A Framework and IoT-Based Accident Detection System to Securely Report an Accident and the Driver’s Private Information
Abstract
:1. Introduction
- To develop an intelligent IoT framework for instantly and securely detecting and reporting car accidents;
- To develop an IoT product that considers security and privacy requirements for protecting critical information;
- To respond as soon as possible to injured people before the situation becomes critical;
- To evaluate and apply lightweight cryptography (LWC) for preserving and encrypting sensitive information.
2. Related Works
2.1. IoT Accident Detection System
2.2. IoT Privacy and Security
2.3. Lightweight IoT Cryptography
2.4. Comparison of Related Works
3. Research Design
3.1. Research Methodology
3.2. Cycle Design
- Relevance cycle: The first stage is to define the problem in context and the requirements: a secure and effective IoT-based system to detect and report car accidents instantly while ensuring privacy. In this cycle, as explained in the figure, the IoT security framework literature is searched, and the requirements needed to implement the proposed artifact are determined. Thus, this cycle specifies the scope of the research and the literature review needed for this work.
- Rigor cycle: This cycle uses a literature review of previous studies that have focused on similar issues. Moreover, the information gathered from the literature will then be used to provide a comprehensive comparison of IoT LWC algorithms. Equally important, this cycle also provides a summary of all studies on IoT security frameworks related to detecting and reporting car accidents instantly.
- Design cycle: A comparison between the IoT and LWC algorithms will assist in delivering an IoT security framework considering the delivery of sensitive information by message and the authentication processes between the sender and recipient to prevent spoofing by an attacker. Thus, the proposed research follows the DSR process for developing and evaluating a prototype system as an IoT-based security framework artifact for an accident detection system. Additionally, the following section covers how the research methodology works, aligns with the research objectives, and develops the proposed artifact.
3.3. Development of the Study Using the Research Approach
- Environment (relevance cycle): With this element, the research problem and motivation are clearly defined. In addition, the value of the solution is justified, as mentioned in Section 1, as well as in all related publications’ research outputs sections that identify the problem and clearly motivate the research direction toward a solution. The related work is divided into three major sections: IoT accident detection, IoT security and privacy, and the IoT–LWC method. The sections were divided by the research’s objectives to define the problem and present the previous studies mentioned [3,5,6,7,8,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24]. Equally important, the researcher conducted face-to-face interviews with experts in the fields of cryptography and the IoT as well as observational studies to gather data for this study.
