1. Introduction
Software development enterprises follow a certain method when developing software, either an established software development method or a custom in-house method even if only informally defined. Following a software development method, i.e., using the right practices, tools, and techniques, makes the process of developing software more manageable and efficient, resulting in greater competitiveness and success [
1]. An adequate software development method is therefore crucial for any software development enterprise trying to produce a competitive product in terms of sustainability, costs, quality, and time invested. Today’s market demands increasingly frequent software releases. Traditional software development methods tend to be sequential and rigid, which is not well-suited for the demands of the market [
2,
3]. Modifications of software due to frequent changes in software requirements are time consuming and costly during software development with traditional methods [
4]. To overcome the shortcomings of traditional methods, agile software development methods, such as Scrum and eXtreme Programming, emerged [
5,
6]. Most agile methods lean on software development iterations and increments, self-organizing teams, face-to-face daily communications among team members, and short feedback loops with customers [
7,
8]. These characteristics are among the key reason why agile methods offer a highly adaptable, efficient, and fast software development process becoming one of the most popular paradigms for software development today [
9].
Security is one of the key features of any software according to established standards [
10,
11]. Software can be considered secure when it is adequately resistant to the alterations during intentional or unintentional attacks [
12]. Agile software development methods, however, seem poorly suited for secure software development [
13]. They predominantly focus on functional requirements of the developed software while security, a quality property, is often neglected [
14,
15]. Various security-oriented software development methods exist following both traditional and agile software development paradigms [
16]. The key issue of these mostly traditional methods is the additional overhead they require as it obstructs rapid software development and adaptability to new requirements. It is therefore unclear how to ensure the development of secure software with agile methods without compromising their agility [
17].
The overall aim of this paper is to provide small and medium-sized enterprises with the means to improve their software development in terms of software security despite their limitations, such as low capacity and/or financial resources. The specificities of SMEs are additionally pronounced in enterprises practicing the DevOps concept since the (DevOps) teams are traditionally heavily loaded. Such load usually results in software deliverables’ degradation, quality decrease, and minimization of the efficiency of the DevOps teams [
18]. Furthermore, SMEs are often focused on providing specific solutions for particular needs of their customers, hence they frequently base their software development methods on agile principles [
19]. Since such enterprises face highly competitive pressure, their solutions must rely on highly adaptable and cost-efficient frameworks which provide solutions that meet their needs [
20].
This paper tries to achieve the overall aim gradually. First, this paper aims to identify security elements found in the literature since the publication of the agile manifesto at the start of this century. We understand a security element as any role, activity, or artifact added to software development methods in the literature to improve the security of the developed software, regardless of its level of abstraction. Even though strong associations between different components (e.g., a specific role can be associated with a specific artifact or activity) can be present, these usually appear in enterprises with more complex and sophisticated software development methodologies (i.e., multinationals). The evaluation of baseline individual impacts of security elements on costs and agility is, however, especially relevant in the context of SMEs, where the limited multiteam environment and significantly lower change resistance from existing power structures often does not require complex and sophisticated methodologies intricately linking several security components [
21]. Additionally, roles, for example, in addition to their association with formal activities and artifacts, also introduce a series of informal activities influencing dynamics and efficiency of the development team, thus their synergies with other elements can vary greatly case by case [
22].
The published literature does not differentiate between secure software development methods for large enterprises and SMEs. Therefore, the paper does not focus on security elements for SMEs. Rather, it embraces the variety of security elements found in the literature and looks for means to best adapt their use for SMEs. Second, it aims to group and then evaluate the identified security elements according to three key dimensions: provided security, cost efficiency, and retained agility with SMEs in mind. Third, it aims to provide a way for the software development enterprises to take advantage of the evaluation of security elements. The following research questions operationalize the aims of this paper:
RQ1: How much does the individual type of security element impact the software security, costs, and agility of the software development process?
RQ2: How can assessment of provided security, cost efficiency, and retained agility of security elements be useful to small and medium software development enterprises?
To answer these research questions, we first review the literature on secure software development. Since secure software development can be inspired by other security-centric development contexts [
23], the literature from other domains, such as the development of safety-critical systems, is also included. Safety-critical systems are those whose failure may result in substantial property, environmental damage, or in some cases in the endangerment or loss of lives [
24]. Since the software is an essential part of such systems, the reliability, confidentiality, and integrity of software used in safety-critical systems are of utmost importance [
25]. The review focuses on security elements of software development methods (i.e., activities, roles, and artifacts) compatible with agile software development. The key dimensions of security elements (increased security, cost efficiency, and retained agility) are evaluated in an international survey among secure software development practitioners. Finally, we develop a novel lightweight approach for the evaluation of formal or informal agile methods used in software development enterprises from the security perspective.
