A Bridge Damage Visualization Technique Based on Image Processing Technology and the IFC Standard
Abstract
:1. Introduction
2. Damage Information Collection Based on Image Processing Technology
2.1. Image Processing
- Graying
- 2.
- Image enhancement
- 3.
- Noise processing
- 4.
- Image segmentation and post processing
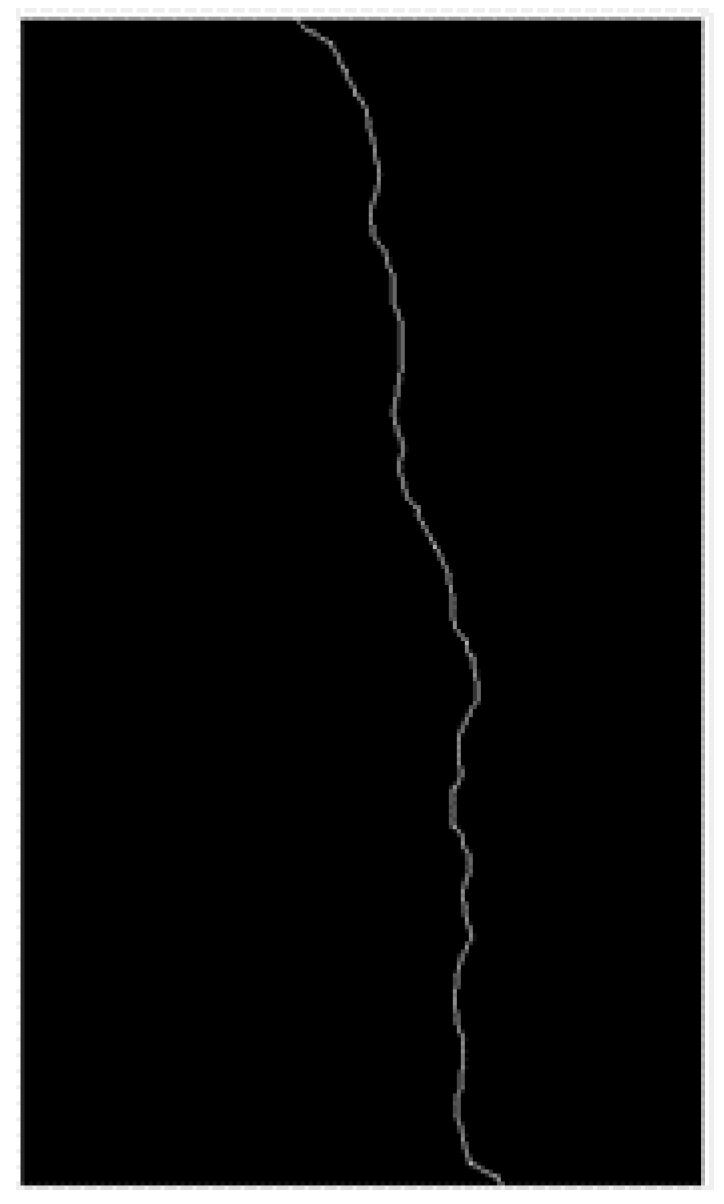
2.2. Extracting Image Information
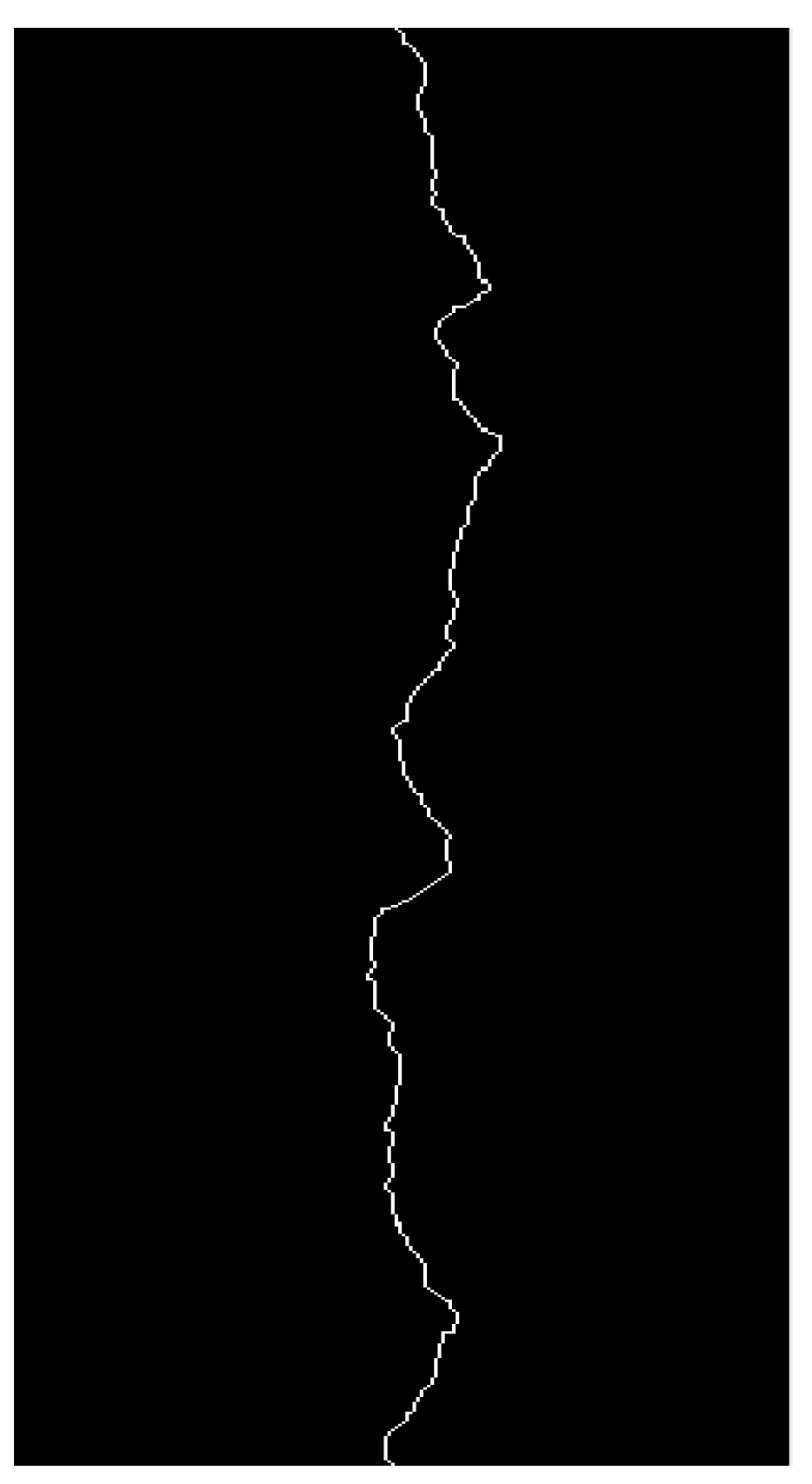
- Obtain crack length
- 2.
- Obtain crack width
- 3.