- Designs Science Research: This element is divided into two sections.
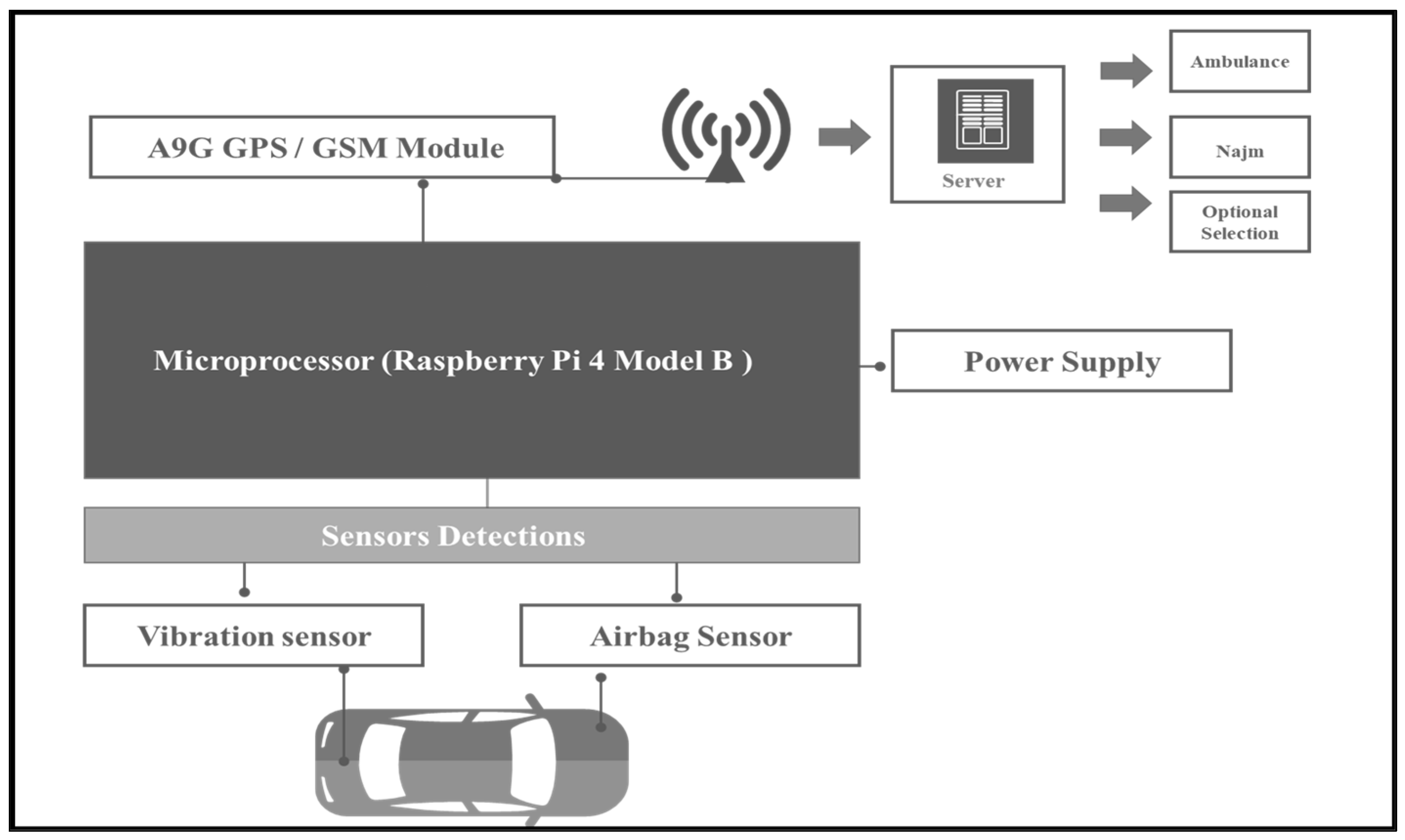
- Build/develop the artifact: This section shows the design and development of the research artifact. Here, the theoretical knowledge obtained from the environment and knowledge base is applied to the creation of an artifact. To address the identified problems, this includes both functionality and architecture. In addition, the artifact is designed and tested, utilized in simulations, or used in other ways as a solution to the perceived problems [26,27]. The proposed solution of this research study was to provide a secure and effective IoT-based system to detect and report car accidents instantly. This used RPM, which relates to other technologies such as IoT sensors (airbag and vibration) and GSM and GPS modules, to detect accidents faster.
- Evaluate: In this section, an analysis is performed as to how well the research artifact meets the objectives highlighted once the problem has been identified [27]. The evaluating and testing section includes the sections that design and implement the overall proposed artifact. Additionally, improvements can be made to the artifact to ensure the IoT-based security framework for the accident detection system meets the objectives of detecting and reporting a car accident instantly, preserving the driver’s private information securely.
- Knowledge Base:
4. Requirement Analysis
4.1. The Overall Conditions and Challenges for IoT–LWC (Research Study Challenges)
Challenges Faced in an IoT-Based ECC LWC
- Application of the ECIES algorithm:
- Time consumption when sending a message: This research explored the use of ECC to improve data privacy and security in the IoT. Due to its effectiveness and performance in terms of time and energy, it is intended to demonstrate that ECC is relevant for the IoT. To do so, this study also emphasizes earlier studies on lightweight ECC to demonstrate the significance of ECC and to assess the effectiveness of techniques, as described in Section 2.3 (Lightweight IoT Cryptography), to quickly report an accident to first responders and encrypt messages. Thus, this study focused on the ECIES algorithm key size and compared it with the RSA algorithm in terms of time consumption in the generation of the RSA key size. Furthermore, a comparison between the ECIES algorithm and the RSA method is covered in the evaluation.