2. Literature Review
Several literature surveys and mapping studies on agile software development methods can be found in the literature [
16,
26,
27,
28,
29,
30,
31,
32,
33]. Recently, reviews of state-of-the-art agile secure software development methods [
25,
34,
35,
36] and the DevSecOps framework [
37] emerged. Literature surveys on agile secure software development focus on several perspectives, such as security measures in agile projects [
36], agile development of safety-critical systems [
25], agile requirements for secure software engineering [
35], agile security engineering methods [
34], and challenges and solutions of agile secure software development methods [
5,
38]. Although a paper [
37] focused on the DevSecOps framework in a multivocal literature survey, it only attempted to consolidate the definition of the framework rather than identify potential security elements that could be included in the framework or existing secure software development methods [
37]. Additionally, BSIMM [
39] offers an extensive overview of SSD activities, however, some roles and artifacts proposed in the literature are not included. These surveys offer relatively comprehensive insights into the current state-of-the-art of agile secure software development. They address several aspects of secure software development, such as identification of most frequently used methods, security requirement engineering phases, types of solution approaches [
35], security activities [
34], and secure software development challenges [
38].
None of these studies provide an overview of security elements designed for the agile software development process appropriate for small and medium-sized enterprises (SMEs). Additionally, studies show that more than half of proposed software development approaches remain fully theoretical [
33]. This lack of empirical evidence raises concerns about their security-enhancing potential, and associated costs and suitability for agile methods. In this section, we provide an overview of existing approaches to security elements which will later be evaluated according to the mentioned dimensions.
Literature offers several approaches to motivating developers and other team members to "think secure," eventually producing a more secure end product. Gamification as an approach for achieving increased motivation and productivity in the software development process was first proposed as Planning Poker in 2002 [
40] but has been more thoroughly discussed in the literature since 2014 [
41]. Planning Poker is heavily influenced by the Wideband Delphi method, and the rules do not resemble actual Poker rules, except that players (developers and other team members) hide their cards until a designated time. Incorporating security into agile software development by implementing gamification elements was proposed as a variation of Planning Poker as Protection Poker [
42] and Threat Poker [
43]. However, motivation is not necessarily achieved through gamification. More traditional approaches to security prioritization include business impact analysis [
44], continuous aligning of business and security goals, security goals’ identification [
45] on predominantly strategic levels, and security triage [
46], introducing more security controls [
47], security intention recap meetings [
48], and identifying architectural security requirements [
49] on the operational level.
Analyzing and reviewing the code for security issues and security testing are two important and frequently discussed groups of security elements. Security auditing as code analyses and security tests may be performed continuously within the project cycle, such as code analysis [
50], analyses performed with automated testing and analysis tools [
44,
51], security reviews [
52], design and code inspections [
53], or towards ends of the project cycle, such as penetration testing [
54] or other security tests [
47,
55]. However, different approaches require respective specialized knowledge within the development team. Hence, several authors propose involvement and incorporation of at least one new subject (role) into the existing methodology. Most commonly, this is a variation of a security guru, namely security engineer [
56], security master [
57], security-matter expert [
58], or security expert [
59]. Additionally to these roles, a security developer [
44] or a penetration tester [
60] may be included in the process. The core purpose of an additional role is to introduce expert knowledge into the development team by identifying the features that have a security risk based on a security principle, documenting risks in the security backlog (if existent), mitigating identified risks, and performing security testing for selected features. A more comprehensive approach, proposed by Baca et al. [
54], includes a set of security roles forming a security group. This group should consist of four security roles with different competencies: (1) a security manager who handles non-technical issues, such as ISO certification, legal aspects, etc., (2) a security architect who is responsible for a technical description of the particular features of business use cases, (3) a security master who is responsible for security activities performed during the development process, and (4) a penetration tester who is responsible for final security-related quality assurance. Even though this holistic approach incorporates security by design efficiently, the major drawbacks are time consumption and an increase in cost. Therefore, holistic approaches remain most suitable for safety-critical systems. An additional solution to introducing new knowledge into a development team is the frequently proposed security element, the security training of the development team [
55] or even of all stakeholders [
61].
