conference on Information Security and Cryptology (ISCTURKEY), Ankara, Turkey, 2–3 December 2021; pp. 132–137. [Google Scholar] [CrossRef]
- Tahir, S.; Tahir, H.; Sajjad, A.; Rajarajan, M.; Khan, F. Privacy-preserving COVID-19 contact tracing using blockchain. J. Commun. Netw. 2021, 23, 360–373. [Google Scholar] [CrossRef]
- Tan, L.; Yu, K.; Shi, N.; Yang, C.; Wei, W.; Lu, H. Towards Secure and Privacy-Preserving Data Sharing for COVID-19 Medical Records: A Blockchain-Empowered Approach. IEEE Trans. Netw. Sci. Eng. 2022, 9, 271–281. [Google Scholar] [CrossRef]
- Jabarulla, M.Y.; Lee, H.N. A Blockchain and Artificial Intelligence-Based, Patient-Centric Healthcare System for Combating the COVID-19 Pandemic: Opportunities and Applications. Healthcare 2021, 9, 1019. [Google Scholar] [CrossRef] [PubMed]
- Zhang, J.; Wu, M. Blockchain Use in IoT for Privacy-Preserving Anti-Pandemic Home Quarantine. Electronics 2020, 9, 1746. [Google Scholar] [CrossRef]
- Hasanat, R.T.; Arifur Rahman, M.; Mansoor, N.; Mohammed, N.; Rahman, M.S.; Rasheduzzaman, M. An IoT based Real-time Data-centric Monitoring System for Vaccine Cold Chain. In Proceedings of the 2020 IEEE East-West Design Test Symposium (EWDTS), Varna, Bulgaria, 4–7 September 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Dell’Atti, S.F.G.D.V.; Tatullo, M. Blockchain in healthcare: Insights on COVID-19. Int. J. Environ. Res. Public Health 2020, 17, 853–865. [Google Scholar]
- Manoj, M.; Srivastava, G.; Somayaji, S.R.K.; Gadekallu, T.R.; Maddikunta, P.K.R.; Bhattacharya, S. An Incentive Based Approach for COVID-19 planning using Blockchain Technology. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Naren; Tahiliani, A.; Hassija, V.; Chamola, V.; Kanhere, S.S.; Guizani, M. Privacy-Preserving and Incentivized Contact Tracing for COVID-19 Using Blockchain. IEEE Internet Things Mag. 2021, 4, 72–79. [Google Scholar] [CrossRef]
- Yong, B.; Shen, J.; Liu, X.; Li, F.; Chen, H.; Zhou, Q. An intelligent blockchain-based system for safe vaccine supply and supervision. Int. J. Inf. Manag. 2020, 52, 102024. [Google Scholar] [CrossRef]
- Ranisch, R.; Nijsingh, N.; Ballantyne, A.; van Bergen, A.; Buyx, A.; Friedrich, O.; Hendl, T.; Marckmann, G.; Munthe, C.; Wild, V. Digital contact tracing and exposure notification: Ethical guidance for trustworthy pandemic management. Ethics Inf. Technol. 2020, 23, 285–294. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. Fortified-Chain: A Blockchain-Based Framework for Security and Privacy-Assured Internet of Medical Things with Effective Access Control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Xu, H.; Zhang, L.; Onireti, O.; Fang, Y.; Buchanan, W.J.; Imran, M.A. BeepTrace: Blockchain-Enabled Privacy-Preserving Contact Tracing for COVID-19 Pandemic and Beyond. IEEE Internet Things J. 2021, 8, 3915–3929. [Google Scholar] [CrossRef]
- Lv, W.; Wu, S.; Jiang, C.; Cui, Y.; Qiu, X.; Zhang, Y. Towards Large-Scale and Privacy-Preserving Contact Tracing in COVID-19 Pandemic: A Blockchain Perspective. IEEE Trans. Netw. Sci. Eng. 2022, 9, 282–298. [Google Scholar] [CrossRef]
- Bilal, M.; Kang, S.G. An Authentication Protocol for Future Sensor Networks. Sensors 2017, 17, 979. [Google Scholar] [CrossRef] [Green Version]
- Bilal, M.; Kang, S.G. A secure key agreement protocol for dynamic group. Clust. Comput. 2017, 20, 2779–2792. [Google Scholar] [CrossRef]
- Santhosh, B.; Pradhan, A.K. CoVID-19Block. 2022. Available online: https://github.com/BhaskaraSanthosh/Fortified-Chain (accessed on 1 December 2022).