- SMS message length: The message content must be kept to a minimum via a maximum SMS message length for mobile devices to achieve the objective of sending a message instantly while also being encrypted by ECC. In fact, the message can only be 160 characters long at most. For instance, if an accident occurs, a location is sent through an SMS message to first responders. For this reason, only the longitude and latitude are encrypted to keep the message short, and only one SMS is sent. However, the encrypted message is still more than 160 characters [28], and to solve this challenge, the message is sent from the device controlling the signals, encrypted, and then sent to the CServer as MQTT. The message is then sent from the CServer to the first responders.
- IoT-based Accident Detection System
4.2. Requirement Specification
4.2.1. Software Requirements
- Raspberry Pi OS Raspbian: The Raspbian operating system supports Raspberry Pi. Based on Debian, Raspbian is a free operating system designed specifically for the Raspberry Pi device [29].
- PyCharm IDE Software2022.3.2: PyCharm is a Python IDE developed by JetBrains, the organization that also produces the well-known IntelliJ IDEA IDE for Java. Any developer who wants to construct Python applications, including web applications, data science applications, or even simply basic Python scripts, is encouraged to use PyCharm [30]. It has a code editor with tools such as automatic indentation, brace matching, and syntax highlighting. A “Python file” is written code or a program.
- The Central Server (CServer)—“Website-Database Server”: All information on an accident is kept in a Microsoft SQL database, and MySQL was adopted as the database management system (DBMS). In addition, the website develops client-side interfaces using HTML, CSS, and Bootstrap. For server-side programming, it uses PHP [31].
- MQTT (message queuing telemetry transport): An IoT ecosystem uses the MQTT protocol for communication, which runs on top of the transport control protocol. Moreover, MQTT is considered a lightweight machine-to-machine communication protocol, and it was developed by IBM. It is used to send data from sensors to the server [32].
- Fritzing Software 0.9.10: The Fritzing software package can be helpful during development phases, such as the assembly of the prototype based on the scheme in the mock-up sketch and boards, as well as the automatic generation of schematic diagrams and the PCB [33].
- Twilio SMS Massage Service: The use of virtual phone numbers to deliver SMS messages is made possible by Twilio’s cloud-based messaging technology [34].
4.2.2. Hardware Requirements
- Raspberry Pi Model B: The newest and fastest Raspberry Pi model, the Raspberry Pi 4 Model B, was used to build an IoT ecosystem. It features different RAM capacities (2, 4, or 8 GB), a USB-C port for power, a MicroSD card slot for the operating system and file storage, two micro-HDMI ports, and the option to connect to the Internet wirelessly or with an ethernet cable. The features of the Raspberry Pi 4 Model B used in this experiment are listed in Table 4 [35].
- Airbag sensor: An airbag is a type of occupant restraint system and a vehicle safety component. It is composed of an inflatable fabric bag, an impact sensor, an inflation module, and an airbag cushion. If an accident causes the airbag to blow, the sensor detects it. If the airbag bursts, the airbag sensor detects that an accident has occurred [36]. The digital airbag sensor in this research requires three wires for connection: a ground pin wire (GND), a voltage pin (+5 Vcc) to supply the circuit with the required electricity, and an input pin to communicate with the Raspberry Pi.
- Vibration sensor (VS): This is a transducer that transforms vibrations into an electrical equivalent, such as a voltage, such as one that uses a laser or piezoelectric crystal. It is also known as a vibration transducer. It detects the vibration of a car, which is a specific and substantial vibration. However, vibration sensors are used to measure and analyze linear velocity, displacement, proximity, and various shock triggers [37].
- GPS and GSM modules: A radio navigation system called GPS, or “global positioning system”, enables land, sea, and aerial users to pinpoint their precise location, speed, and time at any time, day or night, in any weather, anywhere in the world. An accident’s location will be known. In addition, it is a digital mobile telephony system that is widely utilized in Europe and other parts of the world. It stands for global system for mobile communication [38]. Furthermore, the GSM and GPS modules are utilized as a security system to improve the project and make it more secure by calling or texting the user’s phone number if there is a car theft attempt [39].
- Power supply: This is an electronic device that supplies electric energy to an electrical load [38].