Considering that user stories are a driving force of the agile software development process, alteration of product backlog or incorporation of a new security-specific repository, i.e., backlog, is a sensible solution proposal. Several approaches for security-conscious software development can be found in the literature. By adding an additional security-dedicated backlog [
56,
57], authors suggest that the development team will have a comprehensive overview of potential security issues and security requirements. The additional proposed solution is altering the product backlog by introducing security-related user stories, such as abuser stories [
56] and generic security user stories [
62] which are security-related user stories: a set of possible scenarios and threats to the end product. The main difference between abuser stories and generic security user stories is in user story development process. Abuser stories are usually developed in collaboration with all participating parties, whereas generic security user stories are ready-made for development teams to use. In contrast to expanding an existing product backlog, it was also proposed that misuse or abuse cases [
63] as an independent element should be incorporated into the development process. This can help developers see the software from the attackers’ perspective. A sensible approach to enhance the security-conscious software development is an incorporation of security tags within security repositories and user stories. Security tags may be included in the form of S-Tags and S-Marks as suggested by [
8] or as security keywords [
52].
Building on the premise that a significant drawback of agile methodologies is a lack of a complete overview of security issues [
54], various forms of security planning and modeling with security prioritization and monitoring activities and risk management activities are proposed. The main difference is that planning, modeling, prioritization, and monitoring activities are commonly performed at the operational level. These are activities such as security "games" (as mentioned earlier), security test cases and test plan reviews, attack surface recognition and reduction [
44], security goals identification [
45,
51], security meetings [
13], defining criticalities [
44], and prioritization of security requirements [
64]. On the other hand, risk management activities are performed at the strategic level. Traditional activities associated with risk management, such as risk identification, risk analysis, risk assessment, and their variations, are proposed in the literature [
50,
54,
55,
65,
66]. Various reports on security matters (either security issues or audit reports) commonly accompany security activities [
44].
Security elements discussed in this section are grouped and summarized in
Table 1. The table includes the code to which the results section refers, a consolidated name of the group of security elements, a brief description, and sources in which particular security elements can be found in the literature.
Even though several approaches can be found in the literature proposing a relatively large amount of security elements, only a fraction (approximately one-fifth) of those approaches were tested in industrial settings [
33]. Hence, little is known about their direct impact on agility and costs. In rare cases, studies report on cost increases [
54] and a possible compromise of agility of some elements [
45,
51]. However, to the best of our knowledge, there is no systematic evaluation of all security elements or their corresponding security element groups regarding their impact on the agility of the software development process and costs of their implementation. Therefore, this paper aims to fill this gap by conducting an evaluation of security element groups from the practitioners’ perspective.
3. Materials and Methods
To answer the first research question, we evaluated the impacts of security element groups on security, costs, and agility of software development. We conducted an international survey among secure software development practitioners between April and May 2022 on the prolific.co platform in two phases. In the first phase, we conducted a screening survey under the criteria “Industry: Software.” No other limitations were applied. The screening survey included a definition of secure software engineering and questions on their work experience with software development and agile software development (in years) and their work experience with secure software engineering (in years). We received 1053 responses in total, out of which 167 respondents had three or more years of experience with secure software engineering. These were considered as appropriately knowledgeable to participate in the second phase of the survey.
In the second phase, we invited the 167 respondents with three or more years of experience with secure software engineering to participate in a survey to evaluate security elements. The questionnaire in the second phase was developed to measure three key performance dimensions of each security element: (1) provided security to developed software (i.e., the resistance of software to attacks), (2) increased costs of software development (e.g., man-hours, direct costs), and (3) compromised agility of the software development solution (i.e., a departure from the agile principles). The survey questionnaire first included a short introduction with an explanation of the evaluation criteria presented above. The main part of the questionnaire consisted of three sections, one for each element group (i.e., roles, activities, and artifacts). A description was provided for each security element group, followed by the question: How would implementing an average element from this cluster affect an agile method without security-related elements? The three key performance dimensions were evaluated on 7-point unipolar scales: from 1 (no effect on security) to 7 (considerably improve security) (provided security), from 1 (no effect on costs) to 7 (considerably increase costs) (increased costs), and from 1 (no effect on agility) to 7 (considerably reduce agility) (compromised agility). All questionnaire items were self-developed.
Out of the 167 invited participants, we received 117 fully and 13 partially completed surveys. After the data cleaning, 112 responses were appropriate for further analyses, returning a response rate of 62.3 percent. Average response duration was 6 min and 46 s. The respondents’ age ranged from 22 to 62, with a mean of 36.2 years (
SD = 9.2). Respondents’ experience in secure software engineering ranged from 3 to 20 years, with a mean of 6.0 years (
SD = 3.8). Other demographic characteristics of the respondents are presented in
Table 2.
