Risk Analysis and Evaluation of Nuclear Security Radiation Events in Spent Fuel Reprocessing Plants
Abstract
:1. Introduction
2. Determine the Basic Event Probability
2.1. Construct an Expert Scoring System
2.2. Calculation of Probability of Occurrence of Basic Events
3. Construct FTA for Nuclear Security Radiation Events
3.1. Structure Function of Fault Tree
3.2. Importance Analysis of the Fault Tree
4. Construct a Fuzzy Comprehensive Evaluation System
4.1. Construct Factor Set
4.2. Construct Weight Set
4.3. Construct Evaluation Set
4.4. Single Factor Fuzzy Evaluation
4.5. Fuzzy Comprehensive Evaluation
5. Probability and Mathematical Statistical Evaluation
6. Comparative Analysis of Results
7. Conclusions
- (1)
- The probability of occurrence of basic events is difficult to obtain and the accuracy is low, the expert scoring method can be adopted to avoid the error by setting the weight corresponding to the qualifications of experts. The method of frequency instead of probability can obtain the probability of basic events.
- (2)
- The fuzzy comprehensive evaluation method and the combination of probabilistic-mathematical statistics are used to obtain the hazards of each evaluation unit and plant area, which provides theoretical support for nuclear safety operations and emergency prevention of spent fuel reprocessing plants.
- (3)
- Through the fault tree and risk analysis, it is concluded that the computer nuclear security incident is the most dangerous of the eight types of nuclear security basic events, so it is necessary to take more precautions against the occurrence of such accidents in daily operation. Through the fuzzy comprehensive evaluation and the calculation method of probabilistic-mathematical statistics, it is concluded that the tail-end transformation plant in the main process area has the highest danger, and