4.2.3. Proposed System
4.3. System Design
4.3.1. Design Goal
4.3.2. Security Issue
4.4. System Architecture
4.4.1. Block Diagram
4.4.2. Sequence Diagram
5. Implementation
Development Tools
- Phase 1: QR Code Scanning (Website—Database Server):
- Driver details table: This table includes all driver-related data, including Driver_Name, Driver_Address, Driver_Email, and Driver_Phone number;
- Vehicle table: Vehicle information, including Vehicle_ID, Vehicle_Name, and Vehicle_Insuracne, is available and provided in this table;
- Diseases (medical records) table: This table contains data on all diseases and the health insurance of the driver;
- Device table: This table contains all data related to the device, such as Device_ID, Driver_ID, Vehicle_ID, and the private keys utilized in the decryption process. The system generates the QR code for each vehicle to allow the driver to input the required information;
- Accident table: This table is used to keep track of all details of accidents, such as Driver_ID, Device_ID, Location_ latitude, and Location_ longitude, including those that were used during the notification phase.
- 2.
- Phase 2: IoT Accident Detection Sensors
- Airbag sensor (AS): While developing the circuit, an AS is linked to the RPM. Thus, the AS works to detect the signals when an airbag is bursting. Furthermore, the AS can be added to the breadboard and connected to the microprocessor to complete the circuit;
- Vibration sensor (VS): The second sensor used in this research is the VS, which works to detect signals when it is activated. It also employs a digital VS. The sensor’s vibration frequency ranges from 40 Hz to 65,535 Hz when it is attached to the RPM. In addition, the shock sensitivity of the VS was modified by selecting a time alert to detect the shock. Periodically shaking the sensor causes it to automatically produce “1” when working as a digital signal (as an indicator of shaking or movement).
- 3.
- Phase 3: Accident Transmission Encryption Message
- Raspberry Pi Microprocessor (RPM): In this research, the system uses a Raspberry Pi 4 Model B connected to a CServer, an AS, a vibration sensor, GSM/GPRS, and other devices to detect and report accidents instantly. The Raspberry Pi receives the signals, requests the location of the accident, encrypts the message, and sends the encrypted message to the CServer; thus, the IoT devices connect to the Raspberry Pi through input pins (Figure 8), and the CServer retrieves the data through MQTT.
- GPS and GSM module: The A9 GSM/GPRS module is a tiny GSM modem that can be used in numerous IoT projects. In this research, the GSM was used to send the encrypted message to the CServer via MQTT. Additionally, the exact location of the vehicle is also determined through the GSM/GPRS and GPS tracking systems, which also use GPS technology. In this research, we proposed a GPS technology system to capture the location. Additionally, the connection pins of the A9G GSM/GPRS+GPS were as follows (Table 5).
- 4.
- Phase 4: Notifications
6. Evaluating the Phases (As Experimental Implementation)
- Phase 1: QR Code Scanning (Data Entry) Implementation
- 2.
- Phase 2: IoT Accident Detection Sensor Implementation
- 3.
- Phase 3: Accident Transmission Encryption Message
- 4.
- Phase 4: Notifications to First Responders and Accident Details
6.1. Overall Outcomes/Results
6.2. Case Study and System Limitations
6.3. Comprehensive Remarks on the Overall Proposed System (Adding Knowledge Base)
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Almoshaogeh, M.; Abdulrehman, R.; Haider, H.; Alharbi, F.; Jamal, A.; Alarifi, S. Shafiquzzaman Traffic Accident Risk Assessment Framework for Qassim, Saudi Arabia: Evaluating the Impact of Speed Cameras. Appl. Sci. 2021, 11, 6682. [Google Scholar] [CrossRef]
- Raghad, A.; Areej, S. IoT Based Accident Prevention System Using Machine Learning Techniques. Available online: https://www.researchgate.net/profile/Hala-Qudaih/publication/369595854_IoT_Based_Accident_Prevention_System_using_Machine_Learning_techniques/links/6424132192cfd54f8439c7bc/IoT-Based-Accident-Prevention-System-using-Machine-Learning-techniques.pdf (accessed on 1 April 2023).