4. Results
To facilitate the interpretation of the results, the scores for
increased costs and
compromised agility were reversed (i.e., recoded from 1, 2, …, 7 to 7, 6, …, 1, respectively). These performance dimensions were also renamed to
cost efficiency and
retained agility, respectively, to reflect the change. For all three key performance dimensions, a lower score means worse performance (i.e., less provided security, lesser cost efficiency, and less retained agility) and a higher score means better performance (i.e., more provided security, better cost efficiency, and more retained agility). A summary of overall means for roles, activities, and artifacts is presented in
Table 3.
In the following, we present means, standard deviations, medians, and modes for the three key performance dimensions of all security element groups. Security elements are grouped together into a table for each type. They are sorted descending according to provided security.
The evaluation of roles is presented in
Table 4. The
Security team provides most security not only among roles but among all security element groups. However, it is also the least cost-efficient and retains the least agility. Although a
Security guru is among the most frequently proposed security elements in the literature, a
Penetration tester or
Security developer may be a more cost-efficient alternative providing a similar or higher level of security and retaining a comparable level of agility. Summarily, roles provide the most security compared to activities and artifacts (
Msecurity = 5.70). Roles are, however, the least cost-efficient of the three (
Mcosts = 3.27) and retain the least agility (
Magility = 4.27). The univariate skewness and kurtosis values for the roles ranged from −1.77 to 0.67 and −0.96 to 2.93, respectively, indicating an approximately normal data distribution [
73].
Table 5 presents the evaluation of activities.
Security analysis and testing provides the most security. However, it is also the least cost-efficient and retains the average agility among the activities.
Security training retains the most agility and provides the fourth-most security while being averagely cost-efficient. Even though
Security planning and threat modeling and
Risk management are among those that are most frequently found in the literature, our results indicate that their provided security is among the lowest among the activities. In summary, activities seem to be between roles and artifacts regarding provided security, retained agility, and cost efficiency (
Msecurity = 5.26,
Mcosts = 3.76,
Magility = 4.40). The univariate skewness and kurtosis values for the activities ranged from −1.23 to 0.29 and −1.04 to 1.87, respectively, indicating an approximately normal data distribution [
74].
The evaluation of artifacts is presented in
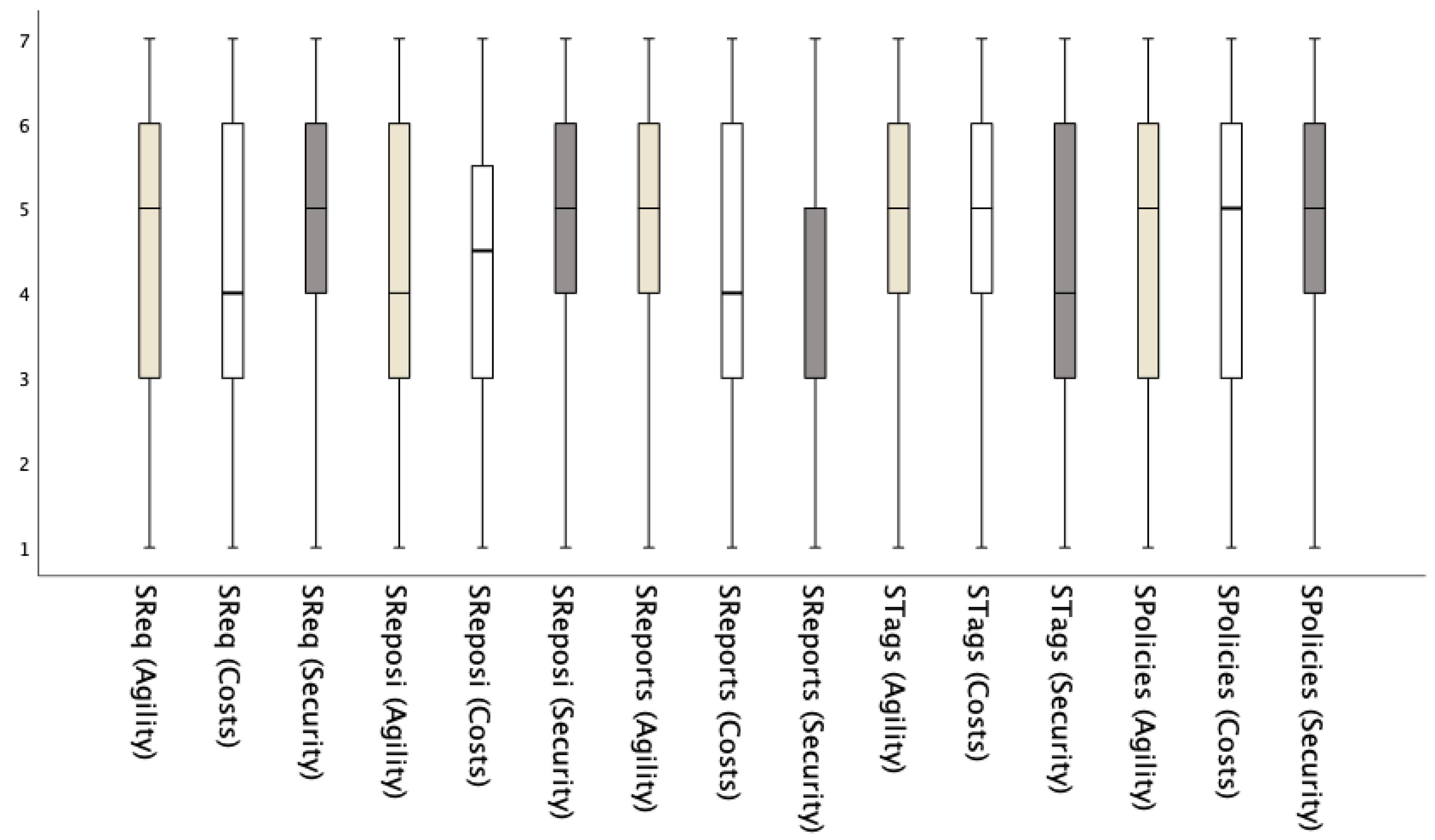
Table 6. The only artifacts with a mean value greater than 5 are
Security policies. Besides providing the most security among artifacts, it retains the least agility but is the second most cost-efficient artifact.
Security reports together with
Security tags provide the least security among all security element groups regardless of their type. Overall, artifacts are the most cost-efficient (
Mcosts = 5.52) and retain the most agility (
Magility = 4.64). However, they also provide the least security (
Msecurity = 4.64). The univariate skewness and kurtosis values for the artifacts ranged from −0.67 to −0.13 and −1.03 to −0.13, respectively, indicating an approximately normal data distribution [
74].
To identify possible outliers, we present the results in the boxplots in
Figure 1,
Figure 2 and
Figure 3 for roles, activities, and artifacts, respectively. As seen from the figures, only four definite outliers in all three boxplots can be observed. The outliers are presented in the security dimension of two elements (security team, security analysis and testing) that already score very high in security. Thus, removing them would increase their security scores even more and would not impact the relative position of elements in scatter plot quadrants.