the dormitory unit in the pre-plant area of the factory has the lowest danger. The method of adding and taking the average value shows that the main process area is the most dangerous, the pre-plant area is the least dangerous, and there is a relationship of about 1.5 times, so a considerable proportion of manpower and material resources should be invested in the work to achieve the most economical and safe preventive effect.
- (4)
- In this paper, the expert scoring method is used to obtain the probability of eight basic events, which will make the subjective factors stronger. In the process of establishing the model, the fuzzy comprehensive evaluation method is inevitably affected by subjective factors in terms of index selection, evaluation criteria establishment and weight determination, which has certain limitations. Therefore, our future work will mainly focus on how to correctly handle the impact of subjective and objective factors on the results, and reduce the impact of subjectivity as much as possible.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, F.; Wang, J.; Wang, J.; Li, Y.; Hu, L.; Wu, Y. Risk monitor risk angel for risk-informed applications in nuclear power plants. Ann. Nucl. Energy 2016, 91, 142–147. [Google Scholar] [CrossRef]
- Tromm, W. Nuclear energy research in Germany 2010. Research centers. Atw. Int. Z. Kernenerg. 2011, 56, 412–418. [Google Scholar]
- Ibrahim, M.; Hamdan, S.N.; Haris, M.F.; Ismail, S.; Sulaiman, M.S.; Aris, S.M.N.; Hasan, M.H.B.; Aslan, M.D.A.; Ghani, N.F.A.; Hamid, A.H.A.; et al. Big data analytics nuclear security framework. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1106, 012026. [Google Scholar] [CrossRef]
- Majewski, M.; Nestler, K.; Veit, D.A.; Diekmeyer, B.; Waldeck, S.; Port, M.; Becker, B.V. Detection of embedded low-level radioactive shrapnel after the explosion of a radiological dispersal device in radiological emergency imaging. Health Phys. 2020, 119, 95–100. [Google Scholar] [CrossRef] [PubMed]