- Sharma, S.; Sebastian, S. IoT based car accident detection and notification algorithm for general road accidents. Int. J. Electr. Comput. Eng. 2019, 9, 4020. [Google Scholar] [CrossRef]
- Sklavos, N.; Zaharakis, I.D. Cryptography and Security in Internet of Things (IoTs): Models, Schemes, and Implementations. In Proceedings of the 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016; pp. 1–2. [Google Scholar] [CrossRef]
- Borgia, E. The Internet of Things vision: Key features, applications and open issues. Comput. Commun. 2014, 54, 1–31. [Google Scholar] [CrossRef]
- Bhardwaj, I.; Kumar, A.; Bansal, M. A review on lightweight cryptography algorithms for data security and authentication in IoTs. In Proceedings of the 2017 4th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 21–23 September 2017; pp. 504–509. [Google Scholar] [CrossRef]
- Fotovvat, A.; Rahman, G.M.E.; Vedaei, S.S.; Wahid, K.A. Comparative Performance Analysis of Lightweight Cryptography Algorithms for IoT Sensor Nodes. IEEE Internet Things J. 2020, 8, 8279–8290. [Google Scholar] [CrossRef]
- Sridhar, S.; Smys, S. Intelligent security framework for iot devices cryptography based end-to-end security architecture. In Proceedings of the 2017 International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, 19–20 January 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and Internet of Things Security. Computer 2017, 50, 76–79. [Google Scholar] [CrossRef]
- Lee, S.; Tewolde, G.; Kwon, J. Design and implementation of vehicle tracking system using GPS/GSM/GPRS technology and smartphone application. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Republic of Korea, 6–8 March 2014; pp. 353–358. [Google Scholar] [CrossRef]
- Jethwa, A. Vehicle Tracking System Using Gps and Gsm Modem—A Review. Int. J. Recent Sci. Res. 2015, 6, 4805–4808. [Google Scholar]
- Khan, M.A.; Khan, S.F. IoT based framework for Vehicle Over-speed detection. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Yee, T.H.; Lau, P.Y. Mobile vehicle crash detection system. In Proceedings of the 2018 International Workshop on Advanced Image Technology (IWAIT), Chiang Mai, Thailand, 7–9 January 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Nasr, E.; Kfoury, E.; Khoury, D. An IoT approach to vehicle accident detection, reporting, and navigation. In Proceedings of the 2016 IEEE International Multidisciplinary Conference on Engineering Technology (IMCET), Beirut, Lebanon, 14–16 November 2016; pp. 231–236. [Google Scholar] [CrossRef]
- Khot, I.; Jadhav, M.; Desai, A.; Bangar, V. Go Safe: Android application for accident detection and notification. Int. Res. J. Eng. Technol. 2018, 5, 4118–4122. [Google Scholar]
- Chaturvedi, N.; Srivastava, P. Automatic Vehicle Accident Detection and Messaging System Using GSM and GPS Modem. Int. Res. J. Eng. Technol. 2018, 5, 252–254. [Google Scholar]
- Khaliq, K.A.; Raza, S.M.; Chughtai, O.; Qayyum, A.; Pannek, J. Experimental validation of an accident detection and management application in vehicular environment. Comput. Electr. Eng. 2018, 71, 137–150. [Google Scholar] [CrossRef]
- Cauteruccio, F.; Cinelli, L.; Corradini, E.; Terracina, G.; Ursino, D.; Virgili, L.; Savaglio, C.; Liotta, A.; Fortino, G. A framework for anomaly detection and classification in Multiple IoT scenarios. Futur. Gener. Comput. Syst. 2021, 114, 322–335. [Google Scholar] [CrossRef]
- OWASP Internet of Things Top Ten Project. The Open Web Application Security Project®. 2014. Available online: https://owasp.org/www-project-internet-of-things-top-10/#tab=OWASP_Internet_of_Things_Top_10_for_2014 (accessed on 5 December 2022).