5. Proposed Model for SMEs
To answer the second research question, we are proposing a lightweight approach for the evaluation of secure software development method elements. The proposed approach can be considered lightweight since it has few rules and practices and is simple and easy to learn. Further, the improvements achieved through the implementation of the approach can be applied to different development projects later. It is a separate activity that can be used as a tool or a first steppingstone when planning changes in development methods from a security perspective or implementing any novelty where compromised agility, cost efficiency, and added security should be considered. The approach consists of three phases: (1) identification of security elements comprising the software development method used by a software development enterprise, (2) evaluation of identified security elements, and (3) improvement of the existing method (see
Figure 4).
The first phase aims to gain insights into the existing software development method needed for evaluating and improving it. This phase enables software development enterprises to use the proposed approach for any software development method even if there is no formal method or if software development is “as agile as it gets” (i.e., denial of the existence of any method). In this phase, enterprises first identify all elements comprising their software development method, whether they are focused on security or not. By identifying all elements, enterprises will get an overview of the elements and the relationships between them. An in-depth insight into the existing software development method is necessary to avoid unwanted effects of potential improvements, such as the introduction of elements duplicating parts of existing elements or conflicting with them. Next, security elements need to be identified. This enables the evaluation of security elements that are already in place.
The
second phase aims to evaluate the security elements in place. The results of our international evaluation study provide the grounds for such evaluation. In this phase, software development enterprises need to determine which security elements in place can be mapped to which security element groups (as identified in this
Section 2). Since the security element groups cover nearly all security elements found in the literature, most if not all security elements in place can be mapped to one of the security element groups. This enables enterprises to seamlessly evaluate the provided security, cost efficiency, and retained agility of the security elements in place. If enterprises, however, identify a security element in place that cannot be mapped to any of the security element groups, the evaluation needs to be repeated among available experts for
all security elements in place to avoid skewed results due to potential differences in the respondents’ bias of our study and the new evaluation.
The
third phase aims to provide recommendations for improving the existing software development method. The existing software development method can be improved in various ways. For example, it can be more security-focused, cost efficient, and/or agile. To facilitate decision making, the evaluation of security elements is visualized with scatter plots. One scatter plot shows the trade-off between provided security and cost efficiency, and another one shows the trade-off between provided security and retained agility. Different quadrants in the scatter plots provide their own heuristic recommendations for improving the existing software development method through security elements placed in it. The quadrants were named as shown in
Figure 5 to ease the understanding of the meaning of security element placements:
Goldilocks,
Possible overkill,
Prospects, and
Wastrels.