- The damage area is calculated by pixel points
3. Expression of Bridge Damage Information
3.1. Characteristics of the IFC Architecture
3.2. IFC Expression of Cracks
4. Visual Display of a Cable-Stayed Bridge Damage Information
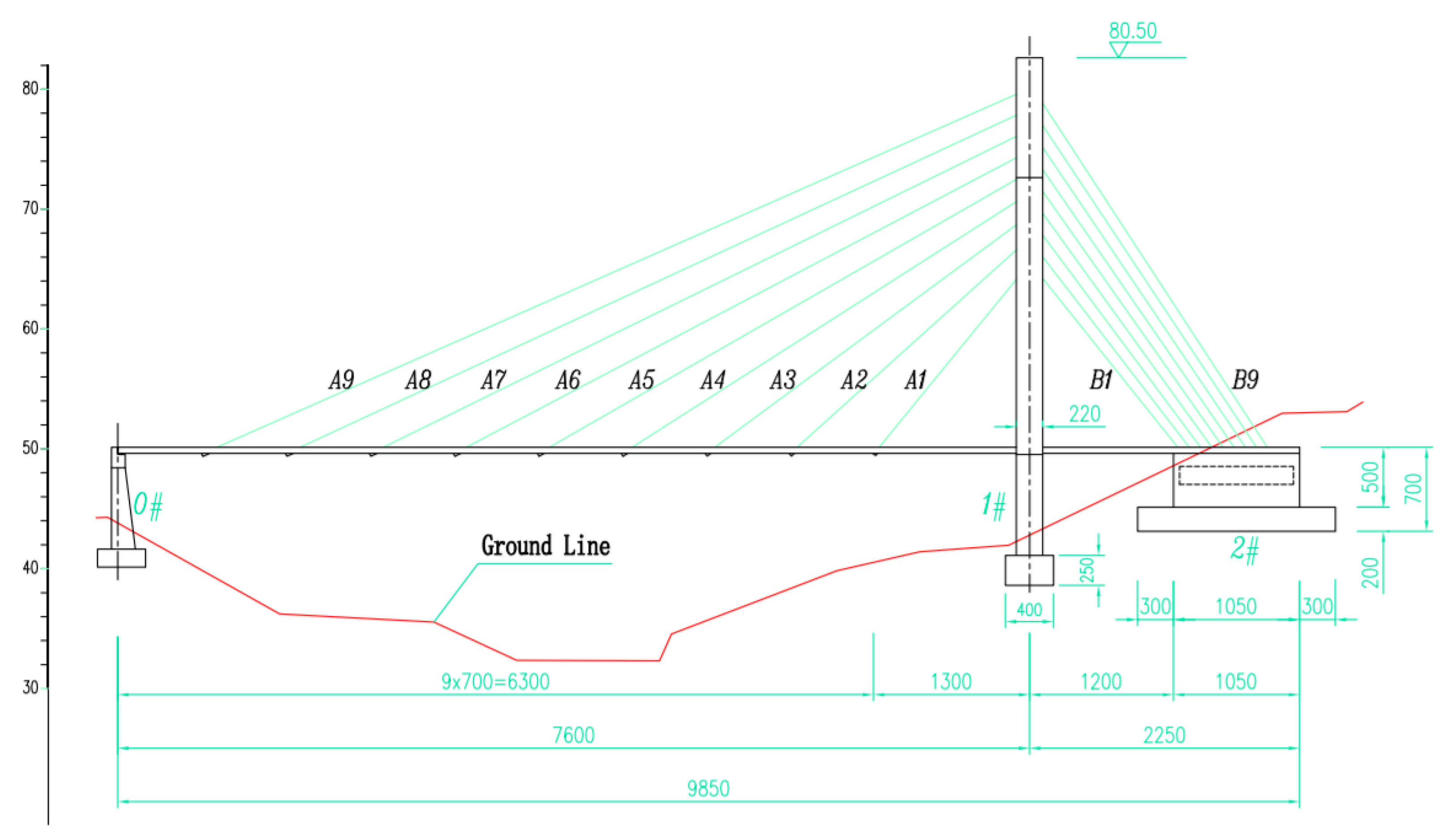