- Cho, H.S.; Woo, T.H. Cyber security in nuclear industry—Analytic study from the terror incident in nuclear power plants (NPPs). Ann. Nucl. Energy 2017, 99, 47–53. [Google Scholar] [CrossRef]
- Moo, J.H.; Chirayath, S.S.; Cho, S.G. Physical protection system vulnerability assessment of a small nuclear research reactor due to TNT-shaped charge impact on its reinforced concrete wall. Nucl. Eng. Technol. 2022, 54, 2135–2146. [Google Scholar] [CrossRef]
- Tao, L.; Wang, J.; Long, P.; Wang, D.; Wang, F.; Zhou, B.; Chen, J. Probabilistic safety assessment method for spent nuclear fuel road transportation. Ann. Nucl. Energy 2020, 137, 107043. [Google Scholar] [CrossRef]
- Ni, S.; Zou, S.; Chen, J. Evolutionary Game Model of Internal Threats to Nuclear Security in Spent Fuel Reprocessing Plants Based on RDEU Theory. Sustainability 2022, 14, 2163. [Google Scholar] [CrossRef]
- Solodov, A.; Williams, A.; Al Hanaei, S.; Goddard, B. Analyzing the threat of unmanned aerial vehicles (UAV) to nuclear facilities. Secur. J. 2018, 31, 305–324. [Google Scholar] [CrossRef]
- Al Hamrashdi, H.; Monk, S.D.; Cheneler, D. Passive gamma-ray and neutron imaging systems for national security and nuclear non-proliferation in controlled and uncontrolled detection areas: Review of past and current status. Sensors 2019, 19, 2638. [Google Scholar] [CrossRef] [Green Version]
- Busch, N. Risks of Nuclear Terror: Vulnerabilities to Theft and Sabotage at Nuclear Weapons Facilities. Contemp. Secur. Policy 2002, 23, 19–60. [Google Scholar] [CrossRef]
- Li, R.R. Application of Risk Assessment Grading Method in Accident Analysis of Nuclear Fuel Reprocessing Plant; University of South China: Hengyang, China, 2018. [Google Scholar]