The Goldilocks quadrant consists of security elements with above-average provided security and above-average cost efficiency or retained agility. Security elements in this quadrant have the best ratio between provided security and cost efficiency or retained agility and can be thus regarded as the most suitable for small and medium software development enterprises that cannot afford less cost-efficient security elements or want to lose too much agility in their software development. The Possible overkill quadrant contains security elements with above-average provided security but below-average cost efficiency or retained agility. Security elements in this quadrant are a potential security overkill for small and medium software development enterprises. Even though they provide above-average security, they may be too costly or compromise too much agility. Nevertheless, they may be suitable for developing safety-critical software and other software when security is a top priority (e.g., online banking). The Prospects quadrant consists of security elements with below-average provided security and above-average cost efficiency or retained agility. Security elements in this quadrant can underperform in terms of provided security. If security is not a top priority, these security elements can be considered as a cost-efficient way to provide some security while retaining agility. For small and medium enterprises, they can also be attractive as alternatives for less cost-efficient security elements providing more security, especially coupled with some such elements. The Wastrels quadrant contains security elements with below-average provided security and below-average cost efficiency or retained agility. Since these security elements are less cost efficient or retain less agility while providing less security, there are poor grounds for including them in software development methods. Unless they have some other added value justifying their inclusion, these security elements may be dropped. An analysis of the impact on security may be needed before dropping any security elements. If needed, the dropped security elements may be replaced by other security elements.
To demonstrate the use of scatter plots, we visualized the results of the international survey among published secure software development authors. The
x-axis is placed at the provided security median for all security element groups regardless of their type. The
y-axis is placed at the median of cost efficiency (
Figure 6) and retained agility (
Figure 7) for all security element groups regardless of their type.
The results seen in
Figure 3 indicate a negative relationship between security and costs, as less cost-efficient security elements provide more security. A similar negative relationship can be seen in in
Figure 4, whereas less agile-threatening security elements provide more security. Only very few outliers can be observed.
No security element groups were placed in the Goldilocks quadrant in both scatter plots. However, Security training is placed in the Goldilocks quadrant in the security–retained agility scatter plot, while being reasonably close to this quadrant in the security–cost efficiency scatter plot. Hence, this security element may be the most appropriate for small and medium software development enterprises. Security guru was placed in the Goldilocks quadrant in one scatter plot but in the Possible overkill quadrant in the other, while the Security prioritization and monitoring group was, in both cases, placed in the Possible overkill quadrant; however, in the security–cost efficiency scatter plot, it was placed reasonably close to the Goldilocks quadrant. Hence, the Security guru is not as cost-efficient, but it does provide above-average security while not interfering with the agility of the method. Since the Security prioritization and monitoring group provides a reasonable cost efficiency while offering above-average security, it could be considered in the same context as the Security guru. Small and medium enterprises may consider the trade-off between costs and agility when deciding among these security elements. Six security element groups were placed in the Prospects quadrant in both scatter plots: Security policies, Risk management, Security requirements artifacts, Security repositories, Security reports, and Security tags. Although these element groups provide below-average security for the end product, they may still be considered when security is essential but not the highest priority or in cases where an enterprise plans to invest fewer resources or sacrifice agility as little as possible but still aims to introduce secure software development elements into their method. The Wastrels quadrant seems to be inhibited similarly to the Goldilocks. No security element groups were placed in this quadrant in both scatter plots. Only Security requirements engineering and Security planning and modeling were placed in this quadrant in the security–retained agility scatter plot. None of the security element groups were placed within Wastrels in the security–cost efficiency scatter plot. These two security elements should be considered for incorporation into the development method of an SME when there is a reasonable justification for their inclusion, mainly since they introduce an approximately average level of security in comparison to others and may affect the agility of the process.
To provide an informative overview of the placements of security element groups into quadrants, we summarize the findings of our study in
Table 7.
6. Discussion
This paper aimed to provide SMEs with the means to improve their software development in terms of software security. To achieve this, it centers around the concept of security elements—those elements (i.e., activities, roles, artifacts) of software development methods [
73] that provide security. Security elements were first collected from published literature and then grouped. The security element groups resemble the core phases of secure software development suggested by [
16]: software requirements security, software design security, software construction security, and software testing security. This paper, however, breaks down these core phases into smaller parts according to the type of method element. Several previously proposed secure software development frameworks, approaches, and maturity models, e.g., [
39,
75,
76], provide some support for the security element groups presented in this paper.