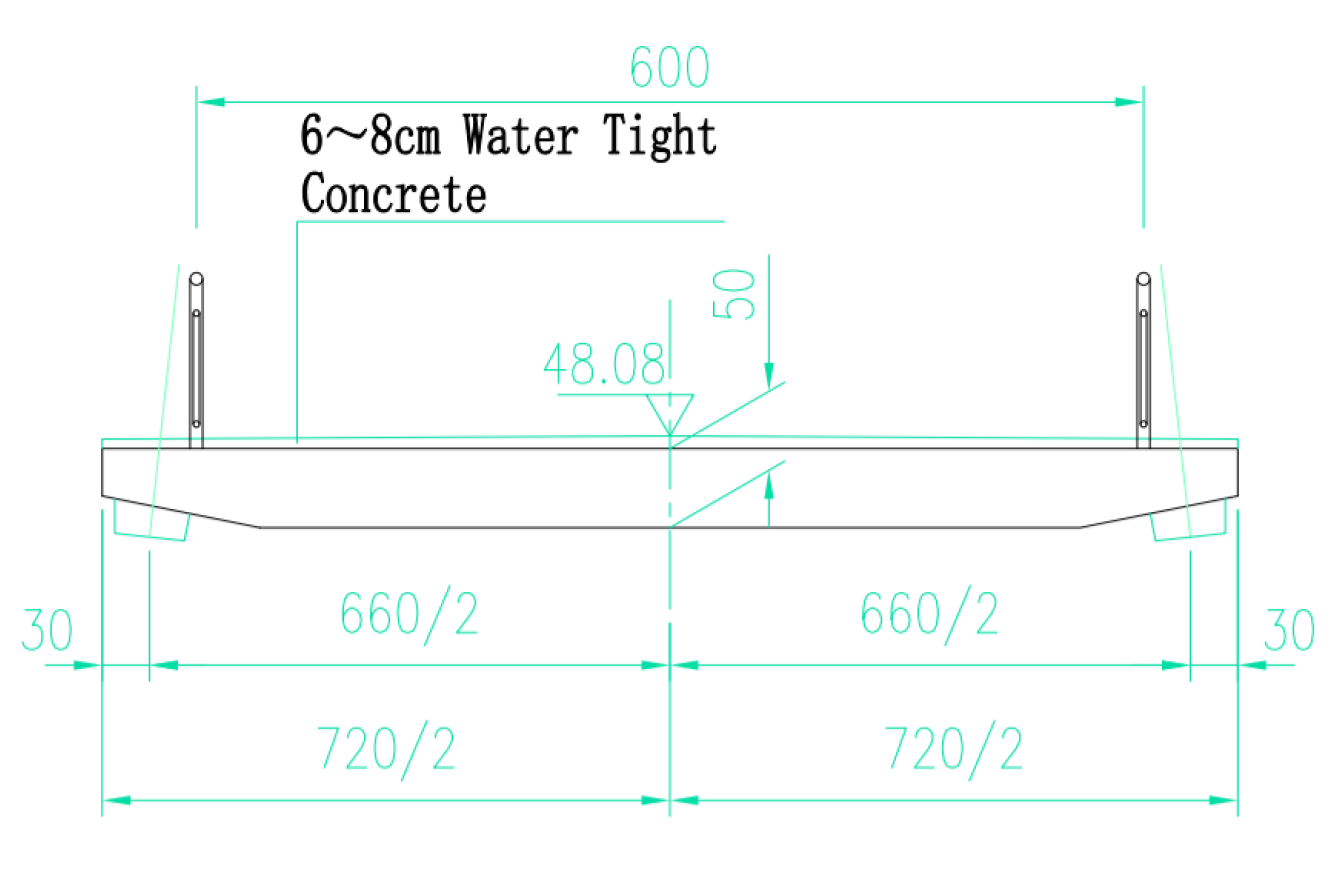
4.1. Project Overview
4.2. Collect and Process Damage Images
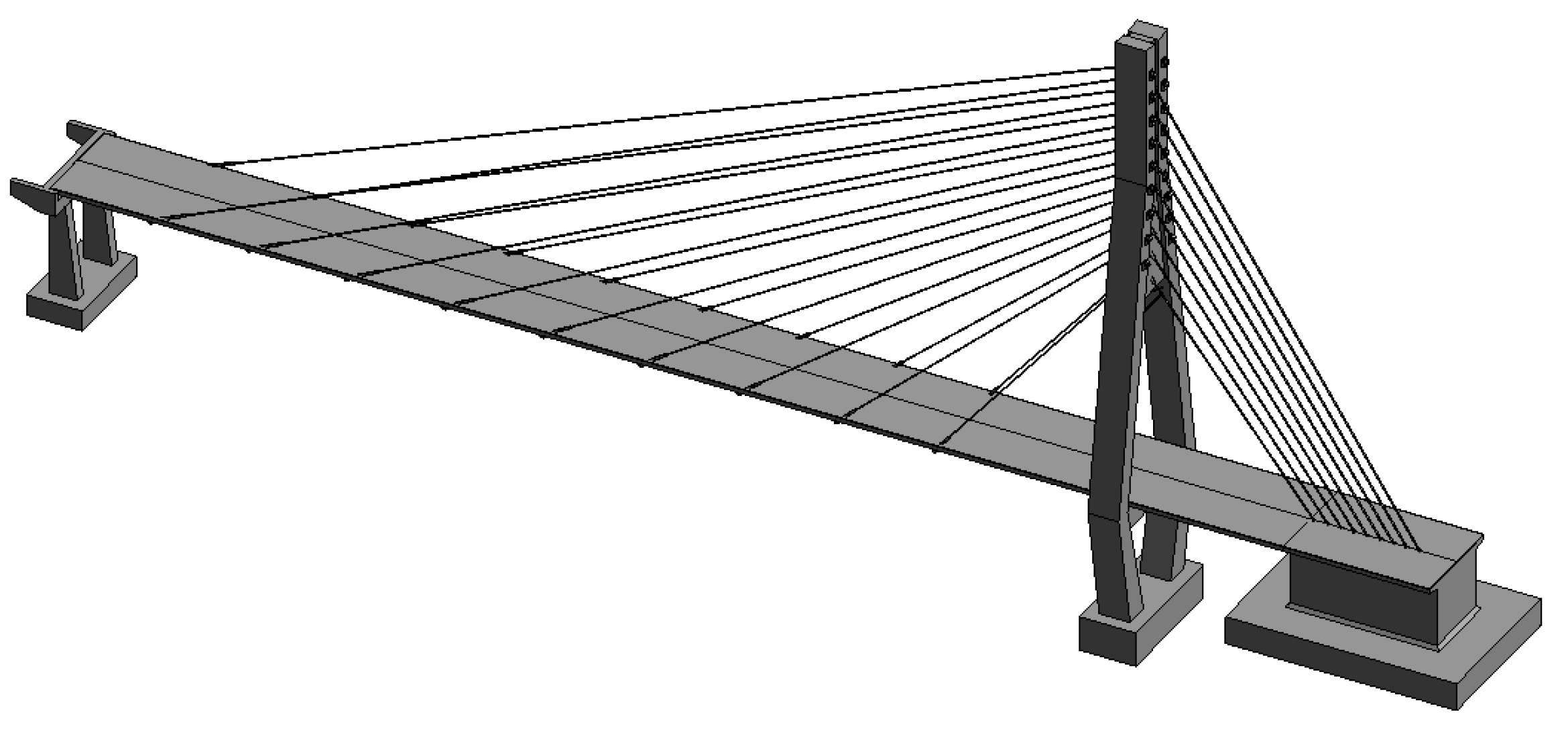
4.3. Establishment of Revit Model of Cable-Stayed Bridge
- Create families for each component of the cable-stayed bridge.