| Smart Contract | Transaction Fee (Ether) | Max Gas Fee (Gwei) | Execution Time (ms) | Response Time In (ms) | Cost in USD (Dollar) |
|---|---|---|---|---|---|
| User Registration | 0.00010504 | 2.500000011 | 27.2 | 32.26 | 0.12 |
| Immunization Tracking | 0.000155366 | 2.500000018 | 20.6 | 29.64 | 0.17 |
| SubGroup Generation | 0.000155611 | 2.600000102 | 28.73 | 34.64 | 0.17 |
| Electing New Leader | 0.000019348 | 2.600001102 | 40.23 | 49.12 | 0.022 |
| New Digital Certificate | 0.000011826 | 2.500000002 | 22.65 | 26.93 | 0.013 |
| Access Rule Update | 0.000012214 | 2.400000180 | 34.1 | 42.5 | 0.014 |
| Pseudo-Identity Generation | 0.000019309 | 2.600000002 | 38.06 | 45.43 | 0.022 |
| Public Identity Generation | 0.000010116 | 2.500001110 | 26.7 | 29.7 | 0.011 |
| Data Size | Data Writing (ms) | Data Reading (ms) | Response Time (ms) | Local Cache Response Time (ms) |
|---|---|---|---|---|
| 40 kb | 135 | 790 | 350 | 120 |
| 70 kb | 238 | 1160 | 410 | 145 |
| 100 kb | 290 | 1436 | 490 | 156 |
| 130 kb | 320 | 1570 | 540 | 163 |
| 160 kb | 350 | 1610 | 565 | 171 |
| 190 kb | 390 | 1690 | 589 | 183 |
| 220 kb | 423 | 1740 | 603 | 193 |
| System Name | 20 | 25 | 30 | 35 | 40 |
|---|---|---|---|---|---|
| H-CPS with Blockchain | 16.32 | 19.38 | 21.21 | 21.98 | 23.72 |
| CoviBlock with DDSS | 0.020 | 0.041 | 0.059 | 0.082 | 0.093 |
| Work Name | Proposed Solution | Computing Platform | Features | DDoS Proof |
|---|---|---|---|---|
| [12] | Blockchain-based EHR management system | Centralised | Security and Privacy management | No |
| [13] | Blockchain-based EHR management system | Decentralised | Privacy management | Yes |
| [14] | Blockchain-based EHR management system | Hybrid (centralised) | Privacy management | No |
| [16] | Blockchain-based quarantine management system | Partially decentralised | records sharing | No |
| [18] | quarantine records management system | Centralised | Data sharing | No |
| [19] | Blockchain-based records management system | Partially decentralised | Supply-chain management | No |
| [20] | Privacy-preserving and incentivized contact tracing for COVID-19 | Decentralised | Privacy management | No |
| CoviBlock | Blockchain-based EHR security and privacy management system | Hybrid (decentralised) | Privacy, security, traceability, scalability, anonymity, digital certificates | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Egala, B.S.; Pradhan, A.K.; Gupta, S.; Sahoo, K.S.; Bilal, M.; Kwak, K.-S. CoviBlock: A Secure Blockchain-Based Smart Healthcare Assisting System. Sustainability 2022, 14, 16844. https://doi.org/10.3390/su142416844
Egala BS, Pradhan AK, Gupta S, Sahoo KS, Bilal M, Kwak K-S. CoviBlock: A Secure Blockchain-Based Smart Healthcare Assisting System. Sustainability. 2022; 14(24):16844. https://doi.org/10.3390/su142416844
Chicago/Turabian StyleEgala, Bhaskara S., Ashok K. Pradhan, Shubham Gupta, Kshira Sagar Sahoo, Muhammad Bilal, and Kyung-Sup Kwak. 2022. "CoviBlock: A Secure Blockchain-Based Smart Healthcare Assisting System" Sustainability 14, no. 24: 16844. https://doi.org/10.3390/su142416844
APA StyleEgala, B. S., Pradhan, A. K., Gupta, S., Sahoo, K. S., Bilal, M., & Kwak, K.-S. (2022). CoviBlock: A Secure Blockchain-Based Smart Healthcare Assisting System. Sustainability, 14(24), 16844. https://doi.org/10.3390/su142416844