- Sun, M.; Zheng, W.X.; Duan, X.B. Research on Deep Coal Seam Mining Floor Starta Water Bursting Influenced Factors Based on Analytic Hierachy Process. Appl. Mech. Mater. 2014, 608–609, 737–741. [Google Scholar] [CrossRef]
- Jin, H.; Hu, Z.; Li, K.; Chu, M.; Zou, G.; Yu, G.; Zhang, J. Study on How Expert and Novice Pilots Can Distribute Their Visual Attention to Improve Flight Performance. IEEE Access 2021, 9, 44757–44769. [Google Scholar] [CrossRef]
- Gavrilyuk, V.I.; Drapey, S.S.; Kaydyk, B.V.; Kirischuck, V.I.; Parkhomenko, V.V.; Romanova, O.P.; Samsonenko, A.V.; Katunin, E.I.; Boyko, A.V. Nuclear security risks in Ukraine< TITLE lang=""> Piɜiki y cϕepi ϕiɜiчнoї yaдepнoї δeɜпeki Уkpaїнi. Nucl. Phys. At. Energy 2021, 22, 409–414. [Google Scholar]
- Wang, J.; Lin, M. Seismic probabilistic risk analysis and application in a nuclear power plant. Nucl. Technol. 2018, 203, 221–231. [Google Scholar] [CrossRef]
- Fahmy, R.A.; Gomaa, R.I. Dynamic fault tree analysis of auxiliary feedwater system in a pressurized water reactor. Kerntechnik 2021, 86, 164–172. [Google Scholar] [CrossRef]
- Hermansyah, H.; Kumaraningrum, A.R.; Purba, J.H.; Yohda, M. Safety analysis technique for system with limited data: Case study of the multipurpose research reactor in Indonesia. Energies 2020, 13, 1975. [Google Scholar] [CrossRef] [Green Version]
- Hu, Y.; Wu, L.; Pan, X.; Wang, Z.; Xu, X. Comprehensive evaluation of cloud manufacturing service based on fuzzy theory. Int. J. Fuzzy Syst. 2021, 23, 1755–1764. [Google Scholar] [CrossRef]
- Purba, J.H.; Tjahyani, D.T.S.; Widodo, S.; Ekariansyah, A.S. Fuzzy probability based event tree analysis for calculating core damage frequency in nuclear power plant probabilistic safety assessment. Prog. Nucl. Energy 2020, 125, 103376. [Google Scholar] [CrossRef]
