1. Introduction
Trust is defined as the belief that something is sufficiently reliable to not harm or disrupt the smooth operation of continuous implementations. It is critical in regular day-to-day existence, just as it is when managing delicate information. Most wireless body area network (WBAN) medical care applications manage substantial sensitive information. Thus, trust is critical and fundamentally affects the quality and authenticity of medical care applications and administrations. A trust-based arrangement includes an express relationship with a medical care expert as this ensures a precise and quick finding of a client [
1]. Wireless body area networks (WBANs) are a kind of wireless sensor network (WSN) comprised of smaller-than-usual biosensors that are joined to or embedded inside a substance’s body to recognize vital boundaries [
2]. The embedded biosensors that screen natural changes, which are not expensive, are then conveyed to the passage through control hubs, and afterward to the far-off medical server (MS) [
3]. Because there are few biosensors connected to the substance body, and these are mostly supervised by such a focal regulator, wireless body area networks (WBANs) anticipate broad geography for the most part [
4]. These focal regulators are asset-rich gadgets; yet, because biosensor gadgets are asset-obliged, issues arise.
Moreover, with wireless body area networks (WBANs), energy effectiveness is similarly significant as far as unwavering quality is concerned. In WBANs, battery substitutions are avoided during distant patient observation, which is remarkable on account of the embedded biosensors [
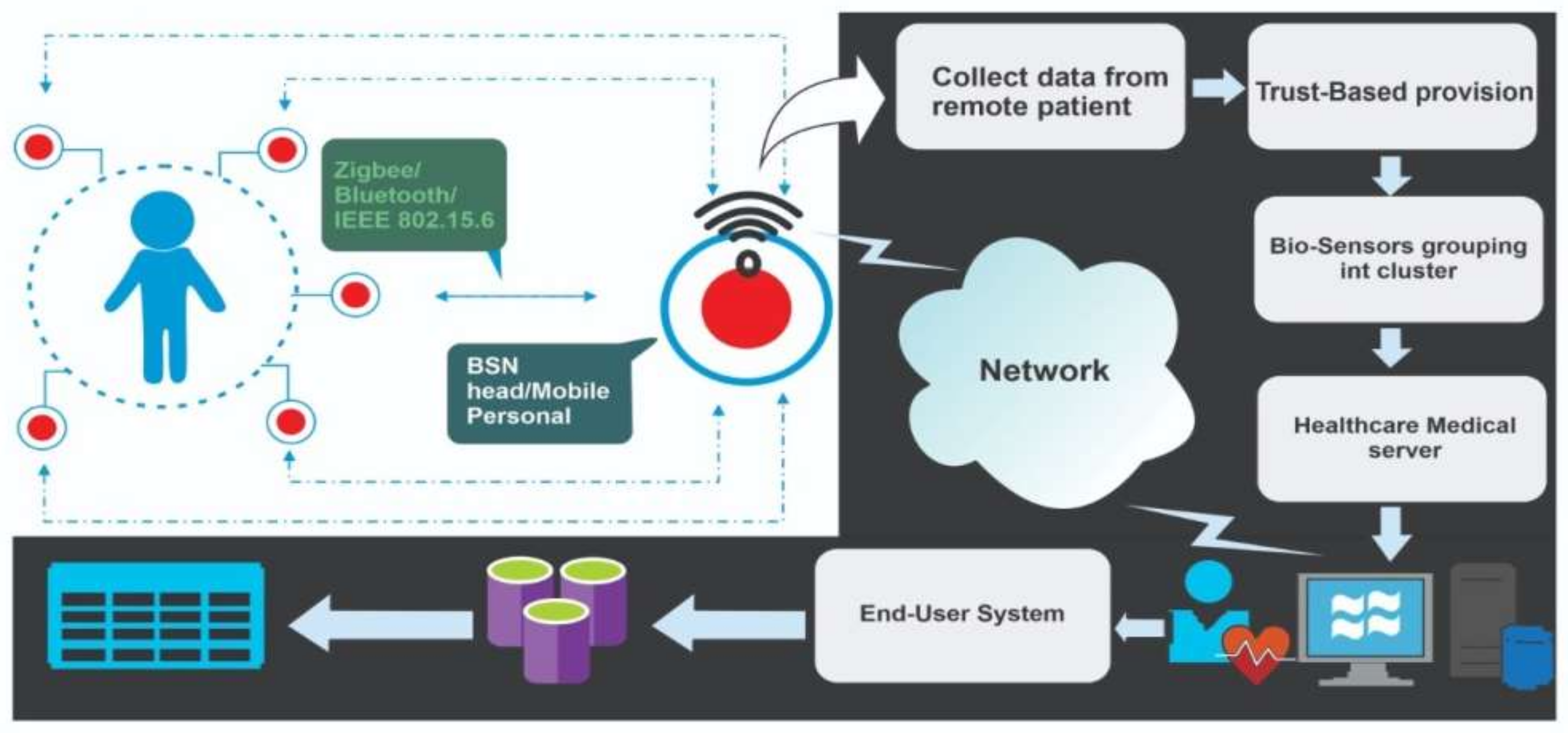
5]. An expansive depiction of a trust-based methodology for the far-off checking framework in wireless body area networks (WBANs) is displayed in
Figure 1. Through the body control unit, information is gathered from the far-away tolerant BCU. The information from the trusted motor is then passed on. Following the fundamental activity and trust, the arrangement saves the trustworthy information in the clinical worker’s dataset. When information from the biosensors is gathered, the trust arrangement is completed. In
Section 3 of this review an itemized situation is presented. Over 80% of wireless body area network (WBAN) applications, as per research insights, are in the area of wellbeing [
6]. Accordingly, most creators utilize medical services applications as an experiment for wireless body area network (WBANs) arrangements [
7].
Due to the affectability of information, reliable data are required for medical service experts in the checking of distant patients. Therefore, in wireless body area networks (WBANs) [
8,