According to the opinion of the surveyed practitioners,
roles provide the most security among different types of security element groups. All roles have above-average provided security indicating that security expertise is one of the key factors in ensuring the security of developed software. The
security team typically consists of several security specialists whose expertise highly impacts the security of the developed software. However, it also compromises the agility of the software development process (e.g., by introducing various security controls into existing activities) and significantly increases its costs. It is widely and commonly known that security specialists, such as
penetration testers and
security gurus, are highly sought after and relatively expensive. Such findings are in line with the current literature reporting up to a 500 percent increase in costs due to the inclusion of several security roles in the development process [
54]. According to the survey results, the
security developer is the most balanced role providing considerable security at relatively low costs while also retaining agility. Additionally,
security developers are actively involved in the development process and thus importantly improve the expertise of the development team, which may be complemented by the
penetration tester (involved during testing or later) and
security guru (not actively involved in the development process). Roles seem to compromise agility the most, which can be associated with the prerequisite of more sequential organization of the development process—e.g., stages at which those roles are most frequently used at the development stages: analysis, design, coding, and testing [
45].
As characteristic for agile methods [
73],
activities are the most represented type of security elements both in terms of quantity and diversity. They retain the second least agility among all three types of security element groups, which may be due the fact that including new activities into agile methods inherently compromises agility to an extent. The effects on agility and costs can be especially pronounced if the development team does not have the necessary knowledge to efficiently perform the introduced activities.
Security training is the only activity in the
Goldilocks quadrant for agility and is placed extremely close to it in terms of cost efficiency. This is especially valuable since its results increase the security knowledge of the development team, directly affecting one of the key factors in providing security. Not only does
security training not compromise the agility of the software development process in the long term but also the costs invested are subsidized across different projects as the acquired security knowledge stays with the development team members. Additionally, security training is typically held outside of the development process, hence it does not affect its agility. This finding is also consistent with the published literature emphasizing the importance of security skills and training [
68,
77].
Risk management is among the more popular security elements for agile methods. Our results, however, suggest that it provides the least security among activities, which may be attributed to its focus on the strategic level of security planning and a lacking practical application during project implementation. This can be also seen in some degree of compromised agility if this activity is implemented in practice. Consistent with these findings, a study focusing on secure software development practices indicated that these practices could be characterized as compliance-based, arbitrary, late, and error-driven rather than risk-oriented [
78].
Although artifacts are generally the most cost-efficient and retain the most agility, they perform relatively poorly in providing security. For example, security reports are among the most widespread security elements, yet they score very low on the security scale. Not all artifacts perform poorly, though. For example, security policies fall into the upper part of the Prospects quadrant for both costs and agility. Security requirement artifacts and Security repositories do not fall far behind. These artifacts guide the development team to think about the developed software more from the security perspective, potentially somewhat making up for lacking security expertise of developers.
6.1. Theoretical Implications
Our research advances the current literature in several ways. First, we have developed a novel approach for multi-dimensional evaluation (i.e., security, cost, agility) of agile secure software development methods. Our approach focuses on the evaluation of security elements. It is designed in a way that enables evaluation of any agile method since even the least defined methods consist of certain recurring elements (i.e., artifacts, roles, activities) that can be evaluated. The evaluation of multiple dimensions of security elements provides insights from different viewpoints, which enables a more comprehensive evaluation of software development methods from the security perspective.
Second, the results of the international study among practitioners indicate that there may be a negative relationship between provided security of the developed software and retained agility of the development process and in the relationship between provided security and cost efficiency. Future work may focus on identifying prospective security elements beyond those already known to be applicable to agile methods to confirm such a finding.
Third, our study provides a list of 16 security element groups. This list can be used as a baseline for scholars and practitioners developing new security elements or combining them into holistic secure software development methods. The provided evaluation of security elements may help them improve their decision-making process when selecting the security elements that provide the best combination of a desired level of security and acceptable levels of costs and agility. The list of security element groups may be useful beyond the current timeframe in which it was created. The list is based on a review of two decades of agile secure software development research; therefore, it may not be too surprising if future security elements can be consolidated into one of those already on the list.
Fourth, the evaluation of security elements appears to point to an interesting finding. Several relatively cost-efficient security elements that provide ample security while retaining agility (i.e., security training, security requirement artifacts, and security developer) deal with increasing the security expertise of software developers, thus improving the whole software development process. Future work may thus focus on developing new long-term approaches for incrementally improving the security expertise in the development team, which would not significantly compromise the agility or increase the costs of software development. However, empirical evidence would be very needed to determine the actual effectiveness of such approaches in the long run.