- Aghimien, D.O.; Aigbavboa, C.; Edwards, D.J.; Mahamadu, A.M.; Olomolaiye, P.; Nash, H.; Onyia, M. A fuzzy synthetic evaluation of the challenges of smart city development in developing countries. Smart Sustain. Built Environ. 2020, 11, 405–421. [Google Scholar] [CrossRef]
- Oppong, G.D.; Chan, A.P.; Ameyaw, E.E.; Frimpong, S.; Dansoh, A. Fuzzy evaluation of the factors contributing to the success of external stakeholder management in construction. J. Constr. Eng. Manag. 2021, 147, 04021142. [Google Scholar] [CrossRef]
- Yucesan, M.; Gul, M. Hospital service quality evaluation: An integrated model based on Pythagorean fuzzy AHP and fuzzy TOPSIS. Soft Comput. 2020, 24, 3237–3255. [Google Scholar] [CrossRef]
- Vivek, K.; Subbarao, K.V.; Routray, W.; Kamini, N.R.; Dash, K.K. Application of fuzzy logic in sensory evaluation of food products: A comprehensive study. Food Bioprocess Technol. 2020, 13, 1–29. [Google Scholar] [CrossRef]
- Robati, M.; Rezaei, F. Evaluation and ranking of urban sustainability based on sustainability assessment by fuzzy evaluation model. Int. J. Environ. Sci. Technol. 2022, 19, 625–650. [Google Scholar] [CrossRef]
- Li, W.; Liang, W.; Zhang, L.; Tang, Q. Performance assessment system of health, safety and environment based on experts’ weights and fuzzy comprehensive evaluation. J. Loss Prev. Process Ind. 2015, 35, 95–103. [Google Scholar] [CrossRef]
- Xi, J.; Zhao, Y.; Ding, T.; Tian, J.; Li, L. Analysis Model of Risk Factors of Urban Bus Operation Based on FTA-CLR. Adv. Civ. Eng. 2021, 2021, 6657786. [Google Scholar] [CrossRef]

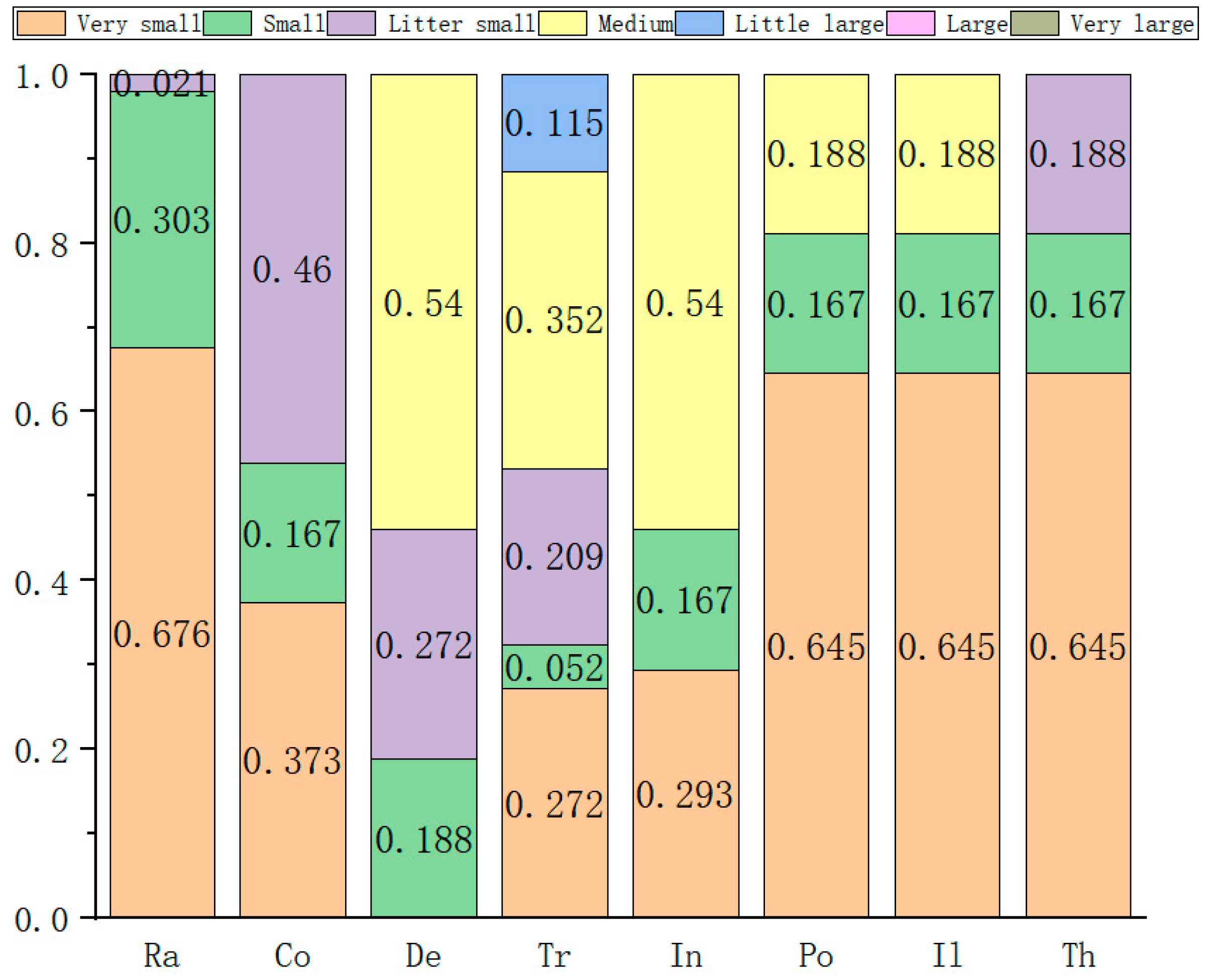
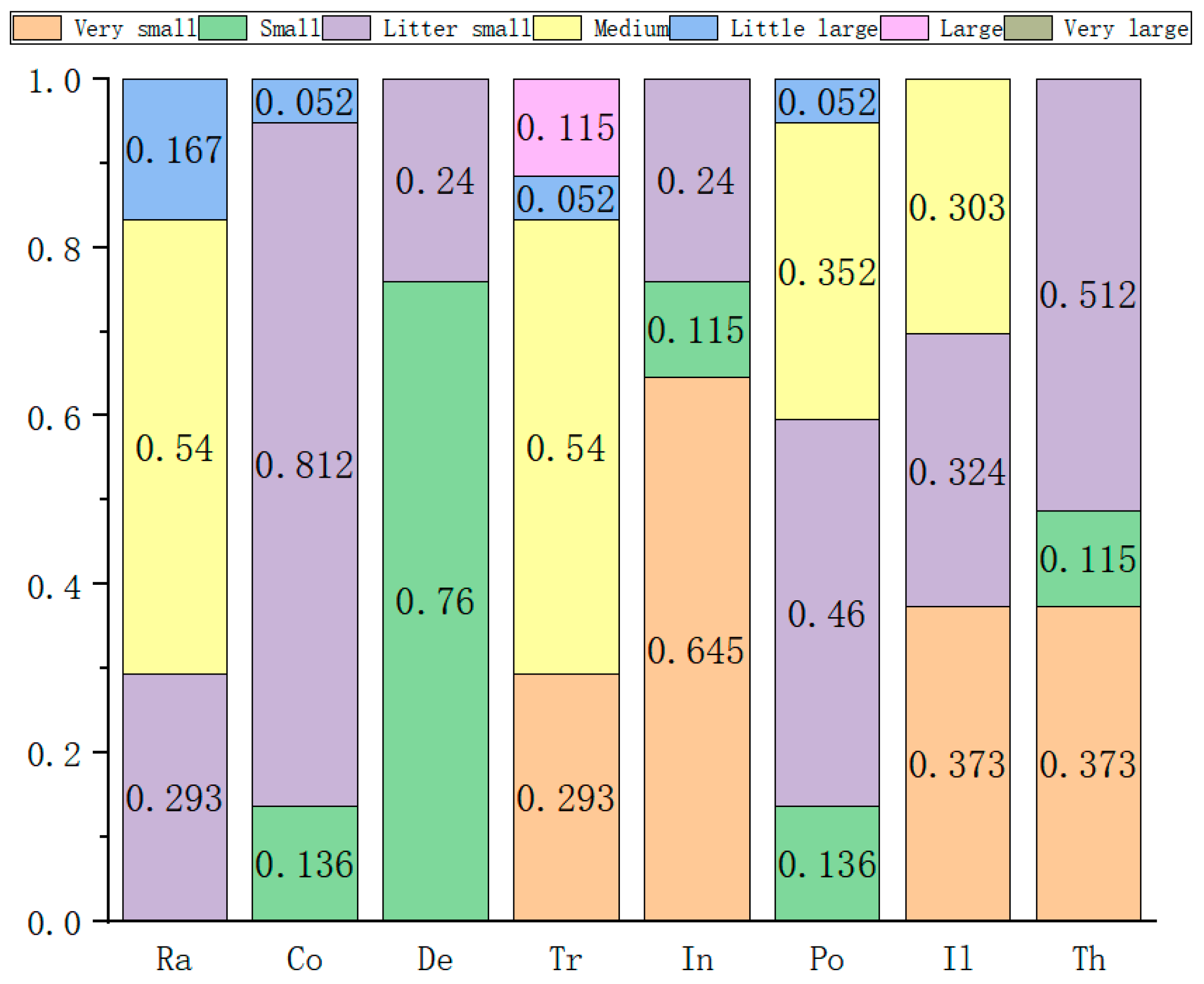
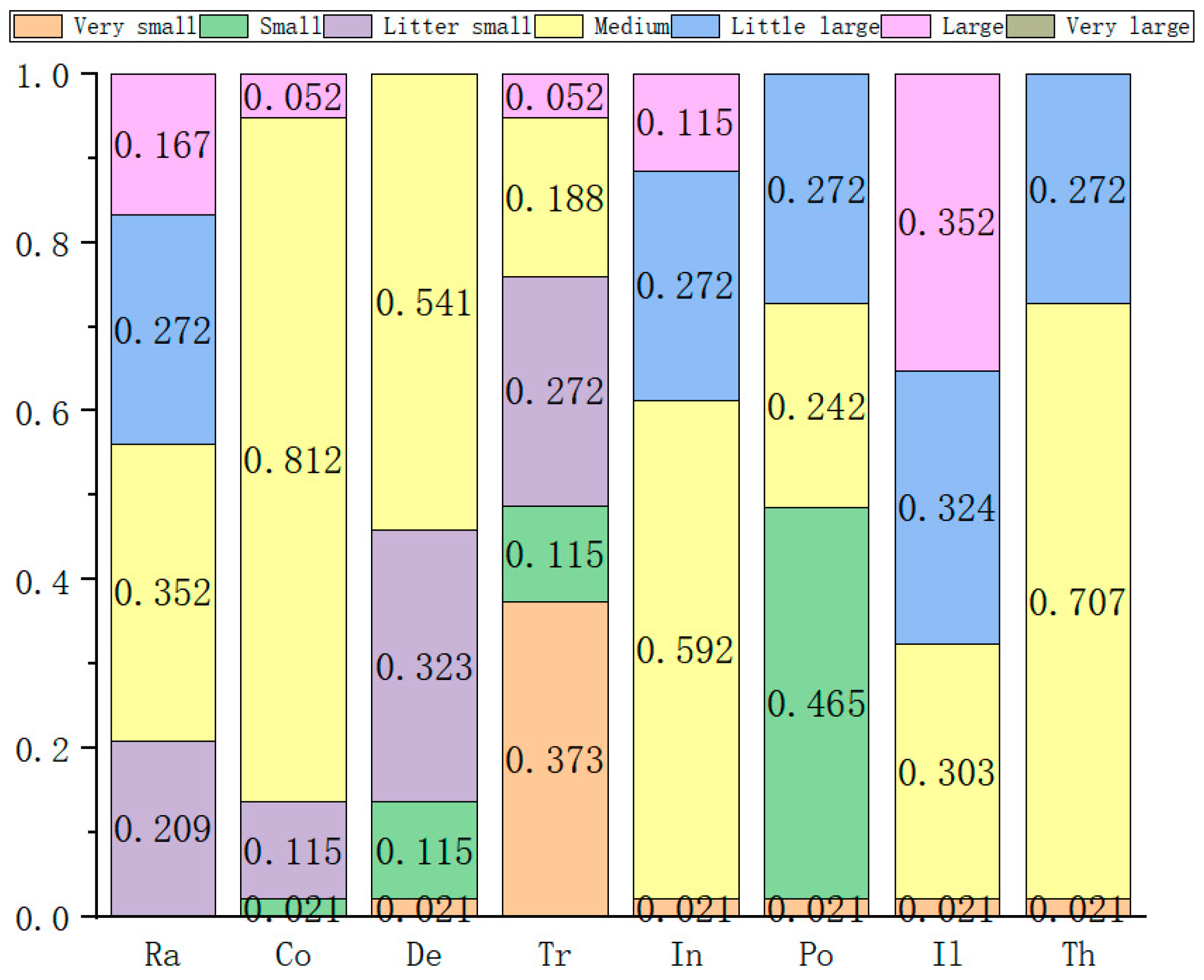
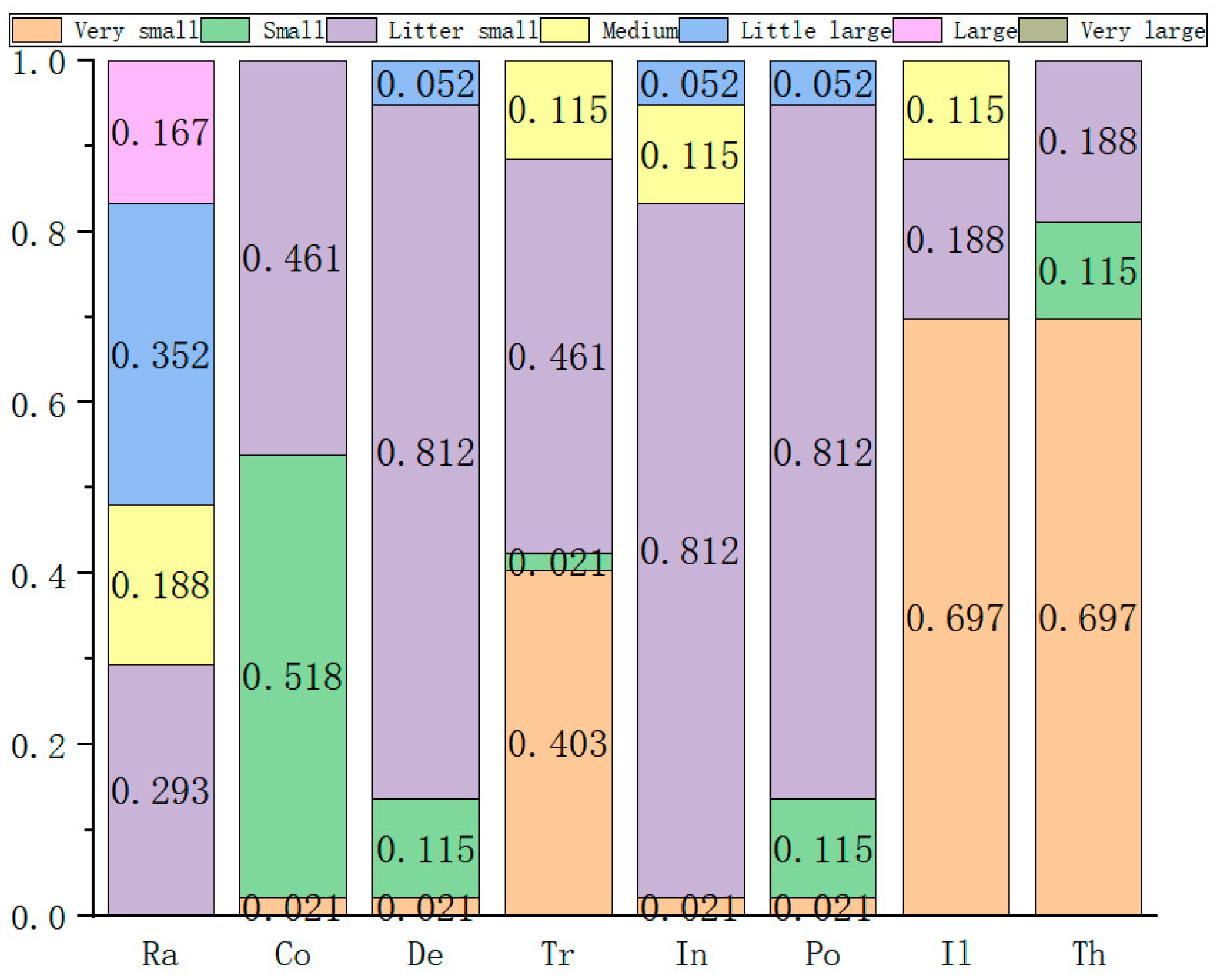
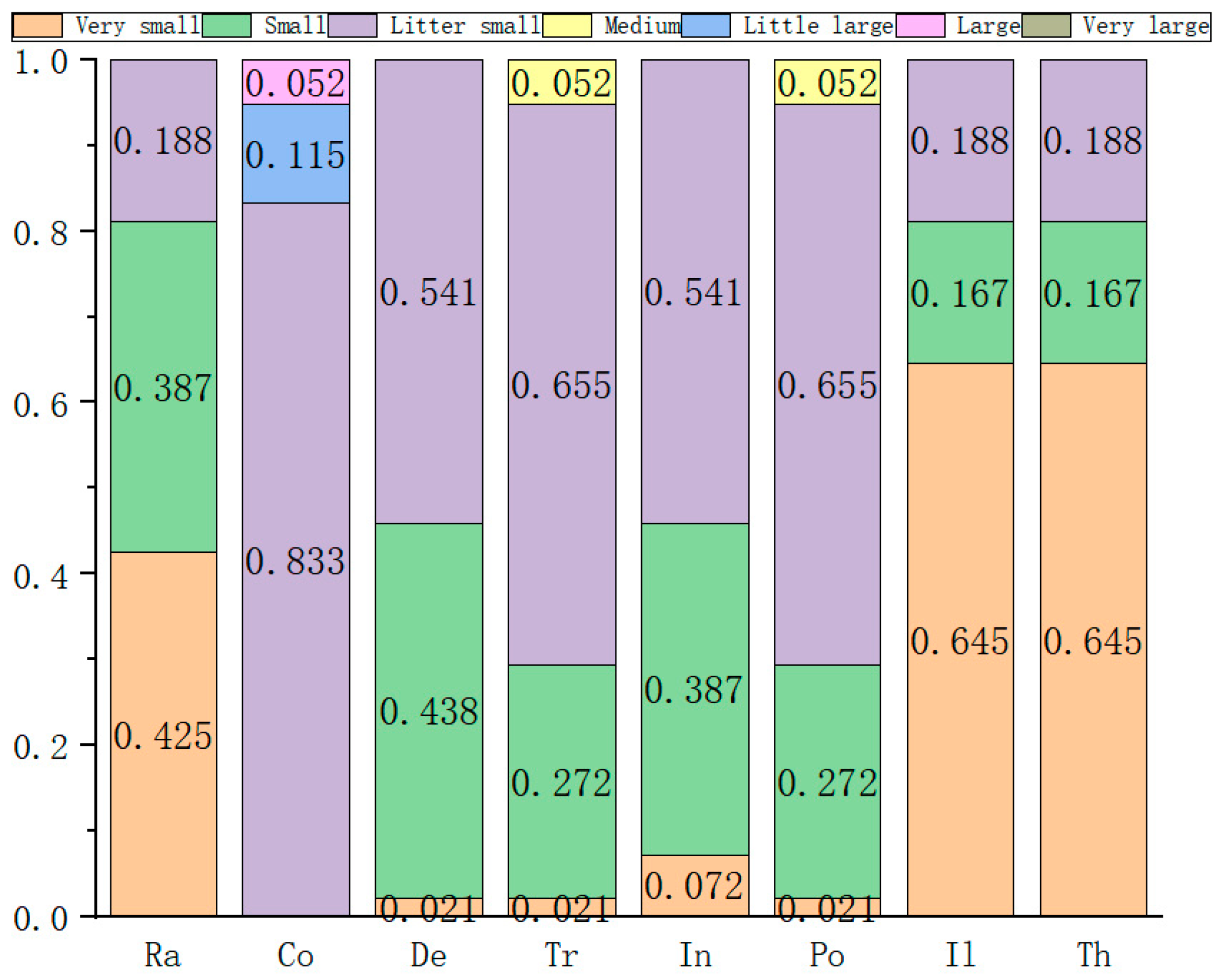

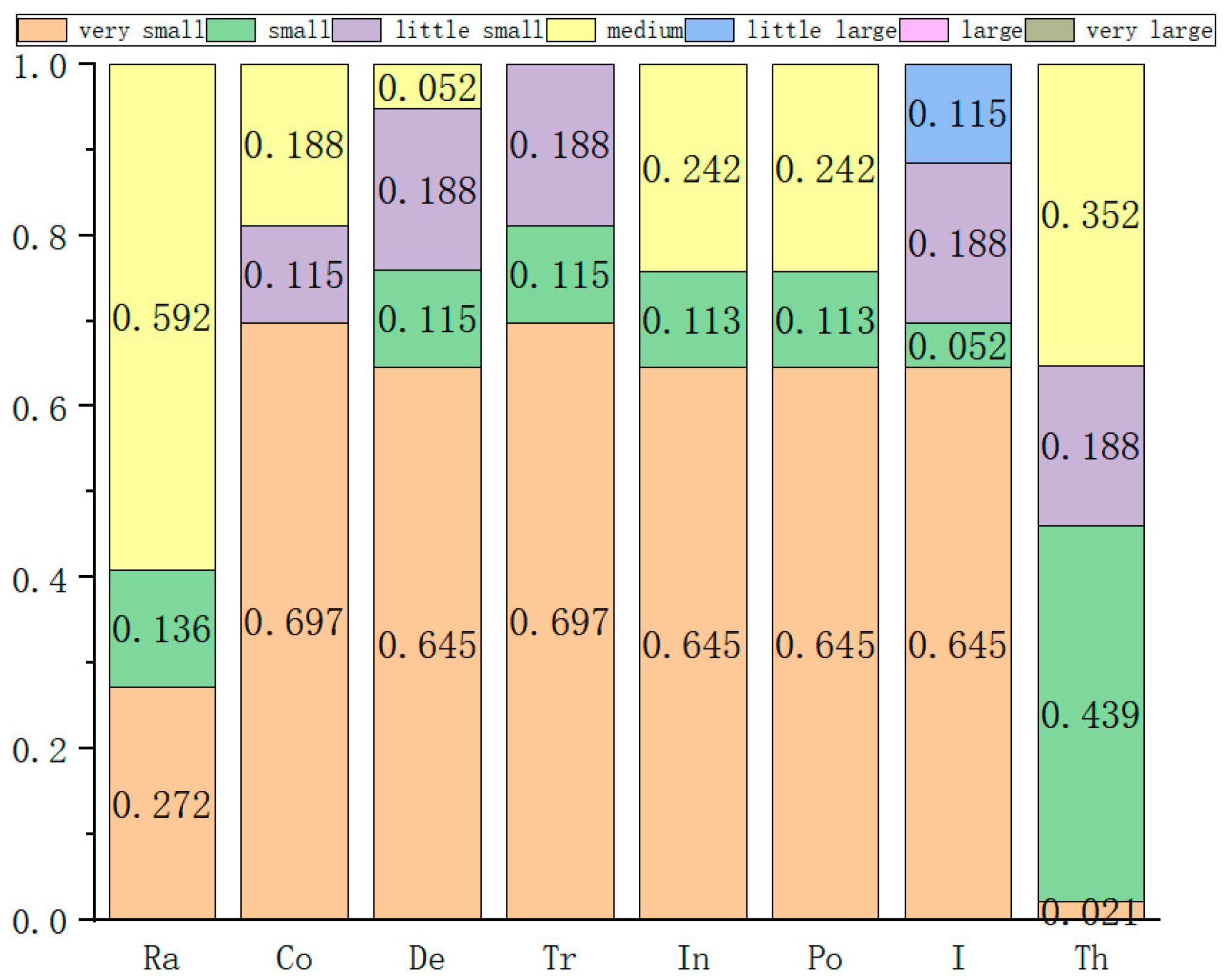
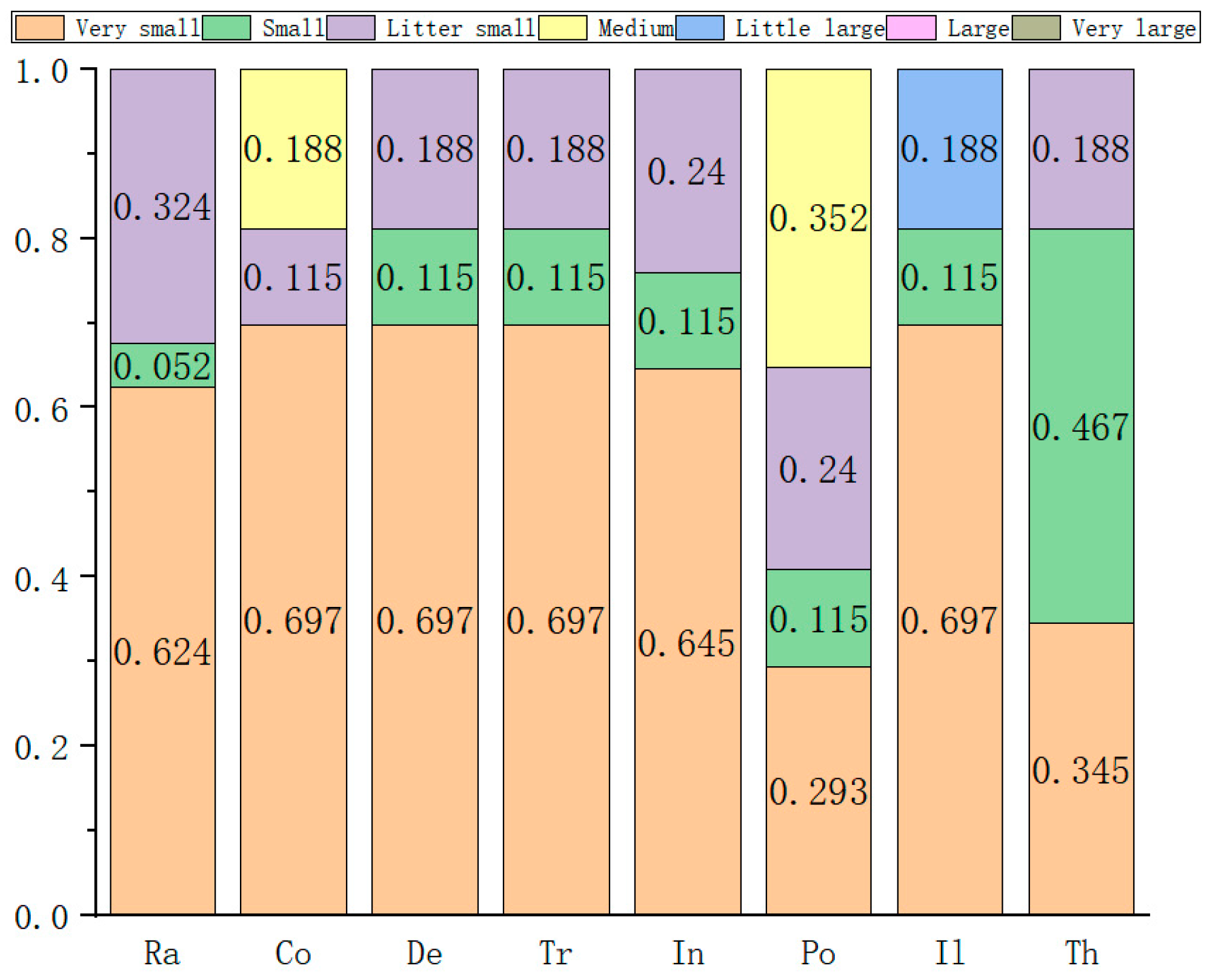
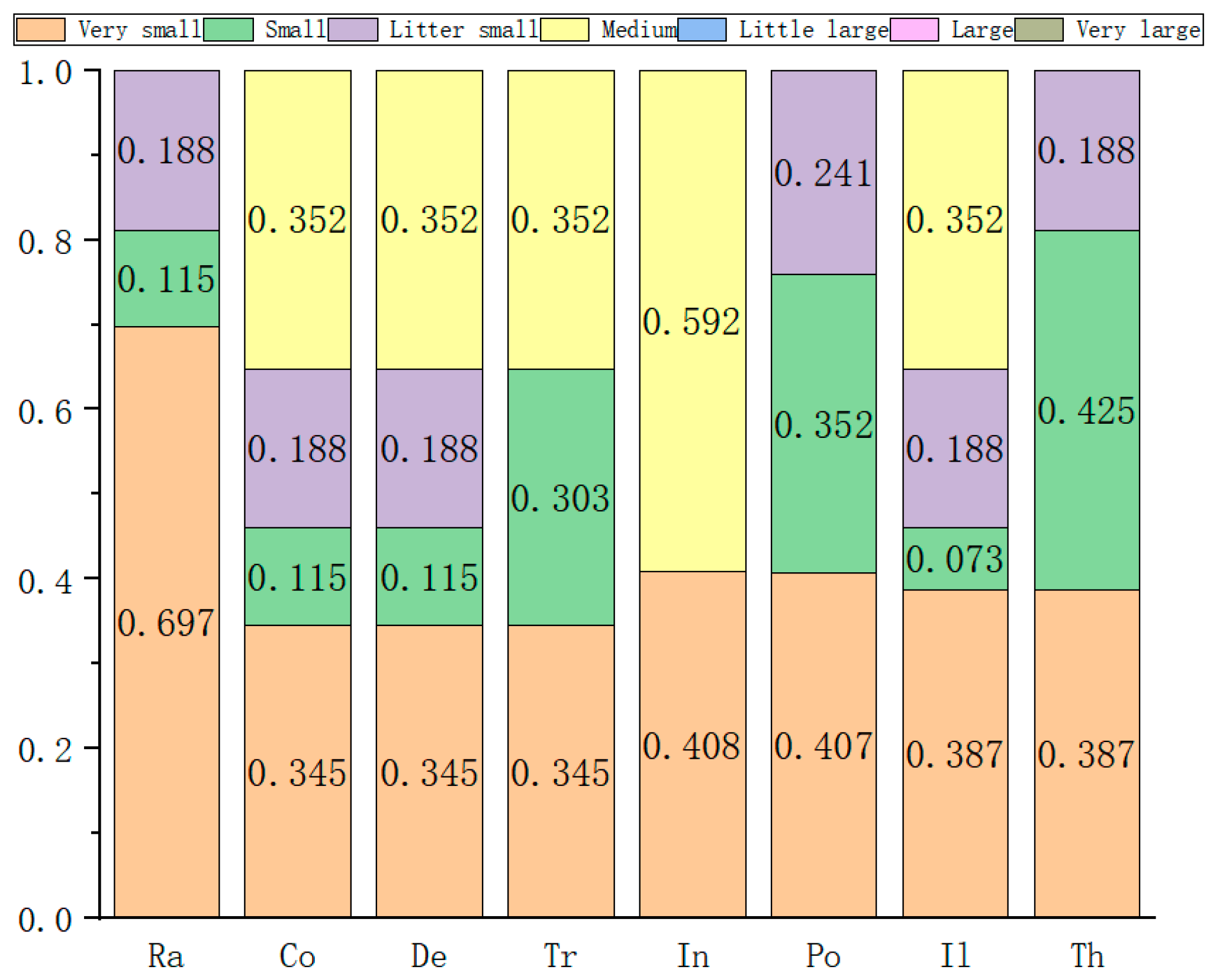