9], the arrangement of certainty and dependability is required for medical care administration. WBANs’ unwavering quality can be improved through trust, which is needed in medical care administration by WBANs [
10]. Moreover, in the closing piece of the proposed answer for security safeguarding and expanded trustworthiness in WBAN, a cryptography-based arrangement is advertised.
The trust among biosensors and different gadgets, for example control hubs and passages, is essential for the dependability of WBANs in medical care applications [
11]. Because the data collected by biosensors are sent to WBANs climate model, it tends to be utilized in the person’s body. In their examination, many researchers have distinguished a variety of issues. Thus, in WBAN, trust should be set up to impart precise information to the clinical worker.
1.1. Problem Statement
Because of sensitive information, WBANs have experienced various trust, security, and reliability concerns. The reliability of products and information are major concerns when it comes to silently managing medical service customers. Safety, mobility, miscellany, reliability, safety, survival compatibility, and most fundamentally, energy, are all part of other key concerns. The unwavering quality of WBAN is enhanced by the use of key management methods that support network trust. Previously, some of the security tools were used during the calculation for the trust of cryptography executives [
12]. Due to the inclusion of tremendous cycles, the recently proposed trust strategies will prevent significant assets of WBANs having property liabilities [
13,
14].
1.2. Contributions and Organization of Paper
This paper endeavors to address the trust of the executives in WBAN while thinking about the necessity of vital assets. Trusting the board in WBAN is a fundamental viewpoint used to work on the unwavering quality of medical care administrations. A few analysts have shown their trust in the board models or plans utilized in WSN and WBAN utilizing various methodologies. A portion of these methodologies are fully rational; AI draws near, bioroused, deterministic, and probabilistic-based methodologies [
15,
16]. Helpful correspondence is a valuable systems administration approach for trusting the executives and building unwavering quality inside the organization. Only a few creators utilized an agreeable correspondence approach for working on the dependability inside the organization. In any event, no detailed execution evaluation has been carried out. As a result, we have been motivated to use trust to collectively solve the problem of trust motor alongside a further-developed, binomial, appropriation-based, trust-the-executive’s framework (BDTMS) approach in the WBAN climate.