6.2. Practical Implications
This paper also has several practical implications. First, the proposed approach offers a practical and cost-efficient way for small and medium-sized software development enterprises to evaluate and improve their software development methods from the security perspective. Based on our approach, enterprises can situationally adapt their software development methods to fit their needs regarding security, agility, and costs. If the primary focus is on the cost efficiency of software development or retaining its agility, most artifacts and several activities may be suitable while roles should generally be avoided. If security, however, is an absolute priority, roles provide most security even though they may not be too cost-efficient. The readers should note that security elements may be related to each other. For example, a security guru can provide security reports, security policies, both, or neither of them. By summarizing the impacts of individual security elements, we may obtain a good estimation of the impact of implementing several security elements. Nevertheless, such an estimation is not perfect since the overall impacts are rarely the sum of individual impacts.
Second, we assessed provided security, cost efficiency, and retained agility of individual security element groups in an international study among practitioners. Practitioners can thus take advantage of this evaluation to make informed decisions regarding which elements to include in their software development methods and projects depending on their specific needs. The placement of security elements into quadrants further facilitates such decision making. For example, practitioners may consider security elements in the Possible overkill quadrant if security is a top priority and high costs or compromised agility can be tolerated. However, security elements in the Goldilocks and Prospects quadrants may be best suitable for most projects, and especially for small and medium-sized enterprises.
6.3. Limitations
This study has some limitations that the readers should note. First, the literature review was not conducted systematically. Although we were searching the most impactful bibliographic databases and employed the snowball method to identify the studies, we might have missed some existing agile software development methods, especially if not present in the literature. Second, the study focused on agile secure software development. Future work may investigate security elements beyond those already known to be applicable to agile methods. For example, future studies may investigate elements from traditional secure software development to determine if and how they perform when used in agile methods. Such studies may be especially beneficial in identifying prospective security elements besides existing ones. Third, the results indicate a relatively low diversity among different security element groups according to cost efficiency and particularly retained agility. Such distribution of data points in scatter plots can be associated with the fact that approximately 65 percent of our respondents work in the same job position, i.e., as software developers. A more evenly distributed sample of software developers, project managers, security experts, and other software consultants may produce higher response diversity. Fourth, some roles, artifacts, and activities may be related, and this may have affected the scores given by practitioners in our survey. However, such relations cannot be claimed for most security elements, as can be observed by the dispersion of security elements in the scatter plots. Fifth, this paper investigated security elements for a generic agile method under the assumption that the used agile method does not affect the outcomes of implementing security elements (i.e., security, retained agility, cost efficiency). Since the outcomes of implementing security elements in the context of specific agile methods (e.g., Scrum, XP) may nevertheless differ, at least for some security elements, future studies would be needed to investigate whether this is the case and for which security elements.
7. Conclusions and Future Work
This paper has identified and categorized security elements proposed in the literature on agile secure software development. The security elements were then assessed for similarity and grouped in 16 distinct security element groups. Security element groups were then evaluated by practitioners from the software development industry for their cost efficiency, compromised agility, and added security. The results indicate that roles might provide the most security but have the highest costs and most compromised agility. On the other hand, artifacts could contribute to the overall security of the end product the least. However, they are by far the most cost-efficient and retain the most agility. Activities lie in between roles and artifacts in all three key dimensions.
We then used these results to develop a lightweight approach for the evaluation of secure software development method elements. The approach is ready-made for implementation and does not require specialized knowledge or rules to follow. The approach can help software development practitioners to adapt their development methods by prioritizing the adoption of new security elements in their development practice according to their needs and available resources.
There are several directions that future work may undertake. For example, future works could investigate additional situational factors related to specific industry contexts. Unique characteristics of some industries, such as automotive, aviation, and aerospace industries, may require a very strong security undertaking, not characteristic of the majority of other industries. Evaluation of security elements individually allows enterprises to adapt their existing software development methods incrementally, by including a single most suitable element at a time according to their needs. Hence, the results of our study may act as a priority checklist for enterprises attempting to improve their software development methods in terms of software security. Future works may further aim to compare and evaluate the use of complete off-the-shelf secure software development methods. Such a holistic approach in which all software development lifecycle stages and architectural levels are considered may provide an additional view on the usability and appropriateness of particular methods when compared to each other. To objectively measure the level of software security and enhance the formal software development in practice, specialized security metrics should be additionally investigated, developed, and proposed in the future.
This study took a quantitative approach to evaluate the impact of implementing security elements. Future studies may employ qualitative research designs, such as interviews with professionals, focus groups, or the Delphi method, to gain further insights into the positioning of security element groups into specific quadrants. For example, it may be possible to determine whether certain security elements are firmly positioned in their quadrants or not (e.g., due to some contextual factors).