- Aleisa, N.; Renaud, K. Privacy of the Internet of Things: A Systematic Literature Review. In Proceedings of the 50th Hawaii International Conference on System Sciences, Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar] [CrossRef]
- Henriques, T.A.; O’Neill, H. Design science research with focus groups—A pragmatic meta-model. Int. J. Manag. Proj. Bus. 2023, 16, 119–140. [Google Scholar] [CrossRef]
- Dhanda, S.S.; Singh, B.; Jindal, P. Lightweight Cryptography: A Solution to Secure IoT. Wirel. Pers. Commun. 2020, 112, 1947–1980. [Google Scholar] [CrossRef]
- Keerthi, K.; Surendiran, B. Elliptic curve cryptography for secured text encryption. In Proceedings of the 2017 International Conference on Circuit, Power and Computing Technologies (ICCPCT), Kollam, India, 20–21 April 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Hevner, A.; Chatterjee, S. Design Science Research in Information Systems. In Design Research in Information Systems; Integrated Series in Information Systems; Springer: Boston, MA, USA, 2010; Volume 22, pp. 9–22. [Google Scholar] [CrossRef]
- Hevner, A.R. A Three Cycle View of Design Science Research. Scand. J. Inf. Syst. 2007, 19, 4. [Google Scholar]
- Hevner, A.R.; March, S.T.; Park, J.; Ram, S. Design Science in Information Systems Research. Manag. Inf. Syst. Q. 2004, 28, 75–105. [Google Scholar] [CrossRef]
- Imam, R.; Areeb, Q.M.; Alturki, A.; Anwer, F. Systematic and Critical Review of RSA Based Public Key Cryptographic Schemes: Past and Present Status. IEEE Access 2021, 9, 155949–155976. [Google Scholar] [CrossRef]
- Alphonse, R.M.; Malalatiana, R.H.; Choube, M.P. Segment optimization of short message service in telecommunication. Innov. Technol. Methodical Res. J. 2021, 2, 81–88. [Google Scholar] [CrossRef]
- Nayak, M.; Dash, P. Smart surveillance monitoring system using raspberry PI and PIR sensor. Indian J. Text. Res. 2018, 7, 493–495. [Google Scholar]
- Saabith, S.; Thangarajah, V.; Fareez, M. A Review on Python Libraries and IDEs for Data Science. Int. J. Res. Eng. Sci. 2021, 9, 36–53. [Google Scholar]
- Kurniawan, D.E.; Iqbal, M.; Friadi, J.; Borman, R.I.; Rinaldi, R. Smart Monitoring Temperature and Humidity of the Room Server Using Raspberry Pi and Whatsapp Notifications. J. Phys. Conf. Ser. 2019, 1351, 012006. [Google Scholar] [CrossRef]
- Dinculeană, D.; Cheng, X. Vulnerabilities and Limitations of MQTT Protocol Used between IoT Devices. Appl. Sci. 2019, 9, 848. [Google Scholar] [CrossRef]
- Kryvonos, O.; Strutynska, O.; Kryvonos, M. The use of visual electronic circuits modelling and designing software fritzing in the educational process. Zhytomyr Ivan Franko State Univ. Jo. Pedagogical Sci. 2022, 1, 198–208. [Google Scholar] [CrossRef]
- Jacobsen, R.H.; Aliu, D.; Ebeid, E. A Low-cost Vehicle Tracking Platform using Secure SMS. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; SCITEPRESS—Science and Technology Publications: Porto, Portugal, 2017; pp. 157–166. [Google Scholar] [CrossRef]
- Alkhudhayr, F.; Moulahi, T.; Alabdulatif, A. Evaluation Study of Elliptic Curve Cryptography Scalar Multiplication on Raspberry Pi4. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 472–479. [Google Scholar] [CrossRef]
- Narayanan, K.L.; Ram, C.R.S.; Subramanian, M.; Krishnan, R.S.; Robinson, Y.H. IoT based Smart Accident Detection & Insurance Claiming System. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 306–311. [Google Scholar] [CrossRef]
- Gautam, R.; Choudhary, S.; Surbhi Kaur, I.; Bhusry, M. Cloud based automatic accident detection and vehicle management. In Proceedings of the 2nd International Conference on Science Technology and Management, New Delhi, India, 27 September 2015; pp. 341–352. [Google Scholar]
- Jebril, N.A.; Al-Haija, Q.A.; AlBarrak, N.; Almutlaq, G.; Alkhaiwani, A.H. Complete Microcontroller Based Vehicle Accident Detection System with Case Study for Saudi Arabia. Wseas Trans. Commun. Arch. 2017, 16, 118–130. [Google Scholar]
- Ghanem, S.; Ghanim, S. Design and Implementation of an Integrated Vehicle Security System (IVSS). Int. J. Ind. Sustain. Dev. 2022, 3, 87–97. [Google Scholar] [CrossRef]
- Barker, E. Recommendation for Key Management: Part 1—General; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020; NIST SP 800-57pt1r5. [CrossRef]
- Brown, D. Sec 2: Recommended Elliptic Curve Domain Parameters. secg.org. 2010. Available online: https://www.secg.org/sec2-v2.pdf (accessed on 2 November 2022).