The proposed work is trust-based and focuses on the further development of a binomial dispersion-based trust-the-executive’s framework (BDTMS) to deal with guaranteed trust, utilizing helpful correspondence. This practice has indeed been adopted to build trust amongst biosensors and to solidify organizations. Furthermore, by using trust endorsement, trust is established with the distant clinical worker. The helpful detection approach, alongside the trusted motor for trusting the executives, has not been utilized before in WBAN. Utilizing this methodology, the help-conveyance proportion is expanded while the normal postponement is limited altogether.
In addition, for protection conservation, another cryptographic arrangement is proposed to secure the information during far-off, tolerant observing in WBAN. The demonstration of the proposed scheme is assessed utilizing broad recreations with different measurements using the MATLAB platform. The point-by-point execution assessment exhibited that the proposed scheme beats the best-in-class, recently proposed plans as far as trust, energy effectiveness, and unwavering quality are concerned. A fully reasoned rank-based assessment is provided at the end of the work. This positioning-based assessment further validated that the recommended plot delivers a further-evolved presentation contrasted with recently proposed plans.
The layout of the remaining paper is as follows. The second section summarizes the most important state-of-the-art techniques for the issue area, with a focus on WBAN and WSN. The proposed remote healthcare strategy employing the WBAN paradigm is presented in
Section 3.
Section 4 illustrates the effectiveness of the suggested algorithm. Lastly, the conclusion and future directions are elicited in
Section 5.
2. Literature Survey
In this section, we audit cutting-edge, trust-based, unwavering quality-related plans in WBAN. In WBAN medical care applications, unwavering quality is a major concern since distant patient checking manages essential information. In distant patient checking, the information is acknowledged from a confided-in element body. Additionally, distant patient observing includes a few substances when sending detected information to the clinical worker. This correspondence is now and again dependent on a Body–Body Network (BBN), which upholds a few creative applications, including far-off persistent checking, intuitive games, and military uses [
17,
18,
19].
In [
20], the author planned ReTrust (attack-resistant and light-weight trust-the-board) two-level engineering for clinical body-sensor organizations. At the principal level, the trust model is characterized; later, the trust estimations of ReTrust are cultivated. In trust estimation, an alternative assault board framework is examined for various classifications of trust. In addition, the suggested ReTrust is being studied for its security, productivity, and usefulness. Based on the preliminary analysis, it is assumed that the proposed technique extends the network lifetime limit and ensures protection. Be that as it may, it does not have the detail of fundamental organization boundaries. Additionally, the clarification realizes the shortcomings of how the proposed trust-the-board approach further develops unwavering quality. Furthermore, the recommended strategy must be evaluated in the new WBAN environment. Similarly, a Dynamic Trust Evaluation Model (DTEM) for WSNs is proposed in [
21]. To deal with the dynamic weight, the presented model combines an immediate trust approach with a suggestion-based trust method. Moreover, direct trust is determined dependent on the number of trust factors comprising past correspondence history. Meanwhile, the proposed trust will be determined and assessed by the outsider. The creator played out a trust assessment toward the end and expressed that a typical hub will consistently coordinate during correspondence while a noxious hub would not. Through a basic survey of the presented plan, we presumed that a trust model is an effective option in contrast to conventional security systems. It can assess and tackle the hub inside a rowdiness assault, which gives security administration to the upper layers. Notwithstanding, it very well might be a provoking errand to send and deal with the trusted expert in limited WBAN because of a confined climate.