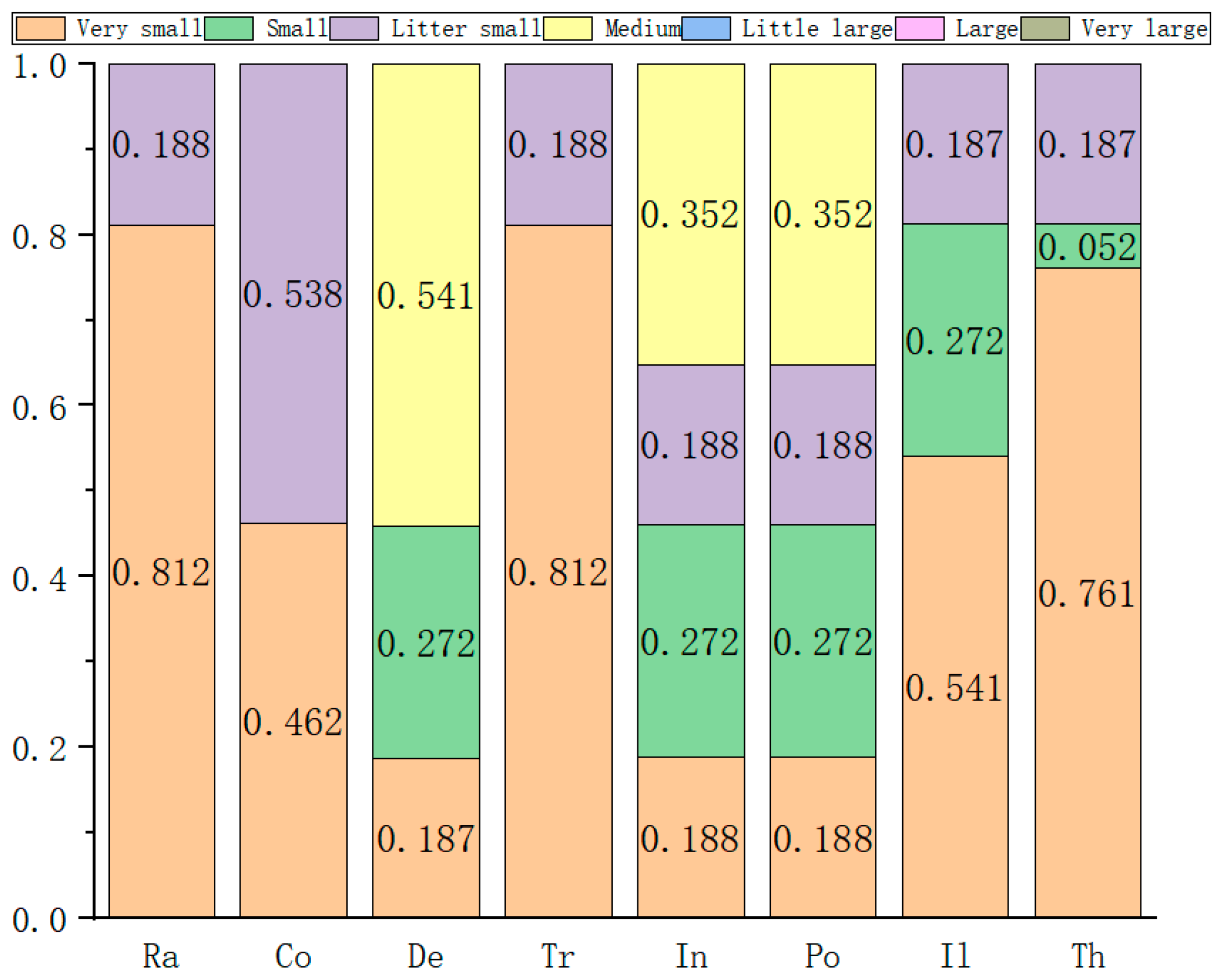
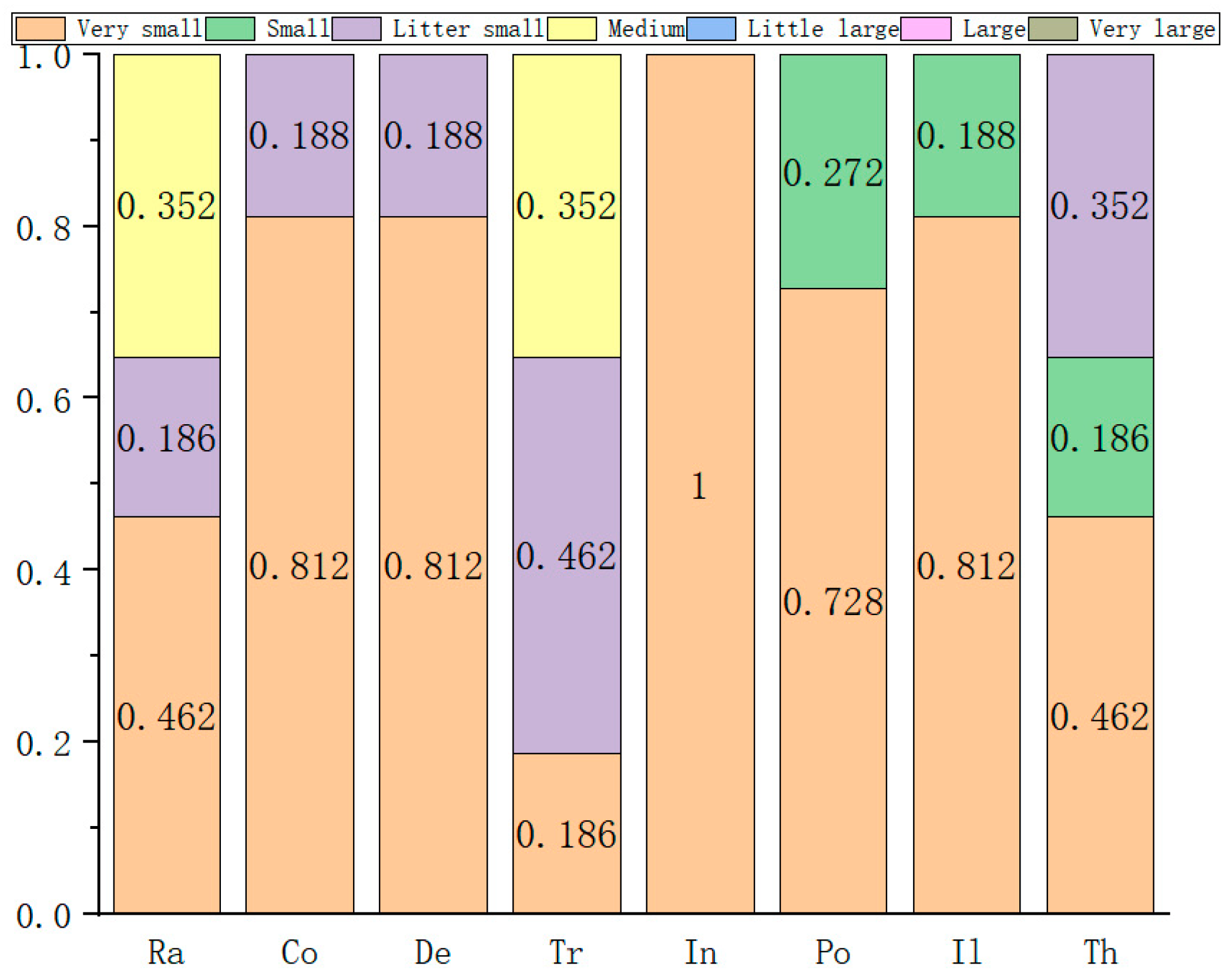
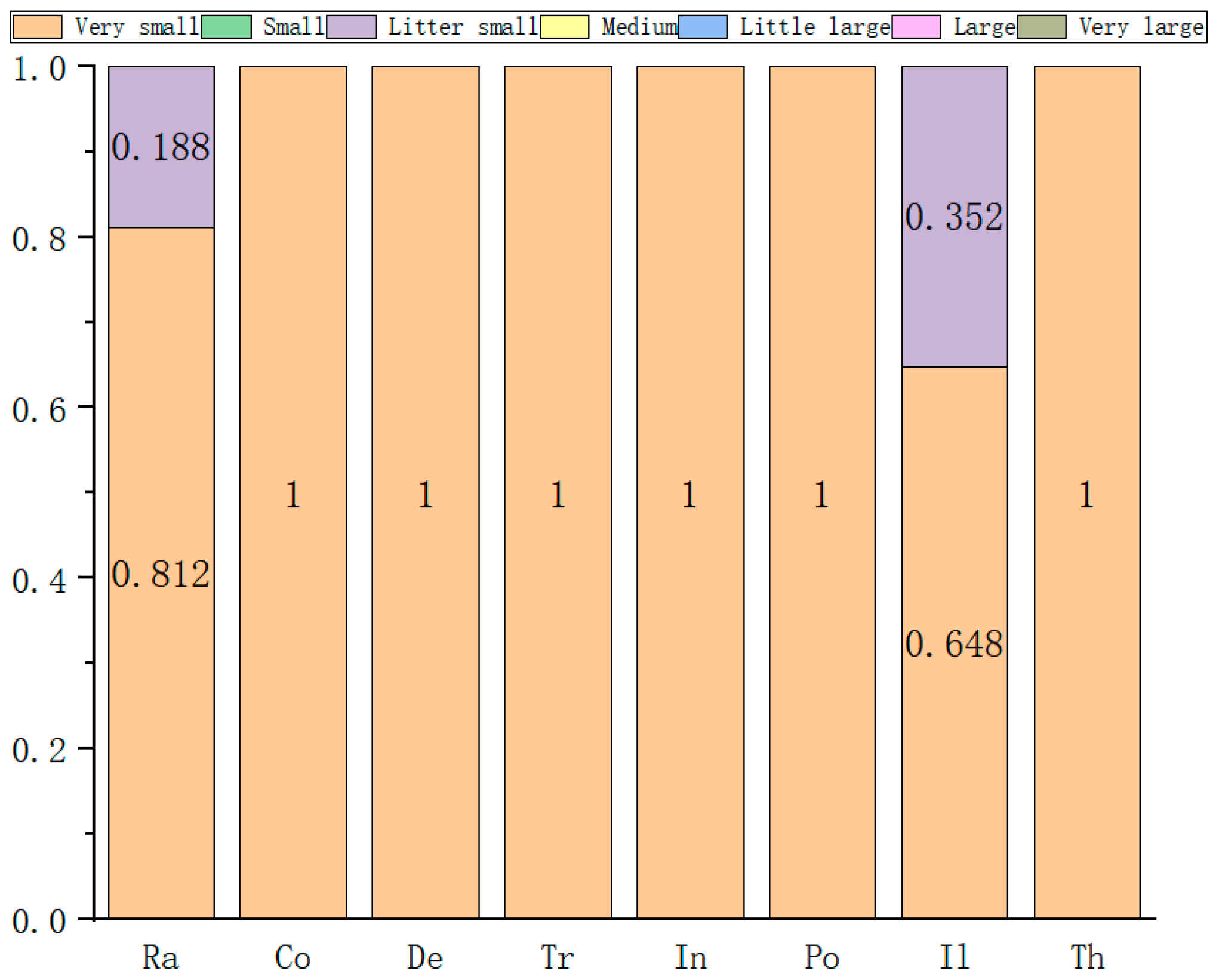
| Serial Number/ Group | Experts | Number of People | Qualification | Length of Service | Record of Formal Schooling | Total | The Weight |
|---|---|---|---|---|---|---|---|
| 1 | Safety Engineer | 9 | 5 (Senior Engineer) | 5 (30 to 40 years) | 5 (PhD students) | 15 | 0.115 |
| 2 | Safety Engineer | 8 | 5 (Senior Engineer) | 4 (20 to 30 years) | 4 (Master’s students) | 13 | 0.352 |
| 3 | Strategic Planner | 6 | 4 (Researcher) | 3 (10 to 20 years) | 5 (PhD students) | 12 | 0.272 |
| 4 | Professor | 4 | 4 (Associate Professor) | 2 (5 to 10 years) | 5 (PhD students) | 11 | 0.188 |
| 5 | Safety Engineer | 2 | 3 (Assistant Engineer) | 2 (5 to 10 years) | 5 (PhD students) | 10 | 0.021 |
| 6 | Safety Engineer | 1 | 3 (Assistant Engineer) | 1 (0 to 5 years) | 4 (Master’s students) | 8 | 0.052 |
| The Serial Number | The Weight | Very Small | Small | Slightly Small | Medium | Somewhat Large | Large | Very Large |
|---|---|---|---|---|---|---|---|---|
| 1 | 0.115 | 3 | 4 | 1 | 0 | 1 | 3 | 0 |
| 2 | 0.352 | 7 | 0 | 0 | 4 | 1 | 0 | 0 |
| 3 | 0.272 | 7 | 2 | 2 | 0 | 1 | 0 | 0 |
| 4 | 0.188 | 0 | 1 | 7 | 4 | 0 | 0 | 0 |
| 5 | 0.021 | 5 | 1 | 6 | 0 | 0 | 0 | 0 |
| 6 | 0.052 | 6 | 1 | 0 | 1 | 1 | 3 | 0 |
| A total of | 5.130 | 1.537 | 1.101 | 2.212 | 0.052 | 0.501 | 0 | |
| The normalized | 0.455 | 0.136 | 0.098 | 0.196 | 0.070 | 0.045 | 0 | |
| 1 − P | 0.545 | 0.864 | 0.902 | 0.804 | 0.930 | 0.955 | 1 |
| Event Number | The Name of the Event | Probability of Occurrence | Normalized Results |
|---|---|---|---|
| X1 | Radioactive dispersal device | 0.697 | 0.12 |
| X2 | Computer nuclear security | 0.706 | 0.13 |
| X3 | Destruction of nuclear facilities | 0.690 | 0.12 |
| X4 | Transportation nuclear security | 0.707 | 0.13 |