- 2.
- Add family instances
- 3.
- Adjust the position of the family
- 4.
- Add cables
4.4. Visual Expression of Damage Based on IFC
5. Conclusions
- In the process of image collection, the image information collected is too complex due to the environment, noise, equipment and other problems, which increases the difficulty of damage information extraction, so the image needs to be processed. The process is as follows:
- The image is grayed by weighted average method.
- The method of gray adjustment is used to enhance the image.
- The image is denoised by linear filter.
- The Otsu binarization method is used to segment the image.
- The final binary image is obtained by removing the interference of small area image and morphological calculation.
- The relevant information can be extracted after processing the damage image. The skeleton method extracts the crack into the crack skeleton connected by a single pixel. The pixel point statistics method counts the pixel points of crack length, width and damage area. The actual length, width and area are obtained by converting with the actual size.
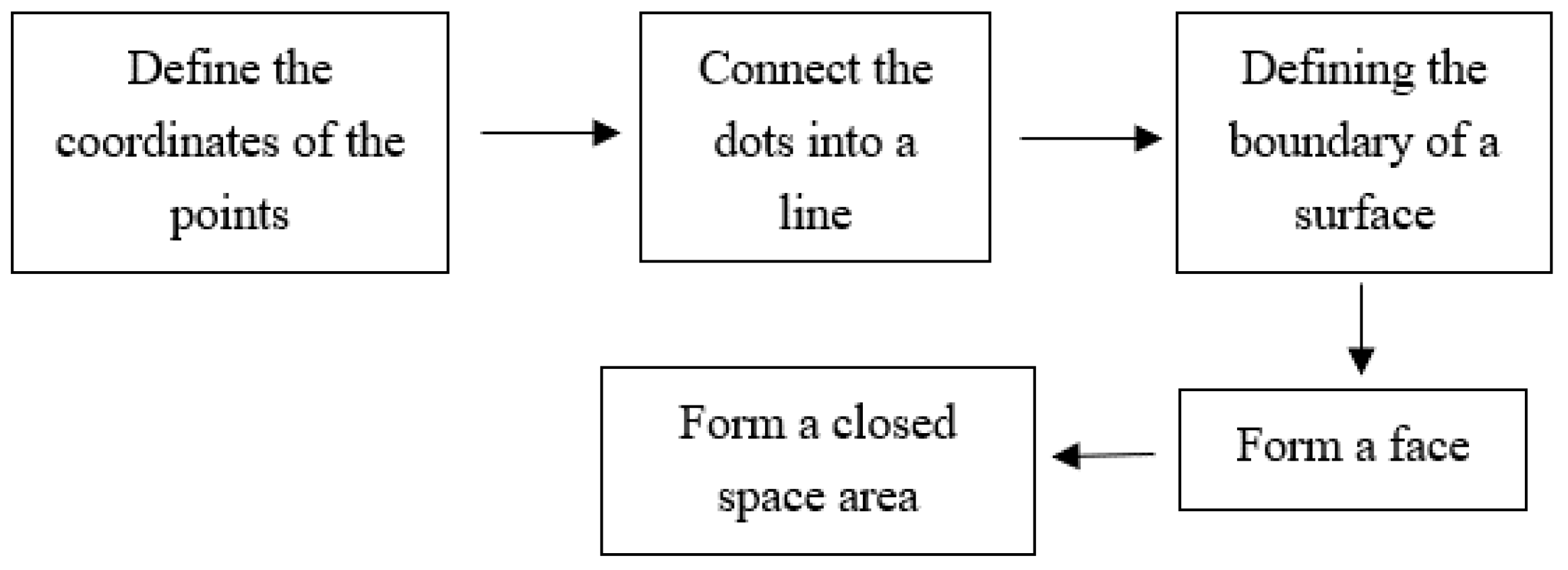
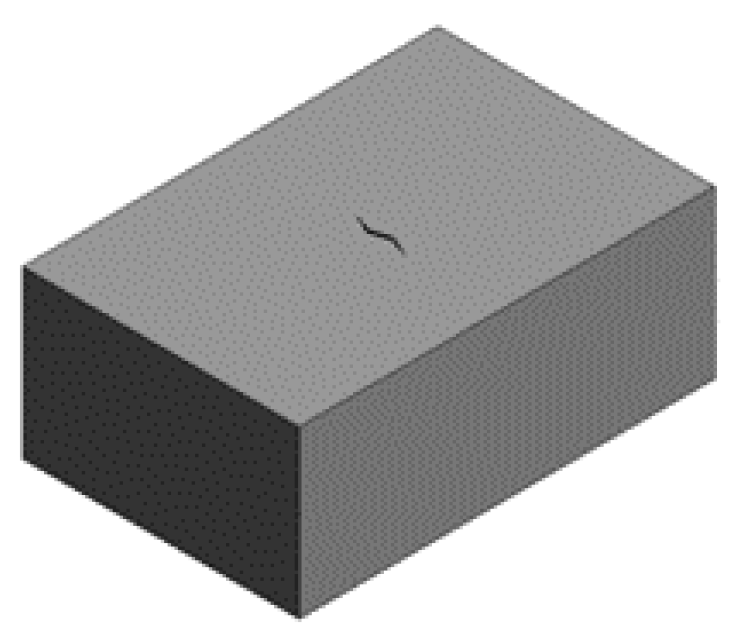
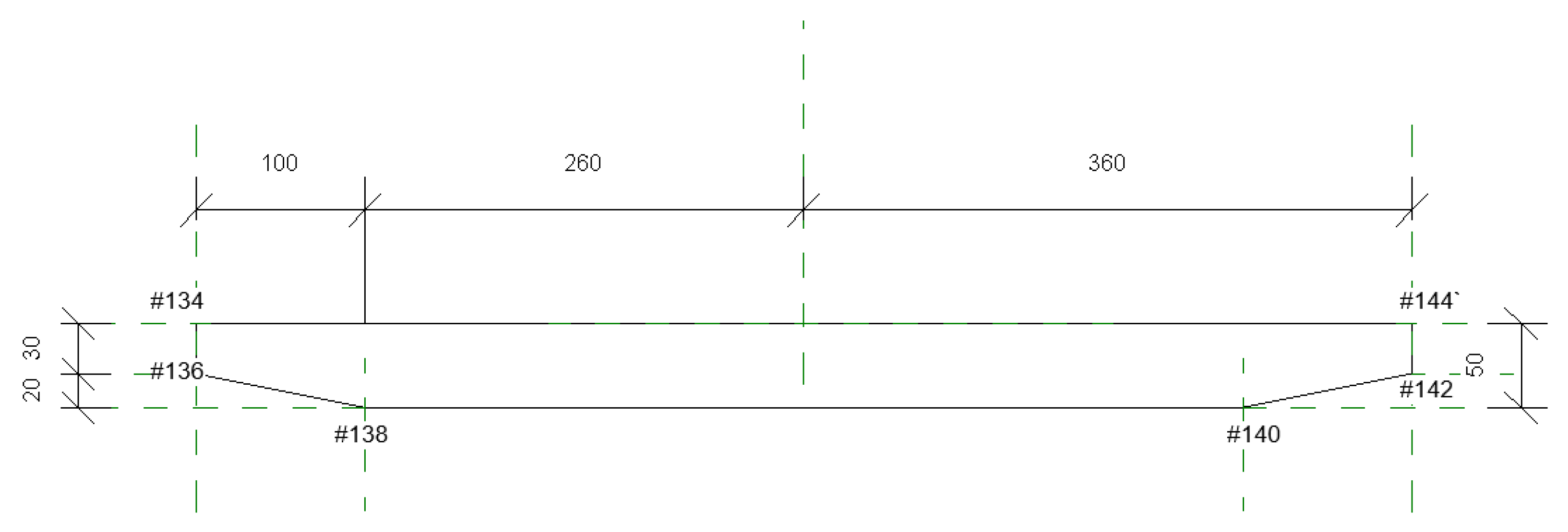
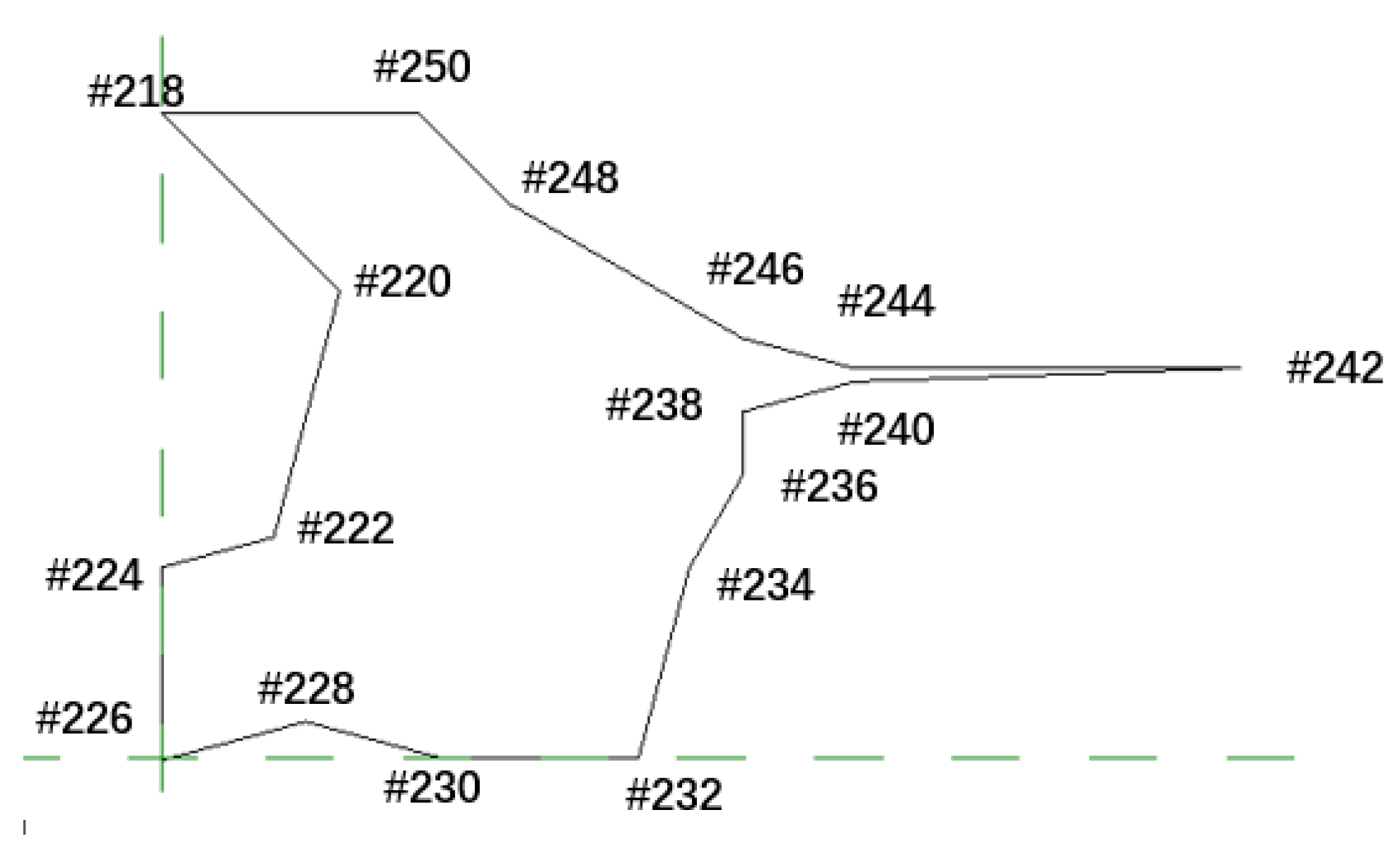
- The damage model is established by the method of boundary representation. The bridge model and the damage are represented as many curved surfaces connected to form a closed space area through the points, lines, planes and the mutual relations to form the bridge model with damage and realize the visualization of the bridge damage.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