| Asymmetric Algorithm | Key Size | Code Length | [20] | Possible Attacks | Key Generation(s) | Signature Generation(s) | Signature Verification(s) | [5] |
| RSA | 1024 | 900 | Module attack, man-in-the-middle, timing | 0.16 | 0.01 | 0.01 | ||
| 15,360 | 679.06 | 9.20 | 0.03 | |||||
| Elliptic curve cryptography (ECC) | 160 | 8838 | Timing attacks, side channel attacks | 0.08 | 0.15 | 0.23 | ||
| 571 | 1.44 | 3.07 | 4.53 |
| Reference | Methodology/Techniques | Measure | Evaluation |
|---|---|---|---|
| [11] | Uses speed and GPS sensors | Accuracy | Prototype |
| [12] | Uses GPS and GSM to detect and send messages | Accuracy | Testing and simulation |
| [13] | Detects the accident using one sensor | Reliability | Testing and simulation |
| [14] | Uses two sensors: accelerometer and GPS | Accuracy | Actual implementation |
| [15] | Uses an accelerometer and GPS for detecting and reporting accidents | Response time | Actual implementation |
| [16] | Based on one sensor: accelerometer for detecting and reporting accidents | Accuracy | Microcontroller Arduino |
| [17] | Uses an accelerometer for detecting and reporting accidents | Response time | Testing and simulation |
| Reference | Vibration | Airbag | GPS | Other | Total | LWC Encryption |
|---|---|---|---|---|---|---|
| [11] | ⊠ | ⊠ | ☑ | ⊠ | 1 | ⊠ |
| [12] | ⊠ | ⊠ | ☑ | ☑ | 2 | ⊠ |
| [13] | ⊠ | ⊠ | ⊠ | ☑ | 1 | ⊠ |
| [14] | ⊠ | ⊠ | ☑ | ☑ | 2 | ⊠ |
| [15] | ⊠ | ⊠ | ☑ | ☑ | 2 | ⊠ |
| [16] | ⊠ | ⊠ | ⊠ | ☑ | 1 | ⊠ |
| [17] | ⊠ | ⊠ | ⊠ | ☑ | 2 | ⊠ |
| Proposed work | ☑ | ☑ | ☑ | ⊠ | 3 | ☑ |
| ☑ | Include | ⊠ | Is not include |
| Raspberry Pi 4 Model B Specifications | |
|---|---|
| Operating system | Raspbian |
| Internet connectivity | Wi-Fi |
| Card size | 4 GB |
| TTL | A9G |
|---|---|
| 5V | USB |
| RX | TX1 |
| TX | RX1 |
| Functional Requirement | Test Conducted | Expected | Actual |
|---|---|---|---|
| QR scanning | The QR barcode is read, and the driver’s information is entered. | The driver can complete all fields with the required information. | The QR is generated by the system. Then, the driver can complete the required information. When the recorded information is complete, the device’s unique ID is created, which can be used during an accident. |
| AS (detection) | The closing of the airbag’s switch is detected. | The airbag communicates with the microprocessor once the airbag switch has been closed or depressed (i.e., blown). | When the airbag button is pressed, the airbag light turns on and sends a signal to the microprocessor to let it know that it has done so. |
| VS (detection) | Once any pressure or shaking is detected. | The VS should send the signal to the microprocessor by delivering a signal as soon as it moves. | The microprocessor is quickly informed that a vibration just occurred when shaking the VS. |
| Locating the position of the vehicle or accident (location recording) | The GPS responds to the signals it receives from the microprocessor. | Once the GPS receives the signals from the microprocessor, it should locate the current position of the accident. | The GPS locates the current position when it receives a request from the microprocessor. |
| Encrypting the message using the ECIES algorithm | Sending the location through the GPS to the microprocessor for application of the ECIES algorithm. | The ECIES algorithm should be utilized by the microprocessor to apply the encryption message through the ECIES utilities library, and the microprocessor should be able to identify the device’s unique ID and GPS location through the encryption message. | GPS provides the device’s unique ID, which the microprocessor recognizes, together with the current location coordinates (longitude and latitude), which are used to encrypt the message. |
| GSM is operational and transmitting an encrypted message | Transmitting the encryption message using GSM and MQTT. | With MQTT, GSM transmits an encrypted message to the CServer. | The GSM sends the MQTT to the CServer after receiving the encrypted message. |