| X5 | Internal threat | 0.702 | 0.12 |
| X6 | Potential threat | 0.687 | 0.12 |
| X7 | Illegal transfer | 0.721 | 0.13 |
| X8 | Theft | 0.709 | 0.13 |
| Number | Incident | Number | Incident |
|---|---|---|---|
| T | Nuclear security radiation incident | M10 | Support equipment failure |
| M1 | Radioactive release event | M11 | Lose |
| M2 | Emergency failure | X1 | Radioactive dispersal device |
| M3 | Leakage of high level of waste liquid | X2 | Computer nuclear security |
| M4 | Container leak | X3 | Destruction of nuclear facilities |
| M5 | Transit system leakage | X4 | Transportation nuclear security |
| M6 | Overfeeding | X5 | Internal threat |
| M7 | Auxiliary device failure | X6 | Potential threat |
| M8 | Monitoring equipment failure | X7 | Illegal transfer |
| M9 | Test instrument failure | X8 | Theft |
| Factors | The Weight | |
|---|---|---|
| U1 | Radioactive dispersal device | 0.12 |
| U2 | Computer nuclear security | 0.13 |
| U3 | Destruction nuclear facilities | 0.12 |
| U4 | Transportation nuclear security | 0.13 |
| U5 | Internal threat | 0.12 |
| U6 | Potential threat | 0.12 |
| U7 | Illegal transfer | 0.13 |
| U8 | Theft | 0.13 |
| The Evaluation Unit | Spent Fuel Pool | Extraction Process Plant | Tail-End Conversion Plant | Waste Liquid Purification Workshop | Solidification Workshop | Discharge Workshop |
|---|---|---|---|---|---|---|
| The calculation results | 0.493 | 0.554 | 0.561 | 0.551 | 0.476 | 0.490 |
| Normalized results | 0.086 | 0.097 | 0.098 | 0.096 | 0.083 | 0.086 |
| The Evaluation Unit | Solid Waste Preparation Workshop | Equipment Room | Warehouse | Centralized Control Room | Office | Dormitory |
| The calculation results | 0.493 | 0.502 | 0.502 | 0.421 | 0.427 | 0.243 |
| Normalized results | 0.086 | 0.088 | 0.088 | 0.074 | 0.075 | 0.043 |