References
- Jin, M.; Huang, Z.; Han, Z.; Han, F. Research on Bridge Crack Width Detection Based on Matlab Image Processing Method. J. China Foreign Highw. 2017, 37, 120–123. [Google Scholar] [CrossRef]
- Zuo, D. Research on Bridge Crack Measurement Method Based on Digital Image Processing; Shijiazhuang Tiedao University: Shijiazhuang, China, 2017. [Google Scholar]
- Wang, Q.; Dong, X.; Shen, Z.; Xiong, G.; Yan, J.; Niu, L. An Image-based Automatic Calculation Algorithm for Bridge Crack Size. In Proceedings of the 2019 Chinese Automation Congress (CAC), Hangzhou, China, 22–24 November 2019. [Google Scholar]
- Wang, L. Research on Digital Image Processing Algorithms for Crack Recognition of Concrete Dams; Dalian University of Technology: Dalian, China, 2019. [Google Scholar] [CrossRef]
- Xiao, Z.; Han, H.; Xu, Y. Research on Key Technology of Pavement Crack Recognition Based on Digital Image Processing. J. Jilin Norm. Univ. 2022, 43, 116–120. [Google Scholar] [CrossRef]
- Cevallos-Torres, L.J.; Minda Gilces, D.; Guijarro-Rodriguez, A.; Barriga-Diaz, R.; Leyva-Vazquez, M.; Botto-Tobar, M. An Approach to the Detection of Post-Seismic Structural Damage Based on Image Segmentation Methods; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Tan, X.; Xu, G.; Song, J.; Zhang, J.; Zhou, R.; Yu, T. Recognition of Concrete Surface Cracks Based on Digital Image Processing Technology. Low Temp. Archit. Technol. 2020, 42, 11–13. [Google Scholar] [CrossRef]
- Shao, Y.; Wang, X.; Ren, X.; Yang, C.; Liu, B.; Shan, Y. Semi-automatic Detection Method of Bridge Crack Based on Computer Vision. J. Guizhou Univ. Financ. Econ. 2019, 15, 176–179. [Google Scholar]