In [
22], researchers proposed a module to take a look at the activities of its neighbor hubs. Aside from this, they looked at whether their exercises were agreeable or nonhelpful. It was inferred that adequate handling and association with sensors are needed to arrive at a steady point. Be that as it may, if the biosensor has a speedy development inside the organization, the proposed system will not perform. Likewise, [
23] proposed a strategy wherein trust is determined, utilizing and examining the neighbor hub’s information-sending conduct. Node Behavioral Strategies Banding Belief Theory into Trust Evaluation (NBBTE) method is used in the proposed scheme to build up trust factors among neighbor hubs. Furthermore, rather than using a basic weighted average, the Dempster–Shafer (D–S) proof hypothesis approach was used to obtain included trust. However, due to the excessive message transmission between neighboring sensor hubs, this strategy is not energy efficient. Authors in [
24] developed a paradigm in which data is divided into three categories: crude information, guided information, and cycle information. As far as distinct hubs can detect information without any additional handling or steering, biosensor essential indicators provide crude data. At whatever point the detected information is shipped off to different hubs, it becomes directed information. Handling implies information translation, such as information combination, information total, or information characterization. In the proposed component, these are related to energy on the off chance that activity by a hub devours the typical force and the impact is matched as expected. However, there are occasions when a basic event requires more effort, which is important for such frameworks to consider, and the proposed solution fails to notice it. Three variables are used to determine trust in [
25]. The first rule is agreeable correspondence, the second is the energy level, and the third is information consistency, which is the opposition to administrative refusal assaults. The main flaw with the proposed idea is the fact that it is unclear how the trust value will indeed be renewed.
In [
26], the authors present a trust model for WSN wherein the trust factor is based on the information’s consistency and agreement. The paper proposes a sophisticated technique for registering a hub with confidence. The presented model has shown to be more effective than different techniques that embrace AI and neural organization-based methodologies. However, the primary disadvantage of the proposed model is that assuming the level of malignant hubs is over half, the model does not function admirably. In [
27], they proposed a vindictive hub-recognition plan named “Boycott Trust”, which recognizes malevolent assaults on WBAN. Boycott-Trust can consider normal practices between the biosensors, i.e., energy, information, and correspondence. Furthermore, the proposed plan utilizes a grouping method to deal with limit delay, energy proficiency, and increment throughput. The described strategy that can be implemented in WBAN in a sophisticated fashion for a long-term, persistent checking framework, with excellent results. In [
28], an issue-mindful trust-assurance calculation (FATD) is presented for Wireless Body Sensor Network (WBSN), in which the hub’s trust is determined by the battery voltage, collector signal strength (RSSI), and hub mobility. Every hub address has trust esteem assigned to it with a notable value between 1 and 1. The proposed computation is a superior solution for trust difficulties and extends the life of the organization. The inventor stated that the suggested work would be tested in a real-world healthcare setting. Notwithstanding, reliance on the battery voltage is not a reasonable way to deal with trust of the executives. Additionally, continuous testing of the proposed calculation with assorted boundaries is required.
Likewise, authors in [
29] attempted to settle the issue of trust by limiting the hubs acting mischievously, with expanded organization lifetime, and kept a trusted and adjusted climate. The creator expressed that the customary cryptographic plans burn through a significant part of the organization’s assets and are additionally convoluted for trust assessment. In this manner, trust and warm, mindful, directing conventions are proposed for trust among hubs to segregate the hubs which get into mischief. Nonetheless, when the traffic load grows, the temperature of some hubs rises, causing WBAN to become corrupted. Authors in [
30] suggested Trust Chain, a security-preserving block-chain approach for edge processing. A component’s trustworthiness for IoT devices can be determined by combining its physical features and personality. This future disposes of actual assaults on IoT gadgets. The principle impediment of the proposed component is that the incorporated worker is utilized for capacity. In addition, the exorbitant trade of messages between the gadget and worker overburdens the organization.
Based on our review of the literature, we concluded that a new strategy is needed to improve the confidence and dependability of WBAN apps. The new strategy is expected to increase trust in WBAN as a tool for remote health monitoring. Furthermore, as the level of trust increases, so does the level of reliability in WBAN.
3. Proposed Methodology
In this section, we will discuss and analyze the trust-management algorithm in the general sense, then propose a binomial distribution-based trust-management algorithm for WBAN-based patient records, as shown in
Figure 2.