| Receiving the message and decrypting it into the Cserver | Decrypting the message and examining the accident details. | Using the database’s private keys, which are created using the encryption procedure, the message is decrypted, and the accident details are displayed in full on the website’s interface. | The accident’s details are displayed on the website’s interface, and the messages are decrypted. |
| CServer and website display the accident details on the web page | To see the driver’s detailed information. | After decrypting, the required information about the accident is loaded on the site. | The required information about the accident is displayed on the website’s interface. |
| Case Number | Case | Sensor Test | Output/Result |
|---|---|---|---|
| Case 1 | In this case, consider the extracted real vibration value with a system that only has one sensor. | The VS rate is 2200 Hz | Accidents that happen at vibrations lower than this one are not detectable by this system because the detectable vibration is up to 4000 Hz. |
| Case 2 | In this case, consider the extracted real vibration value with a system that only has one sensor. | The VS rate is 4000 Hz | The vibration is activated. The mechanism is activated. However, the accuracy of one sensor’s operation is not enough, and a notification is sent even if it turns out to not have been an accident. |
| Case 3 | In this case, consider the possibility of the AS being activated either as a result of an accident or as a result of manufacturing defects. | The AS bursts | The airbag bursts. The system is triggered in any case, and a message is sent. |
| Case 4 | In this case, consider the possibility of two sensors being triggered simultaneously. | The VS rate is 4000 Hz, and the airbag bursts | When the first and second sensors (VS and AS) are activated (hertz value), an accident is recognized (triggered). |
| Case 5 | In this case, the accident is detected by the sensors, and a message is encrypted using the RSA public/private key size (30) via the ECIES algorithm. | The size of the RSA key is 3072 | The private and public keys are generated with RSA, and the key size is determined using a time-consuming process. |
| Case 6 | In this case, the accident is detected by the sensors, and a message is encrypted using the ECC public/private key size (256) via the ECIES algorithm. | ECC key size is 256 | The private and public keys are generated faster than the RSA key size. |
| Security Level | ECIES Key Length | RSA Key Length |
|---|---|---|
| 80 | 160 | 1024 |
| 112 | 224 | 2048 |
| 128 | 256 | 3072 |
| 192 | 384 | 7680 |
| 256 | 512 | 15,360 |
| Key Size Length | Key Generation Running Time (Sec) | Encryption Process Running Time (Sec) | Decryption Process Running Time (Sec) | ||||
|---|---|---|---|---|---|---|---|
| ECC | RSA | ECC | RSA | ECC | RSA | ECC | RSA |
| 256 | 3072 | 0.0021 | 1.887 | 0.006 | 0.002 | 0.003 | 0.009 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alkhaiwani, A.H.; Alsamani, B.S. A Framework and IoT-Based Accident Detection System to Securely Report an Accident and the Driver’s Private Information. Sustainability 2023, 15, 8314. https://doi.org/10.3390/su15108314
Alkhaiwani AH, Alsamani BS. A Framework and IoT-Based Accident Detection System to Securely Report an Accident and the Driver’s Private Information. Sustainability. 2023; 15(10):8314. https://doi.org/10.3390/su15108314
Chicago/Turabian StyleAlkhaiwani, Amal Hussain, and Badr Soliman Alsamani. 2023. "A Framework and IoT-Based Accident Detection System to Securely Report an Accident and the Driver’s Private Information" Sustainability 15, no. 10: 8314. https://doi.org/10.3390/su15108314
APA StyleAlkhaiwani, A. H., & Alsamani, B. S. (2023). A Framework and IoT-Based Accident Detection System to Securely Report an Accident and the Driver’s Private Information. Sustainability, 15(10), 8314. https://doi.org/10.3390/su15108314