- Shi, L.; Yu, Z. Research on On-line Detection Method of Oil Seal Defect Based on Image Processing. J. Chang. Univ. Sci. Technol. 2021, 44, 48–54. [Google Scholar]
- Shen, G. Road crack detection based on video image processing. In Proceedings of the 2016 3rd International Conference on Systems and Informatics (ICSAI), Shanghai, China, 19–21 November 2016; pp. 912–917. [Google Scholar]
- Yang, B. Research on Visualization of Bridge Structure Health Monitoring Information Based on BIM; Chongqing Jiaotong University: Chongqing, China, 2018. [Google Scholar]
- Xu, S.; Wang, J.; Wang, X.; Wu, P.; Shou, W.; Liu, C. A Parameter-Driven Method for Modeling Bridge Defects through IFC. J. Comput. Civ. Eng. 2022. [Google Scholar] [CrossRef]
- Cao, B. Research on Integration and Visualization of Bridge Construction Monitoring Data Based on IFC; Nanjing Forestry University: Nanjing, China, 2020. [Google Scholar] [CrossRef]
- Shi, P. Research on the IFC-Based Component Library; Shanghai Jiao Tong University: Shanghai, China, 2014. [Google Scholar]
- Chu, H. Research on Visual Expression of Bridge Diseases. Master’s Thesis, Huazhong University of Science and Technology, Wuhan, China, 2020. [Google Scholar] [CrossRef]
- Bao, L.; An, P.; Wang, P.; Liang, W.; Yu, L. Research on Visualization of Bridge Safety Information Based on IFC. J. Shenyang Jianzhu Univ. 2022, 38, 682–689. [Google Scholar]
- Wu, Y. Concrete crack information analysis based on IFC standard. J. Guizhou Univ. Financ. Econ. 2017, 13, 157–158. [Google Scholar]