3.1. Trust-Management Algorithm
Trust initiation, reputation allocation, trust reputation intelligence gathering, modeling, transmitting, trust derivation, trust choices, and so on, are all part of the EH-WBAN trust-management system. In essence, there are four stages to the trust management system: A flow is a stream of packets from a source to a destination. The term “quality of service” refers to the goal that a flow aspires to achieve. In a connection-oriented network, all packets in a flow are sent in the same sequence. All packets in a connectionless network may take distinct paths. To preserve confidentiality, several access-control approaches can be used for knowledge management. As shown in
Figure 3, the simplest solution is to encrypt all sensitive data before storing, processing, or transmitting it. While data encryption provides a satisfactory level of security, several subtle and difficult concerns must be handled.
Collection denotes the collection of node behaviors and trust/reputation data through node interaction. It is necessary to assure the reliability and trustworthiness of data that have been sensed and collected. In this case, the physical sensing layer should take into account the trustee’s objective attributes.
Modeling the representation of the trust and reputation connection. Ensures that data and routing information are not tampered with by an intermediary or malicious actor while in transit. As a result, any interruption in data transmission must be identified immediately. The discovered data should be handled and analysed in a trustworthy and safe manner while respecting privacy and security.
Transferring entails the indirect transmitting of reputation and transfer with a value of trust. Data should be sent and exchanged safely and securely once they have been discovered and processed. To achieve the goal of data transmission and communication trust, trust-based routing and secure key management are necessary.
Decision consists of two parts: selecting the next hopping node and demanding nodes with low trust values. These approaches provide unified solutions for access control choices and administration by merging the authentication and authorization processes into one action. These models are also known as computational trust models. Measurements, unlike decision models, can be used to quantify trust. They investigate and measure entities and attributes such as reliability, honesty, and integrity, to determine the worth of trust. Different steps of the algorithm are mentioned in
Figure 3.
In WBSN networks, trust is crucial for network construction and making the addition and/or deletion of sensor nodes from a network due to network expansion, as well as the replacement of damaged and unreliable nodes, as simple and transparent as feasible. The cooperative and trusting nature of a WBSN’s nodes is critical to the network’s formation, operation, management, and lifespan, hence node trust is vital. Due to the resource constraints of sensor nodes, standard tools such as cryptographic tools to generate trust proof and establish trust, and typical protocols to exchange and distribute keys, are not available in a WSN. As a result, new and innovative ways to secure communication and the distribution of trust values across nodes are required. WBSN trust has only scraped the surface of recent research, and it remains a contested topic.
Medical record data, which identifies a patient’s identity and health based on personal and demographic information, medical condition history, ongoing therapy, laboratory tests, and radiographic results, is a common requirement of a health-data management system. Medical records, whether in the form of printed documents or digital data, have always been an important part of the development of health-data management systems. Using personal healthcare data, on the other hand, needs a well-defined balance between assurances of personal healthcare-data privacy, and, for example, transparency toward insurance companies. A person’s insurance status should not be jeopardized as a result of new insights regarding genetically personal risk factors for chronic diseases. Furthermore, individual healthcare data must be used to monitor the public’s health state.
3.2. On–Off Attack Model
Internally, the On–Off attack is quite harmful. A compromised node executes both positive and negative behaviors as if it were a normal node in this attack. Nonstationary periodic features appear to be present in these behaviors. In terms of trust managing, the vulnerable node could earn a considerably higher trust level in a short amount of time by regularly executing good behaviors. Following that, it engages in undesirable behavior regularly over a significant period, lowering its trust worth. It restarts good behavior when the trust value in itself falls to a particular level. As a result, the trust value rises quickly but falls slowly.
3.3. Binomial Distribution-Based Trust-Management Algorithm
The binomial distribution is created by repeating n Bernoulli trials. The completion or failure of each Bernoulli trial is treated in EH-WBAN as the success or failure of the interaction between the nodes. The probability distribution functions of the binomial distribution are then used to determine the node’s reputation. To gain the new trust value, node-to-node interaction is used to update the reputation. In terms of network node contact and collaboration, the binomial distribution statement is more direct. It is appropriate for assessing node behavior in the resource-constrained EH-WBAN [
31] due to its low computing complexity.