| The Factory | The Main Process Area | Three-Waste Area | Auxiliary Equipment Area | Pre-Plant Area |
|---|---|---|---|---|
| The calculation results | 0.536 | 0.503 | 0.502 | 0.364 |
| Normalized results | 0.281 | 0.264 | 0.264 | 0.191 |
| The Evaluation Unit | Spent Fuel Pool | Extraction Process Plant | Tail-End Conversion Plant | Waste Liquid Purification Workshop | Solidification Workshop | Discharge Workshop |
|---|---|---|---|---|---|---|
| The calculation results | 0.240 | 0.272 | 0.736 | 0.707 | 0.034 | 0.059 |
| Normalized results | 0.083 | 0.095 | 0.256 | 0.245 | 0.012 | 0.020 |
| The Evaluation Unit | Solid Waste Preparation Workshop | Equipment Room | Warehouse | Centralized Control Room | Office | Dormitory |
| The calculation results | 0.222 | 0.091 | 0.275 | 0.156 | 0.088 | 0 |
| Normalized results | 0.077 | 0.032 | 0.095 | 0.054 | 0.031 | 0 |
| The Factory | The Main Process Area | Three-Waste Area | Auxiliary Equipment Area | Pre-Plant Area |
|---|---|---|---|---|
| The calculation results | 0.416 | 0.117 | 0.183 | 0.081 |
| Normalized results | 0.522 | 0.146 | 0.230 | 0.102 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wei, C.; Xu, S.; Zou, S.; Zhao, F.; Qin, Z.; Dong, H.; Hou, Z. Risk Analysis and Evaluation of Nuclear Security Radiation Events in Spent Fuel Reprocessing Plants. Sustainability 2023, 15, 781. https://doi.org/10.3390/su15010781
Wei C, Xu S, Zou S, Zhao F, Qin Z, Dong H, Hou Z. Risk Analysis and Evaluation of Nuclear Security Radiation Events in Spent Fuel Reprocessing Plants. Sustainability. 2023; 15(1):781. https://doi.org/10.3390/su15010781
Chicago/Turabian StyleWei, Cuiyue, Shoulong Xu, Shuliang Zou, Fang Zhao, Zhiwei Qin, Hanfeng Dong, and Zhixiong Hou. 2023. "Risk Analysis and Evaluation of Nuclear Security Radiation Events in Spent Fuel Reprocessing Plants" Sustainability 15, no. 1: 781. https://doi.org/10.3390/su15010781