- Ma, J.; Chu, H.; Kong, L.; Guo, X.; Bai, Y. IFC-based Visual Expression of Bridge Damage Information. J. Civ. Eng. Manag. 2020, 37, 66–72. [Google Scholar]
- Hüthwohl, P.; Brilakis, I.; Borrmann, A.; Sacks, R. Integrating RC Bridge Defect Information into BIM Models. J. Comput. Civ. Eng. 2018, 32. [Google Scholar] [CrossRef]
- Isailović, D.; Stojanovic, V.; Trapp, M.; Richter, R.; Hajdin, R.; Döllner, J. Bridge damage: Detection, IFC-based semantic enrichment and visualization. Autom. Constr. 2020, 112, 103088. [Google Scholar] [CrossRef]
- Lim, J.S. Two-Dimensional Signal and Image Processing; Equations 9.44, 9.45, and 9.46; Prentice Hall: Englewood Cliffs, NJ, USA, 1990; p. 548. [Google Scholar]









Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, Y.; Zhang, X.; Chen, H.; Wang, Y.; Wu, H. A Bridge Damage Visualization Technique Based on Image Processing Technology and the IFC Standard. Sustainability 2023, 15, 8769. https://doi.org/10.3390/su15118769
Tian Y, Zhang X, Chen H, Wang Y, Wu H. A Bridge Damage Visualization Technique Based on Image Processing Technology and the IFC Standard. Sustainability. 2023; 15(11):8769. https://doi.org/10.3390/su15118769
Chicago/Turabian StyleTian, Yuan, Xuefan Zhang, Haonan Chen, Yujie Wang, and Hongyang Wu. 2023. "A Bridge Damage Visualization Technique Based on Image Processing Technology and the IFC Standard" Sustainability 15, no. 11: 8769. https://doi.org/10.3390/su15118769
APA StyleTian, Y., Zhang, X., Chen, H., Wang, Y., & Wu, H. (2023). A Bridge Damage Visualization Technique Based on Image Processing Technology and the IFC Standard. Sustainability, 15(11), 8769. https://doi.org/10.3390/su15118769