3.3.1. Binomial Distribution
The binomial distribution is a type of probability distribution. The chance of k successes in n experiments is represented by Bin (n, k). It can be written as:
where, p will be the probability of successes, and
is shown as follows:
When two nodes interact, there are two possible outcomes: cooperation and noncooperation. As a result, the binomial distribution can be used to simulate node interaction. In this case, we assume that the nodes interact a+b times, where a represents the number of times the nodes cooperate, b represents the number of times the nodes do not cooperate, and p represents the probability of cooperation. As a result, the binomial distribution can be used to calculate the probability distribution of node reputation p.
3.3.2. Reputation Simulating
The reputation of node i to node j is expressed as:
3.3.3. Trust Initializing
At the point when trust esteem is instated, it is, for the most part, accepted that all hubs have a similar beginning trust esteem and that all hubs are acceptable hubs (that is, let all hubs’ trust esteem be the most noteworthy). The benefit of this supposition will be that the organization should not be introduced; in any case, the disservice is that it permits as well as supports a malignant hub to produce another ID and lease the organization with the standing. On the other hand, if we consider that all hubs are vindictive, the trustworthiness of all hubs is the lowest. This strategy can alleviate the problem of faked IDs, however, if the network’s original trust level is 0 then these nodes would not trust one another, and it takes a lot of time for the network to create trust before it can function correctly.
When we let a = b = 0 and adapt those two approaches, we expect the hub’s trust esteem to be 0.5 (because the denominator becomes zero when a = b = 0 and we accept a trust worth of 0.5 for a = b = 0). The trust esteem is 0.5 if both a and b are 1, which equals 100, as shown in Formula (7). Despite this, there is a clear distinction between the two situations. If the upsides are few, it demonstrates that there are not many connections, and the acquired trust esteems are not exact enough. Conversely, if the upsides of a and b are huge, the heaviness of authentic trust data will be expanded, which will significantly affect the ensuing trust assessment. The prerequisite of intermingling time for the trust worth will grow; this might influence the typical activity of the organization. In this way, the starting fittings of a and b ought to be chosen.
3.3.4. Reputation Updating
Concerning node j, we presume that node has some form of Rij reputation. The interaction between node i and node j should be increased by (r + s) times. The figures r and s indicate how many people cooperate and how many do not. As a result, there are currently (a + b + r + s) interactions. Node j’s most recent reputation, Rij, is:
3.3.5. Aging
The newly discovered data must be given more weight. As a result, an aging-weighted parameter is added.
Wage signifies the weight loss as one gets older, and the range is (0, 1). The aging weight is responsible for ensuring that all nodes always work together. This setting effectively prevents a rogue node from selecting the cooperative policy and subsequently damaging the network using the initial reputation. This is because, with the right aging weight, historical reputation data could be steadily lowered, and nodes must always collaborate to retain a positive reputation.
The below Algorithm 1 is an improvised version of the previous existing algorithm viz BDTMS [
32].
| Algorithm 1: An Algorithm for IBDTMS
|
- 1
The number of successes in a sequence of Bernoulli trials has a binomial distribution. - 2
Characteristics. - 3
Parameters:
- i
= Probability of success in a trial, . - ii
= Number of trials; - iii
must be a positive integer, Range: - iv
pdf: - v
Mean: - vi
Variance:
- 4
. - 5
- 6
. - 7
GenerationGenerate The number of RNs that are less than is . - 8
Composition: For small p; Generate geometric random numbers . - 9
If the sum of geometric RNs so far is less than or equal to, go back to the previous step. Otherwise, return the number of RNs generated minus one. - 10
For each binomial variate, generate a variate ,and search the array to find so that ; return
|
3.4. Cryptography Solution for Privacy Preservation and Reliability
In this part of the article, WBAN is used to create a lightweight data-encryption strategy for remote medical systems. The privacy-preserving cryptographic mechanism from our earlier study [
33] is thought to be applied here. This hybrid solution combines the session key alongside the trust value created in the previous section to secure anonymity.
The protection issue is a huge test in far-off medical care observing WBAN. Security conservation of medical services is to keep up with trust based the dependable meeting of basic information. As a result, the proposed cryptographic structure aims to provide the best possible protection. The remote-healthcare WBAN protection solution ensured safe and trust-based exchanges across hubs by leveraging meeting key size (128 pieces). The medical service’s client receives a package containing the content of critical signs, hub ID, as well as trust regard. This is also annexed to the gateway, which adds to its enigmatic value. The encoded message is then sent to the clinical worker, who is checked for respectability and granted access based upon trust esteemed by the medical care provider. Later in the safety meeting, helpful information is conveyed. The trust connection is finished at the worker’s side following a particular time, at which point no requirement arises for the organization of information movement.
Figure 4 portrays the cryptographic answer for medical service clients in far-off, quiet observing of WBAN. The medical service client directs solicitation-agreeable trust esteem across the doorway to the clinical worker. Then, the healthcare services supplier verifies their personality and the protected meeting is set up for distant medical service clients. Then, at that point, the meeting is dynamic for a particular hour-long time period. After achieving the movement of information between medical service clients and medical care suppliers, the solid meeting can be finished at whatever point required. This cycle is again started at whatever point another solicitation is conducted for correspondence.
4. Performance Evaluation and Analysis
Here, an assessment of the trust-based energy-productive far-off persistent checking plan utilizing an agreeable system is presented. During the reproduction phase, the situation of the presented work is exhibited to assess its presentation. Following the depiction of the organizational situation, the framework approvals are performed, and the yielded outcomes are analyzed. The analyses are completed utilizing a MATLAB test system to investigate the presentation of the proposed instrument. MATLAB is a re-enactment stage appropriate for low-controlled remote organization situations, for example, sensor organizations. The essential elements of this experimental investigation were specified using current and developed model techniques to deliver improved performance, as shown in the previous parts. We used DTEM, FATD, Trust Chain, IDCA, and the proposed algorithm of IBDTMS to apply several utilization implementations.
5. Results and Discussions
Table 1 provides an overview of a wide range of performance metrics of several parameters analyzed and compared to the literature. A comparison of prior metrics such as accuracy, service delivery ratio, throughput, average delay, energy cost, privacy, confidentiality, and scalability are compared with existing and proposed IBDTMS algorithms.
Table 1 shows the distribution of analyzed metrics, which provides an overall picture of the popularity trend for certain measurements. Overall parameters are critical for metrics, and they are the most commonly studied metrics. Analyzer-related measurements, which are essentially statistical metrics, are only considered in a few instances. As a result, these qualities are important to include when determining total system performance. Additionally,
Figure 5a,b and
Figure 6a,b show graphical representation of accuracy, service delivery ratio, throughput, and energy cost.
Figure 7 depicts comparative analysis of confidentiality in an existing and proposed algorithm. These figures show the performance of this proposed work compared to existing works. Furthermore, these figures show a better performance evaluation of the proposed work.
6. Conclusions and Future Scope
To enable real-time transfer, EH-WBAN can accomplish less delayed data collecting. Meanwhile, stronger management laws have been suggested as a way to improve future security. It is, however, vital to comprehend how to properly handle internal attacks, as well as how to distinguish between hostile attack behavior and various interventions. This research investigates the malicious behavior of the on–off attack and the characteristics of the wireless channel state during unrestricted operation. We propose an advanced bilingual distribution-based trust-management system (BDTMS) for EH-WBAN. In the simulation results, BDTMS has a faster detection period and larger accuracy than the conventional confidence program. Furthermore, BDTMS can defend against inadequate mouth attacks. In medical applications, WBAN allows for continuous monitoring of the patient, allowing for early detection of aberrant conditions and resulting in considerable improvements in quality of life. Patients can participate in normal activities rather than being housebound or dependent on neighboring specialized medical services with basic vital sign monitoring, such as heart rate, SpO2, and so on. The conclusion is that research on this unique technology is essential for better resource utilization. The results of this study can be utilized to plan future research projects. The approach employed in this paper can be used to model and analyze major metrics, continue conceptual research into the aspects of the additional metrics mentioned in this work, namely extended metrics, composite metrics, and hybrid sets of metrics.